| File name: | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex |
| Full analysis: | https://app.any.run/tasks/914c7870-1047-4827-a9e3-5c60908b681f |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | June 10, 2025, 01:30:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 17 sections |
| MD5: | 28DDD0898103E5F95F320EAD1B5DE88F |
| SHA1: | ECEDC4C1EA662404236ACB1D55B3DD8E0B8D25B9 |
| SHA256: | 7683382B9CD94FB17AB6EAF24D52EE9DE6887C451FC276FA077758B8086BC082 |
| SSDEEP: | 98304:EFG9Zwo4w8G3zWsFwK++tQImHK9bz5uzR9VRFaipBz8dipBv8jhcQHrA6D3Z++nk:zj++nfb8B1dzE0bd+qrP |
MALICIOUS
QUASAR mutex has been found
- 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe (PID: 7988)
SUSPICIOUS
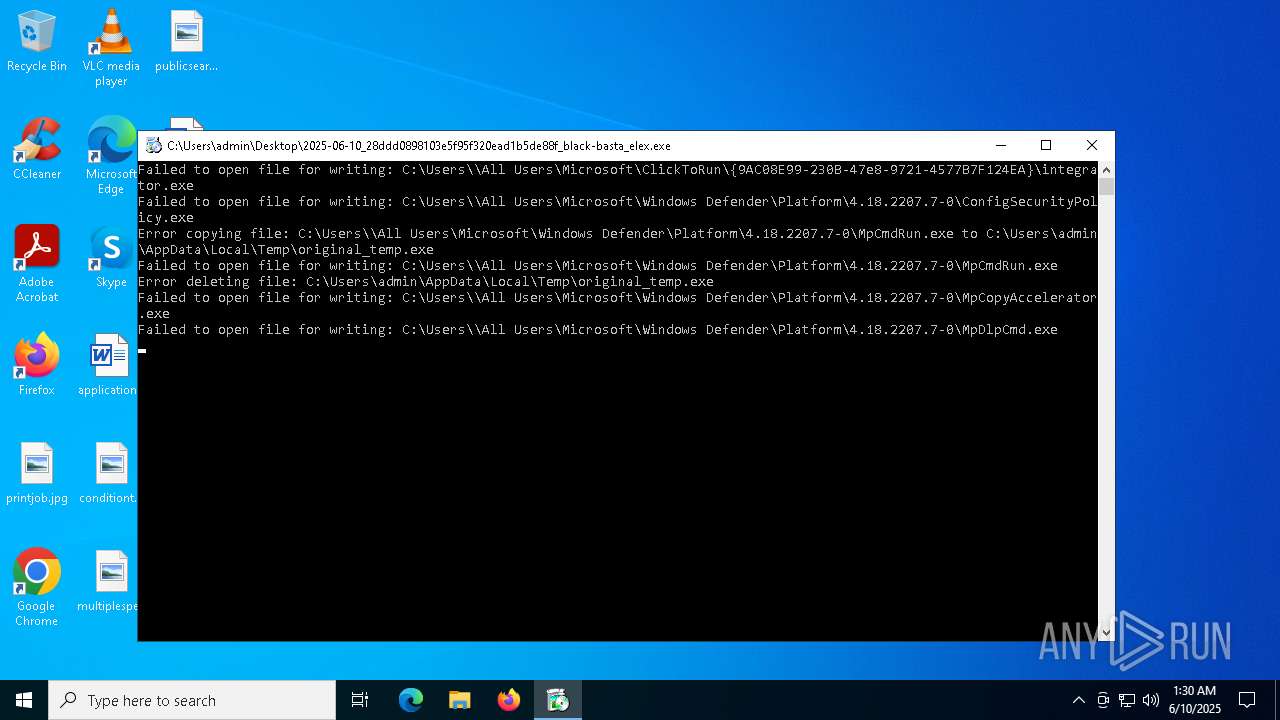
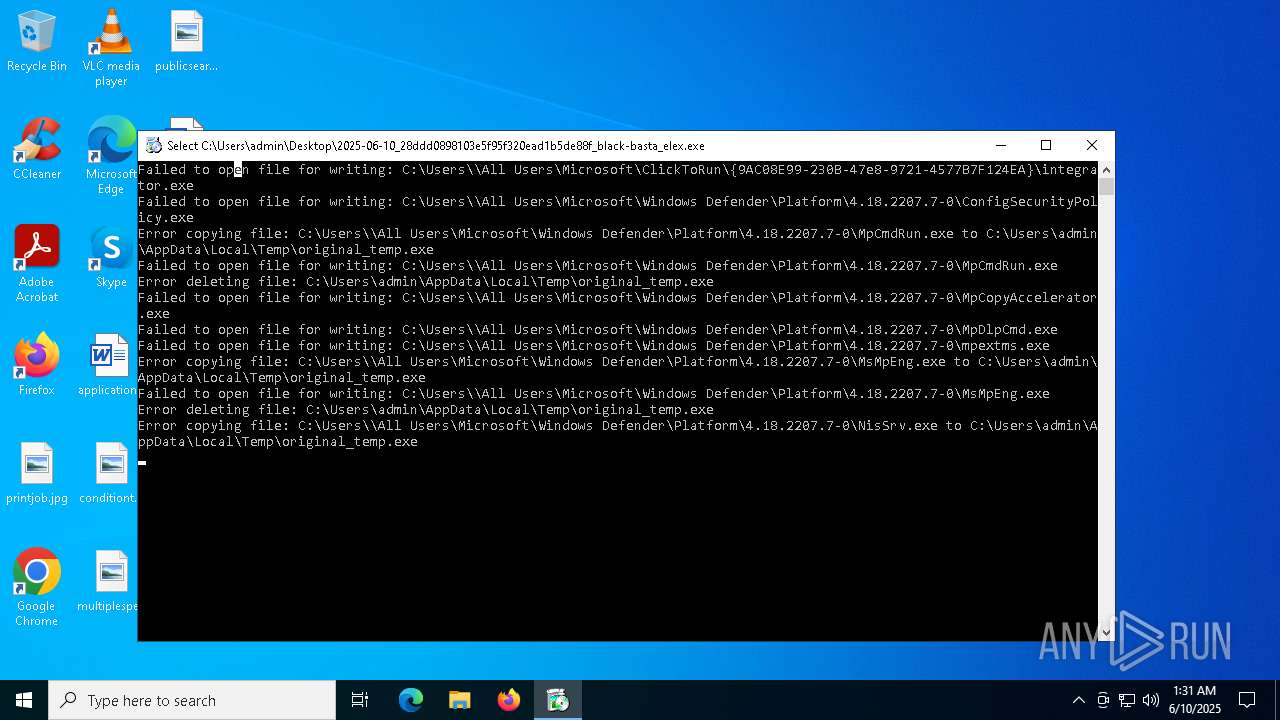
Process drops legitimate windows executable
- 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe (PID: 7988)
Executable content was dropped or overwritten
- 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe (PID: 7988)
INFO
Checks supported languages
- 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe (PID: 7988)
Create files in a temporary directory
- 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe (PID: 7988)
The sample compiled with english language support
- 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe (PID: 7988)
Checks proxy server information
- slui.exe (PID: 1244)
Reads the software policy settings
- slui.exe (PID: 1244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.3) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:31 09:13:09+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.32 |
| CodeSize: | 864256 |
| InitializedDataSize: | 1233408 |
| UninitializedDataSize: | 9728 |
| EntryPoint: | 0x12d0 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
127
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1244 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7988 | "C:\Users\admin\Desktop\2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe" | C:\Users\admin\Desktop\2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 404
Read events
3 404
Write events
0
Delete events
0
Modification events
Executable files
69
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Temp\RCX885.tmp | executable | |
MD5:67121B1924060177DDBD2C48FD8F0732 | SHA256:8039D7390C345EFF150288C208A8C82BC8592B25032E641CE64DF5467EB95CDB | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncConfig.exe | executable | |
MD5:9A55FB56E5201B6B0D45896D864784C9 | SHA256:1DC522443011E94B092BC6B73F6B49DE1538D674101EF6E2B57159456F5B49CC | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Temp\original_temp.exe | executable | |
MD5:394DEEEF3E5FFE6C77A9CDA1832361BB | SHA256:37DCEC7509B0803F2BBA453845ED67FDBAA15771F8A60FC11F9082FD2A64BD23 | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | executable | |
MD5:417C9183EB9A6A3CD85F0E68B7B4A6AA | SHA256:7A10A6AED24725AD7DA2DBFEBE15DCA6795927A5CF02C929A3060871A61F9F6E | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Temp\RCX8F3.tmp | executable | |
MD5:67121B1924060177DDBD2C48FD8F0732 | SHA256:8039D7390C345EFF150288C208A8C82BC8592B25032E641CE64DF5467EB95CDB | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Temp\virus_temp.exe | executable | |
MD5:28DDD0898103E5F95F320EAD1B5DE88F | SHA256:7683382B9CD94FB17AB6EAF24D52EE9DE6887C451FC276FA077758B8086BC082 | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncHelper.exe | executable | |
MD5:F804C5D4C5A2C300AA8877C1D395F4DB | SHA256:9ACD87408B707B55BC5C8A8BB9BFC4035C0E675FD7DDBC5A94AC78198F6AC670 | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Temp\RCXA0E.tmp | executable | |
MD5:67121B1924060177DDBD2C48FD8F0732 | SHA256:8039D7390C345EFF150288C208A8C82BC8592B25032E641CE64DF5467EB95CDB | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Temp\RCX101D.tmp | executable | |
MD5:67121B1924060177DDBD2C48FD8F0732 | SHA256:8039D7390C345EFF150288C208A8C82BC8592B25032E641CE64DF5467EB95CDB | |||
| 7988 | 2025-06-10_28ddd0898103e5f95f320ead1b5de88f_black-basta_elex.exe | C:\Users\admin\AppData\Local\Temp\RCXCD0.tmp | executable | |
MD5:DA78BC5B3F8E83E07534A1F90F4B5BE6 | SHA256:7FFBFB885F638E8125A7EEC46F7E869228722B4C6250629A22FAA01E041D46D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
58
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.32.140:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.32.140:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.65:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.4:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.64:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 400 | 40.126.32.133:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.32.140:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6544 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2104 | SIHClient.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
2104 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2064 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |