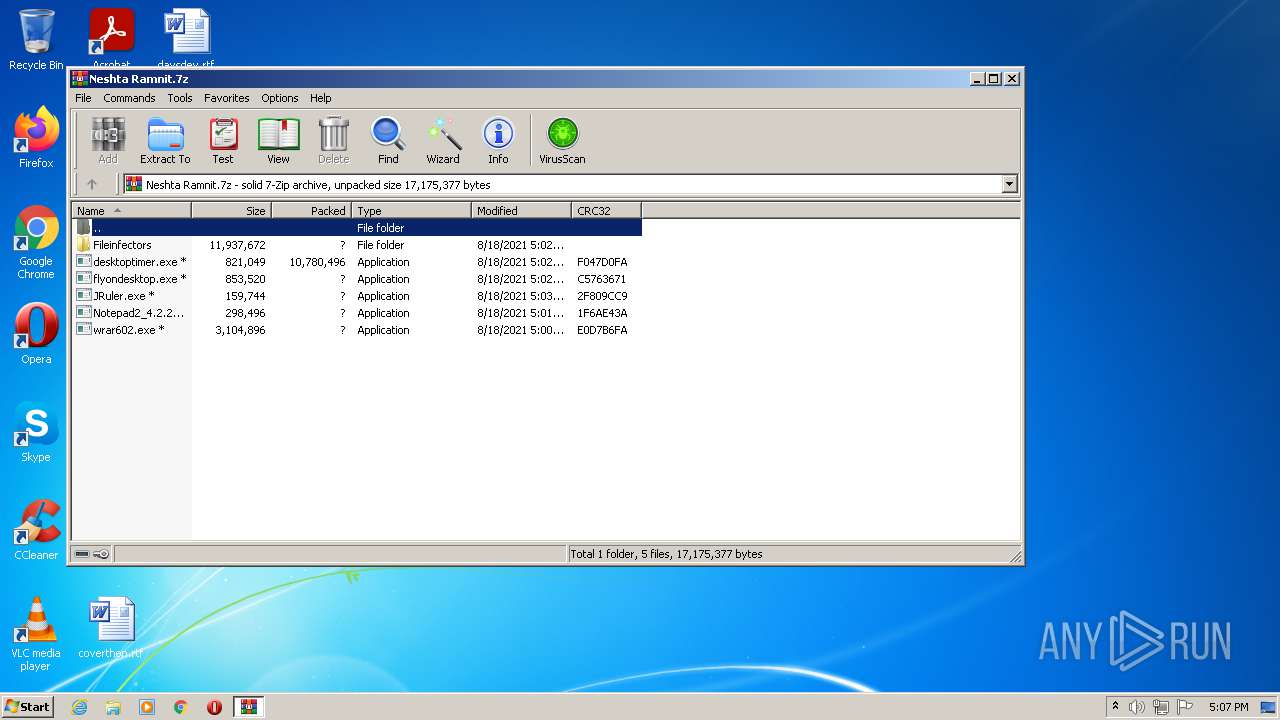
| File name: | Neshta Ramnit.7z |
| Full analysis: | https://app.any.run/tasks/966edfe2-1967-464a-8122-d4d0b54c9b21 |
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | August 18, 2021, 16:07:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 207760DEA1A3B48B3BD79465DC017CE9 |
| SHA1: | 627EEA291560284A26F60C951BB3E30D784E5A93 |
| SHA256: | 785AD0E8D224280B8A2A1282B1C671CC5C008353F13A711AD4BA47AD3A3B5889 |
| SSDEEP: | 196608:Nz6l1xJ0RV0MkBr9tDRz4X/s66WzIXbPAjG4zcV44mzH43zti1ZzFOo:56l1ERevZt4XV6WQbPch46Hwi5Oo |
MALICIOUS
Application was dropped or rewritten from another process
- Neshta - (1).exe (PID: 1300)
- Neshta - (2).exe (PID: 4016)
- Neshta - (1).exe (PID: 3492)
- Neshta - (1).exe (PID: 3500)
- Neshta - (3).exe (PID: 2740)
- Neshta - (4).exe (PID: 2848)
- Neshta - (5).exe (PID: 2496)
- Neshta - (2).exe (PID: 2012)
- Neshta - (6).exe (PID: 2792)
- Neshta - (7).exe (PID: 2444)
- Neshta - (8).exe (PID: 2212)
- Neshta - (9).exe (PID: 3356)
- Neshta - (10).exe (PID: 2120)
- Neshta - (11).exe (PID: 3824)
- Neshta - (12).exe (PID: 2072)
- Neshta - (13).exe (PID: 1568)
- Ramnit - (1).exe (PID: 1936)
- Neshta - (4).exe (PID: 1588)
- Neshta - (3).exe (PID: 3668)
- Ramnit - (1).exe (PID: 3560)
- Ramnit - (2).exe (PID: 1232)
- Neshta - (6).exe (PID: 3248)
- Ramnit - (2).exe (PID: 564)
- Ramnit - (3).exe (PID: 3640)
- Ramnit - (3).exe (PID: 3368)
- sfseunjd.exe (PID: 3276)
- Neshta - (5).exe (PID: 588)
- Ramnit - (4).exe (PID: 2316)
- Ramnit - (4).exe (PID: 3256)
- Ramnit - (5).exe (PID: 3228)
- Ramnit - (5).exe (PID: 3032)
- Ramnit - (6).exe (PID: 740)
- Neshta - (7).exe (PID: 2384)
- Ramnit - (6).exe (PID: 2080)
- Ramnit - (7).exe (PID: 2904)
- Neshta - (12).exe (PID: 3748)
- Neshta - (12).exe (PID: 2768)
- Neshta - (9).exe (PID: 2656)
- Neshta - (11).exe (PID: 3960)
- Neshta - (13).exe (PID: 1456)
- alawsixx.exe (PID: 3580)
- sfseunjd.exe (PID: 2892)
- JRuler.exe (PID: 2696)
- JRuler.exe (PID: 384)
- JRuler.exe (PID: 2824)
- JRuler.exe (PID: 3108)
- Notepad2_4.2.25_x86.exe (PID: 3700)
- Notepad2_4.2.25_x86.exe (PID: 2876)
- Notepad2_4.2.25_x86.exe (PID: 3856)
- wrar602.exe (PID: 3668)
- wrar602.exe (PID: 1344)
- wrar602.exe (PID: 1532)
- uninstall.exe (PID: 568)
- desktoptimer.exe (PID: 740)
- desktoptimer.exe (PID: 732)
- desktoptimer.exe (PID: 2112)
- DesktopTimer.exe (PID: 3968)
- JRuler.exe (PID: 340)
- JRuler.exe (PID: 568)
- JRuler.exe (PID: 1792)
- JRuler.exe (PID: 3620)
Drops executable file immediately after starts
- Neshta - (1).exe (PID: 1300)
- Neshta - (2).exe (PID: 4016)
- Neshta - (3).exe (PID: 2740)
- Neshta - (4).exe (PID: 2848)
- Neshta - (5).exe (PID: 2496)
- Neshta - (6).exe (PID: 2792)
- Neshta - (7).exe (PID: 2444)
- Neshta - (9).exe (PID: 3356)
- Neshta - (12).exe (PID: 2072)
- Neshta - (11).exe (PID: 3824)
- Neshta - (13).exe (PID: 1568)
- Ramnit - (1).exe (PID: 1936)
- Ramnit - (2).exe (PID: 1232)
- Ramnit - (3).exe (PID: 3640)
- Ramnit - (3).exe (PID: 3368)
- sfseunjd.exe (PID: 3276)
- svchost.exe (PID: 3220)
- Ramnit - (4).exe (PID: 2316)
- Ramnit - (5).exe (PID: 3228)
- iexplore.exe (PID: 3760)
- Explorer.EXE (PID: 1724)
- JRuler.exe (PID: 2696)
- JRuler.exe (PID: 2824)
- Notepad2_4.2.25_x86.exe (PID: 3700)
- Notepad2_4.2.25_x86.exe (PID: 3856)
- wrar602.exe (PID: 3668)
- desktoptimer.exe (PID: 740)
- desktoptimer.exe (PID: 732)
- desktoptimer.exe (PID: 2112)
- JRuler.exe (PID: 340)
- JRuler.exe (PID: 1792)
Uses SVCHOST.EXE for hidden code execution
- sfseunjd.exe (PID: 3276)
- sfseunjd.exe (PID: 2892)
Writes to a start menu file
- svchost.exe (PID: 3220)
- iexplore.exe (PID: 3760)
Changes the autorun value in the registry
- svchost.exe (PID: 3220)
- Explorer.EXE (PID: 1724)
- alawsixx.exe (PID: 3580)
- desktoptimer.tmp (PID: 3276)
Runs injected code in another process
- iexplore.exe (PID: 2384)
- Neshta - (12).exe (PID: 2768)
Application was injected by another process
- taskeng.exe (PID: 432)
- Dwm.exe (PID: 1004)
- ctfmon.exe (PID: 1488)
- DllHost.exe (PID: 2504)
- Explorer.EXE (PID: 1724)
- DllHost.exe (PID: 3480)
- DllHost.exe (PID: 2848)
- DllHost.exe (PID: 2868)
- SearchProtocolHost.exe (PID: 2432)
Changes the login/logoff helper path in the registry
- iexplore.exe (PID: 960)
- alawsixx.exe (PID: 3580)
Changes Security Center notification settings
- alawsixx.exe (PID: 3580)
UAC/LUA settings modification
- alawsixx.exe (PID: 3580)
Changes firewall settings
- alawsixx.exe (PID: 3580)
Modifies Windows Defender service settings
- alawsixx.exe (PID: 3580)
Modifies Windows security services settings
- alawsixx.exe (PID: 3580)
RAMNIT was detected
- svchost.exe (PID: 3220)
- iexplore.exe (PID: 960)
- iexplore.exe (PID: 3760)
Connects to CnC server
- svchost.exe (PID: 3220)
- iexplore.exe (PID: 960)
- iexplore.exe (PID: 3760)
Changes Image File Execution Options
- Notepad2_4.2.25_x86.exe (PID: 3856)
Loads dropped or rewritten executable
- WinRAR.exe (PID: 688)
- chrome.exe (PID: 384)
- svchost.exe (PID: 1772)
- chrome.exe (PID: 2860)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 688)
- Neshta - (1).exe (PID: 1300)
- Neshta - (1).exe (PID: 3500)
- Neshta - (2).exe (PID: 4016)
- Neshta - (2).exe (PID: 2012)
- Neshta - (3).exe (PID: 2740)
- Neshta - (3).exe (PID: 3668)
- Neshta - (4).exe (PID: 2848)
- Neshta - (4).exe (PID: 1588)
- Neshta - (5).exe (PID: 2496)
- Neshta - (6).exe (PID: 2792)
- Neshta - (6).exe (PID: 3248)
- Neshta - (7).exe (PID: 2444)
- Neshta - (8).exe (PID: 2212)
- Neshta - (7).exe (PID: 2384)
- dw20.exe (PID: 2684)
- Neshta - (9).exe (PID: 3356)
- Neshta - (10).exe (PID: 2120)
- Neshta - (11).exe (PID: 3824)
- Neshta - (12).exe (PID: 2072)
- Neshta - (12).exe (PID: 3748)
- Neshta - (12).exe (PID: 2768)
- Neshta - (13).exe (PID: 1568)
- Neshta - (13).exe (PID: 1456)
- Ramnit - (1).exe (PID: 1936)
- Ramnit - (1).exe (PID: 3560)
- Ramnit - (2).exe (PID: 1232)
- Ramnit - (2).exe (PID: 564)
- Ramnit - (3).exe (PID: 3640)
- Ramnit - (3).exe (PID: 3368)
- sfseunjd.exe (PID: 3276)
- Ramnit - (4).exe (PID: 2316)
- Ramnit - (5).exe (PID: 3228)
- Ramnit - (4).exe (PID: 3256)
- Ramnit - (5).exe (PID: 3032)
- Ramnit - (6).exe (PID: 740)
- Ramnit - (6).exe (PID: 2080)
- Ramnit - (7).exe (PID: 2904)
- cmd.exe (PID: 2284)
- alawsixx.exe (PID: 3580)
- sfseunjd.exe (PID: 2892)
- JRuler.exe (PID: 2696)
- JRuler.exe (PID: 384)
- JRuler.exe (PID: 3108)
- Notepad2_4.2.25_x86.exe (PID: 3700)
- JRuler.exe (PID: 2824)
- Notepad2_4.2.25_x86.exe (PID: 2876)
- Notepad2_4.2.25_x86.exe (PID: 3856)
- wrar602.exe (PID: 1532)
- uninstall.exe (PID: 568)
- wrar602.exe (PID: 3668)
- desktoptimer.exe (PID: 740)
- desktoptimer.exe (PID: 732)
- desktoptimer.tmp (PID: 1392)
- desktoptimer.exe (PID: 2112)
- desktoptimer.tmp (PID: 3276)
- DesktopTimer.exe (PID: 3968)
- JRuler.exe (PID: 340)
- JRuler.exe (PID: 568)
- JRuler.exe (PID: 1792)
- JRuler.exe (PID: 3620)
Reads the computer name
- WinRAR.exe (PID: 688)
- Neshta - (1).exe (PID: 1300)
- Neshta - (2).exe (PID: 4016)
- Neshta - (3).exe (PID: 2740)
- Neshta - (2).exe (PID: 2012)
- Neshta - (4).exe (PID: 2848)
- Neshta - (5).exe (PID: 2496)
- Neshta - (6).exe (PID: 2792)
- Neshta - (7).exe (PID: 2444)
- Neshta - (6).exe (PID: 3248)
- dw20.exe (PID: 2684)
- Neshta - (9).exe (PID: 3356)
- Neshta - (11).exe (PID: 3824)
- Neshta - (12).exe (PID: 2072)
- Neshta - (13).exe (PID: 1568)
- Ramnit - (1).exe (PID: 1936)
- Ramnit - (2).exe (PID: 1232)
- Ramnit - (3).exe (PID: 3640)
- Ramnit - (3).exe (PID: 3368)
- sfseunjd.exe (PID: 3276)
- Ramnit - (2).exe (PID: 564)
- Ramnit - (4).exe (PID: 2316)
- Ramnit - (5).exe (PID: 3228)
- Ramnit - (5).exe (PID: 3032)
- Ramnit - (4).exe (PID: 3256)
- Ramnit - (6).exe (PID: 740)
- Neshta - (3).exe (PID: 3668)
- Ramnit - (6).exe (PID: 2080)
- Ramnit - (7).exe (PID: 2904)
- Ramnit - (1).exe (PID: 3560)
- alawsixx.exe (PID: 3580)
- sfseunjd.exe (PID: 2892)
- JRuler.exe (PID: 2696)
- JRuler.exe (PID: 384)
- JRuler.exe (PID: 2824)
- JRuler.exe (PID: 3108)
- Notepad2_4.2.25_x86.exe (PID: 3700)
- Notepad2_4.2.25_x86.exe (PID: 2876)
- Notepad2_4.2.25_x86.exe (PID: 3856)
- wrar602.exe (PID: 3668)
- wrar602.exe (PID: 1532)
- uninstall.exe (PID: 568)
- desktoptimer.exe (PID: 740)
- desktoptimer.exe (PID: 732)
- desktoptimer.tmp (PID: 1392)
- desktoptimer.tmp (PID: 3276)
- DesktopTimer.exe (PID: 3968)
- JRuler.exe (PID: 340)
- JRuler.exe (PID: 568)
- JRuler.exe (PID: 1792)
- JRuler.exe (PID: 3620)
Drops a file with too old compile date
- WinRAR.exe (PID: 688)
- Neshta - (1).exe (PID: 1300)
- Neshta - (9).exe (PID: 3356)
- Neshta - (11).exe (PID: 3824)
- Neshta - (13).exe (PID: 1568)
- Ramnit - (1).exe (PID: 3560)
- Ramnit - (5).exe (PID: 3228)
- iexplore.exe (PID: 3760)
- JRuler.exe (PID: 2696)
- JRuler.exe (PID: 2824)
- desktoptimer.exe (PID: 740)
- desktoptimer.exe (PID: 2112)
- desktoptimer.tmp (PID: 3276)
- desktoptimer.exe (PID: 732)
- JRuler.exe (PID: 340)
- JRuler.exe (PID: 1792)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 688)
- Neshta - (2).exe (PID: 4016)
- Neshta - (4).exe (PID: 2848)
- Neshta - (5).exe (PID: 2496)
- Neshta - (6).exe (PID: 2792)
- Neshta - (7).exe (PID: 2444)
- Neshta - (9).exe (PID: 3356)
- Neshta - (13).exe (PID: 1568)
- wrar602.exe (PID: 3668)
- wrar602.exe (PID: 1532)
- desktoptimer.tmp (PID: 3276)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 688)
- Neshta - (2).exe (PID: 4016)
- Neshta - (1).exe (PID: 1300)
- Neshta - (3).exe (PID: 2740)
- Neshta - (4).exe (PID: 2848)
- Neshta - (5).exe (PID: 2496)
- Neshta - (6).exe (PID: 2792)
- Neshta - (7).exe (PID: 2444)
- Neshta - (9).exe (PID: 3356)
- Neshta - (11).exe (PID: 3824)
- Neshta - (12).exe (PID: 2072)
- Neshta - (13).exe (PID: 1568)
- Ramnit - (1).exe (PID: 1936)
- Ramnit - (2).exe (PID: 1232)
- Ramnit - (1).exe (PID: 3560)
- Ramnit - (3).exe (PID: 3640)
- Ramnit - (3).exe (PID: 3368)
- svchost.exe (PID: 3220)
- sfseunjd.exe (PID: 3276)
- Ramnit - (4).exe (PID: 2316)
- Ramnit - (5).exe (PID: 3228)
- iexplore.exe (PID: 3760)
- Explorer.EXE (PID: 1724)
- JRuler.exe (PID: 2696)
- JRuler.exe (PID: 2824)
- Notepad2_4.2.25_x86.exe (PID: 3700)
- Notepad2_4.2.25_x86.exe (PID: 3856)
- wrar602.exe (PID: 3668)
- wrar602.exe (PID: 1532)
- desktoptimer.exe (PID: 740)
- desktoptimer.exe (PID: 732)
- desktoptimer.exe (PID: 2112)
- desktoptimer.tmp (PID: 3276)
- JRuler.exe (PID: 340)
- JRuler.exe (PID: 1792)
Application launched itself
- Neshta - (12).exe (PID: 3748)
- Notepad2_4.2.25_x86.exe (PID: 2876)
Starts itself from another location
- Ramnit - (3).exe (PID: 3368)
- Ramnit - (6).exe (PID: 2080)
Creates files in the user directory
- svchost.exe (PID: 3220)
- Explorer.EXE (PID: 1724)
- Notepad2_4.2.25_x86.exe (PID: 3856)
Creates files in the program directory
- svchost.exe (PID: 3220)
- Ramnit - (7).exe (PID: 2904)
- Notepad2_4.2.25_x86.exe (PID: 3856)
- wrar602.exe (PID: 1532)
Creates files in the Windows directory
- sdbinst.exe (PID: 2212)
- sdbinst.exe (PID: 3108)
- Notepad2_4.2.25_x86.exe (PID: 3856)
Creates a software uninstall entry
- sdbinst.exe (PID: 2212)
- sdbinst.exe (PID: 3108)
- Notepad2_4.2.25_x86.exe (PID: 3856)
- uninstall.exe (PID: 568)
Starts Internet Explorer
- Ramnit - (5).exe (PID: 3032)
- Explorer.EXE (PID: 1724)
- Ramnit - (7).exe (PID: 2904)
- desktoptimer.tmp (PID: 3276)
Starts CMD.EXE for commands execution
- sfseunjd.exe (PID: 3276)
Removes files from Windows directory
- sdbinst.exe (PID: 3108)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1724)
Creates a directory in Program Files
- Notepad2_4.2.25_x86.exe (PID: 3856)
- desktoptimer.tmp (PID: 3276)
Changes default file association
- Notepad2_4.2.25_x86.exe (PID: 3856)
- uninstall.exe (PID: 568)
Reads Microsoft Outlook installation path
- wrar602.exe (PID: 1532)
- iexplore.exe (PID: 4060)
Reads internet explorer settings
- wrar602.exe (PID: 1532)
Creates/Modifies COM task schedule object
- uninstall.exe (PID: 568)
Searches for installed software
- uninstall.exe (PID: 568)
Reads Windows owner or organization settings
- desktoptimer.tmp (PID: 3276)
Reads the Windows organization settings
- desktoptimer.tmp (PID: 3276)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2068)
INFO
Checks supported languages
- DllHost.exe (PID: 2504)
- svchost.exe (PID: 3220)
- svchost.exe (PID: 696)
- sdbinst.exe (PID: 2212)
- iexplore.exe (PID: 2384)
- iexplore.exe (PID: 3760)
- iscsicli.exe (PID: 4084)
- iexplore.exe (PID: 960)
- iexplore.exe (PID: 3316)
- sdbinst.exe (PID: 3720)
- DllHost.exe (PID: 3480)
- svchost.exe (PID: 2292)
- svchost.exe (PID: 3256)
- sdbinst.exe (PID: 3108)
- iscsicli.exe (PID: 1344)
- sdbinst.exe (PID: 2180)
- DllHost.exe (PID: 2848)
- iexplore.exe (PID: 2368)
- iexplore.exe (PID: 4060)
- DllHost.exe (PID: 2868)
- SearchProtocolHost.exe (PID: 2432)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 1632)
- chrome.exe (PID: 3504)
- chrome.exe (PID: 560)
- chrome.exe (PID: 1648)
- chrome.exe (PID: 3564)
- chrome.exe (PID: 2512)
- chrome.exe (PID: 1984)
- chrome.exe (PID: 3104)
- chrome.exe (PID: 1456)
- chrome.exe (PID: 2672)
- chrome.exe (PID: 188)
- chrome.exe (PID: 384)
- chrome.exe (PID: 1176)
- chrome.exe (PID: 3524)
- chrome.exe (PID: 3000)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 2540)
- chrome.exe (PID: 1824)
- chrome.exe (PID: 3396)
- chrome.exe (PID: 2860)
- chrome.exe (PID: 2292)
- chrome.exe (PID: 2576)
- svchost.exe (PID: 1772)
- chrome.exe (PID: 360)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 688)
- chrome.exe (PID: 2068)
Reads the computer name
- DllHost.exe (PID: 2504)
- svchost.exe (PID: 3220)
- svchost.exe (PID: 696)
- iexplore.exe (PID: 2384)
- iexplore.exe (PID: 3760)
- iscsicli.exe (PID: 4084)
- iexplore.exe (PID: 960)
- iexplore.exe (PID: 3316)
- DllHost.exe (PID: 3480)
- svchost.exe (PID: 2292)
- svchost.exe (PID: 3256)
- iscsicli.exe (PID: 1344)
- DllHost.exe (PID: 2848)
- iexplore.exe (PID: 2368)
- iexplore.exe (PID: 4060)
- DllHost.exe (PID: 2868)
- SearchProtocolHost.exe (PID: 2432)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 1632)
- chrome.exe (PID: 560)
- chrome.exe (PID: 1456)
- chrome.exe (PID: 384)
- chrome.exe (PID: 3504)
- chrome.exe (PID: 3396)
- chrome.exe (PID: 2860)
- chrome.exe (PID: 2292)
Manual execution by user
- Neshta - (1).exe (PID: 1300)
- Neshta - (2).exe (PID: 4016)
- Neshta - (3).exe (PID: 2740)
- Neshta - (4).exe (PID: 2848)
- Neshta - (5).exe (PID: 2496)
- Neshta - (6).exe (PID: 2792)
- Neshta - (7).exe (PID: 2444)
- Neshta - (8).exe (PID: 2212)
- Neshta - (9).exe (PID: 3356)
- Neshta - (10).exe (PID: 2120)
- Neshta - (11).exe (PID: 3824)
- Neshta - (12).exe (PID: 2072)
- Neshta - (13).exe (PID: 1568)
- Ramnit - (1).exe (PID: 1936)
- Ramnit - (2).exe (PID: 1232)
- Ramnit - (3).exe (PID: 3640)
- Ramnit - (4).exe (PID: 2316)
- Ramnit - (5).exe (PID: 3228)
- Ramnit - (6).exe (PID: 740)
- Ramnit - (7).exe (PID: 2904)
- iexplore.exe (PID: 3316)
- JRuler.exe (PID: 2696)
- JRuler.exe (PID: 2824)
- Notepad2_4.2.25_x86.exe (PID: 3700)
- wrar602.exe (PID: 3668)
- desktoptimer.exe (PID: 740)
- JRuler.exe (PID: 340)
- chrome.exe (PID: 2068)
- JRuler.exe (PID: 1792)
Checks Windows Trust Settings
- Neshta - (2).exe (PID: 2012)
- Neshta - (6).exe (PID: 3248)
- iexplore.exe (PID: 4060)
- iexplore.exe (PID: 2368)
Reads settings of System Certificates
- Neshta - (2).exe (PID: 2012)
- Neshta - (6).exe (PID: 3248)
- iexplore.exe (PID: 4060)
- iexplore.exe (PID: 2368)
- chrome.exe (PID: 560)
Creates files in the user directory
- iexplore.exe (PID: 3760)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 4060)
Application was dropped or rewritten from another process
- desktoptimer.tmp (PID: 1392)
- desktoptimer.tmp (PID: 3276)
Loads dropped or rewritten executable
- desktoptimer.tmp (PID: 3276)
Creates a software uninstall entry
- desktoptimer.tmp (PID: 3276)
Changes internet zones settings
- iexplore.exe (PID: 2368)
Application launched itself
- iexplore.exe (PID: 2368)
- chrome.exe (PID: 2068)
Reads internet explorer settings
- iexplore.exe (PID: 4060)
Changes settings of System certificates
- iexplore.exe (PID: 4060)
Creates files in the program directory
- desktoptimer.tmp (PID: 3276)
Adds / modifies Windows certificates
- iexplore.exe (PID: 4060)
Reads the date of Windows installation
- iexplore.exe (PID: 2368)
- chrome.exe (PID: 2860)
Reads the hosts file
- chrome.exe (PID: 2068)
- chrome.exe (PID: 560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
192
Monitored processes
122
Malicious processes
46
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,6317281003166757808,15949580386602241053,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3252 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 340 | "C:\Users\admin\Desktop\JRuler.exe" | C:\Users\admin\Desktop\JRuler.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,6317281003166757808,15949580386602241053,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2220 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 384 | "C:\Users\admin\AppData\Local\Temp\3582-490\JRuler.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\JRuler.exe | — | JRuler.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,6317281003166757808,15949580386602241053,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3320 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 432 | taskeng.exe {E7C81B1A-34CA-46B5-933E-02C92A917A9F} | C:\Windows\system32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1052,6317281003166757808,15949580386602241053,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1328 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 564 | "C:\Users\admin\AppData\Local\Temp\3582-490\Ramnit - (2).exe" | C:\Users\admin\AppData\Local\Temp\3582-490\Ramnit - (2).exe | — | Ramnit - (2).exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 568 | "C:\Program Files\WinRAR\uninstall.exe" /setup | C:\Program Files\WinRAR\uninstall.exe | — | wrar602.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: Uninstall WinRAR Exit code: 0 Version: 6.2.0 Modules
| |||||||||||||||
| 568 | "C:\Users\admin\AppData\Local\Temp\3582-490\JRuler.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\JRuler.exe | — | JRuler.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
75 875
Read events
74 262
Write events
1 585
Delete events
28
Modification events
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\171\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Neshta Ramnit.7z | |||
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1724) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (1724) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
100
Suspicious files
111
Text files
313
Unknown types
66
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (11).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (12).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (2).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (4).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (6).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (8).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (1).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (10).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (13).exe | executable | |
MD5:— | SHA256:— | |||
| 688 | WinRAR.exe | C:\Users\admin\Desktop\Fileinfectors\Neshta - (3).exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
107
DNS requests
111
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3248 | Neshta - (6).exe | GET | 304 | 205.185.216.42:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc7ae66b6e2cdf42 | US | — | — | whitelisted |
4060 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
4060 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
4060 | iexplore.exe | GET | 200 | 78.46.117.95:80 | http://freedesktopsoft.com/slider/slider.css | DE | text | 6.40 Kb | suspicious |
4060 | iexplore.exe | GET | 200 | 78.46.117.95:80 | http://freedesktopsoft.com/freedesktoptimerlike.html | DE | html | 6.01 Kb | suspicious |
4060 | iexplore.exe | GET | 200 | 78.46.117.95:80 | http://freedesktopsoft.com/button.css | DE | text | 2.71 Kb | suspicious |
4060 | iexplore.exe | GET | 200 | 78.46.117.95:80 | http://freedesktopsoft.com/slider/slider.js | DE | text | 3.00 Kb | suspicious |
4060 | iexplore.exe | GET | 200 | 78.46.117.95:80 | http://freedesktopsoft.com/images/superman_likeus.gif | DE | image | 30.8 Kb | suspicious |
4060 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8dead6c8fdcc44a6 | US | compressed | 4.70 Kb | whitelisted |
4060 | iexplore.exe | GET | 200 | 78.46.117.95:80 | http://freedesktopsoft.com/main.css | DE | text | 4.15 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3760 | iexplore.exe | 82.112.184.197:447 | supnewdmn.com | Vysokie tehnologii Limited Liability Company | RU | malicious |
3248 | Neshta - (6).exe | 205.185.216.42:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3220 | svchost.exe | 63.251.235.76:443 | jugapqqyejdhysgdymv.com | Voxel Dot Net, Inc. | US | malicious |
960 | iexplore.exe | 107.6.74.76:443 | zahlung.name | Voxel Dot Net, Inc. | US | malicious |
3760 | iexplore.exe | 45.55.36.236:447 | rtvwerjyuver.com | Digital Ocean, Inc. | US | malicious |
3760 | iexplore.exe | 52.16.225.15:447 | tvrstrynyvwstrtve.com | Amazon.com, Inc. | IE | whitelisted |
4060 | iexplore.exe | 78.46.117.95:80 | freedesktopsoft.com | Hetzner Online GmbH | DE | suspicious |
960 | iexplore.exe | 142.250.184.238:80 | google.com | Google Inc. | US | whitelisted |
3220 | svchost.exe | 195.201.179.207:443 | yijlxkulyqfcgfecneu.com | Awanti Ltd. | RU | malicious |
3760 | iexplore.exe | 18.235.92.123:447 | wqerveybrstyhcerveantbe.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
google.com |
| malicious |
supnewdmn.com |
| malicious |
revivalresumed.com |
| malicious |
uhhoatxt.com |
| malicious |
yijlxkulyqfcgfecneu.com |
| malicious |
vxasusphxwkdktm.com |
| malicious |
yractfrwrctboagip.com |
| unknown |
hvkteatvnctsgrie.com |
| malicious |
rkwqxdlhwsbpsoiipkl.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3220 | svchost.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
— | — | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a Suspicious *.myftp.biz Domain |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
960 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
3220 | svchost.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
960 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
3760 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
3760 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
3220 | svchost.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
3220 | svchost.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
Process | Message |
|---|---|
alawsixx.exe | CheckBypassed ok |