| File name: | fortnite.exe |
| Full analysis: | https://app.any.run/tasks/2ab11de4-7d96-4088-b95d-bb4cb53887be |
| Verdict: | Malicious activity |
| Threats: | DarkVision RAT is a low-cost, modular Remote Access Trojan that gives attackers remote control of infected Windows hosts. Initially observed around 2020 and sold in underground marketplaces, DarkVision has become notable for its full feature set (keylogging, screen capture, file theft, remote command execution and plugin support) and for being distributed via multi-stage loaders in recent campaigns. |
| Analysis date: | October 29, 2024, 20:14:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 8 sections |
| MD5: | 5999098B0F0E4E25E826092A7F1E7598 |
| SHA1: | 76F8454429E4A59E4B7361415A6D62E08207577E |
| SHA256: | 74E66581CDA6B55F9DBFCFE260FAEC1DAD8A38D9FA0C5C2F45E64D16E6A11D4E |
| SSDEEP: | 49152:sKqM08jShjsE6gboOCy/7liG3VQnv0MF4jVkFou6hboDHrwj6NqffffIR9OVdQ8D:a8jShjsE6gbo3y5YxFiffff |
MALICIOUS
Adds extension to the Windows Defender exclusion list
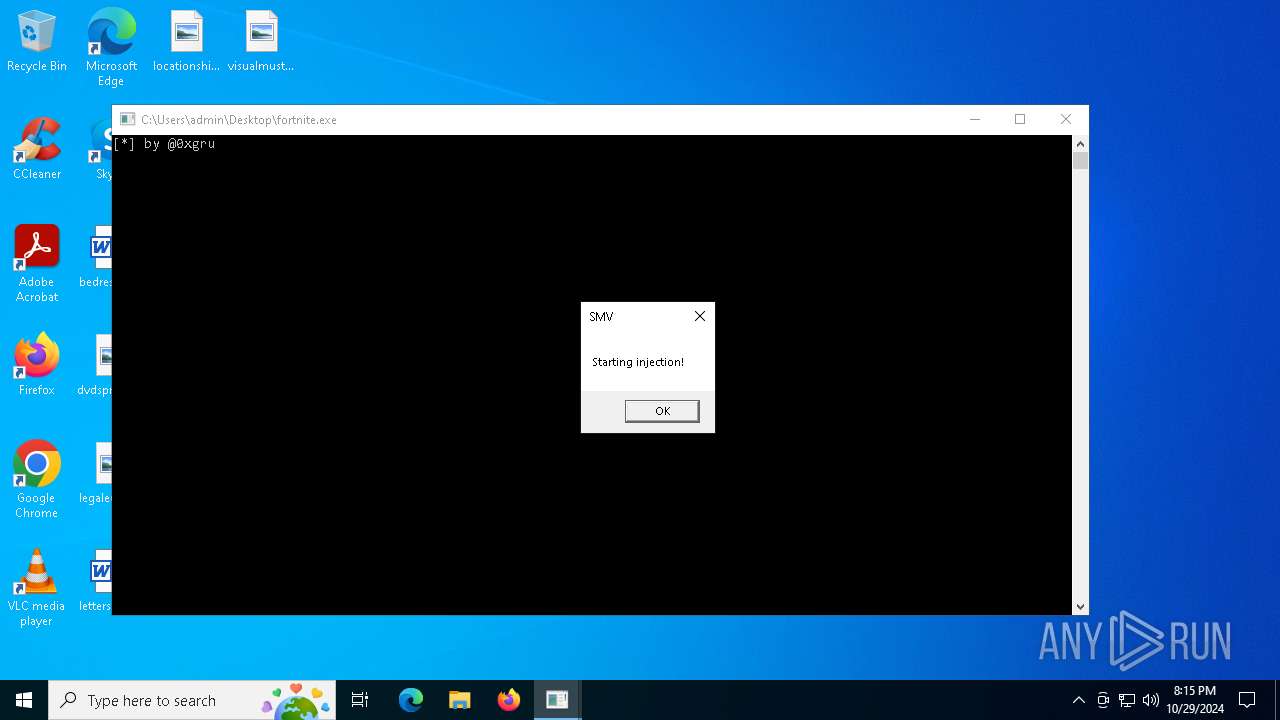
- fortnite.exe (PID: 6756)
- cmd.exe (PID: 5624)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 1008)
[YARA] DarkVision RAT is detected
- fortnite.exe (PID: 6756)
DARKVISION has been detected (SURICATA)
- OperationEnigma4.exe (PID: 6464)
Connects to the CnC server
- OperationEnigma4.exe (PID: 6464)
SUSPICIOUS
Hides command output
- cmd.exe (PID: 5624)
- cmd.exe (PID: 3824)
- cmd.exe (PID: 5036)
- cmd.exe (PID: 1008)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5036)
Starts CMD.EXE for commands execution
- fortnite.exe (PID: 6756)
Script adds exclusion extension to Windows Defender
- cmd.exe (PID: 5624)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5624)
Executable content was dropped or overwritten
- fortnite.exe (PID: 6756)
Connects to unusual port
- OperationEnigma4.exe (PID: 6464)
INFO
Creates a new folder
- cmd.exe (PID: 3824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:10:29 20:10:54+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 641536 |
| InitializedDataSize: | 855040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a6bc |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
136
Monitored processes
12
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | attrib +h +s "C:\ProgramData\Microsoft\WindowsApps" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | C:\WINDOWS\system32\cmd.exe /c schtasks /create /tn "OperationEnigma" /tr "C:\ProgramData\Microsoft\WindowsApps\OperationEnigma4.exe" /sc onlogon /rl highest /f >nul 2>&1 | C:\Windows\System32\cmd.exe | fortnite.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3824 | C:\WINDOWS\system32\cmd.exe /c mkdir "C:\ProgramData\Microsoft\WindowsApps" >nul 2>&1 | C:\Windows\System32\cmd.exe | — | fortnite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | C:\WINDOWS\system32\cmd.exe /c attrib +h +s "C:\ProgramData\Microsoft\WindowsApps" >nul 2>&1 | C:\Windows\System32\cmd.exe | — | fortnite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | C:\WINDOWS\system32\cmd.exe /c color 3 | C:\Windows\System32\cmd.exe | — | fortnite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5624 | C:\WINDOWS\system32\cmd.exe /c powershell -Command "Add-MpPreference -ExclusionExtension 'exe'" >nul 2>&1 | C:\Windows\System32\cmd.exe | — | fortnite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6436 | schtasks /create /tn "OperationEnigma" /tr "C:\ProgramData\Microsoft\WindowsApps\OperationEnigma4.exe" /sc onlogon /rl highest /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6464 | "C:\ProgramData\Microsoft\WindowsApps\OperationEnigma4.exe" | C:\ProgramData\Microsoft\WindowsApps\OperationEnigma4.exe | fortnite.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6692 | "C:\Users\admin\Desktop\fortnite.exe" | C:\Users\admin\Desktop\fortnite.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6756 | "C:\Users\admin\Desktop\fortnite.exe" | C:\Users\admin\Desktop\fortnite.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
8 979
Read events
8 977
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6464) OperationEnigma4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\{8BF8A49D-4386-4359-971B-4BE3BECBC99B} |
| Operation: | write | Name: | {78194B06-8ED4-4E5D-977B-F13329B499F1} |
Value: C0C0EA3E3F2ADB0100000000 | |||
| (PID) Process: | (6464) OperationEnigma4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\{8BF8A49D-4386-4359-971B-4BE3BECBC99B} |
| Operation: | write | Name: | {74AA43ED-C264-4E87-B74F-402B74D57708} |
Value: C:\ProgramData\Microsoft\WindowsApps\OperationEnigma4.exe | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6884 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3pec2bdo.euk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6884 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_oxcxp1q5.z3s.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6884 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:61192FFF36379F3215413D5019251DF9 | SHA256:F28B2D595F184DA940BBEBDC4875ED69E5085D690BF929A0CBB86FD6930AD3A7 | |||
| 6756 | fortnite.exe | C:\ProgramData\Microsoft\WindowsApps\OperationEnigma4.exe | executable | |
MD5:6EDCC30095AAA8BAD21C5E0A1A92AA9C | SHA256:BA3CC8D5120E54C6C8DD15143CDDF6B2040E83704CAAD04373B05EA5FA9A9179 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
72
DNS requests
9
Threats
88
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7044 | RUXIMICS.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7044 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 404 | 104.26.2.16:443 | https://rentry.co/razorrat/rawYDHXBF8ZTF | unknown | html | 4.35 Kb | unknown |
— | — | GET | 404 | 172.67.75.40:443 | https://rentry.co/razorrat/rawYDHXBF8ZTF | unknown | html | 4.35 Kb | unknown |
— | — | GET | 404 | 104.26.2.16:443 | https://rentry.co/razorrat/rawYDHXBF8ZTF | unknown | html | 4.35 Kb | unknown |
— | — | GET | 404 | 104.26.3.16:443 | https://rentry.co/razorrat/rawYDHXBF8ZTF | unknown | html | 4.35 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
7044 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7044 | RUXIMICS.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
rentry.co |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
6464 | OperationEnigma4.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
6464 | OperationEnigma4.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 24 |
6464 | OperationEnigma4.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkVision Check-in |
6464 | OperationEnigma4.exe | A Network Trojan was detected | ET MALWARE Win32/DarkVision RAT CnC Checkin M1 |
6464 | OperationEnigma4.exe | A Network Trojan was detected | ET MALWARE Win32/DarkVision RAT CnC Checkin M1 |
6464 | OperationEnigma4.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkVision Check-in |
6464 | OperationEnigma4.exe | A Network Trojan was detected | ET MALWARE Win32/DarkVision RAT CnC Checkin M1 |
6464 | OperationEnigma4.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkVision Check-in |
6464 | OperationEnigma4.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |