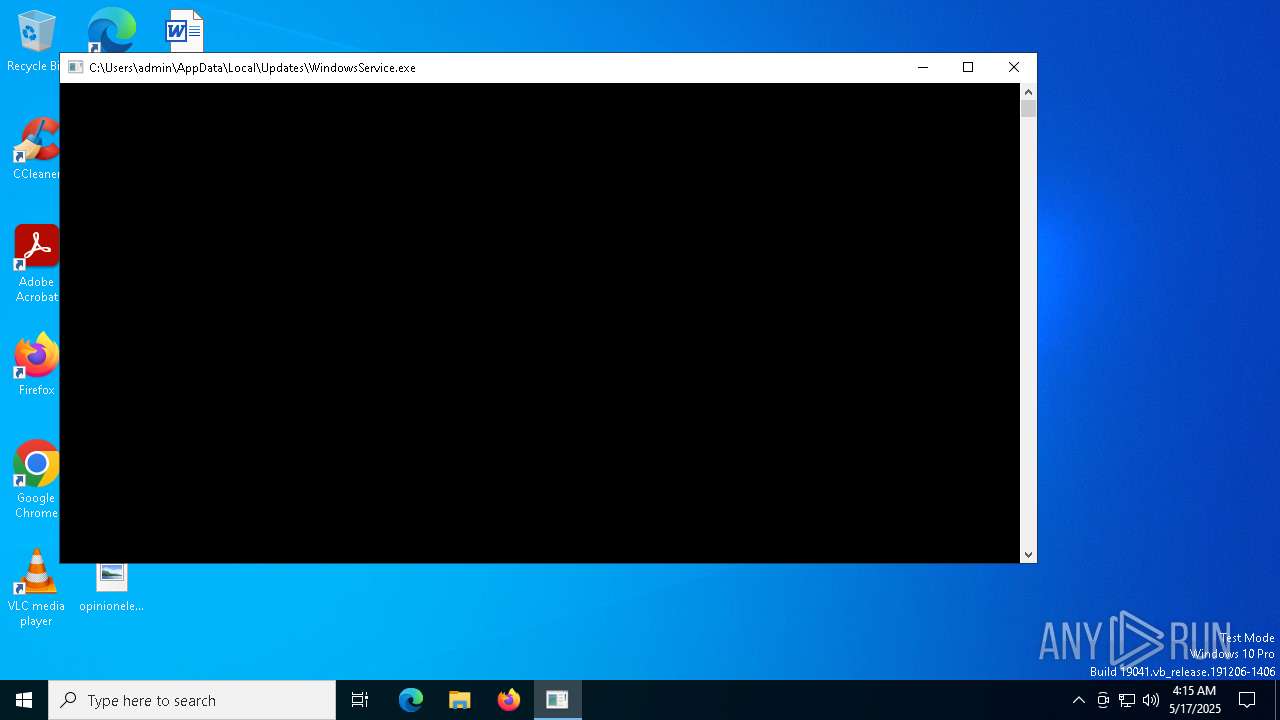
| File name: | Step 3 - Setup_Install_Game.exe |
| Full analysis: | https://app.any.run/tasks/ab424b48-1ba7-4986-b6aa-85c932903366 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 17, 2025, 04:14:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 90E72C56D17C44B3CA300E4D1744A887 |
| SHA1: | 3F0FB4D6D920591B194C8887D9854FA7EA8DB01D |
| SHA256: | 7CC9E17085066CD2299E7C37C743ACBAD0370554EC704C803443D112C27BF486 |
| SSDEEP: | 98304:V0xNLNQWgAERBO59FQr58uXfkdZ5Cf+IfdbWkypTRSJAKSge8U2NSyHFgD1Ulqua:exNufAVu8kf/ZFyqzRx7tyri1Gtl |
MALICIOUS
Creates a new scheduled task via Registry
- msiexec.exe (PID: 3240)
Vulnerable driver has been detected
- WindowsService.exe (PID: 920)
MINER has been detected (SURICATA)
- cmd.exe (PID: 7348)
Connects to the CnC server
- cmd.exe (PID: 7348)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- Step 3 - Setup_Install_Game.exe (PID: 2152)
Reads the Windows owner or organization settings
- Step 3 - Setup_Install_Game.exe (PID: 2152)
- msiexec.exe (PID: 1764)
Process drops legitimate windows executable
- Step 3 - Setup_Install_Game.exe (PID: 2152)
Executable content was dropped or overwritten
- Step 3 - Setup_Install_Game.exe (PID: 2152)
- WindowsService.exe (PID: 920)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 5244)
Checks whether a specific file exists (SCRIPT)
- msiexec.exe (PID: 5244)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 5244)
Drops a system driver (possible attempt to evade defenses)
- WindowsService.exe (PID: 920)
Starts CMD.EXE for commands execution
- WindowsService.exe (PID: 920)
Potential Corporate Privacy Violation
- cmd.exe (PID: 7348)
Connects to unusual port
- cmd.exe (PID: 7348)
- WindowsService.exe (PID: 920)
Reads security settings of Internet Explorer
- WindowsService.exe (PID: 920)
INFO
Checks supported languages
- Step 3 - Setup_Install_Game.exe (PID: 2152)
- msiexec.exe (PID: 1164)
- msiexec.exe (PID: 1764)
- msiexec.exe (PID: 5244)
- MSIC23E.tmp (PID: 5392)
- WindowsService.exe (PID: 920)
- msiexec.exe (PID: 3240)
The sample compiled with english language support
- Step 3 - Setup_Install_Game.exe (PID: 2152)
- msiexec.exe (PID: 1764)
Reads the computer name
- msiexec.exe (PID: 1764)
- Step 3 - Setup_Install_Game.exe (PID: 2152)
- msiexec.exe (PID: 1164)
- msiexec.exe (PID: 5244)
- WindowsService.exe (PID: 920)
- msiexec.exe (PID: 3240)
Creates files or folders in the user directory
- Step 3 - Setup_Install_Game.exe (PID: 2152)
- msiexec.exe (PID: 1764)
- WindowsService.exe (PID: 920)
Reads Environment values
- Step 3 - Setup_Install_Game.exe (PID: 2152)
- msiexec.exe (PID: 5244)
Create files in a temporary directory
- Step 3 - Setup_Install_Game.exe (PID: 2152)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1764)
Starts application with an unusual extension
- msiexec.exe (PID: 1764)
The sample compiled with japanese language support
- WindowsService.exe (PID: 920)
Checks proxy server information
- WindowsService.exe (PID: 920)
Creates files in the program directory
- cmd.exe (PID: 7348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:12:17 11:28:24+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 2149376 |
| InitializedDataSize: | 1314816 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x192554 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | OceanofGames.ccom |
| FileDescription: | EXE - Step 3 - Setup_Install_Game Installer |
| FileVersion: | 1.0.0 |
| InternalName: | Step 3 - Setup_Install_Game |
| LegalCopyright: | Copyright (C) 2022 OceanofGames.ccom |
| OriginalFileName: | Step 3 - Setup_Install_Game.exe |
| ProductName: | EXE - Step 3 - Setup_Install_Game |
| ProductVersion: | 1.0.0 |
Total processes
140
Monitored processes
12
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\AppData\Local\Updates\WindowsService.exe" | C:\Users\admin\AppData\Local\Updates\WindowsService.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1164 | C:\Windows\syswow64\MsiExec.exe -Embedding 33F82C6936B2500D5E36BDB647061EFB C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\AppData\Local\Temp\Step 3 - Setup_Install_Game.exe" | C:\Users\admin\AppData\Local\Temp\Step 3 - Setup_Install_Game.exe | — | explorer.exe | |||||||||||
User: admin Company: OceanofGames.ccom Integrity Level: MEDIUM Description: EXE - Step 3 - Setup_Install_Game Installer Exit code: 3221226540 Version: 1.0.0 Modules
| |||||||||||||||
| 1764 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\WINDOWS\system32\msiexec.exe" /i "C:\Users\admin\AppData\Roaming\OceanofGames.ccom\EXE - Step 3 - Setup_Install_Game 1.0.0\install\326FA02\OceanofGames-Top-Games-EXE.msi" /quiet /qn AI_SETUPEXEPATH="C:\Users\admin\AppData\Local\Temp\Step 3 - Setup_Install_Game.exe" SETUPEXEDIR=C:\Users\admin\AppData\Local\Temp\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1747454204 " AI_EUIMSI="" | C:\Windows\SysWOW64\msiexec.exe | — | Step 3 - Setup_Install_Game.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | "C:\Users\admin\AppData\Local\Temp\Step 3 - Setup_Install_Game.exe" | C:\Users\admin\AppData\Local\Temp\Step 3 - Setup_Install_Game.exe | explorer.exe | ||||||||||||
User: admin Company: OceanofGames.ccom Integrity Level: HIGH Description: EXE - Step 3 - Setup_Install_Game Installer Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | C:\Windows\syswow64\MsiExec.exe -Embedding ED3F42E45DDD01BF607B4AB02EE15C97 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | C:\Windows\syswow64\MsiExec.exe -Embedding C1D6024AEA244E9296555E92D7401289 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5392 | "C:\WINDOWS\Installer\MSIC23E.tmp" /EnforcedRunAsAdmin /DontWait /RunAsAdmin /HideWindow "C:\WINDOWS\Windows.exe" | C:\Windows\Installer\MSIC23E.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: HIGH Description: File that launches another file Exit code: 0 Version: 19.0.0.0 Modules
| |||||||||||||||
Total events
2 515
Read events
2 467
Write events
37
Delete events
11
Modification events
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: E4060000E6C73C41E2C6DB01 | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 21D7AE577F9F0132DD88B4FBF96E39FC03FE23BB0EAA44B6A86AADB9FB7663E1 | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\C8629DFA347D0E349A33F59F05DC260E |
| Operation: | write | Name: | 9C3C72409647DEB49B07B5FE3362AF20 |
Value: 02:\Software\Caphyon\Advanced Installer\LZMA\{0427C3C9-7469-4BED-B970-5BEF3326FA02}\1.0.0\AI_ExePath | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\DF2BE1E07B4C51B44A7650C4AC5C9497 |
| Operation: | write | Name: | 9C3C72409647DEB49B07B5FE3362AF20 |
Value: C:\WINDOWS\fidelity.exe | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\BB021A3CFBD2EA544BA583B2B0250F36 |
| Operation: | write | Name: | 9C3C72409647DEB49B07B5FE3362AF20 |
Value: C:\WINDOWS\NSudo.exe | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\2D70CD27B29F76045BD41841C557D4DF |
| Operation: | write | Name: | 9C3C72409647DEB49B07B5FE3362AF20 |
Value: C:\WINDOWS\Windows.exe | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\WINDOWS\system32\fidelity.exe |
Value: 1 | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\331F5B27BB59723429B30BC67AD117E8 |
| Operation: | write | Name: | 9C3C72409647DEB49B07B5FE3362AF20 |
Value: C:\?WINDOWS\SysWOW64\fidelity.exe | |||
| (PID) Process: | (1764) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\WINDOWS\SysWOW64\NSudo.exe |
Value: 1 | |||
Executable files
28
Suspicious files
17
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2152 | Step 3 - Setup_Install_Game.exe | C:\Users\admin\AppData\Roaming\OceanofGames.ccom\EXE - Step 3 - Setup_Install_Game 1.0.0\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 2152 | Step 3 - Setup_Install_Game.exe | C:\Users\admin\AppData\Local\Temp\shiBCCA.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 1764 | msiexec.exe | C:\Windows\Installer\MSIBFB9.tmp | executable | |
MD5:5788EFA607D26332D6D7F5E6A1F6BD6F | SHA256:9FC2608C9E5EF5A88DD91C82660FA297144BA6BBF4602140D638DE7233A4625D | |||
| 2152 | Step 3 - Setup_Install_Game.exe | C:\Users\admin\AppData\Local\Temp\MSIBD29.tmp | executable | |
MD5:5788EFA607D26332D6D7F5E6A1F6BD6F | SHA256:9FC2608C9E5EF5A88DD91C82660FA297144BA6BBF4602140D638DE7233A4625D | |||
| 1764 | msiexec.exe | C:\Windows\Installer\MSIBFF8.tmp | executable | |
MD5:5788EFA607D26332D6D7F5E6A1F6BD6F | SHA256:9FC2608C9E5EF5A88DD91C82660FA297144BA6BBF4602140D638DE7233A4625D | |||
| 1764 | msiexec.exe | C:\Windows\Installer\10be41.msi | executable | |
MD5:9C19919E95F8FA54EDF0EC14571DBCE0 | SHA256:3577A4FE25AD453C67AFB9F9D8AF0B9525C84E37AA7F7DD7F58831FB150E8DAD | |||
| 2152 | Step 3 - Setup_Install_Game.exe | C:\Users\admin\AppData\Roaming\OceanofGames.ccom\EXE - Step 3 - Setup_Install_Game 1.0.0\install\decoder.dll | executable | |
MD5:31DAF181536165EF11461C18D98D04DA | SHA256:0E38B521210B476057892FA2085EE60D1FB79B8C77CCEFFDAA0E2EF5D63B0F09 | |||
| 2152 | Step 3 - Setup_Install_Game.exe | C:\Users\admin\AppData\Roaming\OceanofGames.ccom\EXE - Step 3 - Setup_Install_Game 1.0.0\install\326FA02\OceanofGames-Top-Games-EXE.msi | executable | |
MD5:9C19919E95F8FA54EDF0EC14571DBCE0 | SHA256:3577A4FE25AD453C67AFB9F9D8AF0B9525C84E37AA7F7DD7F58831FB150E8DAD | |||
| 2152 | Step 3 - Setup_Install_Game.exe | C:\Users\admin\AppData\Roaming\OceanofGames.ccom\EXE - Step 3 - Setup_Install_Game 1.0.0\install\326FA02\WindowsFolder\fidelity.exe | executable | |
MD5:BA352663C76C86C10A8D5C7B7A47F3C5 | SHA256:AFBF22880D0129F8B11B1A5876F175C874F52C8572CB5C4BEDA3C528241A8E6C | |||
| 2152 | Step 3 - Setup_Install_Game.exe | C:\Users\admin\AppData\Roaming\OceanofGames.ccom\EXE - Step 3 - Setup_Install_Game 1.0.0\install\326FA02\SystemFolder\NSudo.exe | executable | |
MD5:5CAE01AEA8ED390CE9BEC17B6C1237E4 | SHA256:19896A23D7B054625C2F6B1EE1551A0DA68AD25CDDBB24510A3B74578418E618 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
17
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
920 | WindowsService.exe | GET | 200 | 188.138.125.61:83 | http://www.google.com.kaz8dwnvmbsopt62.service-windows.com:83/md5.txt | unknown | — | — | unknown |
920 | WindowsService.exe | GET | — | 188.138.25.13:83 | http://www.google.com.roysg3hnqilzkcpm.service-windows.com:83/Resource.bin | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7652 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
920 | WindowsService.exe | GET | 200 | 188.138.125.61:83 | http://www.google.com.kaz8dwnvmbsopt62.service-windows.com:83/md5.txt | unknown | — | — | unknown |
7652 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
920 | WindowsService.exe | 188.138.125.61:83 | www.google.com.3epysib28k7lqtzr.service-windows.com | Host Europe GmbH | FR | unknown |
920 | WindowsService.exe | 188.138.25.13:83 | www.google.com.3epysib28k7lqtzr.service-windows.com | Host Europe GmbH | FR | unknown |
6544 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.google.com.3epysib28k7lqtzr.service-windows.com |
| unknown |
www.google.com.kaz8dwnvmbsopt62.service-windows.com |
| unknown |
www.google.com.roysg3hnqilzkcpm.service-windows.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .service-windows .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .service-windows .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .service-windows .com) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
7348 | cmd.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
7348 | cmd.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |