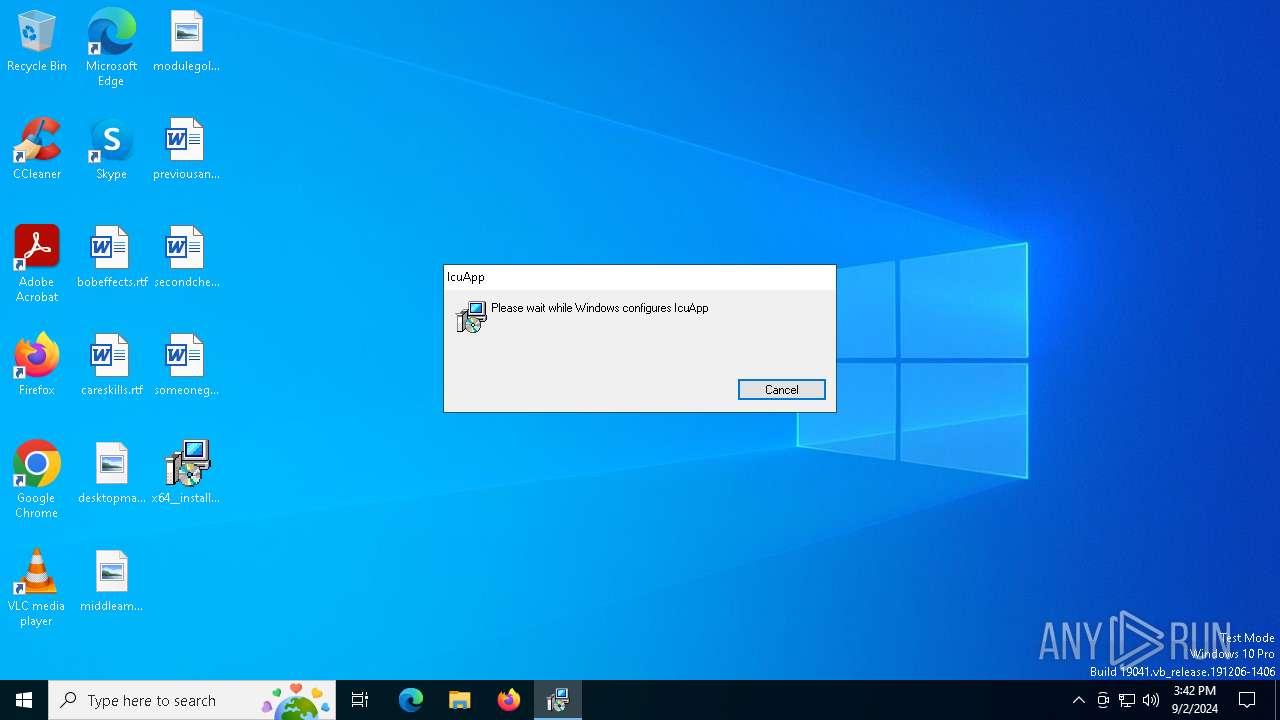
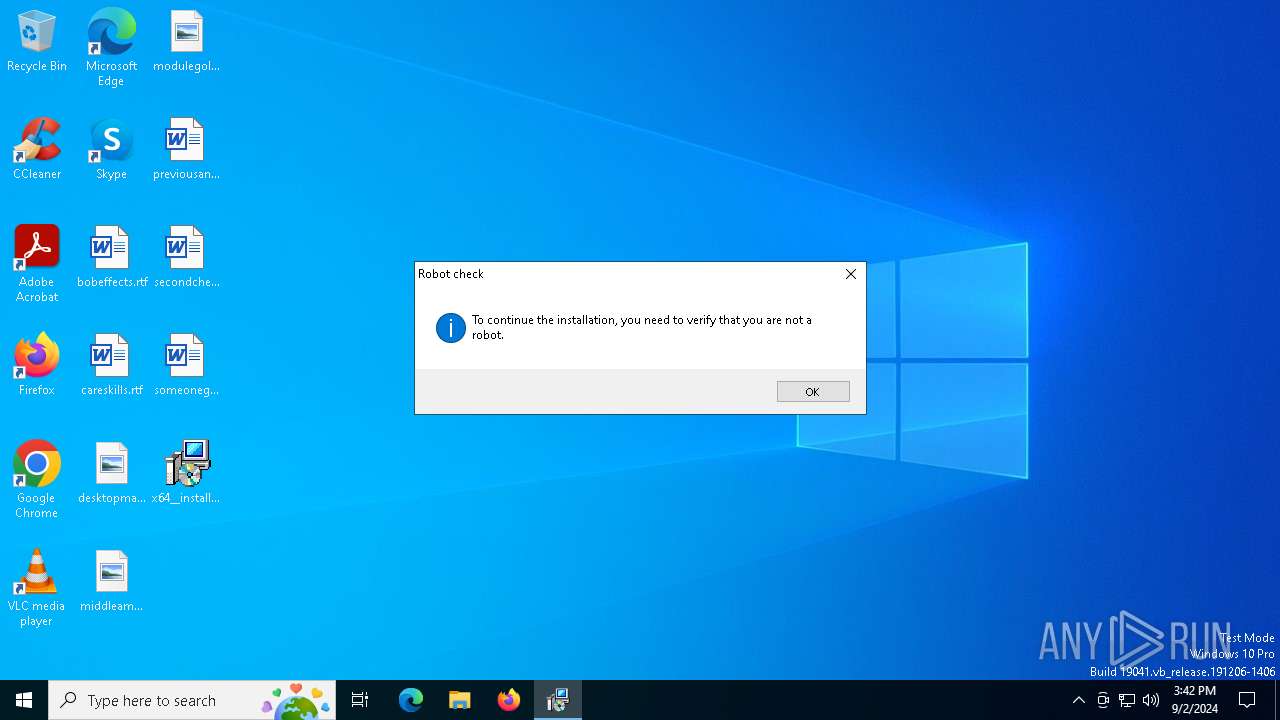
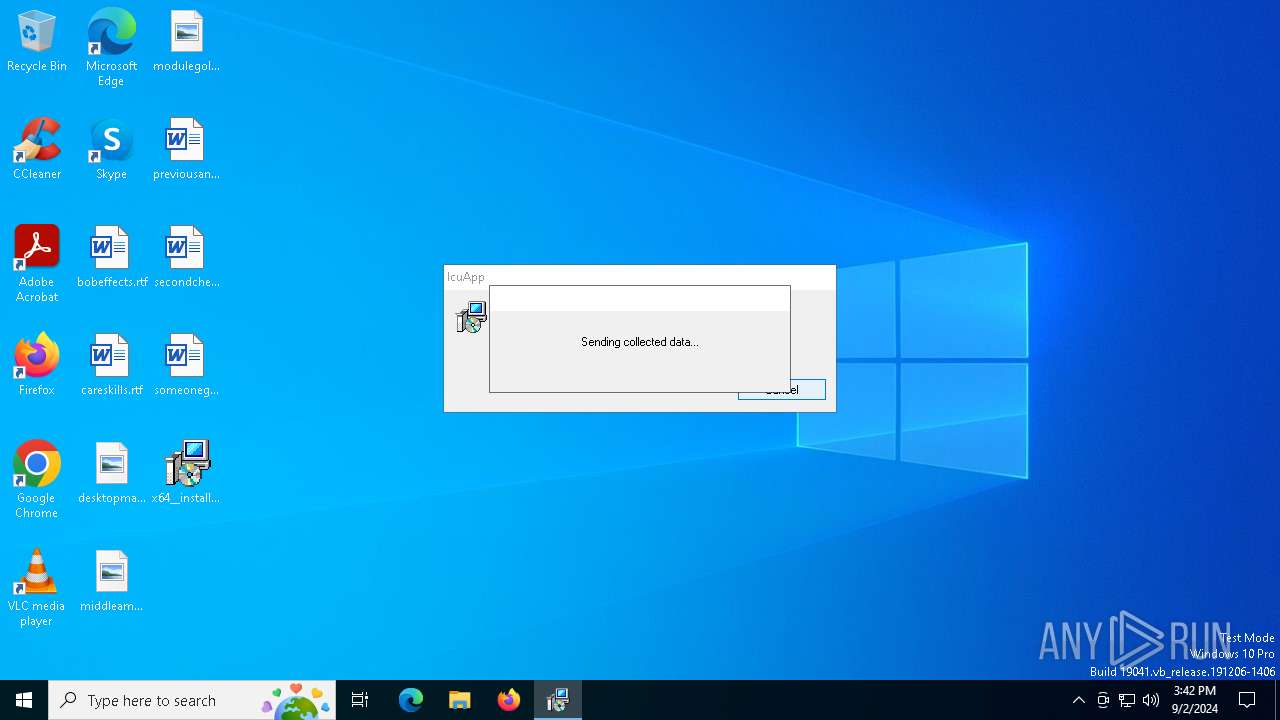
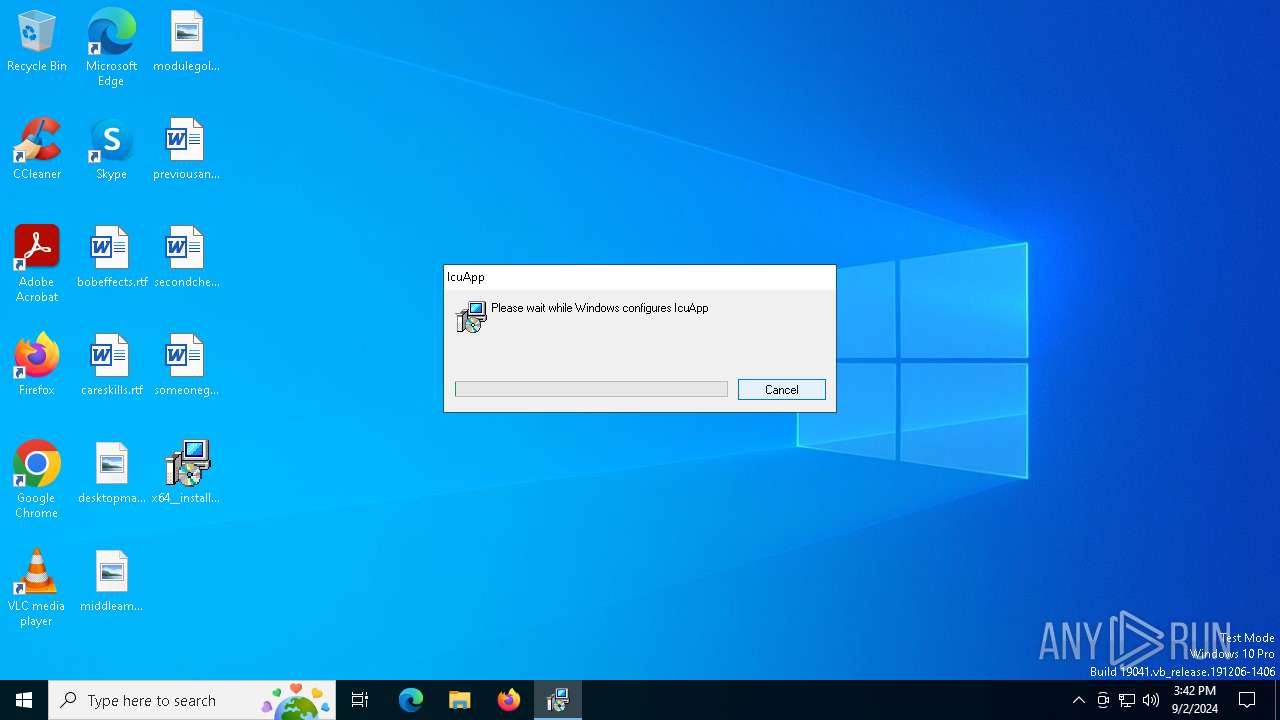
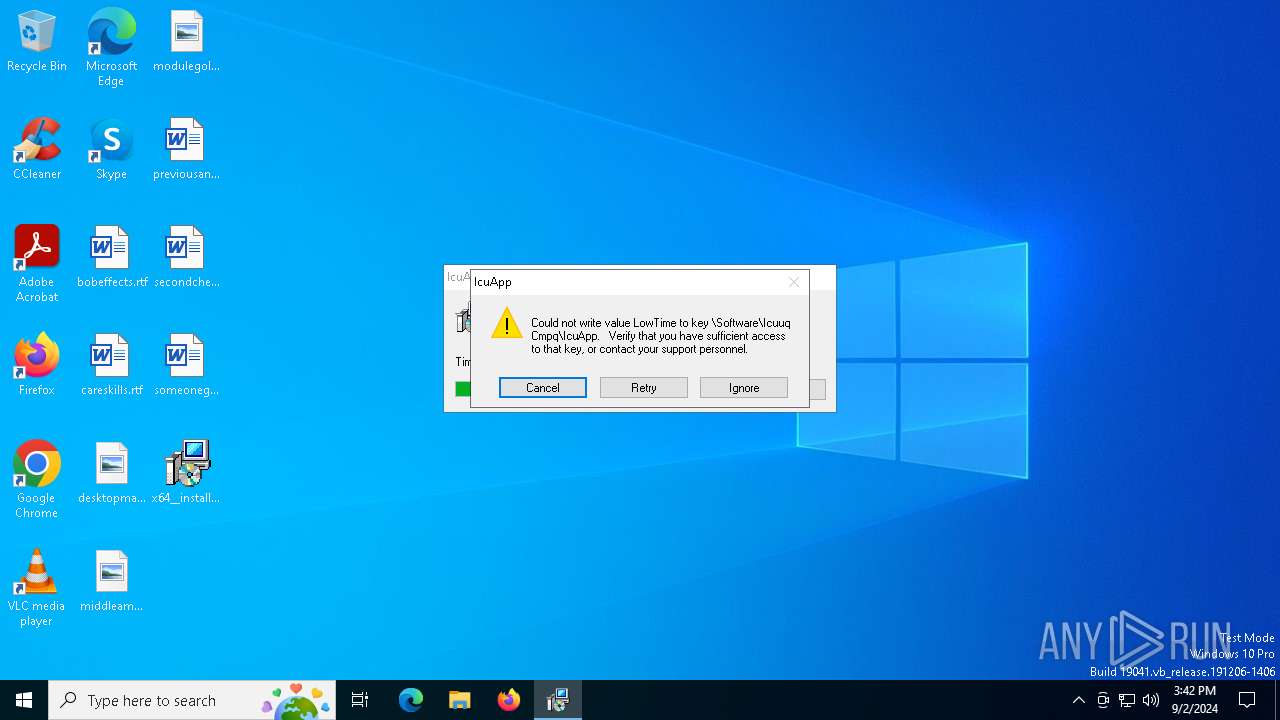
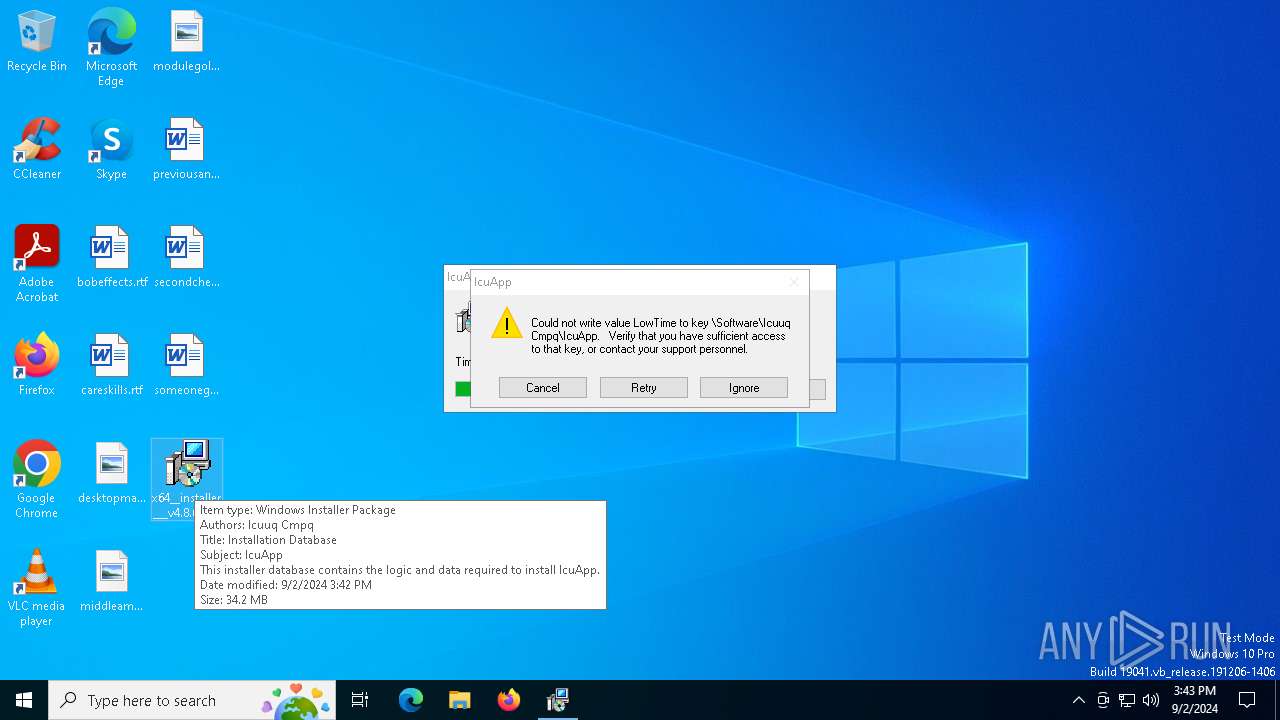
| File name: | x64__installer___v4.8.6.msi |
| Full analysis: | https://app.any.run/tasks/7dfa159b-86f1-4c80-a381-a998f4795a57 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | September 02, 2024, 15:41:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {2BB5763E-C053-4972-96C8-EF57D2A96066}, Number of Words: 10, Subject: IcuApp, Author: Icuuq Cmpq, Name of Creating Application: IcuApp, Template: x64;2057, Comments: This installer database contains the logic and data required to install IcuApp., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Sun Sep 1 18:21:22 2024, Last Saved Time/Date: Sun Sep 1 18:21:22 2024, Last Printed: Sun Sep 1 18:21:22 2024, Number of Pages: 450 |
| MD5: | 07997444061E4ED5F9B6274C4420F261 |
| SHA1: | 37CF9557DC424709D4FA2E99014979EB1FC868FE |
| SHA256: | 75CDF91E7F10807B81E9CC9754DC37D447D46912537F585E6F6B3E2A84FDB7DF |
| SSDEEP: | 196608:FTKDHPKOFfXWZQHvOJgdbOIkVBqjgnMn86M0WFd5ljUaWR261zVzaWM:crJZm7xBJnM86Q/BUaW/Jph |
MALICIOUS
ROBOTDROPPER has been detected
- msiexec.exe (PID: 3236)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 3236)
INFO
Checks supported languages
- msiexec.exe (PID: 3236)
An automatically generated document
- msiexec.exe (PID: 5708)
Creates files or folders in the user directory
- msiexec.exe (PID: 3236)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3236)
Create files in a temporary directory
- msiexec.exe (PID: 5708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {2BB5763E-C053-4972-96C8-EF57D2A96066} |
| Words: | 10 |
| Subject: | IcuApp |
| Author: | Icuuq Cmpq |
| LastModifiedBy: | - |
| Software: | IcuApp |
| Template: | x64;2057 |
| Comments: | This installer database contains the logic and data required to install IcuApp. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2024:09:01 18:21:22 |
| ModifyDate: | 2024:09:01 18:21:22 |
| LastPrinted: | 2024:09:01 18:21:22 |
| Pages: | 450 |
Total processes
121
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3236 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5708 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\x64__installer___v4.8.6.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 409
Read events
1 290
Write events
119
Delete events
0
Modification events
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\12b7a2.rbs |
Value: 31128910 | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\12b7a2.rbsLow |
Value: | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Users\admin\AppData\Roaming\Microsoft\Installer\ |
Value: | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\9821981A3ABF4934796C95EB5BF10CDC |
| Operation: | write | Name: | C7F8AA5646AE2E84BB4875C28F903973 |
Value: C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\ | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\9B8489ABA9DF66F42A0653B3A19343A4 |
| Operation: | write | Name: | C7F8AA5646AE2E84BB4875C28F903973 |
Value: 21:\Software\Icuuq Cmpq\IcuApp\Version | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\CA79783BE2CAD1241B088F1E5885EEF2 |
| Operation: | write | Name: | C7F8AA5646AE2E84BB4875C28F903973 |
Value: C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\jmods\java.base.jmod | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\911C6C1FEF2985240B3EB6BA5D94FDB7 |
| Operation: | write | Name: | C7F8AA5646AE2E84BB4875C28F903973 |
Value: C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\srv\classes.jsa | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\7D935B04105F5C949AEAA7124AD493B6 |
| Operation: | write | Name: | C7F8AA5646AE2E84BB4875C28F903973 |
Value: C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\srv\jvm.dll | |||
| (PID) Process: | (3236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\1D0C93C778D295D4C9F53D5B33CAB5EE |
| Operation: | write | Name: | C7F8AA5646AE2E84BB4875C28F903973 |
Value: C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\instrument.dll | |||
Executable files
69
Suspicious files
19
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3236 | msiexec.exe | C:\Windows\Installer\12b7a0.msi | — | |
MD5:— | SHA256:— | |||
| 3236 | msiexec.exe | C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\jmods\java.base.jmod | — | |
MD5:— | SHA256:— | |||
| 3236 | msiexec.exe | C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\srv\classes.jsa | — | |
MD5:— | SHA256:— | |||
| 3236 | msiexec.exe | C:\Users\admin\AppData\Roaming\Icuuq Cmpq\IcuApp\srv\classes_nocoops.jsa | — | |
MD5:— | SHA256:— | |||
| 3236 | msiexec.exe | C:\Windows\Installer\MSIBA51.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 3236 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:20619CEC775AA5219A6A7B7F05414F6F | SHA256:62C3E085698C80213DBF25A0659BDC251CB2303D276C4616B45E74AAD6DFF535 | |||
| 3236 | msiexec.exe | C:\Windows\Installer\MSIBF74.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 3236 | msiexec.exe | C:\Windows\Installer\MSIB9B4.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 3236 | msiexec.exe | C:\Windows\Installer\MSIBE3A.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 3236 | msiexec.exe | C:\Windows\Installer\MSICB9A.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
15
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 403 | 188.114.96.3:443 | https://to-license2.com/licenseUser.php | unknown | html | 4.41 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
6880 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5768 | msiexec.exe | 188.114.97.3:443 | to-license2.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
to-license2.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] RobotDropper HTTP C2 Request |
1 ETPRO signatures available at the full report