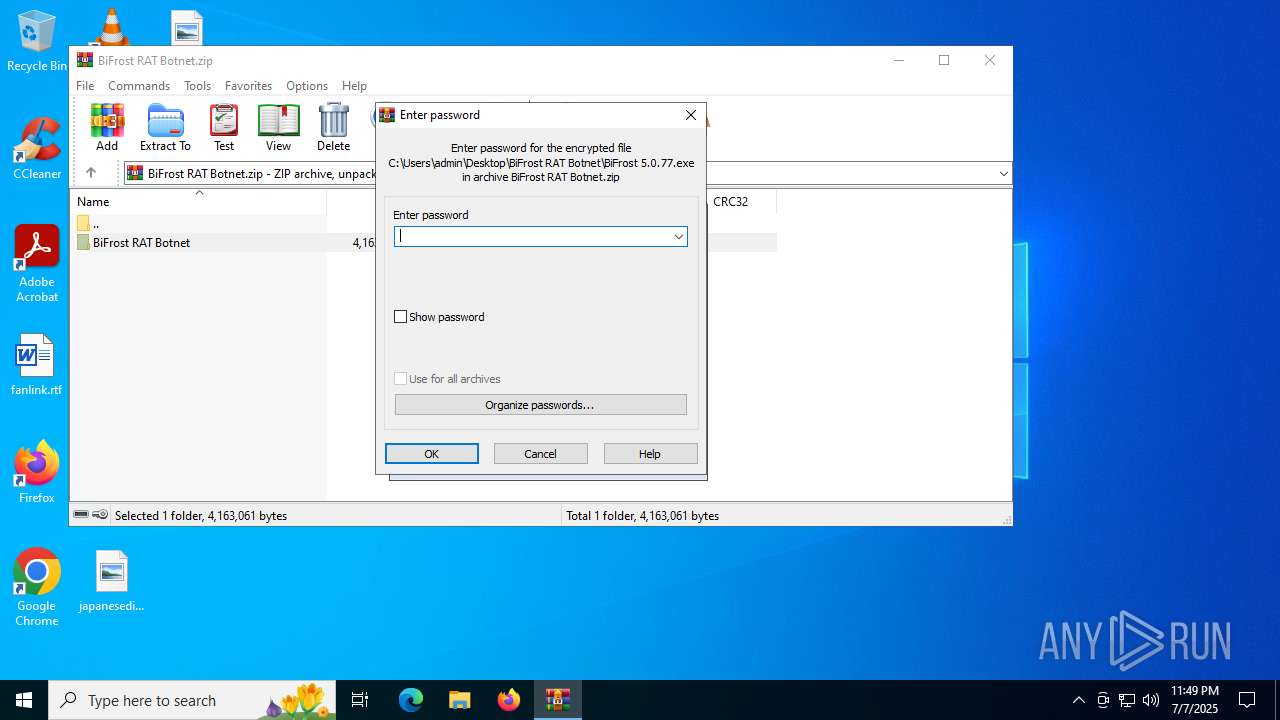
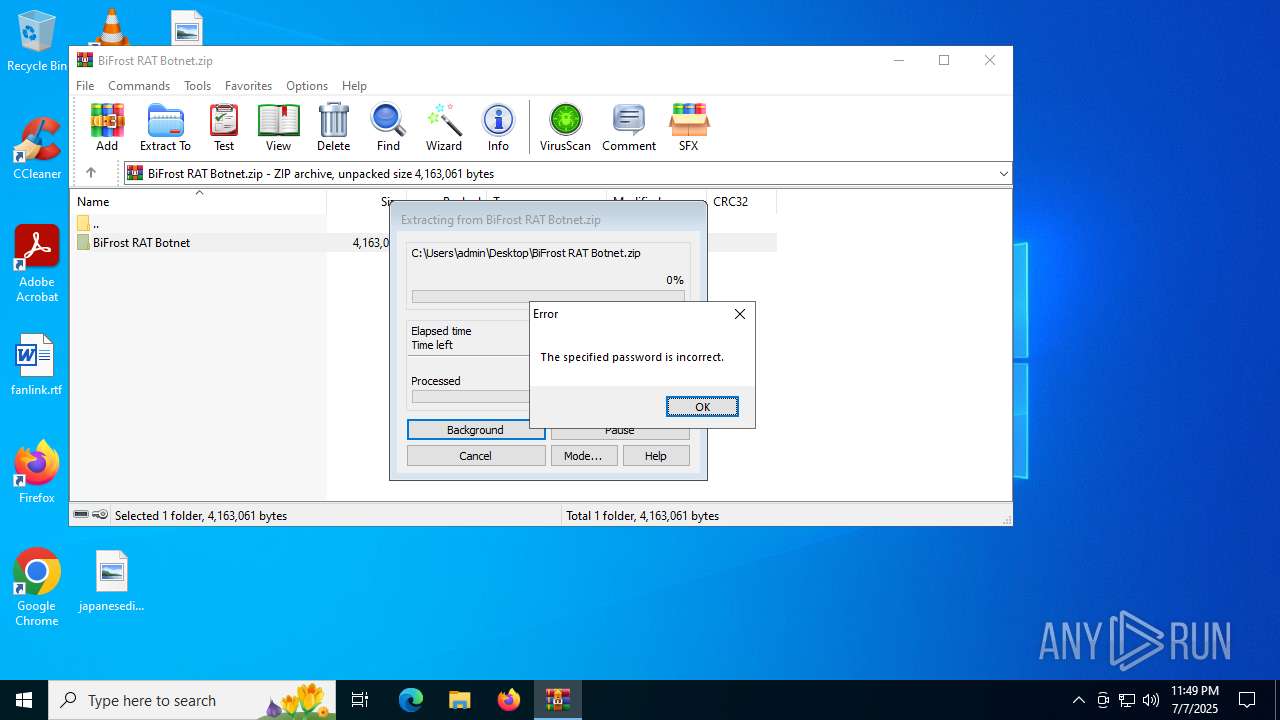
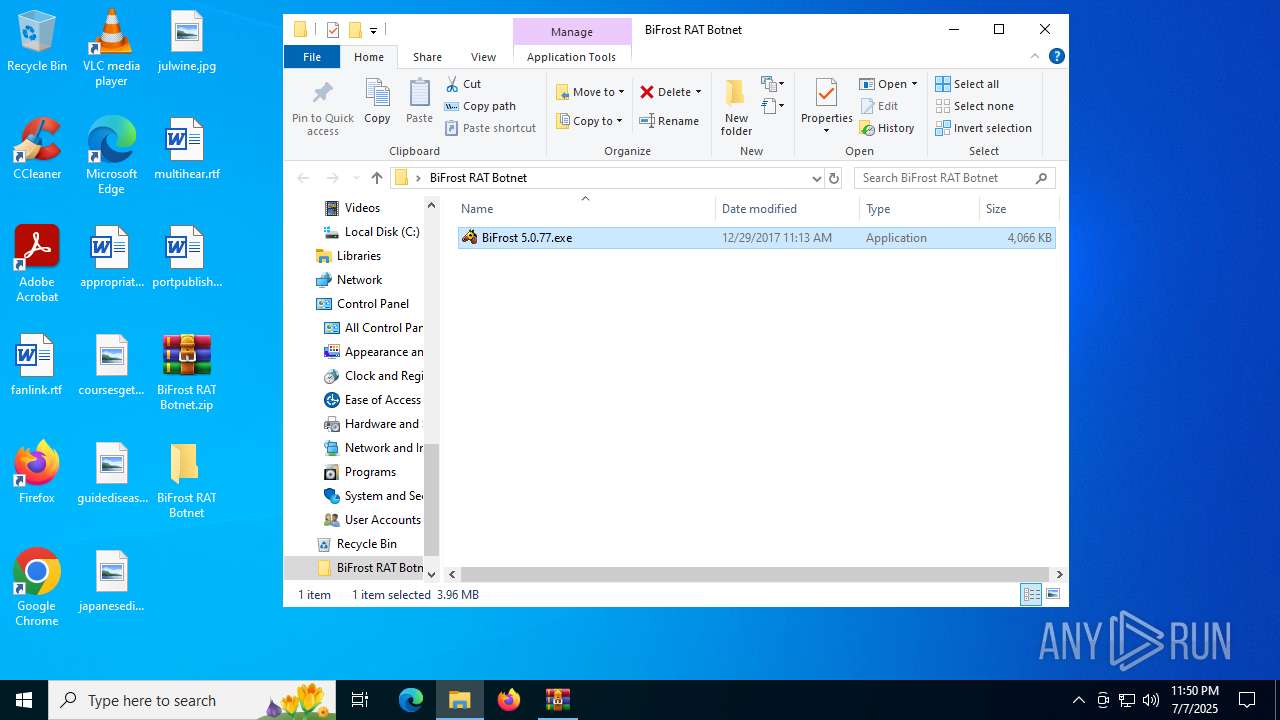
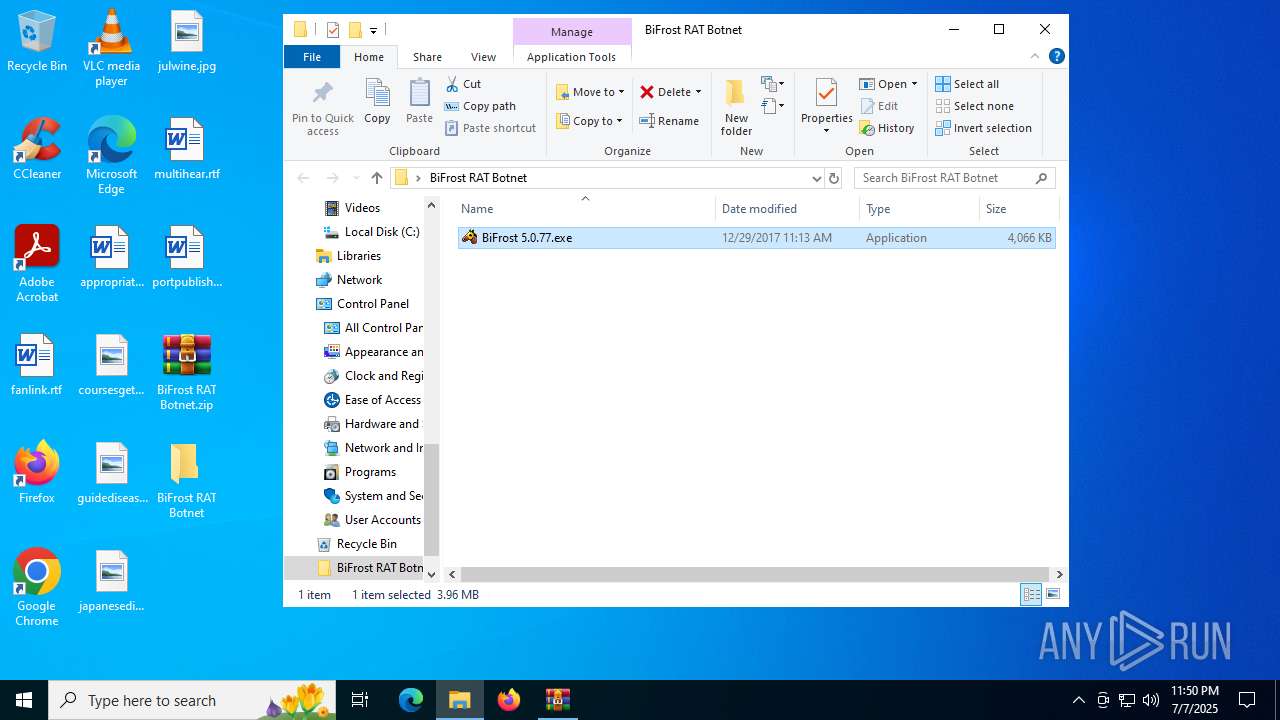
| File name: | BiFrost RAT Botnet.zip |
| Full analysis: | https://app.any.run/tasks/d9519a44-b953-44d9-963c-b332f229136f |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | July 07, 2025, 23:49:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 69F02E73A5C6E89C2B15B74E4EEE2190 |
| SHA1: | C94BA5D27984F5C914C4C623149E2F91CED20FAA |
| SHA256: | 72CCBF7F827D2CB60BA04E6B8762505E8B4802CE61CAFDA649C94CDFAB373C62 |
| SSDEEP: | 98304:V0JT3HN+BJXqvlMaWErXuz0aBUlH7eoV7XTZo365LcdIAy1kwijRh9MdEXHMVgjh:3BE5w0CL |
MALICIOUS
Actions looks like stealing of personal data
- mpv.exe (PID: 7100)
- mpv.exe (PID: 7936)
Steals credentials from Web Browsers
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Create files in the Startup directory
- cmd.exe (PID: 3588)
AVEMARIA mutex has been found
- HTTP Builder.exe (PID: 7136)
- HTTP Builder.exe (PID: 7828)
SUSPICIOUS
Reads the date of Windows installation
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Reads security settings of Internet Explorer
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Executable content was dropped or overwritten
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
BROWSERPASSVIEW has been detected
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Creates file in the systems drive root
- HTTP Builder.exe (PID: 7136)
- HTTP Builder.exe (PID: 7828)
Application launched itself
- HTTP Builder.exe (PID: 7136)
- HTTP Builder.exe (PID: 7828)
Connects to FTP
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
There is functionality for taking screenshot (YARA)
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Starts CMD.EXE for commands execution
- HTTP Builder.exe (PID: 7136)
- HTTP Builder.exe (PID: 7828)
INFO
Reads the computer name
- BiFrost 5.0.77.exe (PID: 5716)
- HTTP Builder.exe (PID: 7136)
- mpv.exe (PID: 7100)
- WBP.exe (PID: 6472)
- mespv.exe (PID: 6412)
- pv.exe (PID: 1520)
- BiFrost 5.0.77.exe (PID: 7624)
- HTTP Builder.exe (PID: 7828)
- mpv.exe (PID: 7936)
- mespv.exe (PID: 304)
- WBP.exe (PID: 8044)
- pv.exe (PID: 5708)
Checks supported languages
- BiFrost 5.0.77.exe (PID: 5716)
- HTTP Builder.exe (PID: 7136)
- mpv.exe (PID: 7100)
- WBP.exe (PID: 6472)
- pv.exe (PID: 1520)
- mespv.exe (PID: 6412)
- BiFrost 5.0.77.exe (PID: 7624)
- HTTP Builder.exe (PID: 7828)
- mpv.exe (PID: 7936)
- WBP.exe (PID: 8044)
- mespv.exe (PID: 304)
- pv.exe (PID: 5708)
Manual execution by a user
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2040)
Process checks computer location settings
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Reads the machine GUID from the registry
- BiFrost 5.0.77.exe (PID: 5716)
- WBP.exe (PID: 6472)
- HTTP Builder.exe (PID: 7136)
- mespv.exe (PID: 6412)
- BiFrost 5.0.77.exe (PID: 7624)
- HTTP Builder.exe (PID: 7828)
- WBP.exe (PID: 8044)
- mespv.exe (PID: 304)
Create files in a temporary directory
- BiFrost 5.0.77.exe (PID: 5716)
- mpv.exe (PID: 7100)
- WBP.exe (PID: 6472)
- mespv.exe (PID: 6412)
- pv.exe (PID: 1520)
- BiFrost 5.0.77.exe (PID: 7624)
- mpv.exe (PID: 7936)
- WBP.exe (PID: 8044)
- mespv.exe (PID: 304)
- pv.exe (PID: 5708)
NirSoft software is detected
- mpv.exe (PID: 7100)
- WBP.exe (PID: 6472)
- pv.exe (PID: 1520)
- mespv.exe (PID: 6412)
- mpv.exe (PID: 7936)
- mespv.exe (PID: 304)
- pv.exe (PID: 5708)
- WBP.exe (PID: 8044)
The sample compiled with english language support
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Reads Microsoft Office registry keys
- pv.exe (PID: 1520)
- pv.exe (PID: 5708)
Reads Windows Product ID
- pv.exe (PID: 1520)
- pv.exe (PID: 5708)
Reads Environment values
- pv.exe (PID: 1520)
- BiFrost 5.0.77.exe (PID: 5716)
- pv.exe (PID: 5708)
- BiFrost 5.0.77.exe (PID: 7624)
Launching a file from the Startup directory
- cmd.exe (PID: 3588)
Disables trace logs
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Checks proxy server information
- BiFrost 5.0.77.exe (PID: 5716)
- slui.exe (PID: 6148)
- BiFrost 5.0.77.exe (PID: 7624)
UPX packer has been detected
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Mpress packer has been detected
- BiFrost 5.0.77.exe (PID: 5716)
- BiFrost 5.0.77.exe (PID: 7624)
Reads product name
- pv.exe (PID: 1520)
- pv.exe (PID: 5708)
Reads the software policy settings
- slui.exe (PID: 6148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2017:12:29 12:46:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | BiFrost RAT Botnet/ |
Total processes
553
Monitored processes
419
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 304 | C:\Users\admin\AppData\Local\Temp\mespv.exe /stext C:\Users\admin\AppData\Local\Temp\mespvp.txt | C:\Users\admin\AppData\Local\Temp\mespv.exe | — | BiFrost 5.0.77.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: Instant Messengers Password Recovery Exit code: 0 Version: 1.42 Modules
| |||||||||||||||
| 416 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 592 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 592 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 632 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 640 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 684 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 728 | "C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe" | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | — | HTTP Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Test Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
6 322
Read events
6 282
Write events
27
Delete events
13
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\BiFrost RAT Botnet.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
11
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6472 | WBP.exe | C:\Users\admin\AppData\Local\Temp\bhv1690.tmp | — | |
MD5:— | SHA256:— | |||
| 8044 | WBP.exe | C:\Users\admin\AppData\Local\Temp\bhvA18.tmp | — | |
MD5:— | SHA256:— | |||
| 5716 | BiFrost 5.0.77.exe | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | executable | |
MD5:A745D03DC37AE88840C212077428B527 | SHA256:7EBB56E6ED6D25B790176320EEA4149FECEDEB18D8FABDC47012422ABA876DA8 | |||
| 2040 | WinRAR.exe | C:\Users\admin\Desktop\BiFrost RAT Botnet\BiFrost 5.0.77.exe | executable | |
MD5:F155AA9D58F8F88CD3DB47AA8D4F4107 | SHA256:71C17ADA2629067D1F47BCF5F18AEA2A0162CBF02348E00CE272C47E8AA7C35A | |||
| 6472 | WBP.exe | C:\Users\admin\AppData\Local\Temp\WBVP.txt | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 5716 | BiFrost 5.0.77.exe | C:\Users\admin\AppData\Local\Temp\WBP.exe | executable | |
MD5:6D95F03EAF83B31686F263260202EE36 | SHA256:29F2A54C829C37FC904A2B682C50B57D6D35E9AF5DC7F43D72B68C8C51255103 | |||
| 5716 | BiFrost 5.0.77.exe | C:\Users\admin\AppData\Local\Temp\mpv.exe | executable | |
MD5:A138FCA70622323E45D6018125322051 | SHA256:677D333648ABA8E2538CBBB9FDD8A32901C67A5E10C8F951970313499304783A | |||
| 5716 | BiFrost 5.0.77.exe | C:\Users\admin\AppData\Local\Temp\mespv.exe | executable | |
MD5:FFC52F2B4435FCDDACA6E15489A88B75 | SHA256:3F3C8484962B395F304A836EE5E8EE17BEAAFE982795C9747D8EE98CC6E4CA8F | |||
| 5716 | BiFrost 5.0.77.exe | C:\Users\admin\AppData\Local\Temp\pv.exe | executable | |
MD5:AFE3AEEFFAA1E1772A926CA45923F33F | SHA256:6CBC1D59FDBA6445B8E7243A08BD64816F01FCF6CE7F68570D9170E13C8810A7 | |||
| 7624 | BiFrost 5.0.77.exe | C:\Users\admin\AppData\Local\Temp\HTTP Builder.exe | executable | |
MD5:A745D03DC37AE88840C212077428B527 | SHA256:7EBB56E6ED6D25B790176320EEA4149FECEDEB18D8FABDC47012422ABA876DA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
28
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4768 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6876 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1164 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6876 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6876 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |