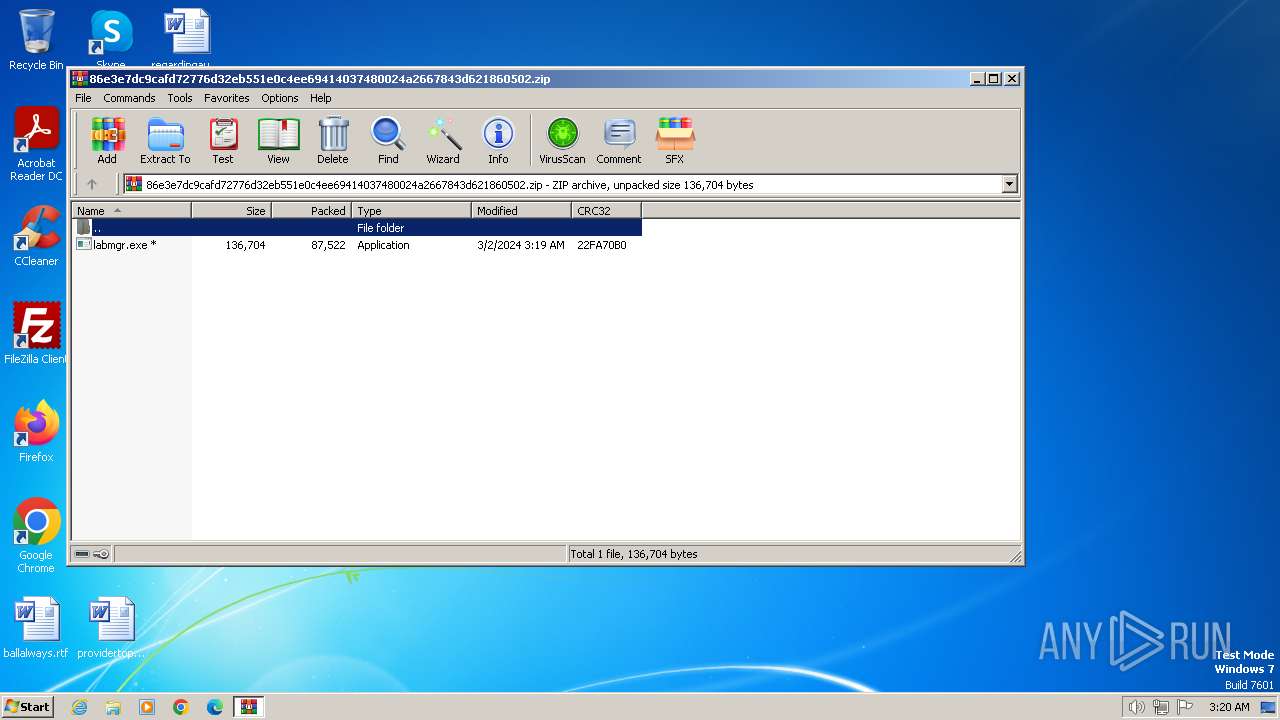
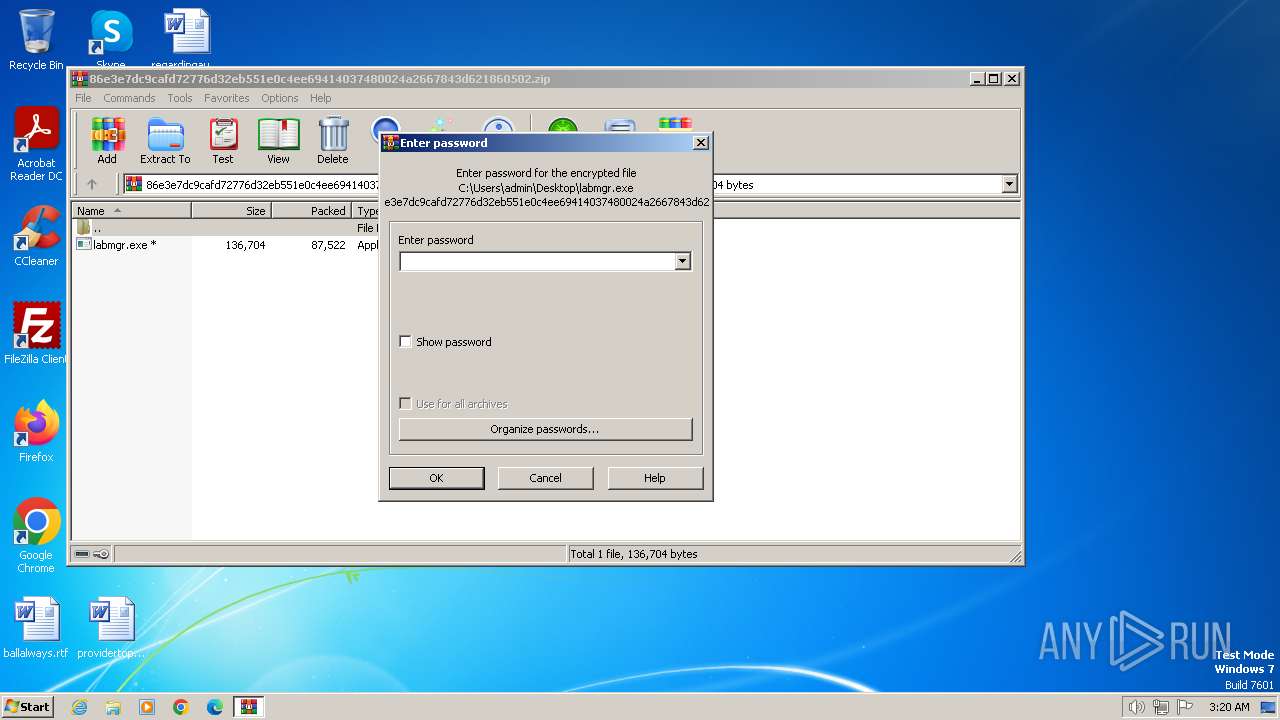
| File name: | 86e3e7dc9cafd72776d32eb551e0c4ee69414037480024a2667843d621860502.zip |
| Full analysis: | https://app.any.run/tasks/4022ee84-73ca-4e03-b574-009a43f85a38 |
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | March 02, 2024, 03:20:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | D522A6E245325D9CB40BE28EBE239102 |
| SHA1: | FC3A3C307947F8DC2701046D75893021B194304F |
| SHA256: | 72D8CAEF6849A37A1CB90703AE79F63ED5DF5AD3259C31959C17DC96C5D0DA3B |
| SSDEEP: | 3072:V9+HOXJdkJvQ5gjs8c5vLj9vKa7jy87SSMG9PFequo:VGOXkJfjsNl5F7jy8eSMOPFeqN |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2472)
Create files in the Startup directory
- iexplore.exe (PID: 3500)
Application was injected by another process
- smss.exe (PID: 260)
- svchost.exe (PID: 1080)
- taskeng.exe (PID: 300)
- explorer.exe (PID: 1164)
- svchost.exe (PID: 1908)
- ctfmon.exe (PID: 1564)
- svchost.exe (PID: 756)
- svchost.exe (PID: 972)
- spoolsv.exe (PID: 1224)
- dwm.exe (PID: 612)
- services.exe (PID: 472)
- svchost.exe (PID: 672)
- IMEDICTUPDATE.EXE (PID: 1440)
- svchost.exe (PID: 1360)
- svchost.exe (PID: 828)
- svchost.exe (PID: 800)
- svchost.exe (PID: 1252)
- lsm.exe (PID: 496)
- svchost.exe (PID: 856)
- svchost.exe (PID: 596)
- svchost.exe (PID: 3196)
- msiexec.exe (PID: 2676)
- dllhost.exe (PID: 2328)
- SearchFilterHost.exe (PID: 3852)
- SearchProtocolHost.exe (PID: 3320)
- winlogon.exe (PID: 428)
- SearchIndexer.exe (PID: 2216)
- wininit.exe (PID: 380)
- csrss.exe (PID: 388)
- csrss.exe (PID: 344)
- dllhost.exe (PID: 1876)
- lsass.exe (PID: 488)
Runs injected code in another process
- iexplore.exe (PID: 2120)
Connects to the CnC server
- iexplore.exe (PID: 3500)
Actions looks like stealing of personal data
- SearchIndexer.exe (PID: 2216)
RAMNIT has been detected (SURICATA)
- iexplore.exe (PID: 3500)
SUSPICIOUS
Process drops legitimate windows executable
- iexplore.exe (PID: 3500)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2472)
- iexplore.exe (PID: 3500)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
Reads the Internet Settings
- explorer.exe (PID: 1164)
Checks supported languages
- labmgr.exe (PID: 2340)
Reads the computer name
- labmgr.exe (PID: 2340)
Creates files in the program directory
- iexplore.exe (PID: 3500)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3500)
Connects to unusual port
- iexplore.exe (PID: 3500)
Manual execution by a user
- labmgr.exe (PID: 2340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:03:02 03:19:56 |
| ZipCRC: | 0x22fa70b0 |
| ZipCompressedSize: | 87522 |
| ZipUncompressedSize: | 136704 |
| ZipFileName: | labmgr.exe |
Total processes
44
Monitored processes
36
Malicious processes
28
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 260 | \SystemRoot\System32\smss.exe | C:\Windows\System32\smss.exe | System | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Session Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 300 | taskeng.exe {CE1452CD-5E82-4DCD-B0CC-498574D17563} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 344 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 380 | wininit.exe | C:\Windows\System32\wininit.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 428 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 472 | C:\Windows\system32\services.exe | C:\Windows\System32\services.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 488 | C:\Windows\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Exit code: 0 Version: 6.1.7601.24545 (win7sp1_ldr_escrow.200102-1707) Modules
| |||||||||||||||
| 496 | C:\Windows\system32\lsm.exe | C:\Windows\System32\lsm.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Session Manager Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 596 | C:\Windows\system32\svchost.exe -k DcomLaunch | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 849
Read events
8 754
Write events
95
Delete events
0
Modification events
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: 525400363EFF | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C4700000000020000000000106600000001000020000000EF3FC27F2EB0B599266B8E40784C73842D1D53B0DAA2FFA1DB93824F89C2F297000000000E8000000002000020000000024E4A26A7D755812D1B6215F9C143287D8DBC2F6A40DE0AA9F35BBC8902860830000000DD0A75BE11FB062415DDBE3A74DB77CF7AF386A11ACFC677DC7C152EC0F1915644AE191EC187A5F4E22FD1F35104F498400000005AC981A2E5808238BE1C9CE40A68C9AAE68BFB998F3882754C9275AB2DBC23BC9FCFDDBDF378B6BB8D77BC37DAEE32506596C99E2B62B63B81D7B6DF1020A1CE | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\86e3e7dc9cafd72776d32eb551e0c4ee69414037480024a2667843d621860502.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
14
Suspicious files
3
Text files
37
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\enbfqohg.exe | executable | |
MD5:97AA362A4243CE01FAC7C3841EB1E05F | SHA256:86E3E7DC9CAFD72776D32EB551E0C4EE69414037480024A2667843D621860502 | |||
| 3500 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\ccme_ecc.dll | executable | |
MD5:E2A0AC14D6CB34616A7A27154D22EEEF | SHA256:78FE30E6793296AA82FBA7F7C829EE1C02A6F003F7123E49B20D04131B42E0D7 | |||
| 3500 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\ccme_asym.dll | executable | |
MD5:8E15A6D26E3623C61EF3412F195A7A8D | SHA256:099E35627745F3674E45CD5E121DCB4000FECAE31A6552598A9853F6112345AD | |||
| 3500 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\ccme_base_non_fips.dll | executable | |
MD5:F031D034AA98E220D8FFA4ED742A0D94 | SHA256:FDA6115E3E2557074664EB297CF9DA211A86206F0B5BB01F09CFCC870DE02460 | |||
| 3500 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\ccme_base.dll | executable | |
MD5:7BD074FD10048EBDE83FE1EE28F465C0 | SHA256:3A3E94FD9D0D86F9AFB8E2D8154B94193A8FEFF6C20163D95A92454767662166 | |||
| 3500 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Legal\ENU\license.html | html | |
MD5:B104B6B842CAFFA0ED8F373C571D6A02 | SHA256:821413D1AA35628CDEE9E74388175F6C1E635E72A59EA0D1B6759E8E487849FE | |||
| 3500 | iexplore.exe | C:\Program Files\Common Files\microsoft shared\OFFICE14\1033\README.HTM | html | |
MD5:C48BFBFDDC16EB72AAA8DE0D1A1468E7 | SHA256:B2FD2878A6CDFE10317252185E918CA91FCF008D1AE7AA9340894008E14A3E04 | |||
| 3500 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\WebResources\Resource1\index.html | html | |
MD5:64F083882D0D5BBF314688C6328E8728 | SHA256:2A40DFED4750C45F0C75EE1C5B67AE4DB1ADD370E7656A2C1D849350EFC50C15 | |||
| 3500 | iexplore.exe | C:\Program Files\Common Files\microsoft shared\OFFICE14\1036\LISEZMOI.HTM | html | |
MD5:E6576A9B9B0701F8B2F8BA6B81AD640C | SHA256:932979D224A81A930EC787012AECDB8E21BB5E875807D5D6E651DDE3F88A615D | |||
| 3500 | iexplore.exe | C:\Program Files\Common Files\microsoft shared\OFFICE14\1031\README.HTM | html | |
MD5:1E6A9019E91CFA5F78AD3B078E9CFEFE | SHA256:D6909ABFB629B472E04DA7A5812D631F94C3B17DF8FBAF23C098B204042B488F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
17
DNS requests
13
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3500 | iexplore.exe | 142.250.185.110:80 | — | GOOGLE | US | whitelisted |
3500 | iexplore.exe | 82.112.184.197:447 | supnewdmn.com | Vysokie tehnologii Limited Liability Company | RU | unknown |
3500 | iexplore.exe | 193.166.255.171:447 | rtvwerjyuver.com | Tieteen tietotekniikan keskus Oy | FI | unknown |
3500 | iexplore.exe | 49.13.77.253:447 | wqerveybrstyhcerveantbe.com | Hetzner Online GmbH | DE | unknown |
3500 | iexplore.exe | 172.217.16.142:80 | google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
supnewdmn.com |
| malicious |
dns.msftncsi.com |
| shared |
tvrstrynyvwstrtve.com |
| unknown |
rtvwerjyuver.com |
| whitelisted |
wqerveybrstyhcerveantbe.com |
| malicious |
google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3500 | iexplore.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Ramnit Checkin |
Process | Message |
|---|---|
svchost.exe | base\diagnosis\diagtrack\matchengine\asimovuploader.cpp(1592)\diagtrack.dll!710F7440: (caller: 710D8A3A) ReturnHr[PreRelease](26) tid(5c4) 80070510 The requested file operation failed because the storage policy blocks that type of file. For more information, contact your system administrator.
|
svchost.exe | base\diagnosis\diagtrack\engine\heartbeat.cpp(199)\diagtrack.dll!710D8A53: (caller: 710D8504) ReturnHr[PreRelease](27) tid(5c4) 80070510 The requested file operation failed because the storage policy blocks that type of file. For more information, contact your system administrator.
|