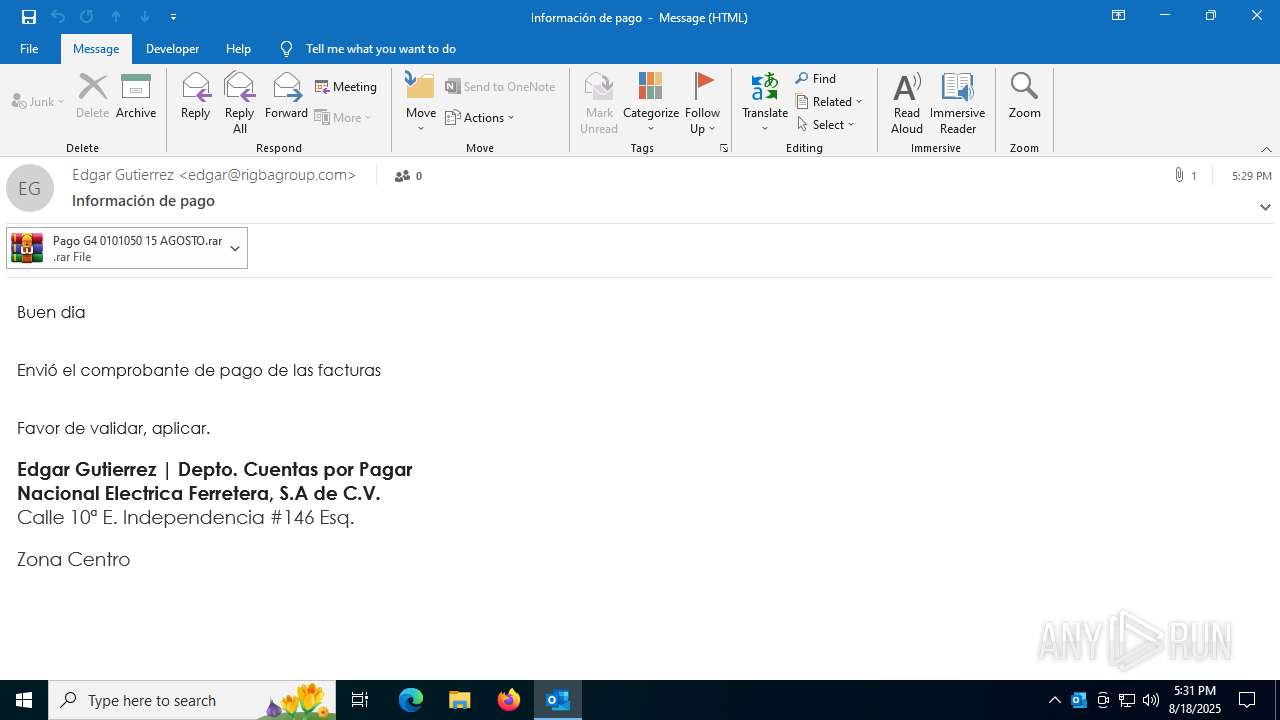
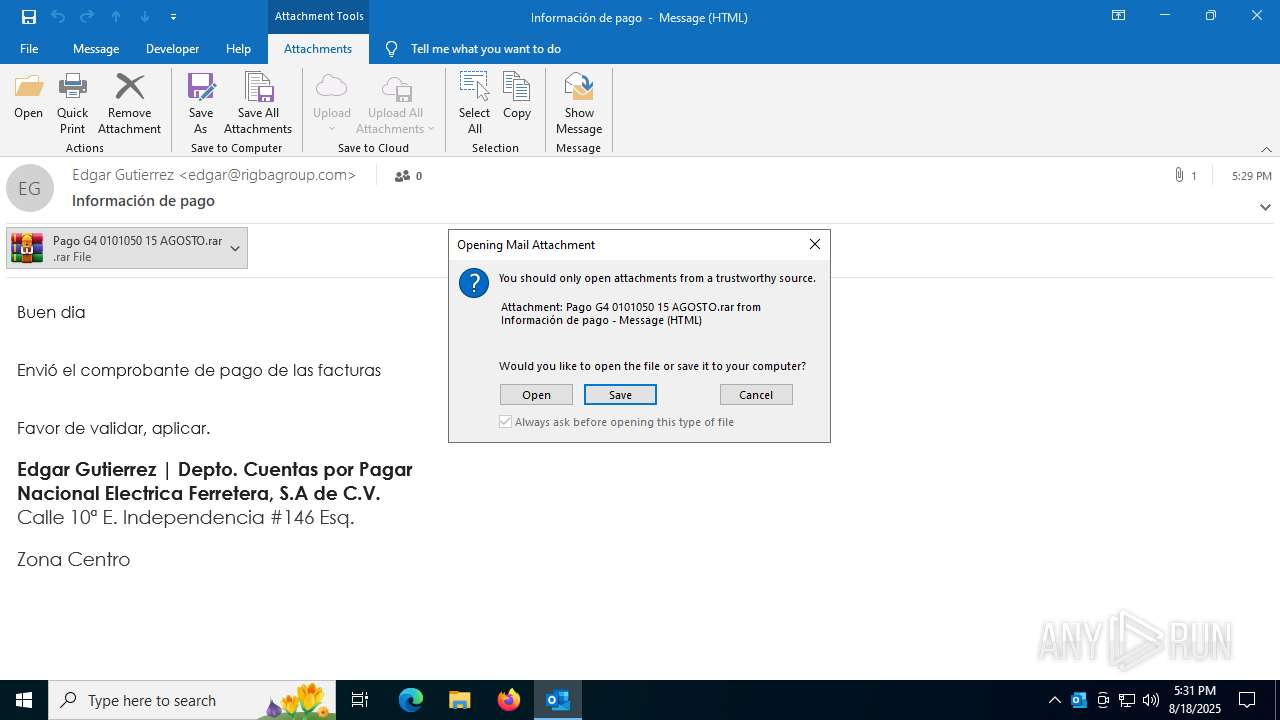
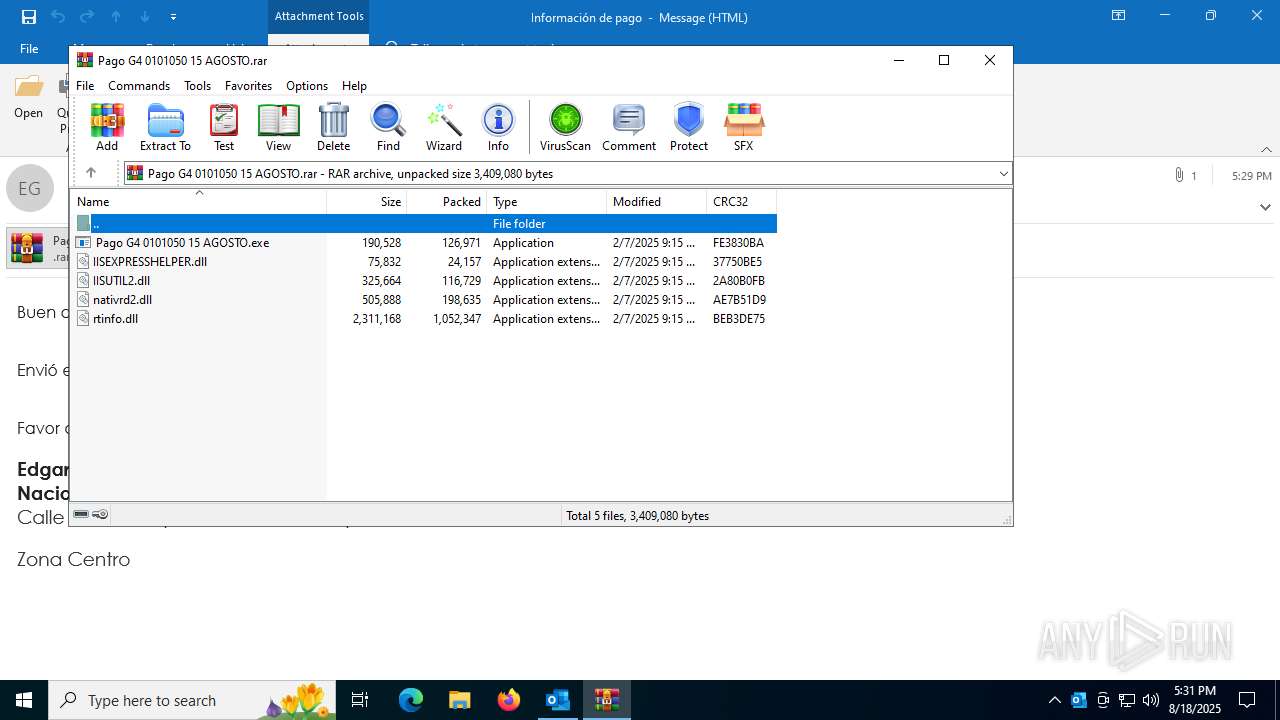
| File name: | Información de pago.msg |
| Full analysis: | https://app.any.run/tasks/7fe171e9-d1b0-434c-b9ee-4c038cb0ca5e |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | August 18, 2025, 17:30:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | E1D356AB74BB8D29CCCFFF69C9E9A5FC |
| SHA1: | B5F782FD35DCA9045B0102EC31DD9A93DE10E410 |
| SHA256: | 7B697B75E979B44674F52507D190C3E048E0C60D06D9981A0C91D2851C88CCFB |
| SSDEEP: | 49152:R8Q2bXvqGaid1l+Vv75jkLhpkHF7v5jT47Lc08MNneFj8onLqPoB4oO+4H36iMGl:Rh4XvYidu7xAhp6N6o0fCj8IOoBP8X6M |
MALICIOUS
Actions looks like stealing of personal data
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
Connects to the CnC server
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
Steals credentials from Web Browsers
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
AGENTTESLA has been detected (SURICATA)
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
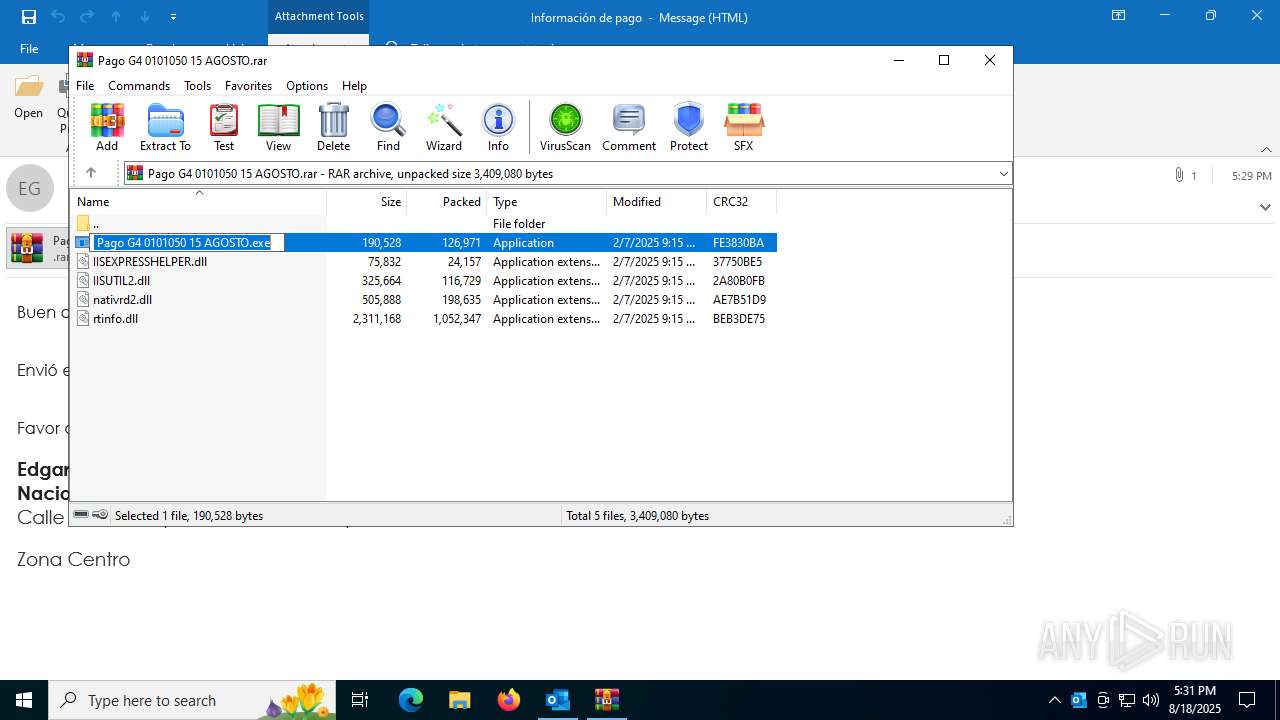
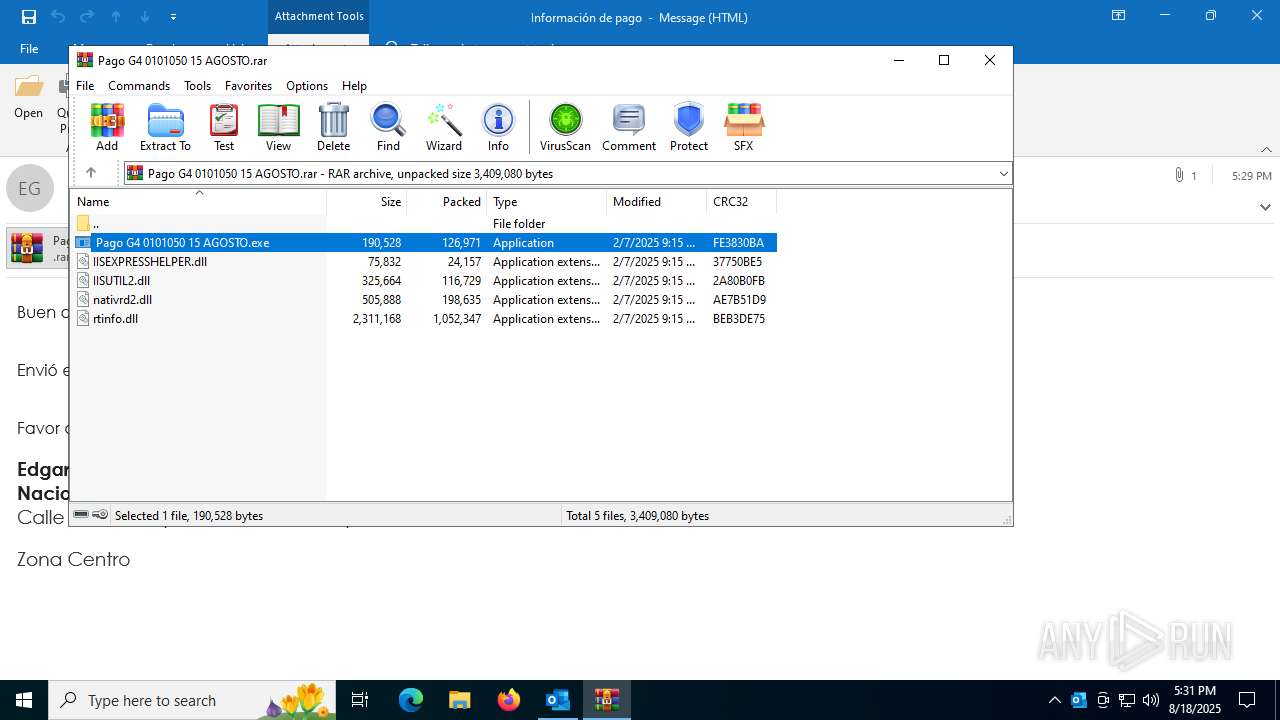
Generic archive extractor
- OUTLOOK.EXE (PID: 2964)
AGENTTESLA has been detected (YARA)
- AddInProcess32.exe (PID: 2596)
SUSPICIOUS
Process drops legitimate windows executable
- OUTLOOK.EXE (PID: 2964)
- WinRAR.exe (PID: 7096)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7096)
Checks for external IP
- svchost.exe (PID: 2200)
- AddInProcess32.exe (PID: 2596)
- AddInProcess32.exe (PID: 3488)
Connects to SMTP port
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
Starts a Microsoft application from unusual location
- Pago G4 0101050 15 AGOSTO.exe (PID: 7084)
- Pago G4 0101050 15 AGOSTO.exe (PID: 3620)
INFO
Checks supported languages
- Pago G4 0101050 15 AGOSTO.exe (PID: 3620)
- AddInProcess32.exe (PID: 3488)
- Pago G4 0101050 15 AGOSTO.exe (PID: 7084)
- AddInProcess32.exe (PID: 2596)
Reads the computer name
- AddInProcess32.exe (PID: 3488)
- Pago G4 0101050 15 AGOSTO.exe (PID: 3620)
- Pago G4 0101050 15 AGOSTO.exe (PID: 7084)
- AddInProcess32.exe (PID: 2596)
Reads the machine GUID from the registry
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
Checks proxy server information
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
Reads the software policy settings
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
Disables trace logs
- AddInProcess32.exe (PID: 3488)
- AddInProcess32.exe (PID: 2596)
ULTRAVNC has been detected
- AddInProcess32.exe (PID: 2596)
- AddInProcess32.exe (PID: 3488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(2596) AddInProcess32.exe
Protocolsmtp
Hostsmtp.santonswitchgears.com
Port587
Usernametech1@santonswitchgears.com
PasswordcJPF@$I3
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
147
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Pago G4 0101050 15 AGOSTO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | Pago G4 0101050 15 AGOSTO.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
AgentTesla(PID) Process(2596) AddInProcess32.exe Protocolsmtp Hostsmtp.santonswitchgears.com Port587 Usernametech1@santonswitchgears.com PasswordcJPF@$I3 | |||||||||||||||
| 2964 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Información de pago.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3488 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | Pago G4 0101050 15 AGOSTO.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.8259\ Pago G4 0101050 15 AGOSTO.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.8259\ Pago G4 0101050 15 AGOSTO.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IIS Express Worker Process Exit code: 4294967295 Version: 10.0.26013.1000 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "0DA56CFB-7095-4906-B721-441D0AB26710" "3C6203C9-1BE1-4A74-ACD1-63CC7BC4D0D2" "2964" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Pago G4 0101050 15 AGOSTO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.9020\ Pago G4 0101050 15 AGOSTO.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.9020\ Pago G4 0101050 15 AGOSTO.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IIS Express Worker Process Exit code: 4294967295 Version: 10.0.26013.1000 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 287
Read events
15 133
Write events
1 033
Delete events
121
Modification events
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | SessionId |
Value: E1D3B523-96AE-464C-8F17-9C200B2EC8EE | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Preferences |
| Operation: | delete value | Name: | ChangeProfileOnRestart |
Value: | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1D00000000000000 | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\outlook |
| Operation: | write | Name: | BuildNumber |
Value: 16.0.16026 | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs\outlook |
| Operation: | write | Name: | Expires |
Value: int64_t|0 | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs\outlook |
| Operation: | delete value | Name: | ConfigIds |
Value: | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs\outlook |
| Operation: | delete value | Name: | ETag |
Value: | |||
| (PID) Process: | (2964) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
Executable files
10
Suspicious files
8
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2964 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:401FA4965DCA8409D8C4960A1086D220 | SHA256:D9F0F0D285930074AFC4E4C21EB13D8A96A1F1ACBBC85FC1917A8C394BD5283F | |||
| 2964 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:3DAAD9A2A63B5E7C5231E17235AE1F3C | SHA256:D25F3C30DF6AF4C0A10CE7547979B3353E15CB6FA60953A8F67345D6480E3ED4 | |||
| 2964 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\33RGTWZ9\Pago G4 0101050 15 AGOSTO (002).rar:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.8259\ Pago G4 0101050 15 AGOSTO.exe | executable | |
MD5:B0D39CE242699383FBE4CF1F16B53719 | SHA256:01FCAFF363713CECD482D9ECF99814FC83870871B82A62BF11AB43D8844A8281 | |||
| 2964 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\33RGTWZ9\Pago G4 0101050 15 AGOSTO.rar:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.9020\nativrd2.dll | executable | |
MD5:8AE813C940BB9EA0E1031E229822DDA6 | SHA256:794686BA1B4F568E281B95814BEB31B12E205C8CB49853D831D650B528A6DB56 | |||
| 2964 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:BAC706DBDD4149ECC8A20D75E3839EC6 | SHA256:C9CAD75E690503076662053F227161D2B7CF7E784458C817D41BBAF94347C99C | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.8259\rtinfo.dll | executable | |
MD5:713F9EF73AF78DFF043A1E3790BC4774 | SHA256:DF8401044F13F9056ADAA1B0462F4741B6BC507A07FB9F79C20EC9B1F40F038F | |||
| 2964 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\33RGTWZ9\Pago G4 0101050 15 AGOSTO (002).rar | compressed | |
MD5:37201D758AA2C7A1833C9BBC05455028 | SHA256:5A8FFB6C02450F599C07DA06941DFB66C2C15AE77633041C5C2BD6A8219480C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
34
DNS requests
24
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3540 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2596 | AddInProcess32.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
5884 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5884 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2964 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3488 | AddInProcess32.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5968 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2964 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2964 | OUTLOOK.EXE | 23.50.131.94:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
2964 | OUTLOOK.EXE | 52.111.231.8:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2964 | OUTLOOK.EXE | 48.209.192.93:443 | nleditor.osi.office.net | — | US | whitelisted |
2964 | OUTLOOK.EXE | 52.109.28.48:443 | odc.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
3488 | AddInProcess32.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
3488 | AddInProcess32.exe | A Network Trojan was detected | ET MALWARE Common Stealer Behavior - Source IP Associated with Hosting Provider Check via ip.api .com |
3488 | AddInProcess32.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
3488 | AddInProcess32.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |