| download: | CrystalCrypter2.zip |
| Full analysis: | https://app.any.run/tasks/432d738b-565d-4a02-a7ec-673c9818fe01 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 27, 2022, 09:56:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | C6A2E7778294128F204654BE18FC4BB1 |
| SHA1: | B4483E311FB3510964FEFF512D4E86B41B4DFDDD |
| SHA256: | 79929C389CE10E81B34FD52F257C076BEE6847756174D2110BFA9B3E05A654D2 |
| SSDEEP: | 98304:6fK/fCcjKoZeupHwsL8cD+mSWr4o5iGuUPz8V3id0qpK:6fKnFVwRml4o96MpK |
MALICIOUS
Application was dropped or rewritten from another process
- CrystalCrypter2.exe (PID: 3388)
- win64obf.exe (PID: 2772)
- win32dll.exe (PID: 2168)
- 12.exe (PID: 1844)
- CrystalCrypter2.exe (PID: 1612)
Executes PowerShell scripts
- cmd.exe (PID: 3692)
- cmd.exe (PID: 3472)
Drops executable file immediately after starts
- CrystalCrypter2.exe (PID: 3388)
- win64obf.exe (PID: 2772)
- WinRAR.exe (PID: 3172)
Stealing of credential data
- 12.exe (PID: 1844)
Steals credentials from Web Browsers
- 12.exe (PID: 1844)
Actions looks like stealing of personal data
- 12.exe (PID: 1844)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 924)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 984)
ASYNCRAT detected by memory dumps
- win32dll.exe (PID: 2168)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3556)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3172)
- powershell.exe (PID: 4064)
- powershell.exe (PID: 1788)
- 12.exe (PID: 1844)
- win64obf.exe (PID: 2772)
- powershell.exe (PID: 2340)
- win32dll.exe (PID: 2168)
Starts CMD.EXE for commands execution
- CrystalCrypter2.exe (PID: 3388)
- win64obf.exe (PID: 2772)
Checks supported languages
- CrystalCrypter2.exe (PID: 3388)
- cmd.exe (PID: 3692)
- powershell.exe (PID: 1788)
- cmd.exe (PID: 3472)
- powershell.exe (PID: 4064)
- WinRAR.exe (PID: 3172)
- win64obf.exe (PID: 2772)
- cmd.exe (PID: 992)
- cmd.exe (PID: 2348)
- cmd.exe (PID: 2072)
- 12.exe (PID: 1844)
- powershell.exe (PID: 2340)
- cmd.exe (PID: 924)
- cmd.exe (PID: 3468)
- win32dll.exe (PID: 2168)
Executable content was dropped or overwritten
- CrystalCrypter2.exe (PID: 3388)
- win64obf.exe (PID: 2772)
- WinRAR.exe (PID: 3172)
Drops a file with a compile date too recent
- CrystalCrypter2.exe (PID: 3388)
- win64obf.exe (PID: 2772)
- WinRAR.exe (PID: 3172)
Creates files in the user directory
- 12.exe (PID: 1844)
- win64obf.exe (PID: 2772)
Reads the cookies of Mozilla Firefox
- 12.exe (PID: 1844)
Reads Windows Product ID
- 12.exe (PID: 1844)
Reads Environment values
- 12.exe (PID: 1844)
Checks for external IP
- 12.exe (PID: 1844)
Searches for installed software
- 12.exe (PID: 1844)
INFO
Manual execution by user
- CrystalCrypter2.exe (PID: 1612)
- CrystalCrypter2.exe (PID: 3388)
Checks Windows Trust Settings
- powershell.exe (PID: 4064)
- powershell.exe (PID: 1788)
- powershell.exe (PID: 2340)
Reads settings of System Certificates
- powershell.exe (PID: 4064)
- powershell.exe (PID: 2340)
Checks supported languages
- schtasks.exe (PID: 984)
- timeout.exe (PID: 2488)
Reads the computer name
- schtasks.exe (PID: 984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(2168) win32dll.exe
C2 (1)ggho5t.duckdns.org
Ports (1)60671
Version0.5.7B
Autoruntrue
MutexWindows-DLL_0s0QnaPNG
CertificateMIIE8jCCAtqgAwIBAgIQAPtRUe35Ba2BQknB3nZQgzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNTMxMTQ0NTQ2WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAJPeAGnilCmBFX0TG4tnG+7PkUdJz/5qVqxHFTk+bbj+0Qi2p64FqRA7KQ+AppswCc9IabcTjeof...
Server_SignatureHQuG+mi0Oi1Vl9KZFfjd1D8A7usHxos8nh0FyMs0RsXDs0J+6Fbd0dAaWrRq9yg8IRX5uwIZNAW1tsUU1WyiEQIGHLk1Zjt93f1qp/GF435d3/kyfDctk/P/BWJYCvhJyDuPLlPkzVegp3V//SfjN4npu+4MDoQG+eG3bD3JKcPuErKBpaN7BOnXnkMSryDXGdkQ4wJLk+9BwNHXDIw/5QQd0UuwFwNv7t4xmRlz+klcPbZ+SC9zsCmG4du6pzf3ucMgnBLDAjUaA8rOhttAecKsjKvZgreW9u3CkZHDnSko...
AntiVMfalse
PasteBinnull
bdosfalse
BotnetYouTube
Aes_Keye25c9eefe2303a70a9bc899133e386df497c24dfae74b0c9c8b8545af545e6bb
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Install_Folder%AppData%
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | CrystalCrypter2/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:06:27 11:37:09 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
68
Monitored processes
19
Malicious processes
11
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 924 | "C:\Windows\System32\cmd.exe" /c schtasks /create /f /sc onlogon /rl highest /tn "win32dll" /tr '"C:\Users\admin\AppData\Roaming\win32dll.exe"' & exit | C:\Windows\System32\cmd.exe | win64obf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 984 | schtasks /create /f /sc onlogon /rl highest /tn "win32dll" /tr '"C:\Users\admin\AppData\Roaming\win32dll.exe"' | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | cmd /c start "" "C:\Users\admin\AppData\Local\Temp\Defender Smart Screen.exe" | C:\Windows\system32\cmd.exe | — | CrystalCrypter2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1612 | "C:\Users\admin\Desktop\CrystalCrypter2\CrystalCrypter2.exe" | C:\Users\admin\Desktop\CrystalCrypter2\CrystalCrypter2.exe | — | Explorer.EXE | |||||||||||
User: admin Company: CrystalCrypter Integrity Level: MEDIUM Description: CrystalCrypter Exit code: 3221226540 Version: 2,0,0,0 Modules
| |||||||||||||||
| 1788 | powershell -Command "Add-Type -AssemblyName System.Windows.Forms;[System.Windows.Forms.MessageBox]::Show('Unable to find VCCRuntime140.dll','Error','OK','Error')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
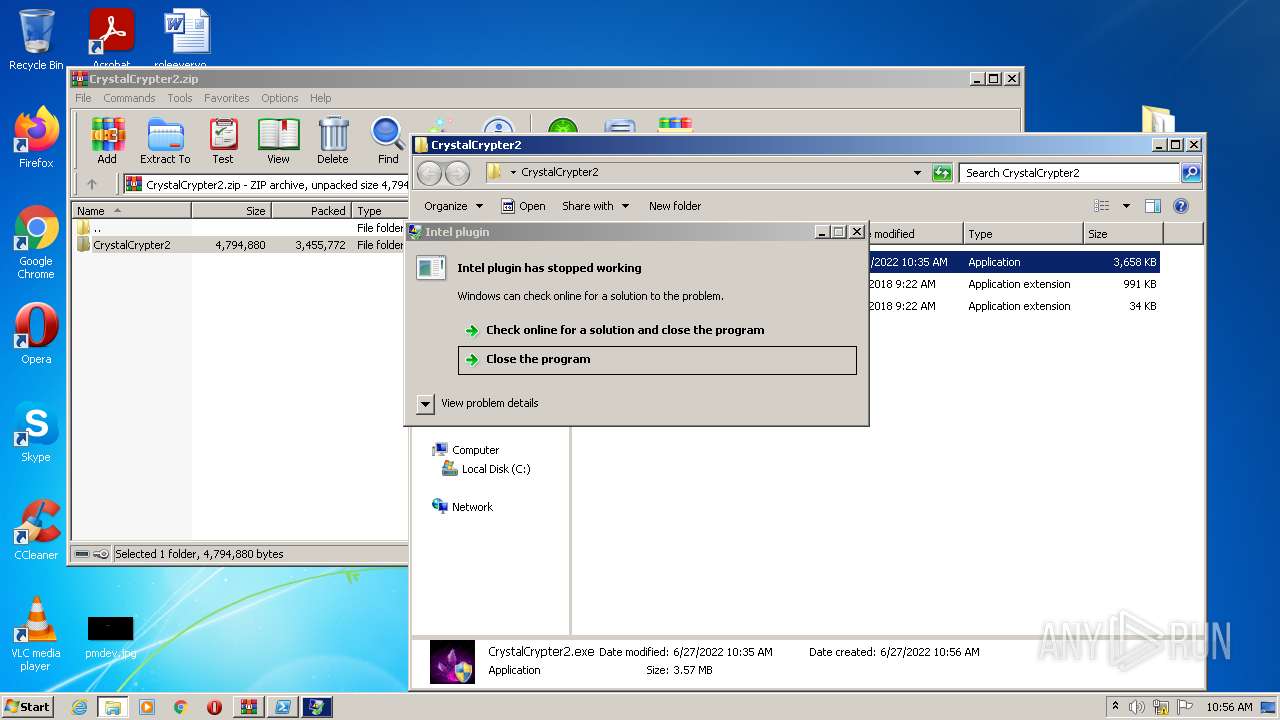
| 1844 | "C:\Users\admin\AppData\Local\Temp\12.exe" | C:\Users\admin\AppData\Local\Temp\12.exe | cmd.exe | ||||||||||||
User: admin Company: Intel plugin Integrity Level: HIGH Description: Intel plugin Exit code: 3762504530 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2072 | cmd /c start "" "C:\Users\admin\AppData\Local\Temp\win64obf.exe" | C:\Windows\system32\cmd.exe | — | CrystalCrypter2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\AppData\Roaming\win32dll.exe" | C:\Users\admin\AppData\Roaming\win32dll.exe | cmd.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: HIGH Description: Firefox Exit code: 0 Version: 101.0.1.8194 Modules
AsyncRat(PID) Process(2168) win32dll.exe C2 (1)ggho5t.duckdns.org Ports (1)60671 Version0.5.7B Autoruntrue MutexWindows-DLL_0s0QnaPNG CertificateMIIE8jCCAtqgAwIBAgIQAPtRUe35Ba2BQknB3nZQgzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNTMxMTQ0NTQ2WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAJPeAGnilCmBFX0TG4tnG+7PkUdJz/5qVqxHFTk+bbj+0Qi2p64FqRA7KQ+AppswCc9IabcTjeof... Server_SignatureHQuG+mi0Oi1Vl9KZFfjd1D8A7usHxos8nh0FyMs0RsXDs0J+6Fbd0dAaWrRq9yg8IRX5uwIZNAW1tsUU1WyiEQIGHLk1Zjt93f1qp/GF435d3/kyfDctk/P/BWJYCvhJyDuPLlPkzVegp3V//SfjN4npu+4MDoQG+eG3bD3JKcPuErKBpaN7BOnXnkMSryDXGdkQ4wJLk+9BwNHXDIw/5QQd0UuwFwNv7t4xmRlz+klcPbZ+SC9zsCmG4du6pzf3ucMgnBLDAjUaA8rOhttAecKsjKvZgreW9u3CkZHDnSko... AntiVMfalse PasteBinnull bdosfalse BotnetYouTube Aes_Keye25c9eefe2303a70a9bc899133e386df497c24dfae74b0c9c8b8545af545e6bb Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 Install_Folder%AppData% | |||||||||||||||
| 2340 | powershell -Command "Add-MpPreference -ExclusionExtension @('exe','dll') -Force" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2348 | cmd /c start "" "C:\Users\admin\AppData\Local\Temp\12.exe" | C:\Windows\system32\cmd.exe | — | CrystalCrypter2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
10 867
Read events
10 765
Write events
102
Delete events
0
Modification events
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\CrystalCrypter2.zip | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
7
Suspicious files
7
Text files
11
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3172.44475\CrystalCrypter2\CrystalCrypter2.exe | executable | |
MD5:— | SHA256:— | |||
| 3388 | CrystalCrypter2.exe | C:\Users\admin\AppData\Local\Temp\12.exe | executable | |
MD5:— | SHA256:— | |||
| 3388 | CrystalCrypter2.exe | C:\Users\admin\AppData\Local\Temp\win64obf.exe | executable | |
MD5:— | SHA256:— | |||
| 3388 | CrystalCrypter2.exe | C:\Users\admin\AppData\Local\Temp\Defender Smart Screen.exe | executable | |
MD5:— | SHA256:— | |||
| 1844 | 12.exe | C:\Users\admin\AppData\Roaming\NPFLPTyNFPPNRNLywHNR1F8BFBFF000506E3C4BA364779\791F8BFBFF000506E3C4BA3647NPFLPTyNFPPNRNLywHNR\Files\decisionhp.jpg | image | |
MD5:— | SHA256:— | |||
| 1844 | 12.exe | C:\Users\admin\AppData\Roaming\NPFLPTyNFPPNRNLywHNR1F8BFBFF000506E3C4BA364779\791F8BFBFF000506E3C4BA3647NPFLPTyNFPPNRNLywHNR\Files\littleface.jpg | image | |
MD5:— | SHA256:— | |||
| 1844 | 12.exe | C:\Users\admin\AppData\Roaming\NPFLPTyNFPPNRNLywHNR1F8BFBFF000506E3C4BA364779\791F8BFBFF000506E3C4BA3647NPFLPTyNFPPNRNLywHNR\Files\pmdev.jpg | image | |
MD5:— | SHA256:— | |||
| 1844 | 12.exe | C:\Users\admin\AppData\Roaming\NPFLPTyNFPPNRNLywHNR1F8BFBFF000506E3C4BA364779\791F8BFBFF000506E3C4BA3647NPFLPTyNFPPNRNLywHNR\Files\writtenkeep.jpg | image | |
MD5:— | SHA256:— | |||
| 3172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3172.44475\CrystalCrypter2\dnlib.dll | executable | |
MD5:3E6C695A0396FB1933B2C969ADAE5E32 | SHA256:BD0C0B52DBBDFB47F3A50F5459659F0176F1CD3C1FFC7780E93AFC40B254982B | |||
| 1844 | 12.exe | C:\Users\admin\AppData\Roaming\NPFLPTyNFPPNRNLywHNR1F8BFBFF000506E3C4BA364779\791F8BFBFF000506E3C4BA3647NPFLPTyNFPPNRNLywHNR\Processes.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
4
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1844 | 12.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | xml | 441 b | malicious |
1844 | 12.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | xml | 441 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1844 | 12.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2168 | win32dll.exe | 156.96.151.132:60671 | ggho5t.duckdns.org | XNS Technology Group Inc. | US | malicious |
1844 | 12.exe | 3.220.57.224:443 | api.ipify.org | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
api.ipify.org |
| shared |
ip-api.com |
| malicious |
ggho5t.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1844 | 12.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
1844 | 12.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1844 | 12.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
1844 | 12.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2168 | win32dll.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 14 |