| File name: | Ref8810998235 Auto System Generated Order Form 051022.pdf.z |
| Full analysis: | https://app.any.run/tasks/f155a353-d864-41f8-bf3d-52a045c4ef56 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | October 05, 2022, 05:14:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A9695201D74C3C997C4E12FAE0FFA6EF |
| SHA1: | 5F357D61598E9DDC44E045C087C9BA88F828014B |
| SHA256: | 7993AD9CAE6E6EC83117A02D3D213ED20DBF15D9B33384083AC5C21D1A2B2272 |
| SSDEEP: | 12288:bfmej6Qxh/h0DJKO4zymfJKXqlq+7iqEIfZ0XsshLzdOPZo5n:jj7xxbzymfJKNIFEIfZasshdj5n |
MALICIOUS
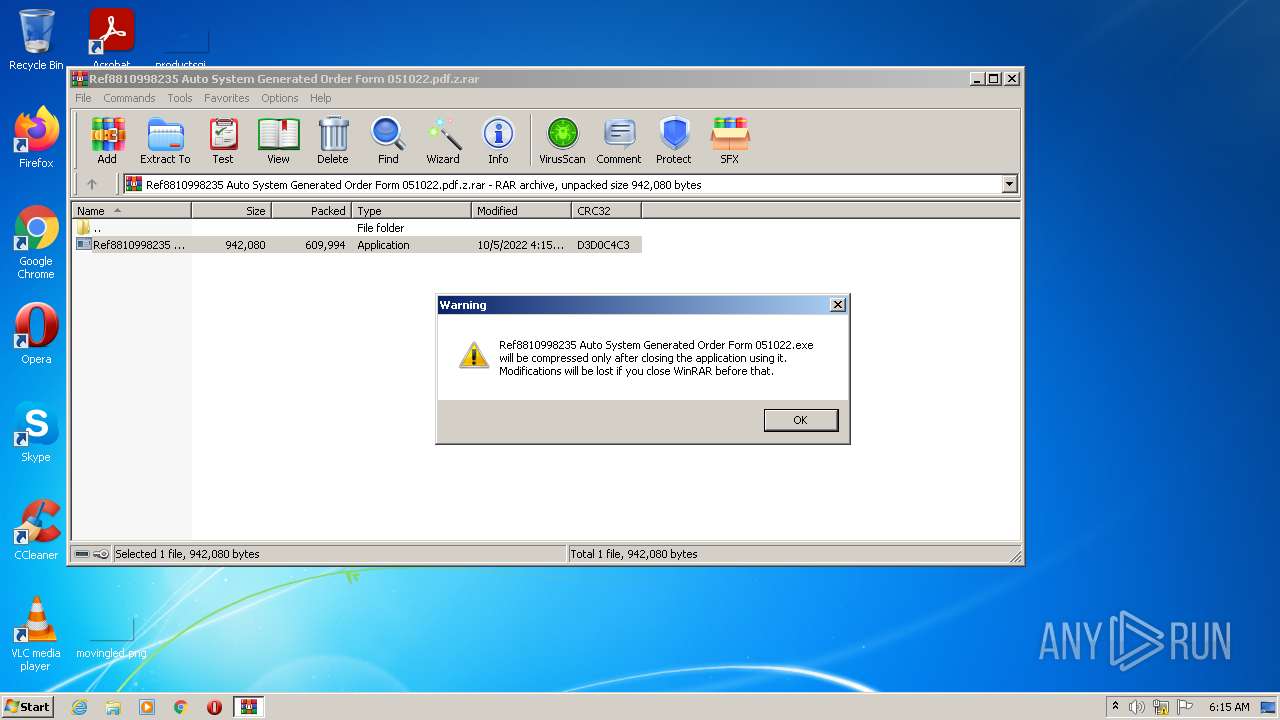
Application was dropped or rewritten from another process
- Ref8810998235 Auto System Generated Order Form 051022.exe (PID: 2316)
- Ref8810998235 Auto System Generated Order Form 051022.exe (PID: 2752)
FORMBOOK detected by memory dumps
- cmd.exe (PID: 2964)
Loads dropped or rewritten executable
- cmd.exe (PID: 2964)
FORMBOOK was detected
- Explorer.EXE (PID: 1488)
SUSPICIOUS
Application launched itself
- Ref8810998235 Auto System Generated Order Form 051022.exe (PID: 2316)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
39
Monitored processes
7
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\Windows\System32\autoconv.exe" | C:\Windows\System32\autoconv.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Conversion Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1488 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Ref8810998235 Auto System Generated Order Form 051022.pdf.z.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2316 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1752.2484\Ref8810998235 Auto System Generated Order Form 051022.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1752.2484\Ref8810998235 Auto System Generated Order Form 051022.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Quickbiz Integrity Level: MEDIUM Description: Hierarchy Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | — | cmd.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2752 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1752.2484\Ref8810998235 Auto System Generated Order Form 051022.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1752.2484\Ref8810998235 Auto System Generated Order Form 051022.exe | — | Ref8810998235 Auto System Generated Order Form 051022.exe | |||||||||||
User: admin Company: Quickbiz Integrity Level: MEDIUM Description: Hierarchy Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 2964 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 619
Read events
2 576
Write events
43
Delete events
0
Modification events
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ref8810998235 Auto System Generated Order Form 051022.pdf.z.rar | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
2
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1752.2484\Ref8810998235 Auto System Generated Order Form 051022.exe | executable | |
MD5:— | SHA256:— | |||
| 2964 | cmd.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\sqlite-dll-win32-x86-3140000[1].zip | compressed | |
MD5:B722723B3142C9D0A3C65E2DABD8003F | SHA256:052404F3FFA178F7E3C5353CFC361675661226D5E09984173EBDA5C3EA1A229C | |||
| 2964 | cmd.exe | C:\Users\admin\AppData\Local\Temp\sqlite3.def | text | |
MD5:DE71633DE073966EB5D5F787EAC989BB | SHA256:C810A7589A228352269413CC503647DF82B4320B7C0B596A15D2842DAC7F843A | |||
| 2964 | cmd.exe | C:\Users\admin\AppData\Local\Temp\033736 | sqlite | |
MD5:CC104C4E4E904C3AD7AD5C45FBFA7087 | SHA256:321BE844CECC903EF1E7F875B729C96BB3ED0D4986314384CD5944A29A670C9B | |||
| 2964 | cmd.exe | C:\Users\admin\AppData\Local\Temp\sqlite3.dll | executable | |
MD5:C6EC991471D42128268EA10236D9CDB8 | SHA256:1B755CC3093DD45A0DF857854AEDFEB3C8F3622CFF5BC491F2D492EBFA3EF8E0 | |||
| 2964 | cmd.exe | C:\Users\admin\AppData\Local\Temp\apxdcv_.zip | compressed | |
MD5:B722723B3142C9D0A3C65E2DABD8003F | SHA256:052404F3FFA178F7E3C5353CFC361675661226D5E09984173EBDA5C3EA1A229C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
32
DNS requests
9
Threats
53
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1488 | Explorer.EXE | POST | 301 | 3.13.31.214:80 | http://www.escalatuconcesionario.com/r83r/ | US | — | — | malicious |
1488 | Explorer.EXE | POST | 301 | 3.13.31.214:80 | http://www.escalatuconcesionario.com/r83r/ | US | — | — | malicious |
1488 | Explorer.EXE | POST | 404 | 199.192.31.144:80 | http://www.sandiancin.info/r83r/ | US | html | 4.30 Kb | malicious |
1488 | Explorer.EXE | POST | 200 | 82.98.135.44:80 | http://www.alquilaynavega.com/r83r/ | ES | html | 605 b | malicious |
1488 | Explorer.EXE | GET | 404 | 8.136.6.150:80 | http://www.yujianliangyuan.com/r83r/?jdZxcnkh=WUng4kfVIKhxxpfy+MMBX9b5JVWk0YYpy8gCWupW4lVARPTQHvJYzDAOVF3HyEFttx9GyE1/w21NUBVtX9WRJjgx6URfBvFiBohGfR0=&CTUL=cv14DBMX | US | html | 1.14 Kb | malicious |
1488 | Explorer.EXE | POST | 200 | 82.98.135.44:80 | http://www.alquilaynavega.com/r83r/ | ES | html | 605 b | malicious |
1488 | Explorer.EXE | POST | 404 | 199.192.31.144:80 | http://www.sandiancin.info/r83r/ | US | html | 4.30 Kb | malicious |
1488 | Explorer.EXE | POST | 404 | 199.192.31.144:80 | http://www.sandiancin.info/r83r/ | US | html | 4.30 Kb | malicious |
2964 | cmd.exe | GET | 404 | 199.192.31.144:80 | http://www.sandiancin.info/r83r/?jdZxcnkh=T0VObpKVtGBi/Me6r7YC3sKge/t04L3KGHkU2dPfLuAeEOIoDpGjfsz7MV8q1TQ69eVBxfVKJUhM8669YP8y/Zgb/+yTCyZaprW2Awk=&CTUL=cv14DBMX&wn=1 | US | html | 4.30 Kb | malicious |
2964 | cmd.exe | GET | 200 | 45.33.6.223:80 | http://www.sqlite.org/2016/sqlite-dll-win32-x86-3140000.zip | US | compressed | 423 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1488 | Explorer.EXE | 8.136.6.150:80 | www.yujianliangyuan.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | malicious |
2964 | cmd.exe | 45.33.6.223:80 | www.sqlite.org | Linode, LLC | US | suspicious |
1488 | Explorer.EXE | 64.190.63.111:80 | www.gobeautyfitness-d.space | SEDO GmbH | DE | malicious |
1488 | Explorer.EXE | 199.192.31.144:80 | www.sandiancin.info | NAMECHEAP-NET | US | malicious |
1488 | Explorer.EXE | 3.13.31.214:80 | www.escalatuconcesionario.com | AMAZON-02 | US | malicious |
2964 | cmd.exe | 199.192.31.144:80 | www.sandiancin.info | NAMECHEAP-NET | US | malicious |
1488 | Explorer.EXE | 82.98.135.44:80 | www.alquilaynavega.com | DinaHosting S.L. | ES | malicious |
1488 | Explorer.EXE | 185.249.60.78:80 | www.30000z.com | sun-asn | HK | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.yujianliangyuan.com |
| malicious |
www.sqlite.org |
| whitelisted |
www.gobeautyfitness-d.space |
| malicious |
www.sandiancin.info |
| malicious |
dns.msftncsi.com |
| shared |
www.escalatuconcesionario.com |
| malicious |
www.alquilaynavega.com |
| malicious |
www.30000z.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1488 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1488 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1488 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1488 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1488 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1488 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1488 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1488 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1488 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1488 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (POST) M2 |
9 ETPRO signatures available at the full report