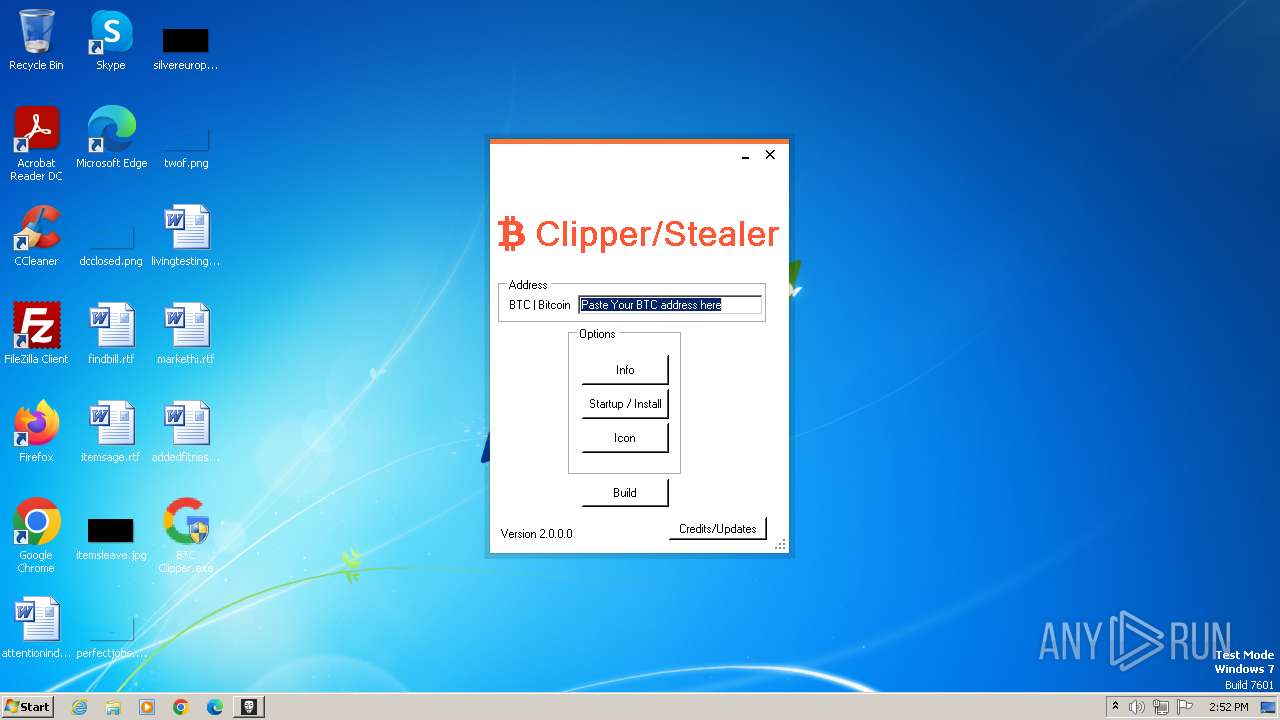
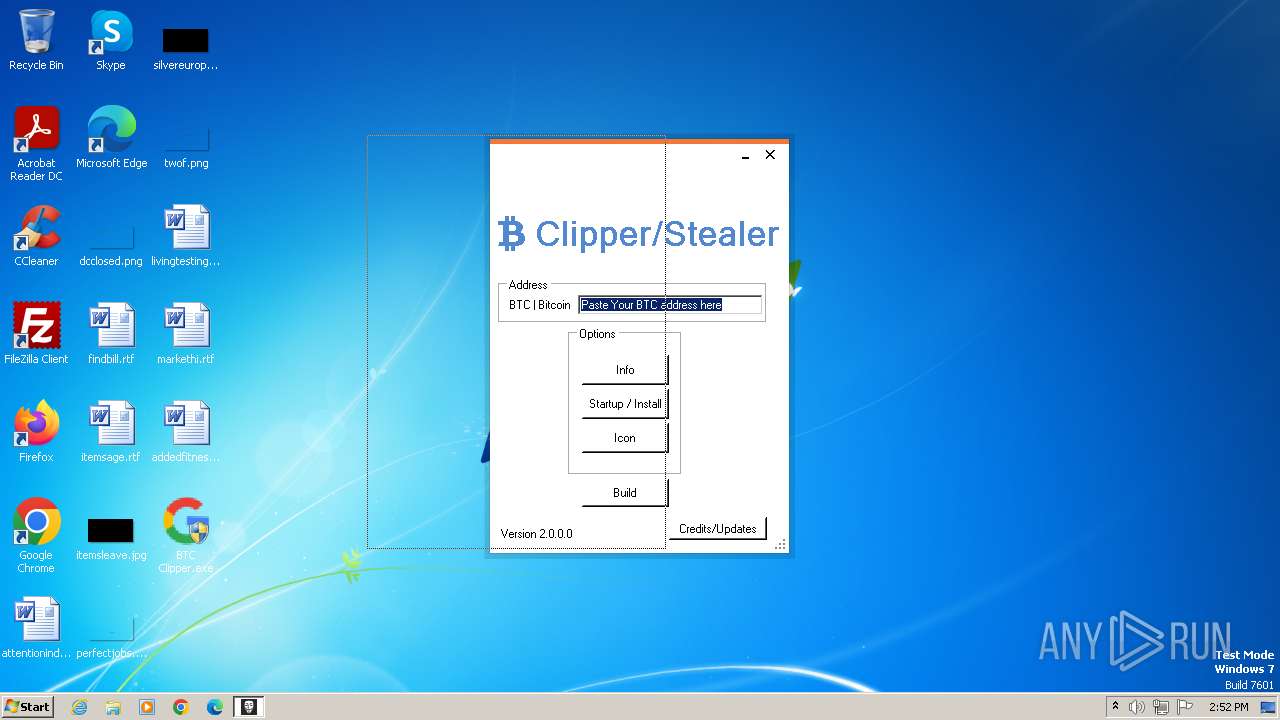
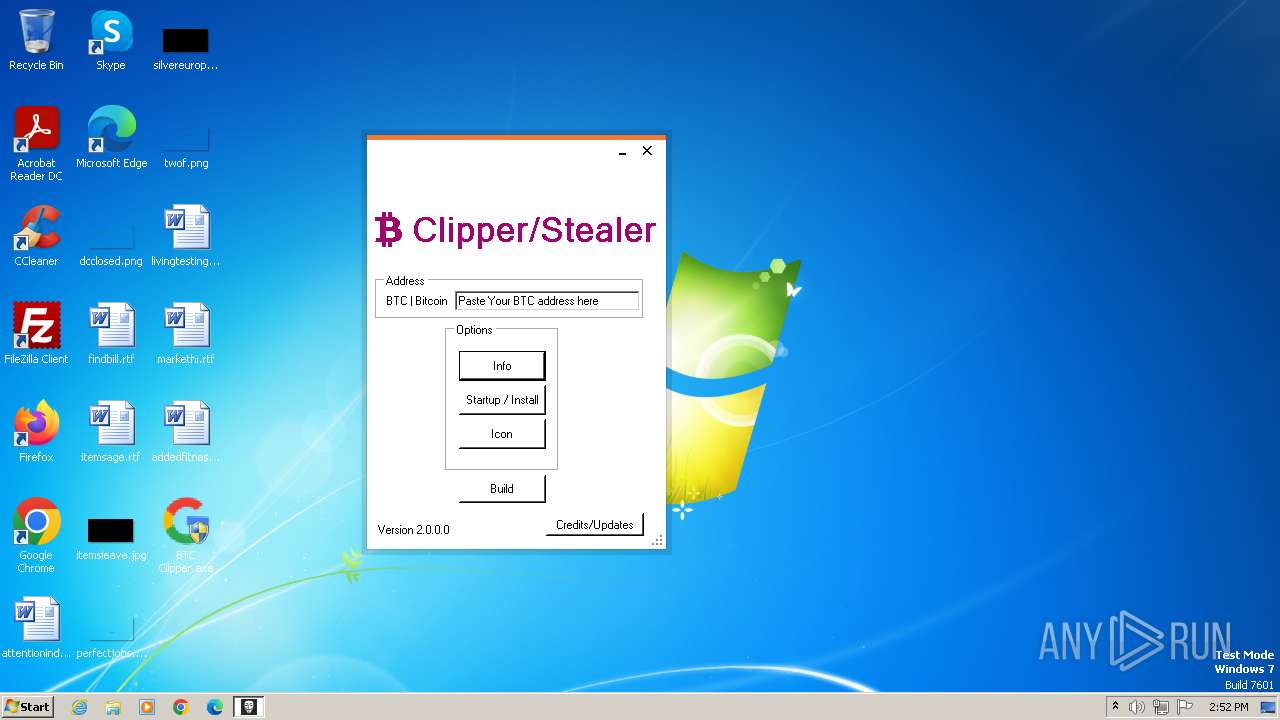
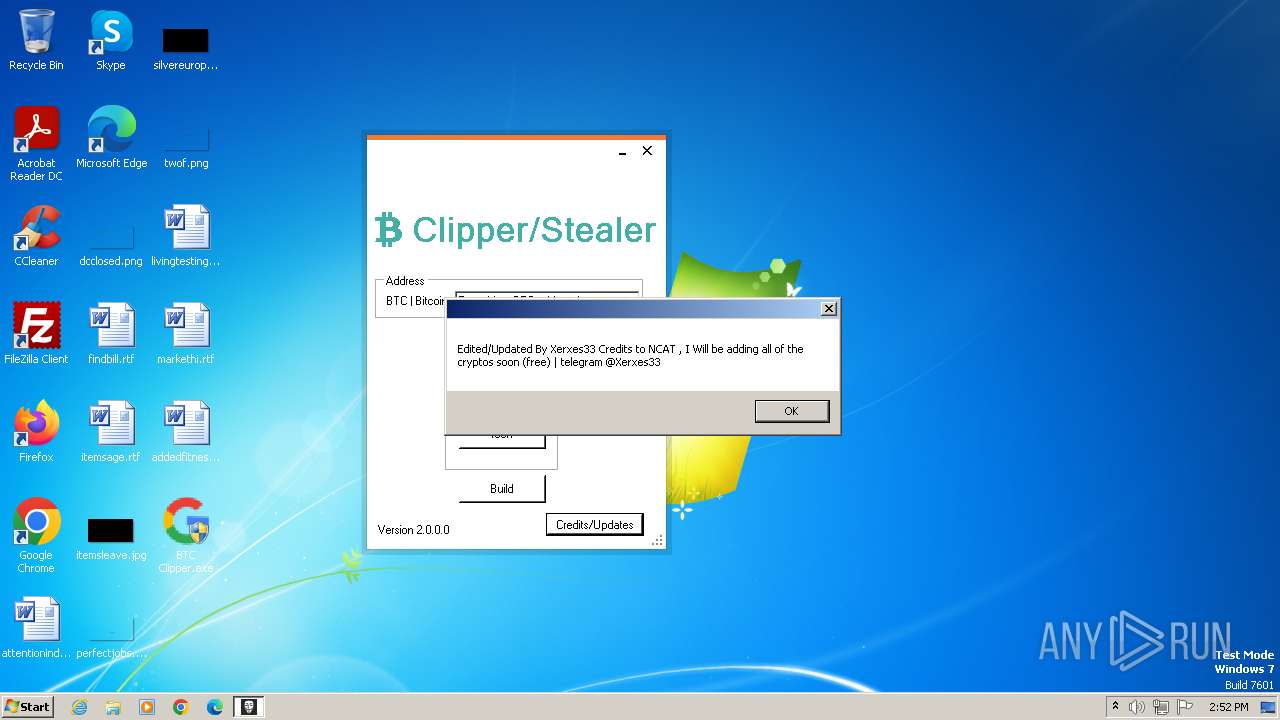
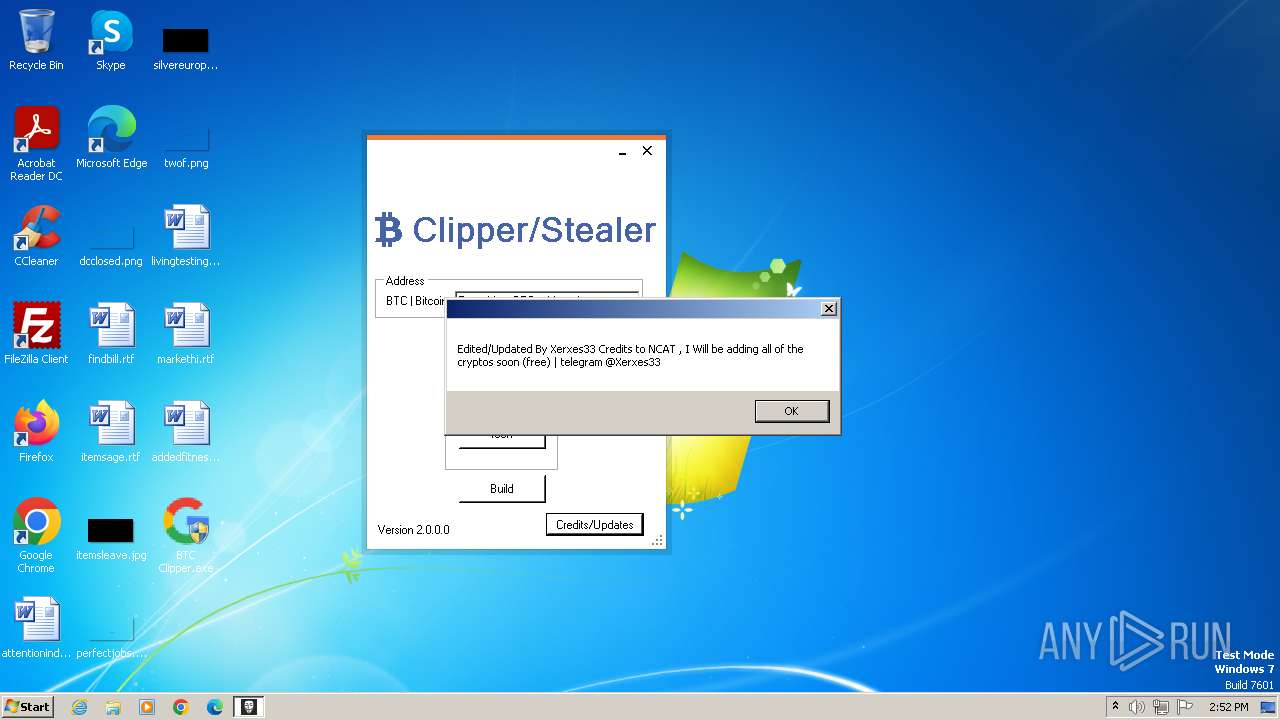
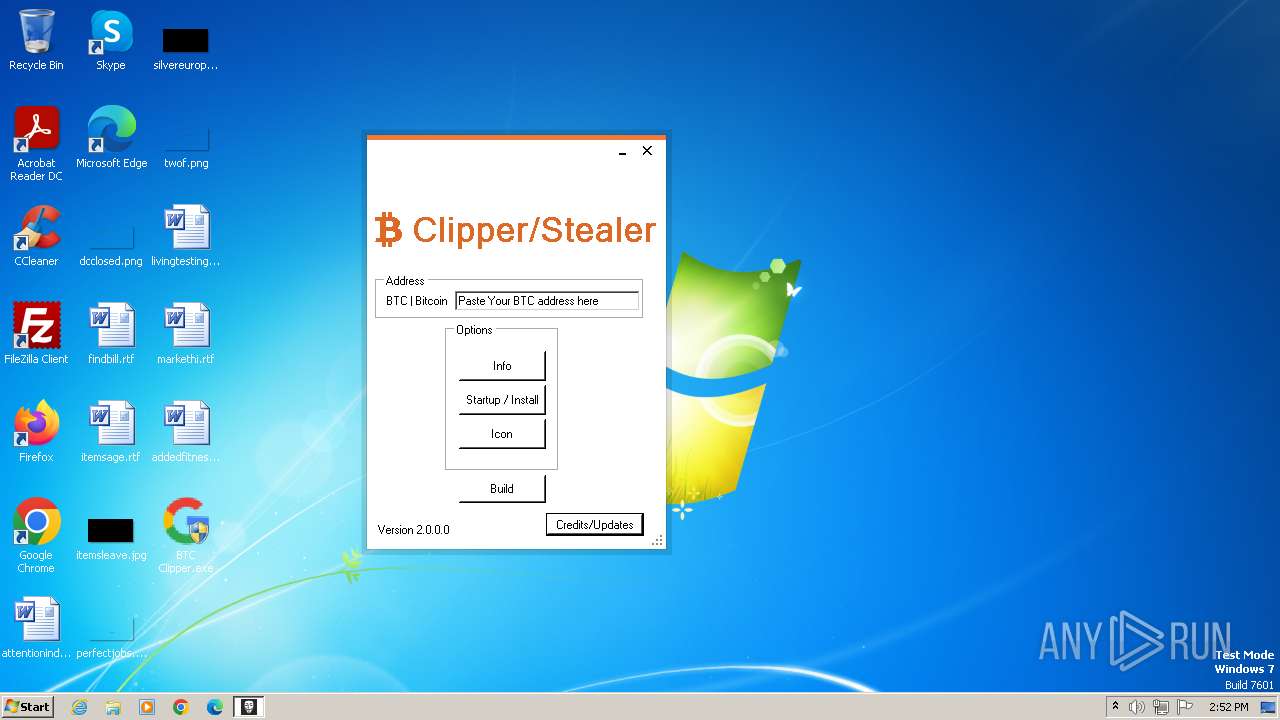
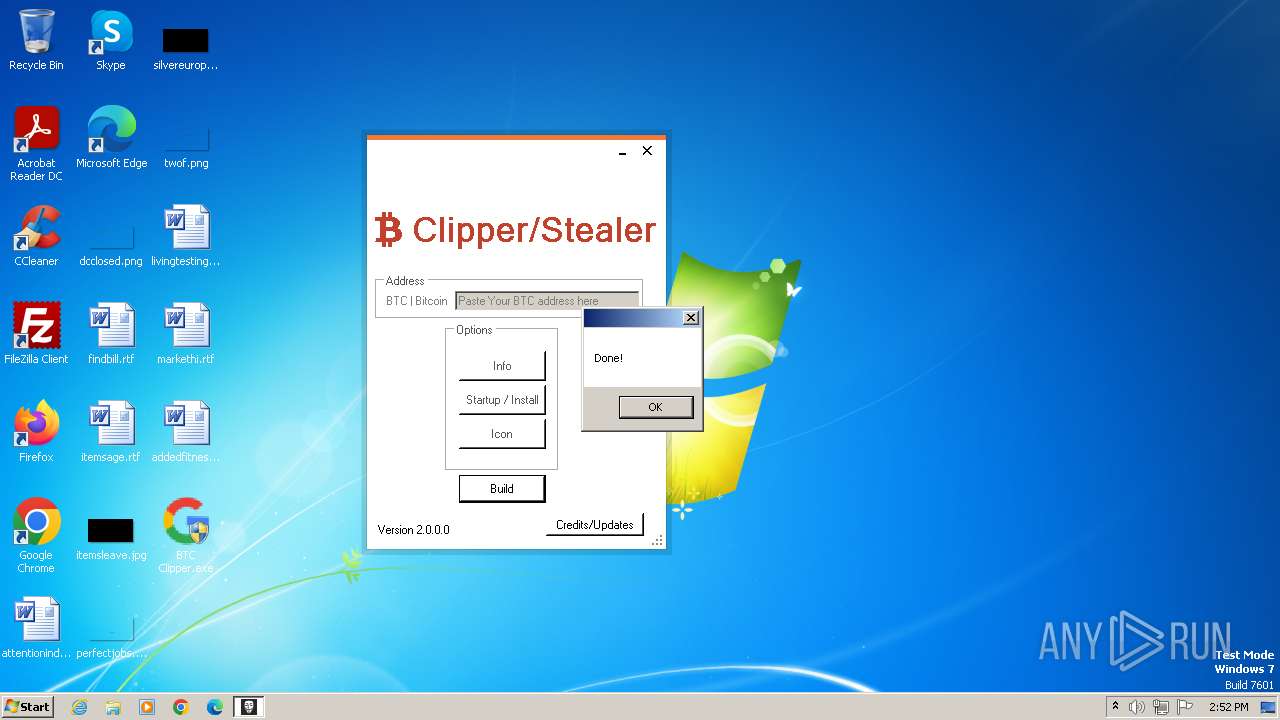
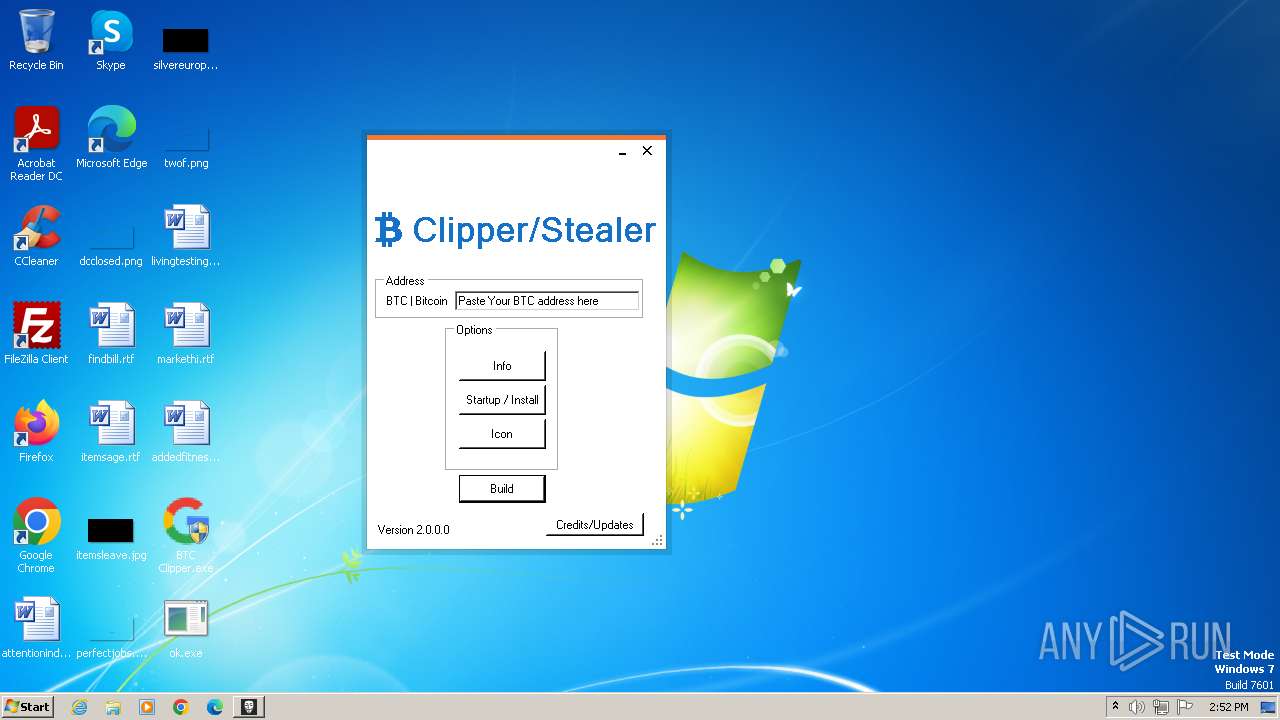
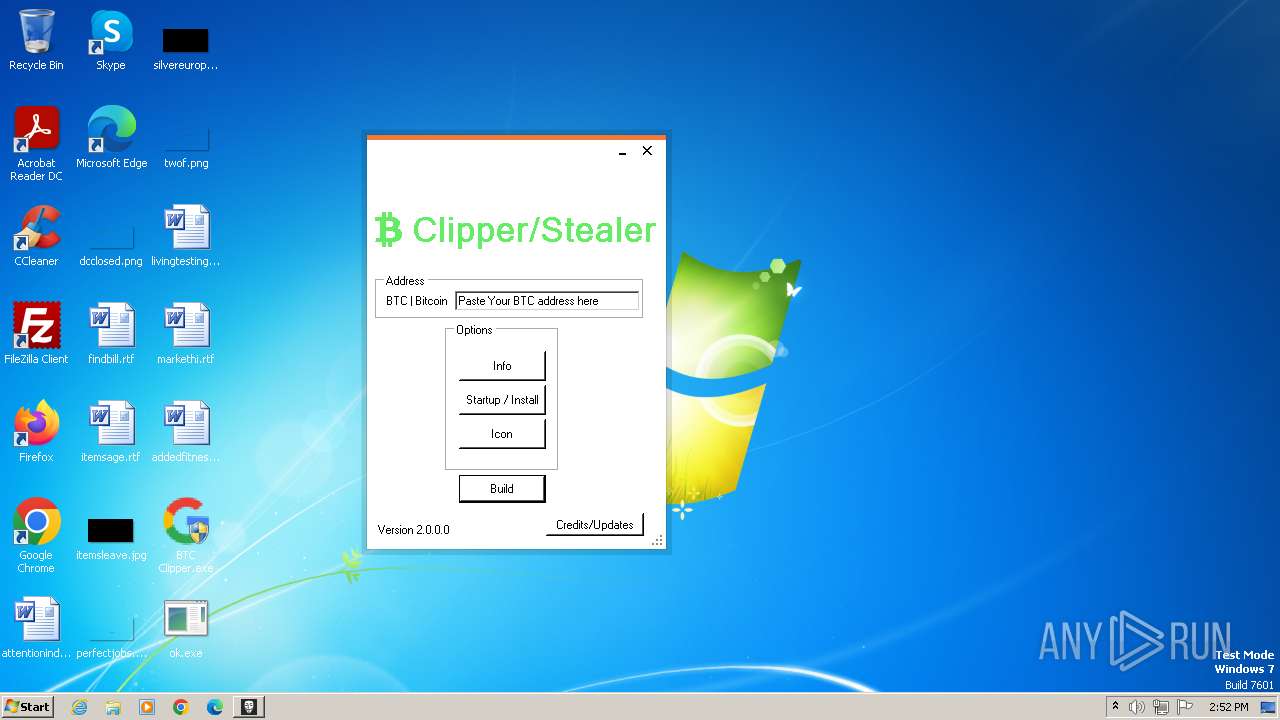
| File name: | BTC Clipper.exe |
| Full analysis: | https://app.any.run/tasks/04235dd6-e04b-4c08-927f-5c0d19981761 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | November 01, 2023, 14:51:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | BD212E070033532AB06F87ECBAA1617A |
| SHA1: | 16BEAB6537DADC0914E08DF8A6A982C05F3D17DC |
| SHA256: | 72E8CFCD324D92545282E013AB2C6CF8D1DB83EAF77D814D66B469EC9C4C9A4E |
| SSDEEP: | 6144:8kTynwQMGQzhfs5milS6NDtdjoFCKlkqFQx0eAbwRayhLlk+je2WPk8:cntmfKlSYjWCCtF05USay5qPk8 |
MALICIOUS
REDLINE has been detected (YARA)
- build.exe (PID: 1180)
Drops the executable file immediately after the start
- BTC Clipper.exe (PID: 328)
- csc.exe (PID: 3792)
Starts Visual C# compiler
- BTC Clipper.exe (PID: 128)
SUSPICIOUS
Reads the Internet Settings
- build.exe (PID: 1180)
- BTC Clipper.exe (PID: 328)
- BTC Clipper.exe (PID: 128)
Uses .NET C# to load dll
- BTC Clipper.exe (PID: 128)
Connects to unusual port
- build.exe (PID: 1180)
INFO
Reads the machine GUID from the registry
- BTC Clipper.exe (PID: 128)
- build.exe (PID: 1180)
- cvtres.exe (PID: 976)
- ok.exe (PID: 2668)
- csc.exe (PID: 3792)
- ok.exe (PID: 1120)
Reads the computer name
- BTC Clipper.exe (PID: 328)
- build.exe (PID: 1180)
- BTC Clipper.exe (PID: 128)
- ok.exe (PID: 2668)
- ok.exe (PID: 1120)
Create files in a temporary directory
- BTC Clipper.exe (PID: 328)
- BTC Clipper.exe (PID: 128)
- cvtres.exe (PID: 976)
Checks supported languages
- BTC Clipper.exe (PID: 328)
- BTC Clipper.exe (PID: 128)
- csc.exe (PID: 3792)
- build.exe (PID: 1180)
- ok.exe (PID: 2668)
- ok.exe (PID: 1120)
- cvtres.exe (PID: 976)
Reads Environment values
- build.exe (PID: 1180)
Manual execution by a user
- ok.exe (PID: 1120)
- ok.exe (PID: 2668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(1180) build.exe
C2 (1)193.161.193.99:22547
Botnetcheat
US (153)
Environment
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Local State
LocalPrefs.json
Host
Port
:
User
Pass
MANGO
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
http://
/
|
Yandex\YaAddon
193.161.193.99:22547
cheat
,
asf
*wallet*
Armory
\Armory
*.wallet
Atomic
\atomic
*
ibnejdfjmmkpcnlpebklmnkoeoihofec
Tronlink
jbdaocneiiinmjbjlgalhcelgbejmnid
NiftyWallet
nkbihfbeogaeaoehlefnkodbefgpgknn
Metamask
afbcbjpbpfadlkmhmclhkeeodmamcflc
MathWallet
hnfanknocfeofbddgcijnmhnfnkdnaad
Coinbase
fhbohimaelbohpjbbldcngcnapndodjp
BinanceChain
odbfpeeihdkbihmopkbjmoonfanlbfcl
BraveWallet
hpglfhgfnhbgpjdenjgmdgoeiappafln
GuardaWallet
blnieiiffboillknjnepogjhkgnoapac
EqualWallet
cjelfplplebdjjenllpjcblmjkfcffne
JaxxxLiberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi
BitAppWallet
kncchdigobghenbbaddojjnnaogfppfj
iWallet
amkmjjmmflddogmhpjloimipbofnfjih
Wombat
UnknownExtension
_
Local Extension Settings
Coinomi
\Coinomi
Profile_
Tel
egram.exe
\Telegram Desktop\tdata
-*.lo--g
1*.1l1d1b
String
Replace
System.UI
File.IO
*.json
string.Replace
Guarda
\Guarda
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
ToString
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
ROWindowsServiceOT\SecurityCenteWindowsServicer2
ROWindowsServiceOT\SecurWindowsServiceityCenter
AntqueiresivirusProdqueiresuct
AntqueiresiSpyqueiresWareProdqueiresuct
FiqueiresrewallProqueiresduct
WindowsService
SELECT * FROM
queires
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
TotalVisibleMemorySize
{0} MB or {1}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:03:31 17:09:55+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 165376 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x315d |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
50
Monitored processes
8
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\AppData\Local\Temp\BTC Clipper.exe" | C:\Users\admin\AppData\Local\Temp\BTC Clipper.exe | — | BTC Clipper.exe | |||||||||||
User: admin Company: BTC Clipper Integrity Level: HIGH Description: BTC Clipper Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 328 | "C:\Users\admin\Desktop\BTC Clipper.exe" | C:\Users\admin\Desktop\BTC Clipper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 976 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESF6C6.tmp" "c:\Users\admin\Desktop\CSC6459833C64D149C3B4844B4D7BF9D9A.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.51209.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 1120 | "C:\Users\admin\Desktop\ok.exe" | C:\Users\admin\Desktop\ok.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\AppData\Local\Temp\build.exe" | C:\Users\admin\AppData\Local\Temp\build.exe | BTC Clipper.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
RedLine(PID) Process(1180) build.exe C2 (1)193.161.193.99:22547 Botnetcheat US (153) Environment UNKNOWN . 1 cmyredmyit_cmyardmys my as21 \ Local State LocalPrefs.json Host Port : User Pass MANGO %USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal WanaLife Def Win String.Replace String.Remove windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob BCrypt.BCryptImportKey() failed with status code:{0} BCrypt.BCryptGetProperty() (get size) failed with status code:{0} BCrypt.BCryptGetProperty() failed with status code:{0} - http:// / | Yandex\YaAddon 193.161.193.99:22547 cheat , asf *wallet* Armory \Armory *.wallet Atomic \atomic * ibnejdfjmmkpcnlpebklmnkoeoihofec Tronlink jbdaocneiiinmjbjlgalhcelgbejmnid NiftyWallet nkbihfbeogaeaoehlefnkodbefgpgknn Metamask afbcbjpbpfadlkmhmclhkeeodmamcflc MathWallet hnfanknocfeofbddgcijnmhnfnkdnaad Coinbase fhbohimaelbohpjbbldcngcnapndodjp BinanceChain odbfpeeihdkbihmopkbjmoonfanlbfcl BraveWallet hpglfhgfnhbgpjdenjgmdgoeiappafln GuardaWallet blnieiiffboillknjnepogjhkgnoapac EqualWallet cjelfplplebdjjenllpjcblmjkfcffne JaxxxLiberty fihkakfobkmkjojpchpfgcmhfjnmnfpi BitAppWallet kncchdigobghenbbaddojjnnaogfppfj iWallet amkmjjmmflddogmhpjloimipbofnfjih Wombat UnknownExtension _ Local Extension Settings Coinomi \Coinomi Profile_ Tel egram.exe \Telegram Desktop\tdata -*.lo--g 1*.1l1d1b String Replace System.UI File.IO *.json string.Replace Guarda \Guarda %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel ToString ( UNIQUE " Width Height CopyFromScreen kernel32 user32.dll GetConsoleWindow ShowWindow SELECT * FROM Win32_Processor Name NumberOfCores root\CIMV2 SELECT * FROM Win32_VideoController AdapterRAM ROWindowsServiceOT\SecurityCenteWindowsServicer2 ROWindowsServiceOT\SecurWindowsServiceityCenter AntqueiresivirusProdqueiresuct AntqueiresiSpyqueiresWareProdqueiresuct FiqueiresrewallProqueiresduct WindowsService SELECT * FROM queires SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELECT * FROM Win32_DiskDrive SerialNumber ' ExecutablePath [ ] 0 Mb or 0 SELECT * FROM Win32_OperatingSystem TotalVisibleMemorySize {0} MB or {1} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ | |||||||||||||||
| 2360 | "C:\Users\admin\Desktop\BTC Clipper.exe" | C:\Users\admin\Desktop\BTC Clipper.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\Desktop\ok.exe" | C:\Users\admin\Desktop\ok.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3792 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\temp\4tkbulxt.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | BTC Clipper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
3 246
Read events
3 163
Write events
80
Delete events
3
Modification events
| (PID) Process: | (328) BTC Clipper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (328) BTC Clipper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (328) BTC Clipper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (328) BTC Clipper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (128) BTC Clipper.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (128) BTC Clipper.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (128) BTC Clipper.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000010000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (128) BTC Clipper.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (128) BTC Clipper.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (128) BTC Clipper.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 328 | BTC Clipper.exe | C:\Users\admin\AppData\Local\Temp\build.exe | executable | |
MD5:C4DEECD4A59A1CC9C44E21C0035980C1 | SHA256:64A2D8E0ABB805B5B0F1784AC306697D60B6A14EDECA6BA0AA24E0339019E5A1 | |||
| 128 | BTC Clipper.exe | C:\Users\admin\AppData\Local\Temp\temp\4tkbulxt.cmdline | text | |
MD5:6EE9AAF3484721B0941EE662AF563D96 | SHA256:14A0D9DABBAB2F31AD9AE161DF081383EA43FE05AF56E0F9F7F0533A917F4D26 | |||
| 3792 | csc.exe | C:\Users\admin\AppData\Local\Temp\temp\4tkbulxt.out | text | |
MD5:82AE75523AC34BCD06DE81A5C9374D78 | SHA256:89B725A668F63C01578401440482C7C8C6EBDF3BB87EAACD616DC9B60944EEED | |||
| 3792 | csc.exe | C:\Users\admin\Desktop\CSC6459833C64D149C3B4844B4D7BF9D9A.TMP | res | |
MD5:D9262AE4AA194C10A9978E5540166F5B | SHA256:B8D62A328F747D74147DE121219DCFE5BB188D6C0147B91CCD3A3E73709FE64D | |||
| 3792 | csc.exe | C:\Users\admin\Desktop\ok.exe | executable | |
MD5:F909AA2FCB8D41DD9CDA60F1FA2168B4 | SHA256:A44781638ED8F767AE6BD754E8D160B8EEFA202254C4521E46534E3B48B796B2 | |||
| 128 | BTC Clipper.exe | C:\Users\admin\AppData\Local\Temp\temp\4tkbulxt.0.cs | text | |
MD5:CFAF34E3784B6B28EA88B0D38AB537FD | SHA256:CBC8101CE0F0A2C2042F354E0107B8D85E7F5492A34846BFDD86B66F6BB8BA22 | |||
| 976 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESF6C6.tmp | o | |
MD5:50E2D32BE182C7303C1138253CB6037E | SHA256:8030F027729B9D52019DC913D0FFB00E547FFEF423A4E29A2F060CFD1219C169 | |||
| 328 | BTC Clipper.exe | C:\Users\admin\AppData\Local\Temp\BTC Clipper.exe | executable | |
MD5:4DF548804756424AB34309266B56683D | SHA256:0B01123EA0752F6E32559658FD2CAC78C26706ABFE375694A7DED496129FEEC1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
15
DNS requests
0
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
— | — | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
1180 | build.exe | POST | 404 | 193.161.193.99:22547 | http://193.161.193.99:22547/ | unknown | xml | 341 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1180 | build.exe | 193.161.193.99:22547 | — | OOO Bitree Networks | RU | malicious |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |