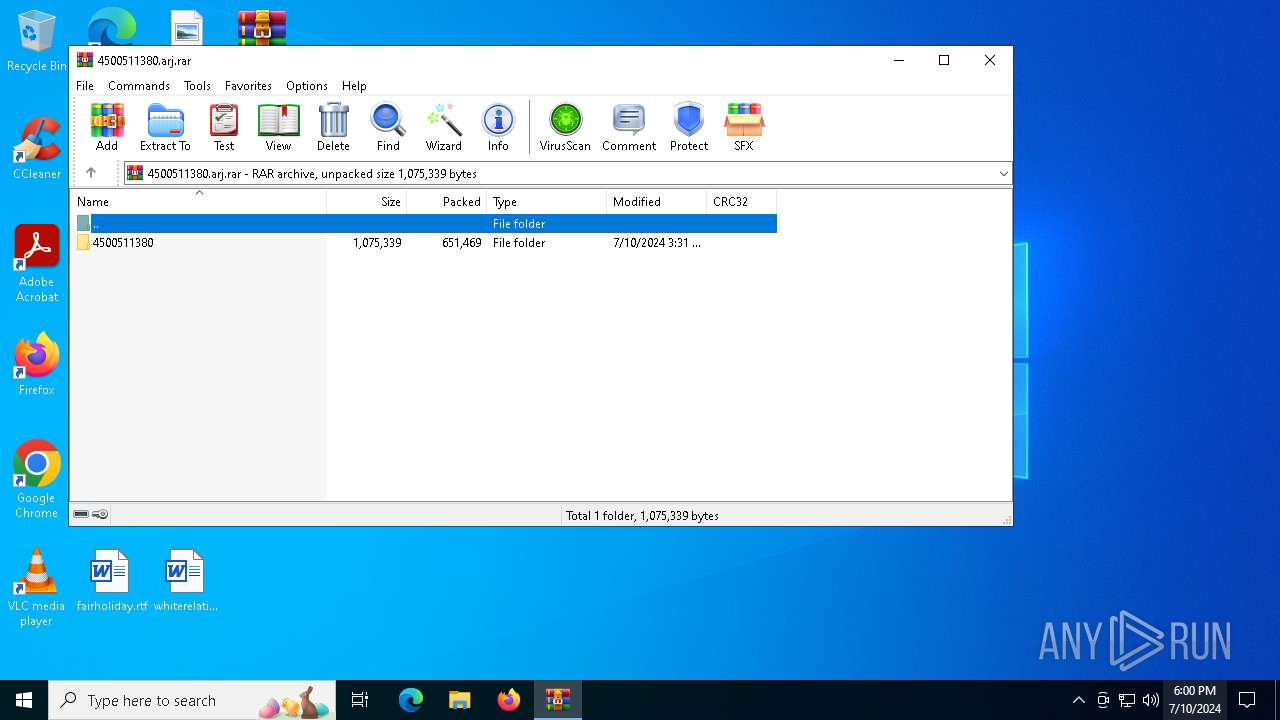
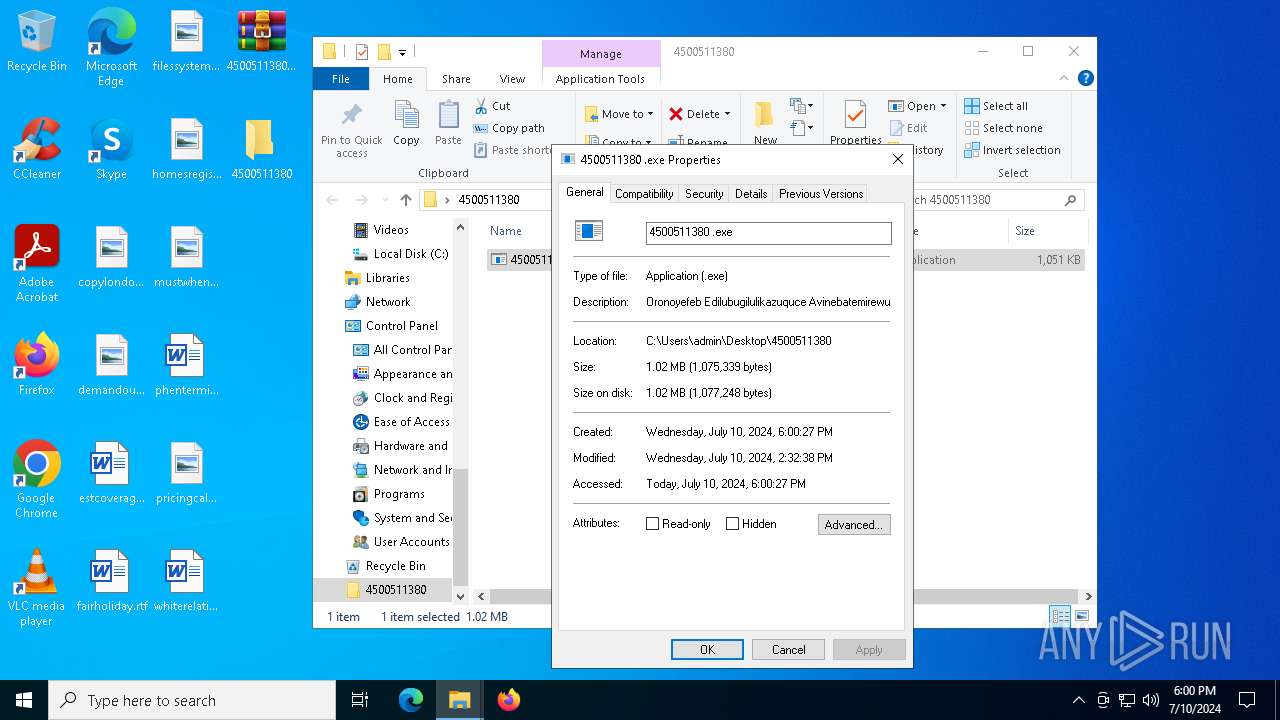
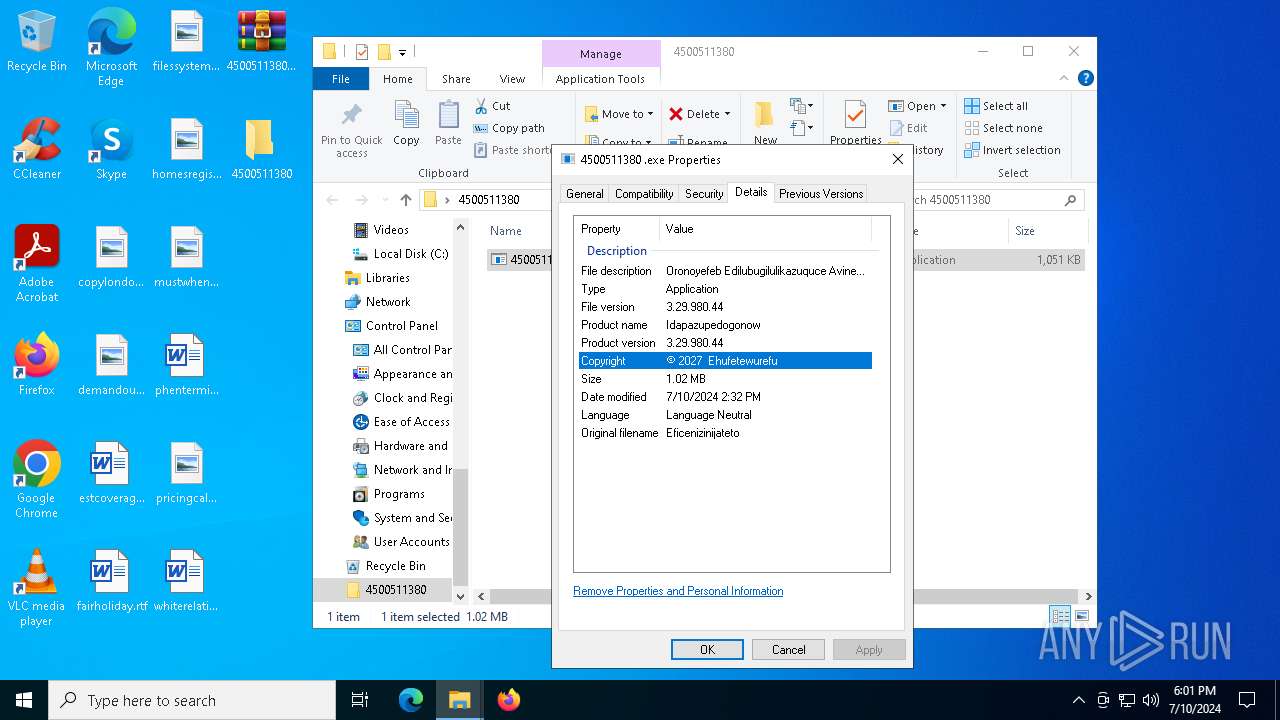
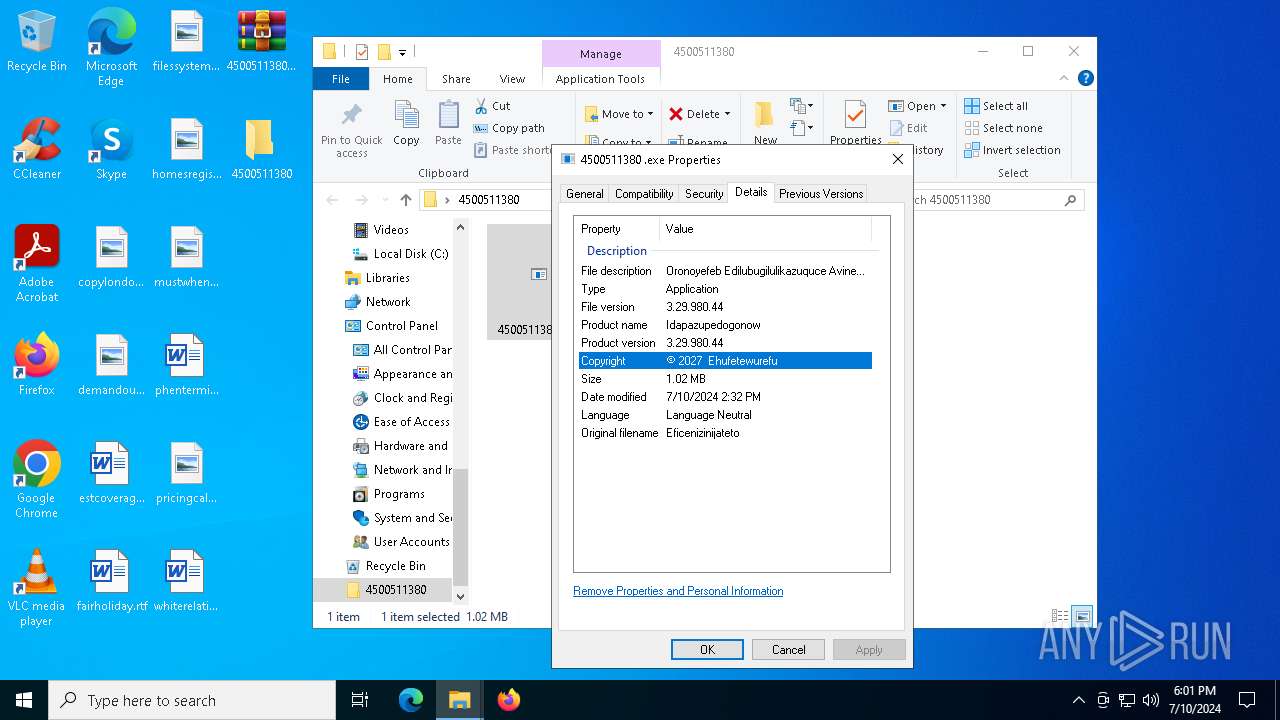
| File name: | 4500511380.arj |
| Full analysis: | https://app.any.run/tasks/da70b80f-8e30-42ba-bf40-1d5aa377cf8a |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | July 10, 2024, 18:00:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4115271ABDE75B7E9D0BA13BA1778CB2 |
| SHA1: | 79D5A2864D23EAC1736BD4F53E223141700F75AA |
| SHA256: | 7A4BD1B864E5F68842EDF9E9D8C8A3949011A72FC1BA1CDD19DF190C7A3877E0 |
| SSDEEP: | 24576:SDwjTiz95a7D9J4zZPC5wEwM4+ltdb62T22JONonz4PH7JXwJoye1:SDwjmz95a7D9J49PC5wEwM4+ltdb62To |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6308)
Adds path to the Windows Defender exclusion list
- 4500511380 .exe (PID: 3848)
FORMBOOK has been detected (YARA)
- auditpol.exe (PID: 3580)
- 4500511380 .exe (PID: 3848)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4500511380 .exe (PID: 3848)
Reads the date of Windows installation
- 4500511380 .exe (PID: 3848)
Script adds exclusion path to Windows Defender
- 4500511380 .exe (PID: 3848)
Starts POWERSHELL.EXE for commands execution
- 4500511380 .exe (PID: 3848)
Executes application which crashes
- 4500511380 .exe (PID: 3848)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5284)
Manual execution by a user
- WinRAR.exe (PID: 5284)
- 4500511380 .exe (PID: 3848)
Checks supported languages
- 4500511380 .exe (PID: 3848)
- ngen.exe (PID: 6448)
Reads the computer name
- 4500511380 .exe (PID: 3848)
Reads the machine GUID from the registry
- 4500511380 .exe (PID: 3848)
Process checks computer location settings
- 4500511380 .exe (PID: 3848)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5464)
Checks proxy server information
- WerFault.exe (PID: 1200)
- slui.exe (PID: 1796)
Creates files or folders in the user directory
- WerFault.exe (PID: 1200)
Reads the software policy settings
- WerFault.exe (PID: 1200)
- slui.exe (PID: 6808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
155
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\system32\WerFault.exe -u -p 3848 -s 1176 | C:\Windows\System32\WerFault.exe | 4500511380 .exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\Windows\SysWOW64\auditpol.exe" | C:\Windows\SysWOW64\auditpol.exe | — | 4500511380 .exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Audit Policy Program Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1796 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3580 | "C:\Windows\SysWOW64\auditpol.exe" | C:\Windows\SysWOW64\auditpol.exe | 4500511380 .exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Audit Policy Program Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | "C:\Users\admin\Desktop\4500511380\4500511380 .exe" | C:\Users\admin\Desktop\4500511380\4500511380 .exe | explorer.exe | ||||||||||||
User: admin Company: Ehufetewurefu Integrity Level: MEDIUM Description: Oronoyefeb Edilubugilulikazuquce Avinebatemirewubi Ojegamiyuvefekafa Ezemuyupilutu Unisixa. Exit code: 3762504530 Version: 3.29.980.44 Modules
| |||||||||||||||
| 4320 | "C:\Windows\System32\svchost.exe" | C:\Windows\System32\svchost.exe | — | 4500511380 .exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 4500511380 .exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5284 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\4500511380.arj.rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
16 592
Read events
16 568
Write events
24
Delete events
0
Modification events
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\4500511380.arj.rar | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
1
Suspicious files
5
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1200 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_4500511380 .exe_2958cec2f5b659531fede63249d22dea8b4f5a3_cef3deed_966f7f4b-95f3-4687-9929-58d9c07f5345\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1200 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\4500511380 .exe.3848.dmp | — | |
MD5:— | SHA256:— | |||
| 5464 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0o2acpbn.olc.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5464 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:6692F3492CDDB840C7F0875890B84D95 | SHA256:50B213B71D2D91CEBCCF7903916631D9B2C7B8B6BDD0D51C64F8AD7B9F9FD367 | |||
| 1200 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:979F91388D4DF2F2D68497400C9830DD | SHA256:A9F27E26AA818BC97449D30D5707254EDCA571D21D36B4576C7CD9A56FB18BC5 | |||
| 5284 | WinRAR.exe | C:\Users\admin\Desktop\4500511380\4500511380 .exe | executable | |
MD5:AE7035FE42AF28D9FA61F2A9D4D93A19 | SHA256:683E96CACFF2FDE395C3C68648B117C5B6DD99C35BB1F048E58A246369167431 | |||
| 1200 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:9DAFC34140C582770F87115E1D6C5AD0 | SHA256:31E77E7CE5003153C94CF25D6D4017AD0F6F373ED43B8F6B2A38996882EEE6A3 | |||
| 1200 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER30B7.tmp.dmp | binary | |
MD5:42B0098DD7BCBCCA7131253CB03BE576 | SHA256:C1FDDAF50719EC713CD6248F0CDCE137D12034C2649E3B67FD502ACE1D8785D1 | |||
| 1200 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER31D2.tmp.xml | xml | |
MD5:36CFD3DE382657E45FDF88AAF65F3280 | SHA256:DB74B20FEA9387D7938B16FC4DF74A93926D33085E8EFAC8B5A32EC5506157AD | |||
| 1200 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER31B2.tmp.WERInternalMetadata.xml | xml | |
MD5:12EEEA2CC6498BC03D2D8239823E0D62 | SHA256:5AF2F97F693A477D171901FC9B918DF7E37B77C0F4F4D55AA1ED627EE8E8AC24 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
79
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2824 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
2824 | MoUsoCoreWorker.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3656 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
7120 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6636 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1200 | WerFault.exe | GET | 200 | 23.48.23.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
1200 | WerFault.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
7120 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2064 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
188 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2824 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2824 | MoUsoCoreWorker.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |