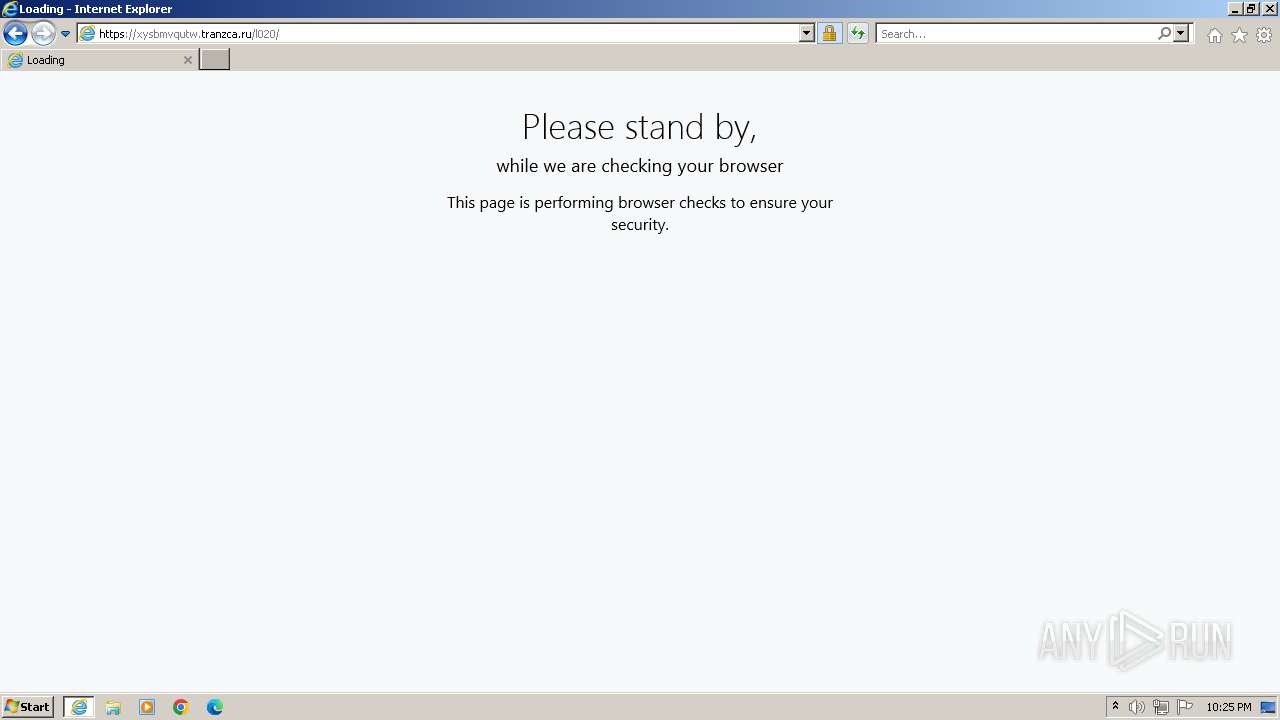
| URL: | https://dentaldomain.co.nz/MessageAtts.html |
| Full analysis: | https://app.any.run/tasks/2b8f1159-b65c-4a93-9707-99b9f585ba22 |
| Verdict: | Malicious activity |
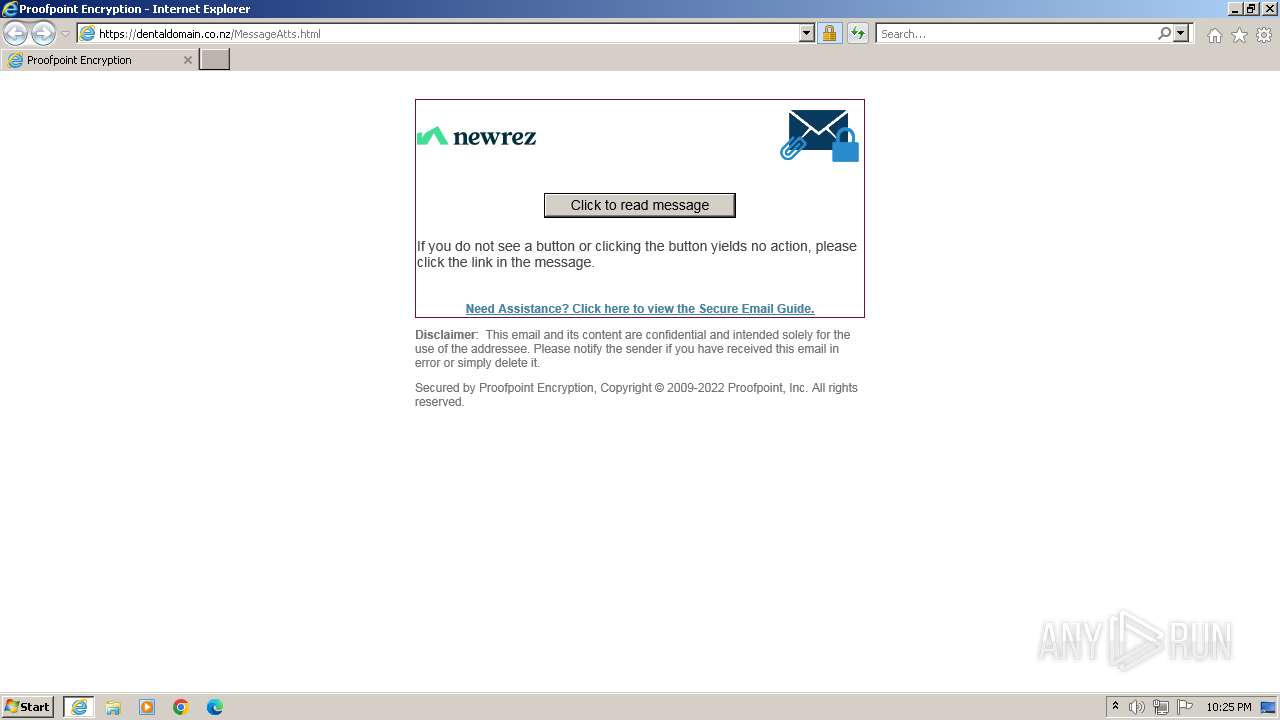
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | December 14, 2023, 22:25:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E30A3948379E7C8DE4C5493B73CA8C3D |
| SHA1: | D9F28F38AE330BBC920A22B92EC03226712B9077 |
| SHA256: | 7AF6DE69DAFFD40CB76FCD2D144C5306A828C953B722556800B5FDC16BDA9D5B |
| SSDEEP: | 3:N8YfGLjfk8NR0:2YfGHRR0 |
MALICIOUS
PHISHING has been detected (SURICATA)
- iexplore.exe (PID: 3028)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3048)
Checks supported languages
- wmpnscfg.exe (PID: 3176)
Manual execution by a user
- wmpnscfg.exe (PID: 3176)
Reads the computer name
- wmpnscfg.exe (PID: 3176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3028 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3048 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3048 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://dentaldomain.co.nz/MessageAtts.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3176 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
14 896
Read events
14 825
Write events
67
Delete events
4
Modification events
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3048) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
43
Text files
19
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarCA2.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabCB3.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:4A92139D6D5BCA05751B79CEDD182966 | SHA256:E4EDE0C26F986861011369ED1C4402B26392F9264732285556295D62332DBA87 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarCC4.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:67CD96C75026291E3C2BA3A59F3D69E5 | SHA256:82AE8F1B22F874F2A75759DFD3C3516E20E348C14623943B8475B33BB8AE65E4 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FDD5435F3890816C533A7F55ED4FB5FC | binary | |
MD5:DDD585391BE3BA75742DBDEFB147FF43 | SHA256:69206C184E27BD40DA537D31D0FF7B17F10E50DCBCED652F35F752117B231896 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3028 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabCA1.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
46
DNS requests
26
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3028 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b59953d50a4a6409 | unknown | compressed | 4.66 Kb | unknown |
3028 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
3028 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c9d7123905c1f3e1 | unknown | compressed | 4.66 Kb | unknown |
3028 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a05e16a1bdaa7520 | unknown | compressed | 65.2 Kb | unknown |
3028 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?028c1e64bf9eff21 | unknown | compressed | 65.2 Kb | unknown |
3028 | iexplore.exe | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3028 | iexplore.exe | GET | 200 | 2.19.120.159:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNldPWEOgpvbSXIN6XF2WRpNQ%3D%3D | unknown | binary | 503 b | unknown |
3048 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
3028 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://certificates.godaddy.com/repository/gdig2.crt | unknown | binary | 1.21 Kb | unknown |
3028 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDf9G2JjIkHBw%3D%3D | unknown | binary | 2.06 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3028 | iexplore.exe | 185.184.154.17:443 | dentaldomain.co.nz | Dreamscape Networks Limited | AU | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3028 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3028 | iexplore.exe | 23.56.202.135:80 | x1.c.lencr.org | AKAMAI-AS | GB | unknown |
3028 | iexplore.exe | 2.19.120.159:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
3048 | iexplore.exe | 2.19.120.21:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3048 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dentaldomain.co.nz |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.newrez.com |
| unknown |
securemail.johnsonbank.com |
| unknown |
certificates.godaddy.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3028 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
3028 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
3028 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
3028 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain chain detected (Tycoon 2FA) |
3028 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Client-Server Socket.IO CDN communication (cdn.socket .io) |