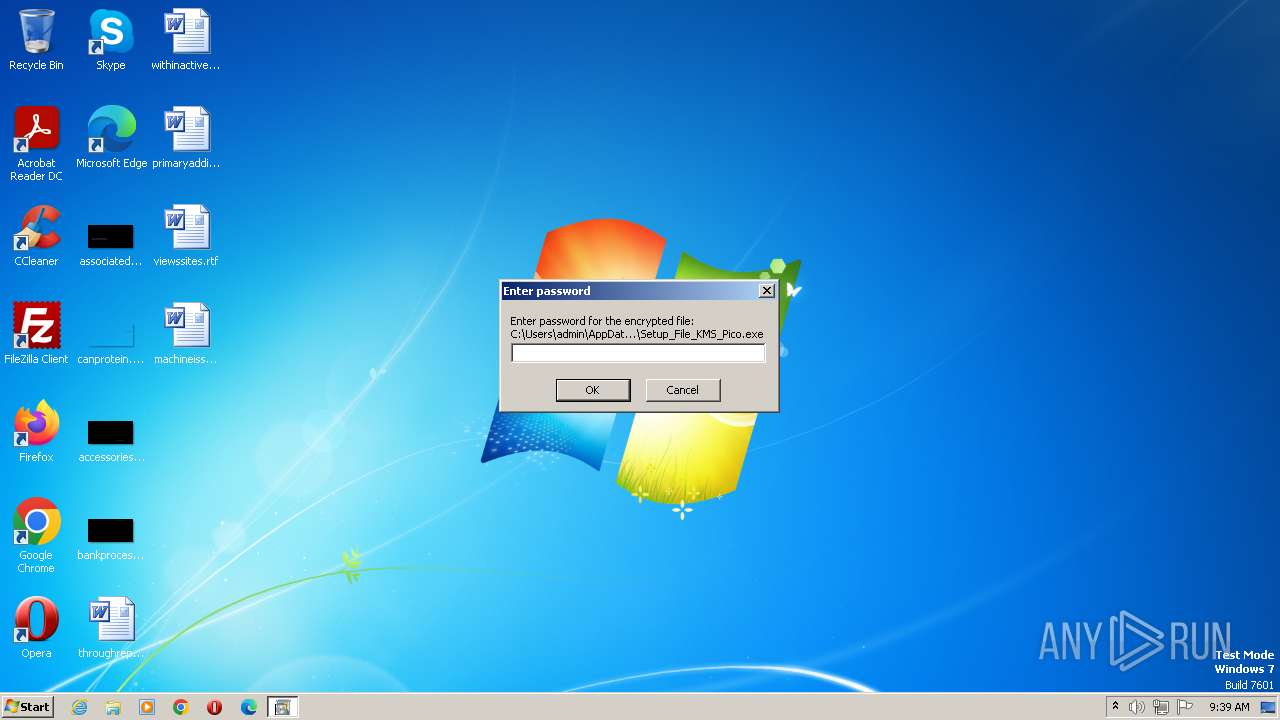
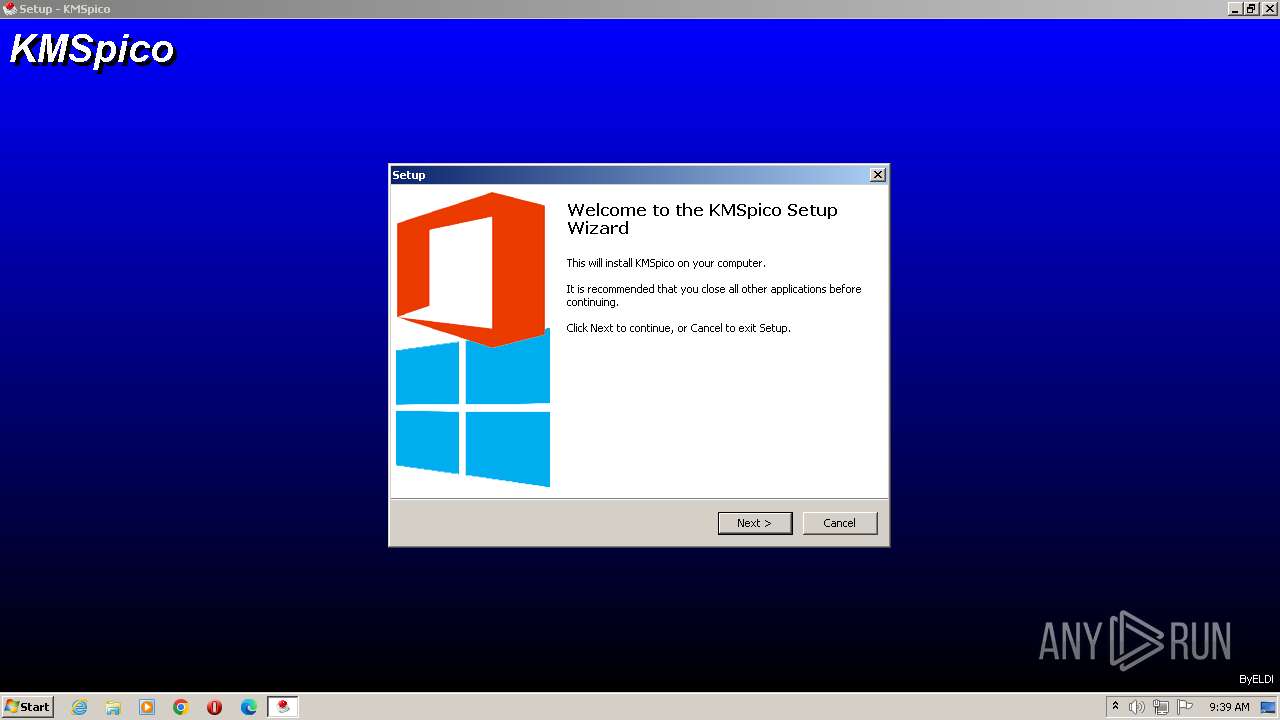
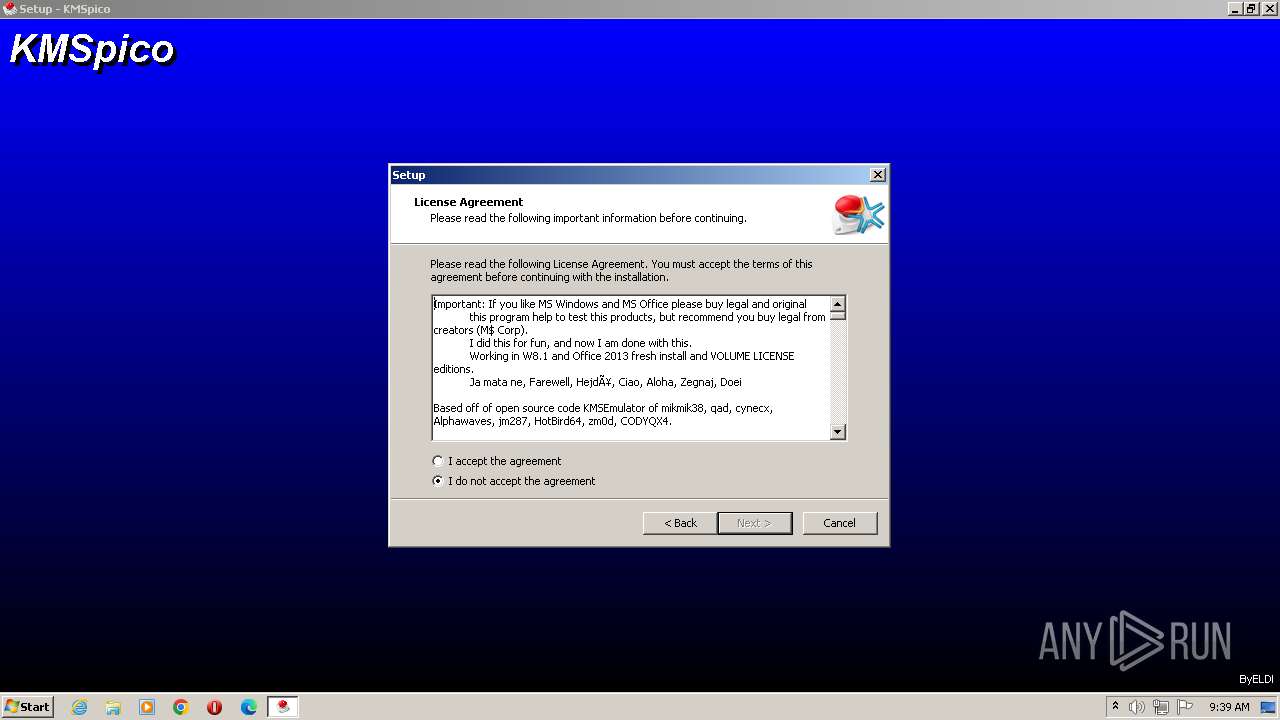
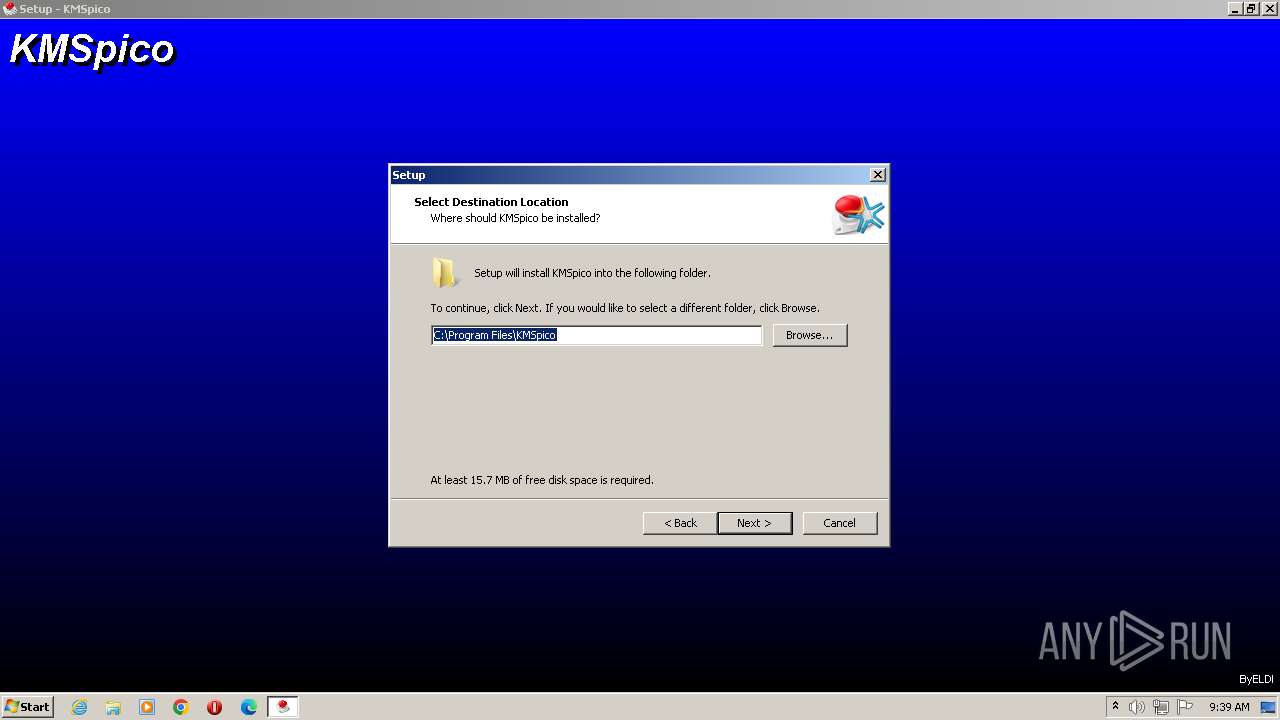
| File name: | Setup_File_KMS_Pico.exe |
| Full analysis: | https://app.any.run/tasks/ae2feaf8-069b-48a9-9d2c-be9df84a9cdf |
| Verdict: | Malicious activity |
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | September 26, 2023, 08:38:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 541F64D5D78ED7A50017728FEE6F4CE7 |
| SHA1: | 866D3056DC235C972087A3E9B7E4972C155DED76 |
| SHA256: | 7A79F51660CA4662F0E0B783DE8330F3C1157911968D04D8DD339A4AC0F3B386 |
| SSDEEP: | 196608:ZDz6BTdm03Pw4VrqACUdelOWZPrs+PPYJ:d6rm03PJqCdelOMrsqa |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2716)
Steals credentials
- KMS_pico.exe (PID: 2396)
Application was dropped or rewritten from another process
- KMS_pico.exe (PID: 2528)
- KMS_pico.exe (PID: 1796)
- consev.exe (PID: 3000)
Loads dropped or rewritten executable
- KMS_pico.tmp (PID: 1196)
CRYPTBOT detected by memory dumps
- KMS_pico.exe (PID: 2396)
Starts CMD.EXE for self-deleting
- KMS_pico.exe (PID: 2396)
Actions looks like stealing of personal data
- KMS_pico.exe (PID: 2396)
SUSPICIOUS
Drops the AutoIt3 executable file
- KMS_pico.exe (PID: 2396)
Reads the Internet Settings
- Setup_File_KMS_Pico.exe (PID: 3564)
- KMS_pico.exe (PID: 2396)
Starts CMD.EXE for commands execution
- KMS_pico.exe (PID: 2396)
Searches for installed software
- KMS_pico.exe (PID: 2396)
Reads the Windows owner or organization settings
- KMS_pico.tmp (PID: 1196)
Reads browser cookies
- KMS_pico.exe (PID: 2396)
The process executes via Task Scheduler
- consev.exe (PID: 3000)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2792)
INFO
Checks supported languages
- KMS_pico.exe (PID: 2396)
- Setup_File_KMS_Pico.exe (PID: 3564)
- KMS_pico.exe (PID: 2528)
- KMS_pico.tmp (PID: 2288)
- KMS_pico.exe (PID: 1796)
- KMS_pico.tmp (PID: 1196)
- consev.exe (PID: 3000)
Reads the computer name
- Setup_File_KMS_Pico.exe (PID: 3564)
- KMS_pico.exe (PID: 2396)
- KMS_pico.tmp (PID: 2288)
- KMS_pico.tmp (PID: 1196)
Reads product name
- KMS_pico.exe (PID: 2396)
Create files in a temporary directory
- Setup_File_KMS_Pico.exe (PID: 3564)
- KMS_pico.exe (PID: 2528)
- KMS_pico.exe (PID: 1796)
- KMS_pico.tmp (PID: 1196)
- KMS_pico.exe (PID: 2396)
Creates files or folders in the user directory
- KMS_pico.exe (PID: 2396)
Reads Environment values
- KMS_pico.exe (PID: 2396)
Reads Windows Product ID
- KMS_pico.exe (PID: 2396)
Reads CPU info
- KMS_pico.exe (PID: 2396)
Application was dropped or rewritten from another process
- KMS_pico.tmp (PID: 2288)
- KMS_pico.tmp (PID: 1196)
Checks proxy server information
- KMS_pico.exe (PID: 2396)
Reads the machine GUID from the registry
- KMS_pico.exe (PID: 2396)
Reads mouse settings
- consev.exe (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
CryptBot
(PID) Process(2396) KMS_pico.exe
C2http://sgizfn14.top/gate.php;
Options
CookiesFirefoxfalse
Screenshottrue
Wallettrue
ChromeExttrue
CookiesEdgefalse
HistoryEdgefalse
Desktoptrue
EdgeExttrue
HistoryChromefalse
EdgeDBtrue
CookiesOperafalse
ChromeDBtrue
CookiesChromefalse
Firefoxfalse
HistoryFirefoxfalse
Edgefalse
FirefoxDBtrue
Operafalse
Chromefalse
HistoryOperafalse
ScreenFile$CREEN.PNG
PasswordFile_AllPasswords.txt
FirefoxDBFolder_Firefox
InfoFile_Information.txt
DesktopFolder_Desktop
CookiesFile_AllCookies.txt
ChromeDBFolder_Chrome
DeleteAfterEndtrue
HistoryFile_AllHistory.txt
UserAgentMozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36
Prefixmrd-
EdgeDBFolder_Edge
MessageAfterEndfalse
WalletFolder_Wallet
ExternalDownload
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| LanguageId: | en |
|---|---|
| ProductVersion: | 1.3.541.1 |
| ProductName: | Dropbox Update |
| OriginalFileName: | DropboxUpdateSetup.exe |
| LegalCopyright: | Copyright: Dropbox, Inc. 2015 (Omaha Copyright Google Inc.) |
| InternalName: | Dropbox Update Setup |
| FileVersion: | 1.3.541.1 |
| FileDescription: | Dropbox Update Setup |
| CompanyName: | Dropbox, Inc. |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.3.541.1 |
| FileVersionNumber: | 1.3.541.1 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x1ec40 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 787968 |
| CodeSize: | 201216 |
| LinkerVersion: | 14 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2020:12:01 18:00:55+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
51
Monitored processes
12
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1196 | "C:\Users\admin\AppData\Local\Temp\is-93U10.tmp\KMS_pico.tmp" /SL5="$B0178,2952592,69120,C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe" /SPAWNWND=$40162 /NOTIFYWND=$60184 | C:\Users\admin\AppData\Local\Temp\is-93U10.tmp\KMS_pico.tmp | — | KMS_pico.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1796 | "C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe" /SPAWNWND=$40162 /NOTIFYWND=$60184 | C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe | KMS_pico.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: KMSpico Setup Exit code: 0 Version: 10.2.0 Modules
| |||||||||||||||
| 2288 | "C:\Users\admin\AppData\Local\Temp\is-J1D3D.tmp\KMS_pico.tmp" /SL5="$60184,2952592,69120,C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe" | C:\Users\admin\AppData\Local\Temp\is-J1D3D.tmp\KMS_pico.tmp | — | KMS_pico.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2396 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\KMS_pico.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\KMS_pico.exe | Setup_File_KMS_Pico.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 5439627 Modules
CryptBot(PID) Process(2396) KMS_pico.exe C2http://sgizfn14.top/gate.php; Options CookiesFirefoxfalse Screenshottrue Wallettrue ChromeExttrue CookiesEdgefalse HistoryEdgefalse Desktoptrue EdgeExttrue HistoryChromefalse EdgeDBtrue CookiesOperafalse ChromeDBtrue CookiesChromefalse Firefoxfalse HistoryFirefoxfalse Edgefalse FirefoxDBtrue Operafalse Chromefalse HistoryOperafalse ScreenFile$CREEN.PNG PasswordFile_AllPasswords.txt FirefoxDBFolder_Firefox InfoFile_Information.txt DesktopFolder_Desktop CookiesFile_AllCookies.txt ChromeDBFolder_Chrome DeleteAfterEndtrue HistoryFile_AllHistory.txt UserAgentMozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36 Prefixmrd- EdgeDBFolder_Edge MessageAfterEndfalse WalletFolder_Wallet ExternalDownload | |||||||||||||||
| 2528 | C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe | C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe | — | cmd.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: KMSpico Setup Exit code: 0 Version: 10.2.0 Modules
| |||||||||||||||
| 2716 | /C schtasks /create /tn \Diagnostic\Service /tr """"C:\Users\admin\AppData\Roaming\faxjrc\consev.exe""" """C:\Users\admin\AppData\Roaming\faxjrc\consev.dat"""" /du 9700:18 /st 00:02 /sc once /ri 1 /f | C:\Windows\System32\cmd.exe | — | KMS_pico.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2760 | schtasks /create /tn \Diagnostic\Service /tr """"C:\Users\admin\AppData\Roaming\faxjrc\consev.exe""" """C:\Users\admin\AppData\Roaming\faxjrc\consev.dat"""" /du 9700:18 /st 00:02 /sc once /ri 1 /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2780 | /C "C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe" | C:\Windows\System32\cmd.exe | — | KMS_pico.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2792 | "C:\Windows\System32\cmd.exe" /c timeout -t 5 && del "C:\Users\admin\AppData\Local\Temp\RarSFX0\KMS_pico.exe" | C:\Windows\System32\cmd.exe | — | KMS_pico.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2812 | timeout -t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 815
Read events
2 795
Write events
20
Delete events
0
Modification events
| (PID) Process: | (3564) Setup_File_KMS_Pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3564) Setup_File_KMS_Pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3564) Setup_File_KMS_Pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3564) Setup_File_KMS_Pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2396) KMS_pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2396) KMS_pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2396) KMS_pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2396) KMS_pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000004F010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2396) KMS_pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2396) KMS_pico.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
28
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3564 | Setup_File_KMS_Pico.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\KMS_pico.exe | — | |
MD5:— | SHA256:— | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Roaming\faxjrc\consev.exe | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Roaming\faxjrc\KMS_pico.exe | executable | |
MD5:A02164371A50C5FF9FA2870EF6E8CFA3 | SHA256:64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Roaming\faxjrc\consev.dat | text | |
MD5:532B7CC788160997EA22DEEC6F7D69F8 | SHA256:DFB8264953A5D0D7DB1EB289430285B488A147F44DDEBAEC70B6EC7D7219FAF0 | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Local\Temp\E4D2.tmp | binary | |
MD5:C9FF7748D8FCEF4CF84A5501E996A641 | SHA256:4D3F3194CB1133437AA69BB880C8CBB55DDF06FF61A88CA6C3F1BBFBFD35D988 | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Local\Temp\E420.tmp | binary | |
MD5:C944D26D2618E307D10F2C8AD90613E4 | SHA256:EE55F8E332F3AF11C9D30638B11EB9E7F214DC32BA4E15EBF2CDAE9CB86D05FF | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Local\Temp\E502.tmp | binary | |
MD5:C6BA1CC62D2EB388E2998BEC2D03ABAC | SHA256:F5D028F3C77174AF630C0EF470273754400C49B54AB023AAB9E24A9E32A1EA5C | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Local\Temp\E462.tmp | binary | |
MD5:F47EB60CDF981C17722D0CE740129927 | SHA256:0210071DF12CA42D70DCB679926668AE072264705AC139A24F94BBC5A129DD8F | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Local\Temp\E391.tmp | text | |
MD5:17F95CAF560E05E9B51AA429081A31BC | SHA256:14D3A68B607FFA75CC9285BA0DB474EF3452DCFA1F9E96529C067B194A6F9AF1 | |||
| 2396 | KMS_pico.exe | C:\Users\admin\AppData\Local\Temp\E371.tmp | text | |
MD5:17F95CAF560E05E9B51AA429081A31BC | SHA256:14D3A68B607FFA75CC9285BA0DB474EF3452DCFA1F9E96529C067B194A6F9AF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
2
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sgizfn14.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |