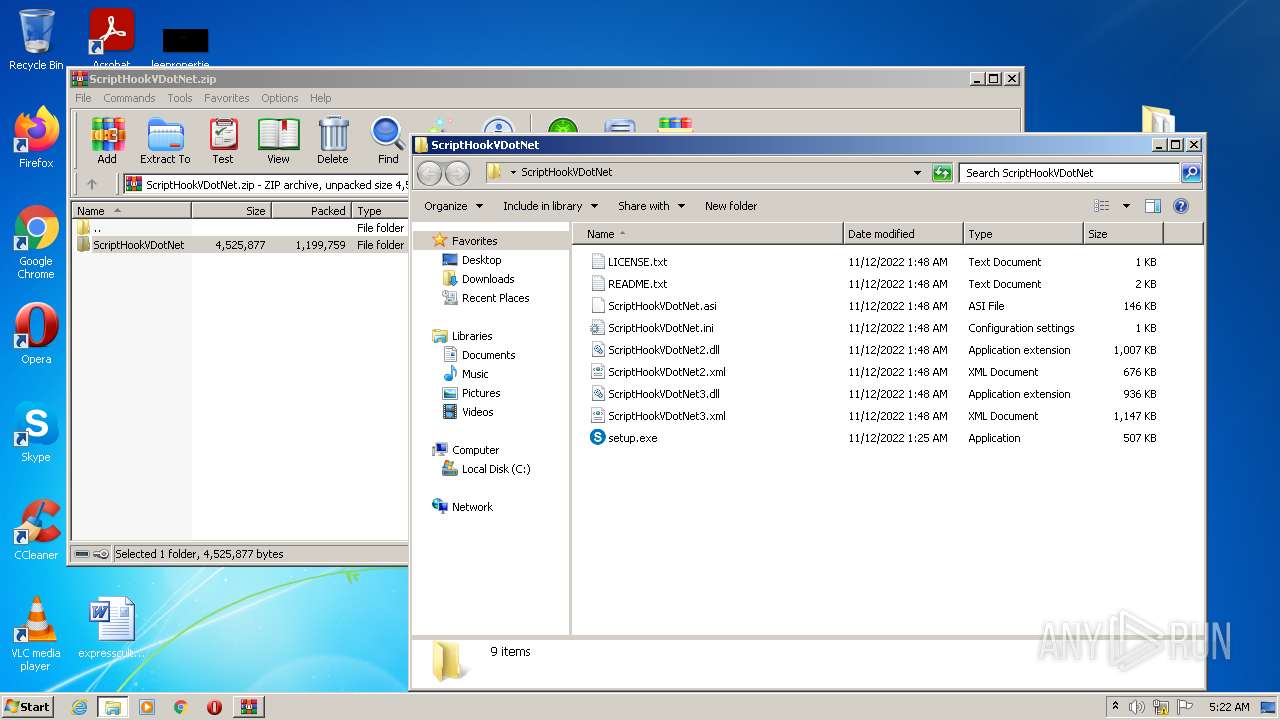
| download: | ScriptHookVDotNet.zip |
| Full analysis: | https://app.any.run/tasks/707e6bf5-e51c-4c69-82bf-c57306ed02e4 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | November 14, 2022, 05:22:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | A99F2AC164C6886C143A16CDB1C8612F |
| SHA1: | C1DF656E75E7BDF7C4815D06AEA9CFB1780B54F3 |
| SHA256: | 74855917D9CB77E2908F31D912DBBF3C9A436AFEAA299AB8E25919D1E23D2C56 |
| SSDEEP: | 24576:ZdD+rc3BCg0f4I1nmdeec0yfm9DfWEhRL2FpJiiRixof7:Z0ryBCg01XwQmZfRhRL2bJiiQSf7 |
MALICIOUS
Application was dropped or rewritten from another process
- setup.exe (PID: 2808)
- setup.exe (PID: 3276)
Changes the autorun value in the registry
- setup.exe (PID: 2808)
- setup.exe (PID: 3276)
Drops the executable file immediately after the start
- setup.exe (PID: 2808)
QUASAR detected by memory dumps
- setup.exe (PID: 3276)
SUSPICIOUS
Executable content was dropped or overwritten
- setup.exe (PID: 2808)
Starts itself from another location
- setup.exe (PID: 2808)
Connects to unusual port
- setup.exe (PID: 3276)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3160)
Reads the machine GUID from the registry
- setup.exe (PID: 2808)
- setup.exe (PID: 3276)
Reads Environment values
- setup.exe (PID: 2808)
- setup.exe (PID: 3276)
Reads the computer name
- setup.exe (PID: 2808)
- setup.exe (PID: 3276)
Process checks LSA protection
- setup.exe (PID: 2808)
- setup.exe (PID: 3276)
Checks supported languages
- setup.exe (PID: 3276)
- setup.exe (PID: 2808)
Creates files in the user directory
- setup.exe (PID: 2808)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3160)
Manual execution by user
- setup.exe (PID: 2808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(3276) setup.exe
Version1.4.0
C2 (2)scripthook.hopto.org:4782
Sub_DirScriptHookNet_TMP
Install_Namesetup.exe
Mutex8daacb9c-576e-4ccb-8514-db41acf5e90b
StartupSystem Fonctionnalities
TagOffice04
LogDirTemp_Keyb
SignatureI9pYfI0j7/aybXOR1JJAfqi+pfH8BD3Al81TPasDY+BB0WR3T5QgWk1GOA3VnICFucRDBQeMf5JRFL4vebbo4PB/aYsPZc2aQj19sfnEcpkQsMDWNWwt2BsWuHsJnC1vks4d10NcmmyKdjVZIw+7NJ89jHpQnnnzyMEJDYzwSyvxiW8X6OTKAa40MWT4tNSw6NHZso58eO31ZkPdaP0Gvy5I7seL6//CmmaYsuAYNZX3mF7pzuF21fcdbBaMCycaHxgJ9/mJZ9VHO89BK19fidbRfwwiucsm4v+lJhZPhen7...
CertificateMIIE9DCCAtygAwIBAgIQAKuZ/D7MTe9DlKX3X4TVoTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTExMDAxMTQzOFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAlZOnzynipri5hWiDchmfyXwrYe9TGGdnM+VZ7bXXItxyWVuUiLTJPcG9TpiXxyZ4HygUFW0P...
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2808 | "C:\Users\admin\Desktop\ScriptHookVDotNet\setup.exe" | C:\Users\admin\Desktop\ScriptHookVDotNet\setup.exe | Explorer.EXE | ||||||||||||
User: admin Company: Shader.me Integrity Level: MEDIUM Description: Community ScriptHookNet Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3160 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\ScriptHookVDotNet.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3276 | "C:\Users\admin\AppData\Roaming\ScriptHookNet_TMP\setup.exe" | C:\Users\admin\AppData\Roaming\ScriptHookNet_TMP\setup.exe | setup.exe | ||||||||||||
User: admin Company: Shader.me Integrity Level: MEDIUM Description: Community ScriptHookNet Exit code: 0 Version: 1.0.0.0 Modules
Quasar(PID) Process(3276) setup.exe Version1.4.0 C2 (2)scripthook.hopto.org:4782 Sub_DirScriptHookNet_TMP Install_Namesetup.exe Mutex8daacb9c-576e-4ccb-8514-db41acf5e90b StartupSystem Fonctionnalities TagOffice04 LogDirTemp_Keyb SignatureI9pYfI0j7/aybXOR1JJAfqi+pfH8BD3Al81TPasDY+BB0WR3T5QgWk1GOA3VnICFucRDBQeMf5JRFL4vebbo4PB/aYsPZc2aQj19sfnEcpkQsMDWNWwt2BsWuHsJnC1vks4d10NcmmyKdjVZIw+7NJ89jHpQnnnzyMEJDYzwSyvxiW8X6OTKAa40MWT4tNSw6NHZso58eO31ZkPdaP0Gvy5I7seL6//CmmaYsuAYNZX3mF7pzuF21fcdbBaMCycaHxgJ9/mJZ9VHO89BK19fidbRfwwiucsm4v+lJhZPhen7... CertificateMIIE9DCCAtygAwIBAgIQAKuZ/D7MTe9DlKX3X4TVoTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTExMDAxMTQzOFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAlZOnzynipri5hWiDchmfyXwrYe9TGGdnM+VZ7bXXItxyWVuUiLTJPcG9TpiXxyZ4HygUFW0P... | |||||||||||||||
Total events
1 346
Read events
1 299
Write events
47
Delete events
0
Modification events
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ScriptHookVDotNet.zip | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\ScriptHookVDotNet2.dll | executable | |
MD5:— | SHA256:— | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\ScriptHookVDotNet.asi | executable | |
MD5:— | SHA256:— | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\LICENSE.txt | text | |
MD5:9762B15C21A8BAAF48CE0DE93FB98634 | SHA256:E5684AAF6331FD05298B8980A6414D1BDC7FBF75278DA7CF3E81C91BE5168B72 | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\ScriptHookVDotNet.ini | text | |
MD5:452AA296F999DC789BE6E935FF190FB7 | SHA256:34AB7E962A9F14AF2589EFF94334D7AA462DAE00CB8023F0EBF7AB773E7A498C | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\ScriptHookVDotNet3.dll | executable | |
MD5:— | SHA256:— | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\ScriptHookVDotNet3.xml | xml | |
MD5:— | SHA256:— | |||
| 2808 | setup.exe | C:\Users\admin\AppData\Roaming\ScriptHookNet_TMP\setup.exe | executable | |
MD5:— | SHA256:— | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\ScriptHookVDotNet2.xml | xml | |
MD5:6A97E64AF486A0C4B37FDD6BC8EE4091 | SHA256:F2A60679F0F09FD0BE23E189EB7D01091B3B586721669869C4917AAF50AB376D | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\README.txt | text | |
MD5:7ADDD208CA47C98865757CE0B4DEE29D | SHA256:CC4E3DCBBEC47508D01E317E03DC002B791E4C07BD77555D9F8A7049A565336D | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.49638\ScriptHookVDotNet\setup.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
31
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3276 | setup.exe | 95.179.230.24:4782 | scripthook.hopto.org | AS-CHOOPA | GB | unknown |
— | — | 95.179.230.24:4782 | scripthook.hopto.org | AS-CHOOPA | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
scripthook.hopto.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.hopto .org |