| URL: | https://gofile.io/d/BahfvM |
| Full analysis: | https://app.any.run/tasks/1efce79a-d1eb-4b0a-958a-6786a38cb8c7 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | July 12, 2020, 19:18:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 21242476801FC6F55296859DEE06BD02 |
| SHA1: | D324BF52FAF8170E59648DEF4E32FBFD52E39A74 |
| SHA256: | 7613B4B4A16B7DA7E18D39D50755409973A23606463027894A87004DF06C53FF |
| SSDEEP: | 3:N8rxL1ENQ:2ZqQ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3488)
- Orcus.Server.Patched.exe (PID: 1884)
- Orcus.Administration.exe (PID: 4008)
Application was dropped or rewritten from another process
- Orcus.Server.Patched.exe (PID: 1884)
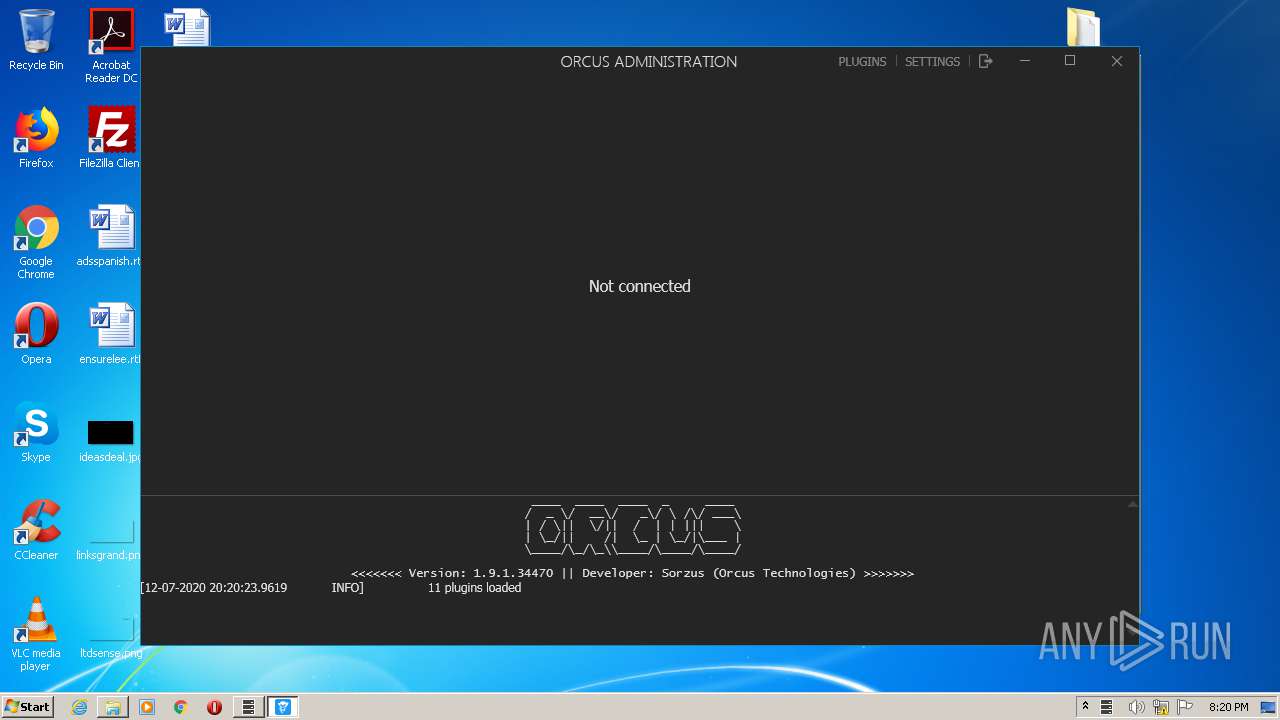
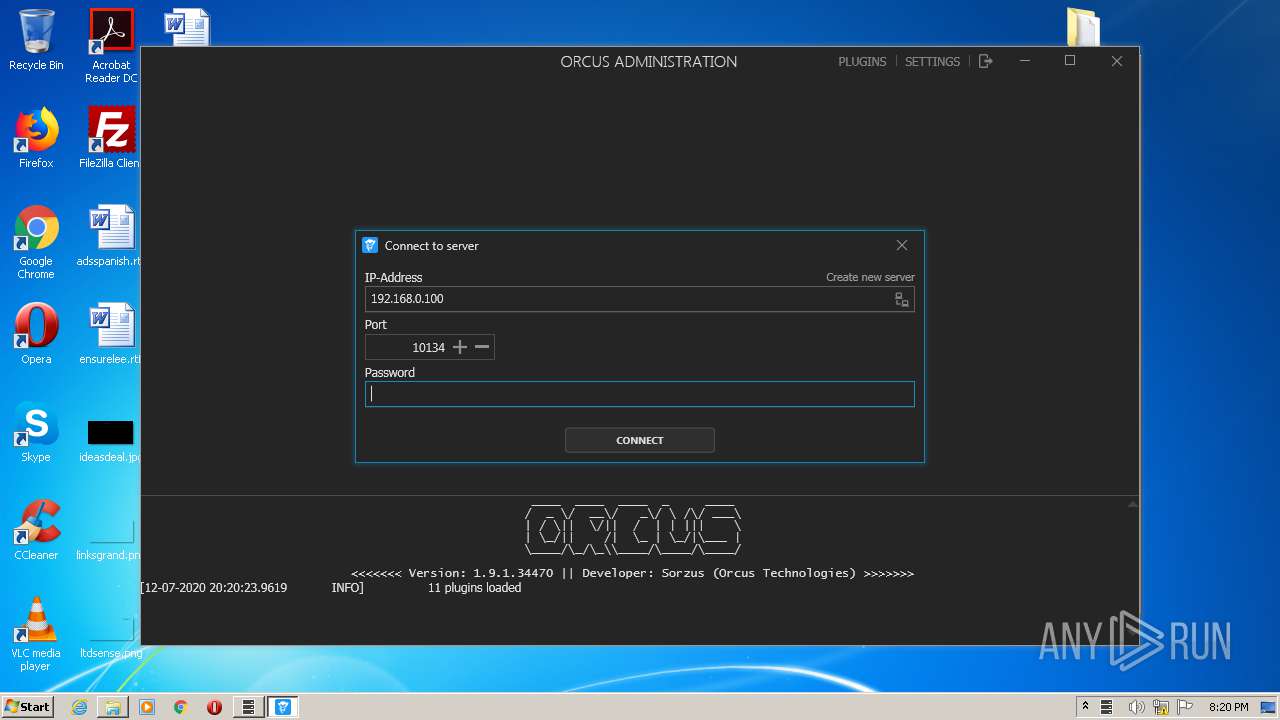
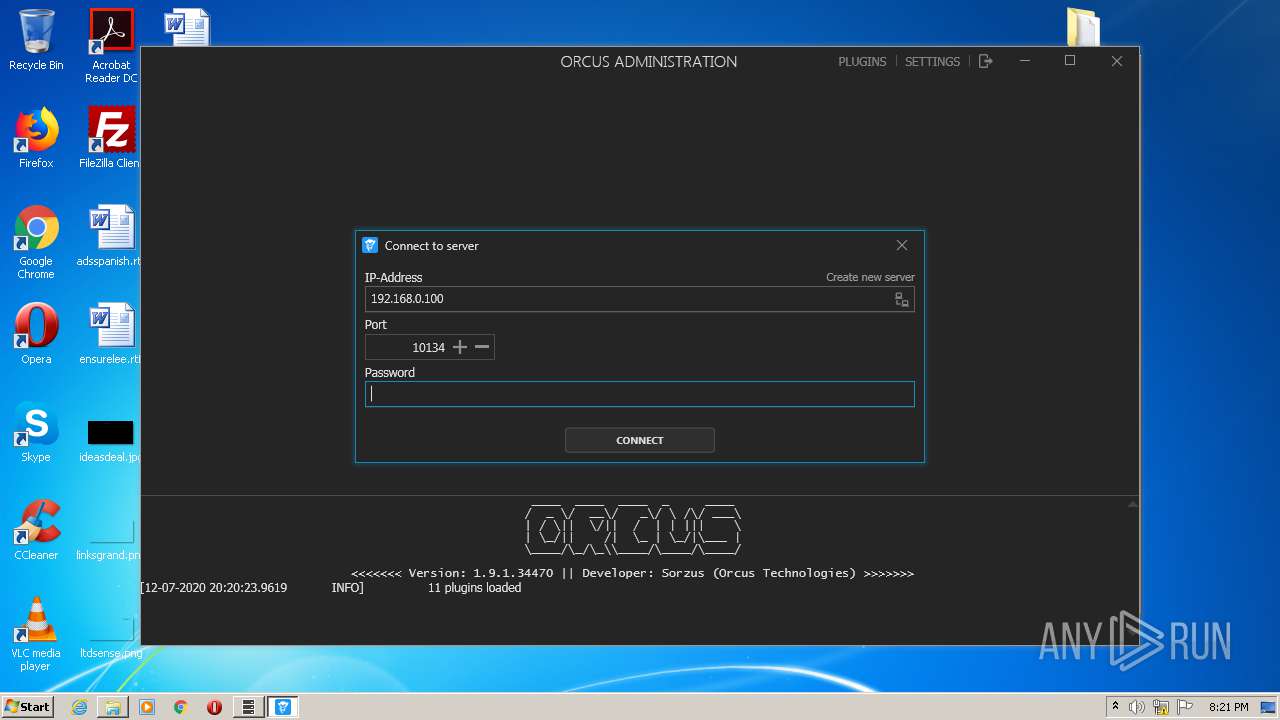
ORCUS was detected
- Orcus.Administration.exe (PID: 4008)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2516)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2868)
- Orcus.Server.Patched.exe (PID: 1884)
Creates files in the user directory
- Orcus.Server.Patched.exe (PID: 1884)
Reads Internet Cache Settings
- Orcus.Server.Patched.exe (PID: 1884)
- Orcus.Administration.exe (PID: 4008)
Creates files in the program directory
- Orcus.Server.Patched.exe (PID: 1884)
Reads Environment values
- Orcus.Server.Patched.exe (PID: 1884)
- Orcus.Administration.exe (PID: 4008)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1724)
- iexplore.exe (PID: 4072)
- chrome.exe (PID: 2516)
Application launched itself
- iexplore.exe (PID: 1724)
- chrome.exe (PID: 2516)
Changes internet zones settings
- iexplore.exe (PID: 1724)
Reads internet explorer settings
- iexplore.exe (PID: 4072)
Creates files in the user directory
- iexplore.exe (PID: 4072)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1724)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2868)
Manual execution by user
- chrome.exe (PID: 2516)
- Orcus.Server.Patched.exe (PID: 1884)
- Orcus.Administration.exe (PID: 4008)
Reads the hosts file
- chrome.exe (PID: 2556)
- chrome.exe (PID: 2516)
Changes settings of System certificates
- iexplore.exe (PID: 1724)
Reads settings of System Certificates
- iexplore.exe (PID: 1724)
- iexplore.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
74
Monitored processes
34
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1405758702396213687 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3852 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9001458901902875801 --mojo-platform-channel-handle=3924 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4699618196877491901 --mojo-platform-channel-handle=3412 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4400193180038098818 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16922216769968491767 --mojo-platform-channel-handle=4468 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15951139275695570994 --mojo-platform-channel-handle=3148 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6037052414341948513 --mojo-platform-channel-handle=3368 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1724 | "C:\Program Files\Internet Explorer\iexplore.exe" https://gofile.io/d/BahfvM | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,8238665998121417199,15365321144849971042,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1214499776199306570 --mojo-platform-channel-handle=1356 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
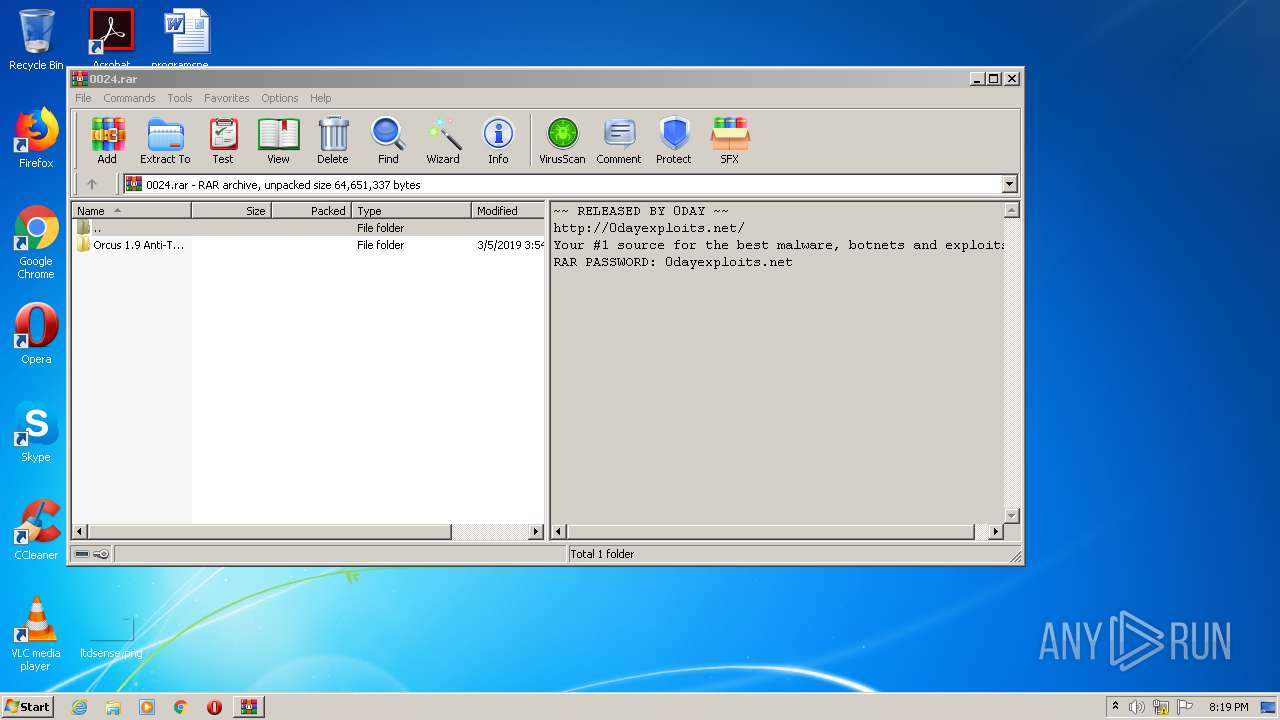
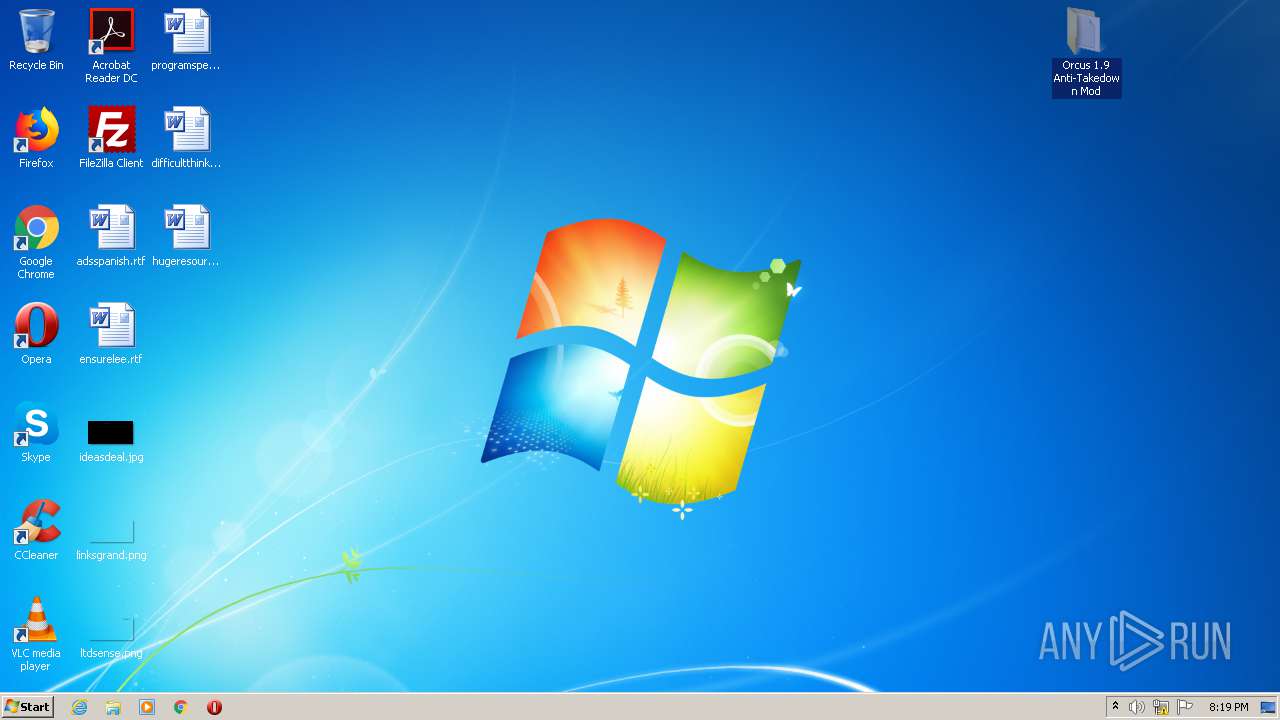
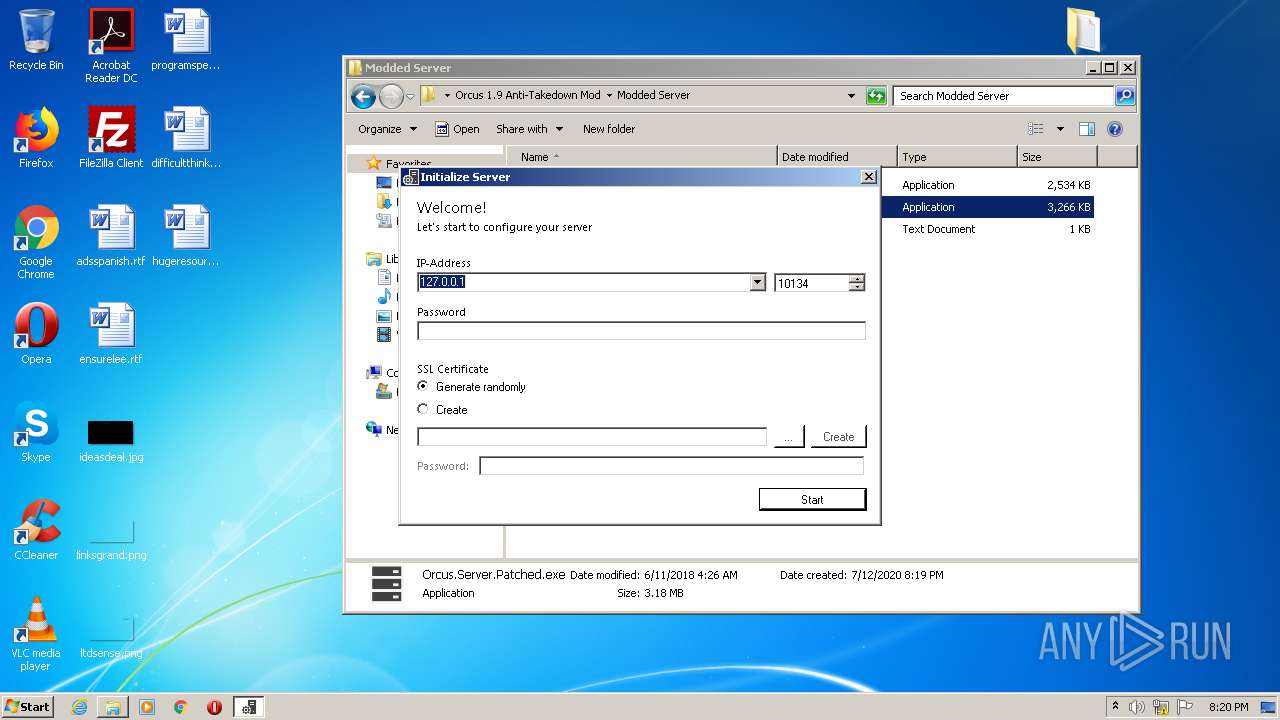
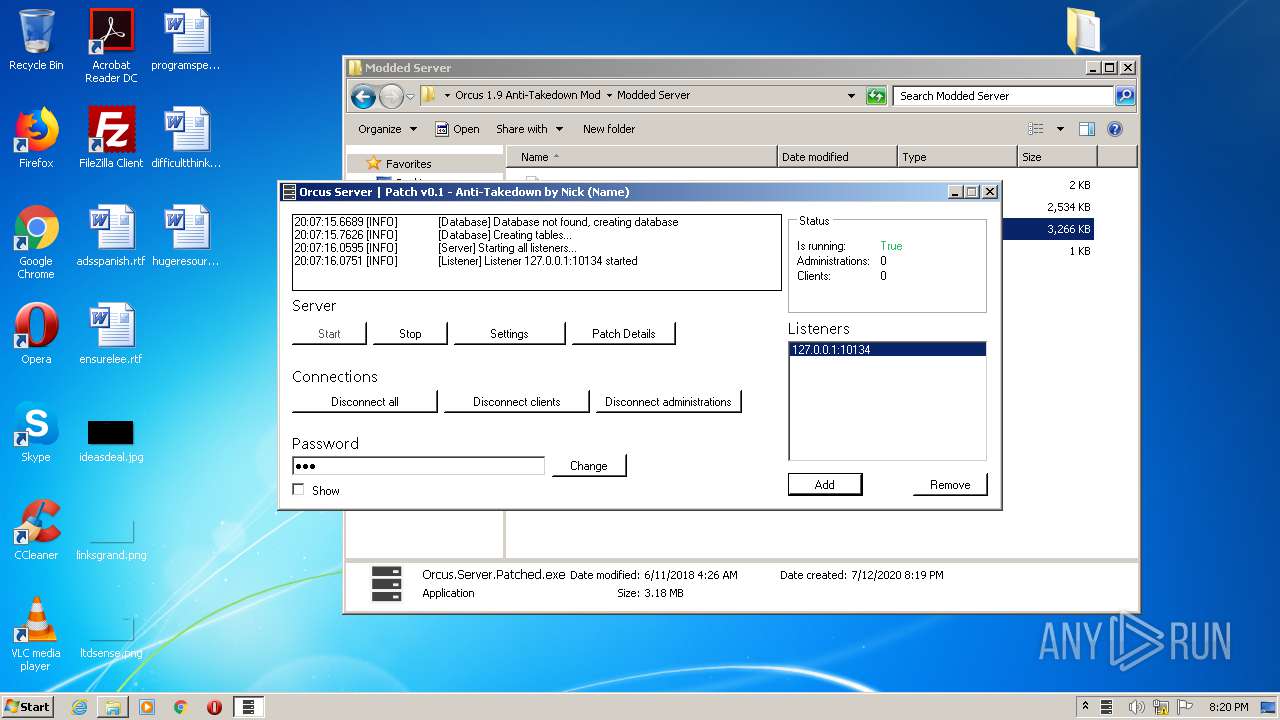
| 1884 | "C:\Users\admin\Desktop\Orcus 1.9 Anti-Takedown Mod\Modded Server\Orcus.Server.Patched.exe" | C:\Users\admin\Desktop\Orcus 1.9 Anti-Takedown Mod\Modded Server\Orcus.Server.Patched.exe | explorer.exe | ||||||||||||
User: admin Company: Orcus Technologies Integrity Level: MEDIUM Description: Orcus Server Exit code: 0 Version: 1.9.1 Modules
| |||||||||||||||
Total events
2 602
Read events
2 288
Write events
277
Delete events
37
Modification events
| (PID) Process: | (4072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1395247458 | |||
| (PID) Process: | (1724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30824577 | |||
| (PID) Process: | (1724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
51
Suspicious files
143
Text files
371
Unknown types
74
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6D18.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6D29.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6F2E.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6F2F.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6F30.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6F31.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | der | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B63B2070F62BD5F36E309FAED531189 | der | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:— | SHA256:— | |||
| 4072 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B63B2070F62BD5F36E309FAED531189 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
95
DNS requests
56
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4072 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
4072 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
4072 | iexplore.exe | GET | 200 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
4072 | iexplore.exe | GET | 200 | 2.16.107.43:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgP%2FkJC6vIKeuwdiMhYkmBXlJg%3D%3D | unknown | der | 527 b | whitelisted |
4072 | iexplore.exe | GET | 200 | 2.16.107.80:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
4072 | iexplore.exe | GET | 200 | 2.16.107.43:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgRONazAeVbvveojcZVjfG8wZg%3D%3D | unknown | der | 527 b | whitelisted |
4072 | iexplore.exe | GET | 200 | 2.16.107.73:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
4072 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 471 b | whitelisted |
4072 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA%2FVhdRLfbN%2FXD5lO%2FSyJvc%3D | US | der | 279 b | whitelisted |
4072 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4072 | iexplore.exe | 2.16.107.73:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | suspicious |
4072 | iexplore.exe | 213.32.73.239:443 | gofile.io | OVH SAS | FR | unknown |
4072 | iexplore.exe | 2.16.107.80:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | suspicious |
4072 | iexplore.exe | 2.16.107.43:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | suspicious |
4072 | iexplore.exe | 216.58.212.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
4072 | iexplore.exe | 151.101.2.109:443 | cdn.jsdelivr.net | Fastly | US | suspicious |
4072 | iexplore.exe | 172.67.70.99:443 | cdn.buymeacoffee.com | — | US | unknown |
4072 | iexplore.exe | 104.22.51.93:443 | cdn.datatables.net | Cloudflare Inc | US | malicious |
4072 | iexplore.exe | 151.139.237.11:443 | cdn.rawgit.com | netDNA | US | suspicious |
4072 | iexplore.exe | 104.16.132.229:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
gofile.io |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
cdn.buymeacoffee.com |
| whitelisted |
cdn.datatables.net |
| whitelisted |
cdn.rawgit.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
Process | Message |
|---|---|
Orcus.Server.Patched.exe | Writing Key: Version=2
|
Orcus.Server.Patched.exe | Writing Key: WaitTimeout=30000
|
Orcus.Server.Patched.exe | Writing Key: MaxParallelTransfers=10
|
Orcus.Server.Patched.exe | Writing Key: RefreshServerIpPeriod=12
|
Orcus.Server.Patched.exe | Writing Key: MaxPluginCacheSize=0
|
Orcus.Server.Patched.exe | Writing Section: [CONFIG_FILE]
|
Orcus.Server.Patched.exe | Writing Key: CheckForDeadConnectionsTimeout=60000
|
Orcus.Server.Patched.exe | Writing Key: CheckForDeadConnectionsInterval=10000
|
Orcus.Server.Patched.exe | Writing Key: EnabledNamedPipe=true
|
Orcus.Server.Patched.exe | Writing Key: UseServerIpAddressIfOutOfRange=true
|