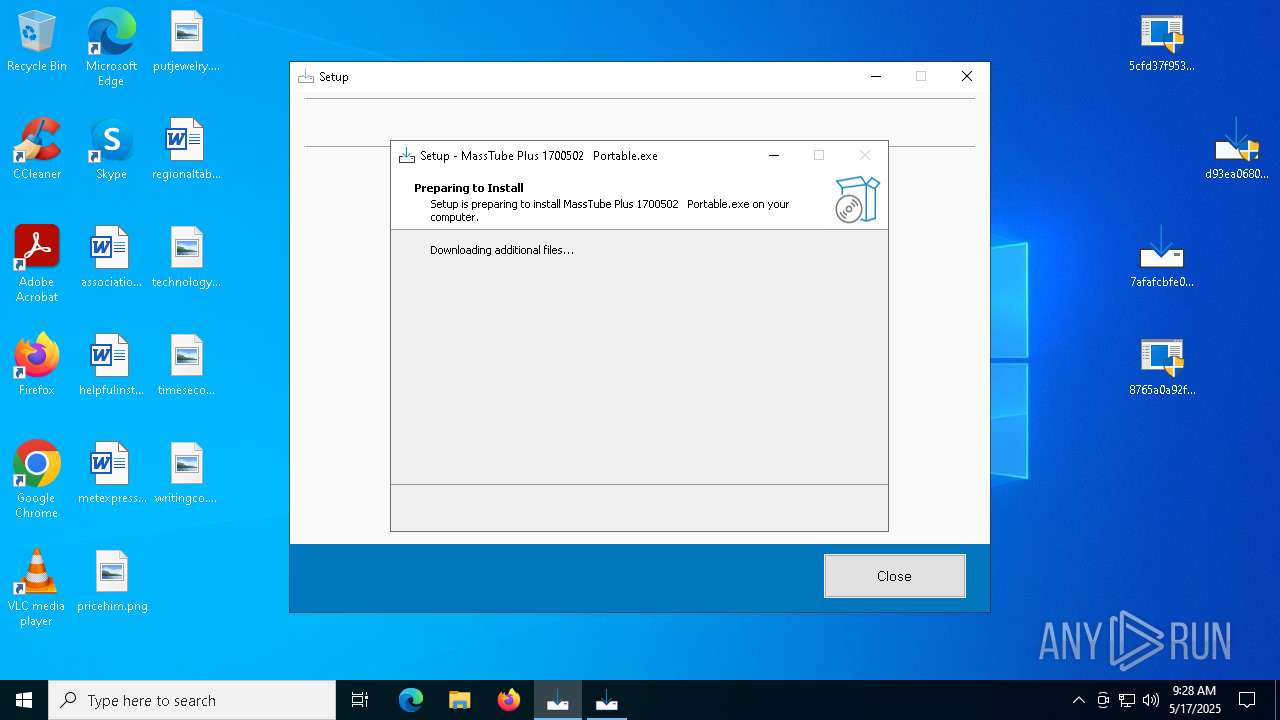
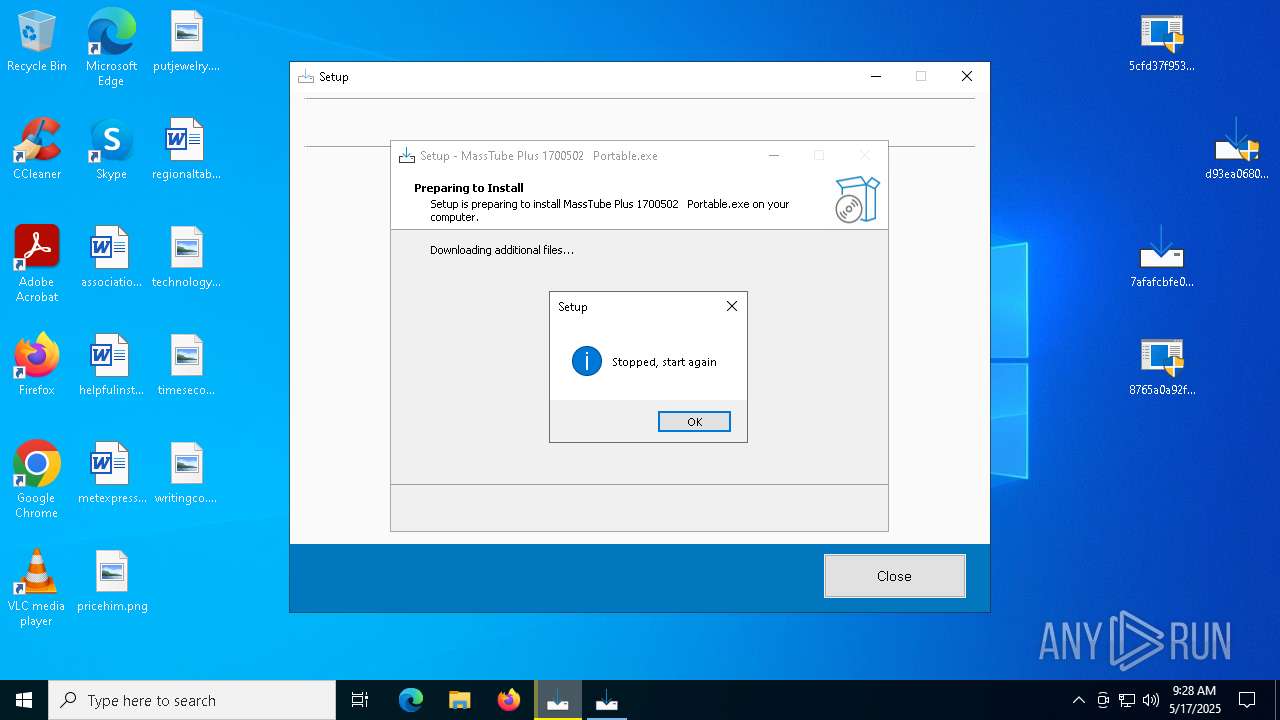
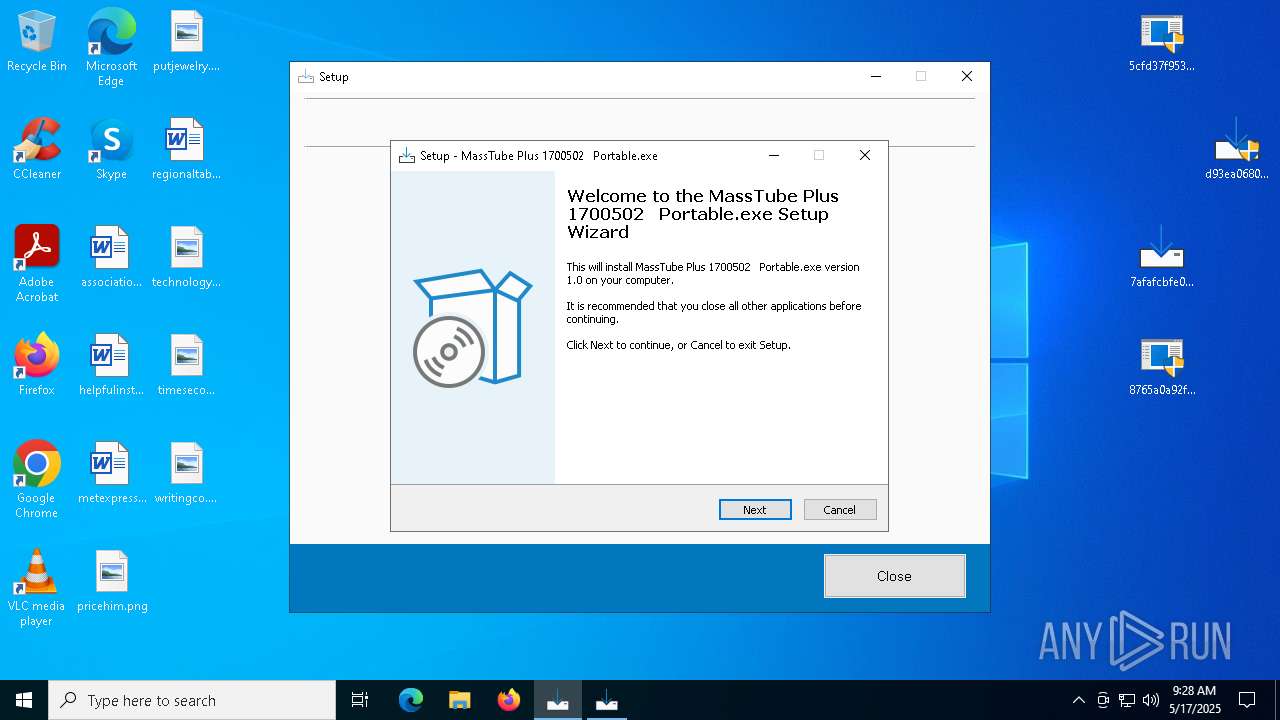
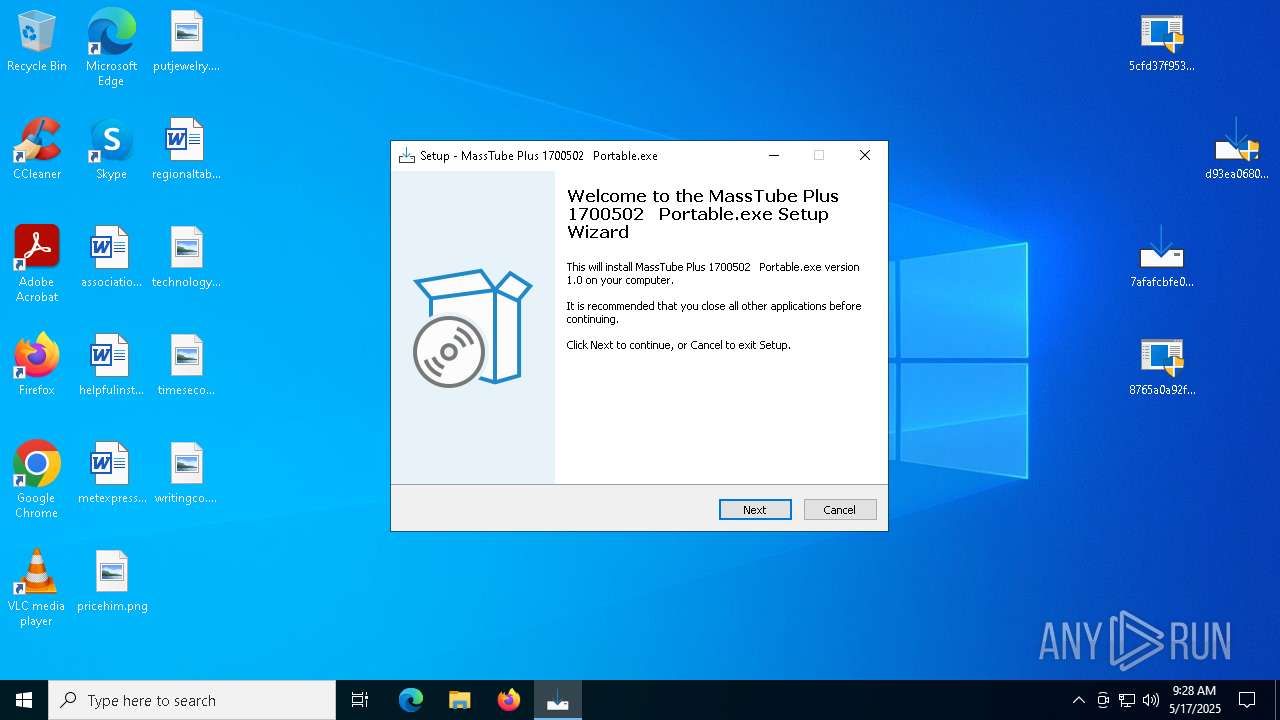
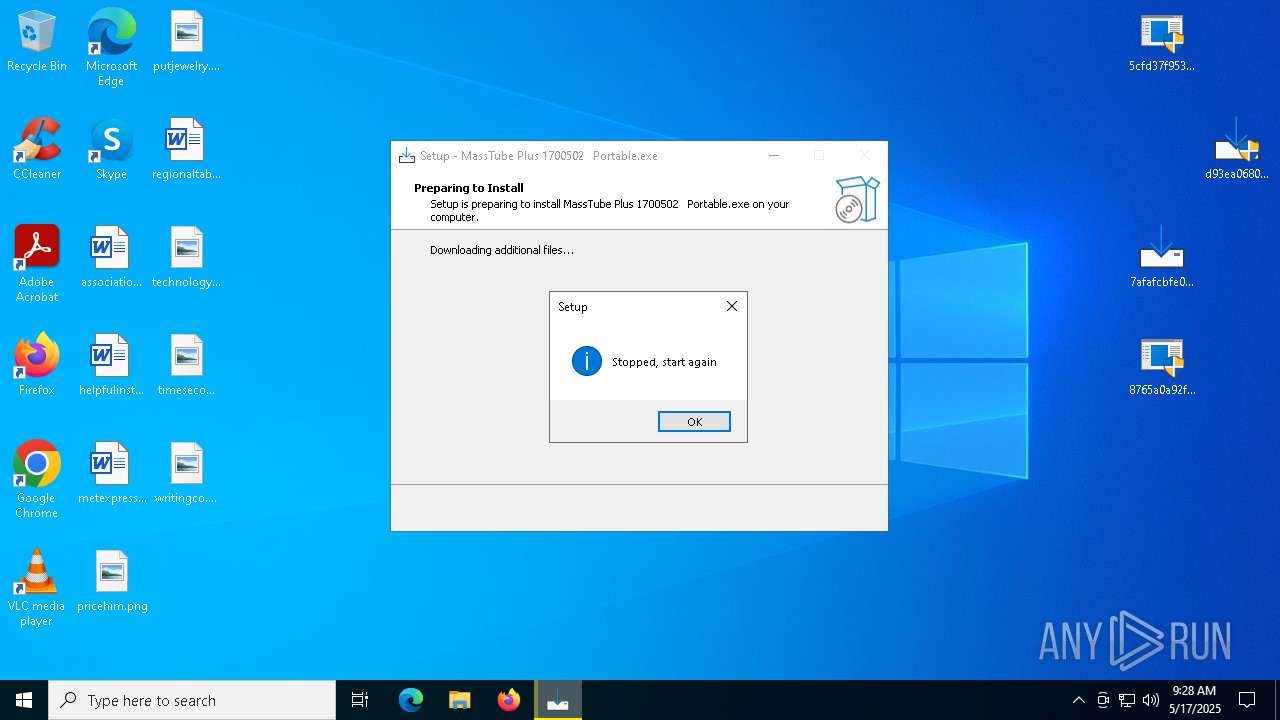
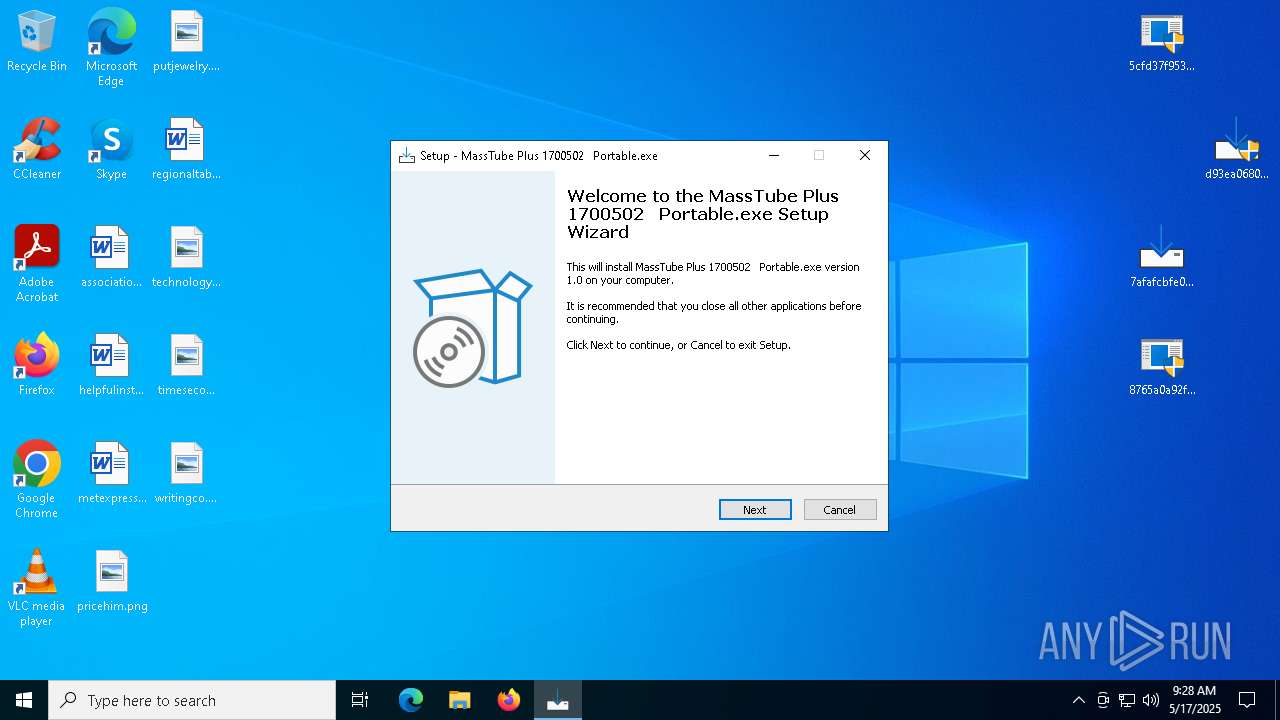
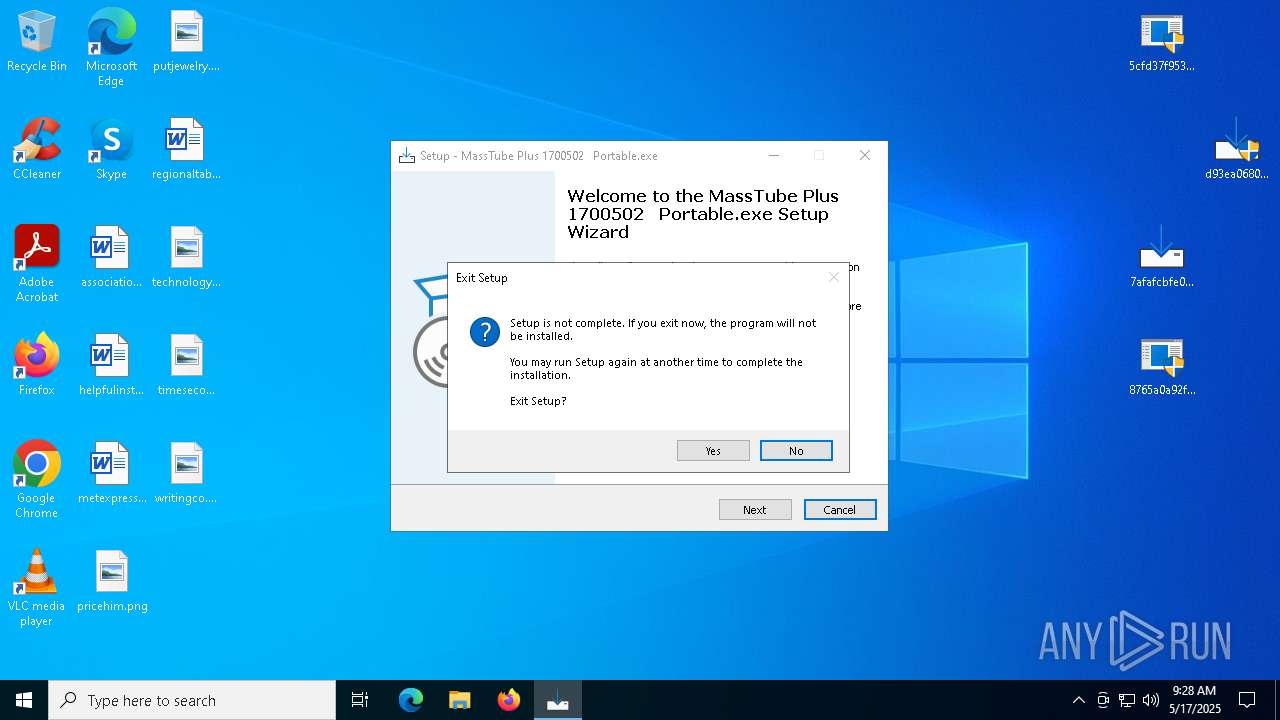
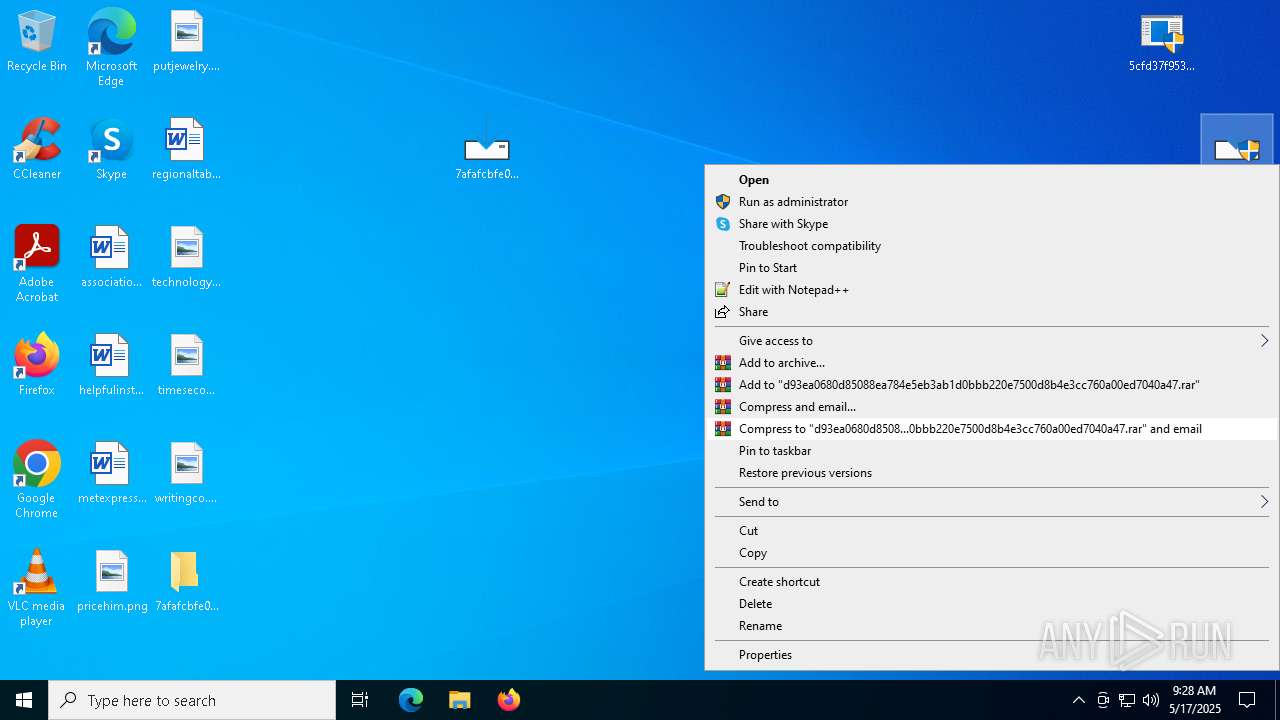
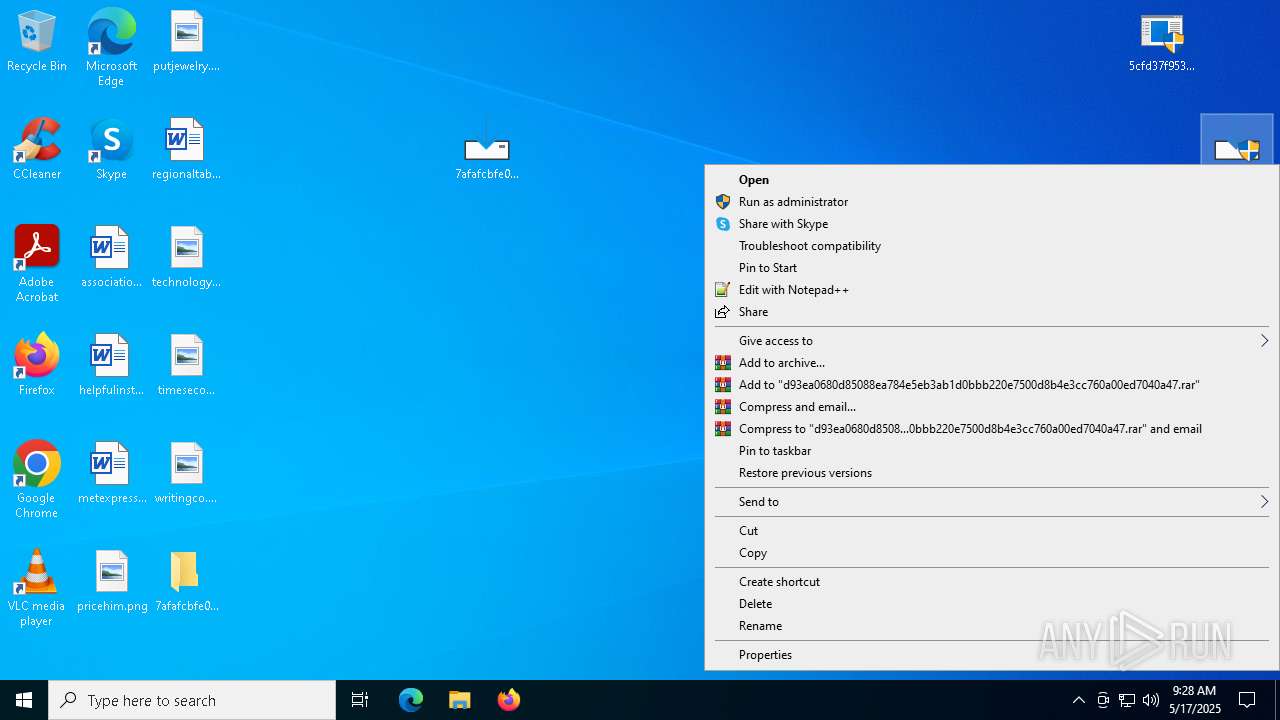
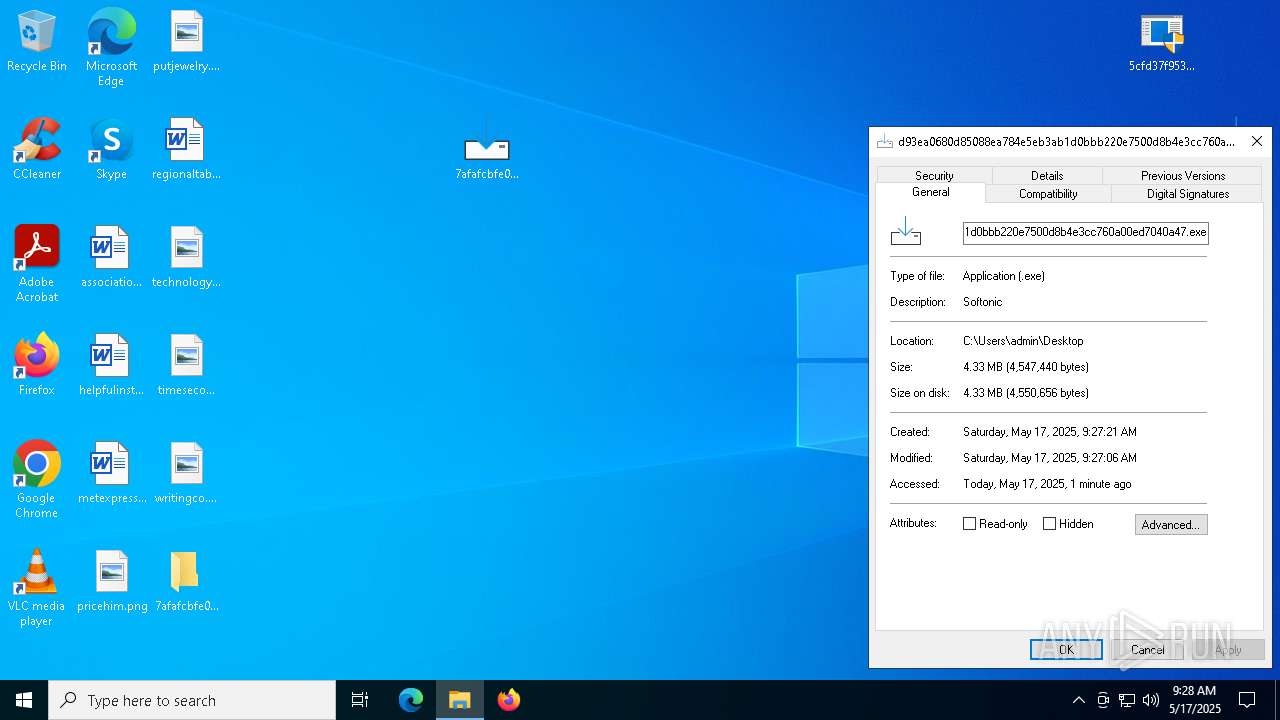
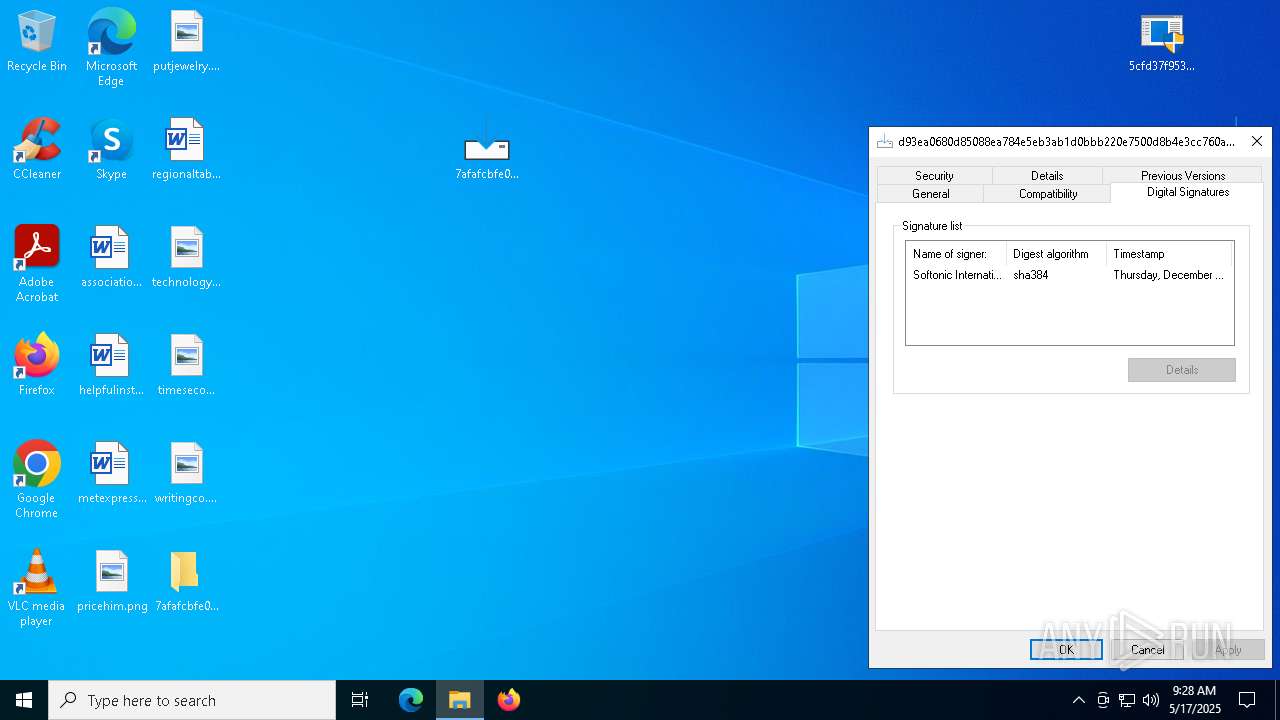
| URL: | https://bazaar.abuse.ch/download/7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7/ |
| Full analysis: | https://app.any.run/tasks/254f7b9f-3c87-475a-8dcc-aab1f3d15994 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | May 17, 2025, 09:25:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0AC7F5B23AD9CBC3038A20BD194496B4 |
| SHA1: | 8CA3D83FCEFA1ABCC5DC22AAAD099DD2182A5174 |
| SHA256: | 75984F7ABCF28BA1F6490A67CA2D3784482EA52DF28EC455FFEC5E752EEB8C90 |
| SSDEEP: | 3:N8N0uDWB4SLGucqHjpr7UHCQYnWIBVXRvXEDSK:23GfLNztDQYnWIBVVUD5 |
MALICIOUS
ADWARE has been found (auto)
- firefox.exe (PID: 7312)
- WinRAR.exe (PID: 8976)
Executing a file with an untrusted certificate
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 1348)
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 7188)
Changes Windows Defender settings
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 7188)
Adds path to the Windows Defender exclusion list
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 7188)
SUSPICIOUS
Executable content was dropped or overwritten
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 5136)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 7212)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp (PID: 4688)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 8340)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 8888)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp (PID: 3008)
Starts POWERSHELL.EXE for commands execution
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 7188)
Script adds exclusion path to Windows Defender
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 7188)
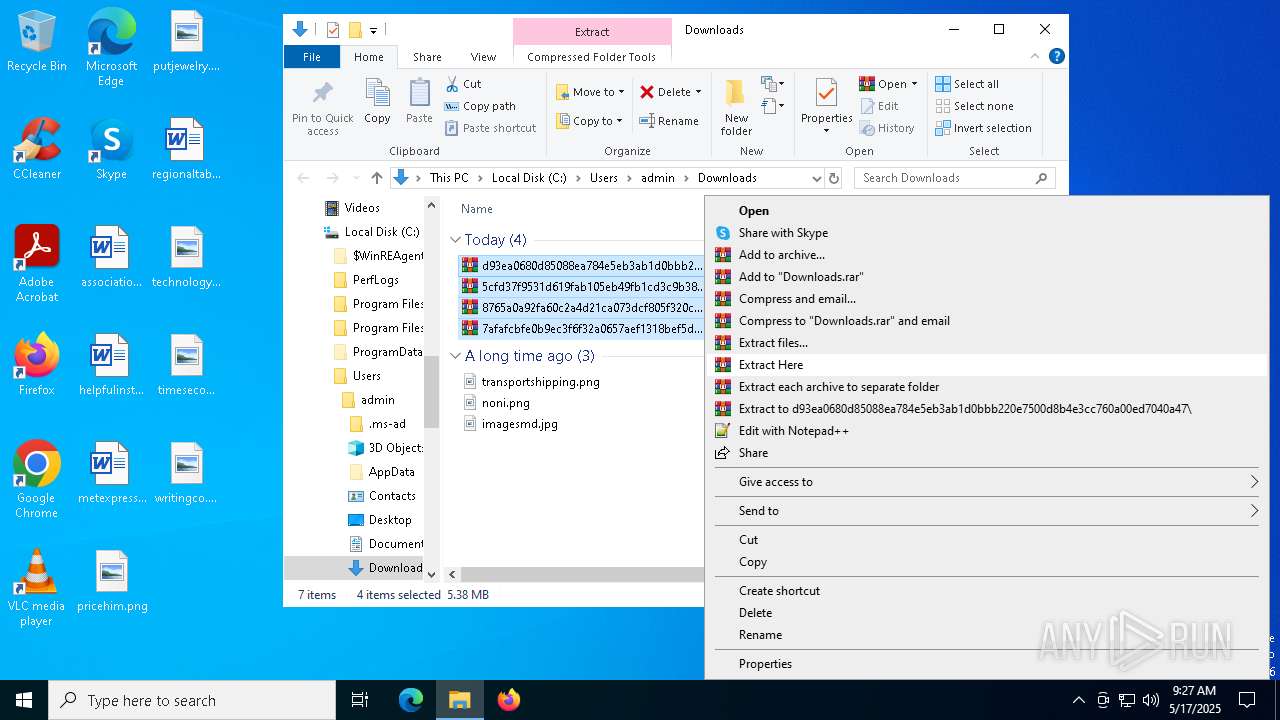
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 6416)
INFO
The sample compiled with english language support
- firefox.exe (PID: 7312)
- WinRAR.exe (PID: 8976)
- WinRAR.exe (PID: 6416)
Application launched itself
- firefox.exe (PID: 7292)
- firefox.exe (PID: 7312)
Manual execution by a user
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 1348)
- WinRAR.exe (PID: 8976)
- 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe (PID: 7188)
- 8765a0a92fa60c2a4d21ca073dcf805f320c2e3d07703b97638b38888fe25d23.exe (PID: 8436)
- 8765a0a92fa60c2a4d21ca073dcf805f320c2e3d07703b97638b38888fe25d23.exe (PID: 6392)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 5136)
- WinRAR.exe (PID: 6416)
- d93ea0680d85088ea784e5eb3ab1d0bbb220e7500d8b4e3cc760a00ed7040a47.exe (PID: 7144)
- d93ea0680d85088ea784e5eb3ab1d0bbb220e7500d8b4e3cc760a00ed7040a47.exe (PID: 7932)
- d93ea0680d85088ea784e5eb3ab1d0bbb220e7500d8b4e3cc760a00ed7040a47.exe (PID: 7148)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 8340)
- 7zFM.exe (PID: 8104)
- d93ea0680d85088ea784e5eb3ab1d0bbb220e7500d8b4e3cc760a00ed7040a47.exe (PID: 7872)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8976)
- WinRAR.exe (PID: 6416)
Reads the software policy settings
- slui.exe (PID: 7284)
Detects InnoSetup installer (YARA)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 5136)
Compiled with Borland Delphi (YARA)
- 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe (PID: 5136)
The sample compiled with russian language support
- WinRAR.exe (PID: 6416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
177
Monitored processes
41
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
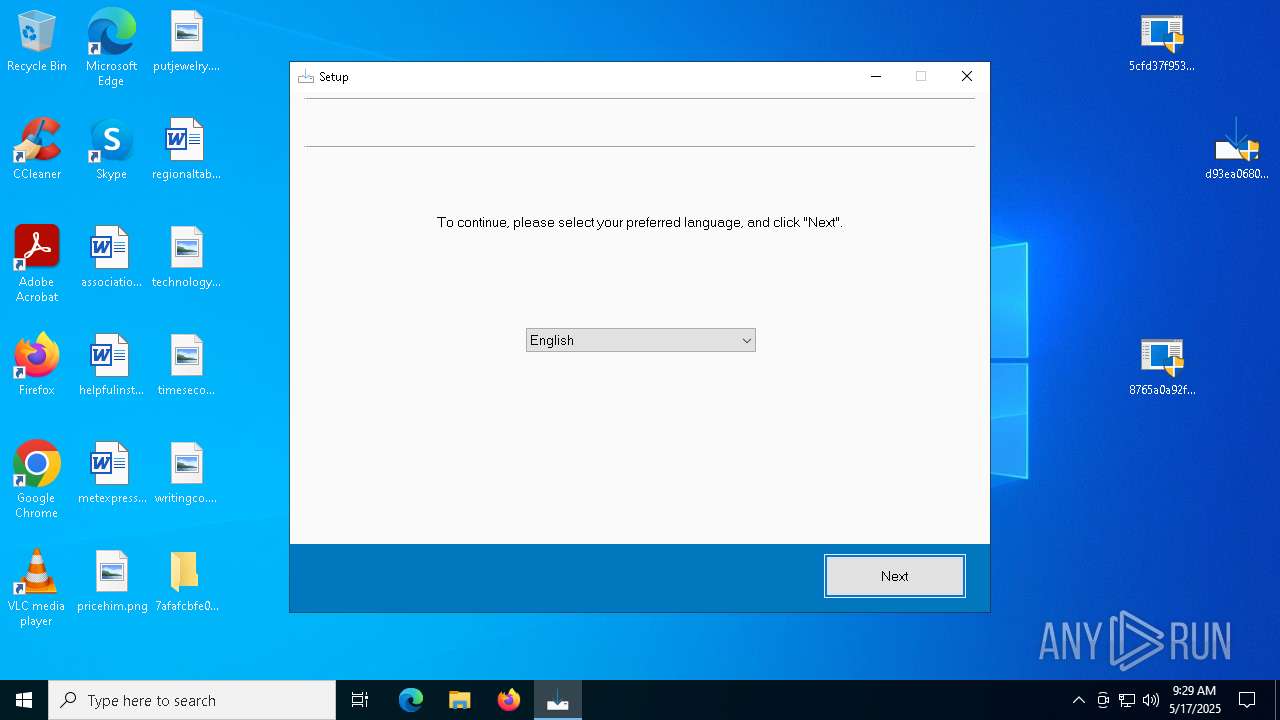
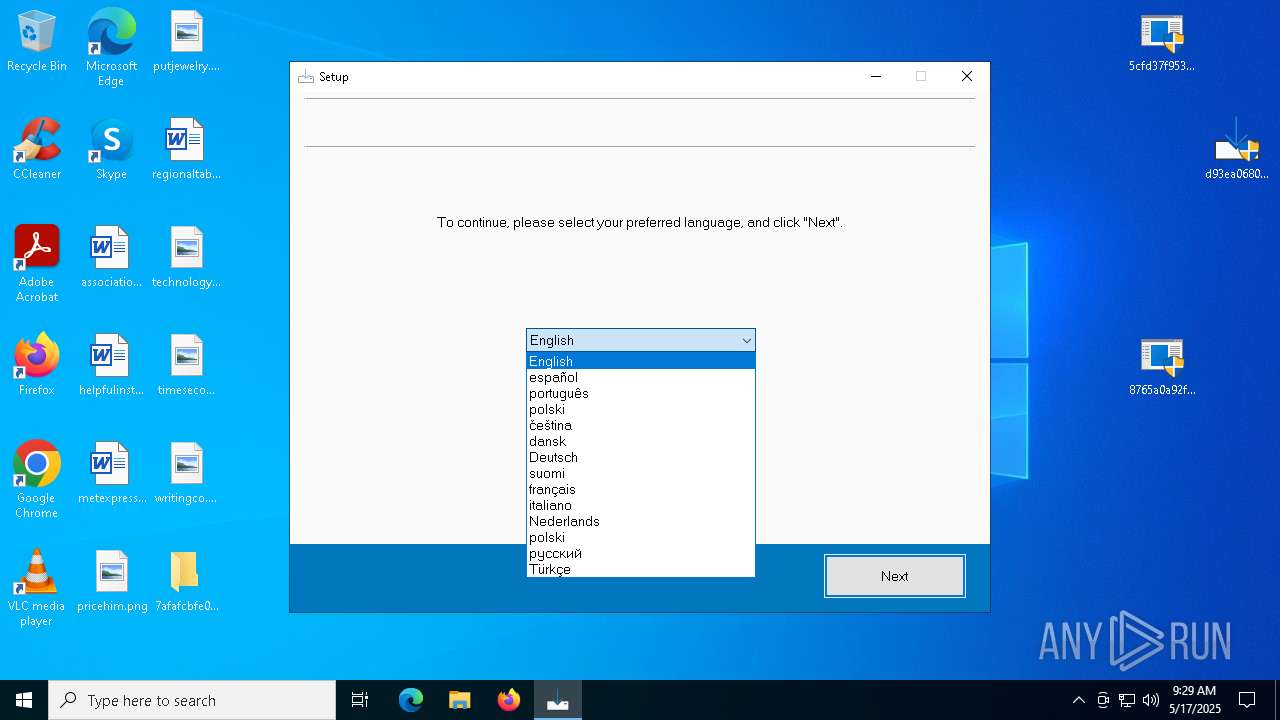
| 664 | "C:\Users\admin\AppData\Local\Temp\is-952R9.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp" /SL5="$B0290,2422026,832512,C:\Users\admin\Desktop\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe" | C:\Users\admin\AppData\Local\Temp\is-952R9.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp | — | 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 720 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4364 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4464 -prefMapHandle 4704 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c57d9937-e803-4f04-838b-f6932248a3d9} 7312 "\\.\pipe\gecko-crash-server-pipe.7312" 22b094b2710 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\Desktop\5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe" | C:\Users\admin\Desktop\5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe | — | explorer.exe | |||||||||||
User: admin Company: iWEBehewIX Integrity Level: MEDIUM Description: ETeZieU uxECoHEjIEu iPOxEaoIeQO aDiDU EOoDuei UquvaAiv uVOtUKIXi IyIfAki. Exit code: 3221226540 Version: 7.83.124.14 Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\AppData\Local\Temp\is-USKL9.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp" /SL5="$9030E,2422026,832512,C:\Users\admin\Desktop\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe" /SPAWNWND=$B02AA /NOTIFYWND=$80340 | C:\Users\admin\AppData\Local\Temp\is-USKL9.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp | 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3192 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4056 | "C:\Users\admin\AppData\Local\Temp\is-F2BBK.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp" /SL5="$80340,2422026,832512,C:\Users\admin\Desktop\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe" | C:\Users\admin\AppData\Local\Temp\is-F2BBK.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp | — | 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4188 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4688 | "C:\Users\admin\AppData\Local\Temp\is-MIP4I.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp" /SL5="$B029A,2422026,832512,C:\Users\admin\Desktop\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe" /SPAWNWND=$3026E /NOTIFYWND=$B0290 | C:\Users\admin\AppData\Local\Temp\is-MIP4I.tmp\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.tmp | 7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
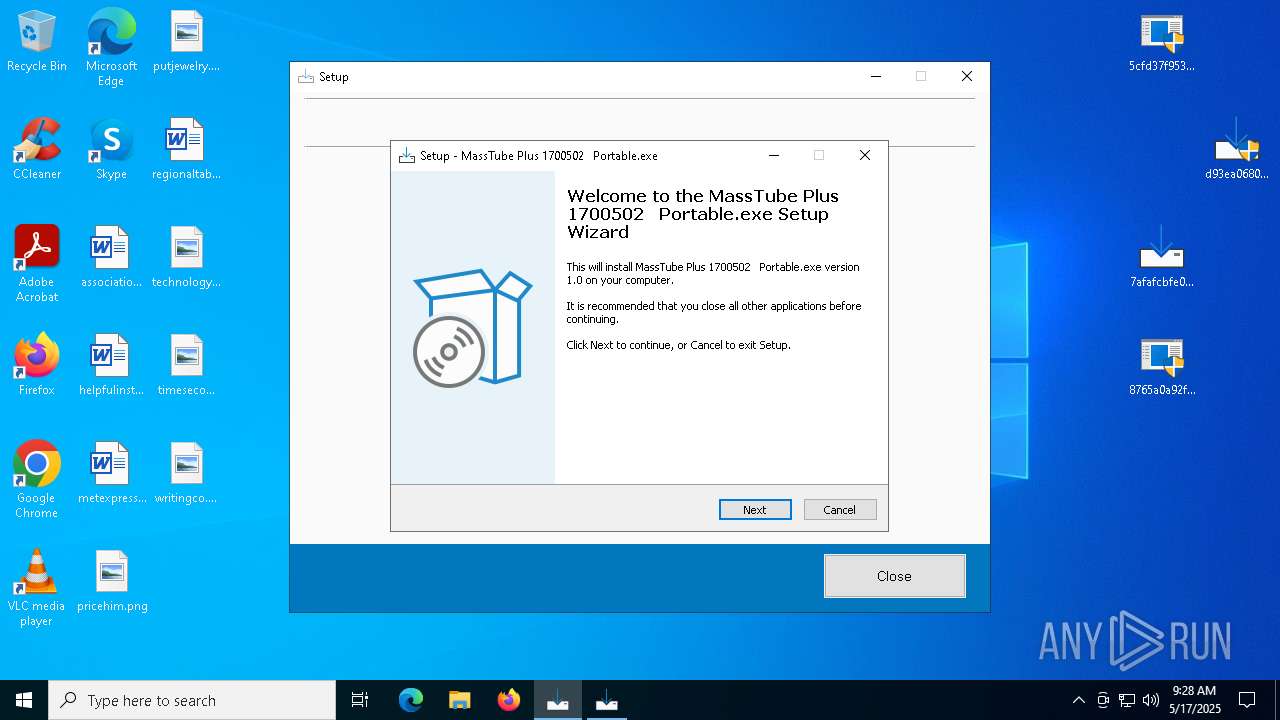
| 5136 | "C:\Users\admin\Desktop\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe" | C:\Users\admin\Desktop\7afafcbfe0b9ec3f6f32a0657aef1318bef5db8e698da4d81db74d0233792af7.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: MassTube Plus 1700502 Portable.exe Setup Exit code: 2 Version: Modules
| |||||||||||||||
| 6136 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngentask.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngentask.exe | 8765a0a92fa60c2a4d21ca073dcf805f320c2e3d07703b97638b38888fe25d23.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework optimization service Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
28 585
Read events
28 527
Write events
58
Delete events
0
Modification events
| (PID) Process: | (7312) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
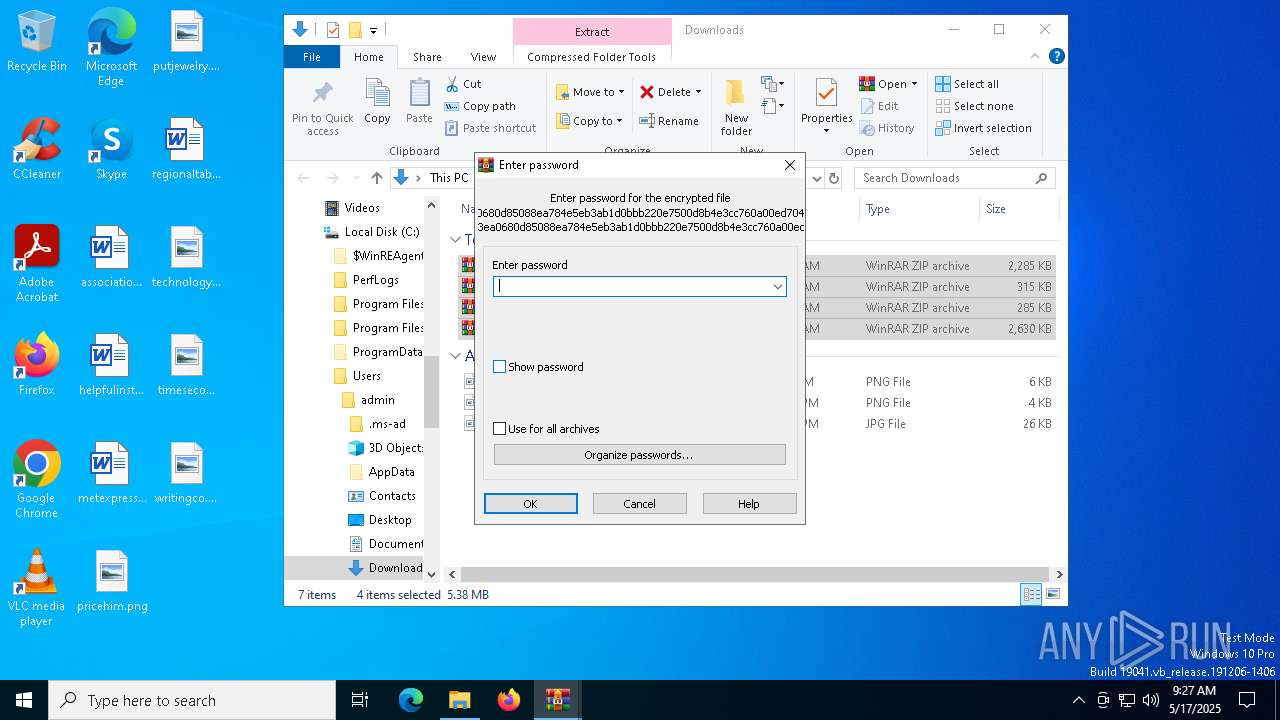
| (PID) Process: | (8976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (8976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | PswAllArchives |
Value: 0 | |||
| (PID) Process: | (8976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7188) 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings\Windows.SystemToast.SecurityAndMaintenance |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (7188) 5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\Users\admin\Desktop\5cfd37f9531d619fab105eb49fb1cd3c9b38adbaab1cd6f7c546b5189f5a4b08.exe |
Value: 0 | |||
| (PID) Process: | (6136) ngentask.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\ngentask_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
19
Suspicious files
200
Text files
131
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7312 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:3B156E12141F8CBCE9D60CDCE2077617 | SHA256:E6287E44B44ABEA20E1B2E3F415D22B9E5E5FBBC155AD9DADBABA63951B2AF6F | |||
| 7312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
94
DNS requests
142
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7312 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7312 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7312 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7312 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7312 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7312 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
7312 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7312 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7312 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7312 | firefox.exe | 151.101.2.49:443 | bazaar.abuse.ch | FASTLY | US | whitelisted |
7312 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
7312 | firefox.exe | 142.250.185.170:443 | safebrowsing.googleapis.com | — | — | whitelisted |
7312 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
bazaar.abuse.ch |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
p2.shared.global.fastly.net |
| whitelisted |
ipv4only.arpa |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |