| File name: | 0001.jar |
| Full analysis: | https://app.any.run/tasks/900d09f7-9234-4878-9dc3-d913b94b8f11 |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | March 22, 2019, 12:55:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | 56B47AAD764420C992F9978422D1369B |
| SHA1: | C06AD08490B4094AF8FF34E5308325415AE55A2B |
| SHA256: | 7DEF2FD14185D19343A8B29B46D1F4B098D65CD41EC12C6093B0A84673BBF1ED |
| SSDEEP: | 12288:EildeU2PqqnujO9pIUy3hhdQBp0fpiYrHj+OynYeolc8OW8JJG:9deUydnuOXIh3XM0fzrDbyolv |
MALICIOUS
Loads dropped or rewritten executable
- javaw.exe (PID: 604)
- java.exe (PID: 2448)
- explorer.exe (PID: 1696)
- javaw.exe (PID: 1452)
- java.exe (PID: 2728)
Application was dropped or rewritten from another process
- java.exe (PID: 2448)
- javaw.exe (PID: 604)
- javaw.exe (PID: 1452)
- java.exe (PID: 2728)
Changes the autorun value in the registry
- reg.exe (PID: 1484)
AdWind was detected
- java.exe (PID: 2728)
- java.exe (PID: 2448)
Uses TASKKILL.EXE to kill security tools
- javaw.exe (PID: 1452)
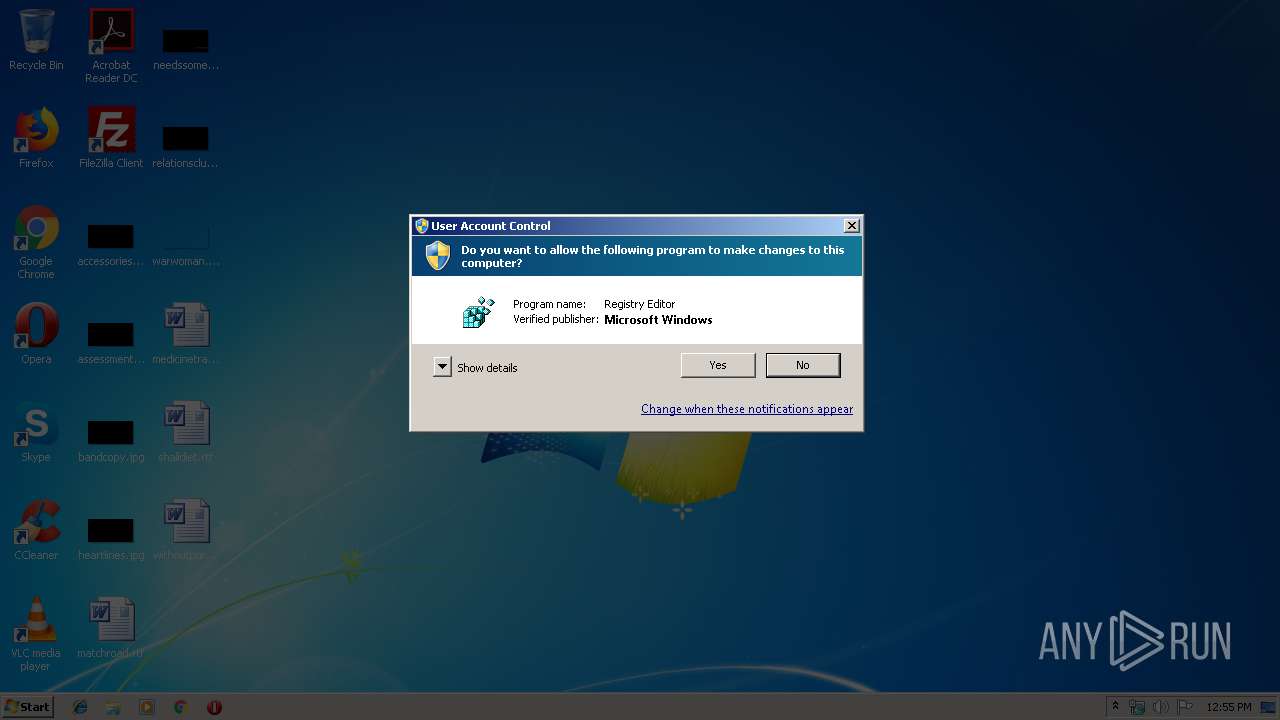
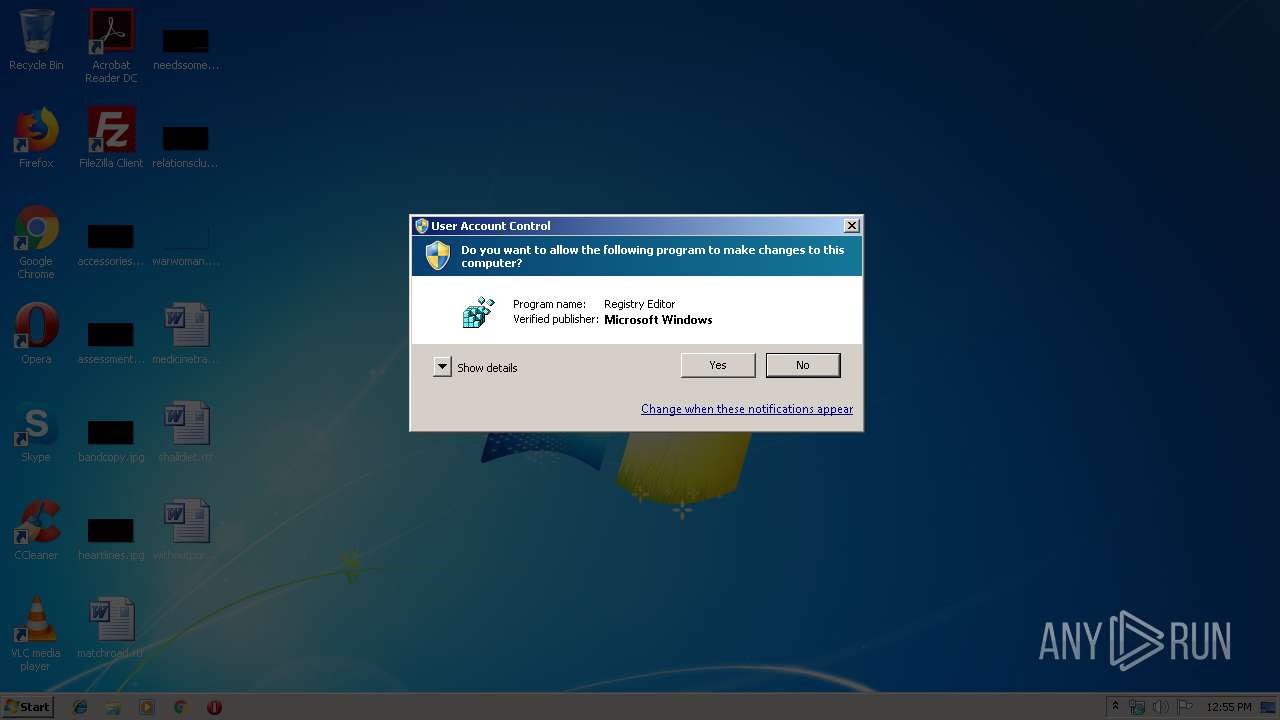
UAC/LUA settings modification
- regedit.exe (PID: 2736)
Turns off system restore
- regedit.exe (PID: 2736)
Changes Image File Execution Options
- regedit.exe (PID: 2736)
SUSPICIOUS
Executes JAVA applets
- explorer.exe (PID: 1696)
- javaw.exe (PID: 604)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 604)
- java.exe (PID: 2448)
- javaw.exe (PID: 1452)
- java.exe (PID: 2728)
Executable content was dropped or overwritten
- xcopy.exe (PID: 4080)
Executes scripts
- cmd.exe (PID: 236)
- cmd.exe (PID: 2932)
- cmd.exe (PID: 1308)
- cmd.exe (PID: 2264)
- cmd.exe (PID: 2028)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 1708)
- cmd.exe (PID: 2312)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 604)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 604)
Starts itself from another location
- javaw.exe (PID: 604)
Uses TASKKILL.EXE to kill process
- javaw.exe (PID: 1452)
Creates files in the user directory
- xcopy.exe (PID: 4080)
- javaw.exe (PID: 604)
Connects to unusual port
- javaw.exe (PID: 1452)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:03:22 06:49:19 |
| ZipCRC: | 0xf0ee3c85 |
| ZipCompressedSize: | 45 |
| ZipUncompressedSize: | 43 |
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
135
Monitored processes
58
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | taskkill /IM rawshark.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 236 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8851972597497137330.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 516 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive610888907110789446.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 588 | taskkill /IM AdAwareTray.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\0001.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 888 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive1906954328283530784.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 964 | taskkill /IM MsMpEng.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1004 | taskkill /IM editcap.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1012 | cmd.exe /c regedit.exe /s C:\Users\admin\AppData\Local\Temp\wGSPFXvsnW8485963487450573992.reg | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1020 | taskkill /IM mbam.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
602
Read events
389
Write events
213
Delete events
0
Modification events
| (PID) Process: | (1696) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000418795FC2F2C5A46852A5EA30B2A11D100000000020000000000106600000001000020000000793B7EC605911E587DD40C99F6C96120D3A38D14F48EE7BAA20B9F22D8B349BB000000000E8000000002000020000000D876B59D73AA4911F0D6D8B419D5EFAEE0B2364260881622630A0192B802593530000000F9148009AA25D8BE6824CCDA4A7CD128FFB62788319888330528C6681FA57717DD5293814052A9E625413DA12BB8E46B4000000024BD27A6A6C2C9BB1A83A696F63ECBD447C4E8845B5F9DB05FE50839650D9C90A81C1438DB058031044015A82402A7CF7E71F3E11FDDC9275AD5A5EFBD20FDC2 | |||
| (PID) Process: | (1484) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | OLHJrJbzZOE |
Value: "C:\Users\admin\AppData\Roaming\Oracle\bin\javaw.exe" -jar "C:\Users\admin\jCpCiFHRafc\ycBtNUaHmPW.cYiRDO" | |||
| (PID) Process: | (1012) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1012) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2736) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments |
| Operation: | write | Name: | SaveZoneInformation |
Value: 1 | |||
| (PID) Process: | (2736) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations |
| Operation: | write | Name: | LowRiskFileTypes |
Value: .avi;.bat;.com;.cmd;.exe;.htm;.html;.lnk;.mpg;.mpeg;.mov;.mp3;.msi;.m3u;.rar;.reg;.txt;.vbs;.wav;.zip;.jar; | |||
| (PID) Process: | (2736) regedit.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | SEE_MASK_NOZONECHECKS |
Value: 1 | |||
| (PID) Process: | (2736) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Environment |
| Operation: | write | Name: | SEE_MASK_NOZONECHECKS |
Value: 1 | |||
| (PID) Process: | (2736) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\UserAccountControlSettings.exe |
| Operation: | write | Name: | debugger |
Value: svchost.exe | |||
| (PID) Process: | (2736) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
Executable files
109
Suspicious files
10
Text files
74
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 604 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Retrive186981662629774058.vbs | — | |
MD5:— | SHA256:— | |||
| 2448 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 4080 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\README.txt | text | |
MD5:0F1123976B959AC5E8B89EB8C245C4BD | SHA256:963095CF8DB76FB8071FD19A3110718A42F2AB42B27A3ADFD9EC58981C3E88D2 | |||
| 4080 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\THIRDPARTYLICENSEREADME.txt | text | |
MD5:745D6DB5FC58C63F74CE6A7D4DB7E695 | SHA256:C77BA9F668FEE7E9B810F1493E518ADF87233AC8793E4B37C9B3D1ED7846F1C0 | |||
| 4080 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\bin\awt.dll | executable | |
MD5:775D4B37E0DDBFA0EB56DB38126FB444 | SHA256:E5D4FC7D47A38A389884AF1EA5F06F7C61C5CDE6AFC154A23A3CB5A127DA1E34 | |||
| 4080 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\bin\dcpr.dll | executable | |
MD5:682CFD9431E5675900B04FEBE6CD4EB9 | SHA256:80111E1D706741F5EF7F661835C3AA46664666425AA1B5F93103410F2BEE1213 | |||
| 4080 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\Welcome.html | html | |
MD5:27CF299B6D93FACA73FBCDCF4AECFD93 | SHA256:3F1F0EE75588DBBA3B143499D08AA9AB431E4A34E483890CFAC94A8E1061B7CF | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive8851972597497137330.vbs | text | |
MD5:3BDFD33017806B85949B6FAA7D4B98E4 | SHA256:9DA575DD2D5B7C1E9BAB8B51A16CDE457B3371C6DCDB0537356CF1497FA868F6 | |||
| 4080 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\bin\decora_sse.dll | executable | |
MD5:94434B8739CB5CD184C63CEC209F06E2 | SHA256:ADF4E9CE0866FF16A16F626CFC62355FB81212B1E7C95DD908E3644F88B77E91 | |||
| 604 | javaw.exe | C:\Users\admin\AppData\Local\Temp\_0.0107966152676050034296110836936282348.class | java | |
MD5:781FB531354D6F291F1CCAB48DA6D39F | SHA256:97D585B6AFF62FB4E43E7E6A5F816DCD7A14BE11A88B109A9BA9E8CD4C456EB9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1452 | javaw.exe | 95.213.251.165:5954 | slimyuyo.duckdns.org | OOO Network of data-centers Selectel | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
slimyuyo.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1072 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |