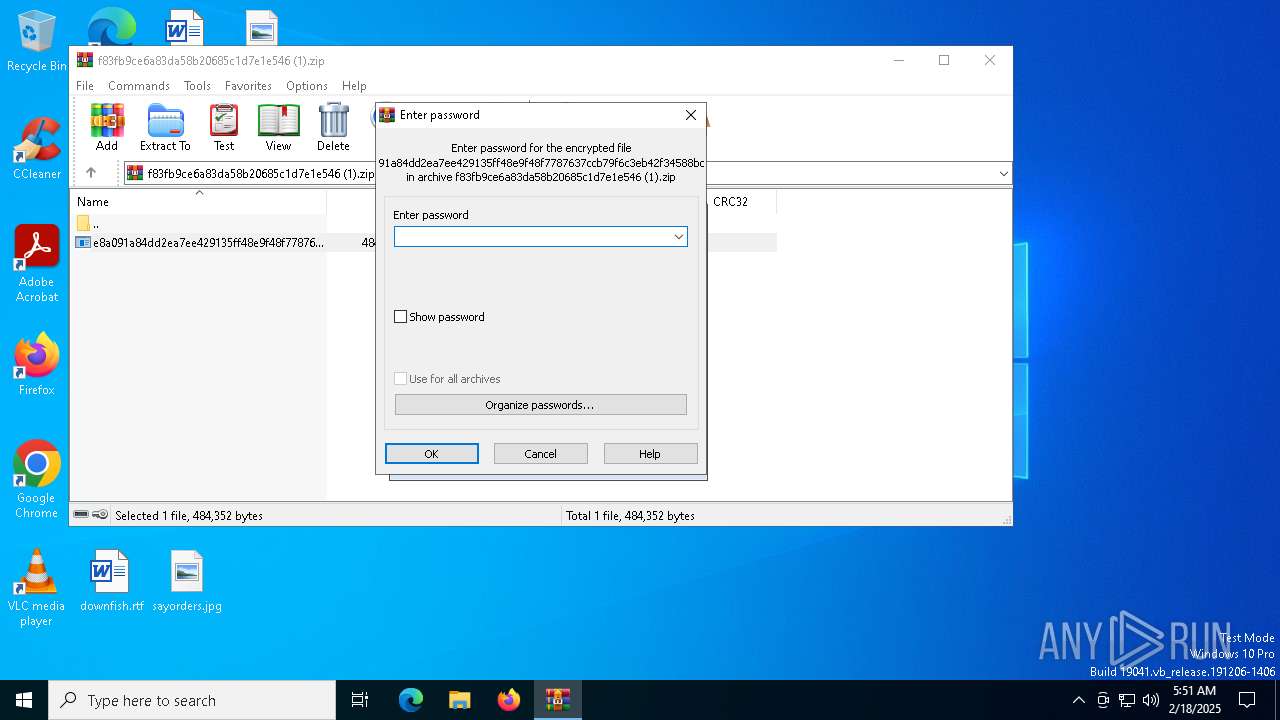
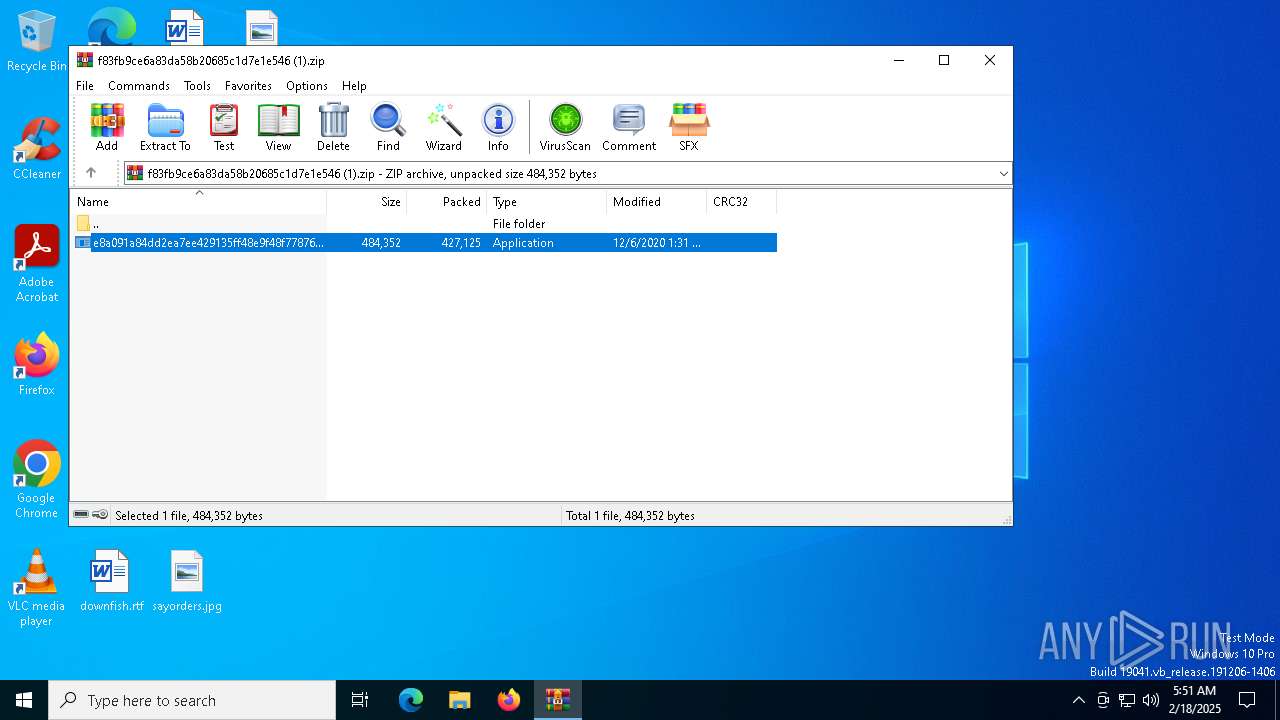
| File name: | f83fb9ce6a83da58b20685c1d7e1e546 (1).zip |
| Full analysis: | https://app.any.run/tasks/c4eae6d3-f244-4f60-ac22-a4f909da1eec |
| Verdict: | Malicious activity |
| Threats: | Maze is ransomware — a malware type that encrypts the victim’s files and restores the data in exchange for a ransom payment. One of the most distinguishable features of Maze is that it is one of the first malware of the kind to publicly release stolen data. |
| Analysis date: | February 18, 2025, 05:50:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
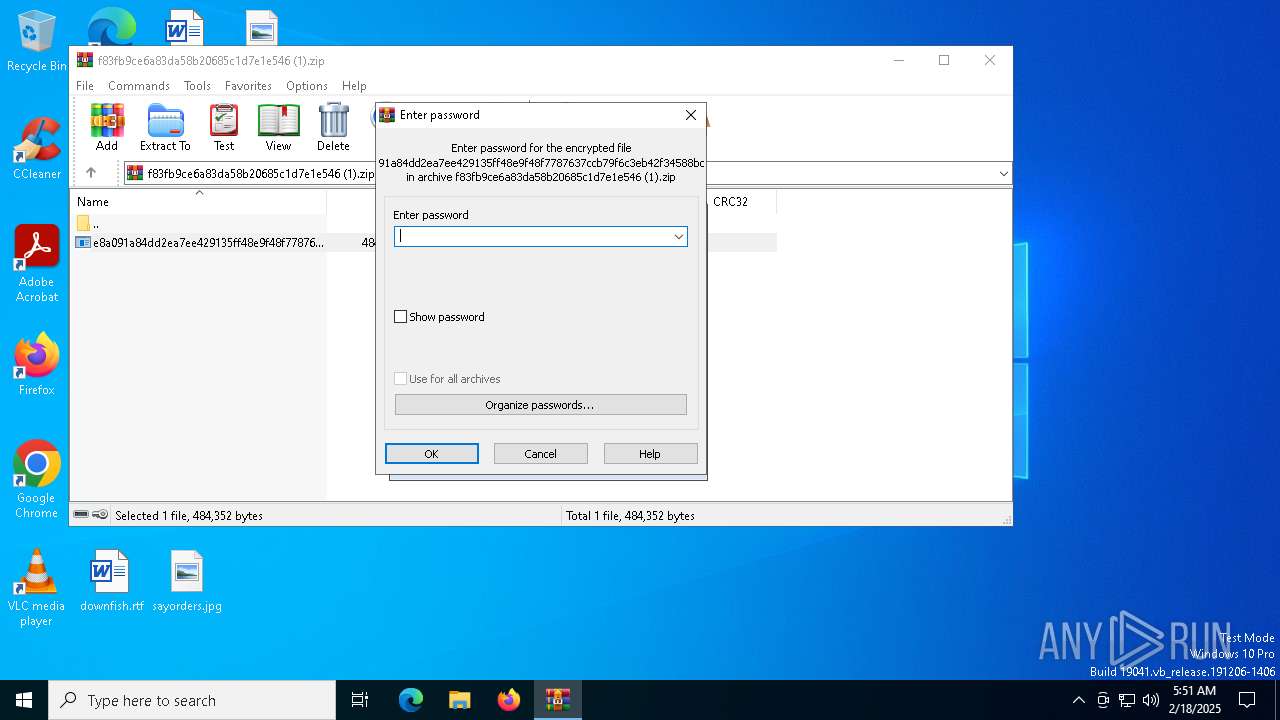
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | A024E1D53D75EAEFC4AA74131FF16FD8 |
| SHA1: | CFD053A7E793EC84EC78679F224B417C760E0A5E |
| SHA256: | 77B2731FF3C7A14B8B962EA387C41293415B3478E73973888851991105777560 |
| SSDEEP: | 12288:6Zr2Dvm+2LDF+jgcz5jCDiIuexi3FBUzvASSB7d:6ZCDvmRLDwjPrIuekUz4SS5 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6412)
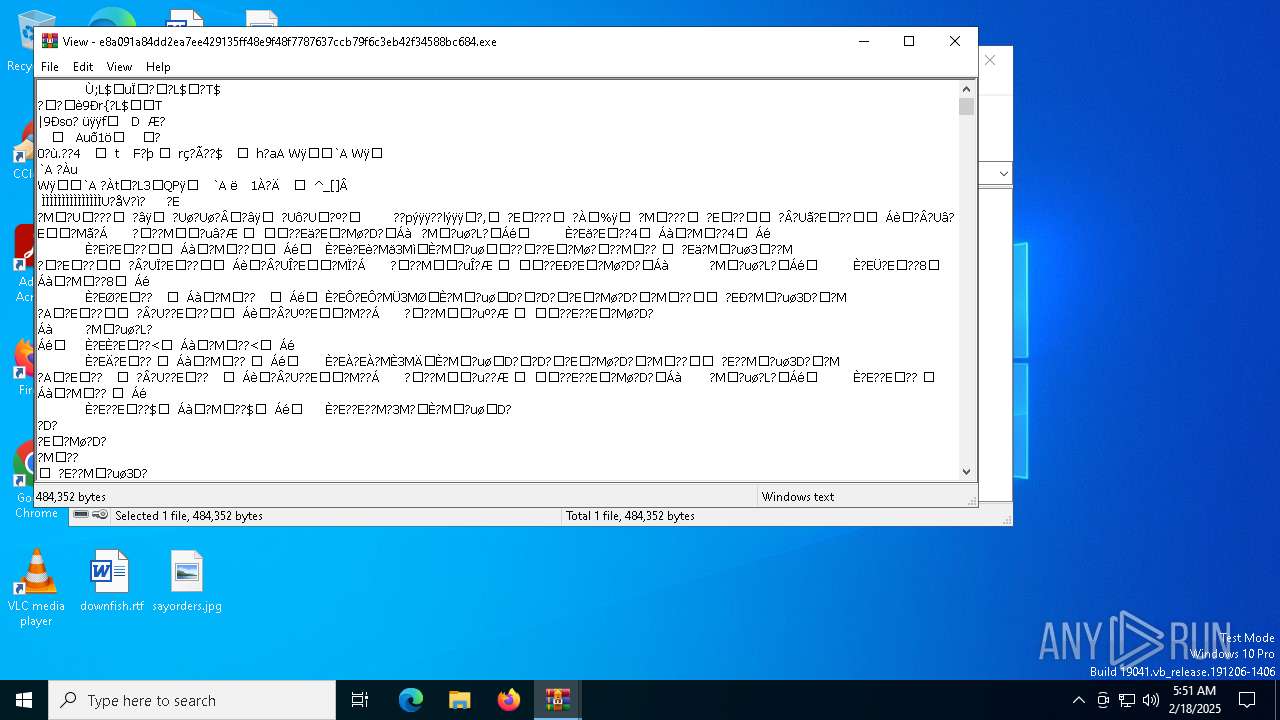
Maze ransom note is found
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Actions looks like stealing of personal data
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
MAZE mutex has been found
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 204)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 3564)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 4624)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Modifies files in the Chrome extension folder
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Maze is detected
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
RANSOMWARE has been detected
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6412)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Creates file in the systems drive root
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Connects to the server without a host name
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
INFO
Checks supported languages
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 204)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 3564)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 4624)
Reads the computer name
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 204)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 3564)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 4624)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6412)
Creates files or folders in the user directory
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Checks proxy server information
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Creates files in the program directory
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Reads the machine GUID from the registry
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 7092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2020:12:06 13:31:08 |
| ZipCRC: | 0x3e6fd65f |
| ZipCompressedSize: | 427125 |
| ZipUncompressedSize: | 484352 |
| ZipFileName: | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe |
Total processes
131
Monitored processes
5
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.23307\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.23307\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3564 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.33557\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.33557\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4624 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.35752\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.35752\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6412 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\f83fb9ce6a83da58b20685c1d7e1e546 (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7092 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.17394\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.17394\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 075
Read events
3 058
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\f83fb9ce6a83da58b20685c1d7e1e546 (1).zip | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7092) e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
28
Suspicious files
3 179
Text files
689
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\DECRYPT-FILES.html | html | |
MD5:D1DEB9D6181BCDF53F8C9FF6AA6EE456 | SHA256:2124C56233C354C85254E774C743B7B225DA29C11D2FEE997C2BE396510EC6DB | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\BOOTNXT.QWVBb4 | binary | |
MD5:218FB88782DDB5A05C6A1387F5B6E1D0 | SHA256:5E1A81FC5E0C9C00F26C3C245891A8D24CEADD7A1722614C3C59EB4D35F3804F | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\ProgramData\foo.db | binary | |
MD5:76F8F28BD51EFA03AB992FDB050C8382 | SHA256:5470F0644589685000154CB7D3F60280ACB16E39CA961CCE2C016078B303BC1B | |||
| 6412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6412.17394\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | executable | |
MD5:F83FB9CE6A83DA58B20685C1D7E1E546 | SHA256:E8A091A84DD2EA7EE429135FF48E9F48F7787637CCB79F6C3EB42F34588BC684 | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\BOOTNXT | binary | |
MD5:218FB88782DDB5A05C6A1387F5B6E1D0 | SHA256:5E1A81FC5E0C9C00F26C3C245891A8D24CEADD7A1722614C3C59EB4D35F3804F | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\bootTel.dat | binary | |
MD5:5D6FF9D2FAD648BA93DFAE0EE790115E | SHA256:019CFD4E2CAB178B5F6B8AC42B8370547D2F34EEE2B1581FC95040D02ACCD2E7 | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeCMapFnt23.lst.F5ReJtI | binary | |
MD5:40CC1CA391F0DE2DC29FF2845967B517 | SHA256:3C1A0C142685EBFAA54F134AD37BA7C609F7258C03C42E8E3881AE8557D8EA4C | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\bootTel.dat.QWVBb4 | binary | |
MD5:5D6FF9D2FAD648BA93DFAE0EE790115E | SHA256:019CFD4E2CAB178B5F6B8AC42B8370547D2F34EEE2B1581FC95040D02ACCD2E7 | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\DECRYPT-FILES.html | html | |
MD5:D1DEB9D6181BCDF53F8C9FF6AA6EE456 | SHA256:2124C56233C354C85254E774C743B7B225DA29C11D2FEE997C2BE396510EC6DB | |||
| 7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst.F5ReJtI | binary | |
MD5:C817BC3F9B7A158AE986AC1F8292B527 | SHA256:3B539A86A05CA91BCBBE91682B0932C59DB7BE59D6BC1292225ACD0947569368 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
50
DNS requests
17
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | POST | — | 92.63.194.20:80 | http://92.63.194.20/tracker/archive/qgcvr.aspx?dl=1ao2n&emyv=ouxo | unknown | — | — | malicious |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6708 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6216 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | POST | 500 | 92.63.194.20:80 | http://92.63.194.20/tracker/archive/qgcvr.aspx?dl=1ao2n&emyv=ouxo | unknown | — | — | malicious |
6216 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | POST | 301 | 92.63.194.3:80 | http://92.63.194.3/webaccess/analytics/yyeqd.phtml | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
372 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1480 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3976 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6708 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | A Network Trojan was detected | ET MALWARE Maze/ID Ransomware Activity |
7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | A Network Trojan was detected | ET MALWARE Maze/ID Ransomware Activity |
7092 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | A Network Trojan was detected | ET MALWARE Maze/ID Ransomware Activity |