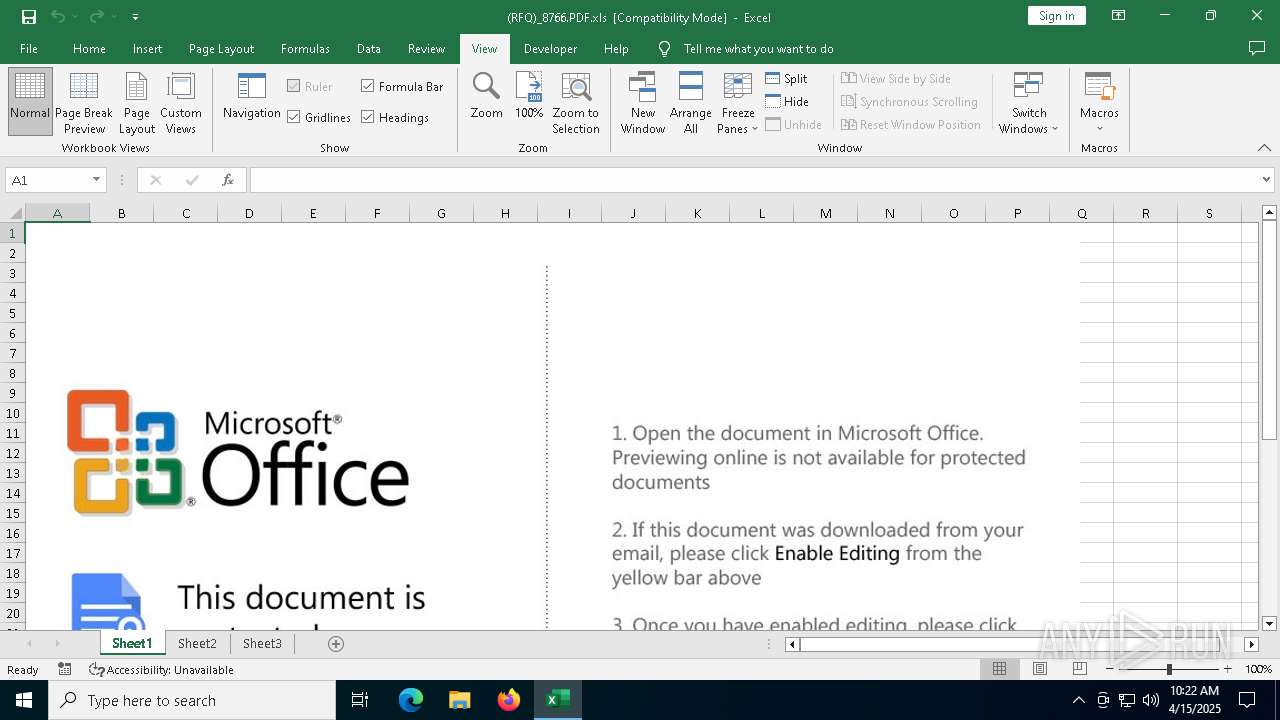
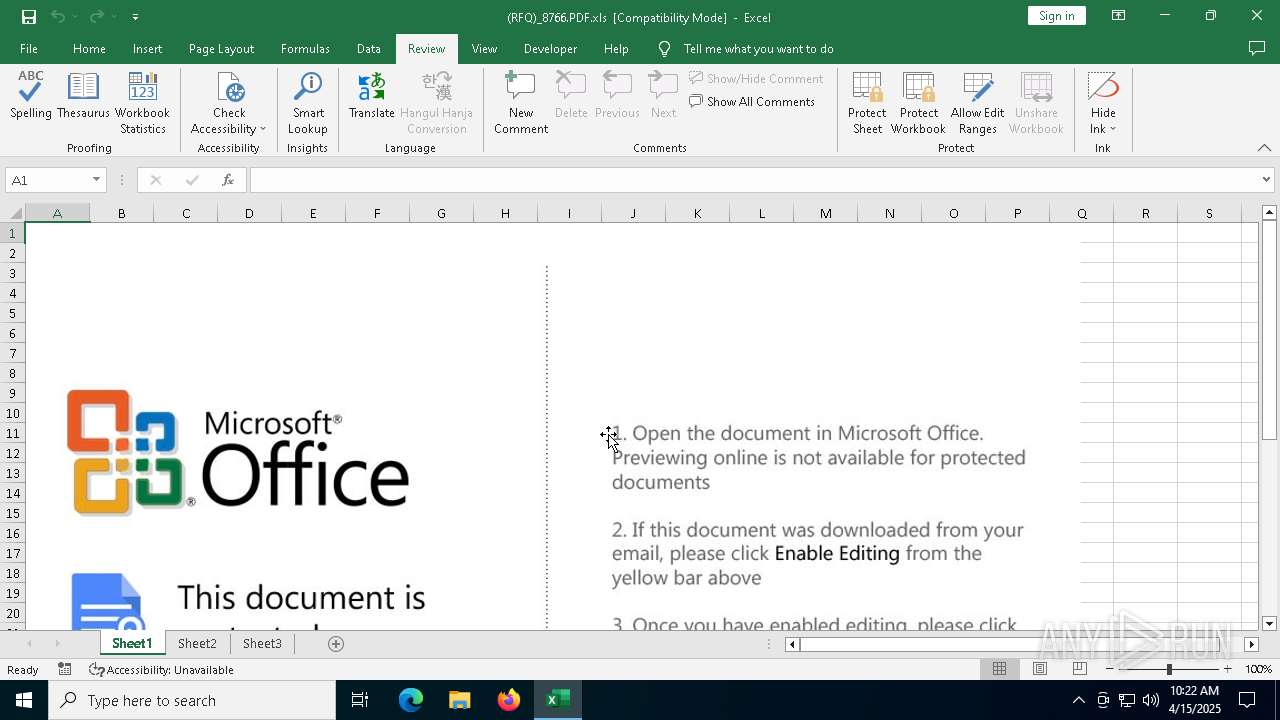
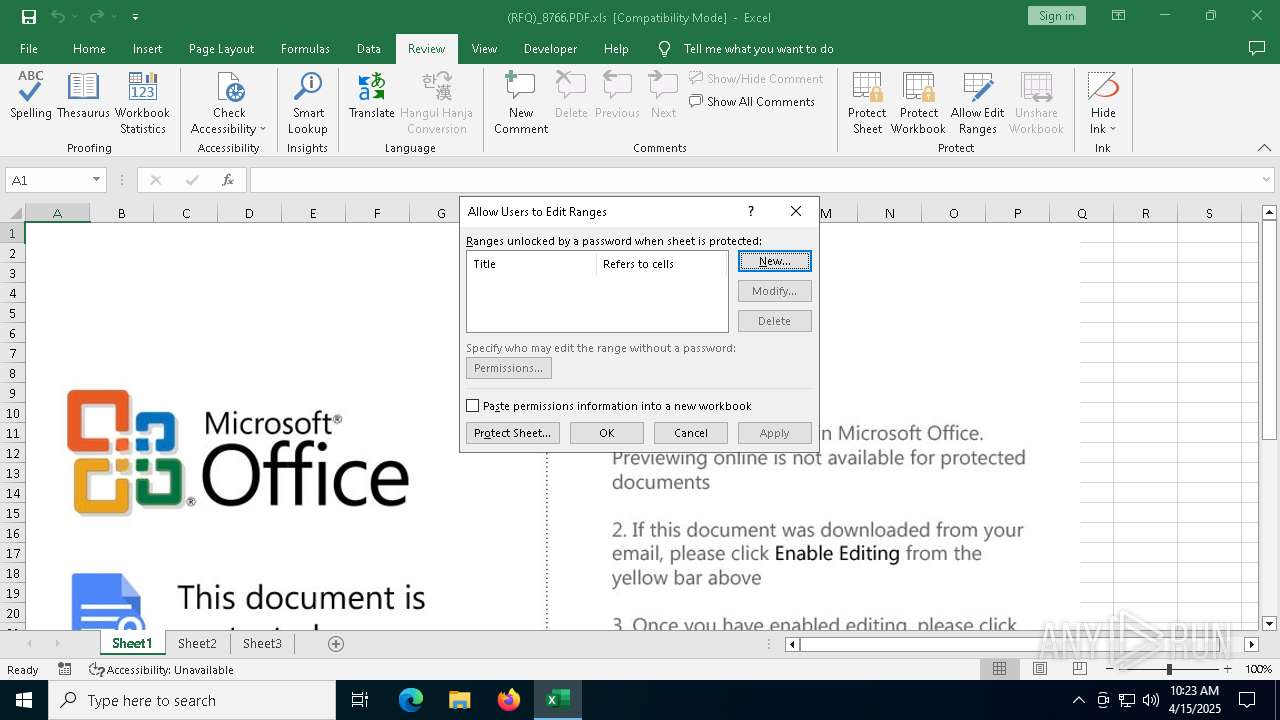
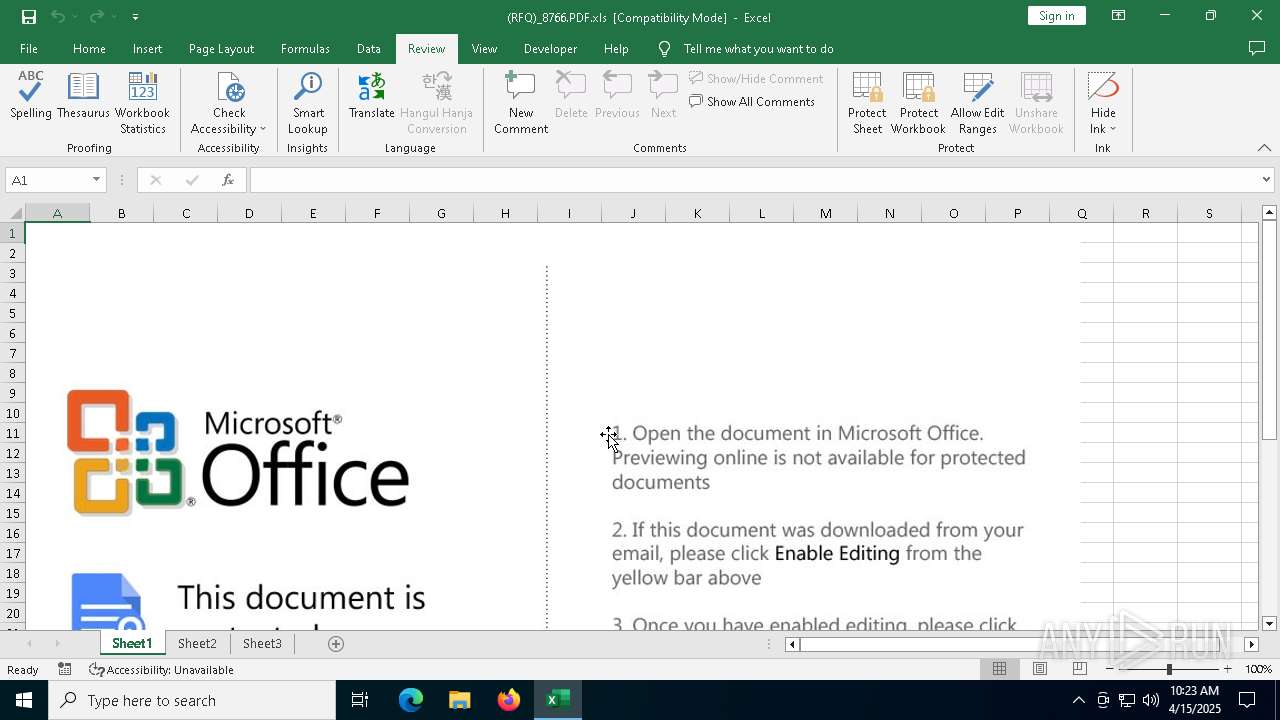
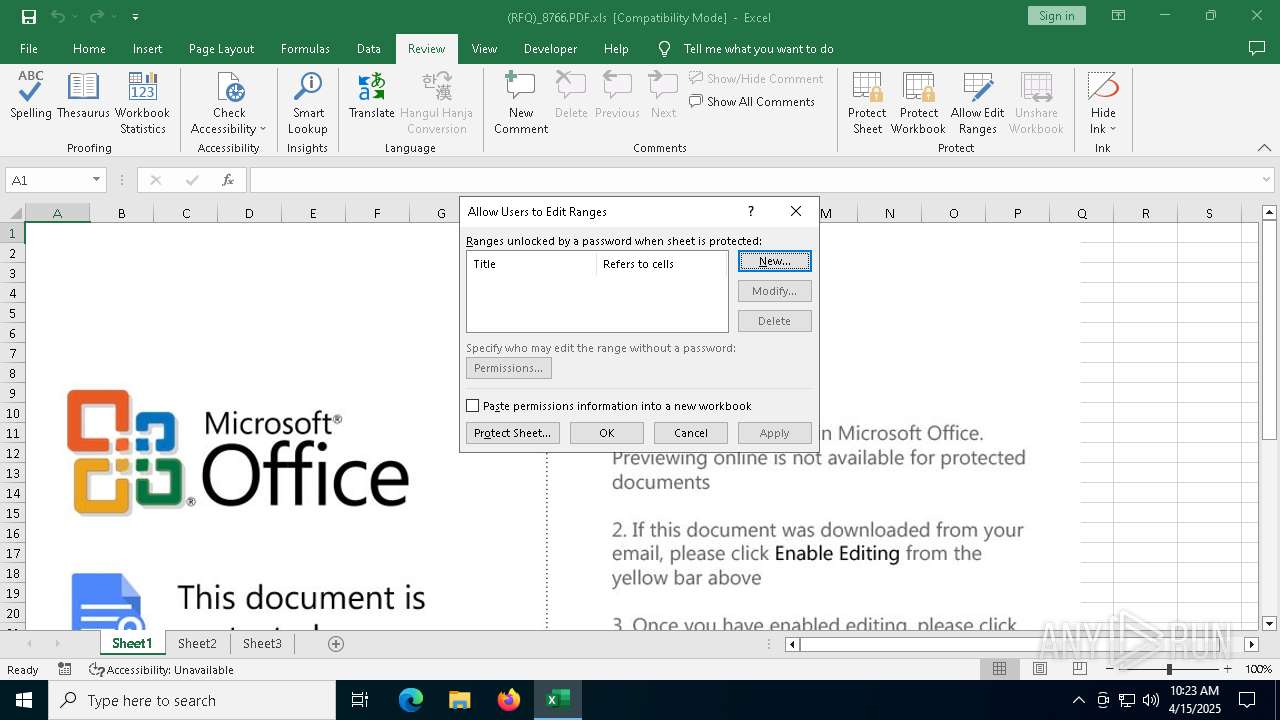
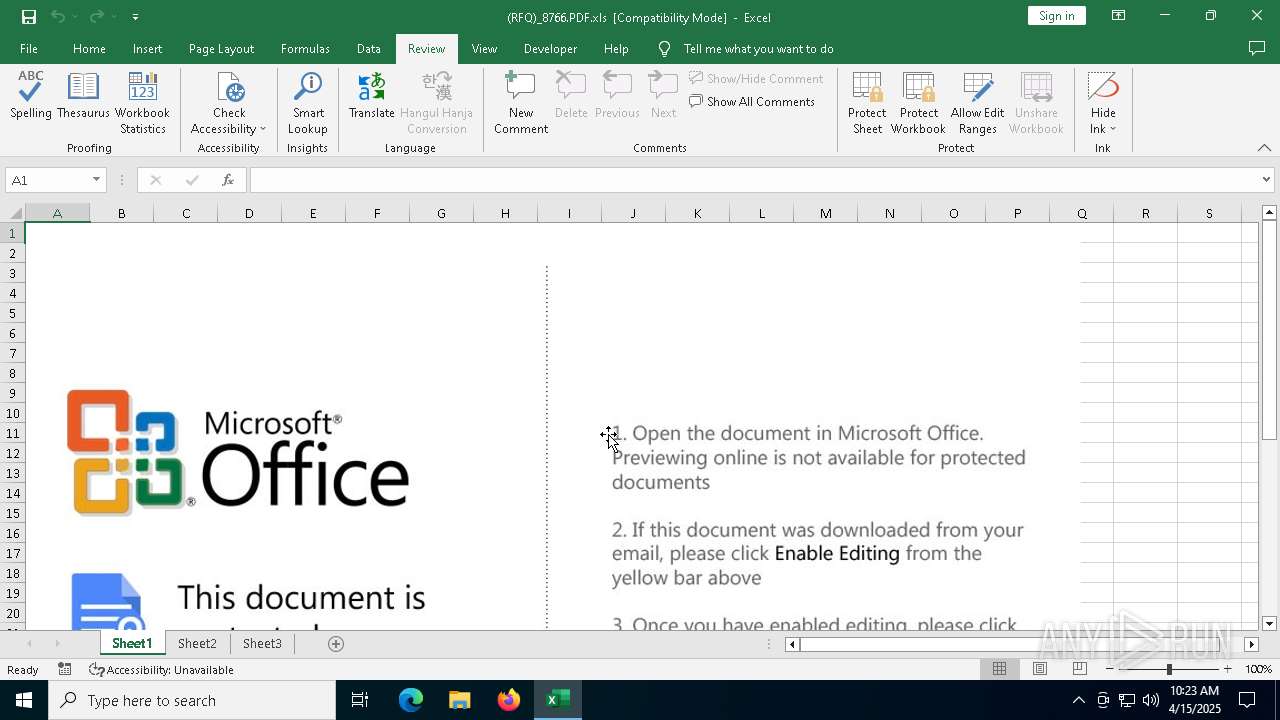
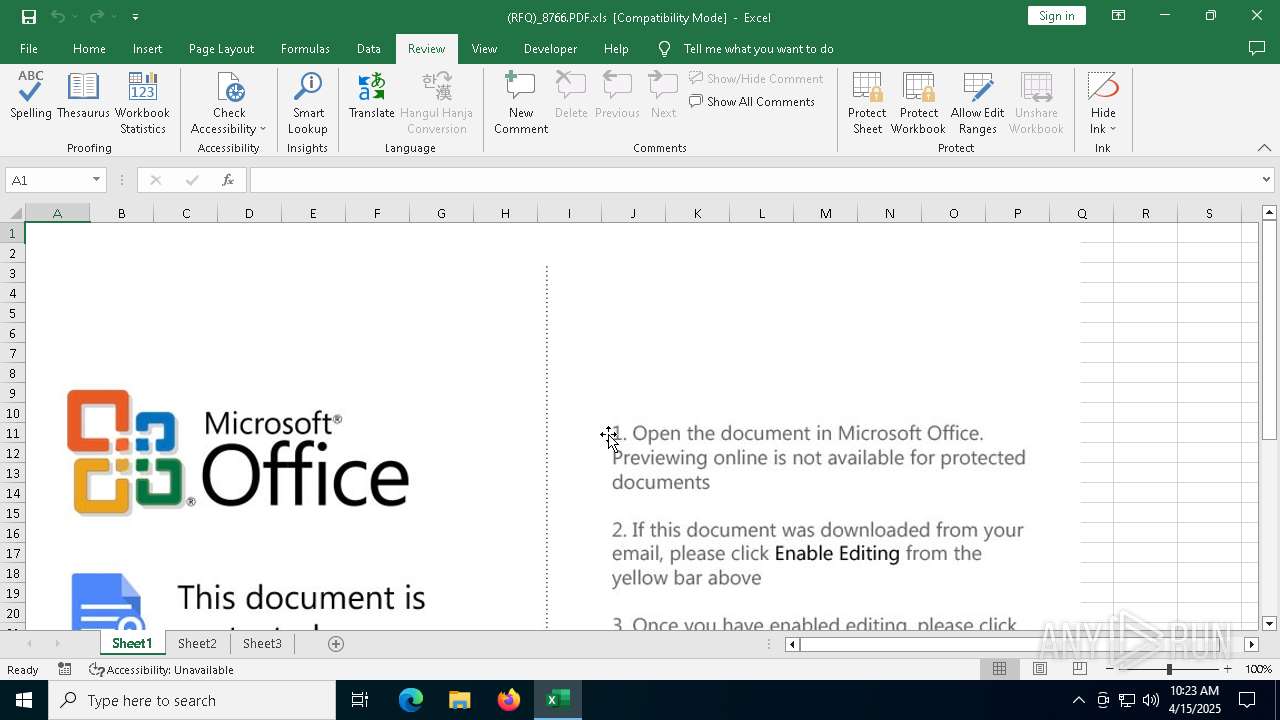
| File name: | (RFQ)_8766.PDF.xls |
| Full analysis: | https://app.any.run/tasks/6080ac5c-9e28-49f1-a6e1-67a82c29fb00 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | April 15, 2025, 10:21:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat Sep 16 00:00:00 2006, Last Saved Time/Date: Mon Apr 14 07:57:51 2025, Security: 0 |
| MD5: | 3EDA5D1E23BC7FC725A892FE25AAFAF0 |
| SHA1: | 8564865999A3BFBC27809A39DB8437A7F198B494 |
| SHA256: | 79316B00E69FE834C46C710106DA165C80304671ECC093DACAE878ED58415D35 |
| SSDEEP: | 1536:SgYPDPijEK1bJmzZ4Gfnbg5cF5Z94dv6c353RZfxM6U:T2DPiXbJS4Knbg5cXqvbFfxM6U |
MALICIOUS
Sends HTTP request (SCRIPT)
- EXCEL.EXE (PID: 7320)
Opens an HTTP connection (SCRIPT)
- EXCEL.EXE (PID: 7320)
Creates a new folder (SCRIPT)
- EXCEL.EXE (PID: 7320)
Creates internet connection object (SCRIPT)
- EXCEL.EXE (PID: 7320)
Checks whether a specified folder exists (SCRIPT)
- EXCEL.EXE (PID: 7320)
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 7320)
Starts POWERSHELL.EXE for commands execution
- EXCEL.EXE (PID: 7320)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 536)
Changes powershell execution policy (RemoteSigned)
- EXCEL.EXE (PID: 7320)
Unusual execution from MS Office
- EXCEL.EXE (PID: 7320)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 6872)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 6872)
AGENTTESLA has been detected (SURICATA)
- RegAsm.exe (PID: 6872)
AGENTTESLA has been detected (YARA)
- RegAsm.exe (PID: 6872)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- EXCEL.EXE (PID: 7320)
Process requests binary or script from the Internet
- EXCEL.EXE (PID: 7320)
Connects to the server without a host name
- EXCEL.EXE (PID: 7320)
- GHAGHASGHASVZvZJzSA.exe (PID: 4736)
Writes binary data to a Stream object (SCRIPT)
- EXCEL.EXE (PID: 7320)
Access the System.Security .NET namespace (SCRIPT)
- EXCEL.EXE (PID: 7320)
The process executes Powershell scripts
- EXCEL.EXE (PID: 7320)
The process bypasses the loading of PowerShell profile settings
- EXCEL.EXE (PID: 7320)
Executable content was dropped or overwritten
- powershell.exe (PID: 536)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 536)
Runs shell command (SCRIPT)
- EXCEL.EXE (PID: 7320)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 536)
Checks for external IP
- svchost.exe (PID: 2196)
- RegAsm.exe (PID: 6872)
Connects to FTP
- RegAsm.exe (PID: 6872)
Connects to unusual port
- RegAsm.exe (PID: 6872)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 7740)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 536)
The executable file from the user directory is run by the Powershell process
- GHAGHASGHASVZvZJzSA.exe (PID: 4736)
Checks supported languages
- GHAGHASGHASVZvZJzSA.exe (PID: 4736)
- RegAsm.exe (PID: 6872)
Reads the computer name
- GHAGHASGHASVZvZJzSA.exe (PID: 4736)
- RegAsm.exe (PID: 6872)
Reads the machine GUID from the registry
- GHAGHASGHASVZvZJzSA.exe (PID: 4736)
- RegAsm.exe (PID: 6872)
Disables trace logs
- GHAGHASGHASVZvZJzSA.exe (PID: 4736)
- RegAsm.exe (PID: 6872)
Checks proxy server information
- GHAGHASGHASVZvZJzSA.exe (PID: 4736)
- RegAsm.exe (PID: 6872)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 7740)
Reads the software policy settings
- slui.exe (PID: 7484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | - |
|---|---|
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2006:09:16 00:00:00 |
| ModifyDate: | 2025:04:14 07:57:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
145
Monitored processes
11
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy RemoteSigned -File "C:\\Temp\\Y1.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | GHAGHASGHASVZvZJzSA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4736 | "C:\Users\admin\AppData\Local\Temp\GHAGHASGHASVZvZJzSA.exe" | C:\Users\admin\AppData\Local\Temp\GHAGHASGHASVZvZJzSA.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ASGJSDJKJ232 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6872 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | GHAGHASGHASVZvZJzSA.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7320 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\AppData\Local\Temp\(RFQ)_8766.PDF.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7452 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7484 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7720 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 293
Read events
13 992
Write events
275
Delete events
26
Modification events
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\7320 |
| Operation: | write | Name: | 0 |
Value: 0B0E10ABC19A3D3E35BF408E2B7075FD301508230046C2A4AFBE83BEEBED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119839D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (7320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
14
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7320 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:F96F257C668ABC455A6F0A29F3F83AD2 | SHA256:C551F9301A6C1CAFD384D23CAC0C351374674A91951F6D74A853E35AEA3E6273 | |||
| 7320 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:8F262A930527AE9D8ED59AB687A6A635 | SHA256:7EE7CAED54B6B2C7A7E94A75C33C983AC56462826D27BD5F54DF8421BB500E15 | |||
| 7320 | EXCEL.EXE | C:\Temp\Y1.ps1 | text | |
MD5:CA5F5BCC856882BD71D50C49CF2DAAA6 | SHA256:20177E26AF9A2A799013928A3D1D1F3F45599751B91AA29F09AF23DB5E7743F0 | |||
| 7320 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\maCRO[1].ps1 | text | |
MD5:CA5F5BCC856882BD71D50C49CF2DAAA6 | SHA256:20177E26AF9A2A799013928A3D1D1F3F45599751B91AA29F09AF23DB5E7743F0 | |||
| 536 | powershell.exe | C:\Users\admin\AppData\Local\Temp\GHAGHASGHASVZvZJzSA.exe | executable | |
MD5:4537EFCFD45F01F709FBA658CAAE27B5 | SHA256:4083959EF665059682D50C094526CB5B6CF39AAF339DC40219AEC105F3A90F3C | |||
| 7320 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:9B62ECDB6258930AE0816134467B1272 | SHA256:BC06644A17370E6FC4D720AA25DC4B9EAA384E662D53937C1BD3034C9DDE890E | |||
| 7320 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | xml | |
MD5:13AF026BB17E87B1A24C00E8295447B0 | SHA256:4695B860F6568E9EDDC220E4C80C848D5B6BE780C9A4A31FAD4D878E098FF8DB | |||
| 7320 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\SmartLookupCache\dictionary_words_bloom_filter.data | binary | |
MD5:A4AF96BCD3EE55F0CB99B37C806A82A5 | SHA256:1BE6D822C31EDC308903E04B986F13388B216DB44019E2BCC3C060284B480BA6 | |||
| 536 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4fog1cng.suv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7320 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2NABF3GHMMOOI2262Q4F.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
24
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7320 | EXCEL.EXE | GET | 200 | 176.65.134.79:80 | http://176.65.134.79/hosting/maCRO.ps1 | unknown | — | — | unknown |
2104 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4736 | GHAGHASGHASVZvZJzSA.exe | GET | 200 | 176.65.134.79:80 | http://176.65.134.79/hosting/NEWDEVVV.txt | unknown | — | — | unknown |
7320 | EXCEL.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2600 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2600 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6872 | RegAsm.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7320 | EXCEL.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7320 | EXCEL.EXE | 52.123.130.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7320 | EXCEL.EXE | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 29 |
7320 | EXCEL.EXE | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
6872 | RegAsm.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
6872 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6872 | RegAsm.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
6872 | RegAsm.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
6872 | RegAsm.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
6872 | RegAsm.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |