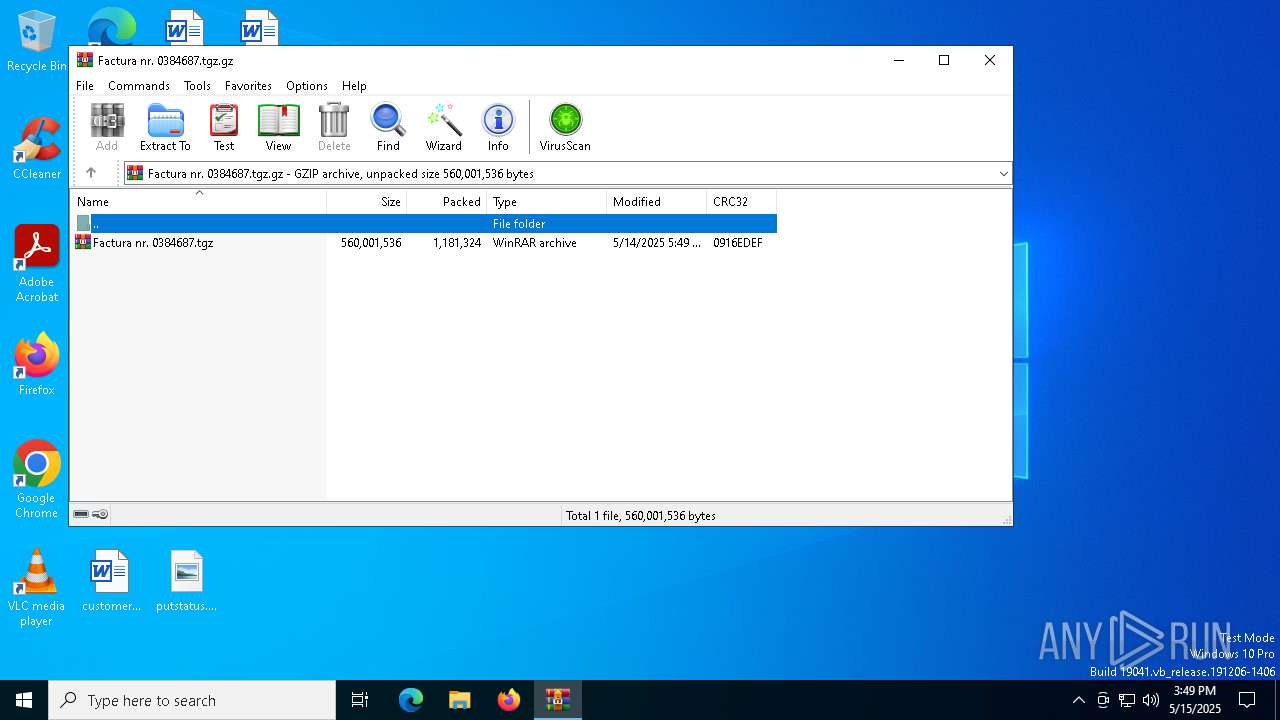
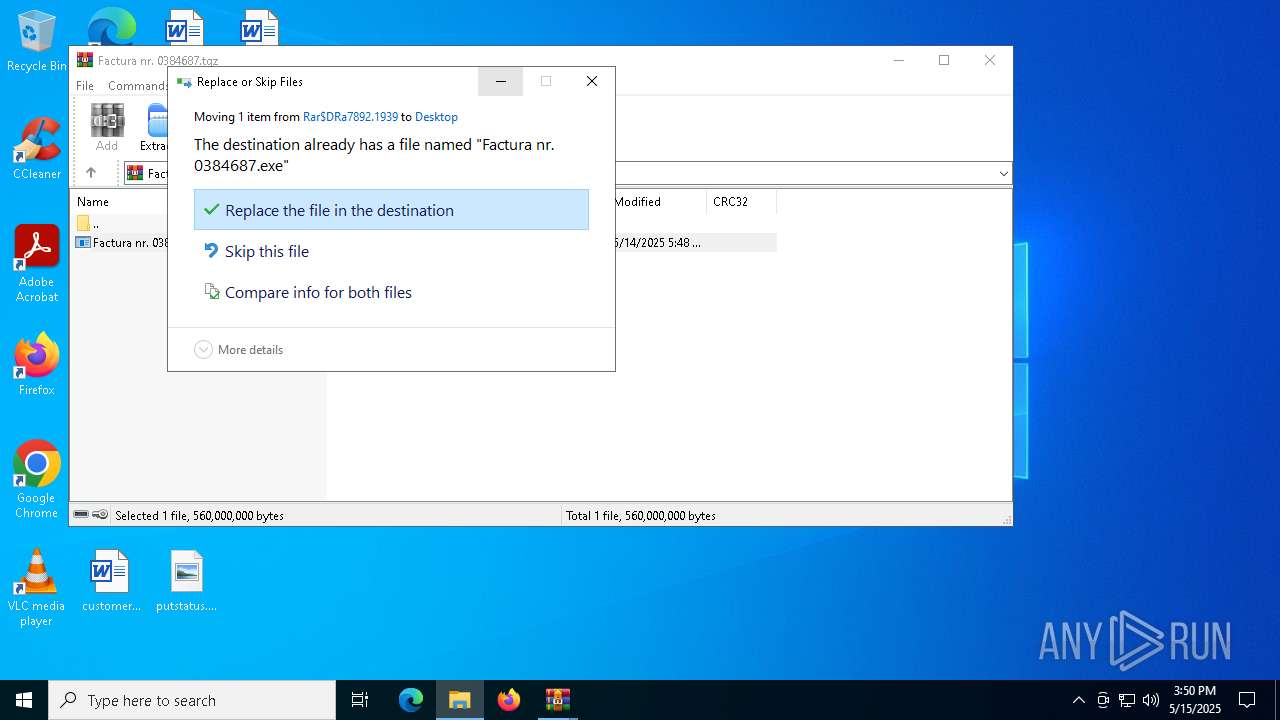
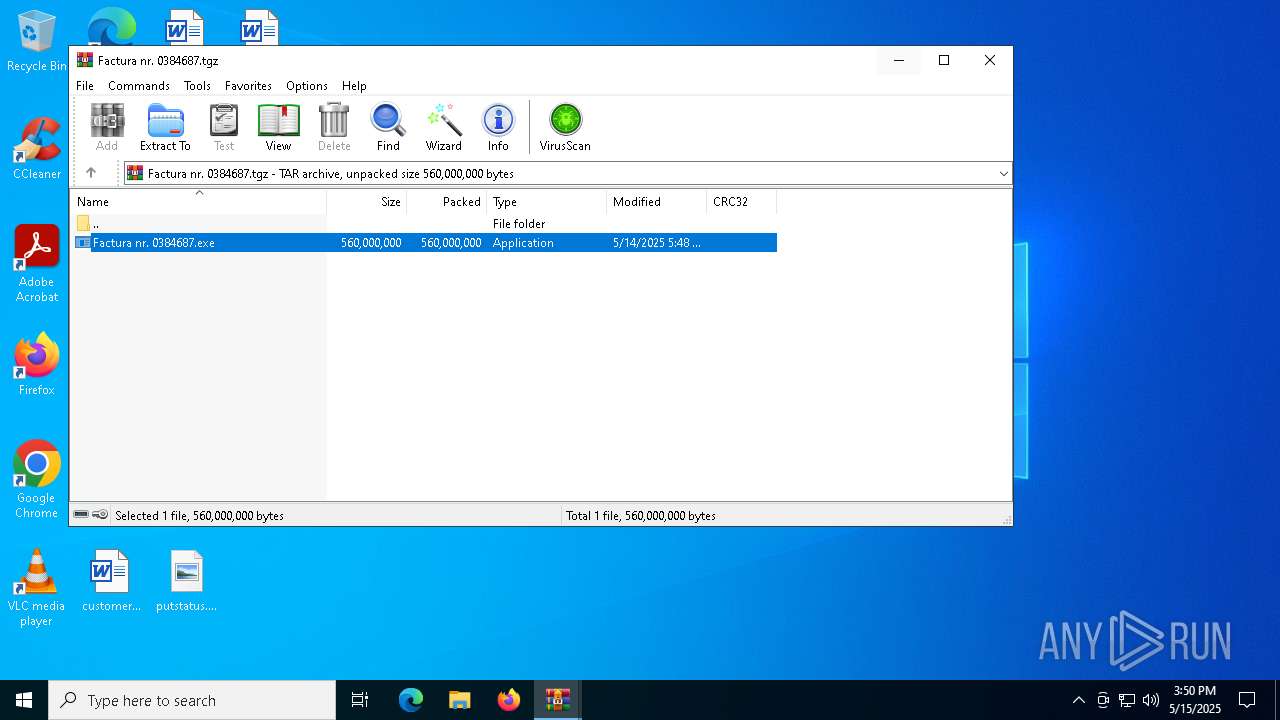
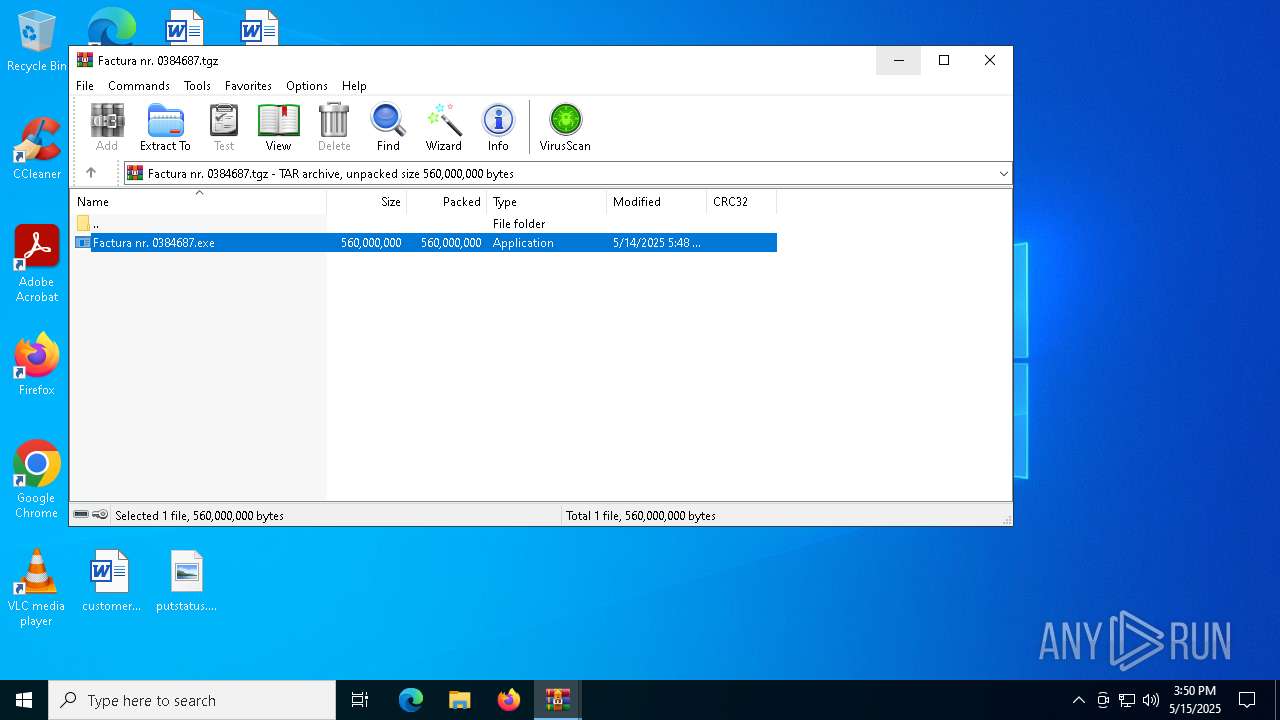
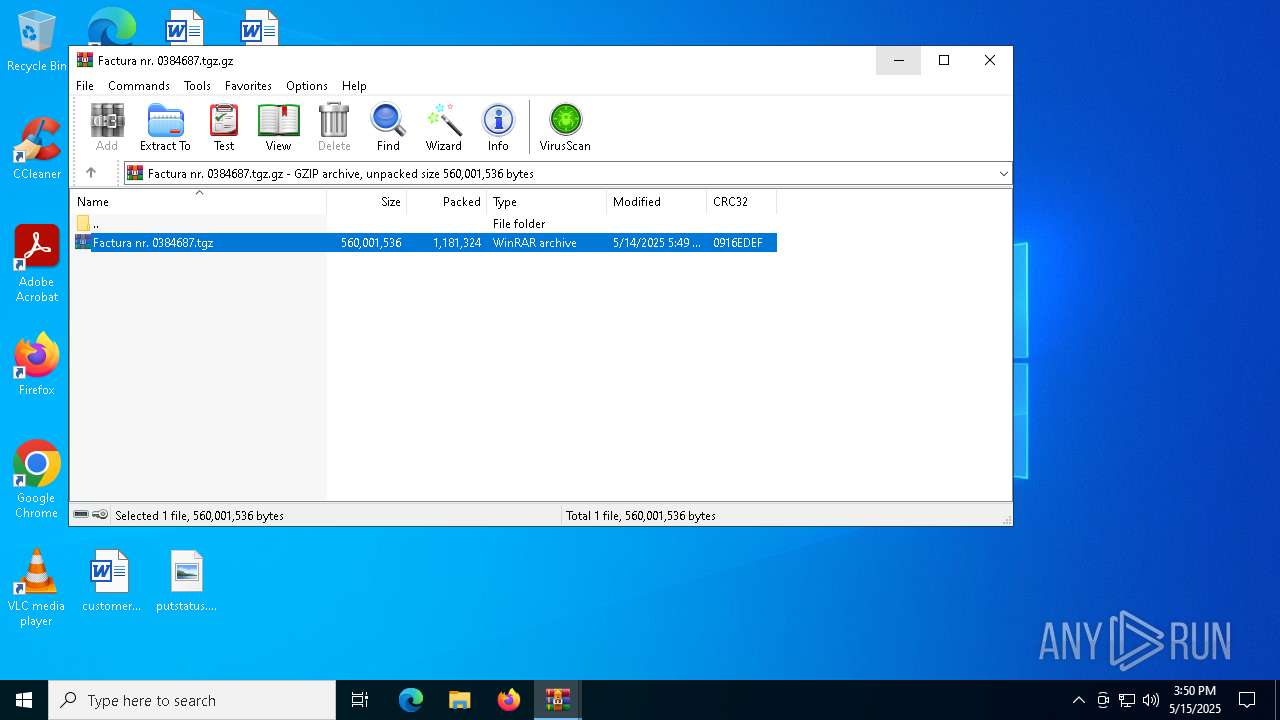
| File name: | Factura nr. 0384687.tgz |
| Full analysis: | https://app.any.run/tasks/66ac0447-131f-47b7-b5a4-40ace44ace4c |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 15, 2025, 15:49:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, last modified: Wed May 14 05:49:40 2025, from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 560001536 |
| MD5: | 2BF752091B2E9F2357EBB5FA529D565D |
| SHA1: | D18123175862F515E849FD4387F8B992B8EA15C8 |
| SHA256: | 75F03C9BE85735C86D5CB4576DDC4E90DE860546B0144DC61B4435942D530708 |
| SSDEEP: | 49152:ZCwoBUQlLdjX9iVDNsAGmrZdFiBeJQF5Xbgy2VAGhp9GseYKBcZ3:o1BUQhxIVDyJ2Fe58y2AGhOIucV |
MALICIOUS
Steals credentials from Web Browsers
- vbc.exe (PID: 4040)
Actions looks like stealing of personal data
- vbc.exe (PID: 4040)
AGENTTESLA has been detected (YARA)
- vbc.exe (PID: 4040)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 7344)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7344)
The process executes VB scripts
- Factura nr. 0384687.exe (PID: 7472)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- vbc.exe (PID: 4040)
The process connected to a server suspected of theft
- vbc.exe (PID: 4040)
Possible usage of Discord/Telegram API has been detected (YARA)
- vbc.exe (PID: 4040)
INFO
Manual execution by a user
- Factura nr. 0384687.exe (PID: 7472)
Reads the computer name
- Factura nr. 0384687.exe (PID: 7472)
- vbc.exe (PID: 4040)
Reads the machine GUID from the registry
- Factura nr. 0384687.exe (PID: 7472)
- vbc.exe (PID: 4040)
Reads the software policy settings
- slui.exe (PID: 7512)
- vbc.exe (PID: 4040)
- slui.exe (PID: 7148)
Checks supported languages
- vbc.exe (PID: 4040)
- Factura nr. 0384687.exe (PID: 7472)
.NET Reactor protector has been detected
- Factura nr. 0384687.exe (PID: 7472)
ULTRAVNC has been detected
- vbc.exe (PID: 4040)
Disables trace logs
- vbc.exe (PID: 4040)
Checks proxy server information
- vbc.exe (PID: 4040)
- slui.exe (PID: 7148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(4040) vbc.exe
Telegram-Tokens (1)7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg
Telegram-Info-Links
7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg
Get info about bothttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getMe
Get incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getUpdates
Get webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook?drop_pending_updates=true
Telegram-Tokens (1)7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg
Telegram-Info-Links
7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg
Get info about bothttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getMe
Get incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getUpdates
Get webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg
End-PointsendDoc
Args
Token7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg
End-PointsendDocument
Args
Telegram-Responses
oktrue
result
message_id2219
from
id7844826162
is_bottrue
first_nameAAR19 ❤️ Подарки ТГшки С ЛАЙКА СЮДА❤️ ОРИГИНАЛ❤️❤️
usernameRichTymelogs5Bot
chat
id6256200431
first_nameRam Info
usernameRichTymelog
typeprivate
date1747324250
document
file_nameadmin-DESKTOP-JGLLJLD 2025-05-15 15-50-50.html
mime_typeapplication/octet-stream
file_idBQACAgQAAxkDAAIIq2gmDVqFlXcN2QlJfM8kDr7hTwpQAAJYGQACqq4wUYcITOgCiVwINgQ
file_unique_idAgADWBkAAqquMFE
file_size423
captionNew PW Recovered!
Time: 05/15/2025 15:50:49
User Name: admin/DESKTOP-JGLLJLD
OSFullName: Microsoft Windows 10 Pro
CPU: Intel(R) Core(TM) i5-6400 CPU @ 2.70GHz
RAM: 4090.45 MB
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 2025:05:14 05:49:40+00:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | FAT filesystem (MS-DOS, OS/2, NT/Win32) |
Total processes
140
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4040 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | Factura nr. 0384687.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Version: 14.8.9037.0 Modules
ims-api(PID) Process(4040) vbc.exe Telegram-Tokens (1)7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg Telegram-Info-Links 7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg Get info about bothttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getMe Get incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getUpdates Get webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getWebhookInfo Delete webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook?drop_pending_updates=true (PID) Process(4040) vbc.exe Telegram-Tokens (1)7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg Telegram-Info-Links 7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg Get info about bothttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getMe Get incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getUpdates Get webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/getWebhookInfo Delete webhookhttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg/deleteWebhook?drop_pending_updates=true Telegram-Requests Token7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg End-PointsendDoc Args Token7844826162:AAHmkutzU62TUPvnEGO_jSKI8EsX0HUPGsg End-PointsendDocument Args Telegram-Responses oktrue result message_id2219 from id7844826162 is_bottrue first_nameAAR19 ❤️ Подарки ТГшки С ЛАЙКА СЮДА❤️ ОРИГИНАЛ❤️❤️ usernameRichTymelogs5Bot chat id6256200431 first_nameRam Info usernameRichTymelog typeprivate date1747324250 document file_nameadmin-DESKTOP-JGLLJLD 2025-05-15 15-50-50.html mime_typeapplication/octet-stream file_idBQACAgQAAxkDAAIIq2gmDVqFlXcN2QlJfM8kDr7hTwpQAAJYGQACqq4wUYcITOgCiVwINgQ file_unique_idAgADWBkAAqquMFE file_size423 captionNew PW Recovered!
Time: 05/15/2025 15:50:49
User Name: admin/DESKTOP-JGLLJLD
OSFullName: Microsoft Windows 10 Pro
CPU: Intel(R) Core(TM) i5-6400 CPU @ 2.70GHz
RAM: 4090.45 MB | |||||||||||||||
| 7148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7344 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Factura nr. 0384687.tgz.gz" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7472 | "C:\Users\admin\Desktop\Factura nr. 0384687.exe" | C:\Users\admin\Desktop\Factura nr. 0384687.exe | — | explorer.exe | |||||||||||
User: admin Company: VelocityForge Technologies Integrity Level: MEDIUM Description: ⚡ System Hyperion Titanium ⚡ Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 7480 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7512 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7892 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa7344.48808\Factura nr. 0384687.tgz" | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 322
Read events
5 292
Write events
30
Delete events
0
Modification events
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Factura nr. 0384687.tgz.gz | |||
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7344.48808\Factura nr. 0384687.tgz | — | |
MD5:— | SHA256:— | |||
| 7892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7892.544\Factura nr. 0384687.exe | — | |
MD5:— | SHA256:— | |||
| 7892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7892.1939\Factura nr. 0384687.exe | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
18
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8136 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8136 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.162:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5216 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
4040 | vbc.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
4040 | vbc.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
4040 | vbc.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |