| File name: | main (2).exe |
| Full analysis: | https://app.any.run/tasks/fb41a04e-62f7-4e00-a30f-d1c398f39e57 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | April 10, 2025, 05:24:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 25997083481BB4EA1B124799F151AC0F |
| SHA1: | BDB0C81B2BEABC682A88F02BA958C574F04A24A4 |
| SHA256: | 7D013CB3991DD2F4C88091FB4CB7DCC6B282A9175914EF2CB44E91C0EBAFDEA2 |
| SSDEEP: | 98304:Bzo5Pu7ZuqLBxTMjjZjhq/Z+buYlxakJx69Xz7L8MzowjRkKoy4PQap9UgtEVc/o:X6zl0ys6uR |
MALICIOUS
Changes the autorun value in the registry
- main (2).exe (PID: 6516)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 6944)
TROX has been detected
- manyak3.exe (PID: 4776)
Create files in the Startup directory
- cstealer.exe (PID: 6476)
- manyak1.exe (PID: 7400)
- prysmax.exe (PID: 856)
- manyak4.exe (PID: 4424)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 6080)
Steals credentials from Web Browsers
- cstealer.exe (PID: 6476)
- manyak2.exe (PID: 7052)
- manyak1.exe (PID: 7400)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
Suspicious data exfiltration via CURL detected
- cstealer.exe (PID: 6476)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 2088)
- cmd.exe (PID: 7148)
Actions looks like stealing of personal data
- cstealer.exe (PID: 6476)
- manyak2.exe (PID: 7052)
- manyak1.exe (PID: 7400)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
Changes Windows Defender settings
- cmd.exe (PID: 7356)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 6156)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 208)
- cmd.exe (PID: 7388)
- cmd.exe (PID: 4932)
- cmd.exe (PID: 5376)
- cmd.exe (PID: 7192)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 7444)
- powershell.exe (PID: 2560)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 7444)
Changes Controlled Folder Access settings
- powershell.exe (PID: 7444)
- powershell.exe (PID: 7940)
VOBFUS mutex has been found
- manyak2.exe (PID: 7052)
Adds path to the Windows Defender exclusion list
- manyak2.exe (PID: 7052)
- cmd.exe (PID: 7356)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 8164)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 7444)
Changes settings for real-time protection
- powershell.exe (PID: 7444)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 7444)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 7444)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 672)
Adds extension to the Windows Defender exclusion list
- cmd.exe (PID: 6156)
- prysmax.exe (PID: 856)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 7192)
BLANKGRABBER has been detected (SURICATA)
- manyak2.exe (PID: 7052)
SUSPICIOUS
Process drops legitimate windows executable
- main (2).exe (PID: 2140)
- manyak2.exe (PID: 672)
- manyak3.exe (PID: 4776)
- manyak2.exe (PID: 728)
- main (2).exe (PID: 6516)
- manyak5.exe (PID: 8024)
- manyak4.exe (PID: 7424)
- manyak1.exe (PID: 7396)
The process drops C-runtime libraries
- main (2).exe (PID: 2140)
- manyak2.exe (PID: 672)
- manyak3.exe (PID: 4776)
- manyak2.exe (PID: 728)
- manyak1.exe (PID: 7396)
- manyak5.exe (PID: 8024)
- main (2).exe (PID: 6516)
- manyak4.exe (PID: 7424)
Application launched itself
- main (2).exe (PID: 2140)
- manyak2.exe (PID: 672)
- manyak2.exe (PID: 728)
- manyak1.exe (PID: 7396)
- manyak5.exe (PID: 8024)
- manyak4.exe (PID: 7424)
Process drops python dynamic module
- main (2).exe (PID: 2140)
- manyak2.exe (PID: 672)
- manyak3.exe (PID: 4776)
- manyak2.exe (PID: 728)
- manyak1.exe (PID: 7396)
- manyak5.exe (PID: 8024)
- main (2).exe (PID: 6516)
- manyak4.exe (PID: 7424)
Executable content was dropped or overwritten
- main (2).exe (PID: 2140)
- main (2).exe (PID: 6516)
- manyak2.exe (PID: 672)
- manyak3.exe (PID: 4776)
- manyak2.exe (PID: 728)
- cstealer.exe (PID: 6476)
- manyak1.exe (PID: 7396)
- manyak5.exe (PID: 8024)
- manyak4.exe (PID: 7424)
- manyak1.exe (PID: 7400)
- manyak4.exe (PID: 4424)
Loads Python modules
- main (2).exe (PID: 6516)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3176)
- prysmax.exe (PID: 856)
Starts CMD.EXE for commands execution
- main (2).exe (PID: 6516)
- manyak2.exe (PID: 6268)
- manyak2.exe (PID: 7052)
- cstealer.exe (PID: 6476)
- prysmax.exe (PID: 856)
- manyak1.exe (PID: 7400)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
There is functionality for taking screenshot (YARA)
- main (2).exe (PID: 2140)
- main (2).exe (PID: 6516)
Reads security settings of Internet Explorer
- main (2).exe (PID: 6516)
- manyak3.exe (PID: 4776)
- StartMenuExperienceHost.exe (PID: 5264)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4408)
- cmd.exe (PID: 5512)
- cmd.exe (PID: 7012)
Changes default file association
- reg.exe (PID: 6944)
Found strings related to reading or modifying Windows Defender settings
- manyak2.exe (PID: 6268)
- manyak2.exe (PID: 7052)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 2152)
- cmd.exe (PID: 4120)
Execution of CURL command
- cstealer.exe (PID: 6476)
Data upload via CURL
- curl.exe (PID: 7596)
- curl.exe (PID: 8100)
- curl.exe (PID: 7892)
- curl.exe (PID: 5332)
- curl.exe (PID: 7196)
- curl.exe (PID: 7688)
Checks for external IP
- cstealer.exe (PID: 6476)
- svchost.exe (PID: 2196)
- prysmax.exe (PID: 856)
- manyak1.exe (PID: 7400)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
- manyak2.exe (PID: 7052)
Script disables Windows Defender's IPS
- cmd.exe (PID: 8164)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 8164)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8164)
- cmd.exe (PID: 7356)
- cmd.exe (PID: 7912)
- cmd.exe (PID: 7284)
- cmd.exe (PID: 6416)
- cmd.exe (PID: 6156)
- cmd.exe (PID: 7576)
- cmd.exe (PID: 2772)
- manyak5.exe (PID: 2100)
- cmd.exe (PID: 6736)
- manyak1.exe (PID: 7400)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 7192)
- cmd.exe (PID: 208)
- cmd.exe (PID: 7388)
- cmd.exe (PID: 4932)
- cmd.exe (PID: 7772)
- cmd.exe (PID: 5376)
Base64-obfuscated command line is found
- cmd.exe (PID: 7356)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7356)
Get information on the list of running processes
- manyak2.exe (PID: 7052)
- cmd.exe (PID: 8104)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 7948)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 5556)
- cmd.exe (PID: 7792)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 2152)
- manyak1.exe (PID: 7400)
Starts application with an unusual extension
- cmd.exe (PID: 7584)
- cmd.exe (PID: 7844)
- cmd.exe (PID: 5228)
- cmd.exe (PID: 7204)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 8068)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7776)
- cmd.exe (PID: 7980)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7492)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 7820)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5404)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 5576)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7732)
Script adds exclusion extension to Windows Defender
- cmd.exe (PID: 6156)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 7192)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 680)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 4604)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 2604)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 5264)
- SearchApp.exe (PID: 7372)
INFO
Reads the computer name
- main (2).exe (PID: 2140)
- main (2).exe (PID: 6516)
- manyak2.exe (PID: 672)
- cstealer.exe (PID: 6476)
- manyak2.exe (PID: 6268)
- manyak2.exe (PID: 728)
- manyak2.exe (PID: 7052)
- curl.exe (PID: 7596)
- manyak1.exe (PID: 7396)
- manyak5.exe (PID: 8024)
- curl.exe (PID: 8100)
- curl.exe (PID: 7892)
- manyak4.exe (PID: 7424)
- manyak3.exe (PID: 4776)
- prysmax.exe (PID: 856)
- manyak1.exe (PID: 7400)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
- MpCmdRun.exe (PID: 672)
- StartMenuExperienceHost.exe (PID: 5264)
- TextInputHost.exe (PID: 8044)
Checks supported languages
- main (2).exe (PID: 2140)
- main (2).exe (PID: 6516)
- manyak2.exe (PID: 672)
- manyak3.exe (PID: 4776)
- manyak2.exe (PID: 6268)
- cstealer.exe (PID: 6476)
- manyak2.exe (PID: 728)
- manyak2.exe (PID: 7052)
- curl.exe (PID: 7596)
- manyak1.exe (PID: 7396)
- tree.com (PID: 7552)
- tree.com (PID: 7600)
- tree.com (PID: 3192)
- tree.com (PID: 8168)
- tree.com (PID: 7472)
- tree.com (PID: 5964)
- curl.exe (PID: 8100)
- manyak5.exe (PID: 8024)
- curl.exe (PID: 7892)
- manyak4.exe (PID: 7424)
- curl.exe (PID: 7196)
- curl.exe (PID: 5332)
- curl.exe (PID: 7688)
- prysmax.exe (PID: 856)
- manyak1.exe (PID: 7400)
- manyak4.exe (PID: 4424)
- manyak5.exe (PID: 2100)
- MpCmdRun.exe (PID: 672)
- StartMenuExperienceHost.exe (PID: 5264)
- TextInputHost.exe (PID: 8044)
- SearchApp.exe (PID: 7372)
Create files in a temporary directory
- main (2).exe (PID: 2140)
- manyak2.exe (PID: 672)
- manyak3.exe (PID: 4776)
- manyak2.exe (PID: 728)
- cstealer.exe (PID: 6476)
- manyak1.exe (PID: 7396)
- manyak2.exe (PID: 7052)
- manyak5.exe (PID: 8024)
- manyak4.exe (PID: 7424)
- prysmax.exe (PID: 856)
- manyak1.exe (PID: 7400)
- MpCmdRun.exe (PID: 672)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
The sample compiled with english language support
- main (2).exe (PID: 2140)
- manyak2.exe (PID: 672)
- manyak3.exe (PID: 4776)
- manyak2.exe (PID: 728)
- main (2).exe (PID: 6516)
- manyak1.exe (PID: 7396)
- manyak5.exe (PID: 8024)
- manyak4.exe (PID: 7424)
Reads the machine GUID from the registry
- main (2).exe (PID: 6516)
- manyak2.exe (PID: 6268)
- manyak2.exe (PID: 7052)
- prysmax.exe (PID: 856)
- manyak5.exe (PID: 2100)
- SearchApp.exe (PID: 7372)
Checks proxy server information
- main (2).exe (PID: 6516)
- cstealer.exe (PID: 6476)
- prysmax.exe (PID: 856)
- manyak1.exe (PID: 7400)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
- SearchApp.exe (PID: 7372)
Creates files or folders in the user directory
- main (2).exe (PID: 6516)
- cstealer.exe (PID: 6476)
- prysmax.exe (PID: 856)
- manyak1.exe (PID: 7400)
- manyak4.exe (PID: 4424)
PyInstaller has been detected (YARA)
- main (2).exe (PID: 2140)
- main (2).exe (PID: 6516)
Process checks computer location settings
- main (2).exe (PID: 6516)
- StartMenuExperienceHost.exe (PID: 5264)
- SearchApp.exe (PID: 7372)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 6080)
- WMIC.exe (PID: 7492)
- WMIC.exe (PID: 5576)
- WMIC.exe (PID: 7388)
- WMIC.exe (PID: 680)
- WMIC.exe (PID: 2604)
Execution of CURL command
- cmd.exe (PID: 7712)
- cmd.exe (PID: 7148)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 2088)
Attempting to use instant messaging service
- cstealer.exe (PID: 6476)
- svchost.exe (PID: 2196)
- prysmax.exe (PID: 856)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
The Powershell gets current clipboard
- powershell.exe (PID: 5728)
Checks the directory tree
- tree.com (PID: 7552)
- tree.com (PID: 7600)
- tree.com (PID: 8168)
- tree.com (PID: 3192)
- tree.com (PID: 5964)
- tree.com (PID: 7472)
Checks operating system version
- prysmax.exe (PID: 856)
- manyak5.exe (PID: 2100)
- manyak4.exe (PID: 4424)
- manyak1.exe (PID: 7400)
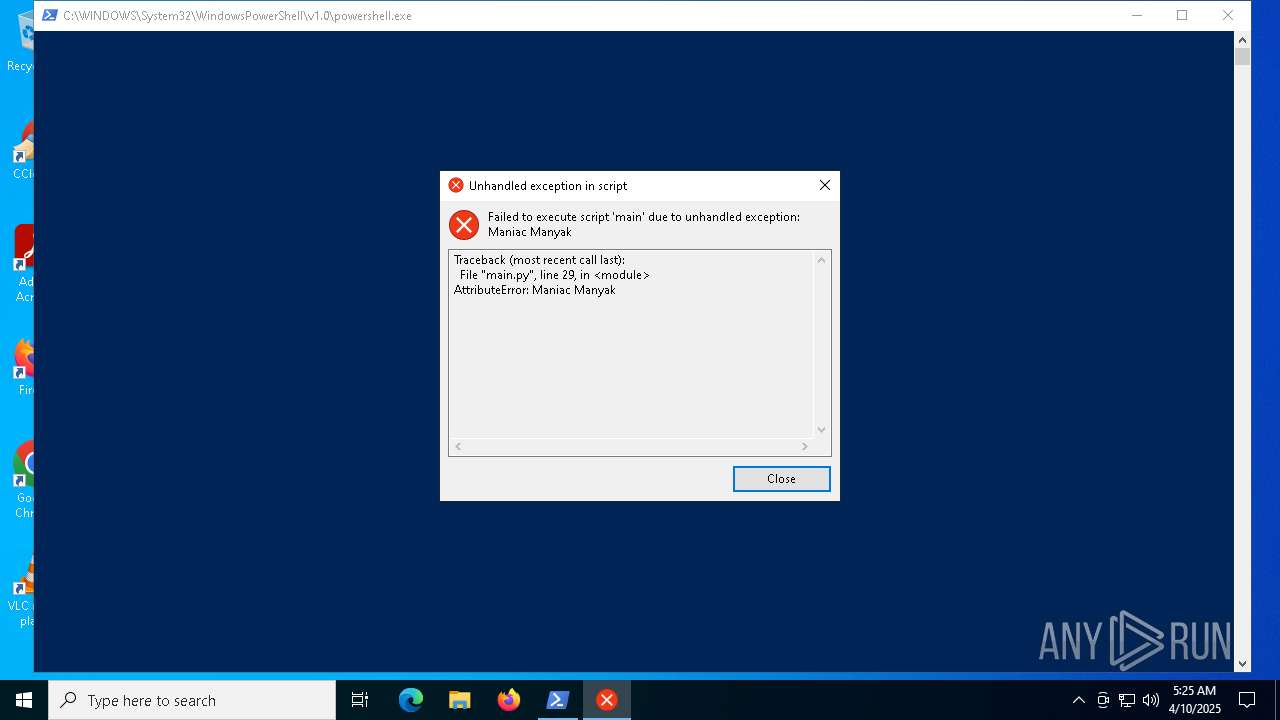
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 672)
- powershell.exe (PID: 7576)
- powershell.exe (PID: 7804)
- powershell.exe (PID: 7444)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7940)
- powershell.exe (PID: 7656)
- powershell.exe (PID: 2924)
- powershell.exe (PID: 5404)
- powershell.exe (PID: 2560)
- powershell.exe (PID: 3024)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7444)
- powershell.exe (PID: 7804)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7940)
- powershell.exe (PID: 7656)
- powershell.exe (PID: 2560)
- powershell.exe (PID: 5404)
- powershell.exe (PID: 2924)
- powershell.exe (PID: 3024)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 7476)
Reads the software policy settings
- SearchApp.exe (PID: 7372)
Reads Environment values
- SearchApp.exe (PID: 7372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:16 14:48:33+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.41 |
| CodeSize: | 156160 |
| InitializedDataSize: | 68608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbdb0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
332
Monitored processes
190
Malicious processes
30
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | powershell "(Get-CimInstance -Class Win32_ComputerSystemProduct).UUID" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | manyak5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | C:\WINDOWS\system32\cmd.exe /c "powershell.exe -command Set-MpPreference -DisableBlockAtFirstSeen $true" | C:\Windows\System32\cmd.exe | — | prysmax.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | systeminfo | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | tasklist /FO LIST | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | "C:\Users\admin\AppData\Local\GagoKa\manyak2.exe" | C:\Users\admin\AppData\Local\GagoKa\manyak2.exe | main (2).exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 672 | powershell Get-ItemPropertyValue -Path HKCU:SOFTWARE\Roblox\RobloxStudioBrowser\roblox.com -Name .ROBLOSECURITY | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -RemoveDefinitions -All | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Malware Protection Command Line Utility Exit code: 0 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Users\admin\AppData\Local\GagoKa\manyak2.exe" | C:\Users\admin\AppData\Local\GagoKa\manyak2.exe | ComputerDefaults.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\GagoKa\afafafaf\prysmax.exe" | C:\Users\admin\AppData\Local\GagoKa\afafafaf\prysmax.exe | main (2).exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
293 879
Read events
293 797
Write events
76
Delete events
6
Modification events
| (PID) Process: | (6516) main (2).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ManiacManyak |
Value: C:\Users\admin\AppData\Roaming\discord\discord.bat | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (6080) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6080) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6080) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6080) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6964) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6964) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6964) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6964) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
564
Suspicious files
108
Text files
123
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\_socket.pyd | executable | |
MD5:CE935058895B0C21B84DE722353CFE70 | SHA256:12AB86D31B22D763B48F5D73FBFE897C70C9095F5C8A488E79DCCF4944150BAE | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\VCRUNTIME140.dll | executable | |
MD5:1A84957B6E681FCA057160CD04E26B27 | SHA256:9FAEAA45E8CC986AF56F28350B38238B03C01C355E9564B849604B8D690919C5 | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\_lzma.pyd | executable | |
MD5:AD2A12AFC53B1EC6556EFFF903AE4613 | SHA256:10DD3ED8F47D77DA0B6FD9A46165620C0234598BAB16A1ED64752FBE551C5747 | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\certifi\cacert.pem | text | |
MD5:234D271ECB91165AAEC148AD6326DD39 | SHA256:C55B21F907F7F86D48ADD093552FB5651749FF5F860508CCBB423D6C1FBD80C7 | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\_hashlib.pyd | executable | |
MD5:23DBE8A452F43C2ACDF0B3E218CDBD9A | SHA256:205D849071DC8039755E8E37679B09D736D6F1F65B0367762B1E50BBA5AE7D07 | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\_queue.pyd | executable | |
MD5:F34E86AAB57D7287825A4D279FAB9A3B | SHA256:9075F1CF7662AE232F627E6E1FEEF01AA261BDB0784D559E9BEAAB0EB35DAC16 | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\_bz2.pyd | executable | |
MD5:936C16D3A7772F6E3AABDE834F910E10 | SHA256:72D24D755142EB06AA3E6A03A63217ED66B141C16D898405DD01DAFFF69AA8DE | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\_decimal.pyd | executable | |
MD5:327BB8AD9E4E30C079C184B960E747F8 | SHA256:382AD65BE697BCCCE12B0826C2601BA05E45D936651BA834B545B3D7261D2A87 | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\base_library.zip | compressed | |
MD5:B694BDA60770A7ED7EF2715DD1894CA9 | SHA256:392760A1DA9C380316E25A4671563CA98A8F10B074B56948C54F6C003E16A5BB | |||
| 2140 | main (2).exe | C:\Users\admin\AppData\Local\Temp\_MEI21402\python39.dll | executable | |
MD5:A4C2EA38237477F75782625753B27939 | SHA256:54CBC44EC6762F35D3B6179ED01379341BF3106BCDF995FD0EF4321508AC67C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
120
DNS requests
34
Threats
159
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 95.101.54.131:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgQj0fhZhehuCFXD1A8dze3Ydg%3D%3D | unknown | — | — | whitelisted |
7520 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7520 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7052 | manyak2.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | whitelisted |
7372 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6516 | main (2).exe | 104.22.69.199:443 | pastebin.com | CLOUDFLARENET | — | whitelisted |
6516 | main (2).exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6268 | manyak2.exe | 104.22.69.199:443 | pastebin.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
pastebin.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.ipify.org |
| shared |
api.gofile.io |
| whitelisted |
geolocation-db.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6476 | cstealer.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
6476 | cstealer.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain in DNS Lookup (geolocation-db .com) |
6476 | cstealer.exe | Misc activity | ET INFO External IP Lookup Domain (geolocation-db .com) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |