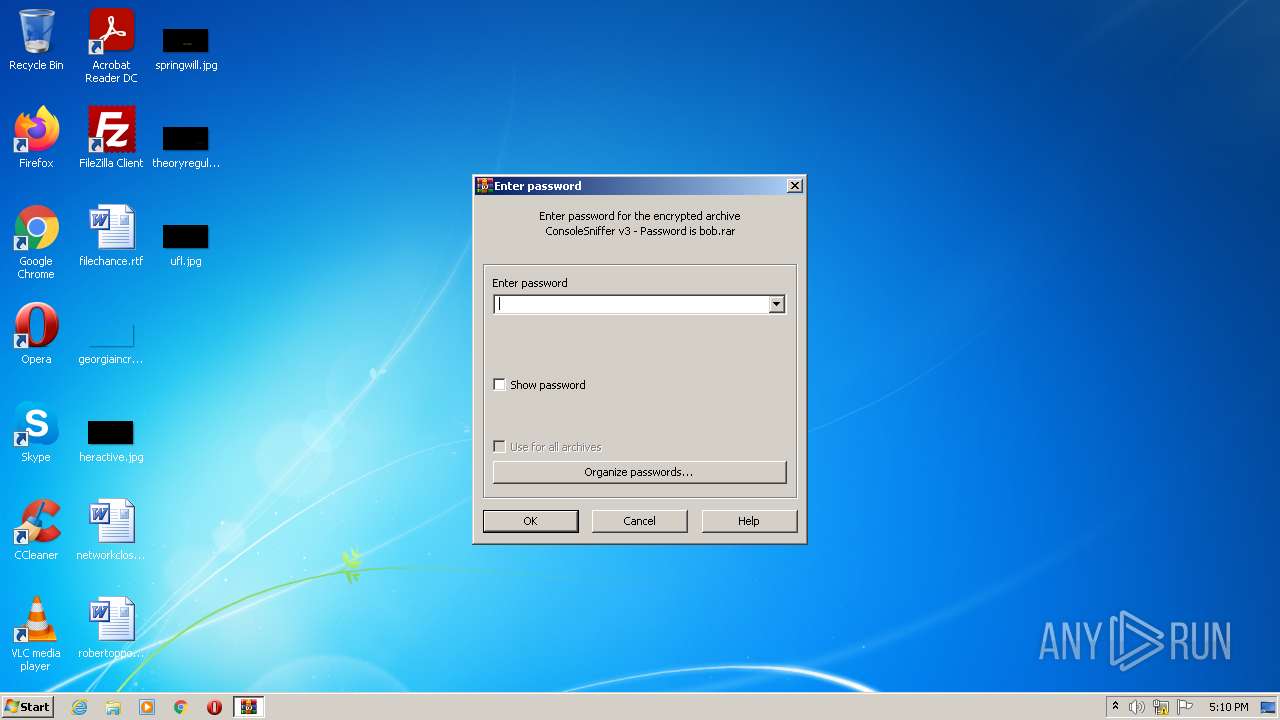
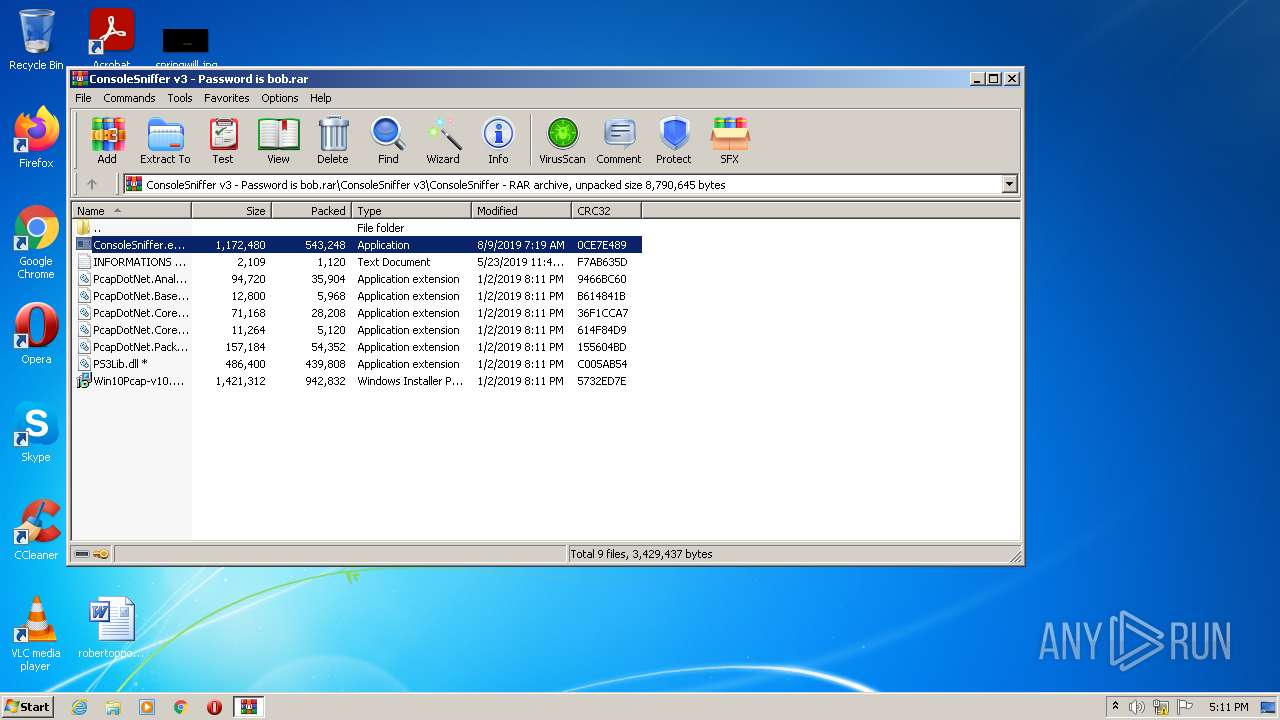
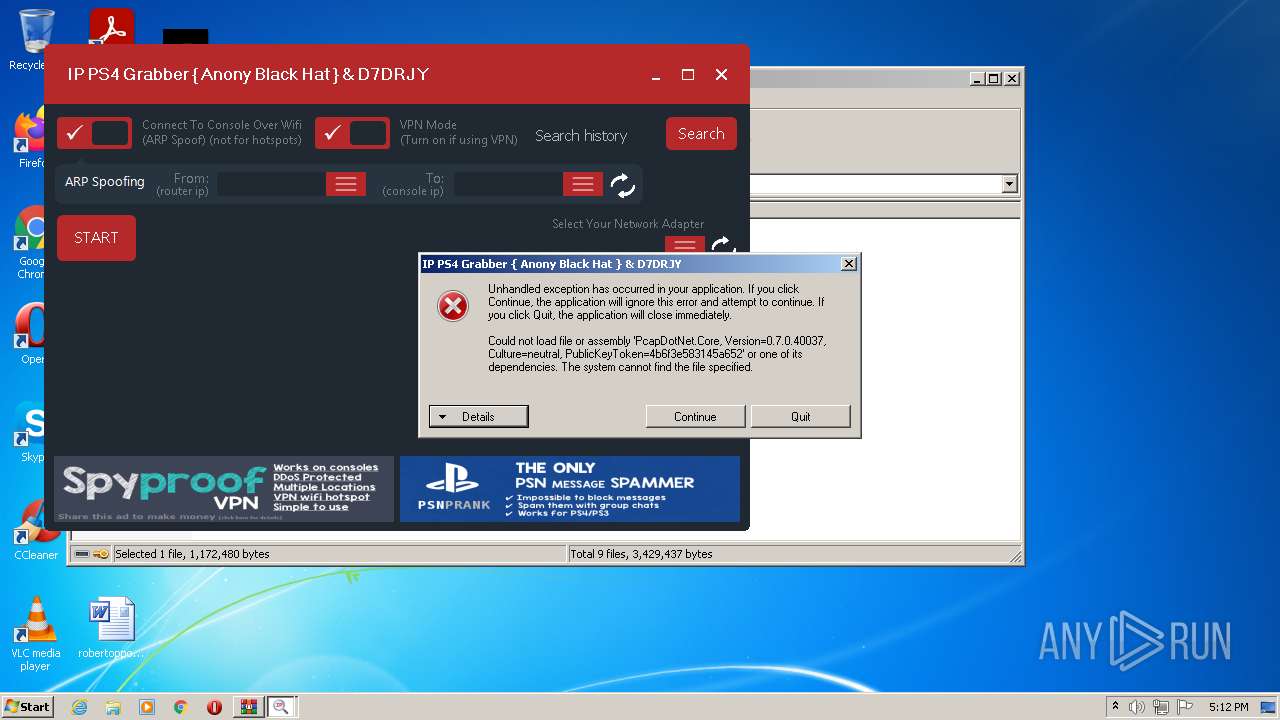
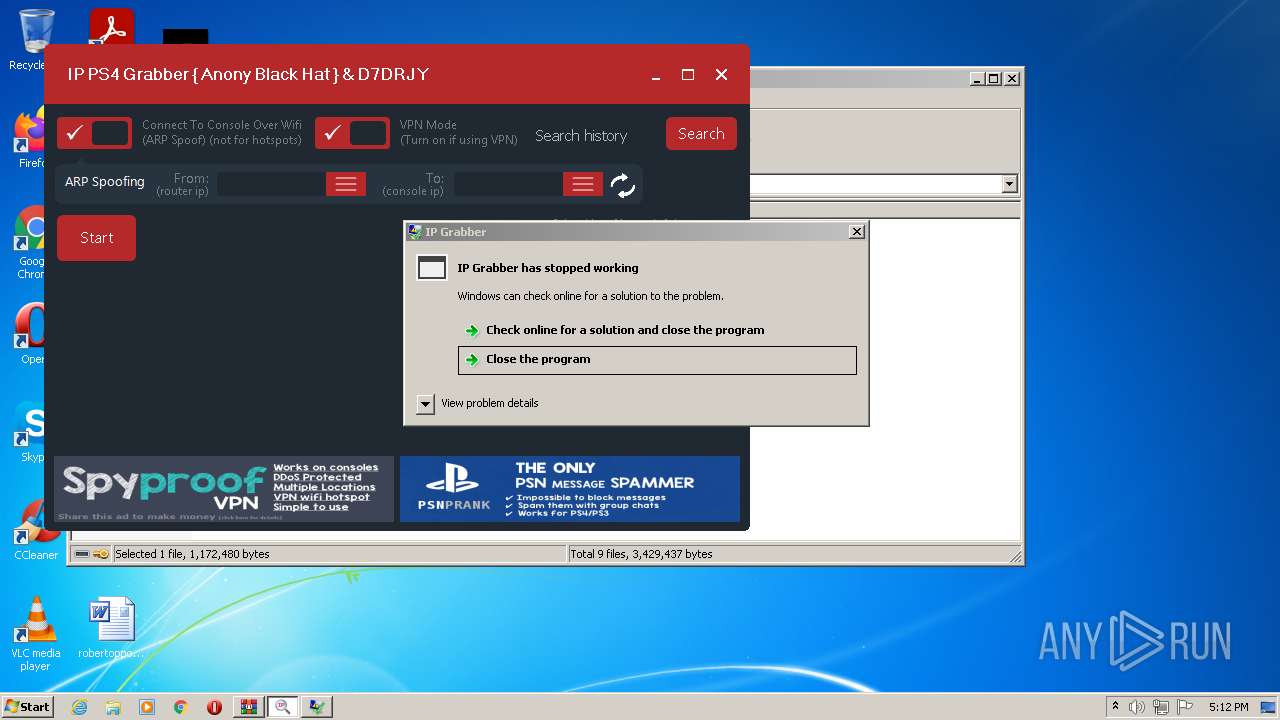
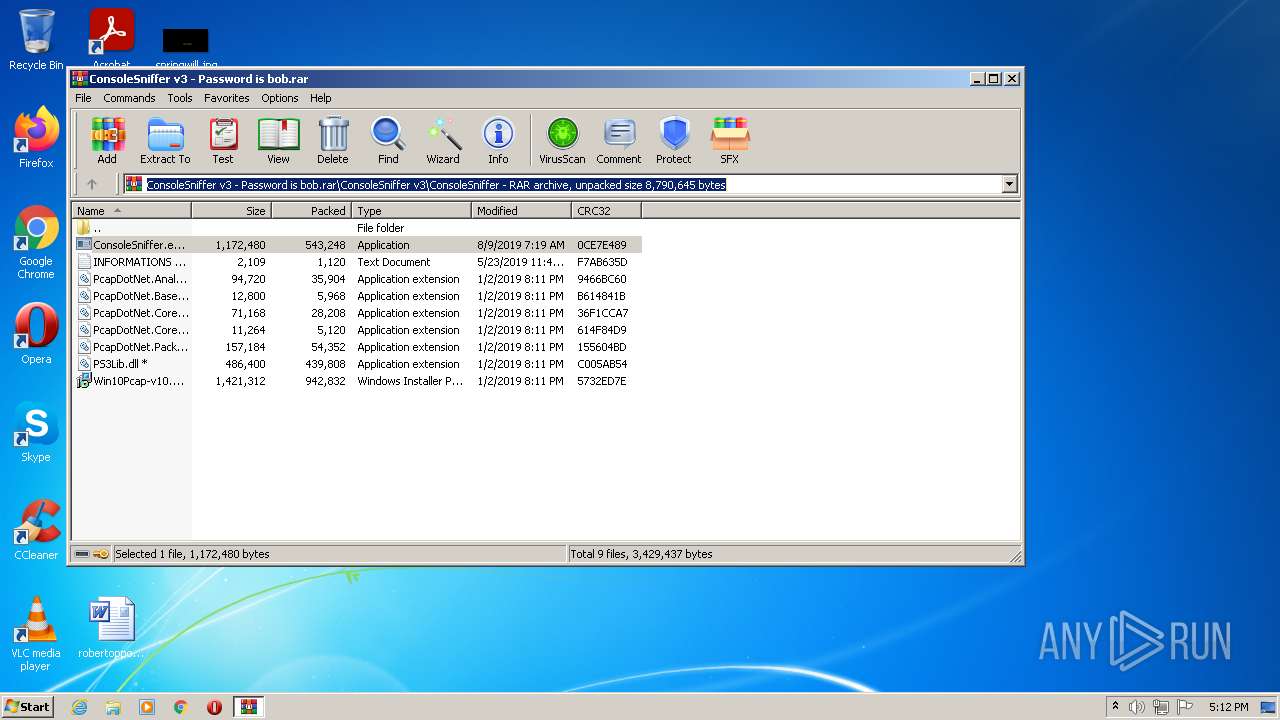
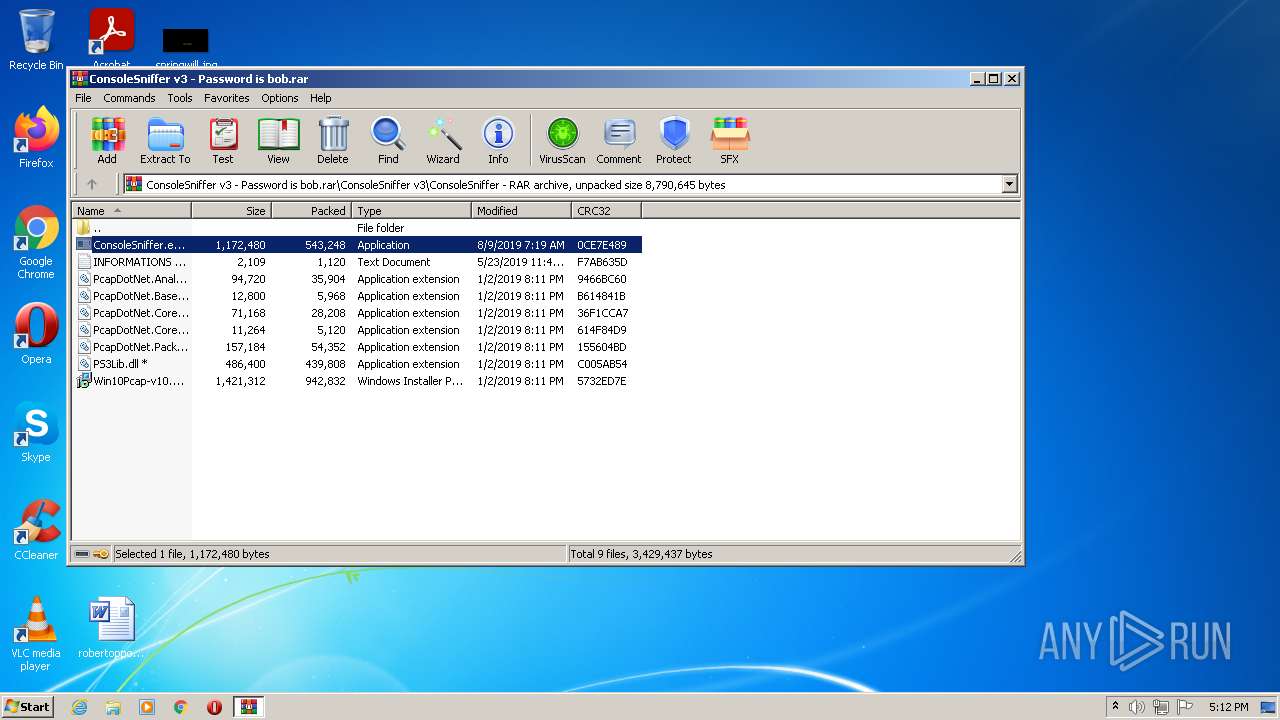
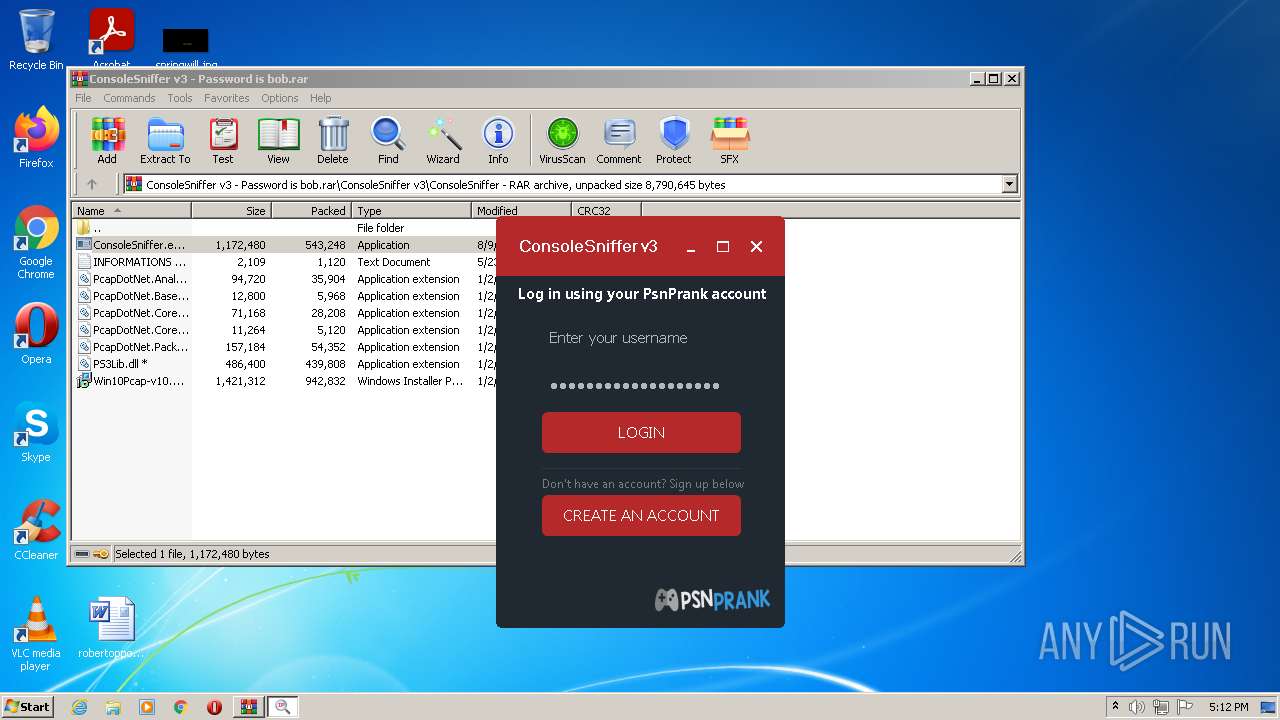
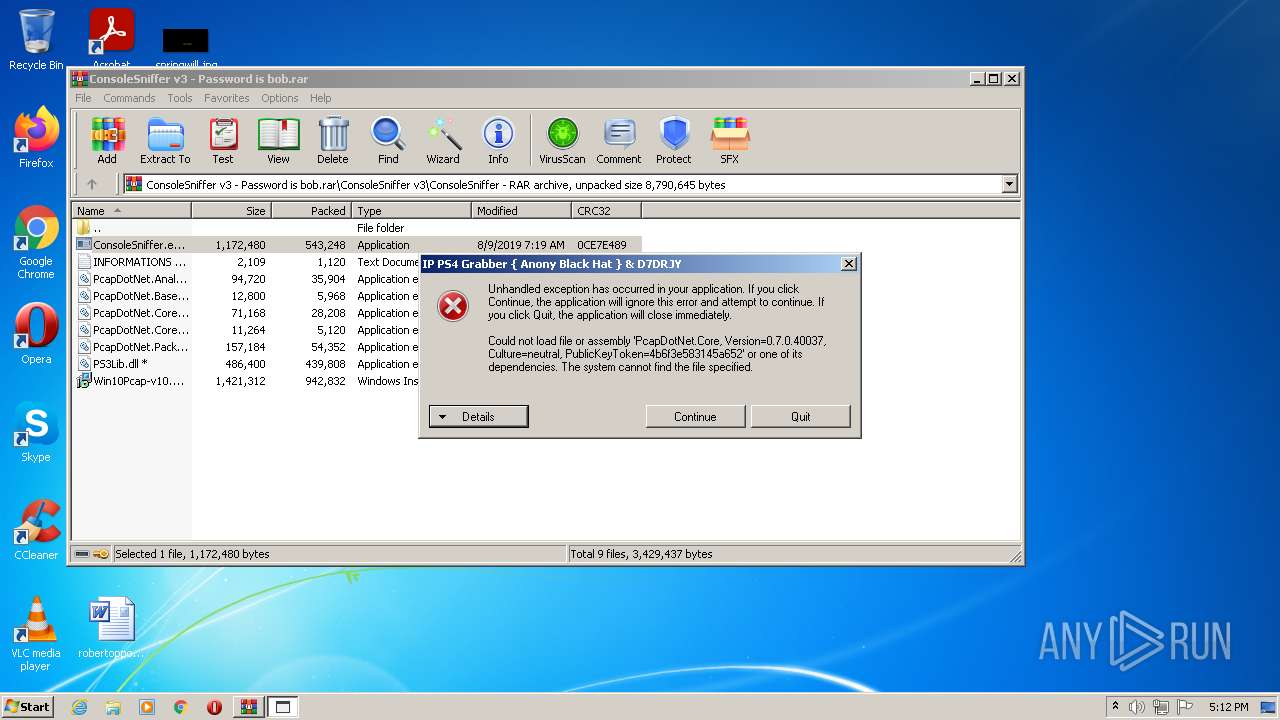
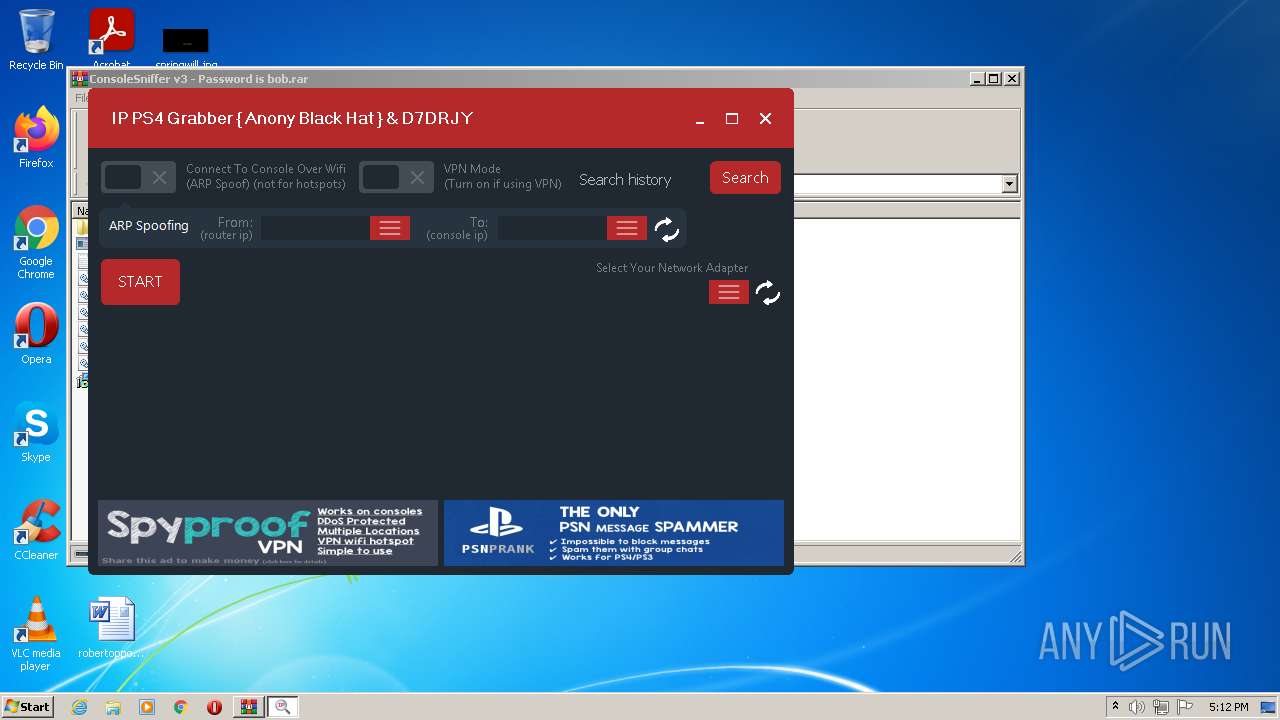
| File name: | ConsoleSniffer v3 - Password is bob |
| Full analysis: | https://app.any.run/tasks/e4483d43-e35d-4f81-bfb3-cefa687b4317 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | May 20, 2022, 16:10:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FEC028CA2FB7F3342B756F26FA329D92 |
| SHA1: | C4B83D141DBE3116CD2B1CE71F2C1A45CBBF12BD |
| SHA256: | 746BB20E63673B15720E6430186EA787422E4DE6E3A7FBA1D9B8799A30970754 |
| SSDEEP: | 196608:yts0F/7CrHvJW+0sdG1pV4TA7wkdtnv3baSqPoI6KJ:EZFCLy7WTA7wOcSqQI6KJ |
MALICIOUS
Drops executable file immediately after starts
- ConsoleSniffer.exe (PID: 1780)
- WinRAR.exe (PID: 2992)
- boom.exe (PID: 1632)
- test.exe (PID: 908)
- WindowsStartup.exe (PID: 3000)
Application was dropped or rewritten from another process
- ConsoleSniffer.exe (PID: 1780)
- boom.exe (PID: 1632)
- test.exe (PID: 908)
- ConsoleSniffer v3.exe (PID: 2344)
- ConsoleSniffer v3.exe (PID: 3040)
- WindowsStartup.exe (PID: 3000)
- WindowsRun.exe (PID: 2036)
- ConsoleSniffer.exe (PID: 3560)
- boom.exe (PID: 2076)
- test.exe (PID: 1556)
- ConsoleSniffer v3.exe (PID: 2228)
- ConsoleSniffer v3.exe (PID: 2852)
- WindowsStartup.exe (PID: 3252)
Drops/Copies Quasar RAT executable
- boom.exe (PID: 1632)
- test.exe (PID: 908)
- WindowsStartup.exe (PID: 3000)
Writes to the hosts file
- ConsoleSniffer v3.exe (PID: 3040)
Changes the autorun value in the registry
- WindowsStartup.exe (PID: 3000)
- WindowsRun.exe (PID: 2036)
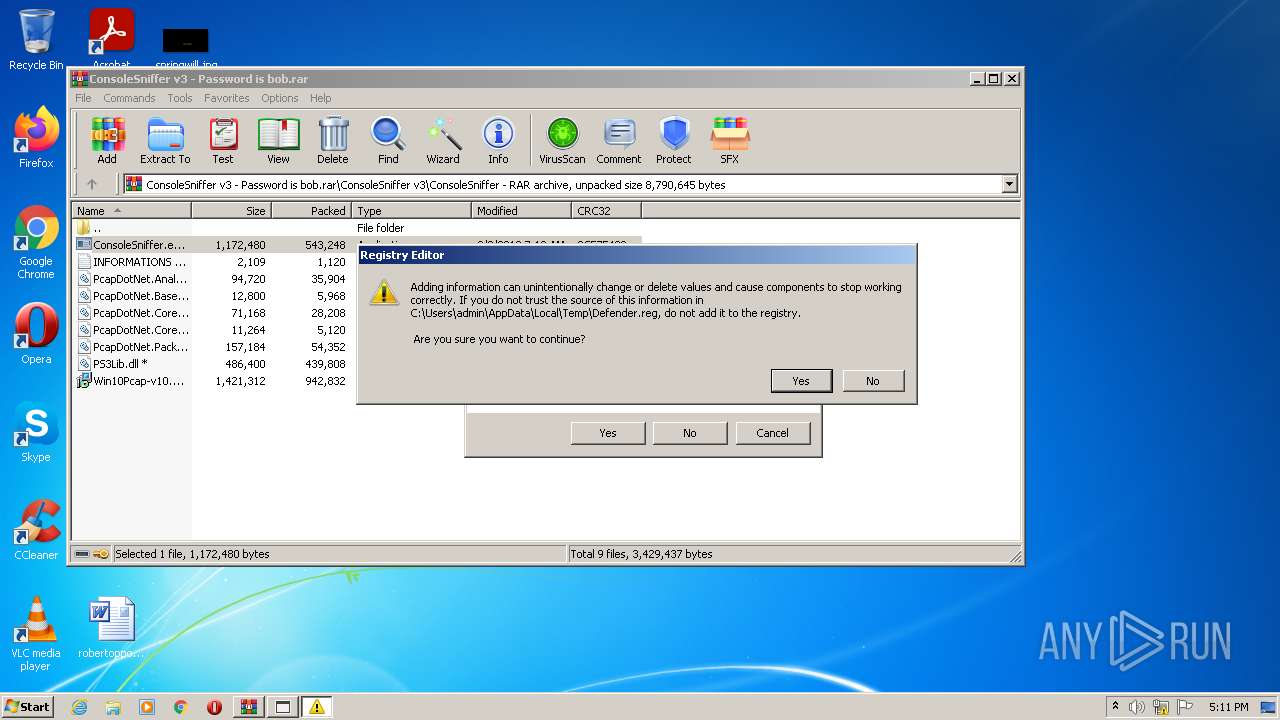
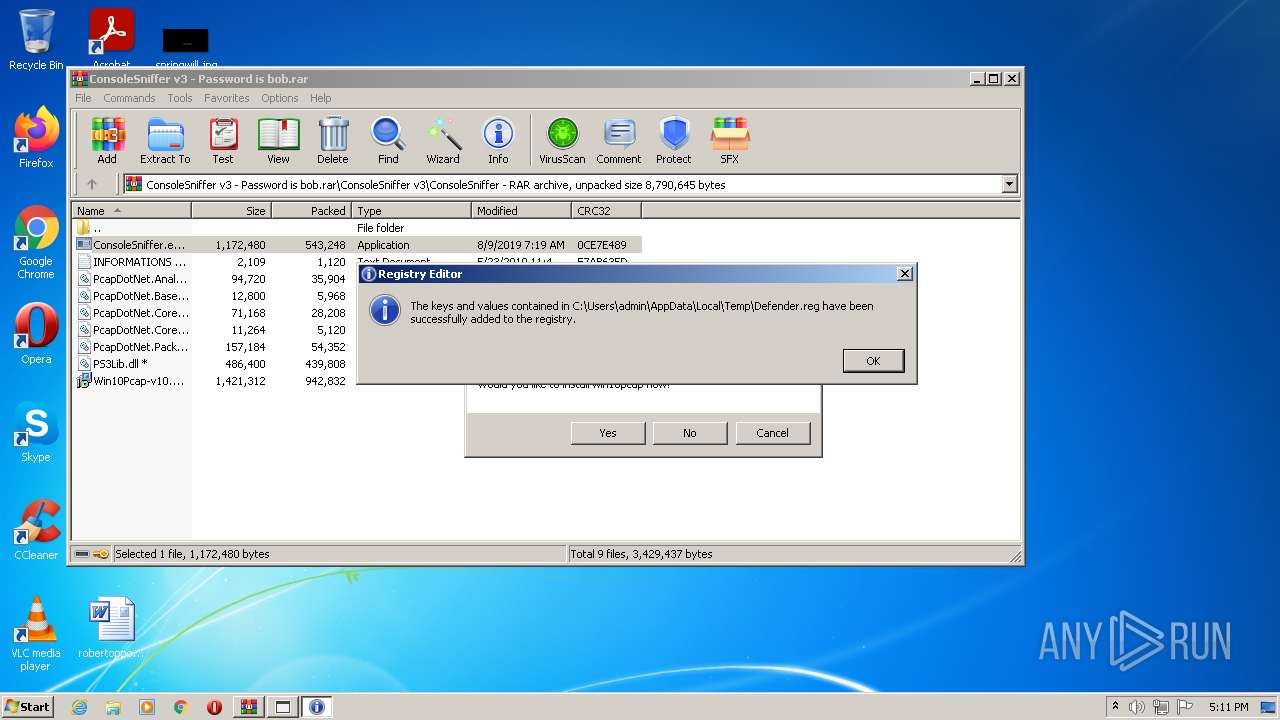
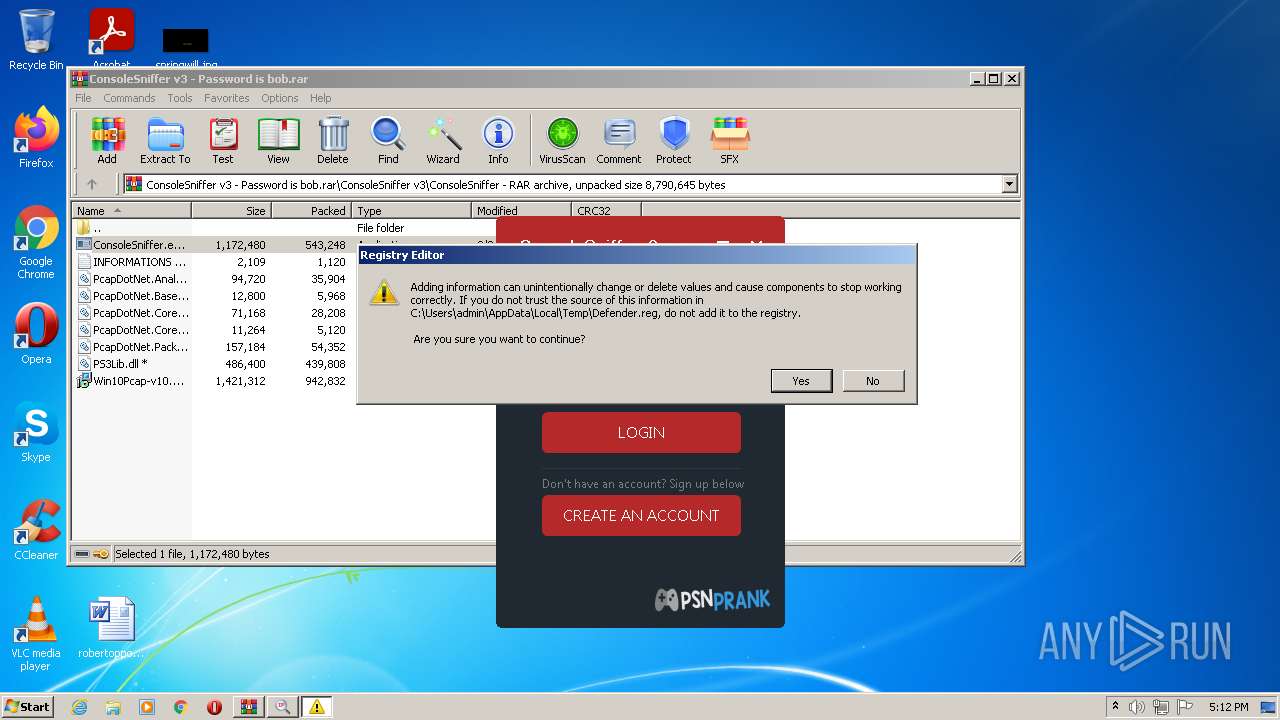
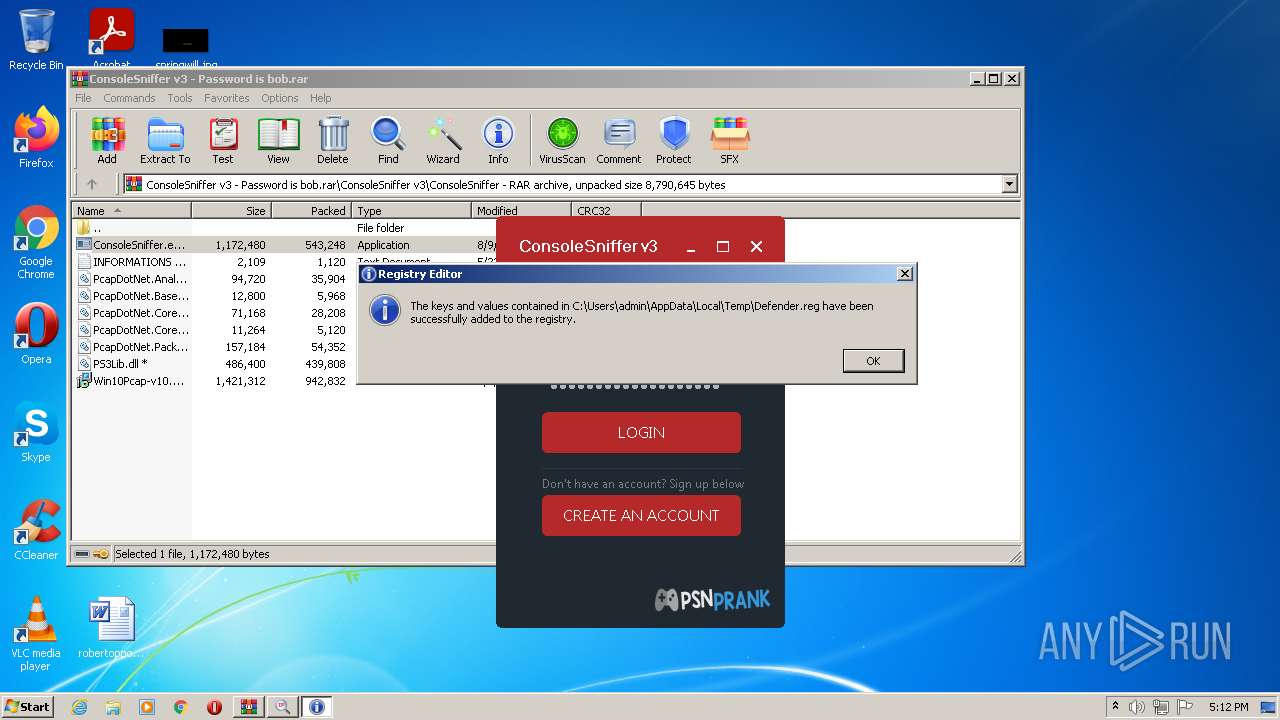
Disables Windows Defender
- regedit.exe (PID: 3832)
- regedit.exe (PID: 3740)
QUASAR detected by memory dumps
- WindowsRun.exe (PID: 2036)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2992)
- ConsoleSniffer.exe (PID: 1780)
- boom.exe (PID: 1632)
- test.exe (PID: 908)
- WindowsStartup.exe (PID: 3000)
Checks supported languages
- WinRAR.exe (PID: 2992)
- ConsoleSniffer.exe (PID: 1780)
- boom.exe (PID: 1632)
- test.exe (PID: 908)
- ConsoleSniffer v3.exe (PID: 3040)
- WindowsStartup.exe (PID: 3000)
- WindowsRun.exe (PID: 2036)
- ConsoleSniffer.exe (PID: 3560)
- boom.exe (PID: 2076)
- ConsoleSniffer v3.exe (PID: 2852)
- WindowsStartup.exe (PID: 3252)
- test.exe (PID: 1556)
Reads the computer name
- WinRAR.exe (PID: 2992)
- ConsoleSniffer.exe (PID: 1780)
- boom.exe (PID: 1632)
- test.exe (PID: 908)
- ConsoleSniffer v3.exe (PID: 3040)
- WindowsStartup.exe (PID: 3000)
- WindowsRun.exe (PID: 2036)
- ConsoleSniffer.exe (PID: 3560)
- boom.exe (PID: 2076)
- WindowsStartup.exe (PID: 3252)
- ConsoleSniffer v3.exe (PID: 2852)
- test.exe (PID: 1556)
Drops a file with a compile date too recent
- ConsoleSniffer.exe (PID: 1780)
- WinRAR.exe (PID: 2992)
- boom.exe (PID: 1632)
- test.exe (PID: 908)
- WindowsStartup.exe (PID: 3000)
Reads Environment values
- WindowsStartup.exe (PID: 3000)
- WindowsRun.exe (PID: 2036)
Creates files in the user directory
- WindowsStartup.exe (PID: 3000)
Checks for external IP
- WindowsStartup.exe (PID: 3000)
- WindowsRun.exe (PID: 2036)
Starts itself from another location
- WindowsStartup.exe (PID: 3000)
INFO
Reads the hosts file
- ConsoleSniffer v3.exe (PID: 3040)
- ConsoleSniffer v3.exe (PID: 2852)
Checks supported languages
- regedit.exe (PID: 3832)
- regedit.exe (PID: 3740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(2036) WindowsRun.exe
Version1.3.0.0
C2 (2)185.217.1.170:56098
Sub_DirWindowsRep
Install_NameWindowsRun.exe
MutexQSR_MUTEX_mXJYTiCQWK23RFk8eh
StartupWindowsRuntiime
TagTarget
LogDirLogs
Signature
Certificate
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
61
Monitored processes
18
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 908 | "C:\Users\admin\AppData\Local\Temp\test.exe" | C:\Users\admin\AppData\Local\Temp\test.exe | boom.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\AppData\Local\Temp\test.exe" | C:\Users\admin\AppData\Local\Temp\test.exe | — | boom.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\AppData\Local\Temp\boom.exe" | C:\Users\admin\AppData\Local\Temp\boom.exe | ConsoleSniffer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
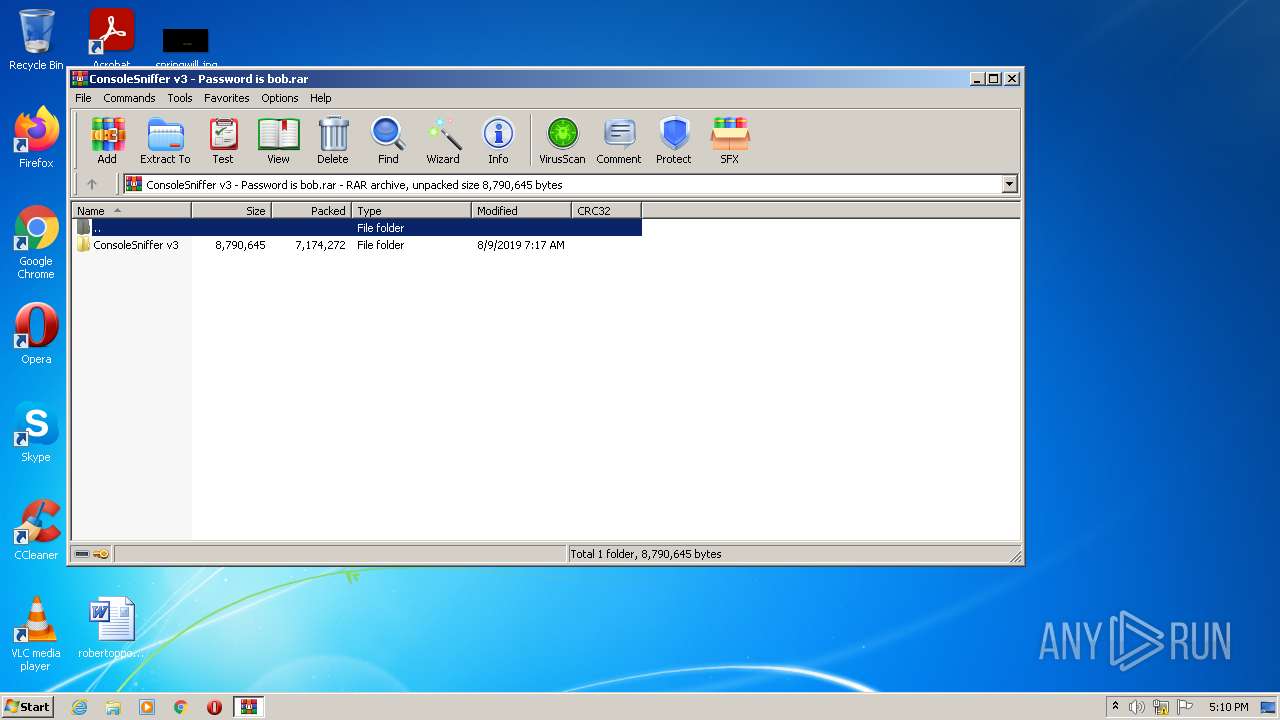
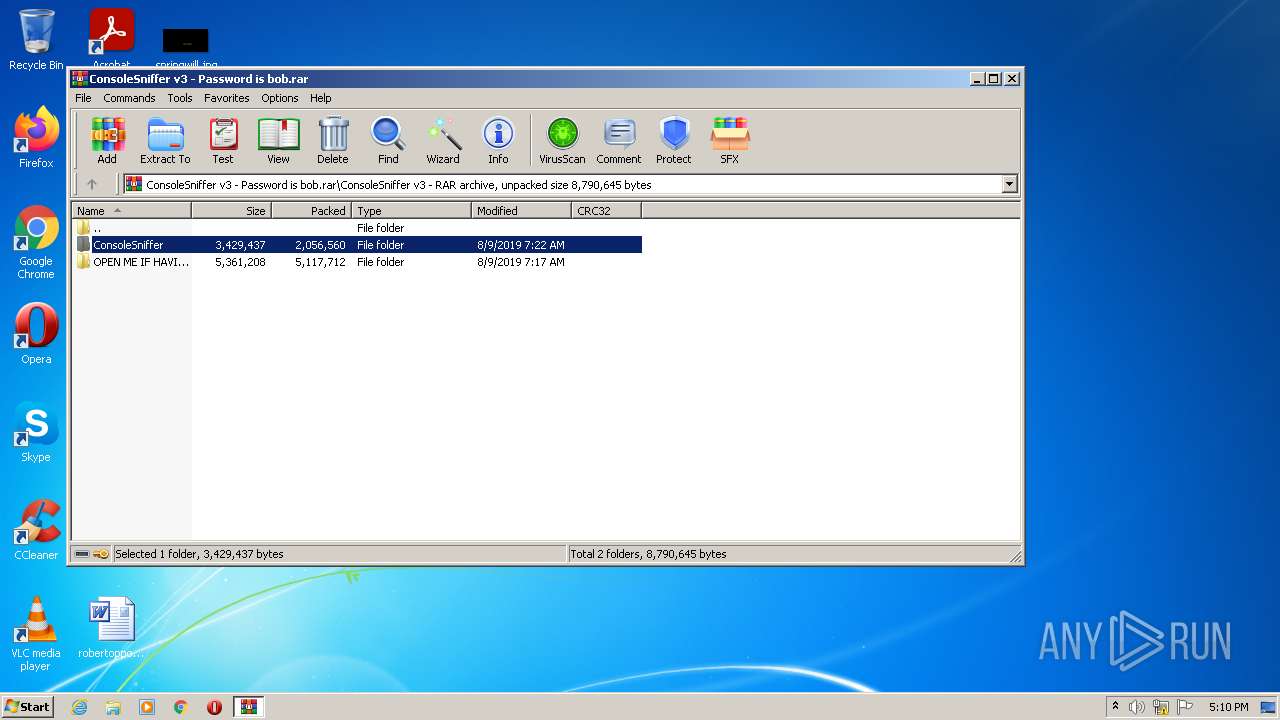
| 1780 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2992.23360\ConsoleSniffer v3\ConsoleSniffer\ConsoleSniffer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2992.23360\ConsoleSniffer v3\ConsoleSniffer\ConsoleSniffer.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\AppData\Roaming\WindowsRep\WindowsRun.exe" | C:\Users\admin\AppData\Roaming\WindowsRep\WindowsRun.exe | WindowsStartup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
Quasar(PID) Process(2036) WindowsRun.exe Version1.3.0.0 C2 (2)185.217.1.170:56098 Sub_DirWindowsRep Install_NameWindowsRun.exe MutexQSR_MUTEX_mXJYTiCQWK23RFk8eh StartupWindowsRuntiime TagTarget LogDirLogs Signature Certificate | |||||||||||||||
| 2076 | "C:\Users\admin\AppData\Local\Temp\boom.exe" | C:\Users\admin\AppData\Local\Temp\boom.exe | — | ConsoleSniffer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
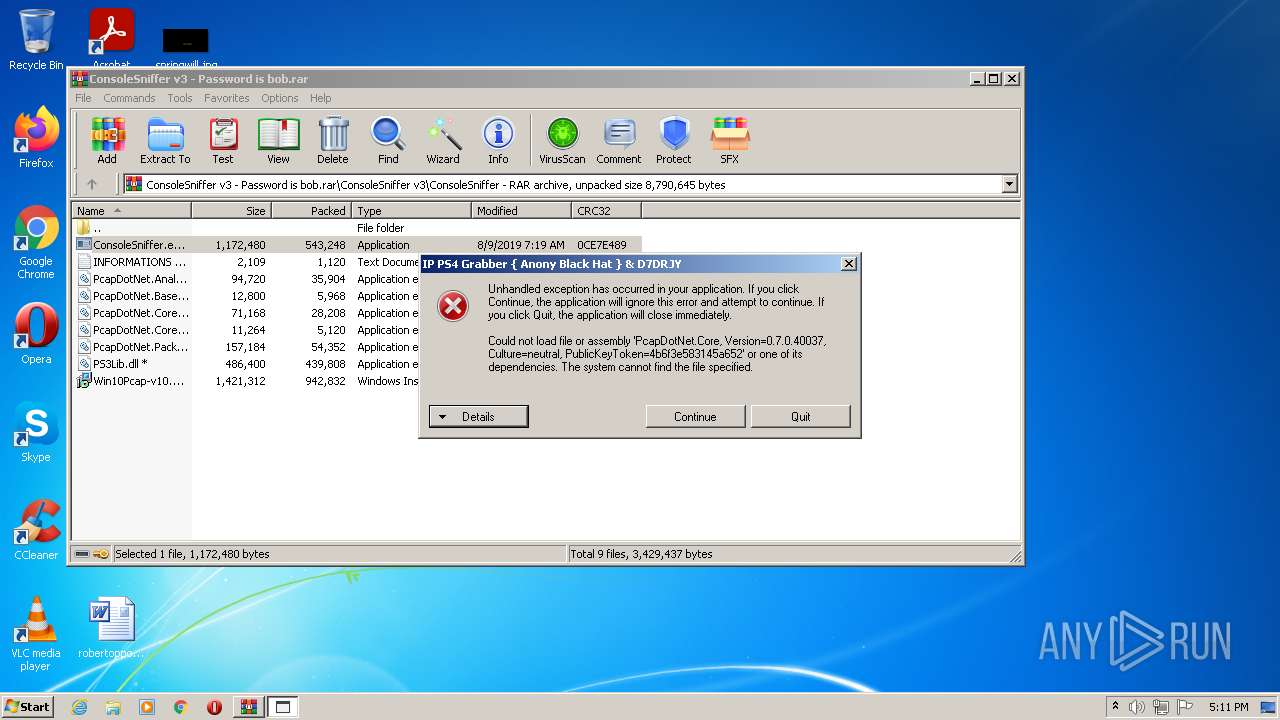
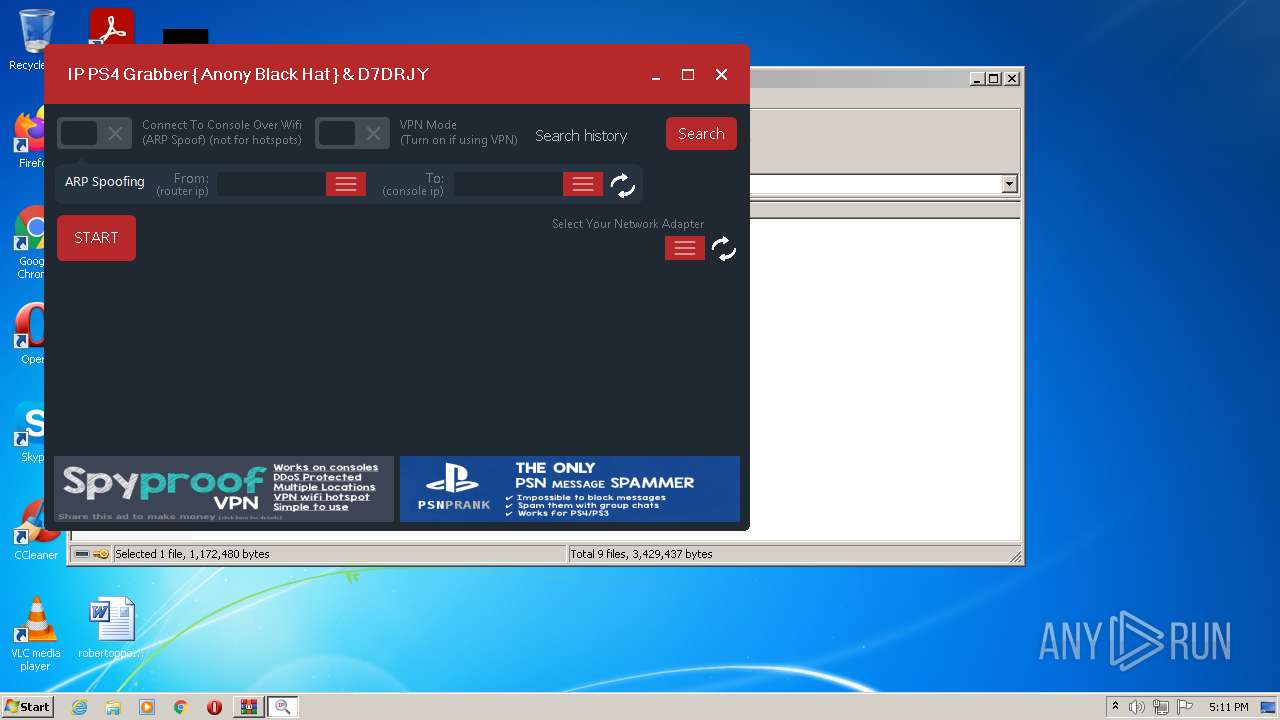
| 2228 | "C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe" | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: IP Grabber Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2344 | "C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe" | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: IP Grabber Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe" | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe | test.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: IP Grabber Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2992 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3 - Password is bob.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 340
Read events
7 192
Write events
148
Delete events
0
Modification events
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3 - Password is bob.rar | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
27
Suspicious files
0
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2992.23360\ConsoleSniffer v3\ConsoleSniffer\ConsoleSniffer.exe | executable | |
MD5:DF5A226B6C70691C85CBF776A17FD221 | SHA256:7E5E87FAF066201221548D5A8912582D7CDFF43DAC06331B68AA81A072F8BD21 | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2992.23360\ConsoleSniffer v3\ConsoleSniffer\INFORMATIONS by lB_U_Z_Z_A_R_Dl.txt | text | |
MD5:4F28D7FDB3DFA2A177C76389A4DD1CC3 | SHA256:84C7DAA41D0B65F1D0AE6AD2813F1E7D6FD3565C78E9CBFA2D9C59100181045A | |||
| 1632 | boom.exe | C:\Users\admin\AppData\Local\Temp\test.exe | executable | |
MD5:— | SHA256:— | |||
| 1780 | ConsoleSniffer.exe | C:\Users\admin\AppData\Local\Temp\boom.exe | executable | |
MD5:— | SHA256:— | |||
| 908 | test.exe | C:\Users\admin\AppData\Local\Temp\ConsoleSniffer v3.exe | executable | |
MD5:— | SHA256:— | |||
| 3000 | WindowsStartup.exe | C:\Users\admin\AppData\Roaming\WindowsRep\WindowsRun.exe | executable | |
MD5:— | SHA256:— | |||
| 908 | test.exe | C:\Users\admin\AppData\Local\Temp\WindowsStartup.exe | executable | |
MD5:— | SHA256:— | |||
| 908 | test.exe | C:\Users\admin\AppData\Local\Temp\Defender.reg | text | |
MD5:— | SHA256:— | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2992.23360\ConsoleSniffer v3\ConsoleSniffer\PcapDotNet.Core.Extensions.dll | executable | |
MD5:BD02851517BA8A2252AE5F6588E8886E | SHA256:925B370A65D5135D1425027E5087BE62D098D822B9F2CECD840CD7EFA5397380 | |||
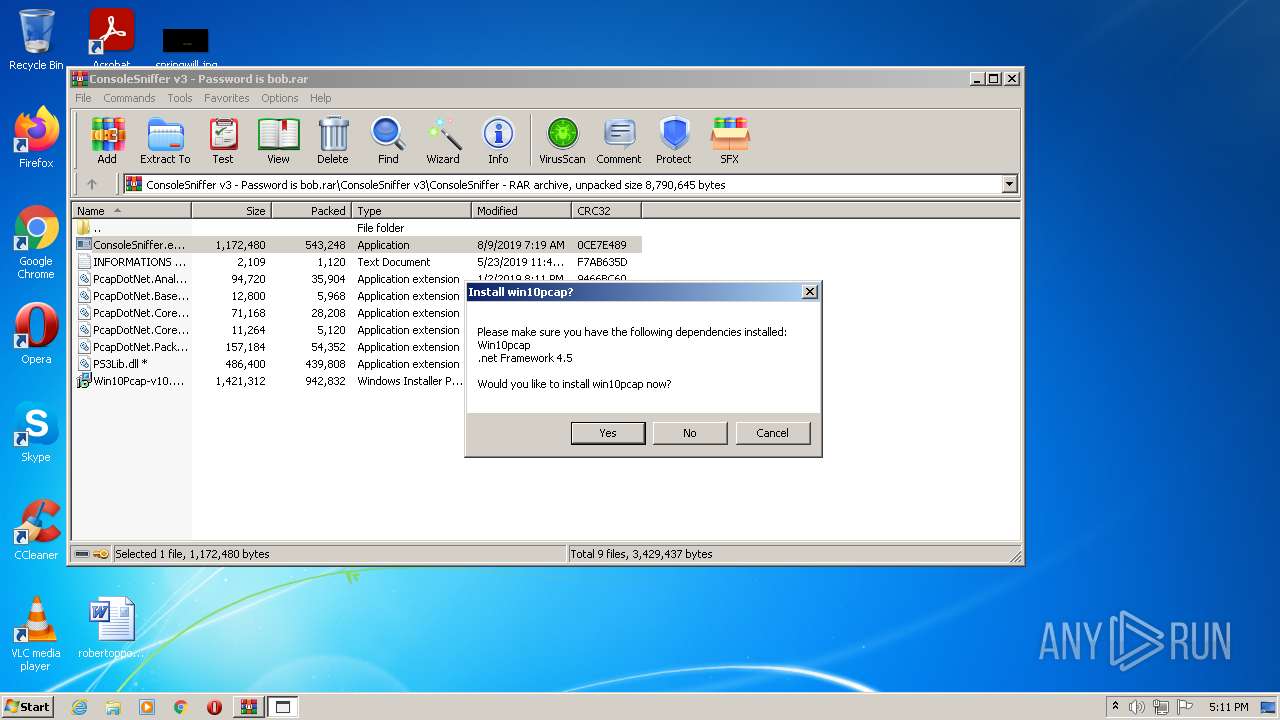
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2992.23360\ConsoleSniffer v3\OPEN ME IF HAVING ERROR\ndp48-web.exe | executable | |
MD5:86482F2F623A52B8344B00968ADC7B43 | SHA256:2C7530EDBF06B08A0B9F4227C24EC37D95F3998EE7E6933AE22A9943D0ADFA57 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
207
DNS requests
1
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2036 | WindowsRun.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 286 b | malicious |
3000 | WindowsStartup.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 286 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3000 | WindowsStartup.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2036 | WindowsRun.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2036 | WindowsRun.exe | 185.217.1.170:56098 | — | Icme Limited | SE | malicious |
— | — | 185.217.1.170:56098 | — | Icme Limited | SE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3000 | WindowsStartup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3000 | WindowsStartup.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2036 | WindowsRun.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2036 | WindowsRun.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2 ETPRO signatures available at the full report