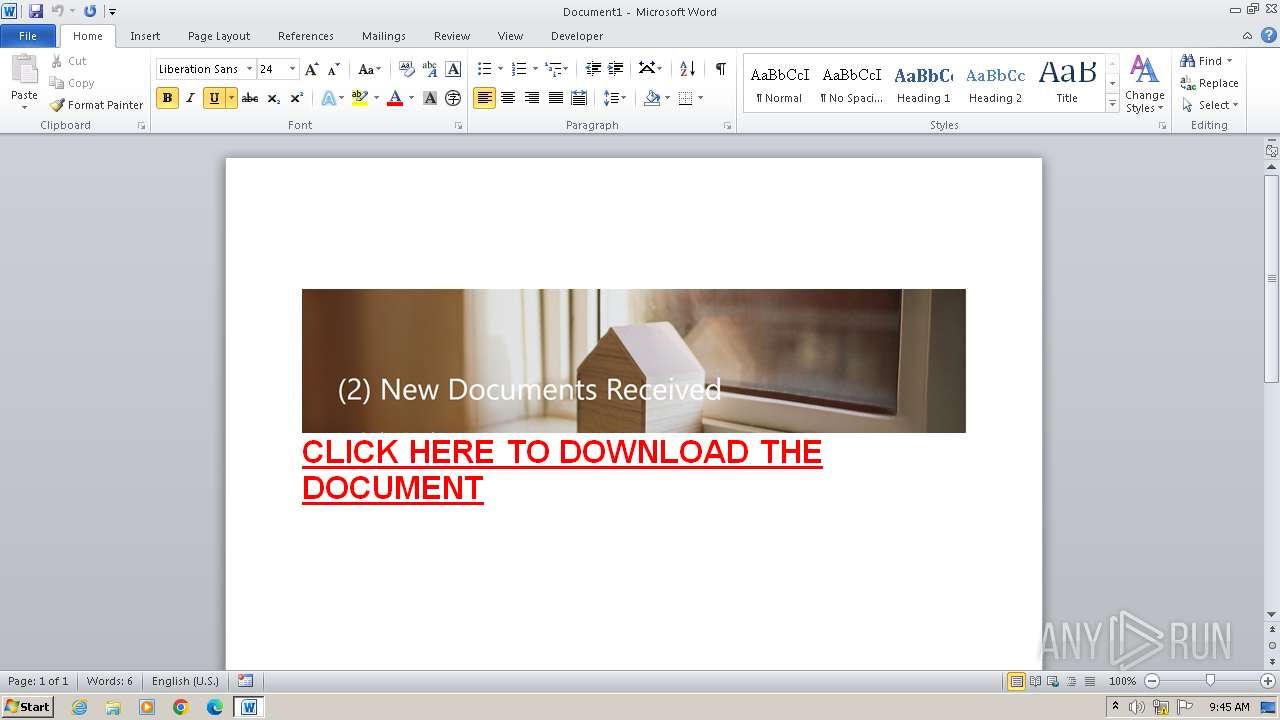
| File name: | Temmel_virus.odt |
| Full analysis: | https://app.any.run/tasks/1f91bb4c-71be-4080-a387-34be2d86f239 |
| Verdict: | Malicious activity |
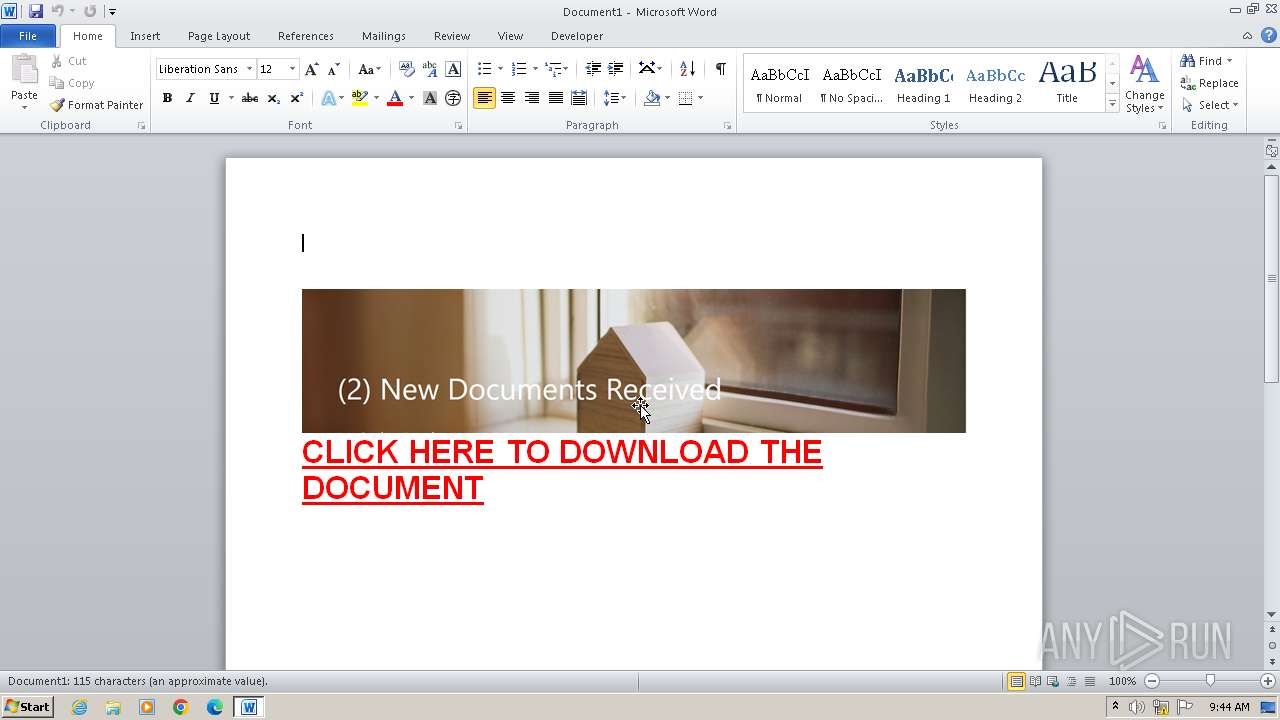
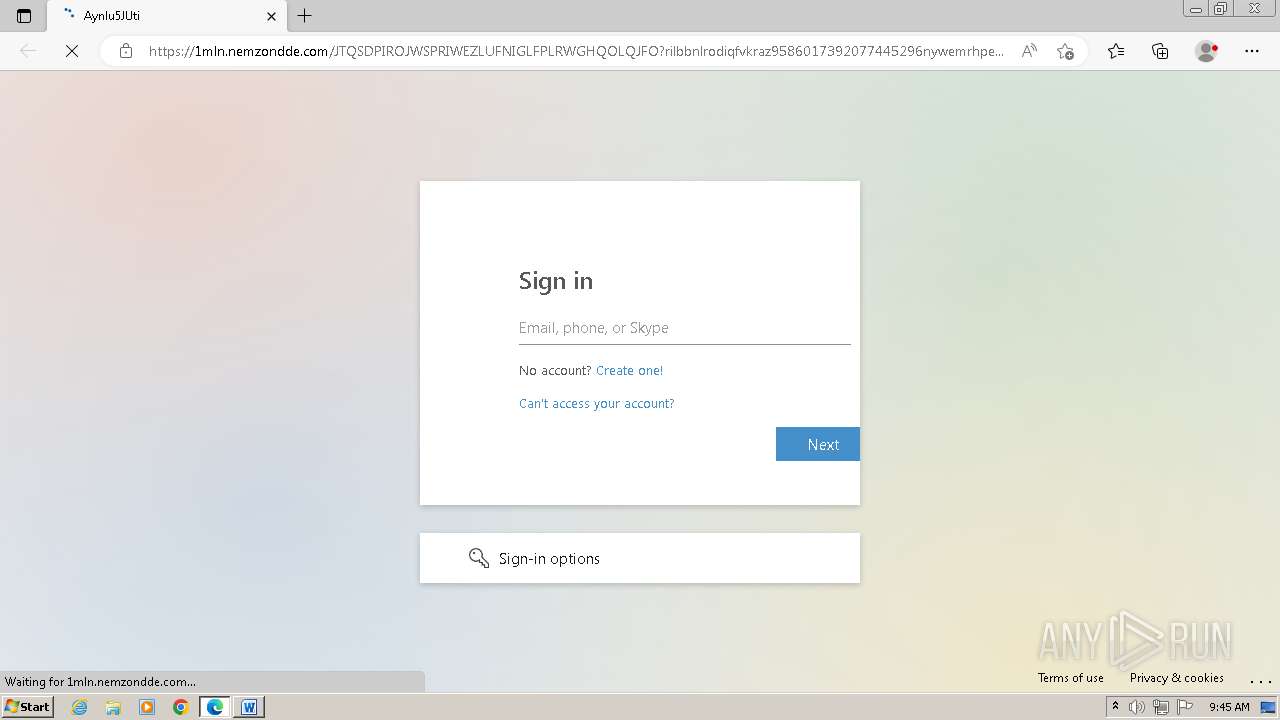
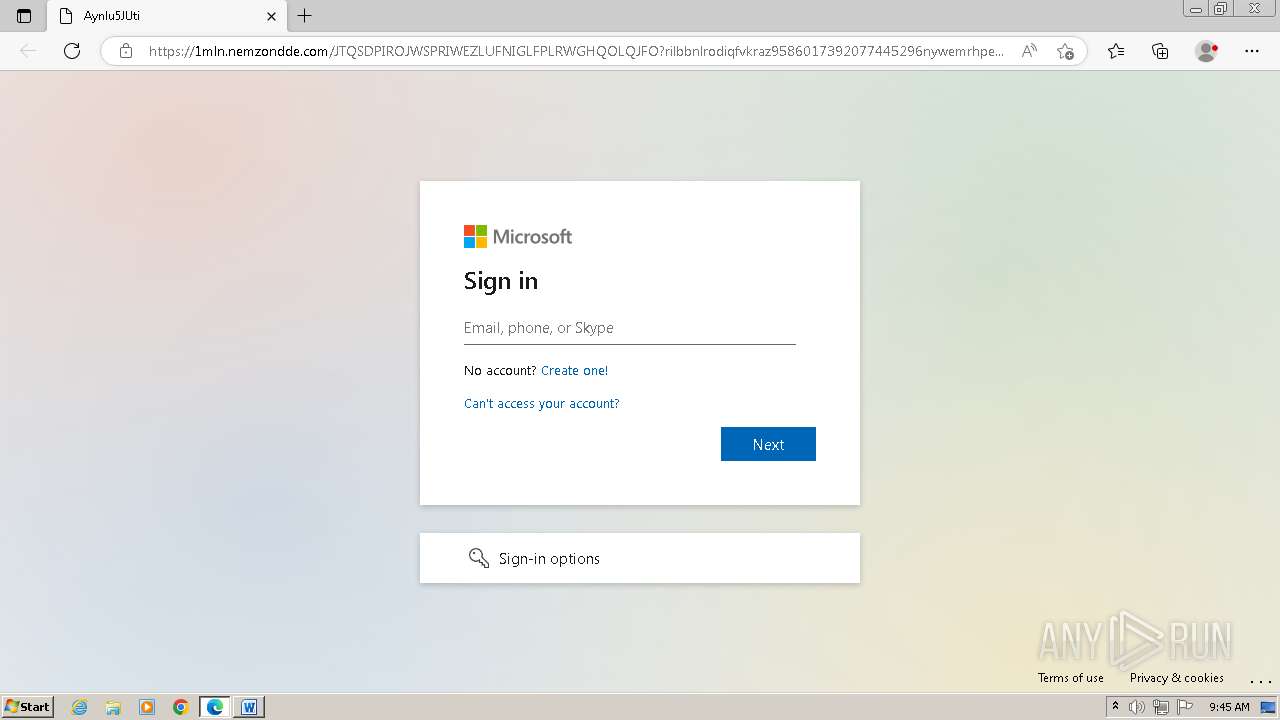
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | May 31, 2024, 08:44:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.oasis.opendocument.text |
| File info: | OpenDocument Text |
| MD5: | 93BBC0DDC92F16826F1A2173C4D01446 |
| SHA1: | 7307ABAF53EC67284D077488871F449F3CD55424 |
| SHA256: | 7B3206F591D7E4D05EAA5AA8AACB3EEDEAC002FDC5311A23484C5A3F95268BC9 |
| SSDEEP: | 49152:ENfbB4bDScGCrhAUobeWP5MCJX84o/obPs0DT3zd4THJTN4bp8kCE/R+0QlEU39s:E9bUDSQhmKGm2sMz61N4bGiRolH3SuI3 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- wmpnscfg.exe (PID: 2316)
Reads the computer name
- wmpnscfg.exe (PID: 2316)
Manual execution by a user
- wmpnscfg.exe (PID: 2316)
Application launched itself
- msedge.exe (PID: 116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .odt | | | OpenDocument Text document (54.1) |
|---|---|---|
| .xmind | | | XMind Workbook (37.6) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
XMP
| Creation-date: | 2019:09:17 00:54:53.266842047 |
|---|---|
| Generator: | Collabora_Office/22.05.15.2$Linux_X86_64 LibreOffice_project/b4081c294d18a40caa8f2e62698b21b548a5d60a |
| Date: | 2024:05:30 12:09:19.243006864 |
| Editing-duration: | PT5M45S |
| Editing-cycles: | 5 |
| Document-statisticTable-count: | - |
| Document-statisticImage-count: | 1 |
| Document-statisticObject-count: | - |
| Document-statisticPage-count: | 1 |
| Document-statisticParagraph-count: | 1 |
| Document-statisticWord-count: | 6 |
| Document-statisticCharacter-count: | 36 |
| Document-statisticNon-whitespace-character-count: | 30 |
Total processes
55
Monitored processes
22
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://1mln.nemzondde.com/1MLN/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2212 --field-trial-handle=1320,i,2354437698399206895,16045328372858118215,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x683ef598,0x683ef5a8,0x683ef5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1272 --field-trial-handle=1320,i,2354437698399206895,16045328372858118215,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=3508 --field-trial-handle=1320,i,2354437698399206895,16045328372858118215,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1644 --field-trial-handle=1320,i,2354437698399206895,16045328372858118215,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2012 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1220 --field-trial-handle=1320,i,2354437698399206895,16045328372858118215,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2248 --field-trial-handle=1320,i,2354437698399206895,16045328372858118215,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2316 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2220 --field-trial-handle=1320,i,2354437698399206895,16045328372858118215,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
16 713
Read events
15 482
Write events
976
Delete events
255
Modification events
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 1n? |
Value: 316E3F008C0F0000010000000000000000000000 | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
76
Text files
38
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3EA1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$mmel_virus.odt | binary | |
MD5:0EDA7CD91A4C600C9B849D748214E8F7 | SHA256:0E16973FD4DDB304C8105629966AD377FCD1F347C59BFA3FE5AE30A4C2D38755 | |||
| 116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Cab734F.tmp | compressed | |
MD5:49AEBF8CBD62D92AC215B2923FB1B9F5 | SHA256:B33EFCB95235B98B48508E019AFA4B7655E80CF071DEFABD8B2123FC8B29307F | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:5AE8478AF8DD6EEC7AD4EDF162DD3DF1 | SHA256:FE42AC92EAE3B2850370B73C3691CCF394C23AB6133DE39F1697A6EBAC4BEDCA | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:F9F6862685AC8EB7B5F5A31A4064A53B | SHA256:7AD884630BD859C12AA4B7CB7D0BDE69764AEF92433492C5DA5E2804A035CEAD | |||
| 116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF108435.TMP | — | |
MD5:— | SHA256:— | |||
| 116 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\D3DCX04R.txt | text | |
MD5:CA6AC4A1DA6F607AF4A2B5BE8636987E | SHA256:DCB0E535E38D589E2EB67B6C6D44B86EEC4E6D6102E5F021CB8325A8467334E3 | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma~RF1079e5.TMP | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
33
DNS requests
36
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3980 | WINWORD.EXE | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0158ce6586be5fef | unknown | — | — | unknown |
— | — | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c465c9ca7c57b2ec | unknown | — | — | unknown |
3980 | WINWORD.EXE | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
3980 | WINWORD.EXE | GET | 200 | 72.246.169.163:80 | http://x2.c.lencr.org/ | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?91e4205cfb4a00a1 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3980 | WINWORD.EXE | 104.21.72.55:443 | 1mln.nemzondde.com | CLOUDFLARENET | — | unknown |
3980 | WINWORD.EXE | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3980 | WINWORD.EXE | 72.246.169.163:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2012 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2012 | msedge.exe | 172.67.175.168:443 | 1mln.nemzondde.com | CLOUDFLARENET | US | unknown |
116 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
2012 | msedge.exe | 13.107.22.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
1mln.nemzondde.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
code.jquery.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
www.bing.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Client-Server Socket.IO CDN communication (cdn.socket .io) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (Tycoon 2FA) |