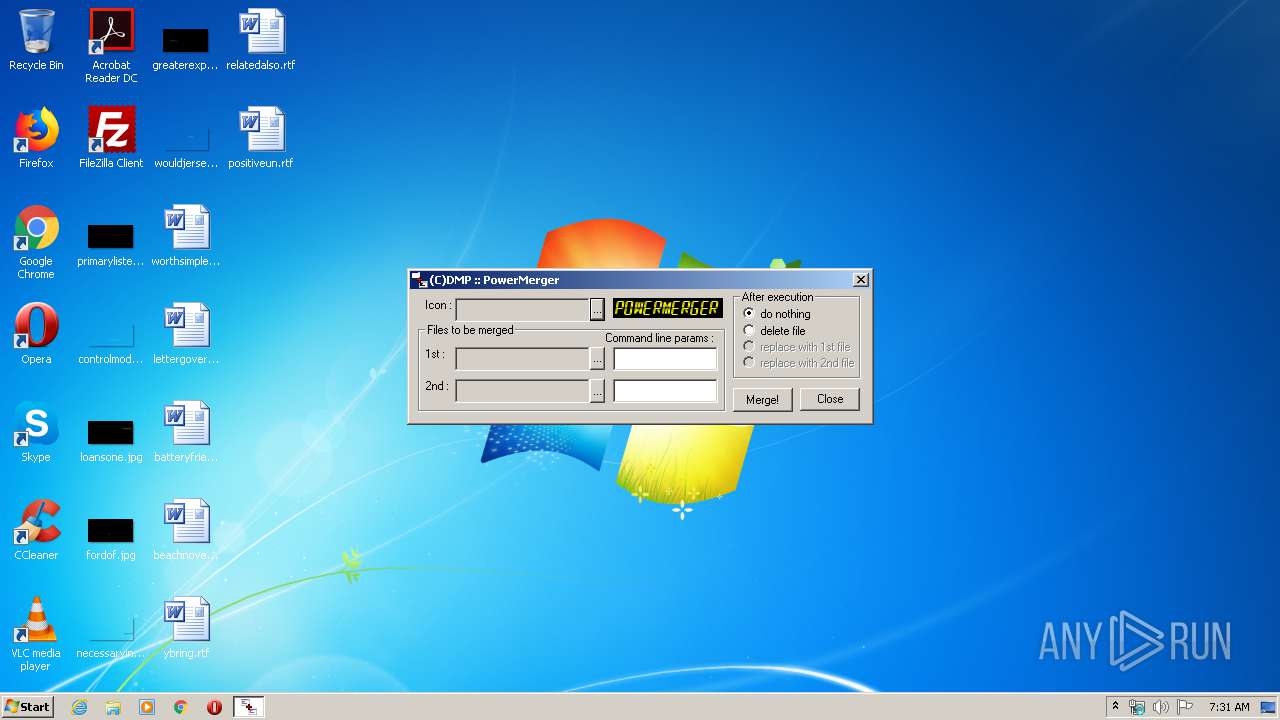
| File name: | PowerMerger.exe |
| Full analysis: | https://app.any.run/tasks/5b71238e-c554-48d5-83b5-aa86cbab4219 |
| Verdict: | Malicious activity |
| Threats: | Gh0st RAT is a malware with advanced trojan functionality that enables attackers to establish full control over the victim’s system. The spying capabilities of Gh0st RAT made it a go-to tool for numerous criminal groups in high-profile attacks against government and corporate organizations. The most common vector of attack involving this malware begins with spam and phishing emails. |
| Analysis date: | May 20, 2020, 06:31:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B57405AF7082A6090475E965033543A4 |
| SHA1: | 9AE1F3BEEEE62583BEC3048C40CE5CD9F3941BC7 |
| SHA256: | 792A8779E332C84956AD34F7C2583142789989B3930DE6AA70F447E3846EFB81 |
| SSDEEP: | 6144:8Za3q8pUBQFClrnA48il6fskiHQ856V96k+UjXt6AZ7ZcWSM8:0N8mC4lrd6fsdH06LUp6A7ZcWSd |
MALICIOUS
Application was dropped or rewritten from another process
- server.exe (PID: 3624)
- incgzwjvl.exe (PID: 3328)
- PowerMerger.exe (PID: 2536)
Changes the autorun value in the registry
- server.exe (PID: 3624)
Loads dropped or rewritten executable
- userinit.exe (PID: 3552)
Connects to CnC server
- userinit.exe (PID: 3552)
GH0ST was detected
- userinit.exe (PID: 3552)
SUSPICIOUS
Executable content was dropped or overwritten
- PowerMerger.exe (PID: 2612)
- incgzwjvl.exe (PID: 3328)
- server.exe (PID: 3624)
- ~__UNINST.EXE (PID: 480)
Starts itself from another location
- PowerMerger.exe (PID: 2612)
Creates files in the Windows directory
- server.exe (PID: 3624)
Creates or modifies windows services
- userinit.exe (PID: 3552)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2001:11:10 14:23:24+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 8192 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x205f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 10-Nov-2001 13:23:24 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 10-Nov-2001 13:23:24 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000013F8 | 0x00002000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 4.32814 |
.rdata | 0x00003000 | 0x0000069A | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.37274 |
.data | 0x00004000 | 0x00000400 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.44895 |
.rsrc | 0x00005000 | 0x00000502 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.0486 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 2.51737 | 744 | UNKNOWN | Italian - Italy | RT_ICON |
2 | 2.48756 | 296 | UNKNOWN | Italian - Italy | RT_ICON |
101 | 2.37086 | 34 | UNKNOWN | Italian - Italy | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
MFC42.DLL |
MSVCRT.dll |
SHELL32.dll |
USER32.dll |
Total processes
48
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Users\admin\AppData\Local\Temp\~__UNINST.EXE" C:\Users\admin\AppData\Local\Temp\PowerMerger.exe | C:\Users\admin\AppData\Local\Temp\~__UNINST.EXE | PowerMerger.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2536 | "C:\Users\admin\AppData\Local\Temp\PowerMerger.exe" | C:\Users\admin\AppData\Local\Temp\PowerMerger.exe | — | ~__UNINST.EXE | |||||||||||
User: admin Company: (C)DMP Integrity Level: HIGH Description: Merger for executables and document files Exit code: 0 Version: 1, 2, 0, 0 Modules
| |||||||||||||||
| 2612 | "C:\Users\admin\AppData\Local\Temp\PowerMerger.exe" | C:\Users\admin\AppData\Local\Temp\PowerMerger.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2744 | "C:\Users\admin\AppData\Local\Temp\~__UNINST.EXE" C:\Users\admin\AppData\Local\Temp\PowerMerger.exe | C:\Users\admin\AppData\Local\Temp\~__UNINST.EXE | — | PowerMerger.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3328 | C:\Windows\system32\incgzwjvl.exe | C:\Windows\system32\incgzwjvl.exe | server.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: install Exit code: 0 Version: 3, 0, 0, 0 Modules
| |||||||||||||||
| 3552 | userinit.exe | C:\Windows\system32\userinit.exe | incgzwjvl.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Userinit Logon Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\AppData\Local\Temp\server.exe" ADN | C:\Users\admin\AppData\Local\Temp\server.exe | ~__UNINST.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: install Exit code: 0 Version: 3, 0, 0, 0 Modules
| |||||||||||||||
Total events
1 147
Read events
1 122
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2612) PowerMerger.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2612) PowerMerger.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (480) ~__UNINST.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (480) ~__UNINST.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3624) server.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{hwfuylj2-d3bm-7n84-ndj2-1vx72bpji2ey} |
| Operation: | write | Name: | stubpath |
Value: C:\Windows\system32\incgzwjvl.exe | |||
| (PID) Process: | (3552) userinit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\PCRatStact |
| Operation: | write | Name: | Type |
Value: 288 | |||
| (PID) Process: | (2536) PowerMerger.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRULegacy |
| Operation: | write | Name: | MRUListEx |
Value: FFFFFFFF | |||
| (PID) Process: | (2536) PowerMerger.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2536) PowerMerger.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000001000000000000000A00000007000000090000000800000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2536) PowerMerger.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\2 |
| Operation: | write | Name: | MRUListEx |
Value: 0000000001000000FFFFFFFF | |||
Executable files
5
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 480 | ~__UNINST.EXE | C:\Users\admin\AppData\Local\Temp\~pmThis.tmp | — | |
MD5:— | SHA256:— | |||
| 3328 | incgzwjvl.exe | C:\Users\admin\AppData\Local\Temp\11040781_res.tmp | — | |
MD5:— | SHA256:— | |||
| 2612 | PowerMerger.exe | C:\Users\admin\AppData\Local\Temp\~__UNINST.EXE | executable | |
MD5:— | SHA256:— | |||
| 480 | ~__UNINST.EXE | C:\Users\admin\AppData\Local\Temp\PowerMerger.exe | executable | |
MD5:ECF6ED44AD11BC65D5AAB8E6EC7D7EB0 | SHA256:627537C298D835603E6552C97D1F29EF53A99A3F5096CE419D29D459A77544CD | |||
| 3328 | incgzwjvl.exe | C:\Users\admin\AppData\Local\Temp\11040781_lang.dll | executable | |
MD5:— | SHA256:— | |||
| 480 | ~__UNINST.EXE | C:\Users\admin\AppData\Local\Temp\server.exe | executable | |
MD5:— | SHA256:— | |||
| 3624 | server.exe | C:\Windows\system32\incgzwjvl.exe_lang.ini | text | |
MD5:— | SHA256:— | |||
| 3624 | server.exe | C:\Windows\system32\incgzwjvl.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
12
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3552 | userinit.exe | 121.166.1.191:80 | — | Korea Telecom | KR | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3552 | userinit.exe | A Network Trojan was detected | ET TROJAN Backdoor family PCRat/Gh0st CnC traffic |
3552 | userinit.exe | A Network Trojan was detected | ET TROJAN Backdoor family PCRat/Gh0st CnC traffic (OUTBOUND) 102 |
3552 | userinit.exe | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor family PCRat/Gh0st CnC (OUTBOUND <256) |
3552 | userinit.exe | A Network Trojan was detected | MALWARE [PTsecurity] PCRat/Gh0st.XORed Request (Bronze Union APT) |
3552 | userinit.exe | A Network Trojan was detected | ET TROJAN Backdoor family PCRat/Gh0st CnC traffic |
3552 | userinit.exe | A Network Trojan was detected | ET TROJAN Backdoor family PCRat/Gh0st CnC traffic (OUTBOUND) 102 |
3552 | userinit.exe | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor family PCRat/Gh0st CnC (OUTBOUND <256) |
3552 | userinit.exe | A Network Trojan was detected | MALWARE [PTsecurity] PCRat/Gh0st.XORed Request (Bronze Union APT) |
3552 | userinit.exe | A Network Trojan was detected | ET TROJAN Backdoor family PCRat/Gh0st CnC traffic |
3552 | userinit.exe | A Network Trojan was detected | ET TROJAN Backdoor family PCRat/Gh0st CnC traffic (OUTBOUND) 102 |
Process | Message |
|---|---|
server.exe | PCRatStact |
server.exe | µ½ACtiveX °²×° |
server.exe | ReleaseResource³É¹¦ |
server.exe | дÈëiniÎļþ |
server.exe | 0vAC8Z8= |
server.exe | ACtiveX °²×°Íê±Ï |
server.exe | C:\Windows\system32\incgzwjvl.exe_lang.ini |
server.exe | {hwfuylj2-d3bm-7n84-ndj2-1vx72bpji2ey} |
server.exe | icon=0 |
incgzwjvl.exe | дÈëÔËÐÐ lpConfigString |