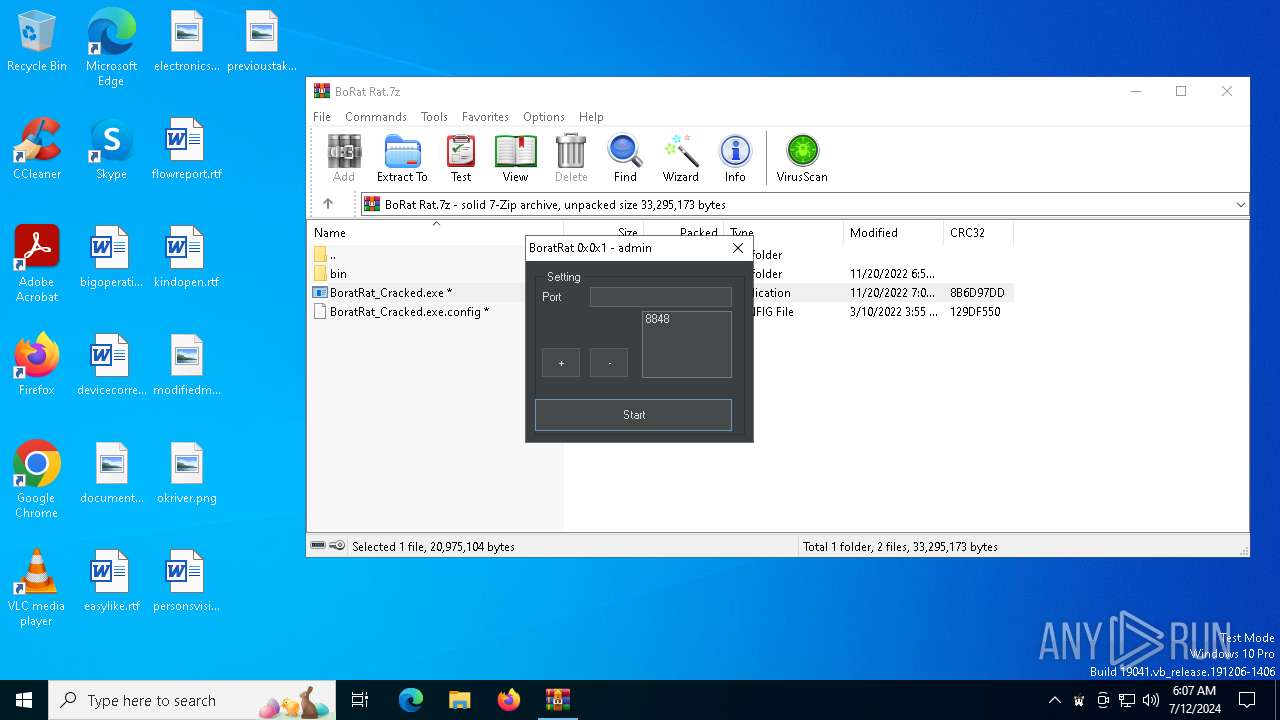
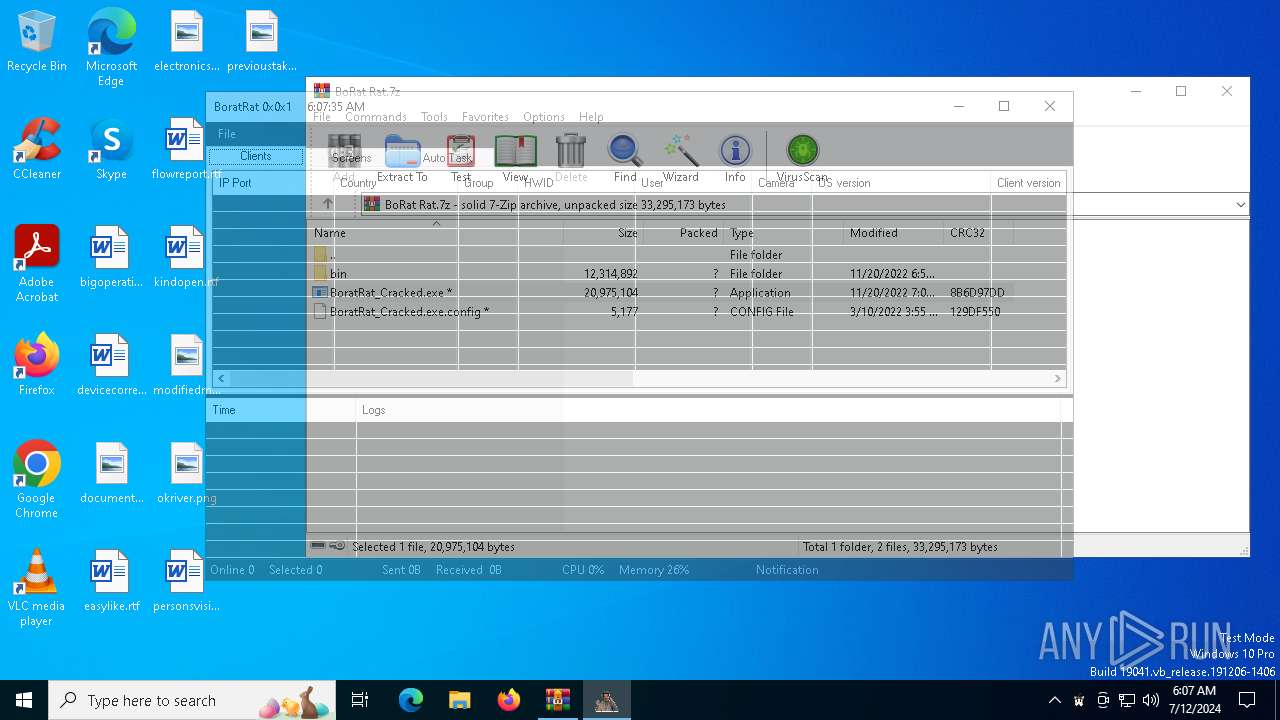
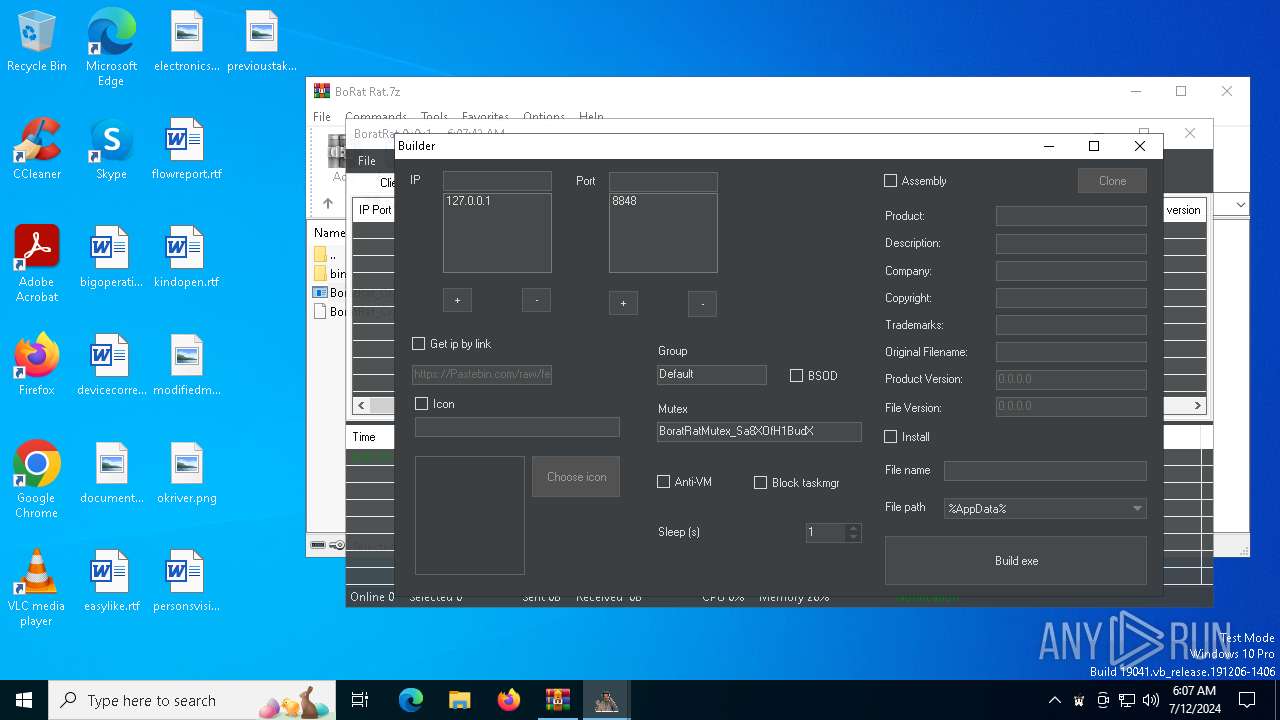
| File name: | BoRat Rat.7z |
| Full analysis: | https://app.any.run/tasks/856c8221-06a3-431d-b084-c614b92398c0 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 12, 2024, 06:06:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 320967EA4C3F77C31CF5B8A7C7281DB1 |
| SHA1: | 4604180A62E0C5E8DF87B9713213551AEF8F911D |
| SHA256: | 758DA04589FAF3A8AEDEAE4F9E26C90C4A7530F5E8368A368EFE8EF792F167D9 |
| SSDEEP: | 98304:tFKpSjCYPyJMSg85p6oVj62iFUCNTeGCYWw9H549XokuXIc9zeBtyMACjnmwWdZm:Mvro8YGfvocaJhGa+I54p |
MALICIOUS
Actions looks like stealing of personal data
- WinRAR.exe (PID: 4780)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4780)
- BoratRat_Cracked.exe (PID: 3128)
ASYNCRAT has been detected (YARA)
- BoratRat_Cracked.exe (PID: 3128)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 4780)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4780)
- BoratRat_Cracked.exe (PID: 3128)
The process checks if it is being run in the virtual environment
- BoratRat_Cracked.exe (PID: 3128)
Executable content was dropped or overwritten
- BoratRat_Cracked.exe (PID: 3128)
Creates file in the systems drive root
- BoratRat_Cracked.exe (PID: 3128)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4780)
Checks supported languages
- BoratRat_Cracked.exe (PID: 3128)
Reads the computer name
- BoratRat_Cracked.exe (PID: 3128)
Reads the machine GUID from the registry
- BoratRat_Cracked.exe (PID: 3128)
Creates files or folders in the user directory
- BoratRat_Cracked.exe (PID: 3128)
Create files in a temporary directory
- BoratRat_Cracked.exe (PID: 3128)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- BoratRat_Cracked.exe (PID: 3128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
113
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1188 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\BoratRat_Cracked.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\BoratRat_Cracked.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BoratRat Version: 1.0.7.0 Modules
| |||||||||||||||
| 4780 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\BoRat Rat.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
15 672
Read events
15 594
Write events
73
Delete events
5
Modification events
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\BoRat Rat.7z | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
26
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\ip2region.db | — | |
MD5:— | SHA256:— | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\Information.dll | executable | |
MD5:87651B12453131DAFD3E91F60D8AEF5A | SHA256:A15D72D990686D06D89D7E11DF2B16BCD5719A40298C19D046FA22C40D56AF44 | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\Fun.dll | executable | |
MD5:499FC6AC30B3B342833C79523BE4A60C | SHA256:DCAC599B1BAB37E1A388AC469E6CC5DE1F35EB02BEAA6778F07A1C090CE3EA04 | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\Logger.dll | executable | |
MD5:872145B37D107144894C9AA8729BAD42 | SHA256:2F258949FD95DA6CD912BEB7203A9FD5E99D050309A40341DE67537EDB75AADC | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\Options.dll | executable | |
MD5:3A474B8DEE059562B31887197D94F382 | SHA256:C9B8E795C5A024F9E3C85BA64534B9BF52CC8C3D29B95FF6417DC3A54BC68B95 | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\MessagePackLib.dll | executable | |
MD5:590B00C87D5FF2FFE09079F0406EB2CD | SHA256:ADB00DEE751B4BA620D3B0E002F5B6D8B89CF63B062F74EC65BBA72294D553D1 | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\Miscellaneous.dll | executable | |
MD5:509D41DA4A688A2E50FC8E3AFCA074C7 | SHA256:F91973113FD01465999CE317F3E7A89DF8C91A5EFADCFA61E5CCCE687BF3580A | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\ProcessManager.dll | executable | |
MD5:91EDCB945924DF5FBF4FF123AA63199C | SHA256:5B1F80FF787BDCD7EE12AA64BE1F2F5F1F658BD644BBC5FD73527B51DA6CE0D6 | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\Recovery.dll | executable | |
MD5:EA1FF113B847312D57FA8621F71F460F | SHA256:58F9E3C90446DFECFEC64221EB11167DD41D0E8DEDDA2EA9F83D9DDA2890E6F3 | |||
| 4780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4780.24537\bin\FileManager.dll | executable | |
MD5:4CCD3DFB14FFDDDFA598D1096F0190EA | SHA256:7F8A306826FCB0EE985A2B6D874C805F7F9B2062A1123EA4BB7F1EBA90FC1B81 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
81
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1928 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |