| File name: | Venom RAT + HVNC + Stealer + Grabber.exe |
| Full analysis: | https://app.any.run/tasks/6eac00aa-f3e5-41e5-b46a-0f01eb892934 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 21, 2025, 23:08:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 3B3A304C6FC7A3A1D9390D7CBFF56634 |
| SHA1: | E8BD5244E6362968F5017680DA33F1E90AE63DD7 |
| SHA256: | 7331368C01B2A16BDA0F013F376A039E6AEB4CB2DD8B0C2AFC7CA208FB544C58 |
| SSDEEP: | 196608:Nja6chUZX81lbFklbYJygrP7aIBhLkNPFCZZwiJl1NLIsPA8fxvuIMzd/95UhS1G:qT+P+Zw6NLIsFfskh1BmXG04N |
MALICIOUS
ASYNCRAT has been detected (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 6572)
SUSPICIOUS
Possible usage of Discord/Telegram API has been detected (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 6572)
Executes application which crashes
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 6572)
INFO
Checks proxy server information
- WerFault.exe (PID: 6752)
Checks supported languages
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 6572)
Reads the computer name
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 6572)
Reads the software policy settings
- WerFault.exe (PID: 6752)
Manual execution by a user
- mspaint.exe (PID: 5036)
Creates files or folders in the user directory
- WerFault.exe (PID: 6752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6572) Venom RAT + HVNC + Stealer + Grabber.exe
Telegram-Tokens (1)5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Telegram-Info-Links
5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Get info about bothttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getMe
Get incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getUpdates
Get webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Discord-Info-Links
1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Get Webhook Infohttps://discord.com/api/webhooks/1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (42.9) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.3) |
| .exe | | | Win64 Executable (generic) (16.1) |
| .scr | | | Windows screen saver (7.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2068:12:31 07:38:15+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 14857728 |
| InitializedDataSize: | 10240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe2d4ae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.1.0 |
| ProductVersionNumber: | 6.0.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | VenomRAT |
| FileVersion: | 6.0.1 |
| InternalName: | Venom RAT + HVNC + Stealer + Grabber.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | Venom RAT + HVNC + Stealer + Grabber.exe |
| ProductName: | - |
| ProductVersion: | 6.0.1 |
| AssemblyVersion: | 6.0.1.0 |
Total processes
128
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 876 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
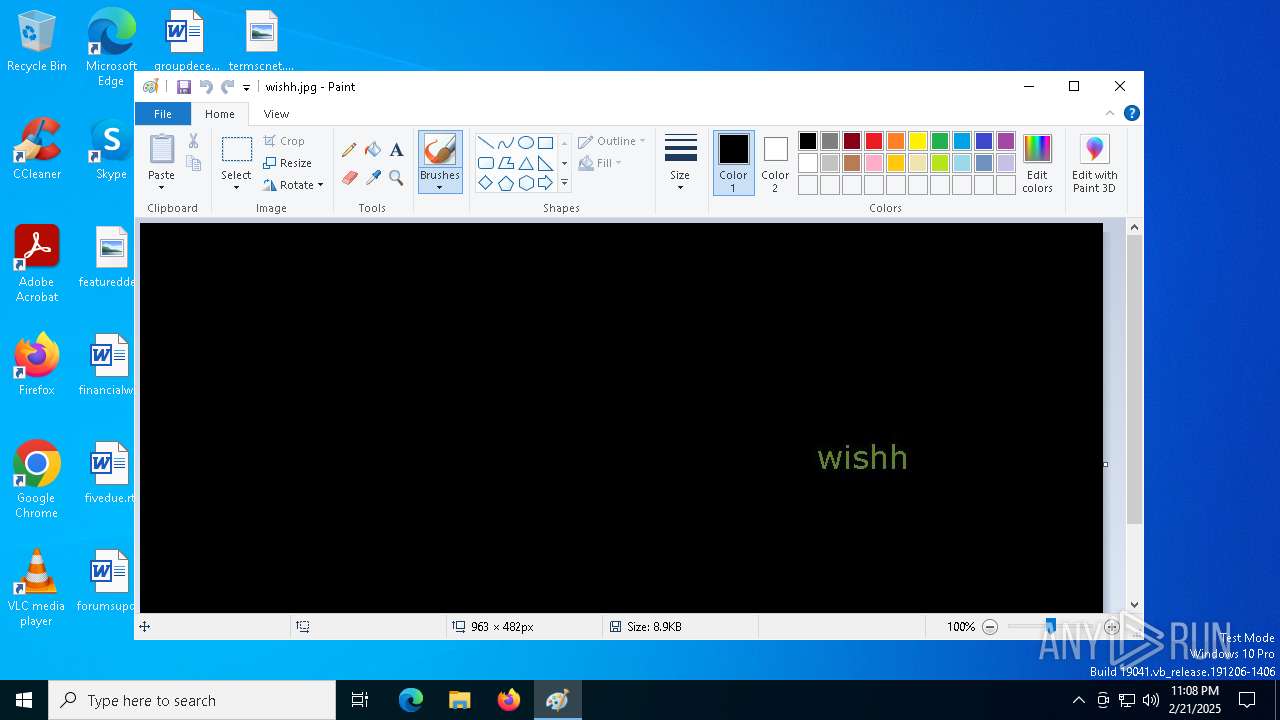
| 5036 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\wishh.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6572 | "C:\Users\admin\AppData\Local\Temp\Venom RAT + HVNC + Stealer + Grabber.exe" | C:\Users\admin\AppData\Local\Temp\Venom RAT + HVNC + Stealer + Grabber.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: VenomRAT Exit code: 3762504530 Version: 6.0.1 Modules
ims-api(PID) Process(6572) Venom RAT + HVNC + Stealer + Grabber.exe Telegram-Tokens (1)5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ Telegram-Info-Links 5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ Get info about bothttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getMe Get incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getUpdates Get webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getWebhookInfo Delete webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook?drop_pending_updates=true Discord-Webhook-Tokens (1)1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM Discord-Info-Links 1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM Get Webhook Infohttps://discord.com/api/webhooks/1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM | |||||||||||||||
| 6752 | C:\WINDOWS\system32\WerFault.exe -u -p 6572 -s 800 | C:\Windows\System32\WerFault.exe | Venom RAT + HVNC + Stealer + Grabber.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 857
Read events
3 828
Write events
28
Delete events
1
Modification events
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | WindowPlacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF7F000000470000007F04000087020000 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowThumbnail |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPWidth |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPHeight |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbXPos |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbYPos |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbWidth |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbHeight |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | UnitSetting |
Value: 0 | |||
| (PID) Process: | (5036) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowRulers |
Value: 0 | |||
Executable files
0
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6752 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Venom RAT + HVNC_ea87d7c01f8e574b49834696c258264836d983e_d3562942_f0978689-c742-4c36-9b00-adef41692920\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6752 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Venom RAT + HVNC + Stealer + Grabber.exe.6572.dmp | — | |
MD5:— | SHA256:— | |||
| 6752 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:8C3F87539AF16CAE75CE30ADB8E3F8AE | SHA256:D75DEF41F137D3A81EF0C7A92D245CD3DF482797D3B44D9817B18CFFA2CF88F9 | |||
| 6752 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
| 6752 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5672.tmp.xml | xml | |
MD5:7FB476EA797AC9668368E334BD8ED0B1 | SHA256:9E045FB61D77D3A973C67CB244E830728CA65186CFB3F22BA8DA7C2E3294AB1A | |||
| 6752 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:680B0331A3CC8FCCE16367586EC7A721 | SHA256:19F1B5D2C7F62663C14D97578411DC610E5F33E6CE4165977314442435F15305 | |||
| 6752 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5642.tmp.WERInternalMetadata.xml | binary | |
MD5:D098C10291B4654C01459E795C473E3F | SHA256:EBC84F48DE63584D57946FF33B8F33F7DB0735797B9333E5EB4DC3B5F4719B47 | |||
| 6752 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5528.tmp.dmp | binary | |
MD5:BE01A7C0CFBB2691E962B8AB20DDD902 | SHA256:563225244A42FD6DFF731E03126BB853ACC00E6620C7EA637B01BD68E31975A7 | |||
| 6752 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:7AA6E1C2C2D6A99B41276394450B695E | SHA256:04ACE464D82B7F3726EE0A3CC3FDAB7FB3F97659320F5C5F453AC7A3B2F02E62 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4008 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4008 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6824 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6752 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1752 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4008 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4008 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |