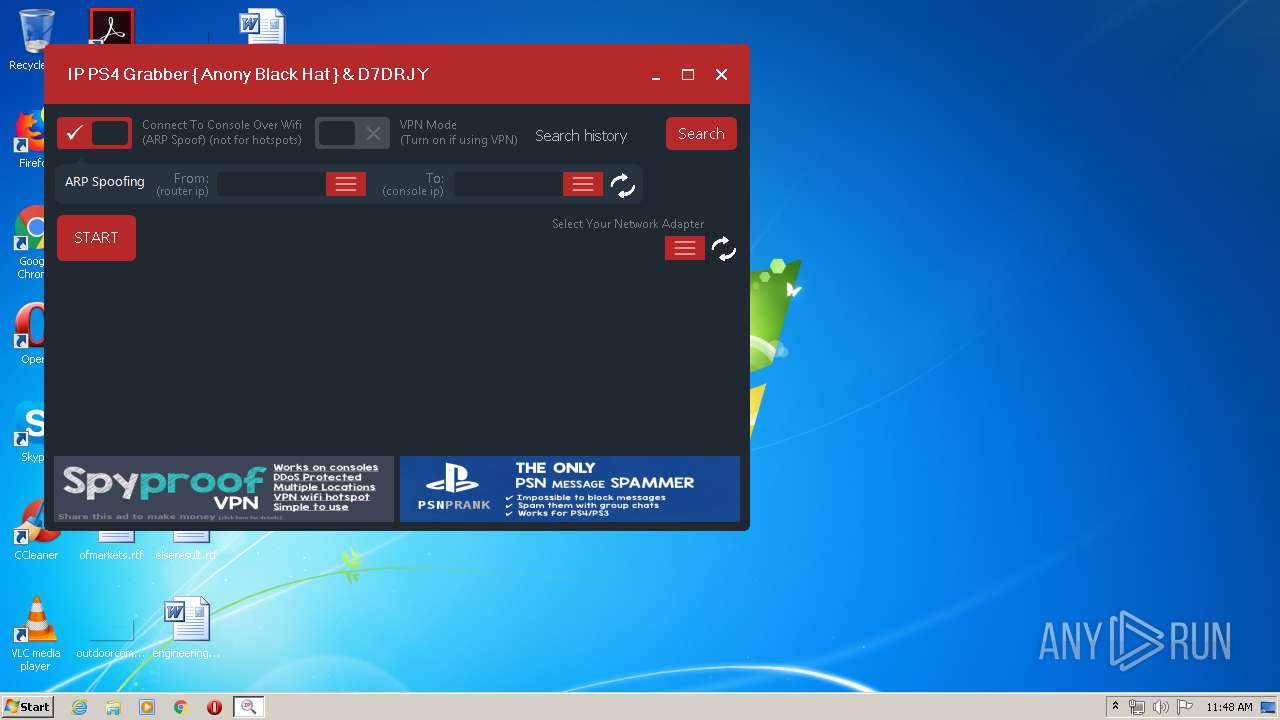
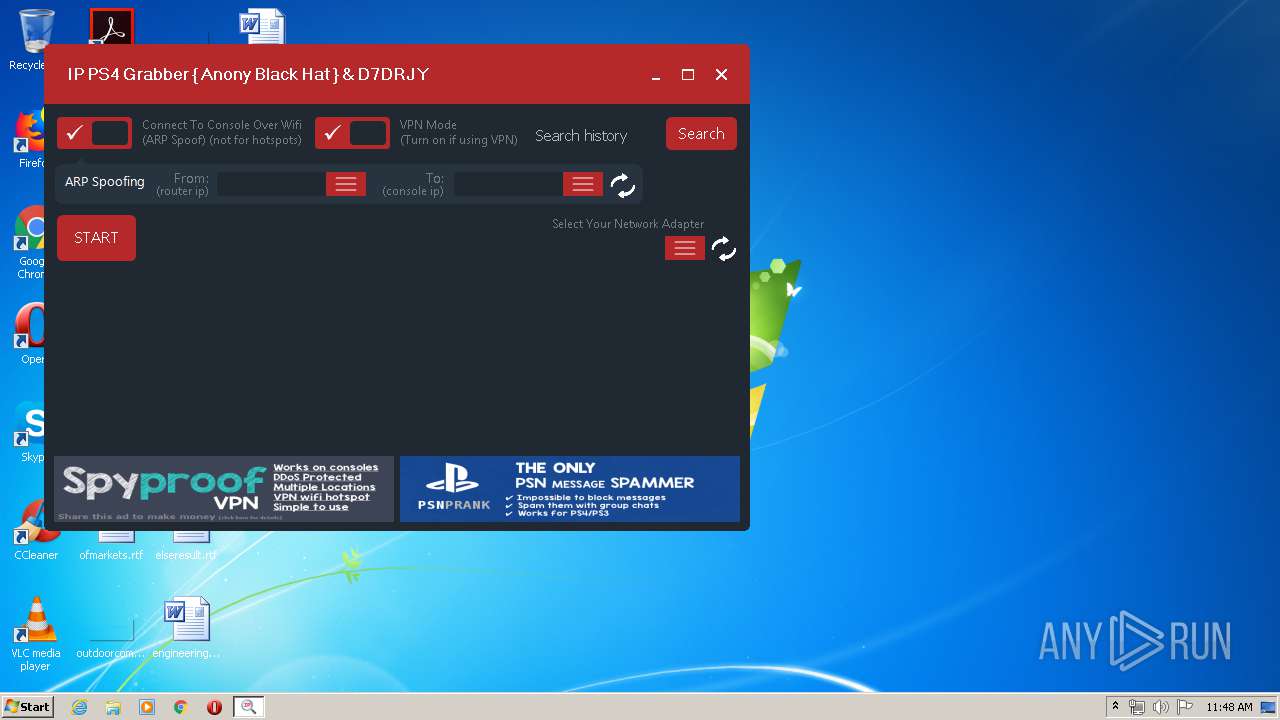
| File name: | ConsoleSniffer.exe |
| Full analysis: | https://app.any.run/tasks/1b0409a5-ae7c-4c6c-a576-0c6316fa0011 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | January 25, 2020, 11:47:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DF5A226B6C70691C85CBF776A17FD221 |
| SHA1: | B9007715C4C3775C6DF8AD77C745DF0CA1F97650 |
| SHA256: | 7E5E87FAF066201221548D5A8912582D7CDFF43DAC06331B68AA81A072F8BD21 |
| SSDEEP: | 24576:T4JMDRy3iWOdqZjdV5vQukdLAk+C4j6tqYsbMGYq+OiDnQArGC11W84UQBrPatc8:ToMDY/kL+ClNtn |
MALICIOUS
Application was dropped or rewritten from another process
- test.exe (PID: 2884)
- ConsoleSniffer v3.exe (PID: 3848)
- ConsoleSniffer v3.exe (PID: 2824)
- boom.exe (PID: 2908)
- WindowsStartup.exe (PID: 1756)
- WindowsRun.exe (PID: 2524)
Drops/Copies Quasar RAT executable
- test.exe (PID: 2884)
- WindowsStartup.exe (PID: 1756)
- boom.exe (PID: 2908)
Writes to the hosts file
- ConsoleSniffer v3.exe (PID: 3848)
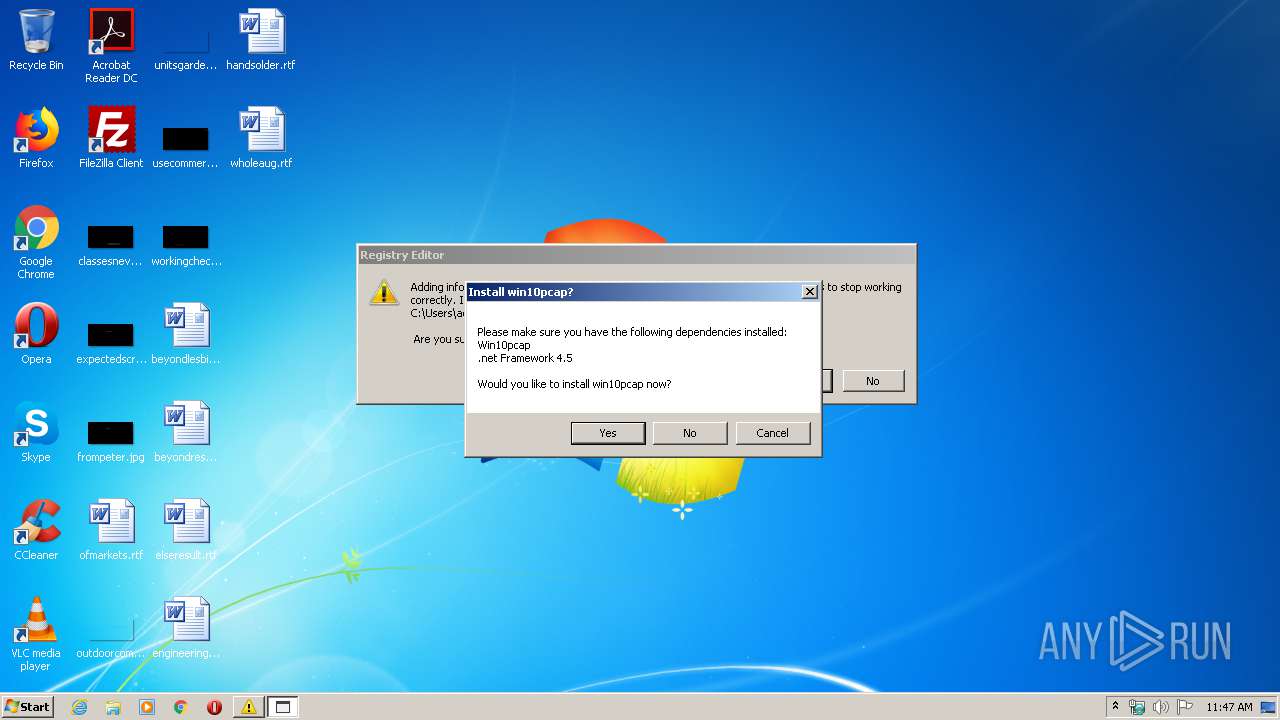
Changes the autorun value in the registry
- WindowsStartup.exe (PID: 1756)
- WindowsRun.exe (PID: 2524)
QUASAR was detected
- WindowsStartup.exe (PID: 1756)
- WindowsRun.exe (PID: 2524)
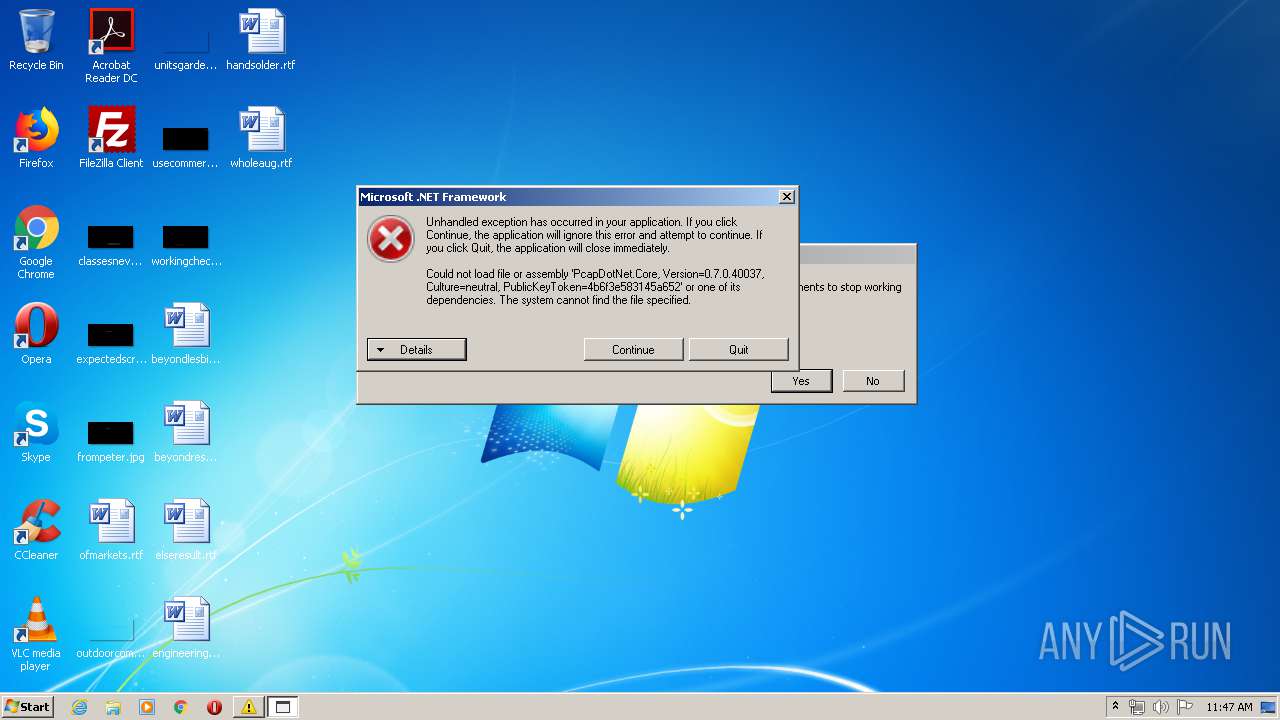
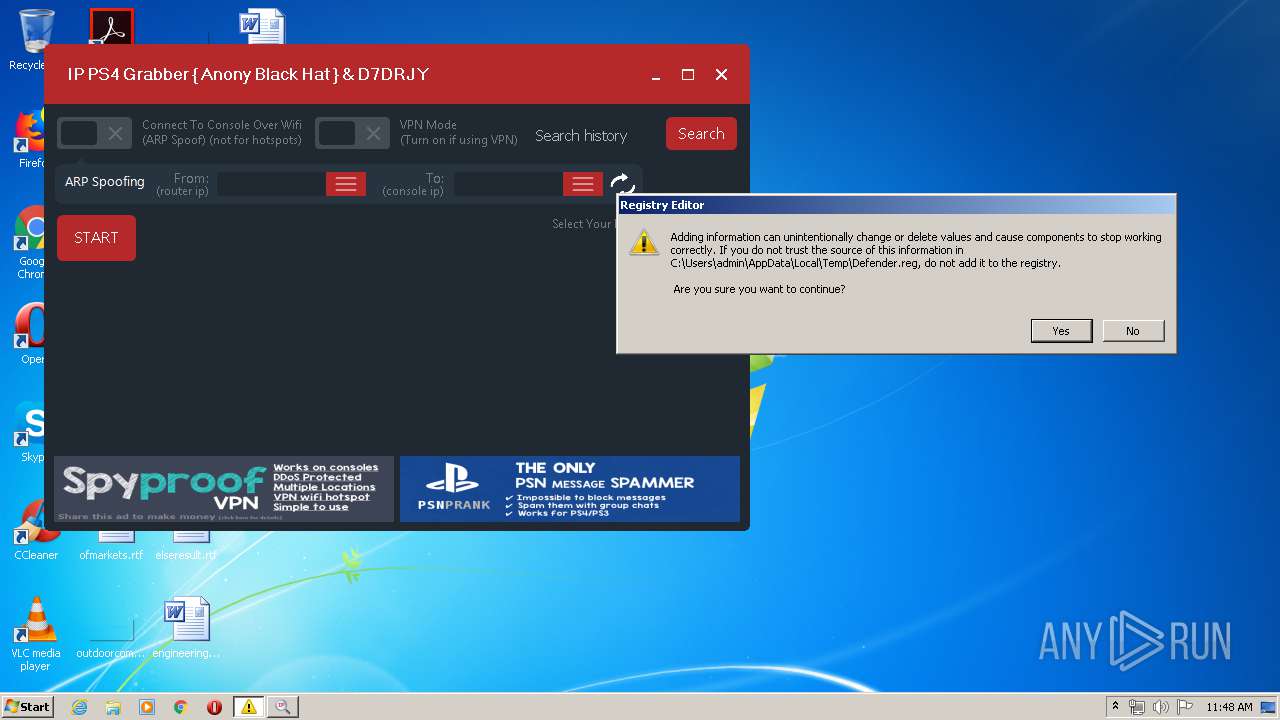
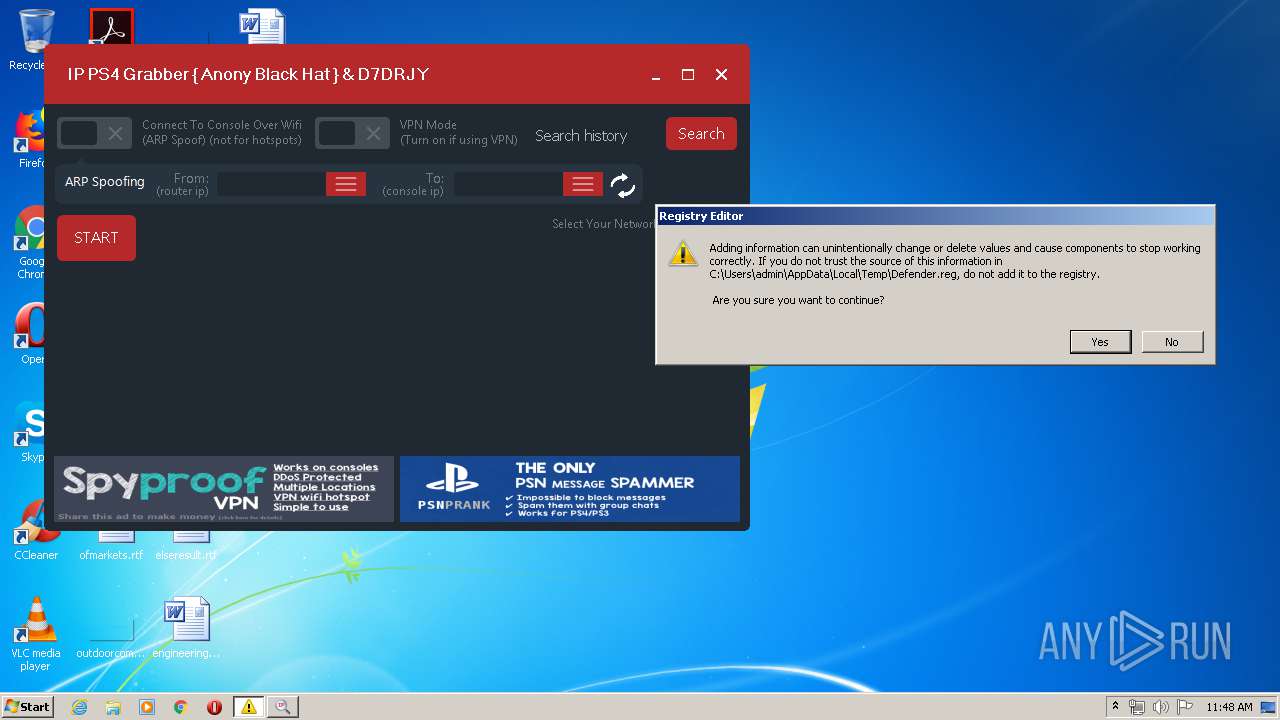
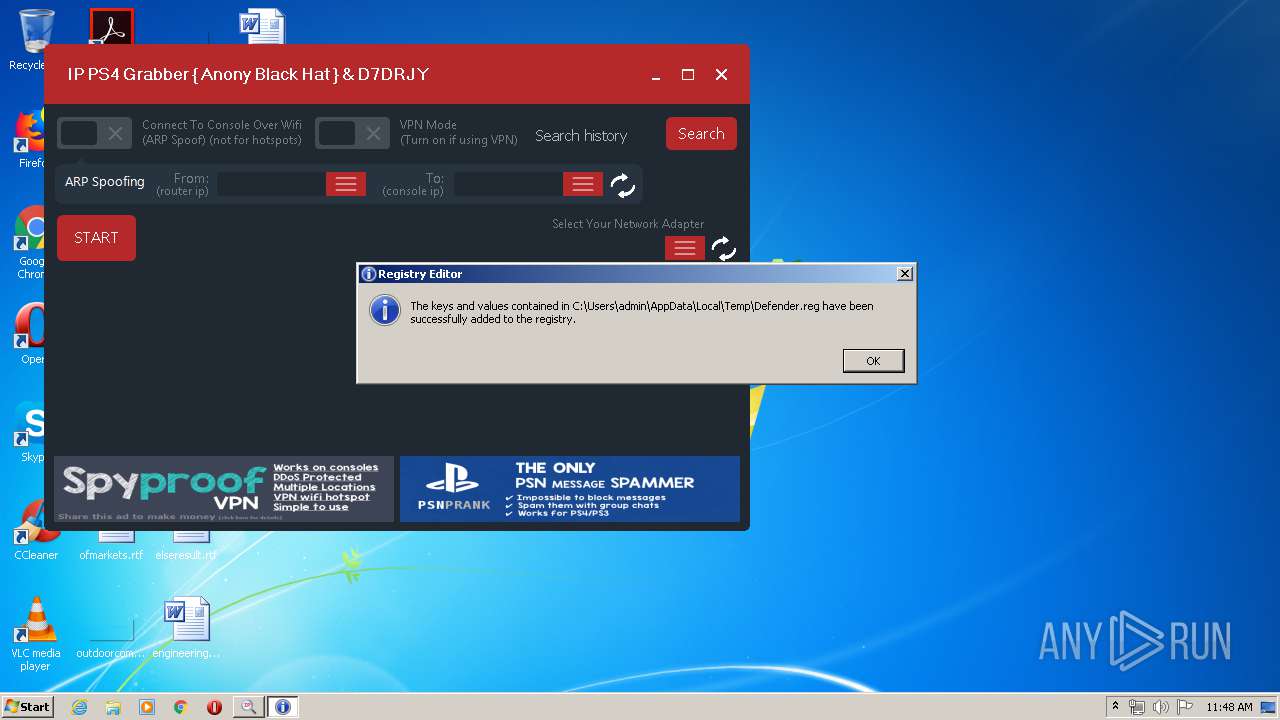
Disables Windows Defender
- regedit.exe (PID: 536)
SUSPICIOUS
Executable content was dropped or overwritten
- WindowsStartup.exe (PID: 1756)
- boom.exe (PID: 2908)
- ConsoleSniffer.exe (PID: 3924)
- test.exe (PID: 2884)
Starts itself from another location
- WindowsStartup.exe (PID: 1756)
Creates files in the user directory
- WindowsStartup.exe (PID: 1756)
Checks for external IP
- WindowsStartup.exe (PID: 1756)
- WindowsRun.exe (PID: 2524)
INFO
Reads the hosts file
- ConsoleSniffer v3.exe (PID: 3848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (96.4) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.3) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 78336 |
| InitializedDataSize: | 1093120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x138e0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x00013044 | 0x00013200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.43594 |
DATA | 0x00015000 | 0x0000060C | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.51863 |
BSS | 0x00016000 | 0x00000CA5 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00017000 | 0x00000A50 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.26186 |
.tls | 0x00018000 | 0x0000000C | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00019000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x0001A000 | 0x000018B8 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.52837 |
.rsrc | 0x0001C000 | 0x00107D08 | 0x00107E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.85513 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 6.80354 | 1049088 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
2 | 2.32126 | 108 | Latin 1 / Western European | English - United States | RT_STRING |
4090 | 2.96843 | 348 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4091 | 3.20818 | 520 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4092 | 3.02839 | 236 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4093 | 3.20724 | 408 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4094 | 3.20409 | 948 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4095 | 3.25436 | 892 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4096 | 3.18442 | 672 | Latin 1 / Western European | UNKNOWN | RT_STRING |
DVCLAL | 4 | 16 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
advapi32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
winmm.dll |
Total processes
47
Monitored processes
9
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\Defender.reg" | C:\Windows\regedit.exe | test.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1392 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\Defender.reg" | C:\Windows\regedit.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1756 | "C:\Users\admin\AppData\Local\Temp\WindowsStartup.exe" | C:\Users\admin\AppData\Local\Temp\WindowsStartup.exe | test.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\AppData\Roaming\WindowsRep\WindowsRun.exe" | C:\Users\admin\AppData\Roaming\WindowsRep\WindowsRun.exe | WindowsStartup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
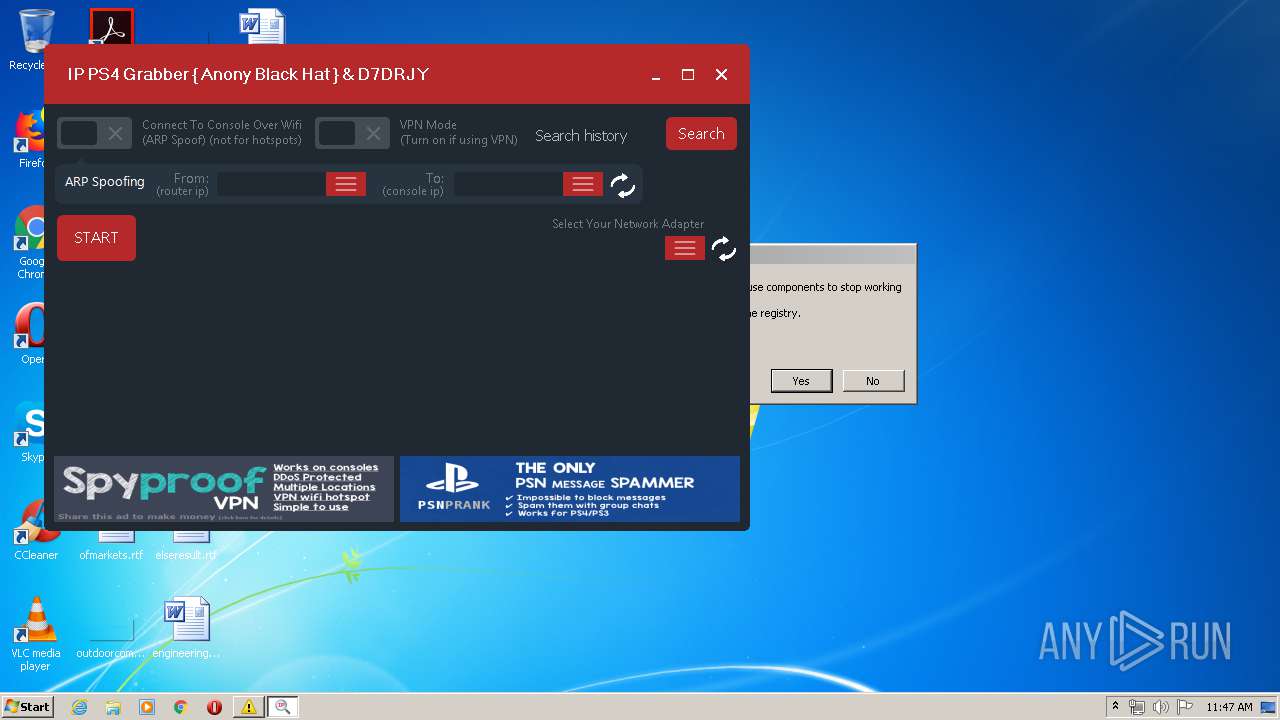
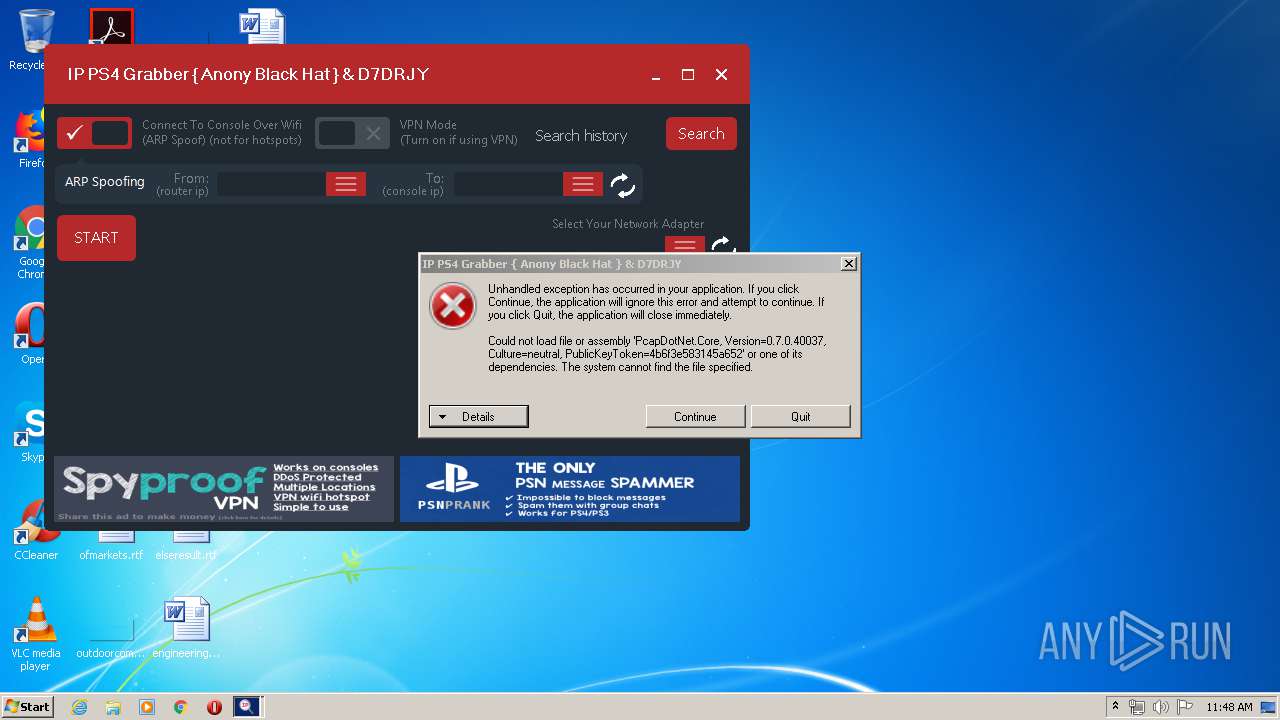
| 2824 | "C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe" | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: IP Grabber Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2884 | "C:\Users\admin\AppData\Local\Temp\test.exe" | C:\Users\admin\AppData\Local\Temp\test.exe | boom.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2908 | "C:\Users\admin\AppData\Local\Temp\boom.exe" | C:\Users\admin\AppData\Local\Temp\boom.exe | ConsoleSniffer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3848 | "C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe" | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe | test.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: IP Grabber Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3924 | "C:\Users\admin\AppData\Local\Temp\ConsoleSniffer.exe" | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 192
Read events
1 128
Write events
64
Delete events
0
Modification events
| (PID) Process: | (3924) ConsoleSniffer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3924) ConsoleSniffer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2908) boom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2908) boom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2884) test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2884) test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3848) ConsoleSniffer v3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3848) ConsoleSniffer v3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1756) WindowsStartup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WindowsStartup_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1756) WindowsStartup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WindowsStartup_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
5
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | ConsoleSniffer v3.exe | C:\Users\admin\AppData\Local\Microsoft\ConsoleSniffer_v3.exe_Url_vmunlbebiyuo3heqvx0jltqvvxm21j50\0.0.0.0\ncpzsmzo.newcfg | — | |
MD5:— | SHA256:— | |||
| 3848 | ConsoleSniffer v3.exe | C:\Users\admin\AppData\Local\Microsoft\ConsoleSniffer_v3.exe_Url_vmunlbebiyuo3heqvx0jltqvvxm21j50\0.0.0.0\etdxx43u.newcfg | — | |
MD5:— | SHA256:— | |||
| 2884 | test.exe | C:\Users\admin\AppData\Local\Temp\Defender.reg | text | |
MD5:— | SHA256:— | |||
| 2908 | boom.exe | C:\Users\admin\AppData\Local\Temp\test.exe | executable | |
MD5:— | SHA256:— | |||
| 1756 | WindowsStartup.exe | C:\Users\admin\AppData\Roaming\WindowsRep\WindowsRun.exe | executable | |
MD5:— | SHA256:— | |||
| 2884 | test.exe | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe | executable | |
MD5:— | SHA256:— | |||
| 2884 | test.exe | C:\Users\admin\AppData\Local\Temp\WindowsStartup.exe | executable | |
MD5:— | SHA256:— | |||
| 3924 | ConsoleSniffer.exe | C:\Users\admin\AppData\Local\Temp\boom.exe | executable | |
MD5:— | SHA256:— | |||
| 3848 | ConsoleSniffer v3.exe | C:\Windows\system32\drivers\etc\hosts | text | |
MD5:39F8EFE05107321AAB5AB51708F80342 | SHA256:C9605FDDD86CFD3FABF92A205798554771F8FCE1F73AE64CC04241A2E7324BB4 | |||
| 3848 | ConsoleSniffer v3.exe | C:\Users\admin\AppData\Local\Microsoft\ConsoleSniffer_v3.exe_Url_vmunlbebiyuo3heqvx0jltqvvxm21j50\0.0.0.0\user.config | xml | |
MD5:7790B9794A63B1B1836FE9CE2EE95577 | SHA256:43BF8409F2C1B653012A09E15E3916136F0E79184C522DDE69C18B101459271D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
24
DNS requests
2
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1756 | WindowsStartup.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 261 b | malicious |
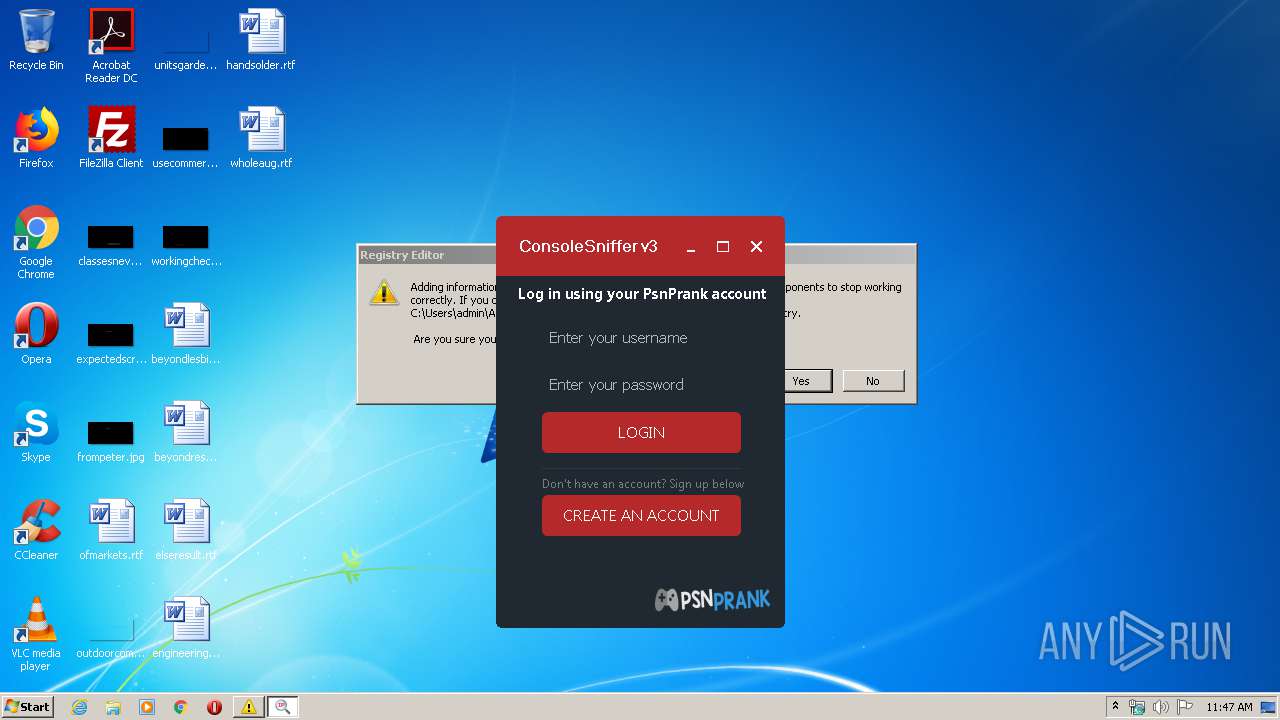
3848 | ConsoleSniffer v3.exe | GET | 200 | 149.56.133.157:80 | http://hub.psnprank.com/api/?access_token=5END8JmdxU8%3D&user=Enter%20your%20username&pass=Enter%20your%20password&a=search_history&search=Search%20history | CA | text | 34 b | unknown |
2524 | WindowsRun.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 261 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2524 | WindowsRun.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2524 | WindowsRun.exe | 185.217.1.170:56098 | — | Icme Limited | SE | malicious |
3848 | ConsoleSniffer v3.exe | 149.56.133.157:80 | hub.psnprank.com | OVH SAS | CA | unknown |
— | — | 185.217.1.170:56098 | — | Icme Limited | SE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
hub.psnprank.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1756 | WindowsStartup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
1756 | WindowsStartup.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1756 | WindowsStartup.exe | A Network Trojan was detected | REMOTE [PTsecurity] Quasar.RAT IP Lookup |
2524 | WindowsRun.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2524 | WindowsRun.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2524 | WindowsRun.exe | A Network Trojan was detected | REMOTE [PTsecurity] Quasar.RAT IP Lookup |
2 ETPRO signatures available at the full report