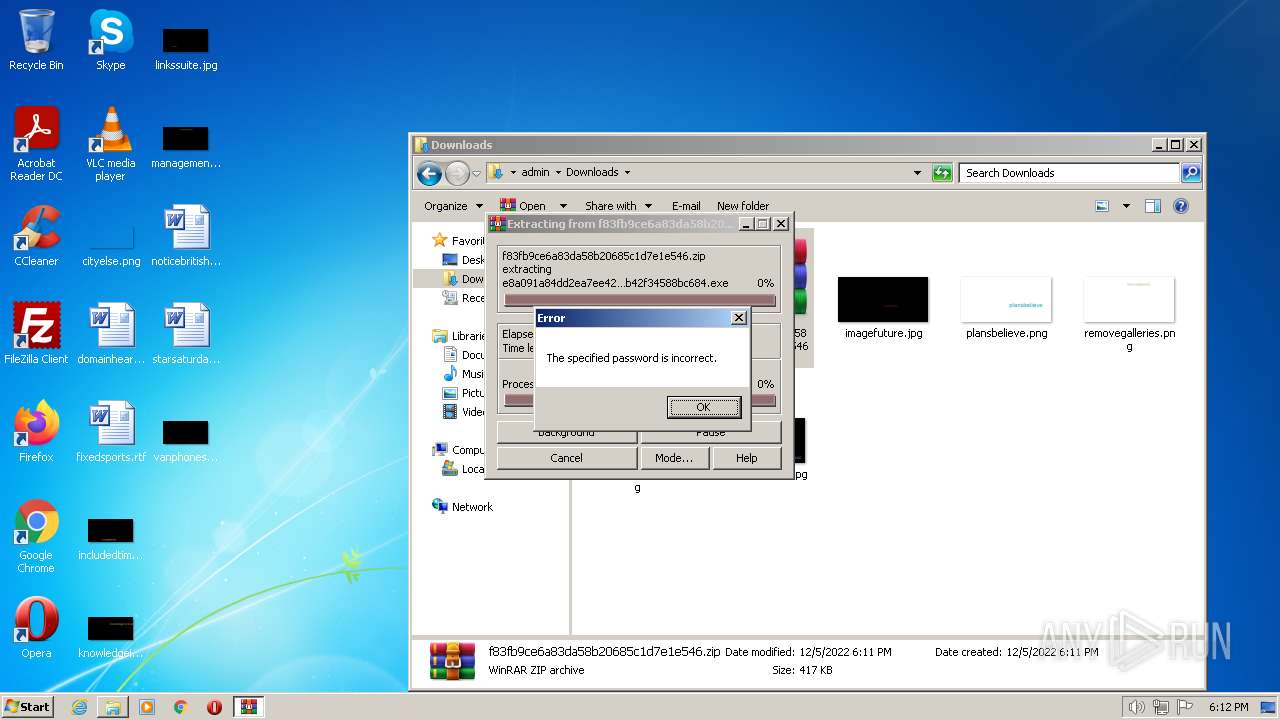
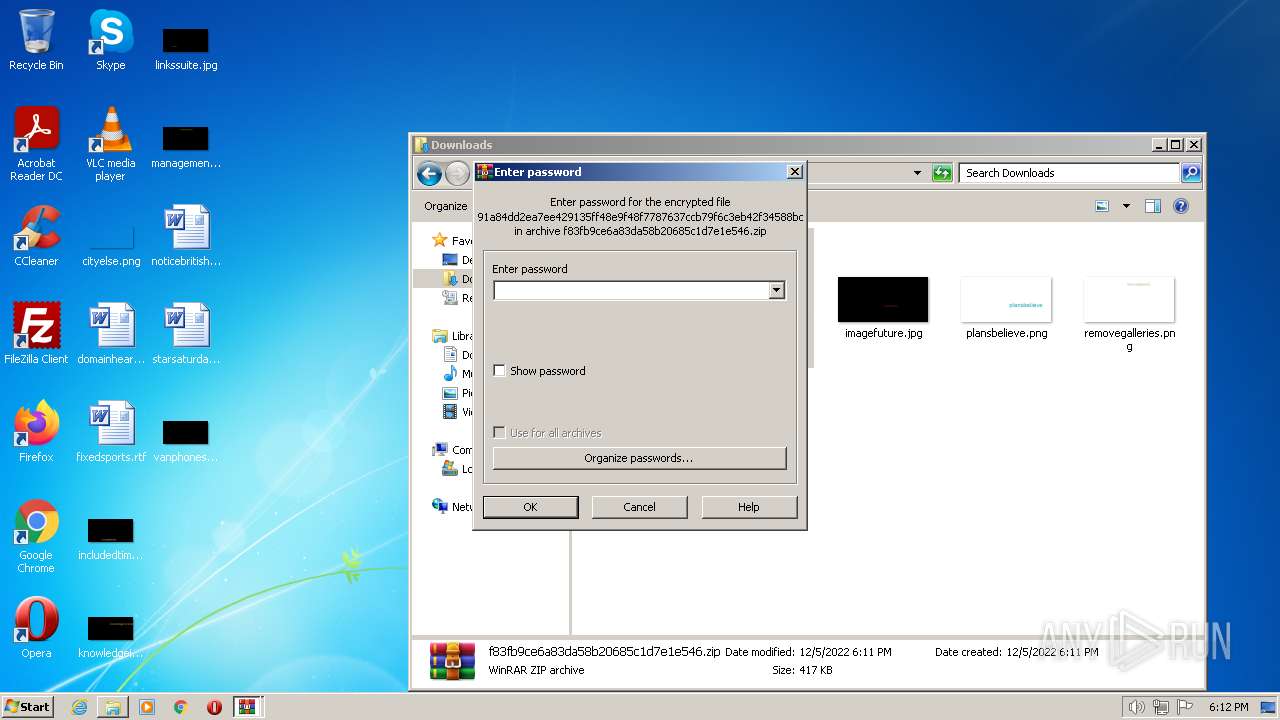
| File name: | f83fb9ce6a83da58b20685c1d7e1e546.zip |
| Full analysis: | https://app.any.run/tasks/685fa2f9-5b74-439a-99cf-0d11059e2b14 |
| Verdict: | Malicious activity |
| Threats: | Maze is ransomware — a malware type that encrypts the victim’s files and restores the data in exchange for a ransom payment. One of the most distinguishable features of Maze is that it is one of the first malware of the kind to publicly release stolen data. |
| Analysis date: | December 05, 2022, 18:11:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | A024E1D53D75EAEFC4AA74131FF16FD8 |
| SHA1: | CFD053A7E793EC84EC78679F224B417C760E0A5E |
| SHA256: | 77B2731FF3C7A14B8B962EA387C41293415B3478E73973888851991105777560 |
| SSDEEP: | 12288:6Zr2Dvm+2LDF+jgcz5jCDiIuexi3FBUzvASSB7d:6ZCDvmRLDwjPrIuekUz4SS5 |
MALICIOUS
Application was dropped or rewritten from another process
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 2296)
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 3064)
Maze ransom note is found
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 3064)
Drops the executable file immediately after the start
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 3064)
SUSPICIOUS
Connects to the server without a host name
- e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe (PID: 3064)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
43
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\ndexw\s\ckg\..\..\..\Windows\he\qafqd\disl\..\..\..\system32\haq\lq\pvhk\..\..\..\wbem\alpu\h\..\..\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1328 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\f83fb9ce6a83da58b20685c1d7e1e546.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2296 | "C:\Users\admin\Downloads\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe" | C:\Users\admin\Downloads\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3064 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1328.38131\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1328.38131\e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3460 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\f83fb9ce6a83da58b20685c1d7e1e546.zip" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3704 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 530
Read events
1 492
Write events
38
Delete events
0
Modification events
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\f83fb9ce6a83da58b20685c1d7e1e546.zip | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
1 050
Text files
330
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\Local\VirtualStore\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\.oracle_jre_usage\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.B7bfjIG | binary | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\MSOCache\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\Local\Adobe\A0A2C719-B8B1-4DC7-B33B-C50E709F20B0\96458326-0F6E-4F95-88EE-ED9F0B2D5401 | binary | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\Local\Adobe\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
| 3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | C:\Users\admin\AppData\Local\DECRYPT-FILES.html | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3064 | e8a091a84dd2ea7ee429135ff48e9f48f7787637ccb79f6c3eb42f34588bc684.exe | POST | — | 92.63.8.47:80 | http://92.63.8.47/analytics/ecrsteudv.aspx?vqu=p51bji&gexc=86ehb5k | TR | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 92.63.8.47:80 | — | Netonline Bilisim Sirketi LTD | CY | malicious |