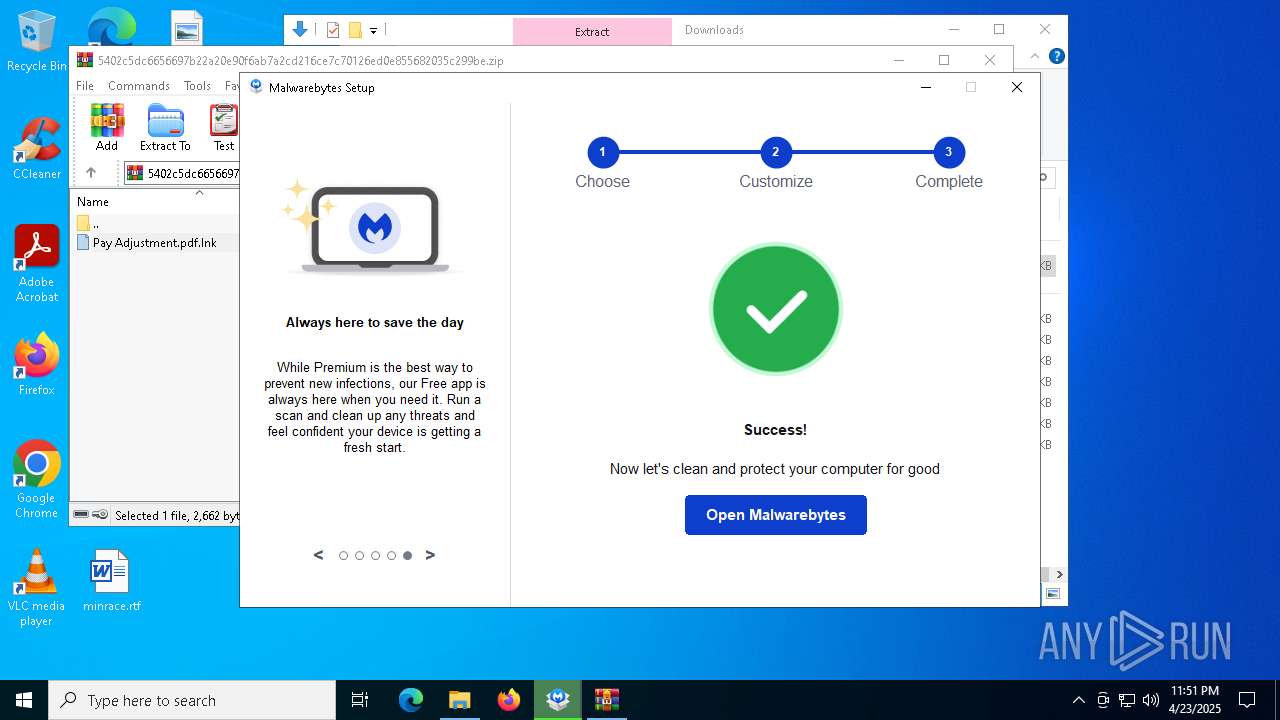
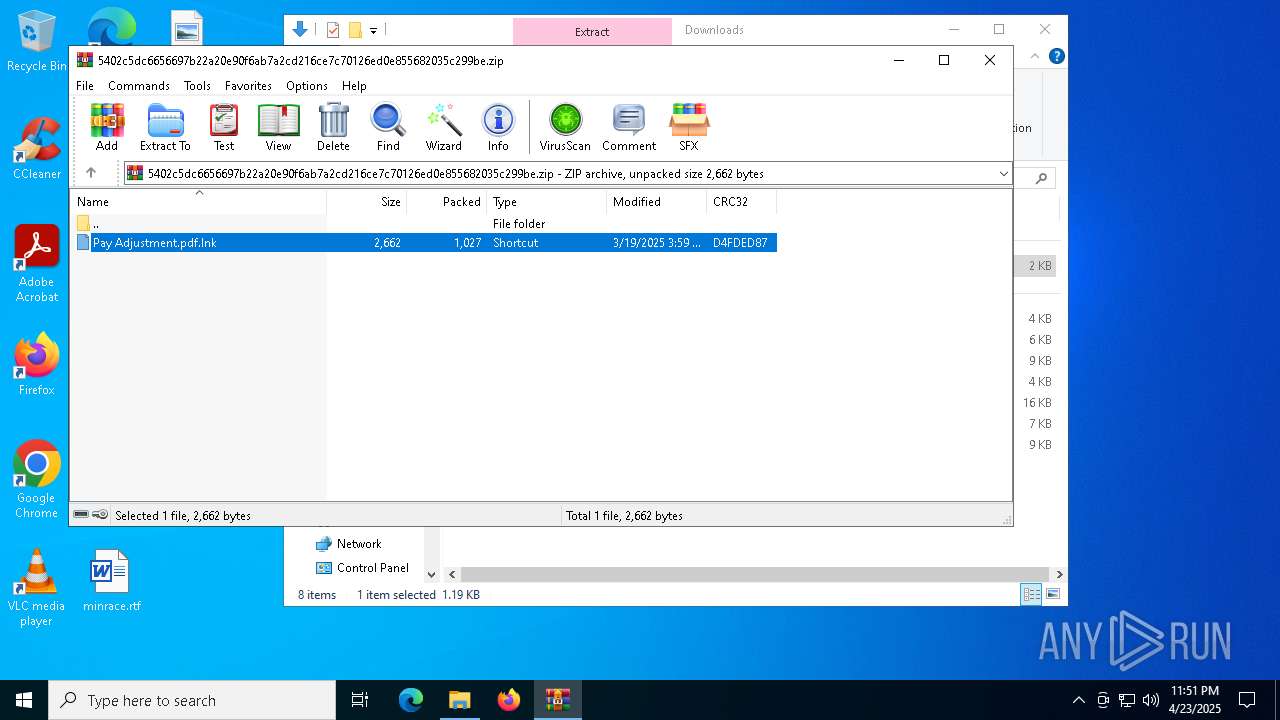
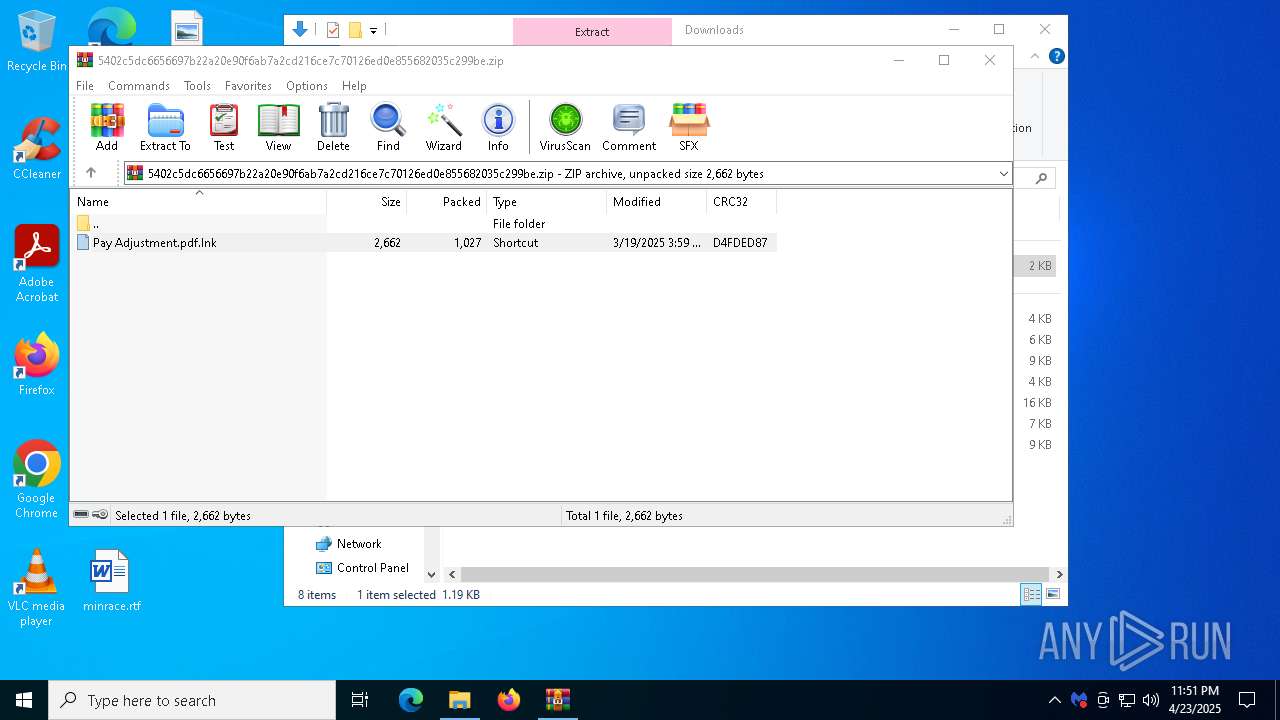
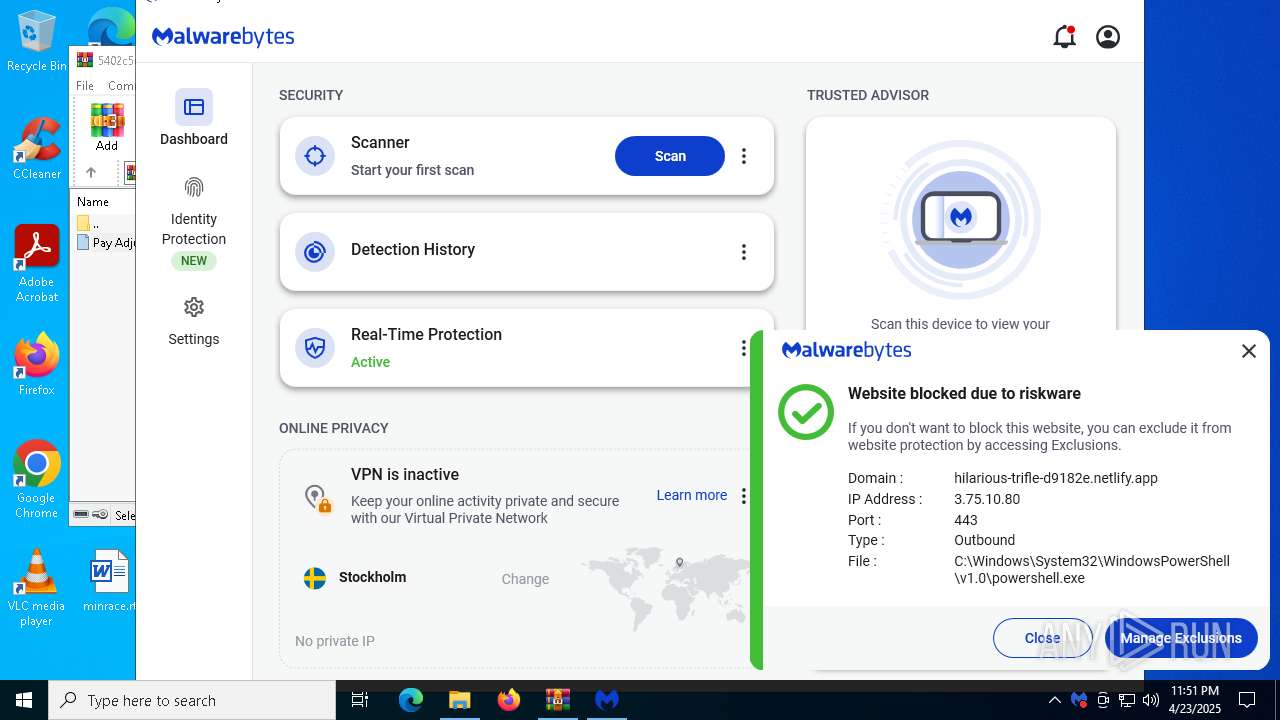
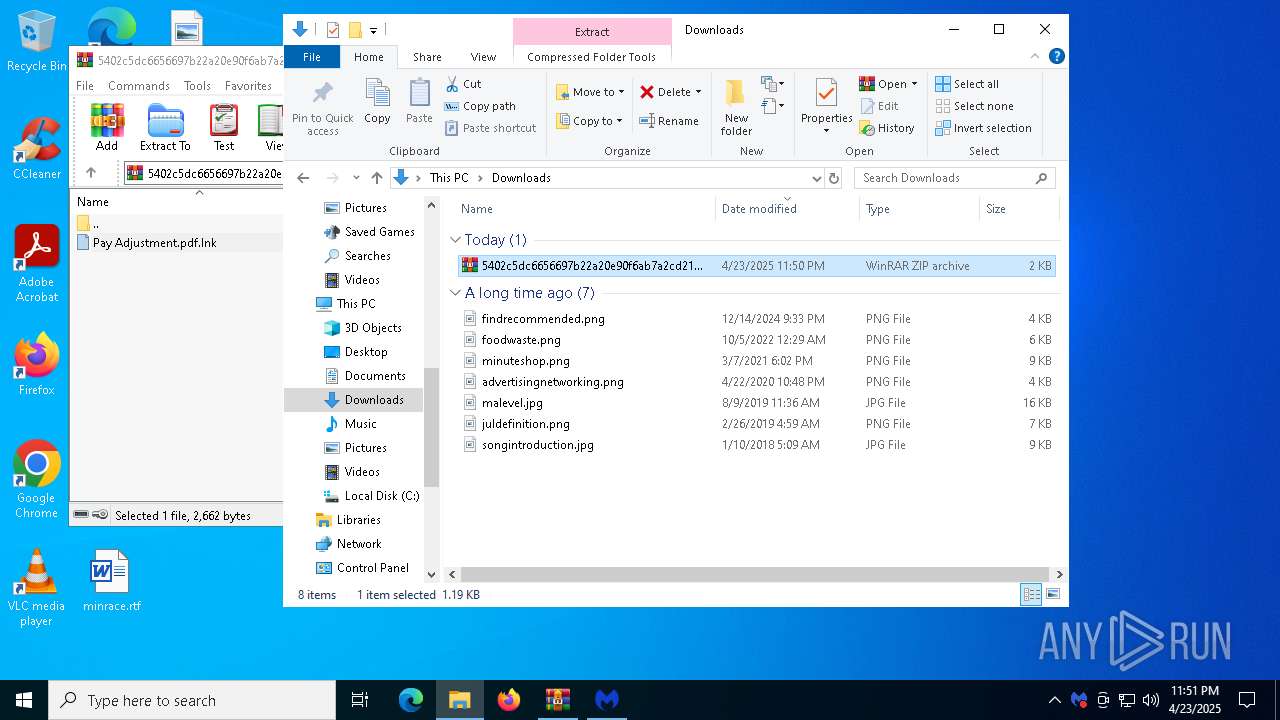
| File name: | MBSetup.exe |
| Full analysis: | https://app.any.run/tasks/ac8e55e8-ae40-4542-954a-564098efe02e |
| Verdict: | Malicious activity |
| Threats: | Havoc is an advanced post-exploitation framework used by hackers to take control of a system once they've breached it. With Havoc, attackers can run commands remotely, inject malicious processes, and access sensitive data. It's often used in targeted attacks, allowing cybercriminals to stay hidden in a network while stealing information or launching further attacks. Its flexibility and ability to bypass detection make it a serious threat, especially in environments that rely on traditional security tools. |
| Analysis date: | April 23, 2025, 23:47:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | B6D8B7E6F74196F62CABA2CA77A7AE91 |
| SHA1: | 6AC9C99F084B5772440E2F135B8D5365F7F45314 |
| SHA256: | 74B0BF9C17091AB1C6C61AF0AEFBC599F1ECC0FFF6DEE0144A3DFD5CD1F5E18F |
| SSDEEP: | 98304:gWn8nBJ4ZfXM5t0X1NrH22IT1PD2222222721vFdGBeQN0aFvGSSRkrlcfABLqIL:DXL |
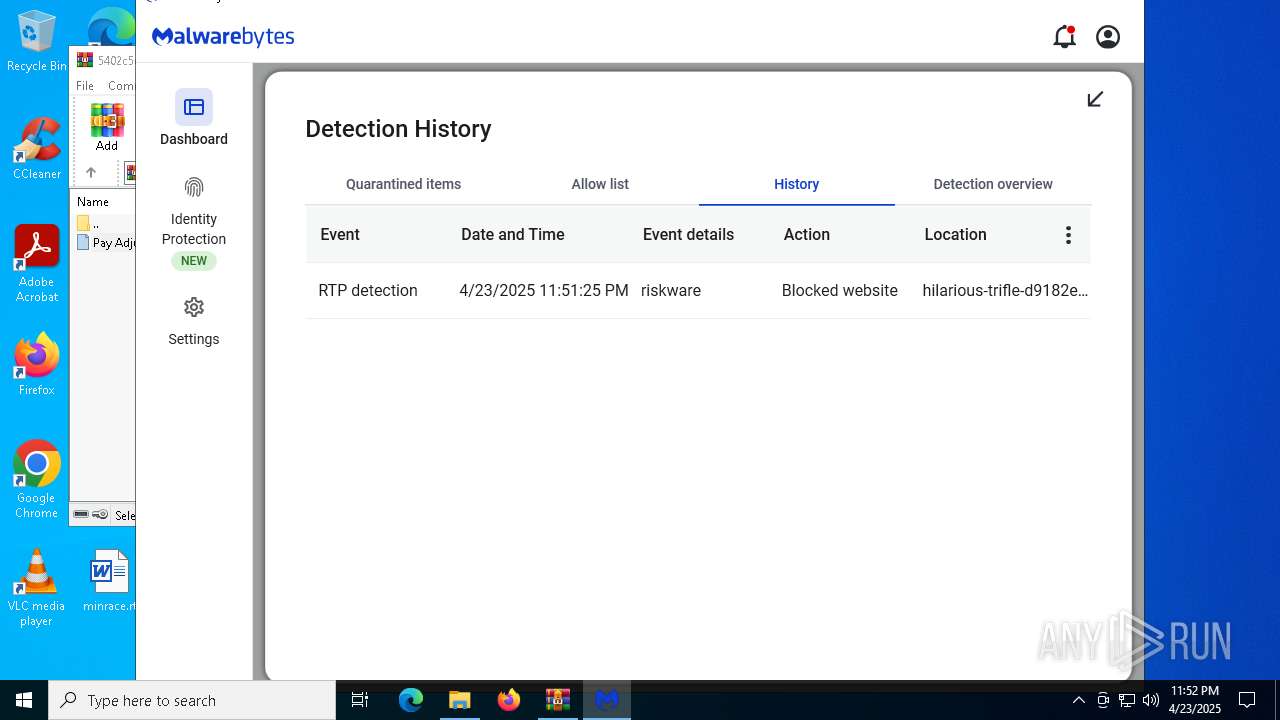
MALICIOUS
HAVOC has been found (auto)
- firefox.exe (PID: 968)
- WinRAR.exe (PID: 5668)
Actions looks like stealing of personal data
- MBAMService.exe (PID: 7808)
Run PowerShell with an invisible window
- powershell.exe (PID: 8220)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 9164)
Bypass execution policy to execute commands
- powershell.exe (PID: 8220)
SUSPICIOUS
Reads the BIOS version
- MBSetup.exe (PID: 6808)
- MBAMService.exe (PID: 7808)
The process verifies whether the antivirus software is installed
- MBSetup.exe (PID: 6808)
- MBAMInstallerService.exe (PID: 664)
- MBVpnTunnelService.exe (PID: 4276)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7728)
- MBAMService.exe (PID: 7808)
- Malwarebytes.exe (PID: 8820)
- Malwarebytes.exe (PID: 8900)
- Malwarebytes.exe (PID: 8972)
- MBAMWsc.exe (PID: 8652)
Creates files in the driver directory
- MBSetup.exe (PID: 6808)
- MBAMInstallerService.exe (PID: 664)
- MBVpnTunnelService.exe (PID: 4276)
- MBAMService.exe (PID: 7728)
- MBAMService.exe (PID: 7808)
- drvinst.exe (PID: 7484)
Searches for installed software
- MBAMInstallerService.exe (PID: 664)
- MBSetup.exe (PID: 6808)
- MBAMService.exe (PID: 7808)
Executable content was dropped or overwritten
- MBSetup.exe (PID: 6808)
- MBAMInstallerService.exe (PID: 664)
- MBVpnTunnelService.exe (PID: 4276)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7728)
- MBAMService.exe (PID: 7808)
Executes as Windows Service
- MBAMInstallerService.exe (PID: 664)
- MBAMService.exe (PID: 7808)
The process drops C-runtime libraries
- MBAMInstallerService.exe (PID: 664)
Drops 7-zip archiver for unpacking
- MBAMInstallerService.exe (PID: 664)
Drops a system driver (possible attempt to evade defenses)
- MBAMInstallerService.exe (PID: 664)
- MBVpnTunnelService.exe (PID: 4276)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7728)
- MBAMService.exe (PID: 7808)
Changes Internet Explorer settings (feature browser emulation)
- MBAMInstallerService.exe (PID: 664)
- MBAMService.exe (PID: 7808)
Adds/modifies Windows certificates
- MBAMInstallerService.exe (PID: 664)
- MBAMService.exe (PID: 7808)
The process creates files with name similar to system file names
- MBAMInstallerService.exe (PID: 664)
Process drops legitimate windows executable
- MBAMInstallerService.exe (PID: 664)
- MBAMService.exe (PID: 7808)
Reads security settings of Internet Explorer
- MBAMService.exe (PID: 7808)
- ig.exe (PID: 1240)
- WinRAR.exe (PID: 5668)
- Malwarebytes.exe (PID: 8820)
Creates/Modifies COM task schedule object
- MBAMService.exe (PID: 7808)
Creates or modifies Windows services
- MBAMService.exe (PID: 7808)
- MBAMService.exe (PID: 7728)
Creates a software uninstall entry
- MBAMInstallerService.exe (PID: 664)
Application launched itself
- Malwarebytes.exe (PID: 8900)
Downloads file from URI via Powershell
- powershell.exe (PID: 8220)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5668)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 9164)
The process executes Powershell scripts
- cmd.exe (PID: 9164)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 9164)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 9164)
There is functionality for taking screenshot (YARA)
- Malwarebytes.exe (PID: 8820)
INFO
Checks supported languages
- MBSetup.exe (PID: 6808)
- MBAMInstallerService.exe (PID: 664)
- MBVpnTunnelService.exe (PID: 4276)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7808)
- ig.exe (PID: 1240)
- MBAMWsc.exe (PID: 8652)
- Malwarebytes.exe (PID: 8820)
- Malwarebytes.exe (PID: 8900)
- MBAMService.exe (PID: 7728)
- Malwarebytes.exe (PID: 8972)
Reads the computer name
- MBSetup.exe (PID: 6808)
- MBAMInstallerService.exe (PID: 664)
- MBVpnTunnelService.exe (PID: 4276)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7728)
- MBAMService.exe (PID: 7808)
- ig.exe (PID: 1240)
- MBAMWsc.exe (PID: 8652)
- Malwarebytes.exe (PID: 8820)
- Malwarebytes.exe (PID: 8900)
- Malwarebytes.exe (PID: 8972)
Creates files in the program directory
- MBSetup.exe (PID: 6808)
- MBVpnTunnelService.exe (PID: 4276)
- MBAMInstallerService.exe (PID: 664)
- MBAMService.exe (PID: 7808)
- Malwarebytes.exe (PID: 8820)
Create files in a temporary directory
- MBSetup.exe (PID: 6808)
Reads the machine GUID from the registry
- MBSetup.exe (PID: 6808)
- MBAMInstallerService.exe (PID: 664)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7808)
The sample compiled with english language support
- MBSetup.exe (PID: 6808)
- MBAMInstallerService.exe (PID: 664)
- MBVpnTunnelService.exe (PID: 4276)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7728)
- MBAMService.exe (PID: 7808)
Reads the software policy settings
- MBAMInstallerService.exe (PID: 664)
- slui.exe (PID: 864)
- slui.exe (PID: 4068)
- MBSetup.exe (PID: 6808)
- drvinst.exe (PID: 7484)
- MBAMService.exe (PID: 7808)
- Malwarebytes.exe (PID: 8820)
Checks proxy server information
- MBSetup.exe (PID: 6808)
- slui.exe (PID: 4068)
- Malwarebytes.exe (PID: 8820)
- powershell.exe (PID: 8220)
Application launched itself
- firefox.exe (PID: 5416)
- firefox.exe (PID: 968)
Manual execution by a user
- firefox.exe (PID: 5416)
- WinRAR.exe (PID: 5668)
- Malwarebytes.exe (PID: 8900)
The sample compiled with spanish language support
- MBAMInstallerService.exe (PID: 664)
Adds/modifies Windows certificates
- drvinst.exe (PID: 7484)
Reads Environment values
- MBAMService.exe (PID: 7808)
Reads the time zone
- MBAMService.exe (PID: 7808)
Reads CPU info
- MBAMService.exe (PID: 7808)
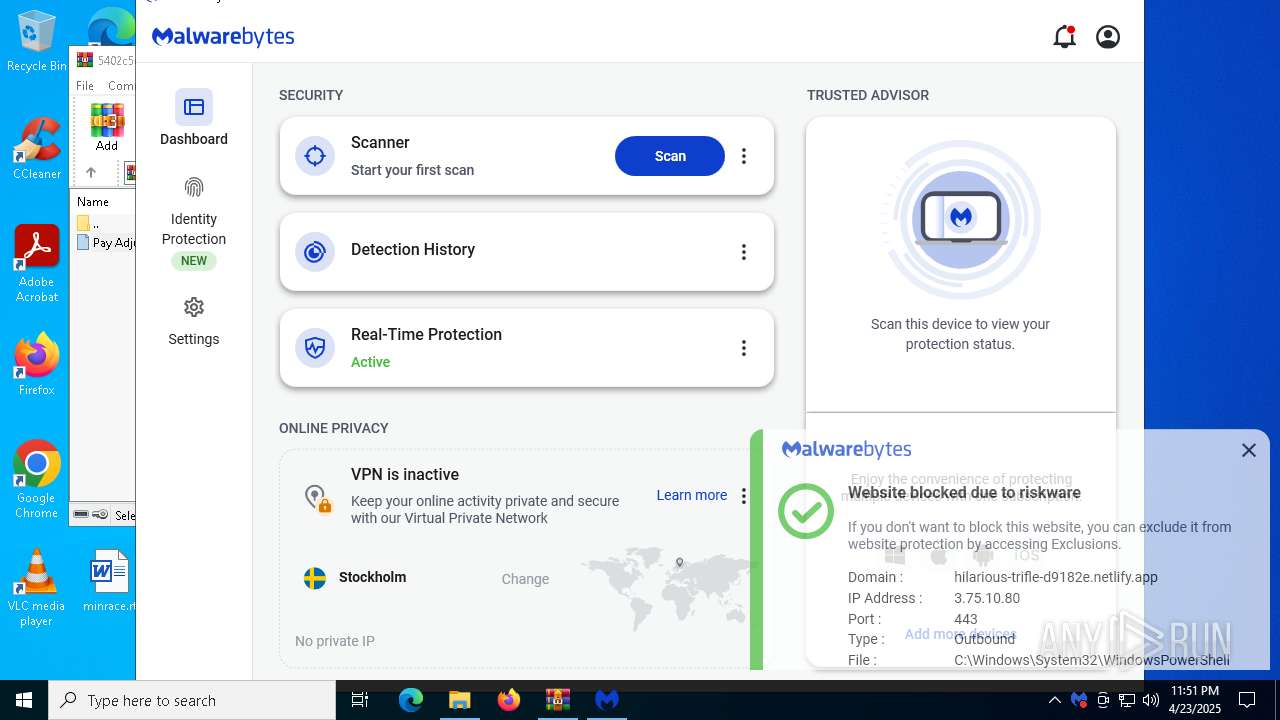
CONNECTWISE has been detected
- MBAMService.exe (PID: 7808)
Creates files or folders in the user directory
- Malwarebytes.exe (PID: 8820)
Process checks whether UAC notifications are on
- Malwarebytes.exe (PID: 8820)
Process checks computer location settings
- Malwarebytes.exe (PID: 8820)
Disables trace logs
- powershell.exe (PID: 8220)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:19 17:48:54+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 750080 |
| InitializedDataSize: | 1796608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6ee6e |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.2.88 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Malwarebytes |
| FileDescription: | Malwarebytes Setup |
| FileVersion: | 5.1.2.88 |
| LegalCopyright: | Copyright (C) 2017 - 2024 Malwarebytes, Inc. All rights reserved. |
| InternalName: | MBSetup.exe |
| OriginalFileName: | MBSetup.exe |
| ProductName: | Malwarebytes |
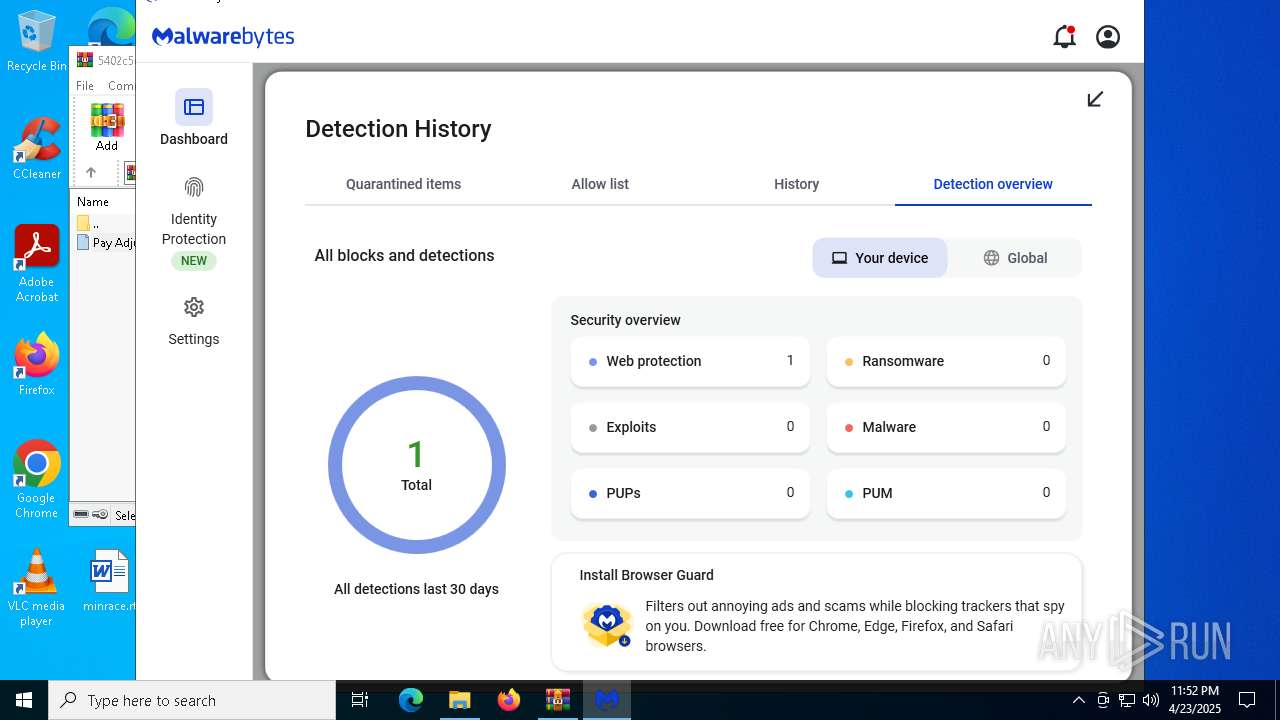
Total processes
175
Monitored processes
39
Malicious processes
12
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Program Files\Malwarebytes\Anti-Malware\MBAMInstallerService.exe" | C:\Program Files\Malwarebytes\Anti-Malware\MBAMInstallerService.exe | services.exe | ||||||||||||
User: SYSTEM Company: Malwarebytes Integrity Level: SYSTEM Description: Malwarebytes Installer Service Exit code: 0 Version: 5.1.0.189 Modules
| |||||||||||||||
| 864 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5536 -childID 5 -isForBrowser -prefsHandle 4920 -prefMapHandle 5060 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1436 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e67af47e-5544-4f83-9df5-91ccb0411543} 968 "\\.\pipe\gecko-crash-server-pipe.968" 19bcc69d310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1240 | ig.exe secure | C:\Users\admin\AppData\LocalLow\IGDump\sec\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 3235811341 Version: 1.0.4.8 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4740 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4708 -prefMapHandle 4728 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {17eb7c91-7b5a-4cf5-9f8a-01e6cc86a2b9} 968 "\\.\pipe\gecko-crash-server-pipe.968" 19bcac32310 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 3968 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2916 -childID 1 -isForBrowser -prefsHandle 2312 -prefMapHandle 2564 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1436 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {25702e6c-992e-4145-bd4d-e2df55f2a7cc} 968 "\\.\pipe\gecko-crash-server-pipe.968" 19bc749cf50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 4068 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4200 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2188 -parentBuildID 20240213221259 -prefsHandle 2180 -prefMapHandle 2176 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {44f5f626-5bf4-4a2b-b8f5-77acd995c7f7} 968 "\\.\pipe\gecko-crash-server-pipe.968" 19bb5880710 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
295 818
Read events
294 852
Write events
936
Delete events
30
Modification events
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Malwarebytes |
| Operation: | write | Name: | id |
Value: ced8f4bdab0e451983652875cde488c0 | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Malwarebytes |
| Operation: | write | Name: | id |
Value: ced8f4bdab0e451983652875cde488c0 | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\mbamtestkey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Malwarebytes |
| Operation: | delete value | Name: | IrisFirstRun |
Value: | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | UserName |
Value: admin | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | ProductCode |
Value: MBAM-C | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | ProductBuild |
Value: consumer | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | ProgramDirectory |
Value: C:\Program Files\Malwarebytes\Anti-Malware | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | LocalAppDataDir |
Value: C:\Users\admin\AppData\Local | |||
| (PID) Process: | (6808) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | Channel |
Value: release | |||
Executable files
1 278
Suspicious files
467
Text files
100
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\ctlrpkg.7z | — | |
MD5:— | SHA256:— | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\dbclspkg.7z | — | |
MD5:— | SHA256:— | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\dotnetpkg.7z | — | |
MD5:— | SHA256:— | |||
| 6808 | MBSetup.exe | C:\Program Files (x86)\mbamtestfile.dat | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\ctlrpkg\mbam.manifest.json | binary | |
MD5:9643D59C2098E597C1D028FB54A20D4D | SHA256:32935392D9D50B0E218FE934BD62D51E659DE97AF437588ED3A096A01BA0F062 | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\ctlrpkg\Malwarebytes.deps.json | binary | |
MD5:442C754A9CF00F1361BA18A4DDA228CE | SHA256:958ACB9D7E79B6DC2EFD1B9E0BBE53E700BDB1C8D6B998873FC341819CD7BCBB | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\ctlrpkg\mbam.firefox.manifest.json | binary | |
MD5:F83DF8976D2F549973B4741AABEC7DC8 | SHA256:81E215E014635B567D9D11CCCCAE20A0E62BB4D640B1CCE0B30ECE970212AF02 | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\servicepkg\mbamelam.cat | binary | |
MD5:BD4CEAE54AF081D6B1DD91FF584C5D61 | SHA256:C3C4967B05CD00C31CAFC39B57000EC2E82CCF2CA295C72365F5CF6E5D191034 | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\ctlrpkg\Malwarebytes_Assistant.deps.json | binary | |
MD5:7C7F655A6E87C1DF9C2B85BF309F0109 | SHA256:8D4E2F82DA101053ED4F5FF642F37970BC4E228FFB93959BD41EDCA808033018 | |||
| 664 | MBAMInstallerService.exe | C:\Windows\Temp\MBInstallTemp6efa4167209d11f089182420b137d17f\ctlrpkg\mbamelam.cat | binary | |
MD5:BD4CEAE54AF081D6B1DD91FF584C5D61 | SHA256:C3C4967B05CD00C31CAFC39B57000EC2E82CCF2CA295C72365F5CF6E5D191034 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
112
DNS requests
162
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
968 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
968 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
968 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
968 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
968 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6808 | MBSetup.exe | 54.148.100.197:443 | api2.amplitude.com | AMAZON-02 | US | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api2.amplitude.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
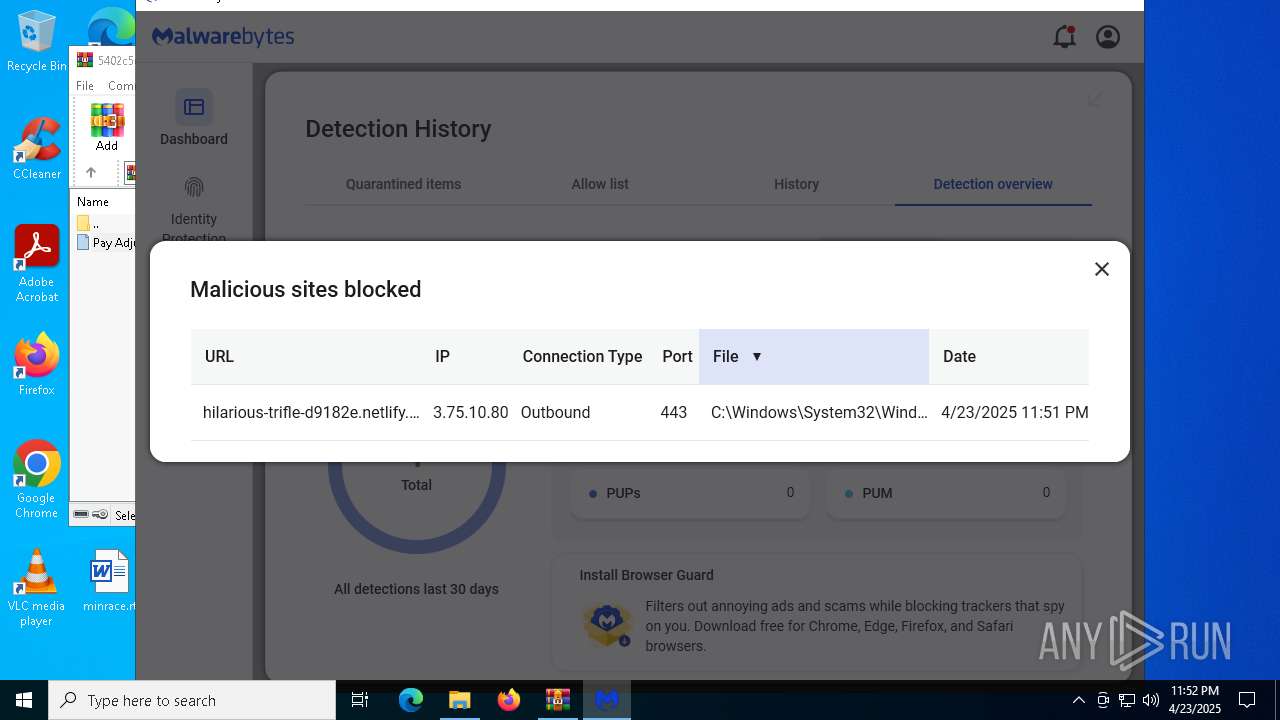
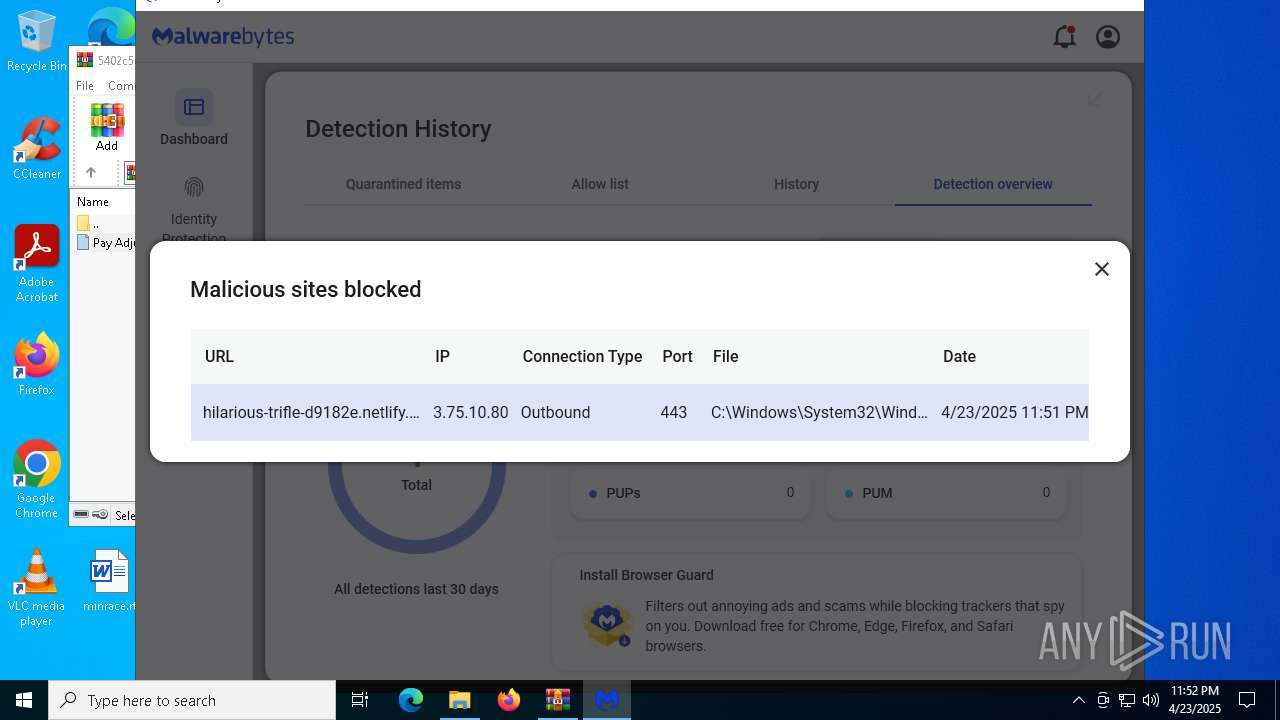
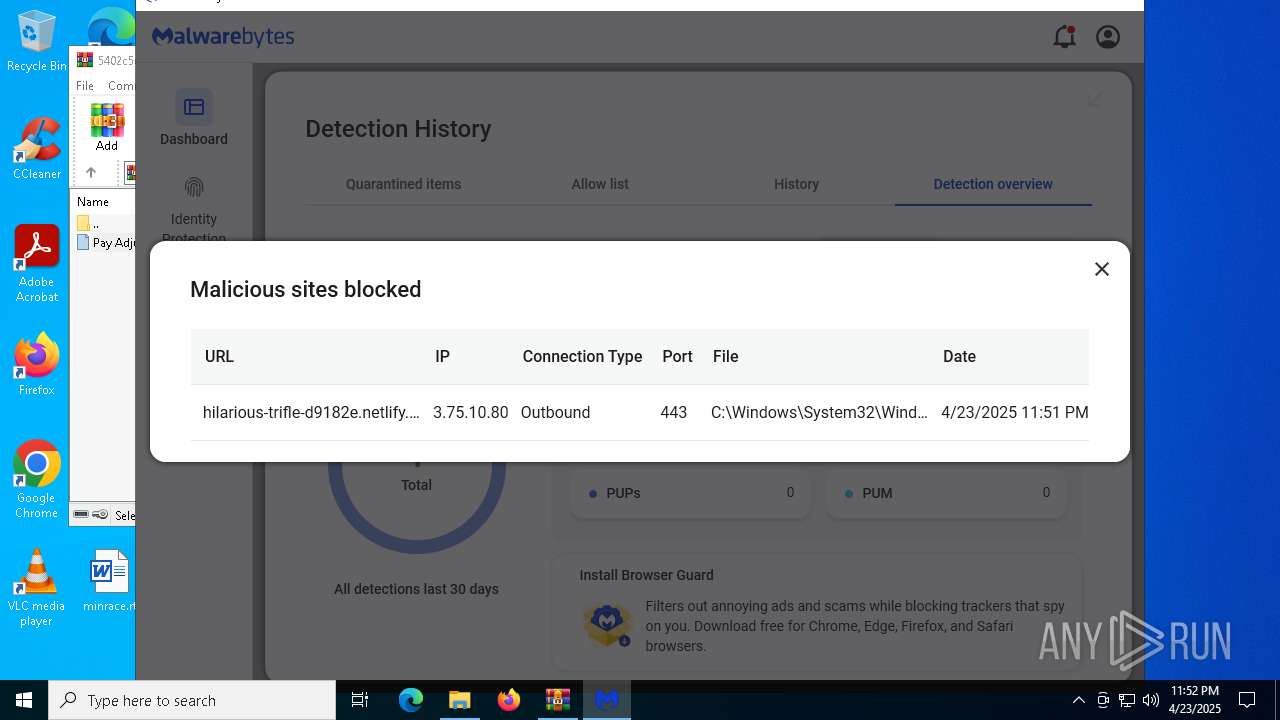
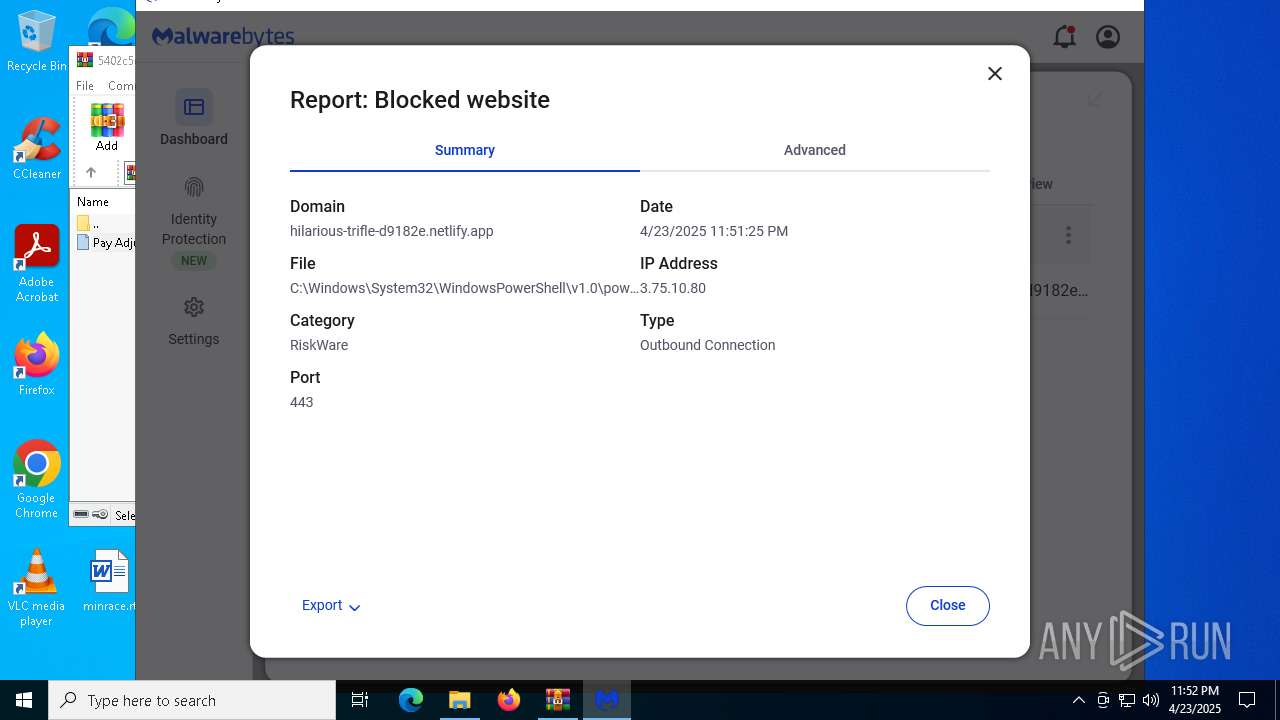
2196 | svchost.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted DNS Request - Possible Phishing Landing |
Process | Message |
|---|---|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|