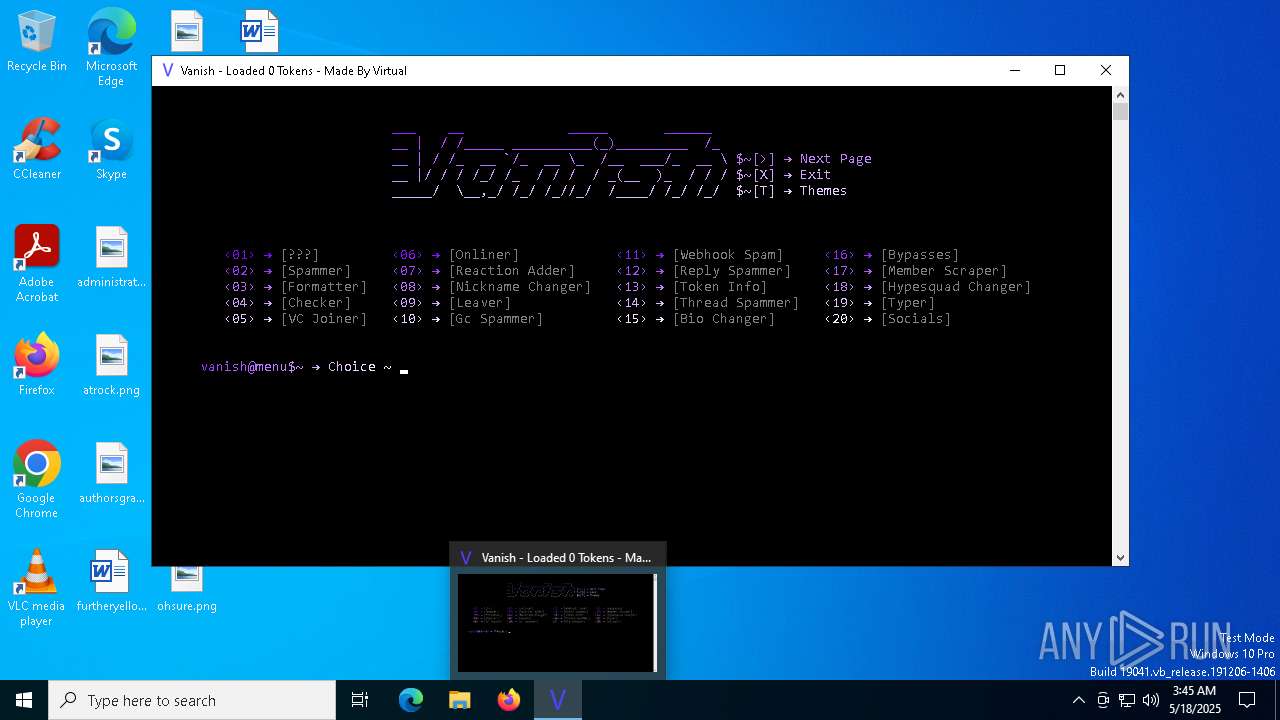
| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/d3e2f801-ef92-4abf-8df0-baa03949b807 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | May 18, 2025, 03:45:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 19 sections |
| MD5: | 223EE27B74181E9423021D24282462BF |
| SHA1: | 9A8346694010DE94F01177ED5F83CA07B5A72815 |
| SHA256: | 78D49B47144E7B27844D73F1502EB84134190ED4170C2176DB0AFC012D2E00D3 |
| SSDEEP: | 49152:QpCsGmAemeqmezK0X0E5OGeDTnidZ9JCDb:7h5OTnidZ9JCDb |
MALICIOUS
QUASAR mutex has been found
- main.exe (PID: 6768)
TROX has been detected
- vanish.exe (PID: 5376)
SUSPICIOUS
Reads security settings of Internet Explorer
- main.exe (PID: 6768)
Executable content was dropped or overwritten
- main.exe (PID: 6768)
- vanish.exe (PID: 5376)
Process drops python dynamic module
- vanish.exe (PID: 5376)
Process drops legitimate windows executable
- vanish.exe (PID: 5376)
The process drops C-runtime libraries
- vanish.exe (PID: 5376)
Reads the date of Windows installation
- main.exe (PID: 6768)
Loads Python modules
- vanish.exe (PID: 4920)
Starts CMD.EXE for commands execution
- vanish.exe (PID: 4920)
INFO
Reads the machine GUID from the registry
- main.exe (PID: 6768)
Creates files or folders in the user directory
- main.exe (PID: 6768)
Reads the computer name
- main.exe (PID: 6768)
- vanish.exe (PID: 4920)
Checks proxy server information
- main.exe (PID: 6768)
- vanish.exe (PID: 4920)
Reads the software policy settings
- main.exe (PID: 6768)
- slui.exe (PID: 1072)
Process checks computer location settings
- main.exe (PID: 6768)
Checks supported languages
- main.exe (PID: 6768)
- vanish.exe (PID: 5376)
- vanish.exe (PID: 4920)
Create files in a temporary directory
- main.exe (PID: 6768)
- vanish.exe (PID: 5376)
- vanish.exe (PID: 4920)
Checks operating system version
- vanish.exe (PID: 4920)
The sample compiled with english language support
- vanish.exe (PID: 5376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:18 03:42:56+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.36 |
| CodeSize: | 750080 |
| InitializedDataSize: | 952320 |
| UninitializedDataSize: | 4096 |
| EntryPoint: | 0x14e0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
140
Monitored processes
14
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | C:\WINDOWS\system32\cmd.exe /c title Vanish - Loaded 0 Tokens - Made By Virtual | C:\Windows\System32\cmd.exe | — | vanish.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | C:\WINDOWS\system32\cmd.exe /c title Vanish - GC Spammer | C:\Windows\System32\cmd.exe | — | vanish.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Users\admin\AppData\Local\Temp\vanish.exe" | C:\Users\admin\AppData\Local\Temp\onefile_5376_133920135176290379\vanish.exe | vanish.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5376 | "C:\Users\admin\AppData\Local\Temp\vanish.exe" | C:\Users\admin\AppData\Local\Temp\vanish.exe | main.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5512 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | vanish.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 283
Read events
5 280
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6768) main.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6768) main.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6768) main.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
39
Suspicious files
603
Text files
8
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5376 | vanish.exe | C:\Users\admin\AppData\Local\Temp\onefile_5376_133920135176290379\vanish.exe | — | |
MD5:— | SHA256:— | |||
| 6768 | main.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:37AD72E014C24333C5F7AEF5C1B2AC5B | SHA256:9CFDD48E41730A288854520947614FB6299A8C4C03ECA8223742D87CC8A4D31A | |||
| 5376 | vanish.exe | C:\Users\admin\AppData\Local\Temp\onefile_5376_133920135176290379\_cffi_backend.pyd | executable | |
MD5:FDE9A1D6590026A13E81712CD2F23522 | SHA256:16ECCC4BAF6CF4AB72ACD53C72A1F2B04D952E07E385E9050A933E78074A7D5B | |||
| 6768 | main.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:E456396997C09B1A6558EC24AAACCD27 | SHA256:B197F0E7010A8F55BC45A0A3C0A8169849540C80912ADBF72DAAB58F4003594E | |||
| 6768 | main.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:DD264EA6AC7C7362C830CEACE6D7033C | SHA256:6FBA003A5155BE506F7529CB25F491BA8AEB0B6F2AD302E12AACCB51D1DCFD83 | |||
| 6768 | main.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\vanish[1].exe | executable | |
MD5:D881AD827C43A30707E52D1CC06CB67C | SHA256:C917F3782D0ACB5332D3C1131B9DF4785CD18B7CE6867EEB5637980846663CE6 | |||
| 6768 | main.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:4C4DF0255086DFC863C28374B642677B | SHA256:4BDA55405F953DA6C7F5A10806CCE2E4531C0ED5D1A31B80692163AC9976A313 | |||
| 6768 | main.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D9CA54E0FA212456E1DB00704A97658E | binary | |
MD5:4663E513A7EF51F10A6DBD9FA1482B47 | SHA256:CCE6DE6B35599FAEA222A648295FA46EDD68B3ABFE2CACFC363141D5B2AE246A | |||
| 6768 | main.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:9E5F1DF28C9064E2E73198AD7E98B197 | SHA256:AA8FFDB539E9F331784341B0F81283C2AE251CBE574A473EAA4DE279D744777A | |||
| 6768 | main.exe | C:\Users\admin\AppData\Local\Temp\vanish.exe | executable | |
MD5:D881AD827C43A30707E52D1CC06CB67C | SHA256:C917F3782D0ACB5332D3C1131B9DF4785CD18B7CE6867EEB5637980846663CE6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
25
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6768 | main.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
6768 | main.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6768 | main.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.24.231.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6768 | main.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
6768 | main.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6768 | main.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
6768 | main.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
6768 | main.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
6768 | main.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |