| File name: | Medusa.zip |
| Full analysis: | https://app.any.run/tasks/4fe894fa-c133-4c0e-b0a6-4b29161914d5 |
| Verdict: | Malicious activity |
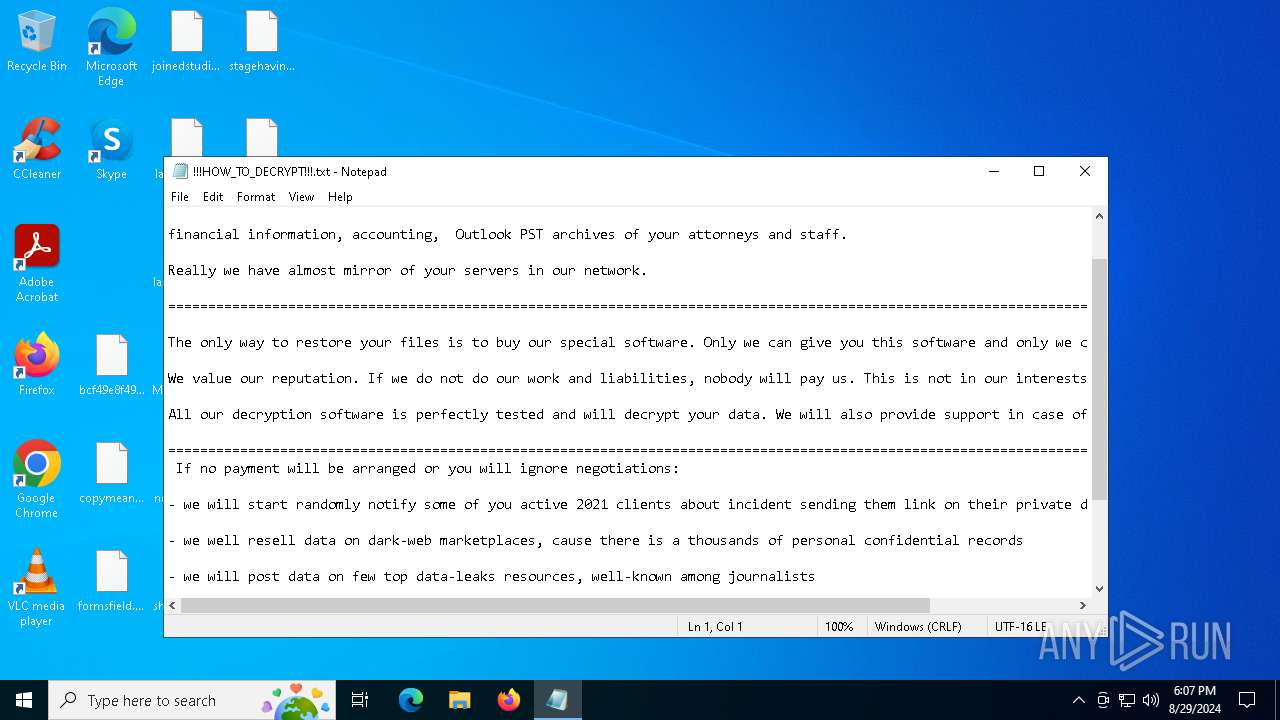
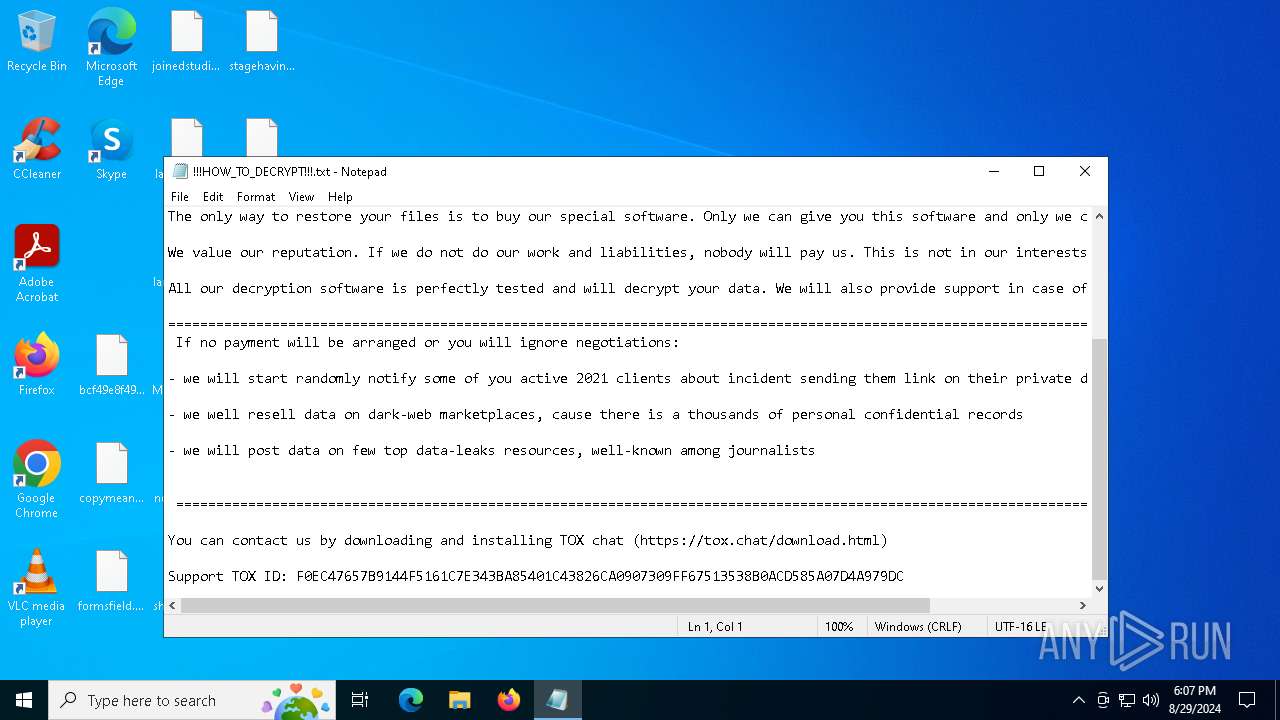
| Threats: | Medusa is a ransomware malware family targeting businesses and institutions. Medusa encrypts crucial data, rendering it inaccessible, and attempts to pressure users to pay to regain control of their information. The group behind this malicious software hosts a TOR website where it shares the list of the organizations whose infrastructure has been compromised. This malware utilizes various tactics, including exploiting vulnerabilities and employs a unique file extension (".MEDUSA") to mark encrypted files. |
| Analysis date: | August 29, 2024, 18:06:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
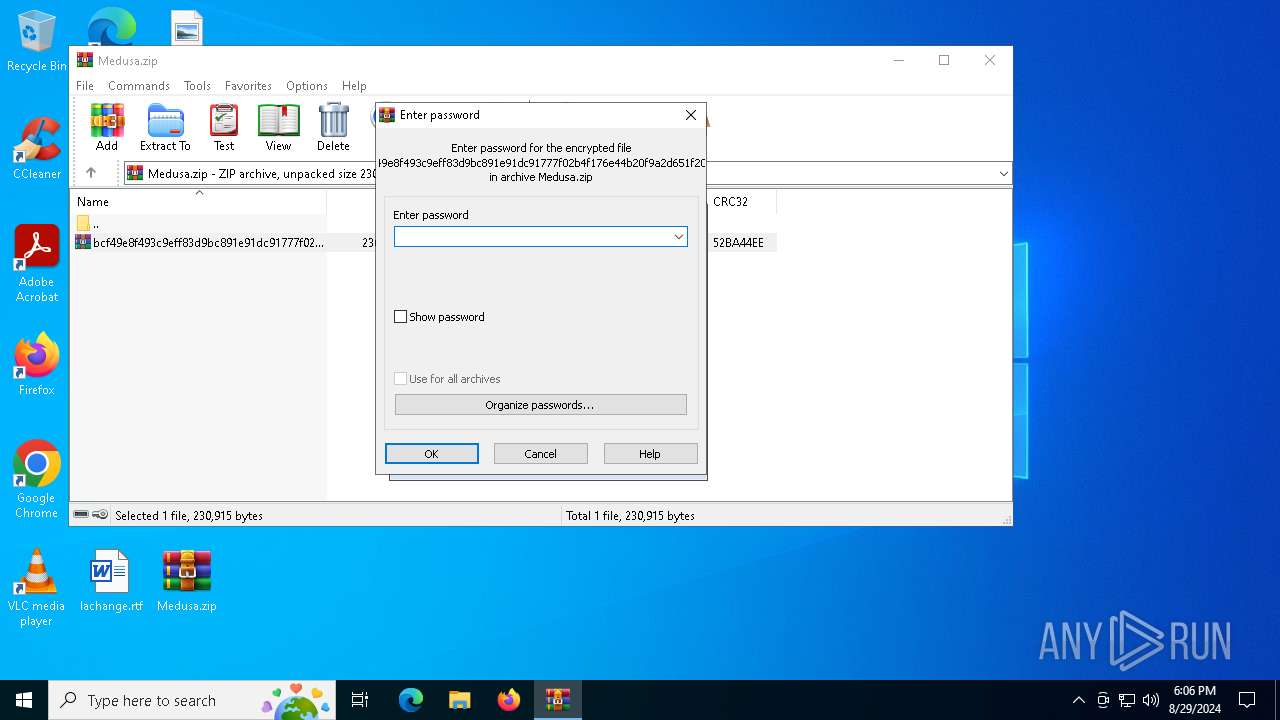
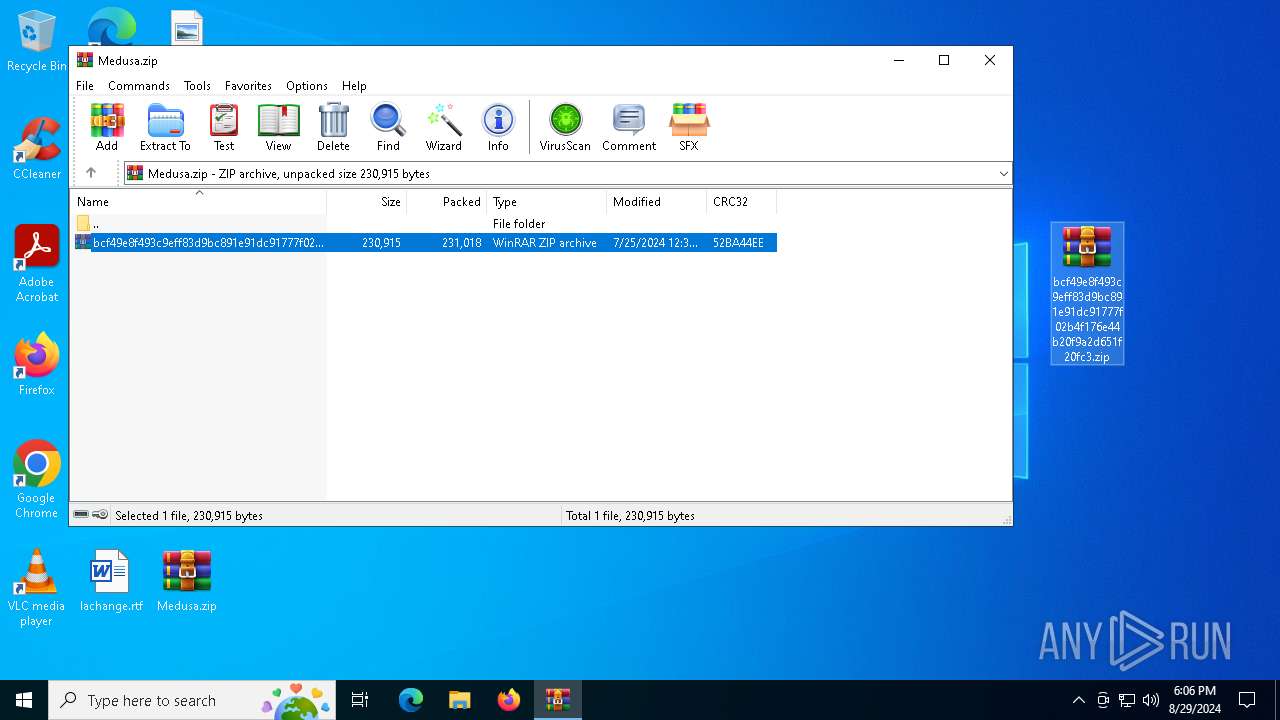
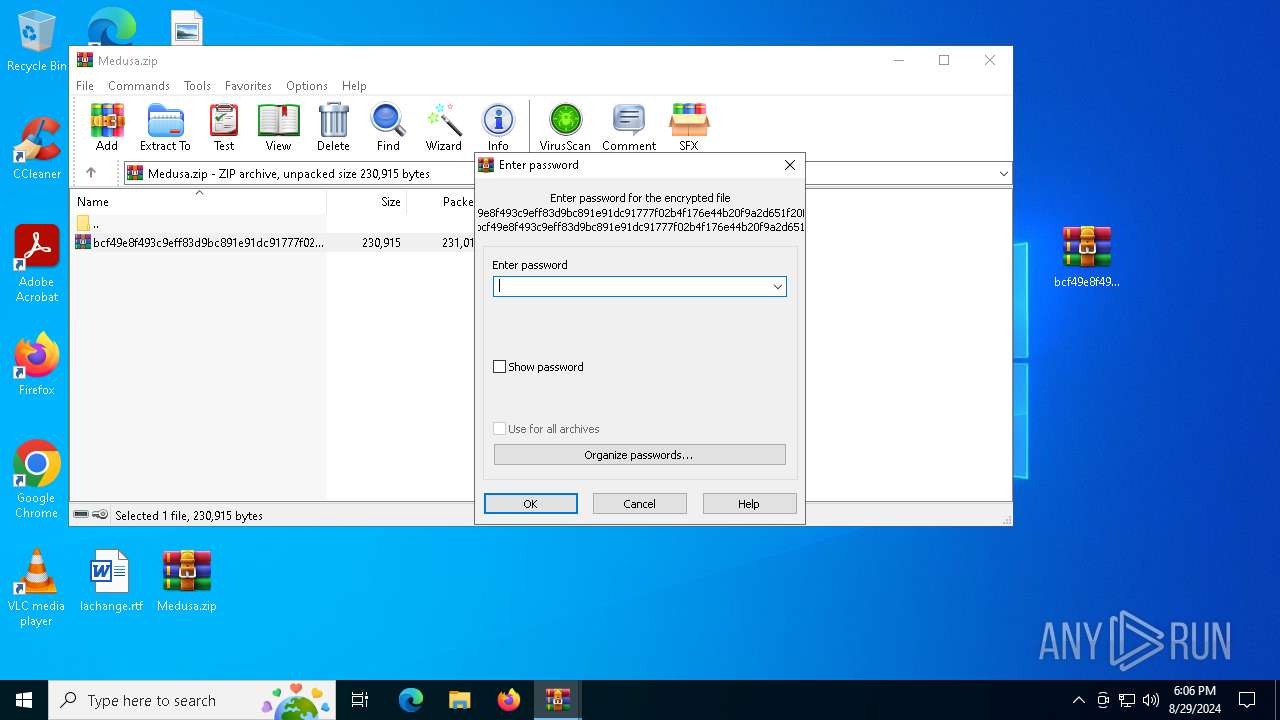
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 7CF7E0C8096FC09FFC0C8F9CACD413A6 |
| SHA1: | 208F78B20CEFCD16D21B70D8FE0361DB717A800D |
| SHA256: | 7689C0AEDCC48C6C508F1920BF451030A1B97D4A00E5D079A07780FD657ECABF |
| SSDEEP: | 3072:AYmwhjaKhxwaRNtCpEY9B2GUXnynvOA0n0g07JNYpjtjfN3vtA/WYznRQAb4F71v:AYaKXpYp1MnynWQ5YtTdvtAjzRQAI71v |
MALICIOUS
Changes the autorun value in the registry
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Starts NET.EXE for service management
- net.exe (PID: 4576)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Deletes shadow copies
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
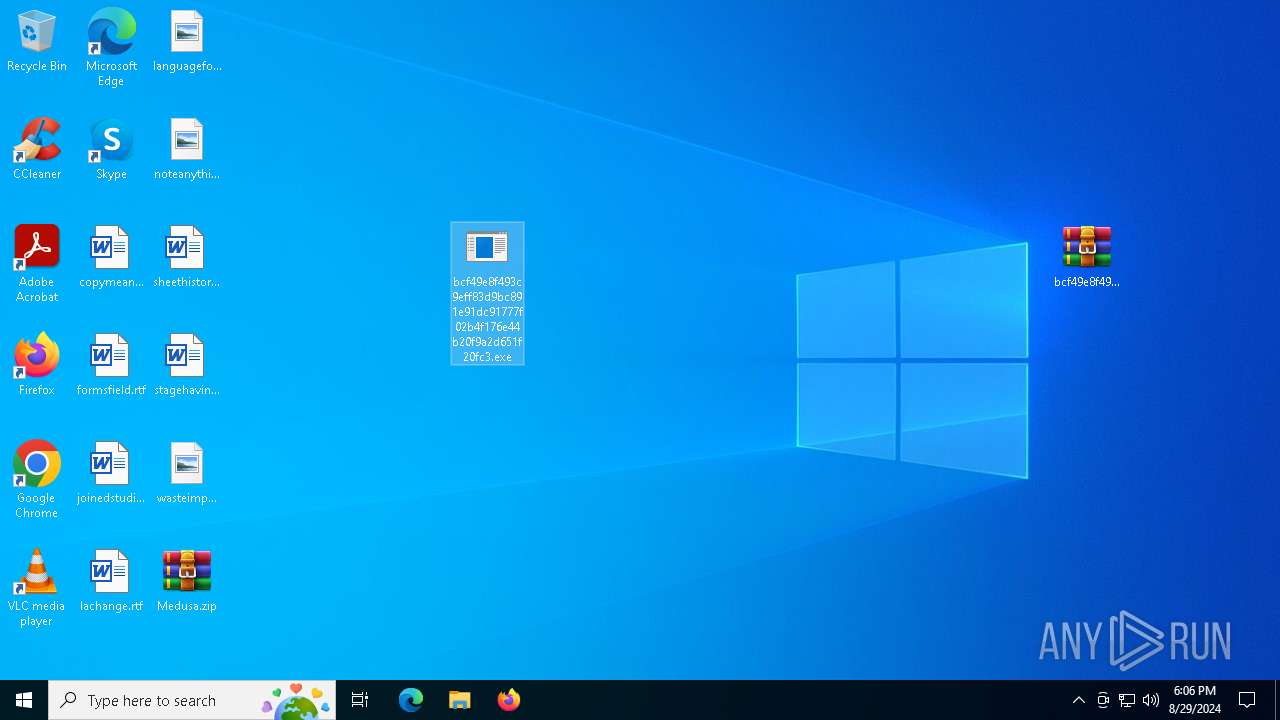
Renames files like ransomware
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
MEDUSALOCKER has been detected (YARA)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Starts CMD.EXE for self-deleting
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3448)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Reads the date of Windows installation
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Reads security settings of Internet Explorer
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
- ShellExperienceHost.exe (PID: 6748)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Starts NET.EXE to manage network resources
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
- net.exe (PID: 4576)
Application launched itself
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
Starts POWERSHELL.EXE for commands execution
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Executes as Windows Service
- VSSVC.exe (PID: 6752)
Uses ICACLS.EXE to modify access control lists
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Write to the desktop.ini file (may be used to cloak folders)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Creates file in the systems drive root
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2248)
Hides command output
- cmd.exe (PID: 2248)
Starts CMD.EXE for commands execution
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 3448)
- WinRAR.exe (PID: 1156)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Manual execution by a user
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
- WinRAR.exe (PID: 1156)
- notepad.exe (PID: 4524)
- Taskmgr.exe (PID: 4540)
- Taskmgr.exe (PID: 4284)
Process checks computer location settings
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Reads the computer name
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
- ShellExperienceHost.exe (PID: 6748)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1156)
Checks supported languages
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 2588)
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
- ShellExperienceHost.exe (PID: 6748)
Reads the machine GUID from the registry
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2036)
Creates files in the program directory
- bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe (PID: 3980)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4524)
- WMIC.exe (PID: 5552)
- Taskmgr.exe (PID: 4284)
Checks proxy server information
- slui.exe (PID: 3900)
Reads the software policy settings
- slui.exe (PID: 4164)
- slui.exe (PID: 3900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:07:25 12:36:36 |
| ZipCRC: | 0x52ba44ee |
| ZipCompressedSize: | 231018 |
| ZipUncompressedSize: | 230915 |
| ZipFileName: | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.zip |
Total processes
161
Monitored processes
26
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2036 | powershell -command "Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2112 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2248 | "C:\WINDOWS\system32\cmd.exe" /c timeout 1 && del "C:\Users\admin\Desktop\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe" >> NUL | C:\Windows\SysWOW64\cmd.exe | — | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2588 | "C:\Users\admin\Desktop\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe" | C:\Users\admin\Desktop\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Medusa.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3900 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\Desktop\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe" | C:\Users\admin\Desktop\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
95 200
Read events
75 679
Write events
9 794
Delete events
9 727
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Medusa.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1156) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
5
Suspicious files
1 655
Text files
85
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | C:\$WinREAgent\Backup\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 3980 | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | C:\$WinREAgent\Backup\Winre.wim.code | — | |
MD5:— | SHA256:— | |||
| 2036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2elikuos.4u1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3980 | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | \\?\Volume{2f5c5e73-85a9-11eb-90a8-9a9b76358421}\Recovery\WindowsRE\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 3980 | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | \\?\Volume{2f5c5e73-85a9-11eb-90a8-9a9b76358421}\Recovery\WindowsRE\Winre.wim.code | — | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3448.9218\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.zip | compressed | |
MD5:60476222658CD166930F43FFF43EE86D | SHA256:0B01BE4D105FCB10C34441407675FF564E2F2612ED847675539D17A39CB7FF3F | |||
| 2036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uza0tv0s.xph.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1156 | WinRAR.exe | C:\Users\admin\Desktop\bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | executable | |
MD5:2979ED84C4CA3DEB2924BD1F26BF88BD | SHA256:BCF49E8F493C9EFF83D9BC891E91DC91777F02B4F176E44B20F9A2D651F20FC3 | |||
| 3980 | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | C:\$WinREAgent\Backup\location.txt | binary | |
MD5:6AC5A6270E4A1E6923081D40AFBA1300 | SHA256:7693B9F53991EE97343A980550A2A9B2F613FAB5BCDB1C3915057B1FB85091F9 | |||
| 3980 | bcf49e8f493c9eff83d9bc891e91dc91777f02b4f176e44b20f9a2d651f20fc3.exe | \\?\Volume{2f5c5e73-85a9-11eb-90a8-9a9b76358421}\$RECYCLE.BIN\S-1-5-21-1693682860-607145093-2874071422-1001\!!!HOW_TO_DECRYPT!!!.txt | binary | |
MD5:5874A3EF6050BCCBE1808CE15B7AFF0A | SHA256:A838BC92D4D1FF8CC1F8AA1C2DE2A6A15B43486292B248D7669459A97AB3E711 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
28
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1280 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4344 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4344 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2400 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4316 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1280 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4344 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |