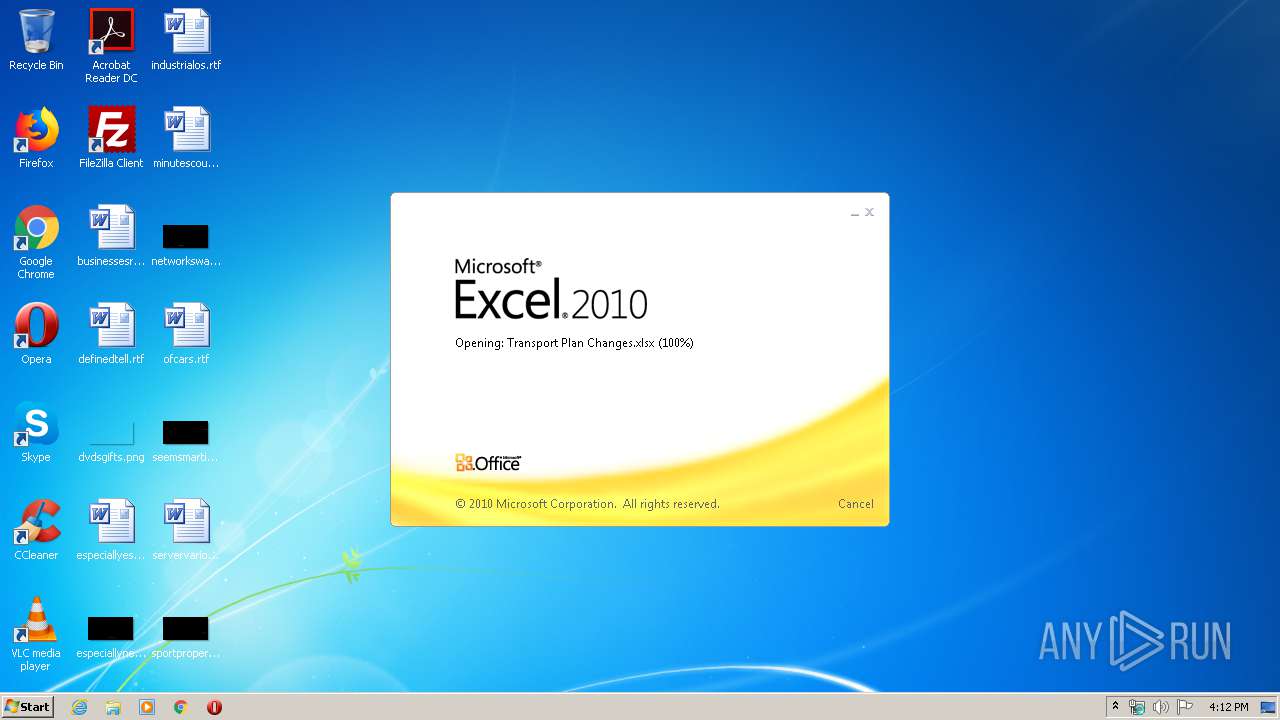
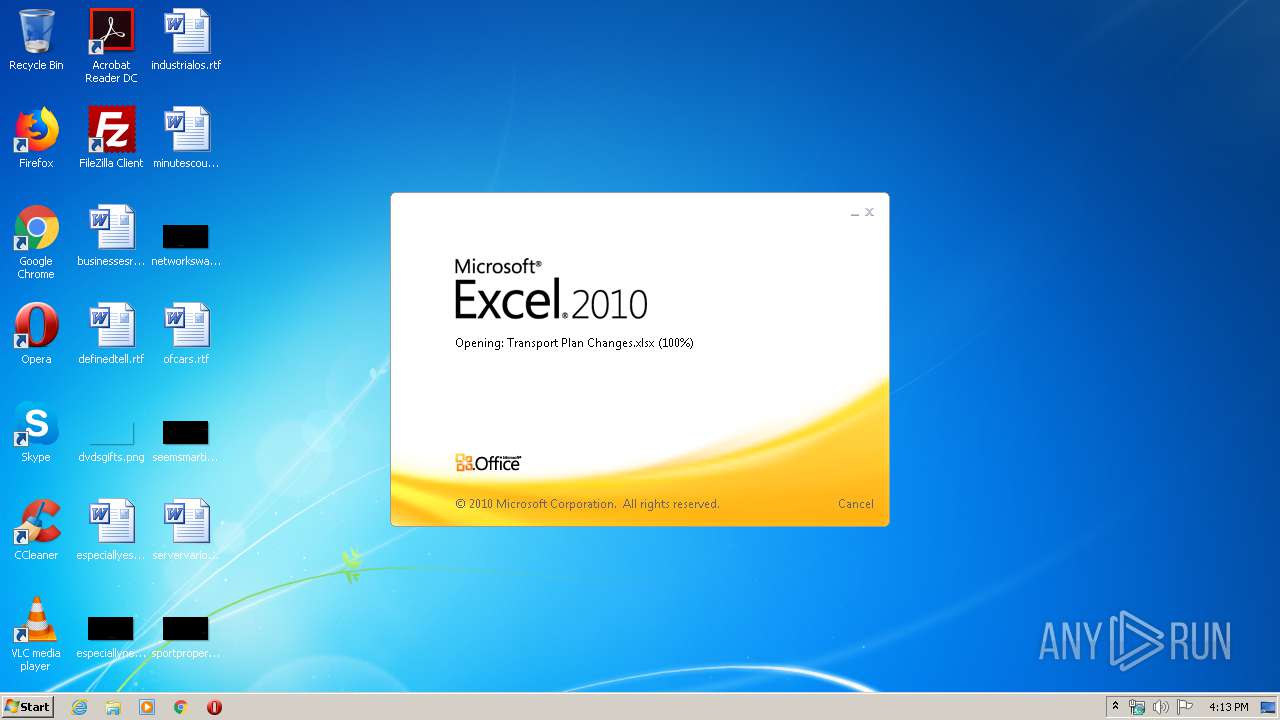
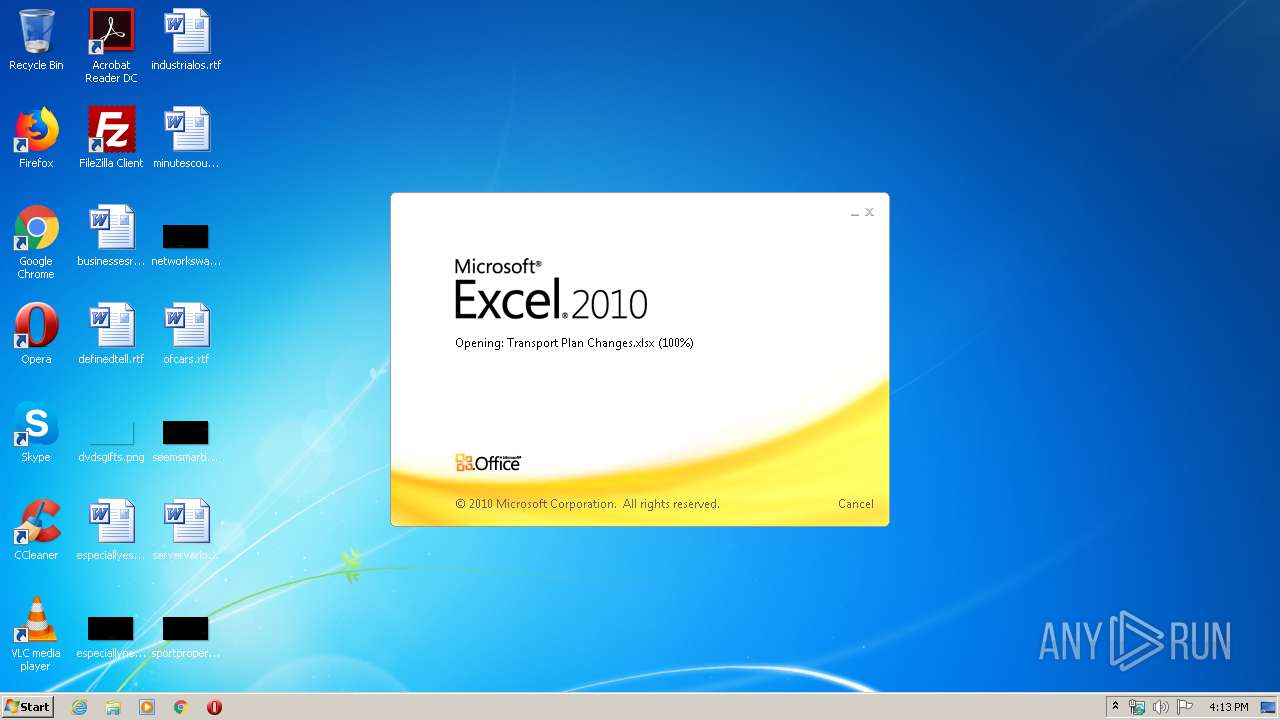
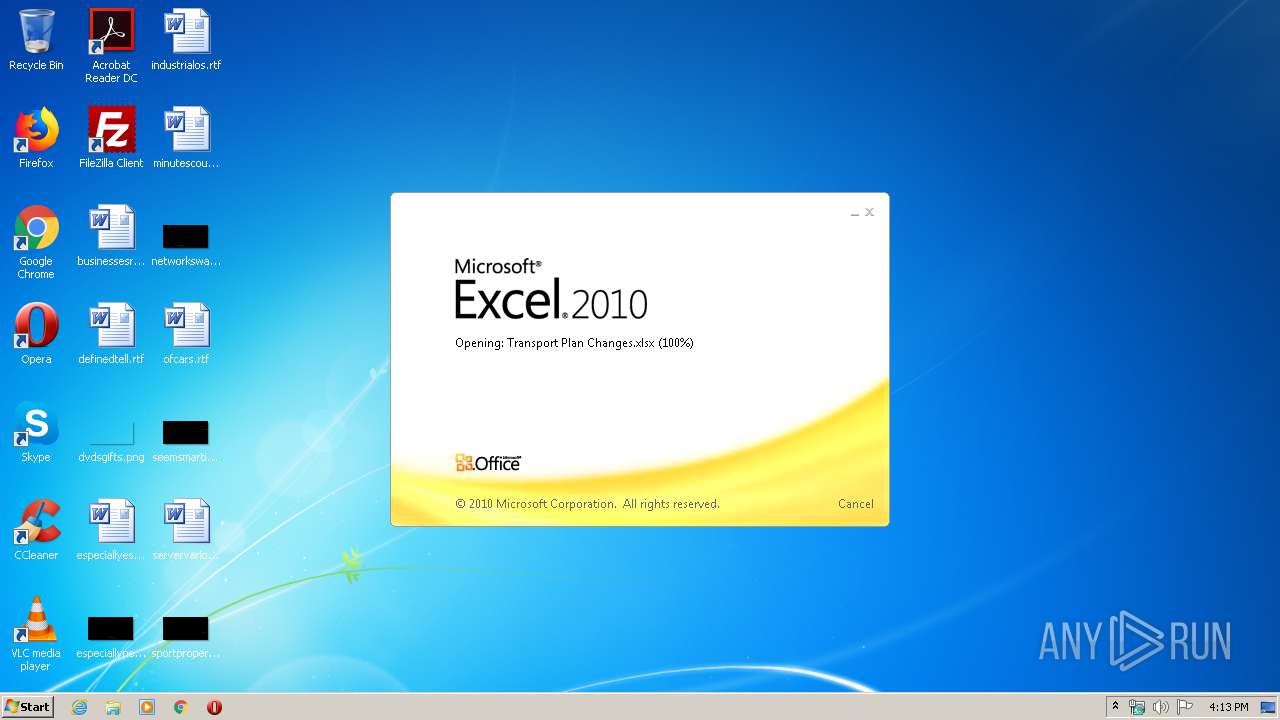
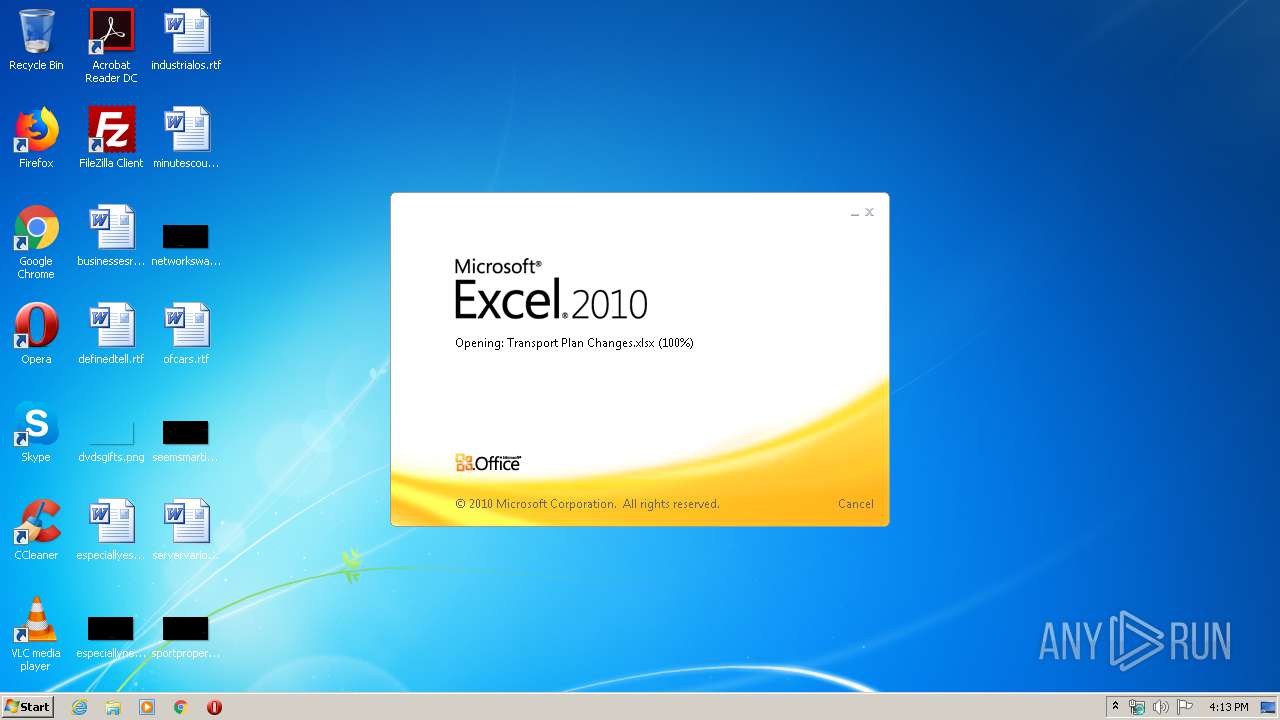
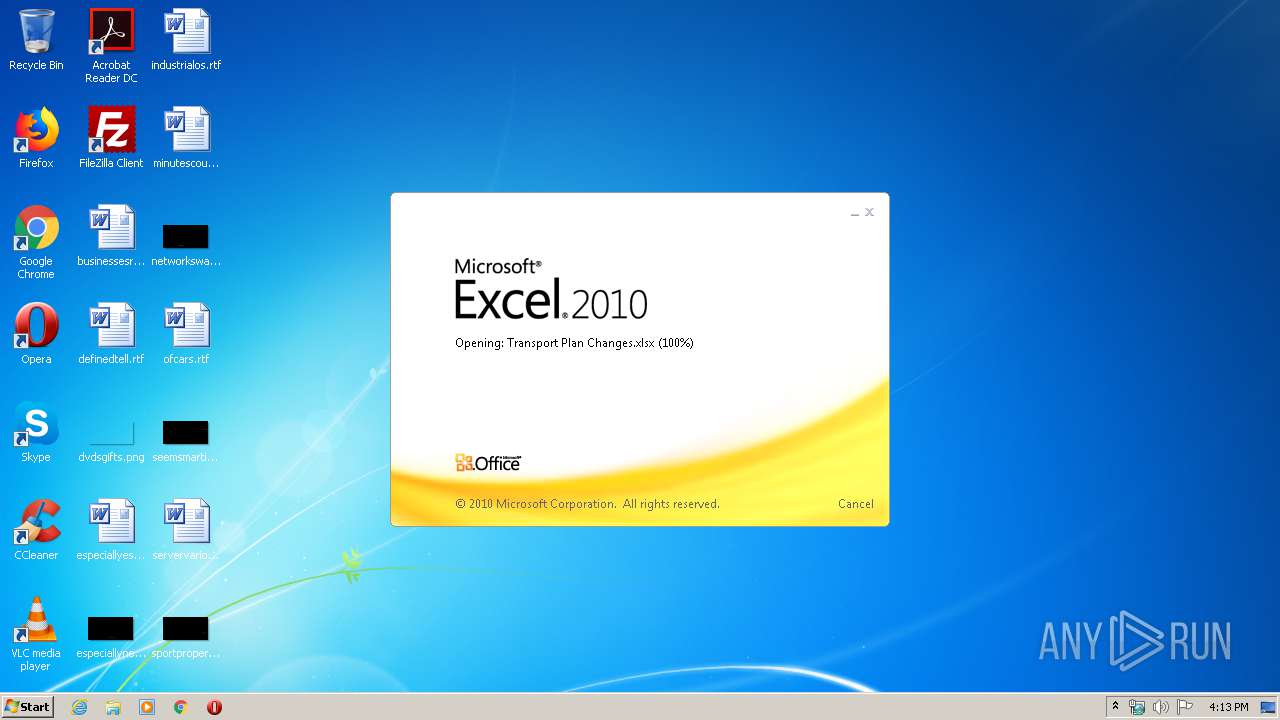
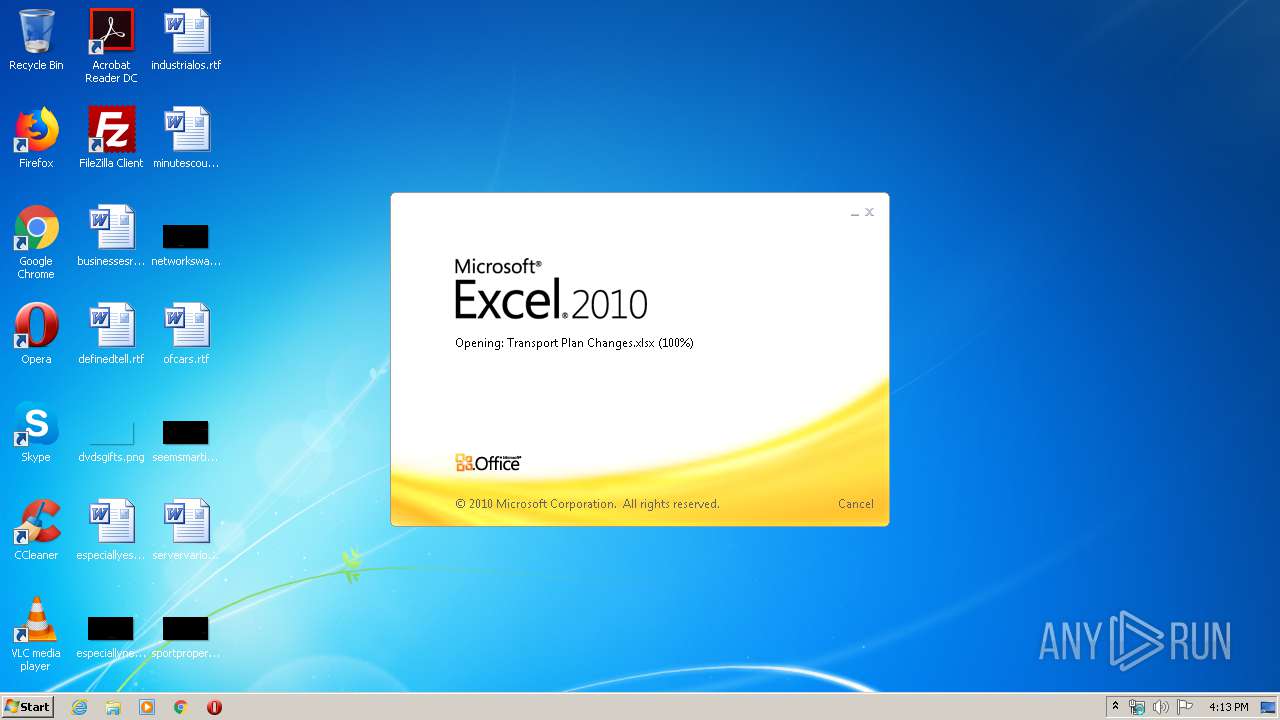
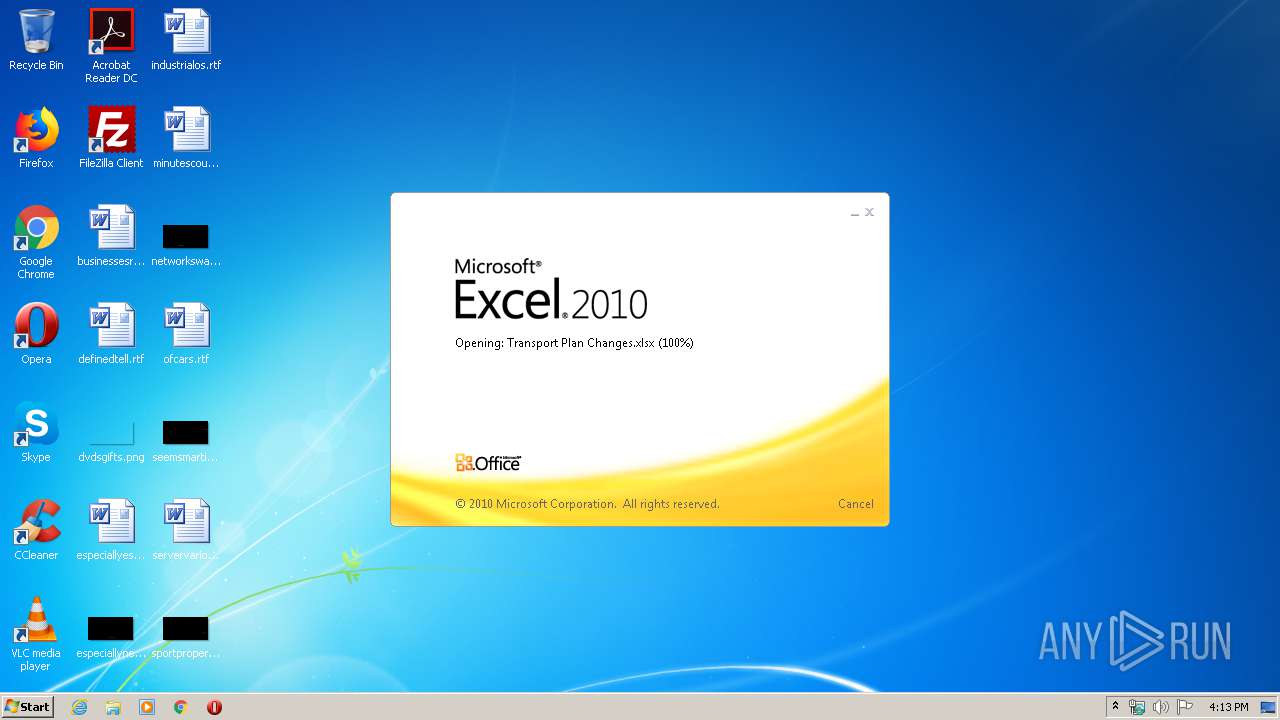
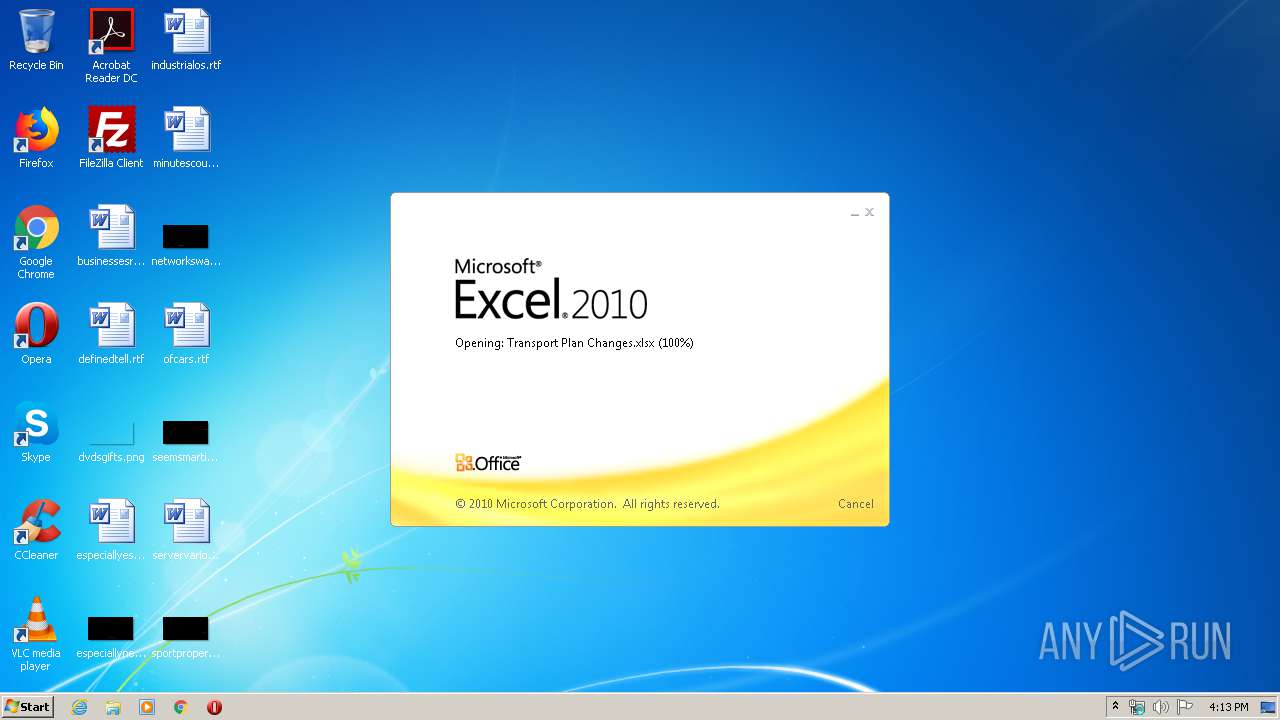
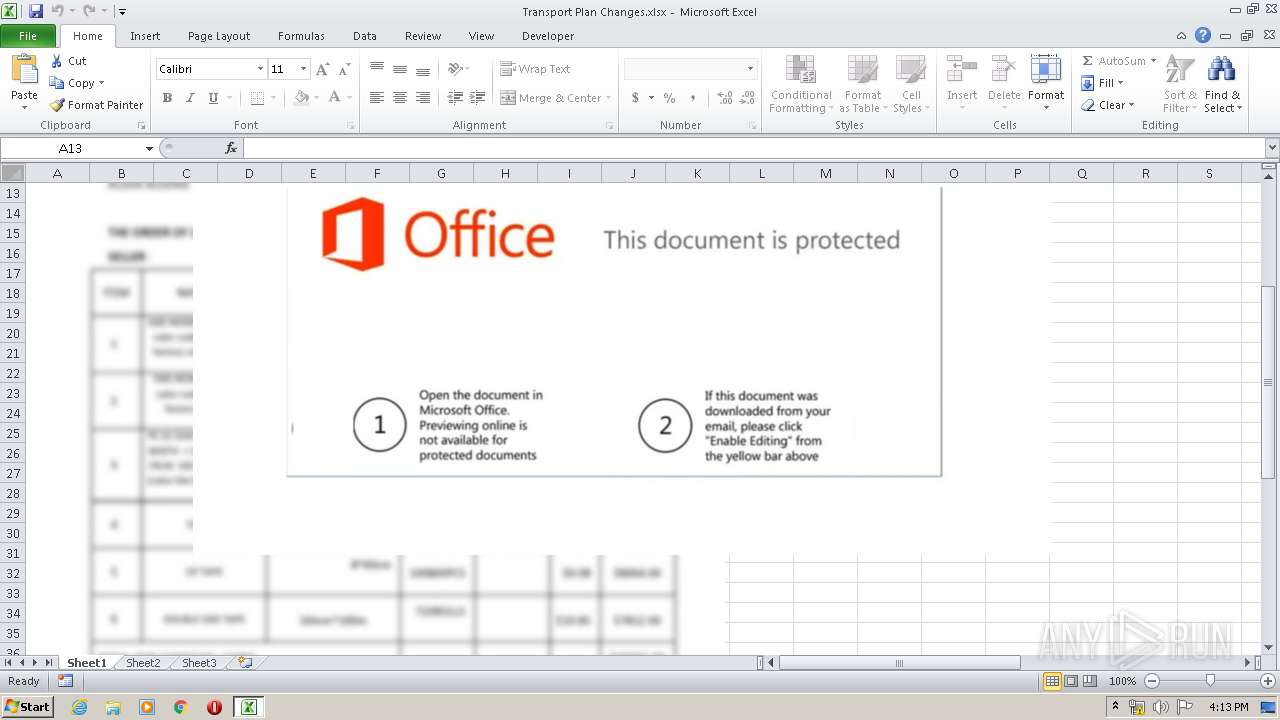
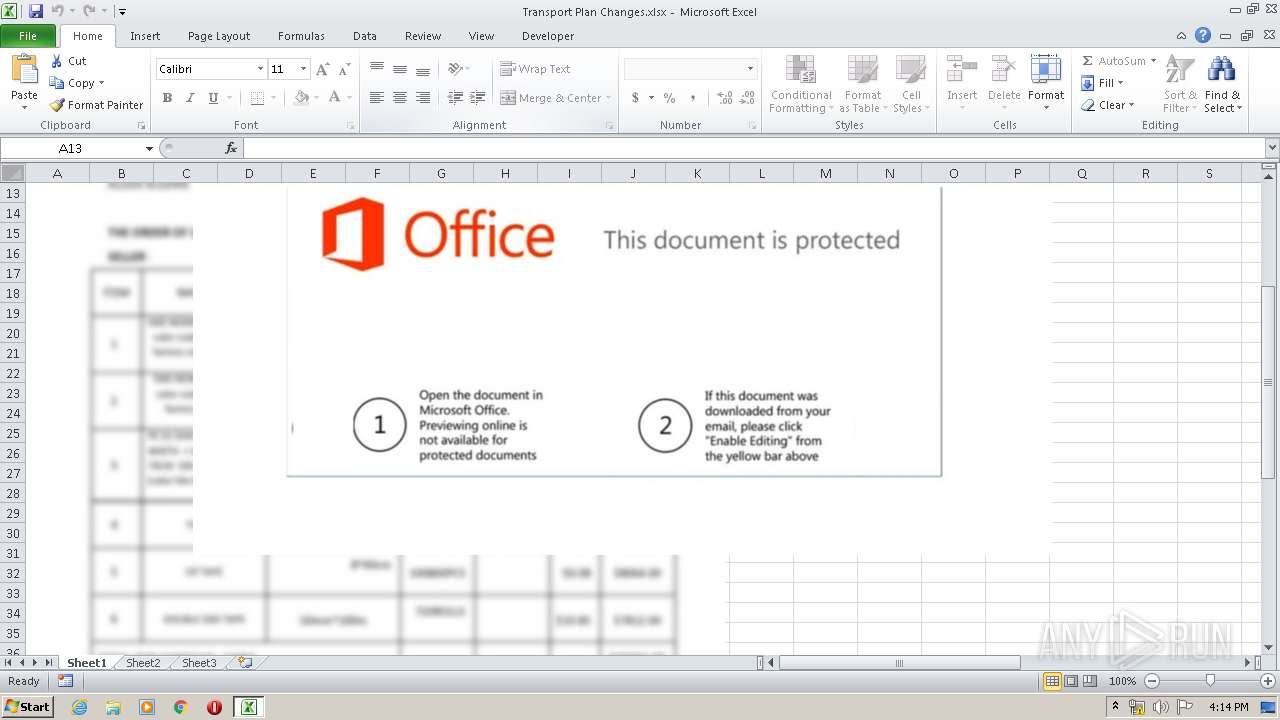
| File name: | Transport Plan Changes.xlsx |
| Full analysis: | https://app.any.run/tasks/88ee3746-5ba1-4e33-bab1-8dc48eaa4176 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 30, 2020, 15:12:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | 6222DDCA4E38E9D468484E19E8B91CF5 |
| SHA1: | 2684091597C692A5DD5E4D5A7A146AFF42825EB9 |
| SHA256: | 74EB485547633DA2DA2556DD5245DE3803D8291FC01A20A67D95944741F21E8B |
| SSDEEP: | 12288:xk9M9mriiTDYVYXe0JRgJqWYOFMx9T3b+UbaAW1WRabxHdQ79p7QuNnLR9k:69M98iin6GgMWYO6H7TbaBK2Q79pkag |
MALICIOUS
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 3320)
Writes to a start menu file
- chlz.exe (PID: 2756)
- chlz.exe (PID: 588)
- chlz.exe (PID: 3384)
- chlz.exe (PID: 2908)
- chlz.exe (PID: 2976)
- chlz.exe (PID: 3260)
- chlz.exe (PID: 3752)
- chlz.exe (PID: 3424)
- chlz.exe (PID: 3984)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 3632)
- chlz.exe (PID: 1356)
- chlz.exe (PID: 2740)
- chlz.exe (PID: 2956)
- chlz.exe (PID: 4092)
- chlz.exe (PID: 3632)
- chlz.exe (PID: 1916)
- chlz.exe (PID: 3500)
- chlz.exe (PID: 2892)
- chlz.exe (PID: 252)
- chlz.exe (PID: 2840)
- chlz.exe (PID: 3860)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 772)
- chlz.exe (PID: 2648)
- chlz.exe (PID: 3372)
- chlz.exe (PID: 1688)
- chlz.exe (PID: 2396)
- chlz.exe (PID: 3824)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 2624)
- chlz.exe (PID: 2860)
- chlz.exe (PID: 3344)
- chlz.exe (PID: 2128)
- chlz.exe (PID: 2536)
- chlz.exe (PID: 3768)
- chlz.exe (PID: 2524)
- chlz.exe (PID: 580)
- chlz.exe (PID: 3960)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 3644)
- chlz.exe (PID: 3928)
- chlz.exe (PID: 2660)
- chlz.exe (PID: 3164)
- chlz.exe (PID: 2680)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 3960)
- chlz.exe (PID: 2360)
- chlz.exe (PID: 2760)
- chlz.exe (PID: 3448)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 2560)
- chlz.exe (PID: 3568)
- chlz.exe (PID: 3452)
- chlz.exe (PID: 3716)
- chlz.exe (PID: 3944)
- chlz.exe (PID: 852)
- chlz.exe (PID: 2420)
- chlz.exe (PID: 3644)
Application was dropped or rewritten from another process
- chlz.exe (PID: 944)
- vbc.exe (PID: 3536)
- chlz.exe (PID: 2556)
- chlz.exe (PID: 588)
- chlz.exe (PID: 2368)
- chlz.exe (PID: 1900)
- chlz.exe (PID: 3384)
- chlz.exe (PID: 748)
- chlz.exe (PID: 2756)
- chlz.exe (PID: 2652)
- chlz.exe (PID: 2908)
- chlz.exe (PID: 1928)
- chlz.exe (PID: 1760)
- chlz.exe (PID: 2976)
- chlz.exe (PID: 1256)
- chlz.exe (PID: 2788)
- chlz.exe (PID: 3260)
- chlz.exe (PID: 480)
- chlz.exe (PID: 332)
- chlz.exe (PID: 3752)
- chlz.exe (PID: 872)
- chlz.exe (PID: 3844)
- chlz.exe (PID: 2540)
- chlz.exe (PID: 3424)
- chlz.exe (PID: 2448)
- chlz.exe (PID: 3984)
- chlz.exe (PID: 2136)
- chlz.exe (PID: 4020)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 2552)
- chlz.exe (PID: 3632)
- chlz.exe (PID: 1548)
- chlz.exe (PID: 2372)
- chlz.exe (PID: 3376)
- chlz.exe (PID: 1356)
- chlz.exe (PID: 3720)
- chlz.exe (PID: 3000)
- chlz.exe (PID: 2956)
- chlz.exe (PID: 3004)
- chlz.exe (PID: 3632)
- chlz.exe (PID: 1516)
- chlz.exe (PID: 3748)
- chlz.exe (PID: 3752)
- chlz.exe (PID: 2740)
- chlz.exe (PID: 2736)
- chlz.exe (PID: 1024)
- chlz.exe (PID: 3412)
- chlz.exe (PID: 2692)
- chlz.exe (PID: 2696)
- chlz.exe (PID: 1504)
- chlz.exe (PID: 4092)
- chlz.exe (PID: 3500)
- chlz.exe (PID: 340)
- chlz.exe (PID: 252)
- chlz.exe (PID: 2672)
- chlz.exe (PID: 4056)
- chlz.exe (PID: 1916)
- chlz.exe (PID: 1724)
- chlz.exe (PID: 2892)
- chlz.exe (PID: 3456)
- chlz.exe (PID: 2840)
- chlz.exe (PID: 2616)
- chlz.exe (PID: 2824)
- chlz.exe (PID: 3360)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 4008)
- chlz.exe (PID: 2072)
- chlz.exe (PID: 3540)
- chlz.exe (PID: 280)
- chlz.exe (PID: 3860)
- chlz.exe (PID: 2412)
- chlz.exe (PID: 2608)
- chlz.exe (PID: 2648)
- chlz.exe (PID: 3588)
- chlz.exe (PID: 2152)
- chlz.exe (PID: 772)
- chlz.exe (PID: 2296)
- chlz.exe (PID: 3168)
- chlz.exe (PID: 2612)
- chlz.exe (PID: 2396)
- chlz.exe (PID: 1348)
- chlz.exe (PID: 3824)
- chlz.exe (PID: 2012)
- chlz.exe (PID: 3324)
- chlz.exe (PID: 1688)
- chlz.exe (PID: 2992)
- chlz.exe (PID: 3612)
- chlz.exe (PID: 4084)
- chlz.exe (PID: 2624)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 2896)
- chlz.exe (PID: 2860)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 3824)
- chlz.exe (PID: 3344)
- chlz.exe (PID: 2080)
- chlz.exe (PID: 3064)
- chlz.exe (PID: 2128)
- chlz.exe (PID: 912)
- chlz.exe (PID: 548)
- chlz.exe (PID: 3792)
- chlz.exe (PID: 2536)
- chlz.exe (PID: 3892)
- chlz.exe (PID: 3756)
- chlz.exe (PID: 3768)
- chlz.exe (PID: 3600)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 2524)
- chlz.exe (PID: 3960)
- chlz.exe (PID: 3528)
- chlz.exe (PID: 3496)
- chlz.exe (PID: 2272)
- chlz.exe (PID: 2392)
- chlz.exe (PID: 580)
- chlz.exe (PID: 3888)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 4072)
- chlz.exe (PID: 2428)
- chlz.exe (PID: 3484)
- chlz.exe (PID: 2724)
- chlz.exe (PID: 3920)
- chlz.exe (PID: 2396)
- chlz.exe (PID: 3928)
- chlz.exe (PID: 3424)
- chlz.exe (PID: 3644)
- chlz.exe (PID: 2660)
- chlz.exe (PID: 3140)
- chlz.exe (PID: 3736)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 3164)
- chlz.exe (PID: 1156)
- chlz.exe (PID: 3016)
- chlz.exe (PID: 3036)
- chlz.exe (PID: 2908)
- chlz.exe (PID: 2360)
- chlz.exe (PID: 3576)
- chlz.exe (PID: 2808)
- chlz.exe (PID: 2680)
- chlz.exe (PID: 2116)
- chlz.exe (PID: 608)
- chlz.exe (PID: 3308)
- chlz.exe (PID: 3960)
- chlz.exe (PID: 3836)
- chlz.exe (PID: 3336)
- chlz.exe (PID: 2760)
- chlz.exe (PID: 3968)
- chlz.exe (PID: 2932)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 2244)
- chlz.exe (PID: 3568)
- chlz.exe (PID: 3660)
- chlz.exe (PID: 1248)
- chlz.exe (PID: 2548)
- chlz.exe (PID: 3448)
- chlz.exe (PID: 3176)
- chlz.exe (PID: 2560)
- chlz.exe (PID: 2976)
- chlz.exe (PID: 2380)
- chlz.exe (PID: 3192)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 3716)
- chlz.exe (PID: 2588)
- chlz.exe (PID: 3452)
- chlz.exe (PID: 3472)
- chlz.exe (PID: 2640)
- chlz.exe (PID: 852)
- chlz.exe (PID: 3608)
- chlz.exe (PID: 2420)
- chlz.exe (PID: 3944)
- chlz.exe (PID: 2884)
- chlz.exe (PID: 2580)
- chlz.exe (PID: 3644)
- chlz.exe (PID: 2812)
- chlz.exe (PID: 3592)
- chlz.exe (PID: 3060)
- chlz.exe (PID: 3332)
- chlz.exe (PID: 3372)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3320)
Downloads executable files from the Internet
- EQNEDT32.EXE (PID: 3320)
Changes the autorun value in the registry
- audiodg.exe (PID: 2576)
FORMBOOK was detected
- audiodg.exe (PID: 2576)
- Firefox.exe (PID: 2488)
- explorer.exe (PID: 372)
Actions looks like stealing of personal data
- audiodg.exe (PID: 2576)
Stealing of credential data
- audiodg.exe (PID: 2576)
Connects to CnC server
- explorer.exe (PID: 372)
SUSPICIOUS
Reads Internet Cache Settings
- EQNEDT32.EXE (PID: 3320)
Executed via COM
- EQNEDT32.EXE (PID: 3320)
Executable content was dropped or overwritten
- vbc.exe (PID: 3536)
- EQNEDT32.EXE (PID: 3320)
Creates files in the user directory
- chlz.exe (PID: 2756)
- vbc.exe (PID: 3536)
- EQNEDT32.EXE (PID: 3320)
- chlz.exe (PID: 588)
- audiodg.exe (PID: 2576)
- chlz.exe (PID: 3384)
- chlz.exe (PID: 2908)
- chlz.exe (PID: 2976)
- chlz.exe (PID: 3260)
- chlz.exe (PID: 3752)
- chlz.exe (PID: 3424)
- chlz.exe (PID: 3984)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 3632)
- chlz.exe (PID: 1356)
- chlz.exe (PID: 2956)
- chlz.exe (PID: 2740)
- chlz.exe (PID: 3632)
- chlz.exe (PID: 4092)
- chlz.exe (PID: 1916)
- chlz.exe (PID: 3500)
- chlz.exe (PID: 252)
- chlz.exe (PID: 2892)
- chlz.exe (PID: 2840)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 3860)
- chlz.exe (PID: 2648)
- chlz.exe (PID: 3372)
- chlz.exe (PID: 772)
- chlz.exe (PID: 2396)
- chlz.exe (PID: 3824)
- chlz.exe (PID: 1688)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 2624)
- chlz.exe (PID: 3344)
- chlz.exe (PID: 2860)
- chlz.exe (PID: 3768)
- chlz.exe (PID: 2128)
- chlz.exe (PID: 2536)
- chlz.exe (PID: 3960)
- chlz.exe (PID: 2524)
- chlz.exe (PID: 580)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 3644)
- chlz.exe (PID: 3928)
- chlz.exe (PID: 2660)
- chlz.exe (PID: 3164)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 2680)
- chlz.exe (PID: 3960)
- chlz.exe (PID: 2360)
- chlz.exe (PID: 2760)
- chlz.exe (PID: 3448)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 2560)
- chlz.exe (PID: 3568)
- chlz.exe (PID: 3716)
- chlz.exe (PID: 3452)
- chlz.exe (PID: 3944)
- chlz.exe (PID: 852)
- chlz.exe (PID: 2420)
- chlz.exe (PID: 3644)
Starts itself from another location
- vbc.exe (PID: 3536)
Application launched itself
- chlz.exe (PID: 944)
- chlz.exe (PID: 588)
- chlz.exe (PID: 2368)
- chlz.exe (PID: 3384)
- chlz.exe (PID: 2652)
- chlz.exe (PID: 1760)
- chlz.exe (PID: 2788)
- chlz.exe (PID: 3260)
- chlz.exe (PID: 480)
- chlz.exe (PID: 872)
- chlz.exe (PID: 2448)
- chlz.exe (PID: 2136)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 3632)
- chlz.exe (PID: 1548)
- chlz.exe (PID: 3376)
- chlz.exe (PID: 3000)
- chlz.exe (PID: 2956)
- chlz.exe (PID: 3752)
- chlz.exe (PID: 3752)
- chlz.exe (PID: 3412)
- chlz.exe (PID: 3500)
- chlz.exe (PID: 2696)
- chlz.exe (PID: 2736)
- chlz.exe (PID: 1504)
- chlz.exe (PID: 1916)
- chlz.exe (PID: 340)
- chlz.exe (PID: 2824)
- chlz.exe (PID: 3456)
- chlz.exe (PID: 4056)
- chlz.exe (PID: 280)
- chlz.exe (PID: 2072)
- chlz.exe (PID: 2508)
- chlz.exe (PID: 772)
- chlz.exe (PID: 2296)
- chlz.exe (PID: 2152)
- chlz.exe (PID: 1348)
- chlz.exe (PID: 3824)
- chlz.exe (PID: 3588)
- chlz.exe (PID: 2612)
- chlz.exe (PID: 2896)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 3824)
- chlz.exe (PID: 2012)
- chlz.exe (PID: 3344)
- chlz.exe (PID: 3064)
- chlz.exe (PID: 548)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 3768)
- chlz.exe (PID: 3892)
- chlz.exe (PID: 2524)
- chlz.exe (PID: 3496)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 2428)
- chlz.exe (PID: 3888)
- chlz.exe (PID: 2392)
- chlz.exe (PID: 2724)
- chlz.exe (PID: 3928)
- chlz.exe (PID: 3644)
- chlz.exe (PID: 3016)
- chlz.exe (PID: 3736)
- chlz.exe (PID: 2396)
- chlz.exe (PID: 2808)
- chlz.exe (PID: 2908)
- chlz.exe (PID: 2680)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 3960)
- chlz.exe (PID: 3308)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 2116)
- chlz.exe (PID: 2760)
- chlz.exe (PID: 2932)
- chlz.exe (PID: 3660)
- chlz.exe (PID: 2244)
- chlz.exe (PID: 3176)
- chlz.exe (PID: 2560)
- chlz.exe (PID: 3452)
- chlz.exe (PID: 2380)
- chlz.exe (PID: 2588)
- chlz.exe (PID: 3472)
- chlz.exe (PID: 3944)
- chlz.exe (PID: 2640)
- chlz.exe (PID: 3608)
- chlz.exe (PID: 3592)
Loads DLL from Mozilla Firefox
- audiodg.exe (PID: 2576)
Executes scripts
- explorer.exe (PID: 372)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 372)
Uses NETSTAT.EXE to discover network connections
- explorer.exe (PID: 372)
Uses IPCONFIG.EXE to discover IP address
- explorer.exe (PID: 372)
Uses NETSH.EXE for network configuration
- explorer.exe (PID: 372)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1740)
Starts Microsoft Office Application
- explorer.exe (PID: 372)
Manual execution by user
- audiodg.exe (PID: 2576)
- rdpclip.exe (PID: 3772)
- cscript.exe (PID: 1876)
- mstsc.exe (PID: 3212)
- rundll32.exe (PID: 2004)
- lsm.exe (PID: 2856)
- dwm.exe (PID: 3152)
- rdpclip.exe (PID: 2780)
- NETSTAT.EXE (PID: 3900)
Reads the hosts file
- audiodg.exe (PID: 2576)
Creates files in the user directory
- Firefox.exe (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
276
Monitored processes
243
Malicious processes
104
Suspicious processes
16
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | chlz.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 280 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" 2 3540 11051750 | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 332 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 340 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" 2 1724 11036875 | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" 2 332 10991906 | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" 2 3792 11089296 | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 580 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | chlz.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 588 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | chlz.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 608 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
51 813
Read events
51 738
Write events
64
Delete events
11
Modification events
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ao0 |
Value: 616F3000CC060000010000000000000000000000 | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1740) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
Executable files
3
Suspicious files
73
Text files
60
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1740 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6BE1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3536 | vbc.exe | C:\Users\admin\AppData\Roaming\chlz\chlz.exe:ZoneIdentifier | — | |
MD5:— | SHA256:— | |||
| 3320 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\bk[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2576 | audiodg.exe | C:\Users\admin\AppData\Roaming\149MTU1F\149logrc.ini | binary | |
MD5:— | SHA256:— | |||
| 2756 | chlz.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\chlz.vbs | text | |
MD5:— | SHA256:— | |||
| 3424 | chlz.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\chlz.vbs | text | |
MD5:— | SHA256:— | |||
| 3536 | vbc.exe | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | executable | |
MD5:— | SHA256:— | |||
| 2488 | Firefox.exe | C:\Users\admin\AppData\Roaming\149MTU1F\149logrf.ini | binary | |
MD5:— | SHA256:— | |||
| 2508 | chlz.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\chlz.vbs | text | |
MD5:— | SHA256:— | |||
| 1740 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\4518BAFE.emf | emf | |
MD5:9DBC4E90F367DF7508C707F6806E8DCA | SHA256:78C2466C6539C3C9AECC57DD4B2EA6303724EEAEF9925FC568C6DA8FC6EFDE19 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
17
DNS requests
11
Threats
371
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
372 | explorer.exe | GET | — | 23.235.208.12:80 | http://www.islandsurfandsoul.com/c9c/?OrpDKZ=n2qqqtzDMFwDHxzkcMqRye7YUmivStKBg0nqnA8l1JQyCXH8WU+RLmDaBtolSJy7yesGwA==&8p=chUxZlTP2 | US | — | — | malicious |
372 | explorer.exe | POST | — | 198.54.112.48:80 | http://www.nyoxibwer.com/c9c/ | US | — | — | malicious |
372 | explorer.exe | POST | — | 23.235.208.12:80 | http://www.islandsurfandsoul.com/c9c/ | US | — | — | malicious |
372 | explorer.exe | POST | — | 184.168.221.89:80 | http://www.onfixers.com/c9c/ | US | — | — | malicious |
372 | explorer.exe | POST | — | 198.54.112.48:80 | http://www.nyoxibwer.com/c9c/ | US | — | — | malicious |
372 | explorer.exe | POST | — | 23.235.208.12:80 | http://www.islandsurfandsoul.com/c9c/ | US | — | — | malicious |
372 | explorer.exe | POST | — | 23.235.208.12:80 | http://www.islandsurfandsoul.com/c9c/ | US | — | — | malicious |
372 | explorer.exe | POST | — | 154.205.128.231:80 | http://www.kk2400.com/c9c/ | ZA | — | — | malicious |
372 | explorer.exe | GET | 404 | 154.205.128.231:80 | http://www.kk2400.com/c9c/?OrpDKZ=ggk2BmOCR8DzQuttUjrqPwG/9k+nGKoxPNyZEovjAi93yksuR6is5jN/FBEmBiL+CqhacQ==&8p=chUxZlTP2 | ZA | html | 1.28 Kb | malicious |
372 | explorer.exe | GET | — | 198.54.112.48:80 | http://www.nyoxibwer.com/c9c/?OrpDKZ=9+GzjCWfCB5OpbaIwLLG+DEC9yR+Eby9VR1o4uz+w/wIAPI0zrxt1y/akEMo4wphdJlLMw==&8p=chUxZlTP2 | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3320 | EQNEDT32.EXE | 109.169.89.118:80 | easydatatransfercleansystemprofessional.duckdns.org | iomart Cloud Services Limited. | GB | malicious |
372 | explorer.exe | 35.242.251.130:80 | www.carolinachildrensmuseum.com | — | US | malicious |
372 | explorer.exe | 23.235.208.12:80 | www.islandsurfandsoul.com | InMotion Hosting, Inc. | US | malicious |
372 | explorer.exe | 184.168.221.89:80 | www.onfixers.com | GoDaddy.com, LLC | US | malicious |
372 | explorer.exe | 154.205.128.231:80 | www.kk2400.com | MacroLAN | ZA | malicious |
372 | explorer.exe | 198.54.112.48:80 | www.nyoxibwer.com | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
easydatatransfercleansystemprofessional.duckdns.org |
| malicious |
www.carolinachildrensmuseum.com |
| malicious |
www.nyoxibwer.com |
| malicious |
dns.msftncsi.com |
| shared |
www.wwwbola168.com |
| unknown |
www.islandsurfandsoul.com |
| malicious |
www.vpp-services.com |
| unknown |
www.onfixers.com |
| malicious |
www.kk2400.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
3320 | EQNEDT32.EXE | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
3320 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
372 | explorer.exe | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYN resend different seq on SYN recv |
372 | explorer.exe | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYNACK resend with different ack |
9 ETPRO signatures available at the full report