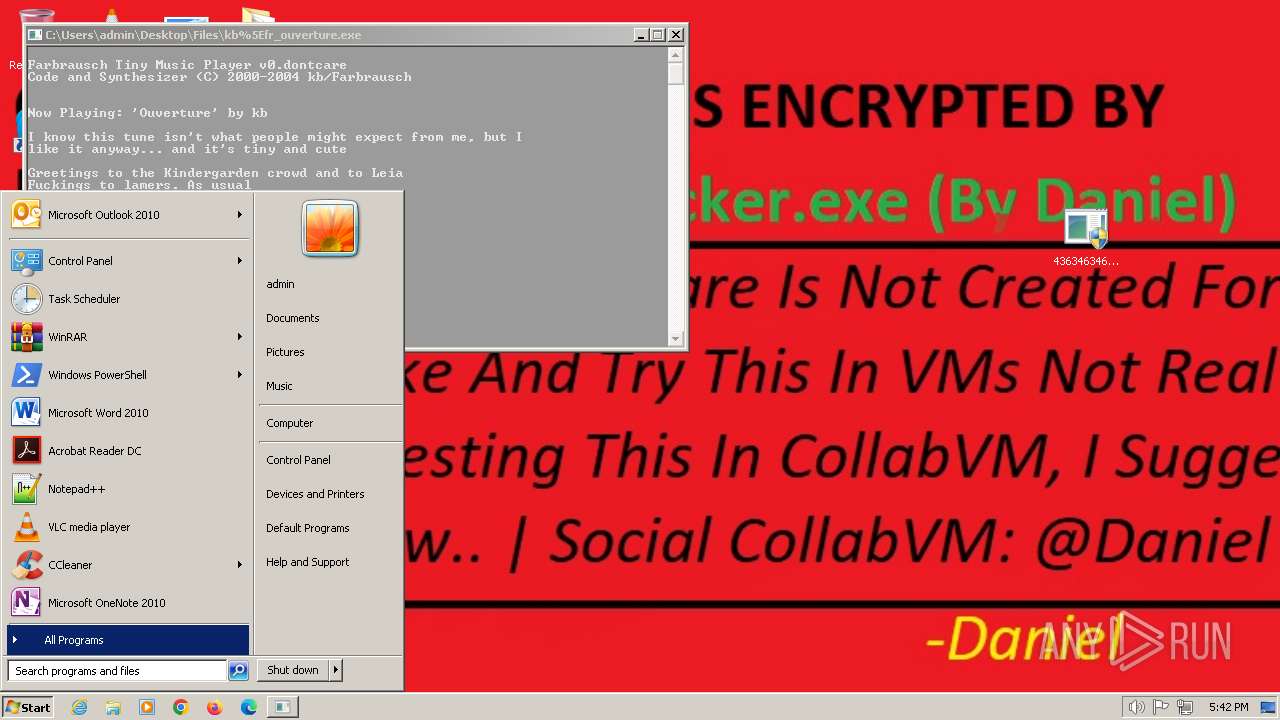
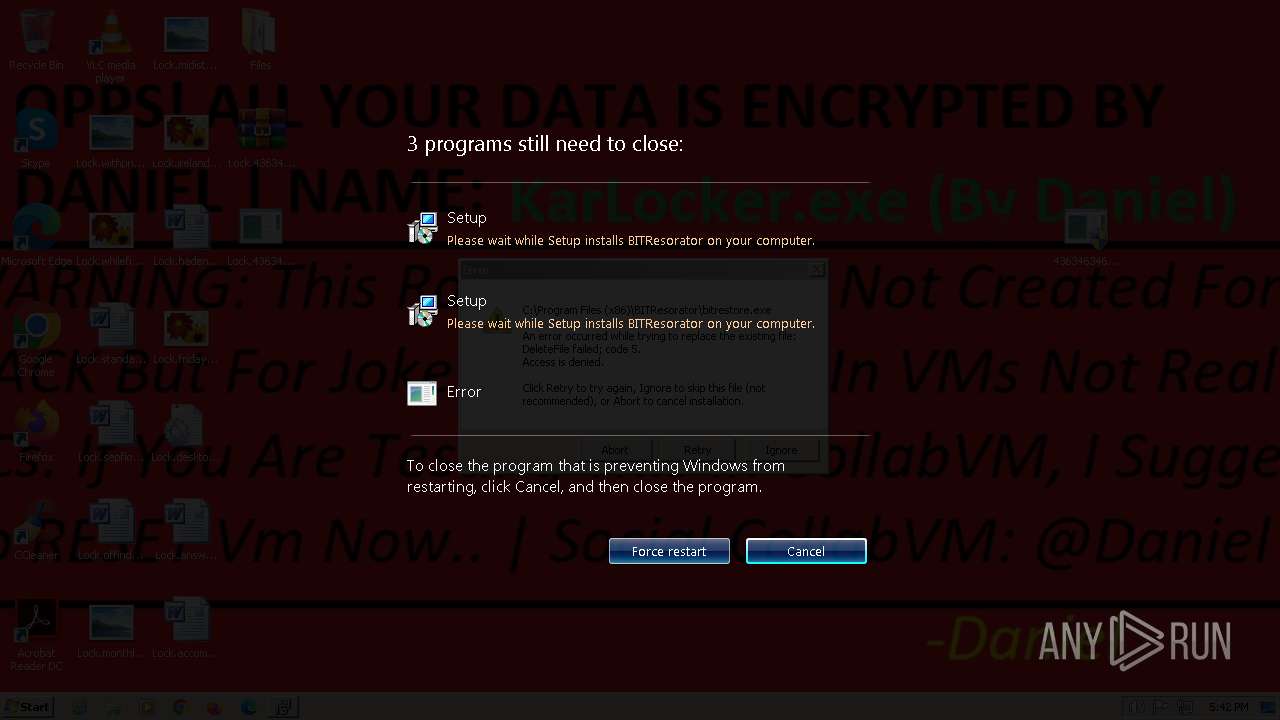
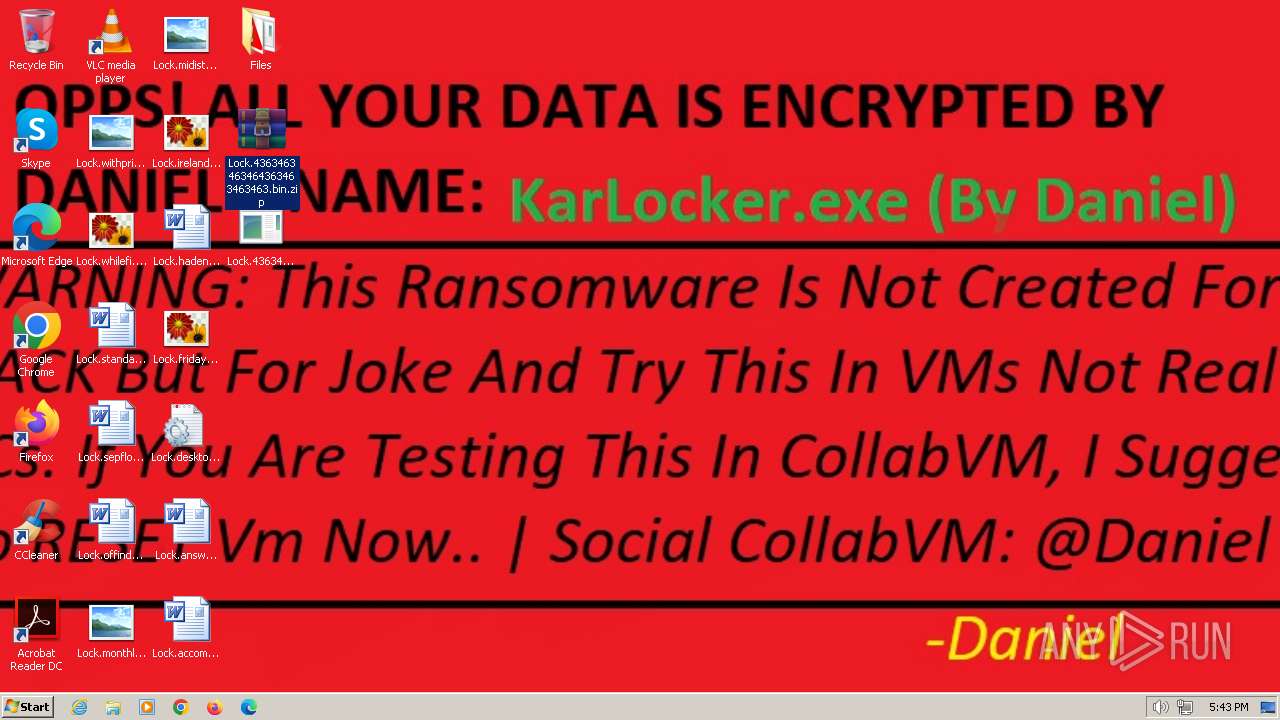
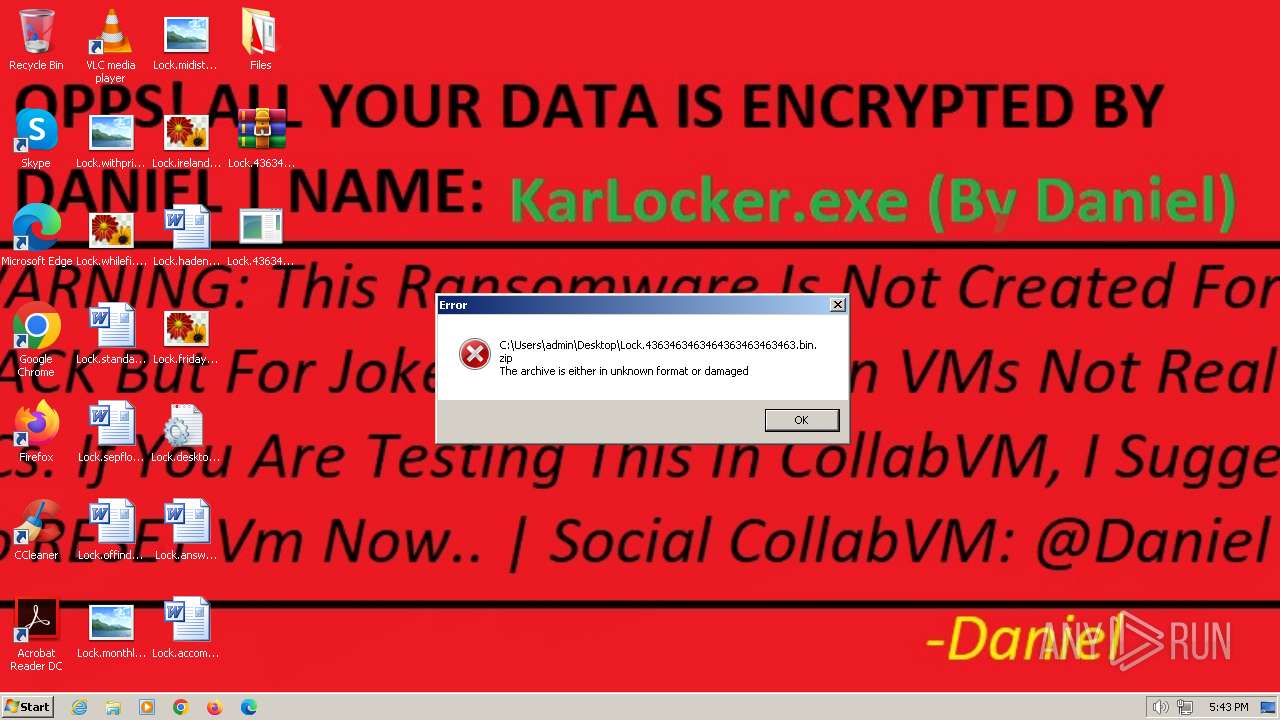
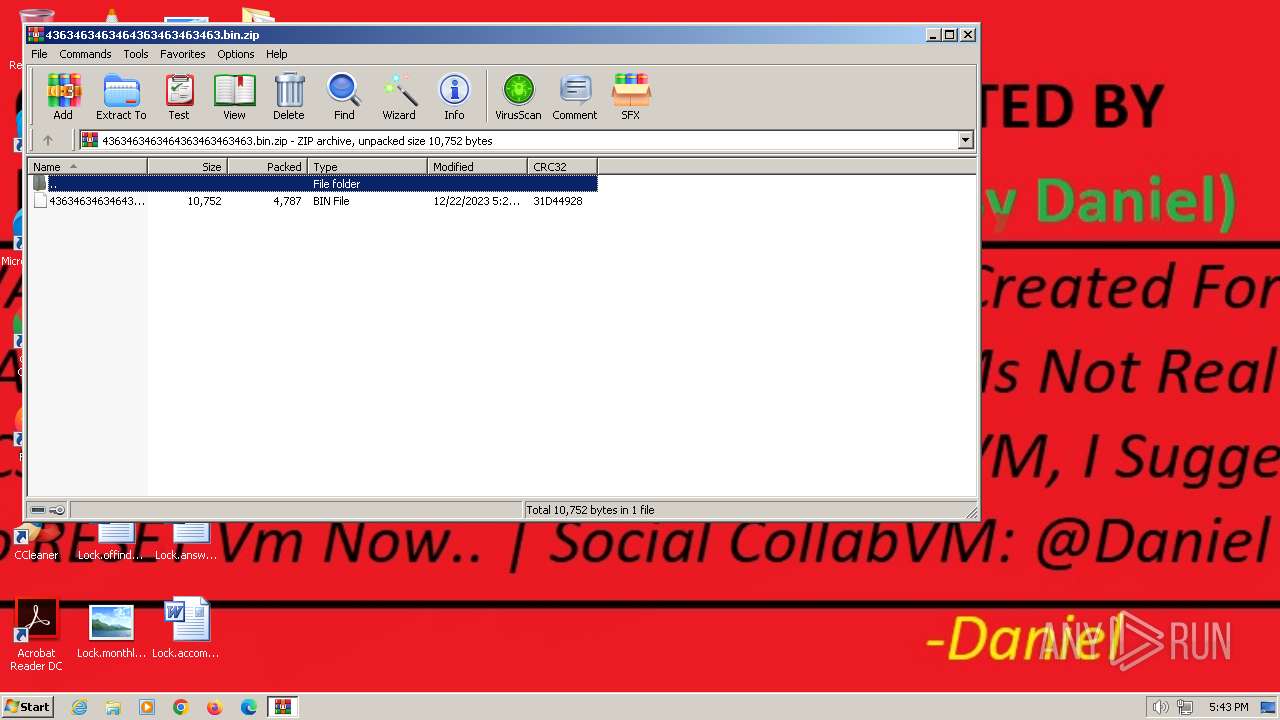
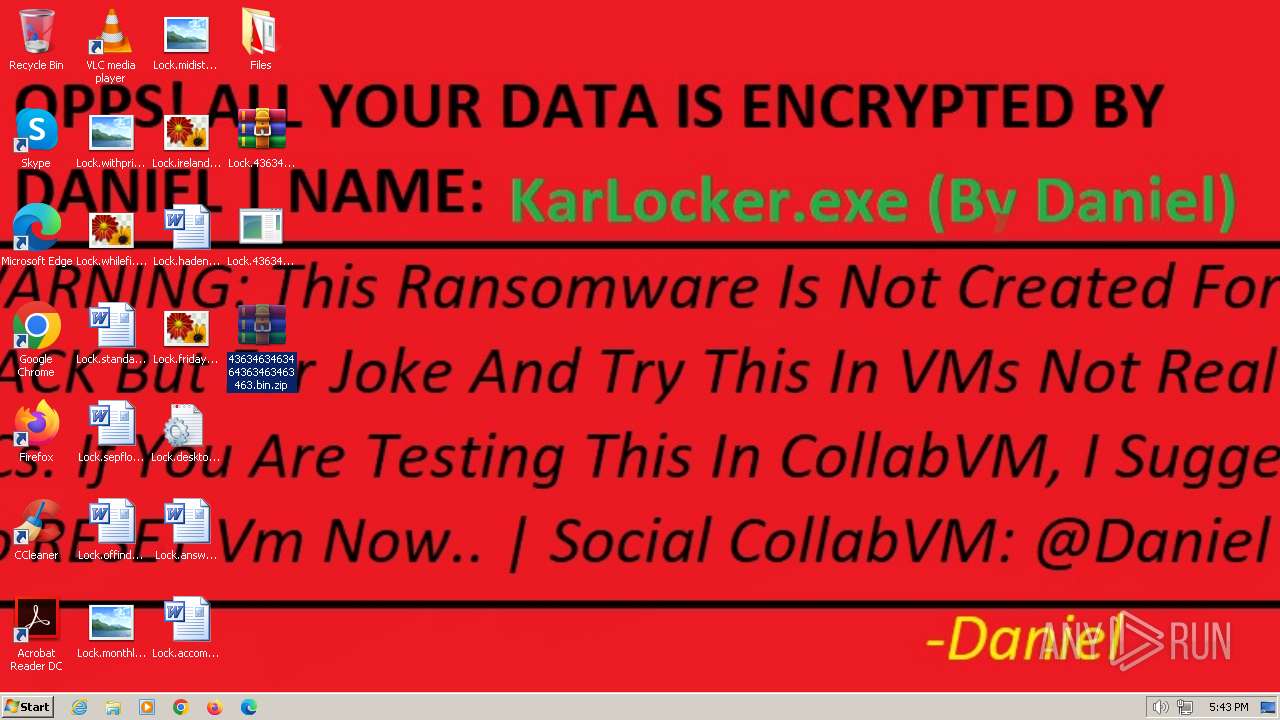
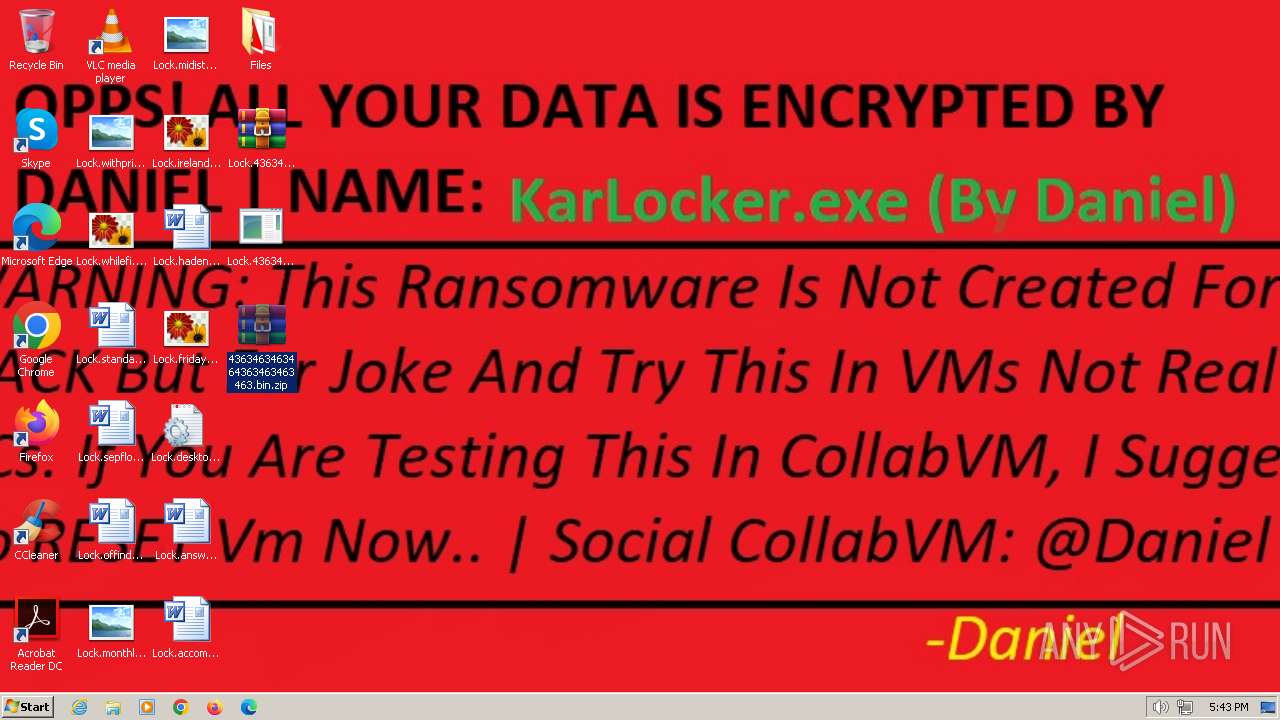
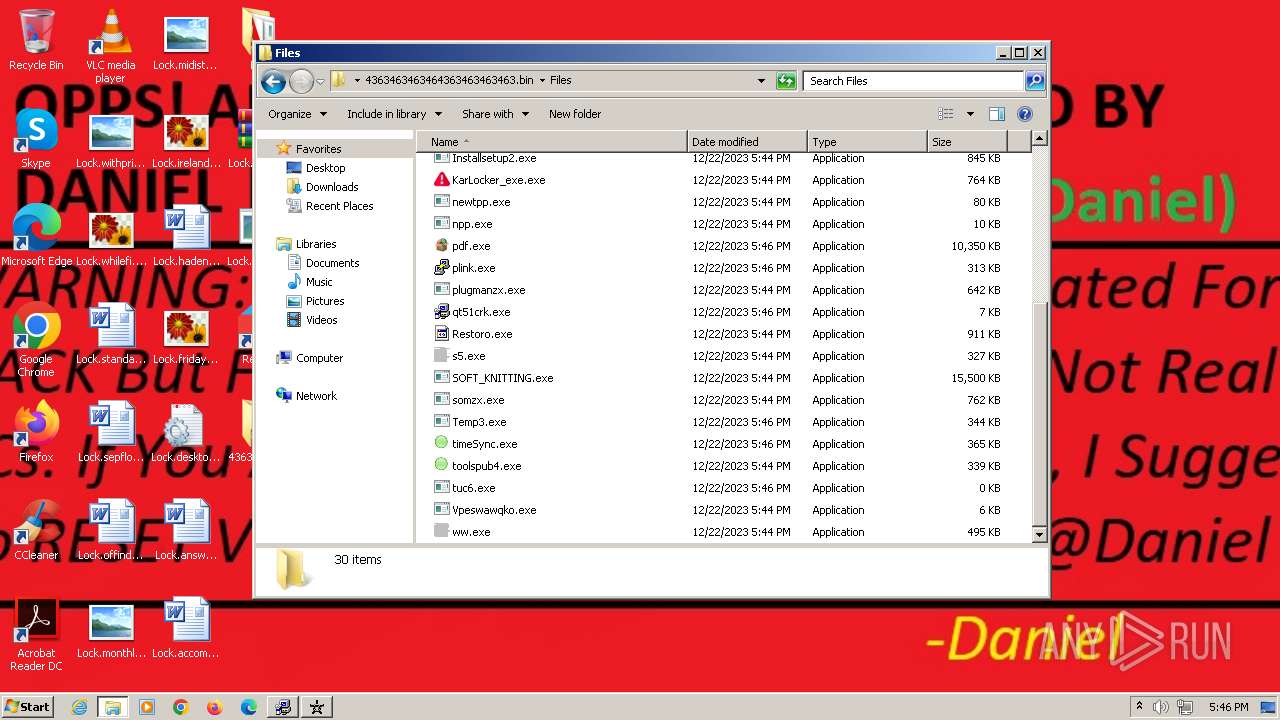
| File name: | 4363463463464363463463463.bin.zip |
| Full analysis: | https://app.any.run/tasks/e31ec095-9f04-4512-b2c4-cc3ae66d16d9 |
| Verdict: | Malicious activity |
| Threats: | The Arechclient2 malware is a sophisticated .NET-based Remote Access Trojan (RAT) that collects sensitive information, such as browser credentials, from infected computers. It employs various stealth techniques, including Base64 encoding to obscure its code and the ability to pause activities to evade automated security tools. The malware also can adjust Windows Defender settings and uses code injection to manipulate legitimate processes. |
| Analysis date: | December 22, 2023, 17:40:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | AC0143F688CAF564859D33C55E8330A5 |
| SHA1: | 9DDEDD45AABB7E710CFC250D31F99A0444FF2A66 |
| SHA256: | 7242F661D5DAF0648CE62C2768687114A32386DFE48E7806590B5C43EEA35175 |
| SSDEEP: | 96:yooGS2uJx8Kxnl5oeAvgn8QgyF9oKXBINJZDV5BA8N5teIKQ5OSdSqfGJLVW+Hln:/63nl+e3eNJz7B5f5Dd7aHlMi2U |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.bin.exe (PID: 2992)
LUMMA has been detected (SURICATA)
- lumtru.exe (PID: 2272)
Connects to the CnC server
- lumtru.exe (PID: 2272)
- lve5.exe (PID: 284)
- explorer.exe (PID: 2004)
- explorer.exe (PID: 1428)
- Vnloubk.exe (PID: 2140)
- Restoro.exe (PID: 2580)
- RegAsm.exe (PID: 2920)
- sysplorsv.exe (PID: 3064)
- nsnDE38.tmp.exe (PID: 3660)
- RestoroSetup.exe (PID: 2568)
- Vnloubk.exe (PID: 1692)
- sysplorsv.exe (PID: 2992)
- explorer.exe (PID: 2120)
- timeSync.exe (PID: 2832)
- powershell.exe (PID: 2736)
- sylsplvc.exe (PID: 3420)
PURPLEFOX has been detected (SURICATA)
- lve5.exe (PID: 284)
- Vnloubk.exe (PID: 2140)
- Vnloubk.exe (PID: 1692)
Actions looks like stealing of personal data
- lumtru.exe (PID: 2272)
- dllhost.exe (PID: 1268)
- sqlite3.exe (PID: 2508)
- sqlite3.exe (PID: 2536)
- sqlite3.exe (PID: 2688)
- Restoro.exe (PID: 2580)
- 1701610814-Dvnzfr.exe (PID: 920)
- sqlite3.exe (PID: 3004)
- fcc.exe (PID: 1380)
- RegAsm.exe (PID: 2920)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- vbc.exe (PID: 2832)
Changes the autorun value in the registry
- wsus.exe (PID: 3024)
- wsus.exe (PID: 2004)
- wsus.exe (PID: 2780)
- Windows Sessions Pause.exe (PID: 2360)
- 1226721741.exe (PID: 3400)
ASYNCRAT has been detected (YARA)
- svchost1.exe (PID: 2948)
REMCOS has been detected (YARA)
- wsus.exe (PID: 3024)
NITOL has been detected (YARA)
- lve5.exe (PID: 284)
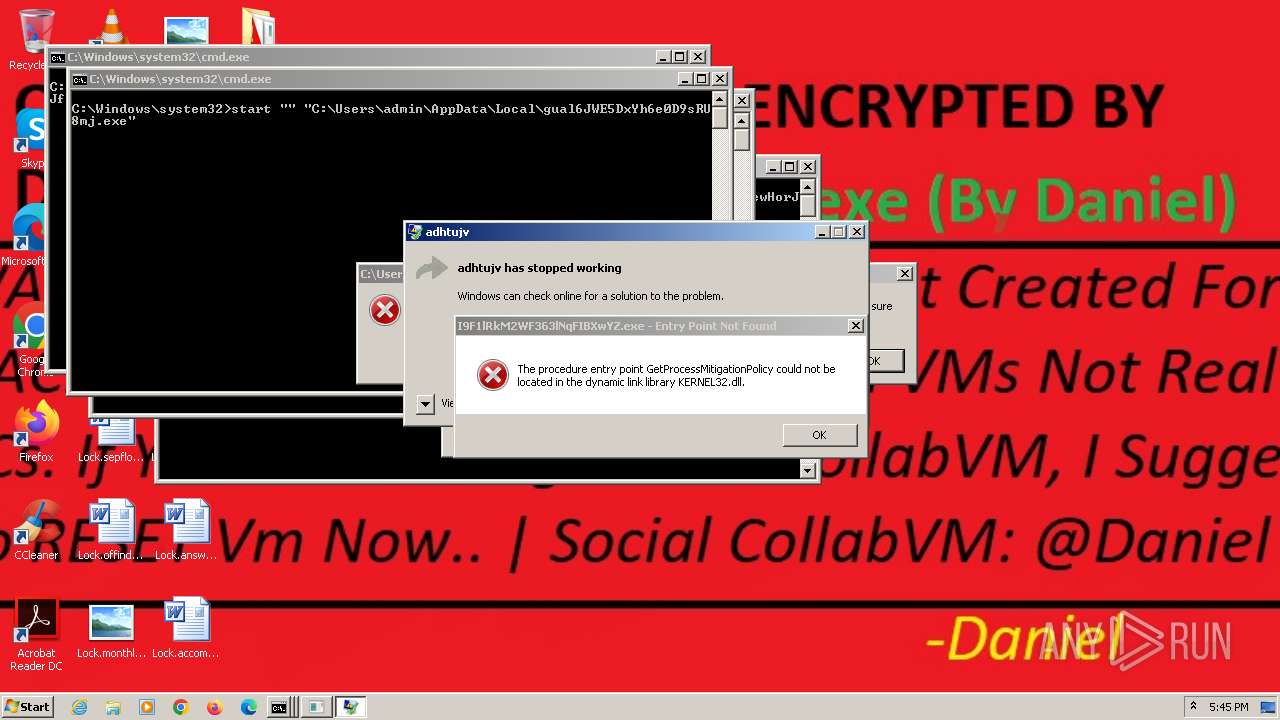
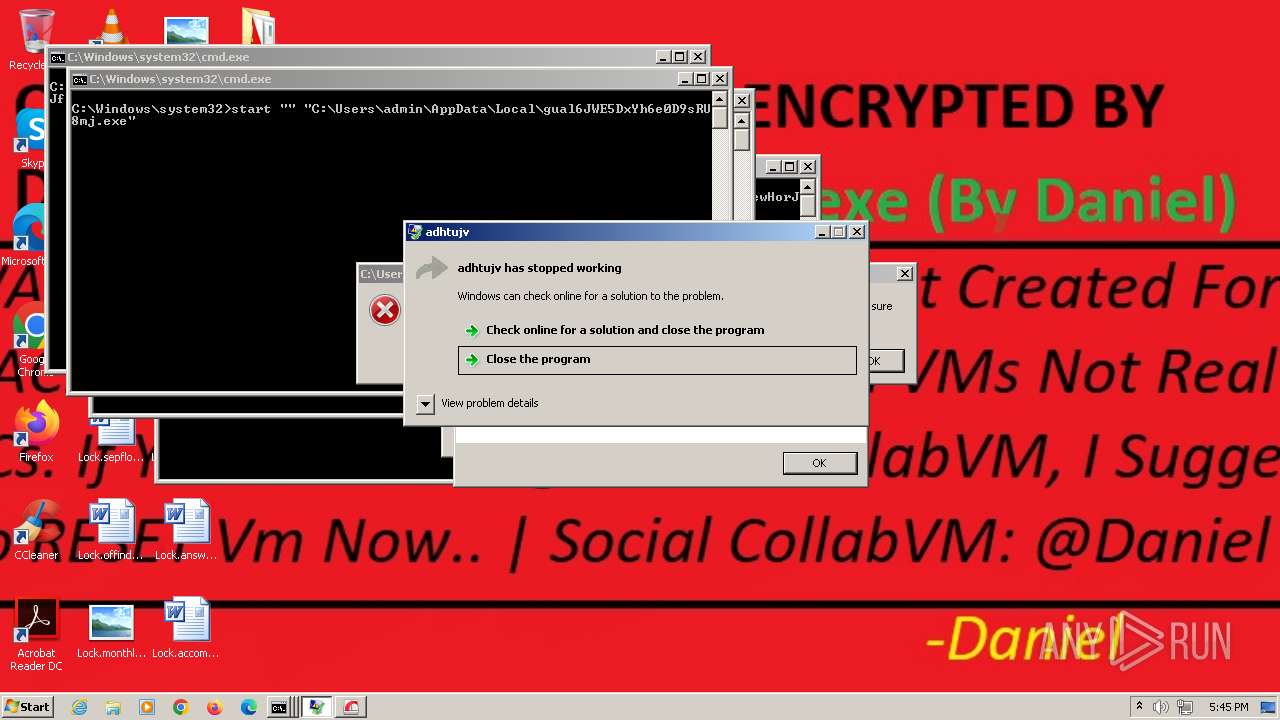
Runs injected code in another process
- cb0e88abe7aee128ff8635e44df9797d0224aff000d03fc5d9166e575b50f4a1.exe (PID: 2680)
- adhtujv (PID: 1520)
- evhtujv (PID: 1984)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 2252)
Adds path to the Windows Defender exclusion list
- more.exe (PID: 1932)
- images.exe (PID: 1624)
- ghoul.exe (PID: 2680)
- Installsetup2.exe (PID: 2828)
- images.exe (PID: 664)
- UiKVWpFsayx.exe (PID: 1708)
Uses Task Scheduler to run other applications
- more.exe (PID: 1932)
- UiKVWpFsayx.exe (PID: 1548)
- images.exe (PID: 1624)
- cmd.exe (PID: 2132)
- RestoroSetup.exe (PID: 2568)
- images.exe (PID: 664)
- UiKVWpFsayx.exe (PID: 1708)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 2444)
- Temp3.exe (PID: 2624)
- Windows Security Client.exe (PID: 2052)
SERVSTART has been detected (SURICATA)
- DNS1.exe (PID: 2148)
DUPZOM has been detected (SURICATA)
- DNS1.exe (PID: 2148)
Create files in the Startup directory
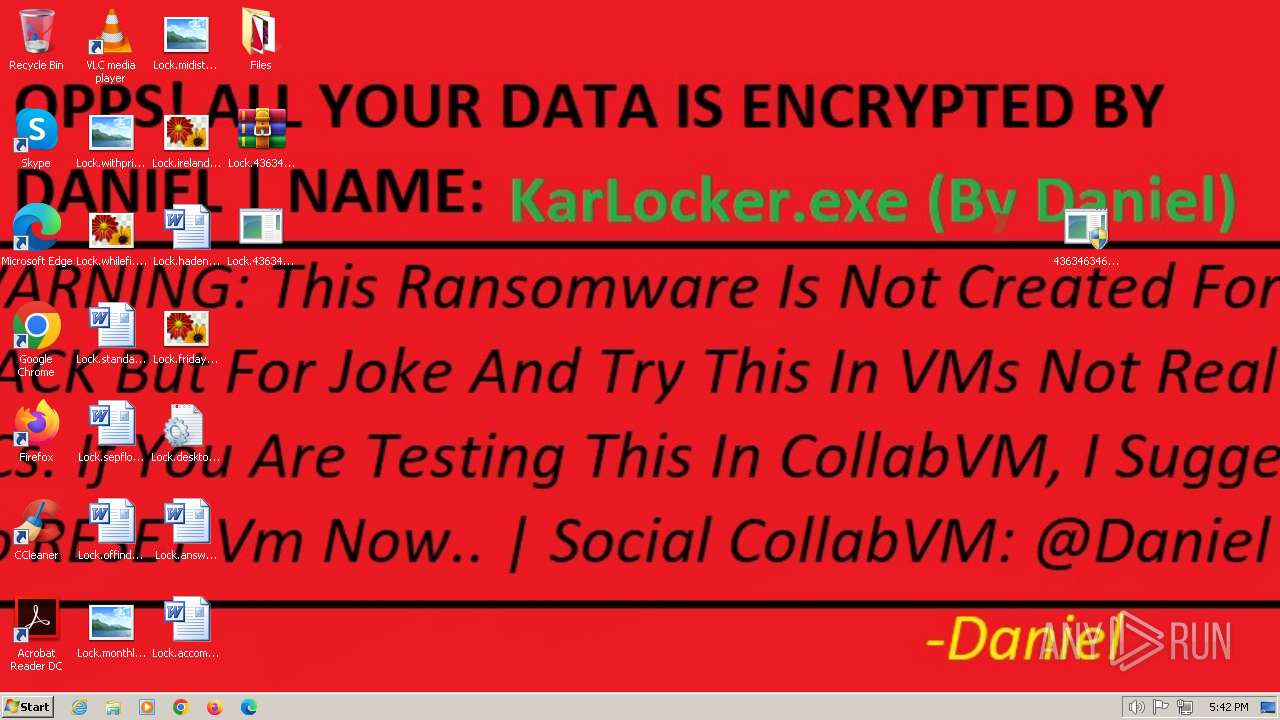
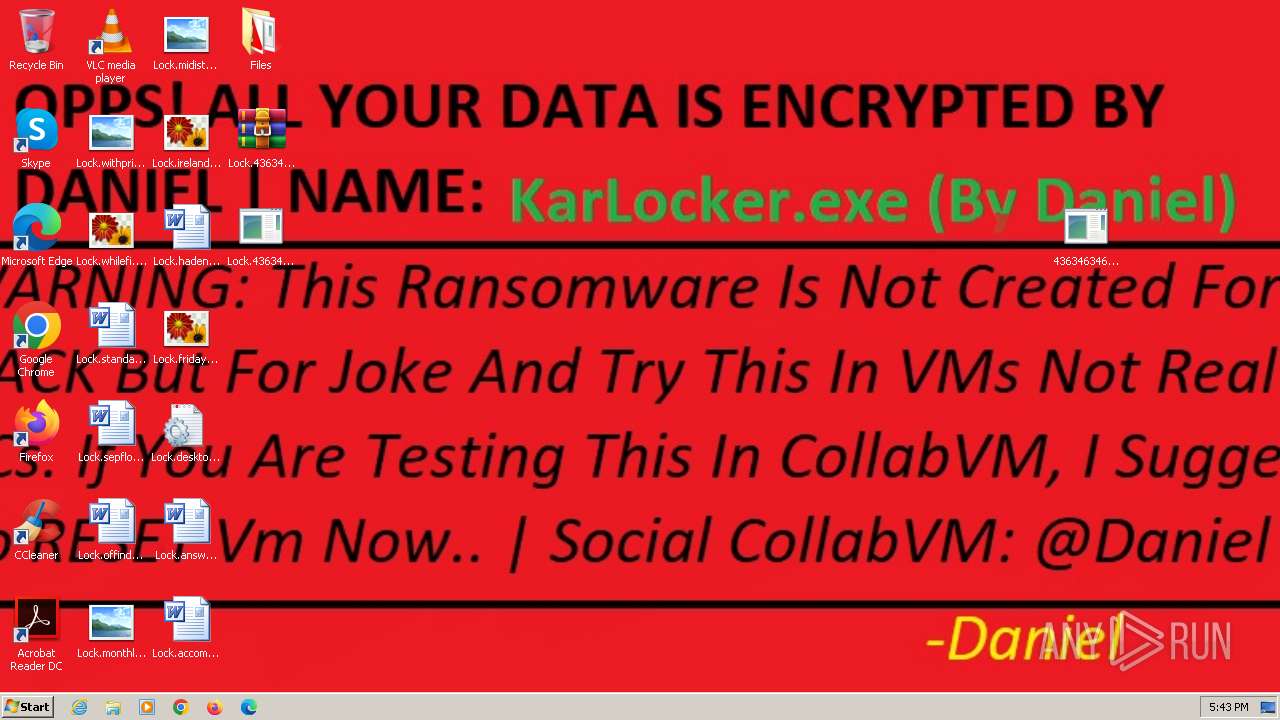
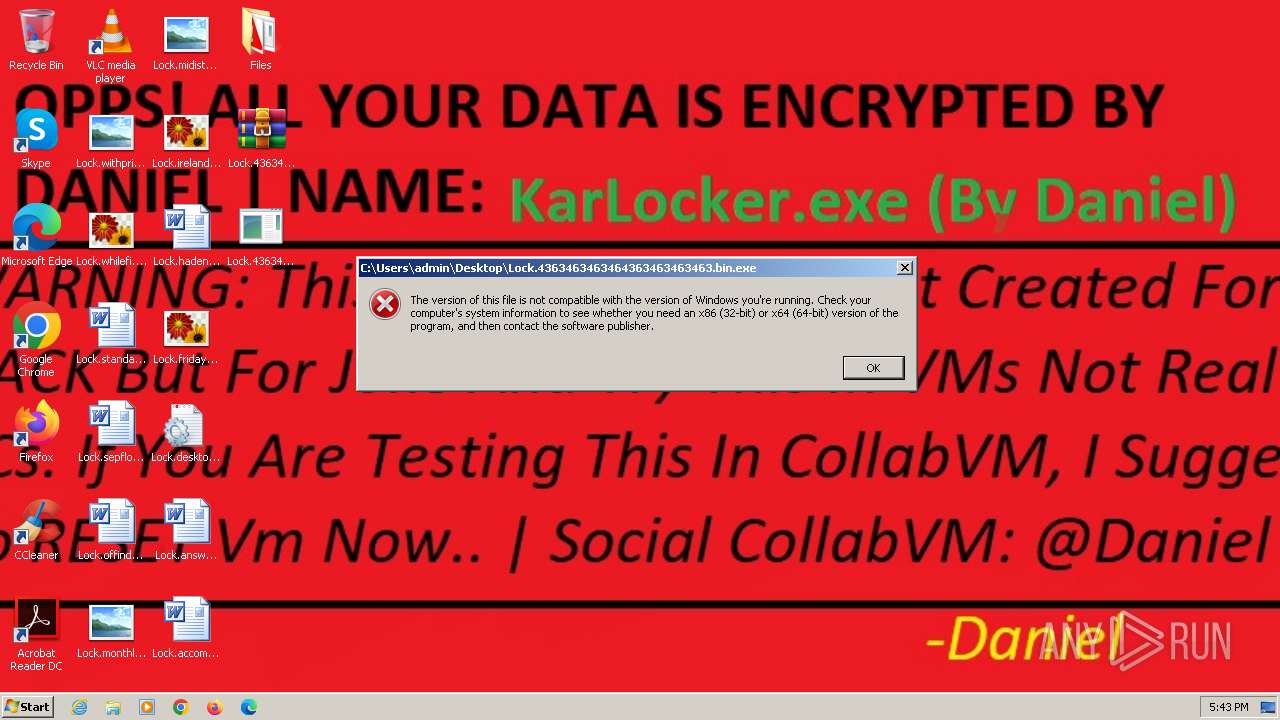
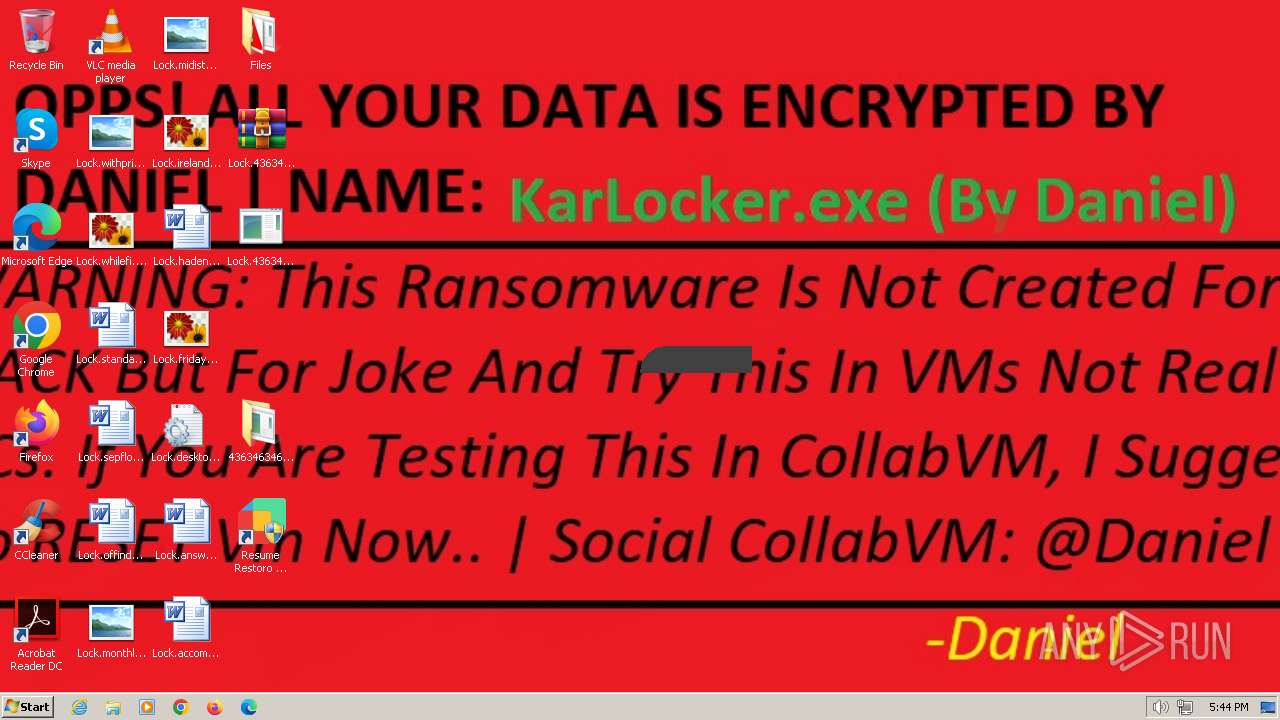
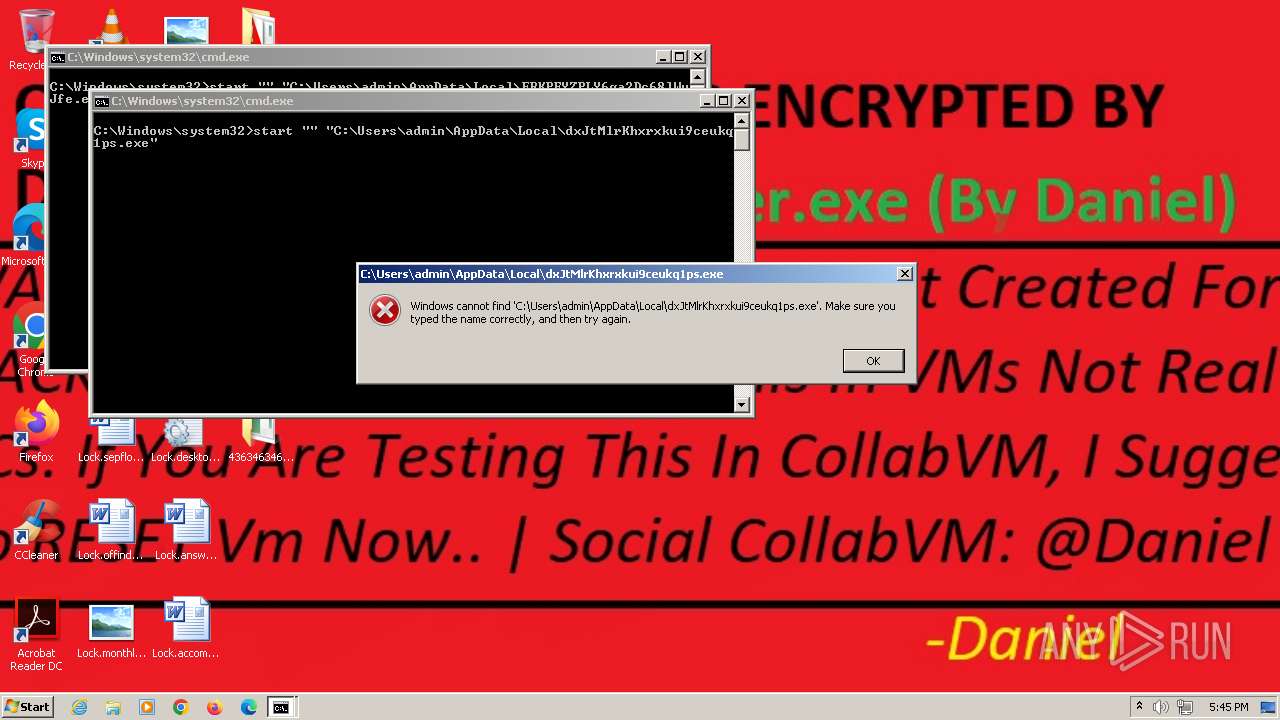
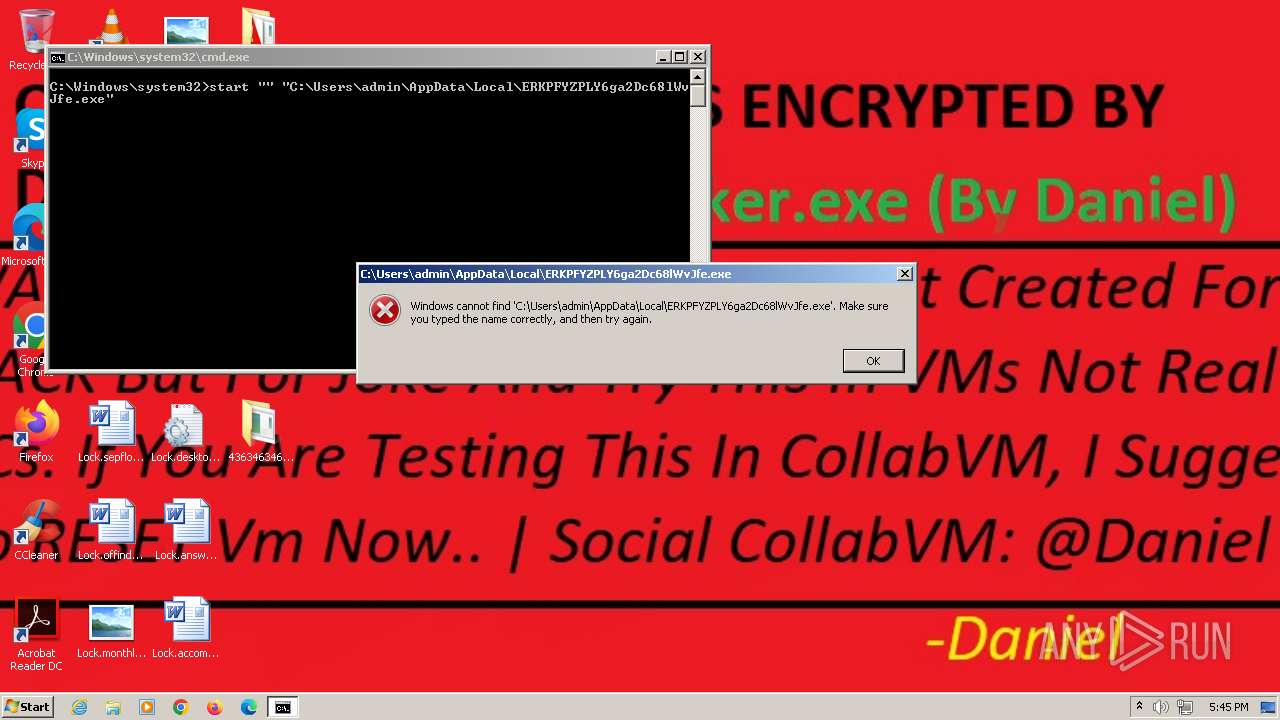
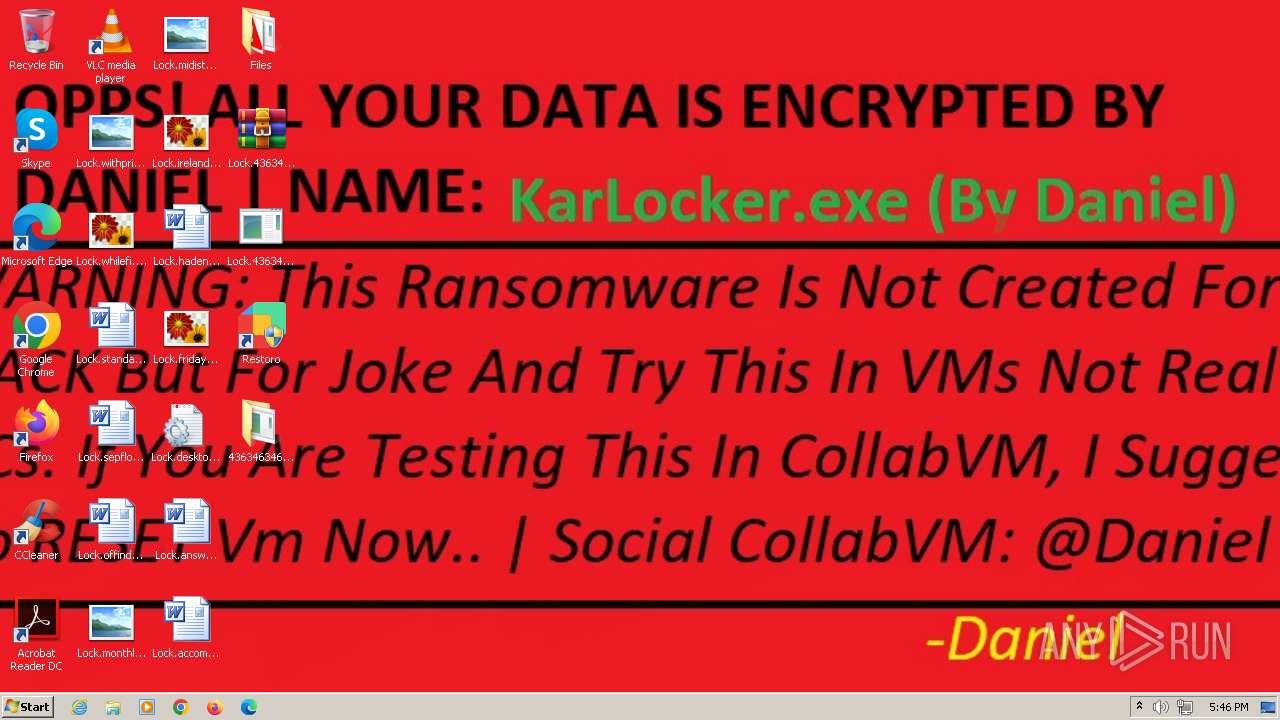
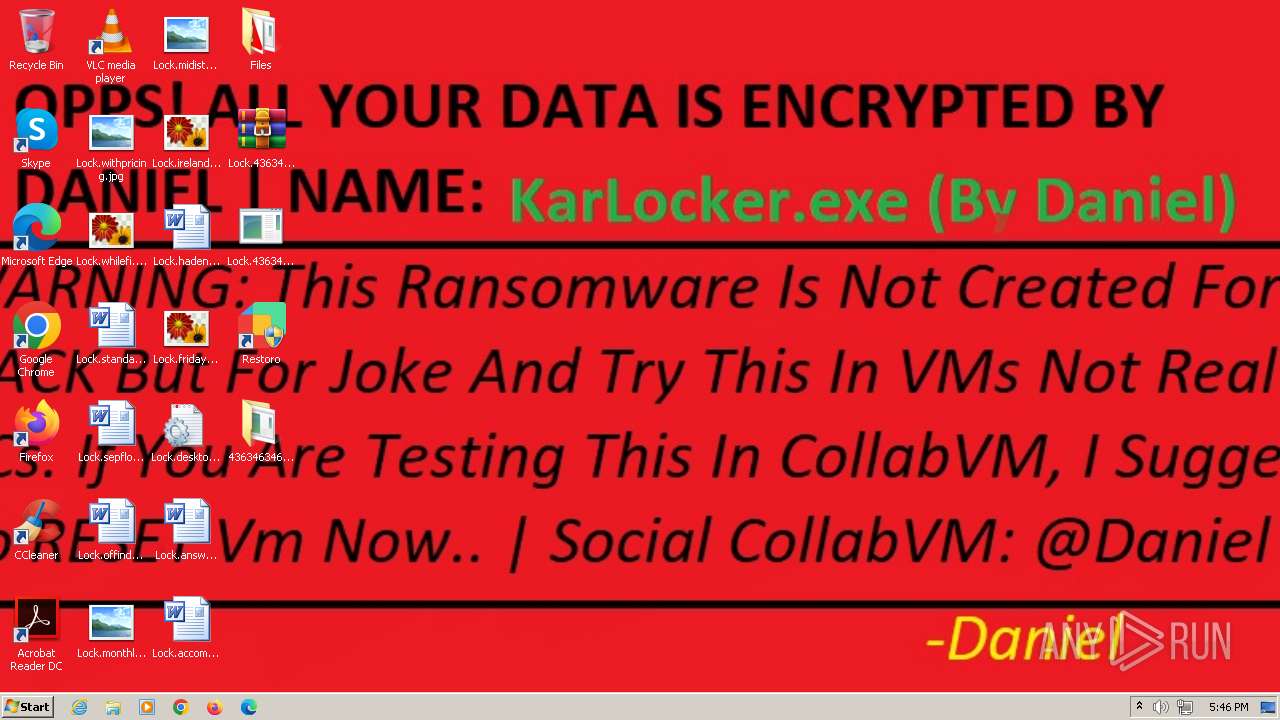
- KarLocker_exe.exe (PID: 2256)
- InstallUtil.exe (PID: 920)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 2004)
- explorer.exe (PID: 1428)
- explorer.exe (PID: 2120)
REDOSDRU has been detected (YARA)
- Ulpktkx.exe (PID: 1436)
Remcos is detected
- wsus.exe (PID: 2004)
- wsus.exe (PID: 2780)
Creates a writable file in the system directory
- Vnloubk.exe (PID: 2140)
- Temp3.exe (PID: 2624)
Steals credentials from Web Browsers
- Restoro.exe (PID: 2580)
- vbc.exe (PID: 2832)
Registers / Runs the DLL via REGSVR32.EXE
- Restoro.exe (PID: 2580)
- RestoroSetup.exe (PID: 2568)
Deletes a file (SCRIPT)
- wscript.exe (PID: 2240)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 2240)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2240)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2240)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 2240)
UAC/LUA settings modification
- Installsetup2.exe (PID: 2828)
Unusual connection from system programs
- wscript.exe (PID: 2240)
- vbc.exe (PID: 1764)
- vbc.exe (PID: 1192)
- vbc.exe (PID: 2832)
ARECHCLIENT2 has been detected (SURICATA)
- RegAsm.exe (PID: 2920)
PHORPIEX has been detected (SURICATA)
- sysplorsv.exe (PID: 3064)
- sysplorsv.exe (PID: 2992)
- sylsplvc.exe (PID: 3420)
GCLEANER has been detected (SURICATA)
- s5.exe (PID: 3148)
STEALC has been detected (SURICATA)
- nsnDE38.tmp.exe (PID: 3660)
- timeSync.exe (PID: 2832)
Changes Security Center notification settings
- sysplorsv.exe (PID: 2992)
- sylsplvc.exe (PID: 3420)
REDLINE has been detected (SURICATA)
- vbc.exe (PID: 2832)
Starts CMD.EXE for self-deleting
- file.exe (PID: 1488)
DOINA has been detected (SURICATA)
- powershell.exe (PID: 2736)
SUSPICIOUS
Reads the Internet Settings
- 4363463463464363463463463.bin.exe (PID: 2992)
- WPS_Setup.exe (PID: 1176)
- more.exe (PID: 1932)
- irsetup.exe (PID: 2420)
- svchost1.exe (PID: 2948)
- wsuscr.exe (PID: 2328)
- VLTKBacdau.exe (PID: 2336)
- more.exe (PID: 1420)
- images.exe (PID: 1412)
- DNS1.exe (PID: 2148)
- images.exe (PID: 1624)
- UiKVWpFsayx.exe (PID: 1548)
- 4363463463464363463463463.bin.exe (PID: 1940)
- Restoro.exe (PID: 2580)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 2708)
- 1230.exe (PID: 1948)
- Vpeswawqko.exe (PID: 2452)
- powershell.exe (PID: 3012)
- DNS2.exe (PID: 1884)
- npp.exe (PID: 2112)
- ghoul.exe (PID: 2680)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 1060)
- InstallUtil.exe (PID: 920)
- Installsetup2.exe (PID: 2828)
- sysplorsv.exe (PID: 3064)
- chungzx.exe (PID: 2180)
- chungzx.exe (PID: 3080)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- s5.exe (PID: 3148)
- nsnDE38.tmp.exe (PID: 3660)
- RestoroUpdater.exe (PID: 3788)
- plugmanzx.exe (PID: 2372)
- RestoroSetup.exe (PID: 2568)
- images.exe (PID: 664)
- sysplorsv.exe (PID: 2992)
- UiKVWpFsayx.exe (PID: 1708)
- 4363463463464363463463463.bin.exe (PID: 2404)
- Windows Sessions Pause.exe (PID: 2308)
- Windows Sessions Pause.exe (PID: 3048)
- timeSync.exe (PID: 2832)
- file.exe (PID: 1488)
- plink.exe (PID: 2912)
- powershell.exe (PID: 2736)
- Temp3.exe (PID: 2624)
- Windows Security Client.exe (PID: 2052)
- sylsplvc.exe (PID: 3420)
Reads settings of System Certificates
- 4363463463464363463463463.bin.exe (PID: 2992)
- 4363463463464363463463463.bin.exe (PID: 1940)
- Vpeswawqko.exe (PID: 2452)
- InstallUtil.exe (PID: 920)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- 4363463463464363463463463.bin.exe (PID: 2404)
- file.exe (PID: 1488)
Adds/modifies Windows certificates
- 4363463463464363463463463.bin.exe (PID: 2992)
- 4363463463464363463463463.bin.exe (PID: 1940)
Process requests binary or script from the Internet
- 4363463463464363463463463.bin.exe (PID: 2992)
- DNS1.exe (PID: 2148)
- 4363463463464363463463463.bin.exe (PID: 1940)
- Restoro.exe (PID: 2580)
- npp.exe (PID: 2112)
- InstallUtil.exe (PID: 920)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- 4363463463464363463463463.bin.exe (PID: 2404)
Connects to the server without a host name
- 4363463463464363463463463.bin.exe (PID: 2992)
- svchost1.exe (PID: 2948)
- 4363463463464363463463463.bin.exe (PID: 1940)
- InstallUtil.exe (PID: 920)
- sysplorsv.exe (PID: 3064)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- nsnDE38.tmp.exe (PID: 3660)
- s5.exe (PID: 3148)
- sysplorsv.exe (PID: 2992)
- 4363463463464363463463463.bin.exe (PID: 2404)
- timeSync.exe (PID: 2832)
- powershell.exe (PID: 2736)
- sylsplvc.exe (PID: 3420)
Reads the Windows owner or organization settings
- irsetup.exe (PID: 2420)
- iusb3mon.exe (PID: 1268)
- tuc6.tmp (PID: 1036)
- Cheat.tmp (PID: 2900)
- tuc2.tmp (PID: 2552)
- tuc6.tmp (PID: 2856)
Connects to unusual port
- reverse.exe (PID: 2900)
- 4363463463464363463463463.bin.exe (PID: 2992)
- lve5.exe (PID: 284)
- svchost1.exe (PID: 2948)
- VLTKBacdau.exe (PID: 2336)
- dialer.exe (PID: 2252)
- dllhost.exe (PID: 1268)
- DNS1.exe (PID: 2148)
- Ulpktkx.exe (PID: 1436)
- wsus.exe (PID: 3024)
- RegSvcs.exe (PID: 2420)
- Ulpktkx.exe (PID: 1864)
- Vnloubk.exe (PID: 2140)
- wsus.exe (PID: 2004)
- SOFT_KNITTING.exe (PID: 2684)
- images.exe (PID: 2648)
- 4363463463464363463463463.bin.exe (PID: 1940)
- vbc.exe (PID: 1764)
- fcc.exe (PID: 1380)
- vbc.exe (PID: 1192)
- RegAsm.exe (PID: 2920)
- dialer.exe (PID: 280)
- sysplorsv.exe (PID: 3064)
- Vnloubk.exe (PID: 1692)
- Ulpktkx.exe (PID: 2816)
- sysplorsv.exe (PID: 2992)
- 4363463463464363463463463.bin.exe (PID: 2404)
- vbc.exe (PID: 2832)
- Windows Security Client.exe (PID: 2052)
- wsus.exe (PID: 2780)
- images.exe (PID: 3140)
- sylsplvc.exe (PID: 3420)
Creates or modifies Windows services
- lve5.exe (PID: 284)
- Vnloubk.exe (PID: 2140)
- Vnloubk.exe (PID: 1692)
Reads browser cookies
- lumtru.exe (PID: 2272)
- sqlite3.exe (PID: 2508)
- RegAsm.exe (PID: 2920)
- vbc.exe (PID: 2832)
Searches for installed software
- lumtru.exe (PID: 2272)
- dllhost.exe (PID: 1268)
- tuc2.tmp (PID: 2552)
- RestoroSetup.exe (PID: 2568)
- RegAsm.exe (PID: 2920)
- vbc.exe (PID: 2832)
- tuc6.tmp (PID: 2856)
Connects to FTP
- VLTKBacdau.exe (PID: 2336)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 2252)
- dialer.exe (PID: 280)
Script adds exclusion path to Windows Defender
- more.exe (PID: 1932)
- images.exe (PID: 1624)
- ghoul.exe (PID: 2680)
- Installsetup2.exe (PID: 2828)
- UiKVWpFsayx.exe (PID: 1708)
- images.exe (PID: 664)
Starts POWERSHELL.EXE for commands execution
- more.exe (PID: 1932)
- images.exe (PID: 1624)
- ghoul.exe (PID: 2680)
- Installsetup2.exe (PID: 2828)
- cmd.exe (PID: 3012)
- UiKVWpFsayx.exe (PID: 1708)
- images.exe (PID: 664)
Accesses Microsoft Outlook profiles
- dllhost.exe (PID: 1268)
Loads DLL from Mozilla Firefox
- dllhost.exe (PID: 1268)
Executing commands from a ".bat" file
- more.exe (PID: 1420)
- Restoro.exe (PID: 2580)
- chungzx.exe (PID: 3080)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2492)
Write to the desktop.ini file (may be used to cloak folders)
- KarLocker_exe.exe (PID: 2256)
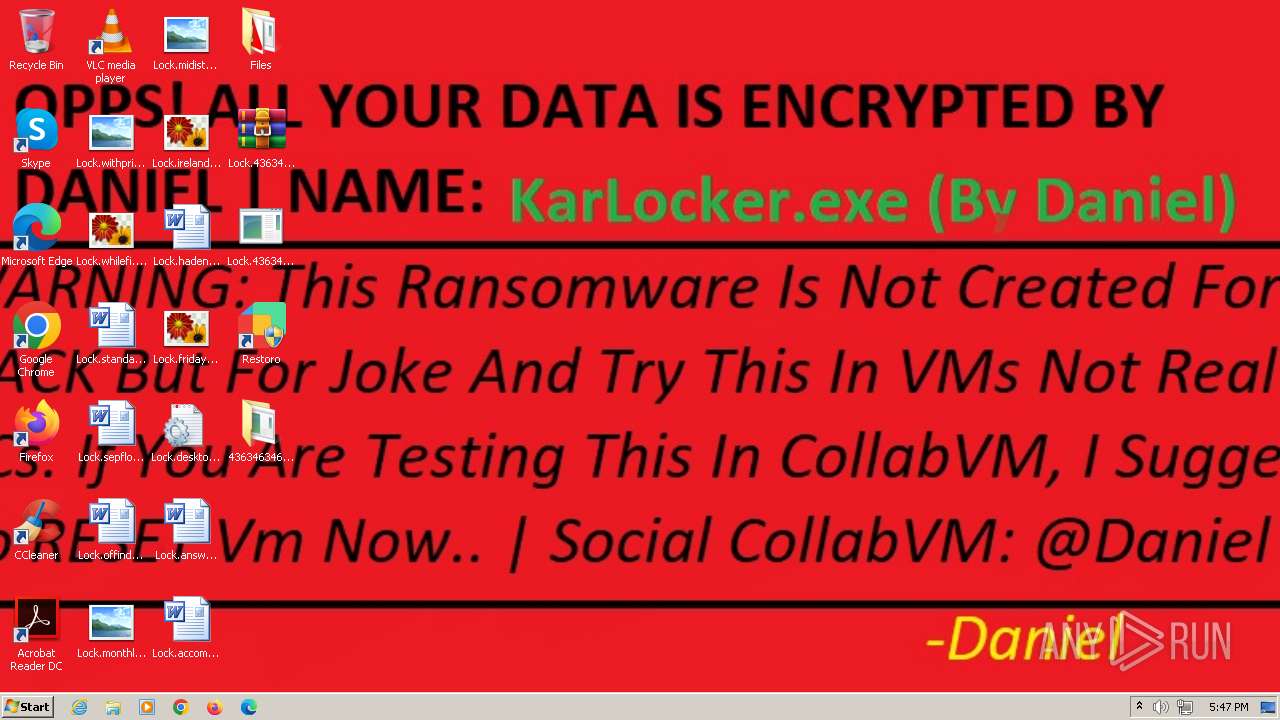
Changes the desktop background image
- KarLocker_exe.exe (PID: 2256)
- x.exe (PID: 1720)
- KarLocker_exe.exe (PID: 2428)
- x.exe (PID: 2496)
Starts CMD.EXE for commands execution
- liveupdate.exe (PID: 972)
- more.exe (PID: 1420)
- Restoro.exe (PID: 2580)
- RestoroSetup.exe (PID: 2568)
- ghoul.exe (PID: 2680)
- fcc.exe (PID: 1380)
- chungzx.exe (PID: 3080)
- RestoroUpdater.exe (PID: 3788)
- file.exe (PID: 1488)
The process creates files with name similar to system file names
- Restoro.exe (PID: 2580)
- RestoroSetup.exe (PID: 2568)
- RestoroUpdater.exe (PID: 3788)
Get information on the list of running processes
- cmd.exe (PID: 2960)
- Restoro.exe (PID: 2580)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 2120)
- cmd.exe (PID: 2188)
- cmd.exe (PID: 3056)
- cmd.exe (PID: 340)
- cmd.exe (PID: 1908)
- cmd.exe (PID: 2208)
- cmd.exe (PID: 2700)
- RestoroSetup.exe (PID: 2568)
- cmd.exe (PID: 2556)
- cmd.exe (PID: 3544)
- RestoroUpdater.exe (PID: 3788)
- cmd.exe (PID: 3840)
The process executes VB scripts
- DNS2.exe (PID: 1884)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 1060)
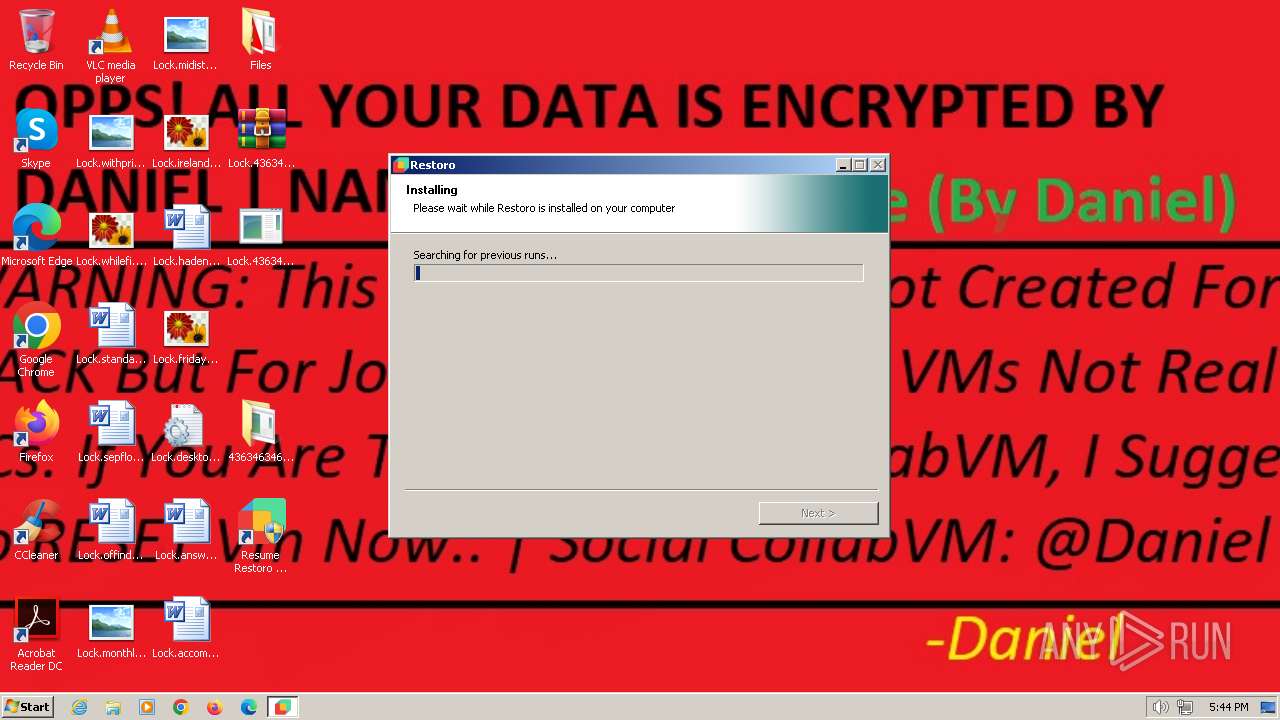
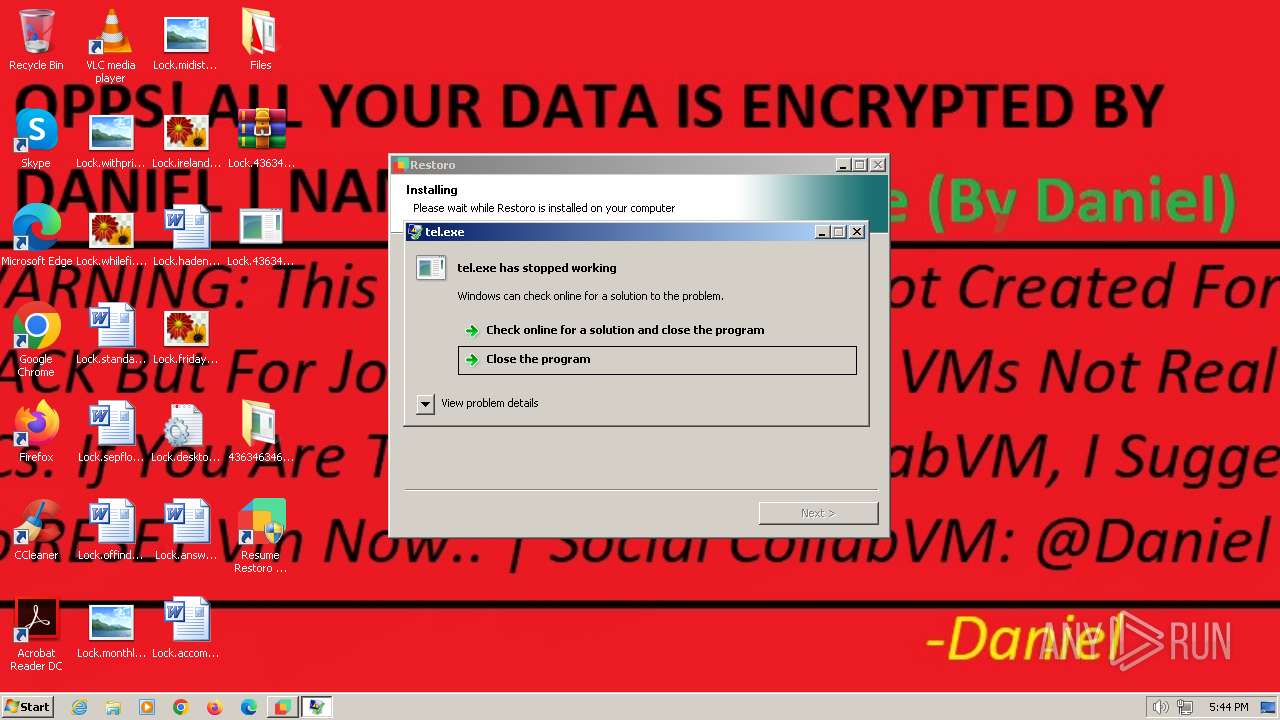
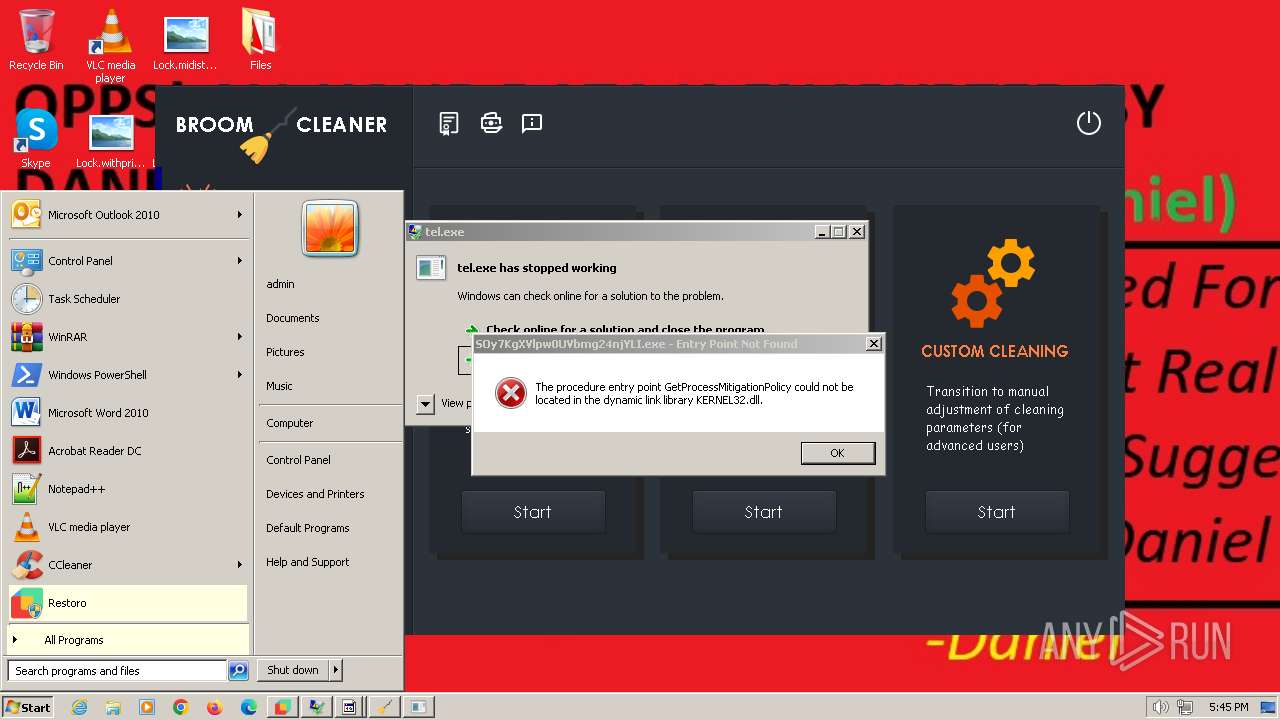
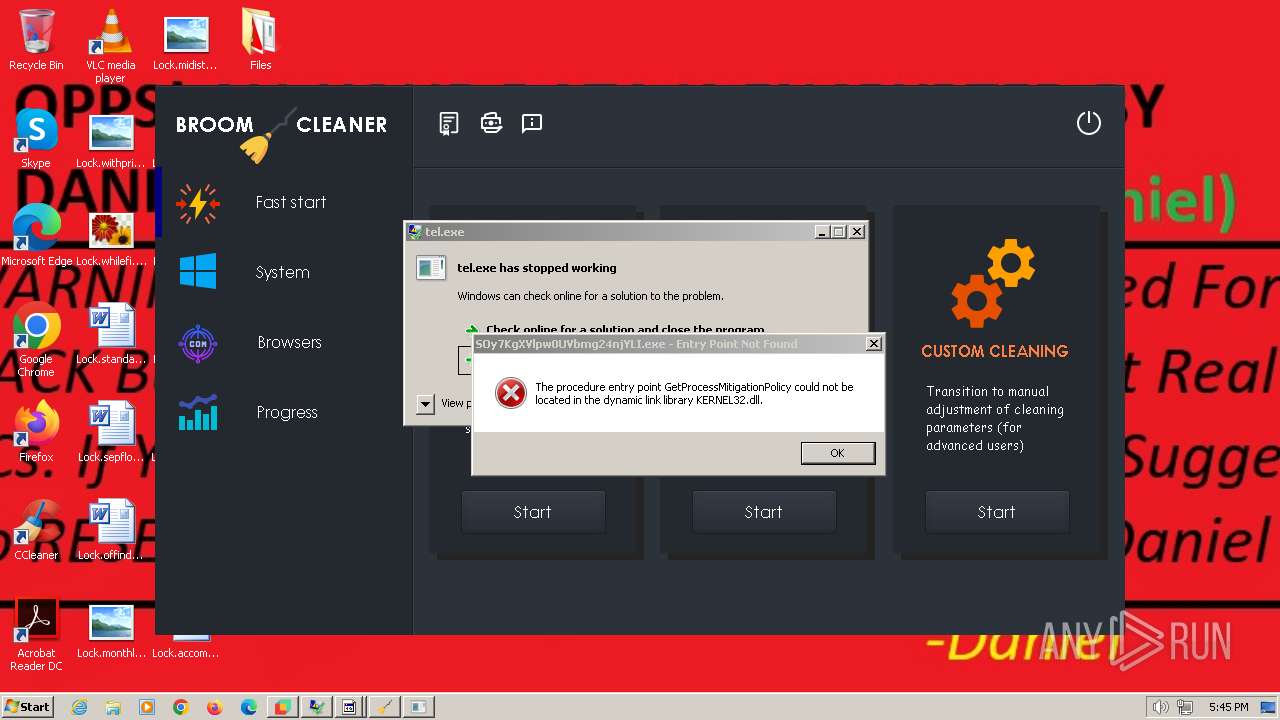
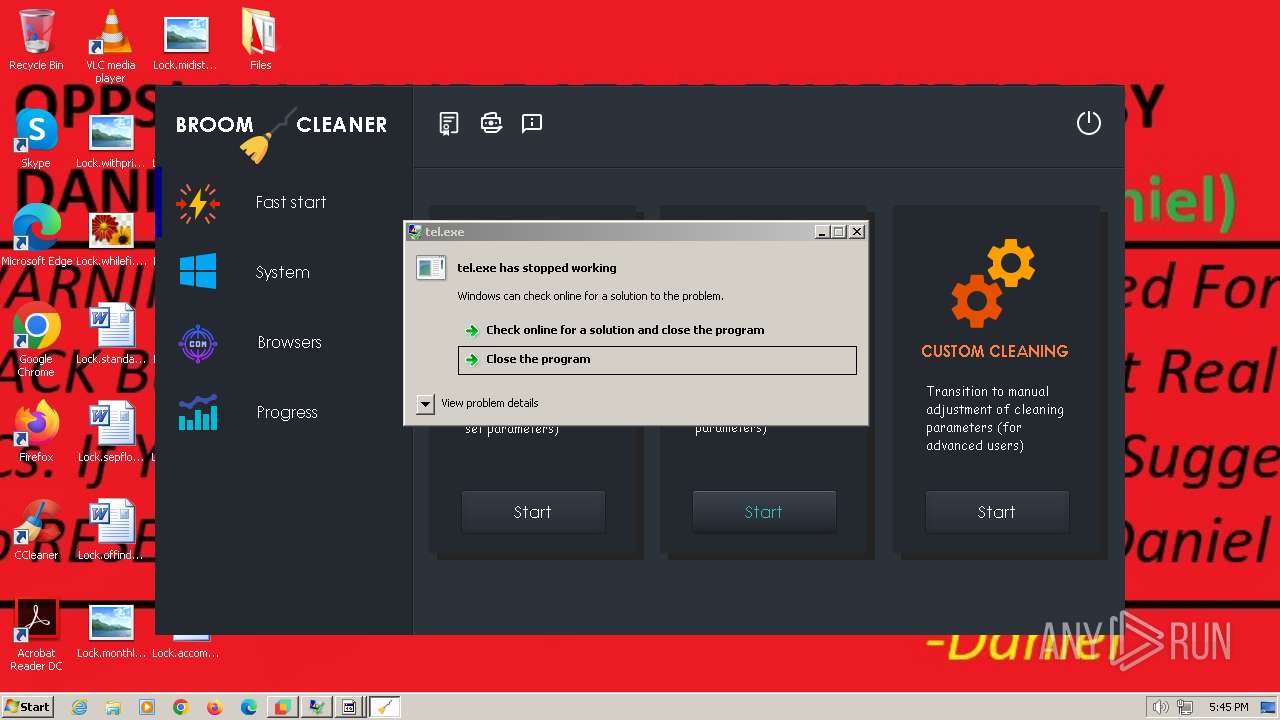
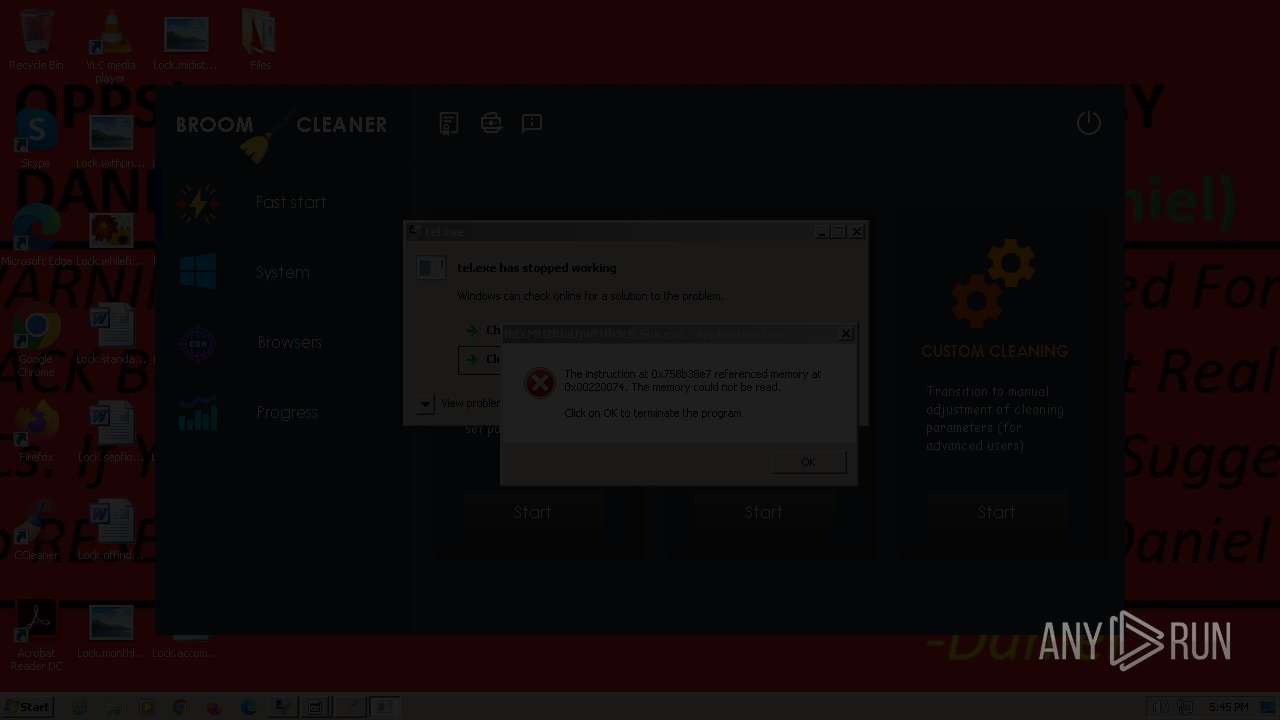
- tel.exe (PID: 1272)
- jjj.exe (PID: 2792)
- pdf.exe (PID: 1004)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2240)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 2240)
Creates a software uninstall entry
- RestoroSetup.exe (PID: 2568)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3184)
Checks for external IP
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- Temp3.exe (PID: 2624)
- Windows Security Client.exe (PID: 2052)
Reads security settings of Internet Explorer
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- file.exe (PID: 1488)
Checks Windows Trust Settings
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- file.exe (PID: 1488)
Starts application with an unusual extension
- evhtujv (PID: 1700)
The process verifies whether the antivirus software is installed
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
The process executes Powershell scripts
- cmd.exe (PID: 3012)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3012)
Probably download files using WebClient
- cmd.exe (PID: 3012)
The Powershell connects to the Internet
- powershell.exe (PID: 2736)
Unusual connection from system programs
- powershell.exe (PID: 2736)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3004)
- WPS_Setup.exe (PID: 1176)
- explorer.exe (PID: 2004)
- irsetup.exe (PID: 2420)
- 4363463463464363463463463.bin.exe (PID: 2992)
- un.exe (PID: 576)
- lve5.exe (PID: 284)
- wsuscr.exe (PID: 2328)
- more.exe (PID: 1932)
- more.exe (PID: 1420)
- Cheat.exe (PID: 2680)
- tuc6.exe (PID: 2464)
- tuc6.tmp (PID: 1036)
- Cheat.tmp (PID: 2900)
- DNS1.exe (PID: 2148)
- KarLocker_exe.exe (PID: 2256)
- bitrestore.exe (PID: 2864)
- tuc2.exe (PID: 2480)
- Controlbackup.exe (PID: 2236)
- tuc2.tmp (PID: 2552)
- Restoro.exe (PID: 2580)
- WinRAR.exe (PID: 2880)
- explorer.exe (PID: 1428)
- 4363463463464363463463463.bin.exe (PID: 1940)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 2708)
- ghoul.exe (PID: 2680)
- newtpp.exe (PID: 2792)
- npp.exe (PID: 2112)
- RestoroSetup.exe (PID: 2568)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 1060)
- hv.exe (PID: 2656)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- InstallUtil.exe (PID: 920)
- LZMA.EXE (PID: 2500)
- chungzx.exe (PID: 3080)
- LZMA.EXE (PID: 3332)
- RestoroUpdater.exe (PID: 3788)
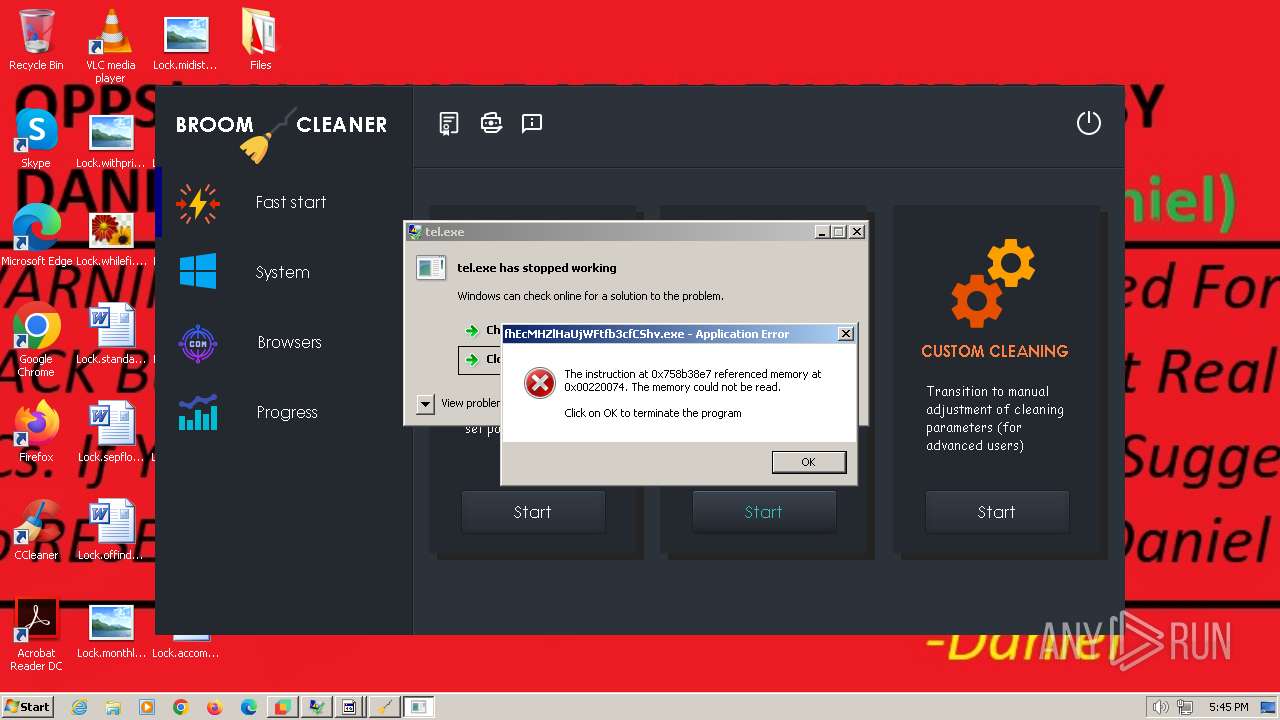
- SOy7KgXVlpw0UVbmg24njYLI.exe (PID: 3928)
- s5.exe (PID: 3148)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- I9F1lRkM2WF363lNqFIBXwYZ.exe (PID: 2540)
- 4363463463464363463463463.bin.exe (PID: 2404)
- Temp3.exe (PID: 2624)
- explorer.exe (PID: 2120)
- tuc6.exe (PID: 1656)
- tuc6.tmp (PID: 2856)
- 1226721741.exe (PID: 3400)
Reads the Internet Settings
- explorer.exe (PID: 2004)
- explorer.exe (PID: 2684)
- explorer.exe (PID: 1428)
- explorer.exe (PID: 2120)
Manual execution by a user
- 4363463463464363463463463.bin.exe (PID: 988)
- 4363463463464363463463463.bin.exe (PID: 2992)
- IMEKLMG.EXE (PID: 1676)
- IMEKLMG.EXE (PID: 1824)
- x.exe (PID: 1720)
- IMEKLMG.EXE (PID: 1688)
- wsus.exe (PID: 1696)
- Ulpktkx.exe (PID: 1864)
- IMEKLMG.EXE (PID: 1844)
- wsus.exe (PID: 1856)
- WinRAR.exe (PID: 2540)
- WinRAR.exe (PID: 2700)
- IMEKLMG.EXE (PID: 2252)
- IMEKLMG.EXE (PID: 2260)
- wsus.exe (PID: 2296)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 2352)
- cmd.exe (PID: 2376)
- x.exe (PID: 2496)
- cmd.exe (PID: 2440)
- RestoroApp.exe (PID: 2280)
- Windows Sessions Pause.exe (PID: 2308)
- IMEKLMG.EXE (PID: 2560)
- cmd.exe (PID: 2568)
- wsus.exe (PID: 2640)
- cmd.exe (PID: 2656)
- IMEKLMG.EXE (PID: 2512)
- cmd.exe (PID: 2696)
- Ulpktkx.exe (PID: 2816)
- sysplorsv.exe (PID: 2992)
- Windows Sessions Pause.exe (PID: 3048)
Reads the machine GUID from the registry
- 4363463463464363463463463.bin.exe (PID: 2992)
- more.exe (PID: 1932)
- svchost1.exe (PID: 2948)
- wsuscr.exe (PID: 2360)
- wsus.exe (PID: 1432)
- VLTKBacdau.exe (PID: 2336)
- more.exe (PID: 1420)
- images.exe (PID: 1412)
- DNS1.exe (PID: 2148)
- WMPSideShowGadget.exe (PID: 2600)
- KarLocker_exe.exe (PID: 2256)
- BestSoftware.exe (PID: 1880)
- RegSvcs.exe (PID: 2420)
- x.exe (PID: 1720)
- wsus.exe (PID: 1696)
- wsus.exe (PID: 1856)
- images.exe (PID: 1624)
- UiKVWpFsayx.exe (PID: 1548)
- 4363463463464363463463463.bin.exe (PID: 1940)
- Restoro.exe (PID: 2580)
- images.exe (PID: 2648)
- UiKVWpFsayx.exe (PID: 2444)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 2708)
- Vpeswawqko.exe (PID: 2452)
- 1230.exe (PID: 1948)
- chungzx.exe (PID: 2180)
- 1701610814-Dvnzfr.exe (PID: 920)
- hv.exe (PID: 2656)
- KarLocker_exe.exe (PID: 2428)
- npp.exe (PID: 2112)
- plugmanzx.exe (PID: 2372)
- somzx.exe (PID: 2692)
- ghoul.exe (PID: 2680)
- vbc.exe (PID: 1764)
- InstallUtil.exe (PID: 920)
- Installsetup2.exe (PID: 2828)
- RestoroSetup.exe (PID: 2568)
- vbc.exe (PID: 1192)
- RegAsm.exe (PID: 2920)
- sysplorsv.exe (PID: 3064)
- s5.exe (PID: 3148)
- Windows Sessions Pause.exe (PID: 3464)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- nsnDE38.tmp.exe (PID: 3660)
- RestoroUpdater.exe (PID: 3788)
- wsus.exe (PID: 2296)
- x.exe (PID: 2496)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- Windows Sessions Pause.exe (PID: 2308)
- UiKVWpFsayx.exe (PID: 1708)
- images.exe (PID: 664)
- wsus.exe (PID: 2640)
- tYGPdjEu3zTeOYFPT8GpiPR9.exe (PID: 2596)
- Windows Sessions Pause.exe (PID: 3048)
- sysplorsv.exe (PID: 2992)
- 4363463463464363463463463.bin.exe (PID: 2404)
- timeSync.exe (PID: 2832)
- file.exe (PID: 1488)
- Temp3.exe (PID: 2624)
- Windows Security Client.exe (PID: 2052)
- vbc.exe (PID: 2832)
- pdf.exe (PID: 1004)
- sylsplvc.exe (PID: 3420)
- images.exe (PID: 3140)
- UiKVWpFsayx.exe (PID: 3164)
Reads Environment values
- 4363463463464363463463463.bin.exe (PID: 2992)
- svchost1.exe (PID: 2948)
- wsuscr.exe (PID: 2328)
- wsus.exe (PID: 3024)
- VLTKBacdau.exe (PID: 2336)
- wsus.exe (PID: 2004)
- 4363463463464363463463463.bin.exe (PID: 1940)
- Vpeswawqko.exe (PID: 2452)
- 1701610814-Dvnzfr.exe (PID: 920)
- ghoul.exe (PID: 2680)
- InstallUtil.exe (PID: 920)
- RegAsm.exe (PID: 2920)
- chungzx.exe (PID: 3080)
- wsus.exe (PID: 2780)
- Windows Sessions Pause.exe (PID: 2360)
- 4363463463464363463463463.bin.exe (PID: 2404)
- Temp3.exe (PID: 2624)
- vbc.exe (PID: 2832)
- Windows Security Client.exe (PID: 2052)
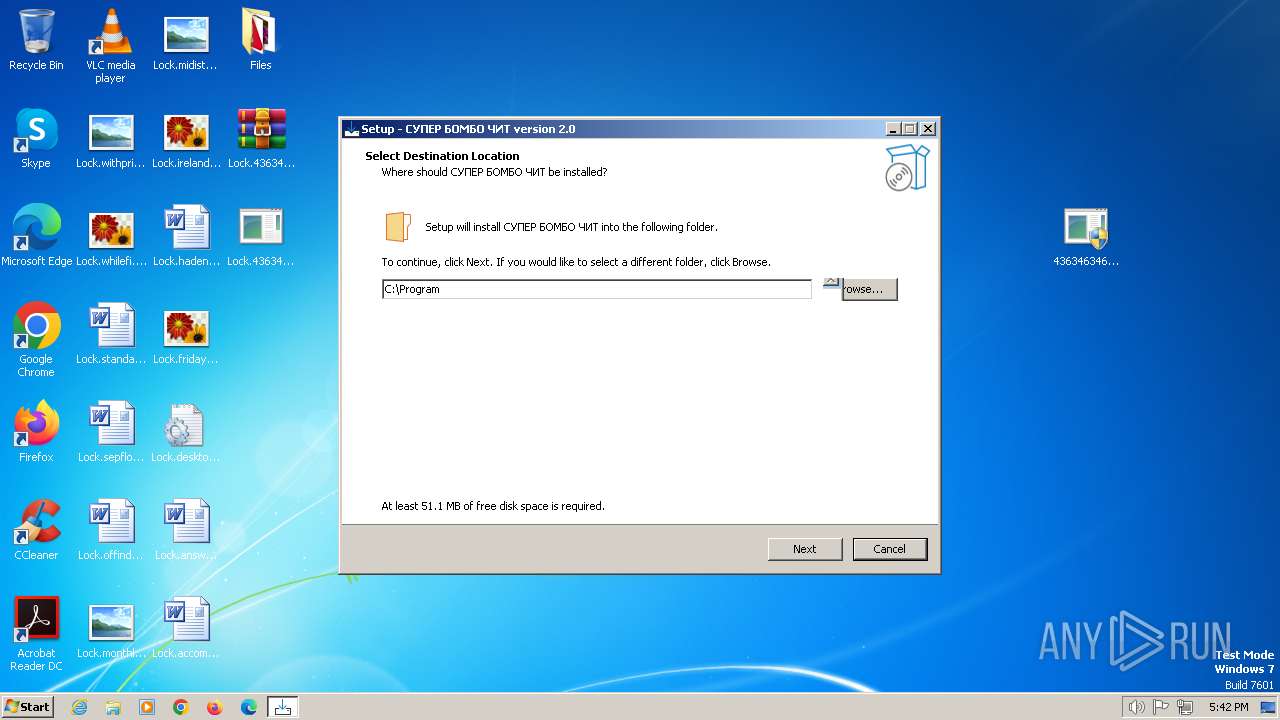
Renames files like ransomware
- explorer.exe (PID: 2004)
Checks supported languages
- 4363463463464363463463463.bin.exe (PID: 2992)
- WPS_Setup.exe (PID: 1176)
- irsetup.exe (PID: 2420)
- more.exe (PID: 1932)
- reverse.exe (PID: 2900)
- un.exe (PID: 2664)
- lumtru.exe (PID: 2272)
- ma.exe (PID: 2476)
- un.exe (PID: 576)
- iusb3mon.exe (PID: 1268)
- tbbhts.exe (PID: 2212)
- svchost1.exe (PID: 2948)
- lve5.exe (PID: 284)
- Vnloubk.exe (PID: 2312)
- Vnloubk.exe (PID: 1880)
- wsuscr.exe (PID: 2360)
- wsuscr.exe (PID: 2328)
- wsus.exe (PID: 1432)
- wsus.exe (PID: 3024)
- VLTKBacdau.exe (PID: 2336)
- cb0e88abe7aee128ff8635e44df9797d0224aff000d03fc5d9166e575b50f4a1.exe (PID: 2680)
- ww.exe (PID: 2572)
- more.exe (PID: 1420)
- Cheat.exe (PID: 2680)
- Cheat.tmp (PID: 2900)
- images.exe (PID: 1412)
- WMPSideShowGadget.exe (PID: 2600)
- tuc6.tmp (PID: 1036)
- DNS1.exe (PID: 2148)
- tuc6.exe (PID: 2464)
- bitrestore.exe (PID: 2864)
- idrB5Event.exe (PID: 2516)
- BestSoftware.exe (PID: 1880)
- Ulpktkx.exe (PID: 1436)
- bitrestore.exe (PID: 1640)
- KarLocker_exe.exe (PID: 2256)
- tuc2.tmp (PID: 2552)
- Controlbackup.exe (PID: 2236)
- kb%5Efr_ouverture.exe (PID: 2568)
- liveupdate.exe (PID: 972)
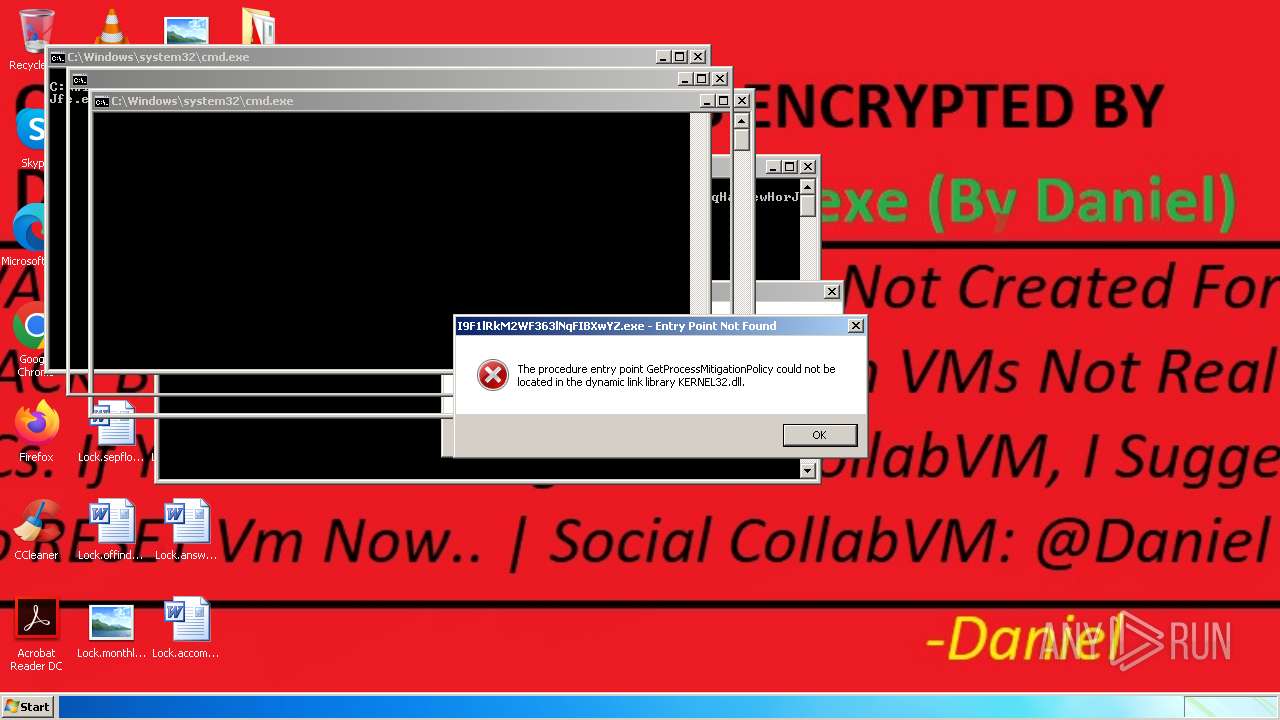
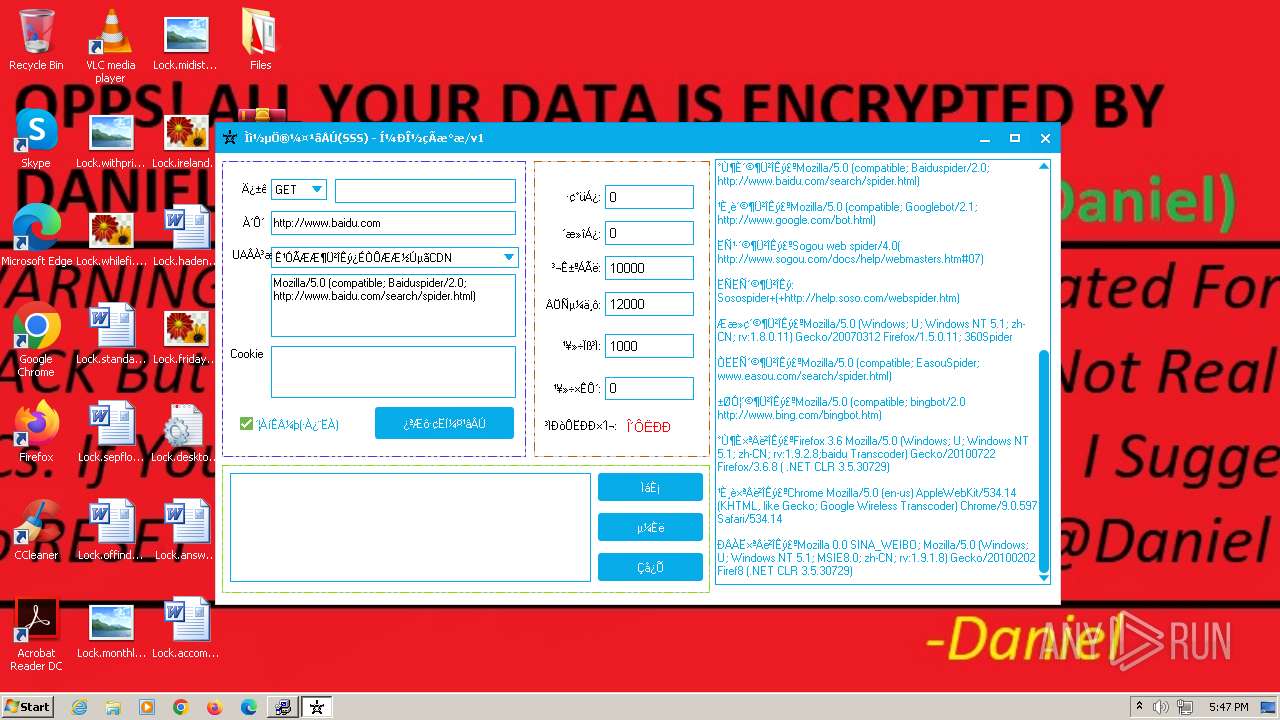
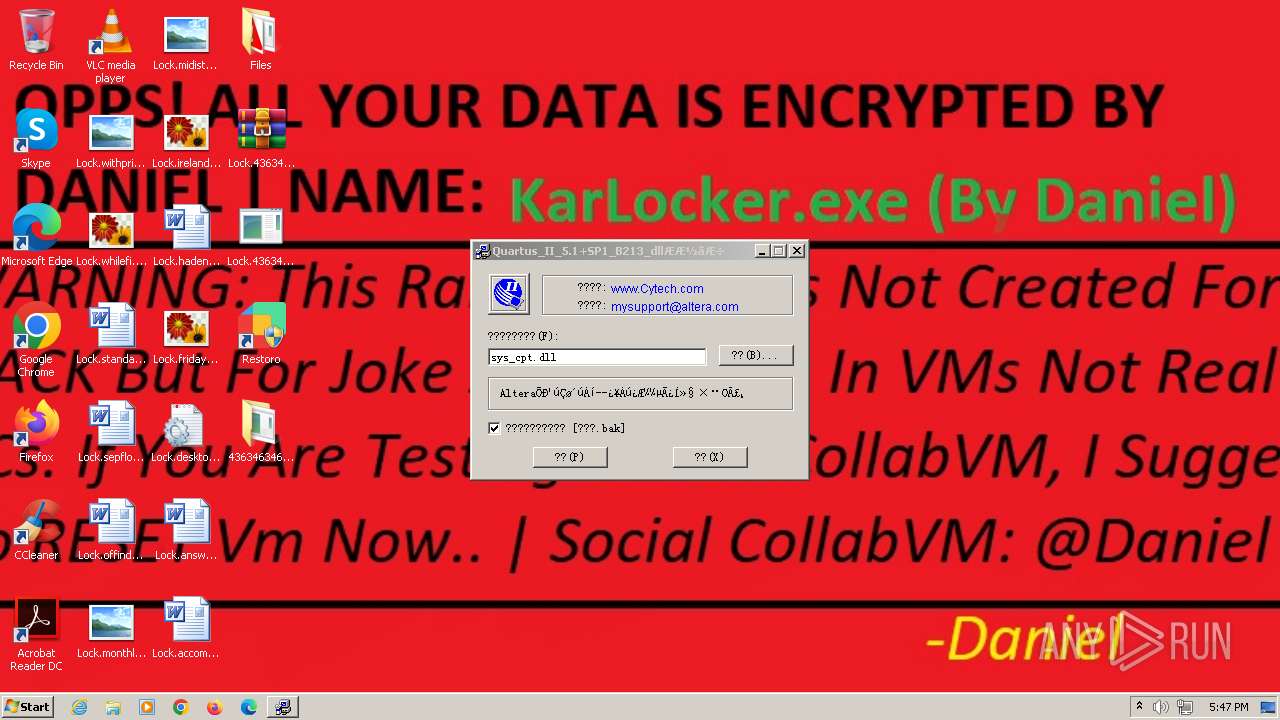
- SystemCrasher_ByDaniel.exe (PID: 1652)
- tuc4.exe (PID: 2240)
- images.exe (PID: 1624)
- adhtujv (PID: 1520)
- UiKVWpFsayx.exe (PID: 1548)
- RegSvcs.exe (PID: 2420)
- wsus.exe (PID: 1696)
- IMEKLMG.EXE (PID: 1676)
- IMEKLMG.EXE (PID: 1688)
- x.exe (PID: 1720)
- IMEKLMG.EXE (PID: 1824)
- IMEKLMG.EXE (PID: 1844)
- Ulpktkx.exe (PID: 1864)
- wsus.exe (PID: 1856)
- Vnloubk.exe (PID: 2140)
- wsus.exe (PID: 2004)
- wsus.exe (PID: 2012)
- Restoro.exe (PID: 2580)
- 4363463463464363463463463.bin.exe (PID: 1940)
- sqlite3.exe (PID: 2508)
- sqlite3.exe (PID: 2536)
- sqlite3.exe (PID: 2688)
- tuc2.exe (PID: 2480)
- SOFT_KNITTING.exe (PID: 2684)
- images.exe (PID: 2648)
- ghoul.exe (PID: 2680)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 2708)
- UiKVWpFsayx.exe (PID: 2444)
- 1230.exe (PID: 1948)
- Vpeswawqko.exe (PID: 2452)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 2260)
- toolspub2.exe (PID: 1952)
- toolspub2.exe (PID: 2500)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 2256)
- chungzx.exe (PID: 2180)
- 1701610814-Dvnzfr.exe (PID: 920)
- KarLocker_exe.exe (PID: 2428)
- adm_atu.exe (PID: 992)
- hv.exe (PID: 2656)
- newtpp.exe (PID: 2792)
- sqlite3.exe (PID: 3004)
- toolspub4.exe (PID: 1364)
- toolspub4.exe (PID: 1768)
- DNS2.exe (PID: 1884)
- sysplorsv.exe (PID: 3064)
- fortnite2.exe (PID: 964)
- npp.exe (PID: 2112)
- somzx.exe (PID: 2692)
- 20434444.exe (PID: 2960)
- plugmanzx.exe (PID: 2372)
- RestoroSetup.exe (PID: 2568)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 1060)
- tel.exe (PID: 1272)
- vbc.exe (PID: 1764)
- jjj.exe (PID: 2792)
- fcc.exe (PID: 1380)
- InstallUtil.exe (PID: 920)
- Installsetup2.exe (PID: 2828)
- s5.exe (PID: 884)
- vbc.exe (PID: 1192)
- ww.exe (PID: 3004)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- BroomSetup.exe (PID: 2628)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 1960)
- chungzx.exe (PID: 3080)
- RegAsm.exe (PID: 2920)
- s5.exe (PID: 3148)
- LZMA.EXE (PID: 2500)
- LZMA.EXE (PID: 3332)
- Windows Sessions Pause.exe (PID: 3464)
- nsnDE38.tmp.exe (PID: 3660)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 3668)
- RestoroUpdater.exe (PID: 3788)
- SOy7KgXVlpw0UVbmg24njYLI.exe (PID: 3928)
- plugmanzx.exe (PID: 364)
- RestoroApp.exe (PID: 3712)
- Vnloubk.exe (PID: 1692)
- evhtujv (PID: 1700)
- adhtujv (PID: 1488)
- images.exe (PID: 664)
- ybrkxyW4wqjA5RTPZCcu9KGy.exe (PID: 3732)
- 6NaBEaPdHGCDBrRcLpJVgrgL.exe (PID: 3700)
- RestoroMain.exe (PID: 3824)
- GOsJa5GJsLMcRtqwDKiwIYiG.exe (PID: 3980)
- evhtujv (PID: 1984)
- IMEKLMG.EXE (PID: 2252)
- IMEKLMG.EXE (PID: 2260)
- UiKVWpFsayx.exe (PID: 1708)
- wsus.exe (PID: 2296)
- Windows Sessions Pause.exe (PID: 2308)
- RestoroApp.exe (PID: 2280)
- IMEKLMG.EXE (PID: 2512)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- IMEKLMG.EXE (PID: 2560)
- x.exe (PID: 2496)
- I9F1lRkM2WF363lNqFIBXwYZ.exe (PID: 2540)
- tYGPdjEu3zTeOYFPT8GpiPR9.exe (PID: 2596)
- wsus.exe (PID: 2792)
- wsus.exe (PID: 2780)
- Ulpktkx.exe (PID: 2816)
- wsus.exe (PID: 2640)
- sysplorsv.exe (PID: 2992)
- Windows Sessions Pause.exe (PID: 3048)
- Windows Sessions Pause.exe (PID: 2344)
- Windows Sessions Pause.exe (PID: 2360)
- 4363463463464363463463463.bin.exe (PID: 2404)
- timeSync.exe (PID: 2832)
- qt51crk.exe (PID: 1496)
- file.exe (PID: 1488)
- plink.exe (PID: 2912)
- Temp3.exe (PID: 2624)
- Windows Security Client.exe (PID: 2052)
- vbc.exe (PID: 2832)
- %E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe (PID: 2392)
- pdf.exe (PID: 1004)
- bitrestore.exe (PID: 2604)
- tuc6.exe (PID: 1656)
- tuc6.tmp (PID: 2856)
- images.exe (PID: 3140)
- UiKVWpFsayx.exe (PID: 3164)
- bitrestore.exe (PID: 3320)
- 1226721741.exe (PID: 3400)
- sylsplvc.exe (PID: 3420)
Reads the computer name
- 4363463463464363463463463.bin.exe (PID: 2992)
- WPS_Setup.exe (PID: 1176)
- irsetup.exe (PID: 2420)
- un.exe (PID: 2664)
- more.exe (PID: 1932)
- lumtru.exe (PID: 2272)
- un.exe (PID: 576)
- ma.exe (PID: 2476)
- iusb3mon.exe (PID: 1268)
- svchost1.exe (PID: 2948)
- lve5.exe (PID: 284)
- Vnloubk.exe (PID: 2312)
- Vnloubk.exe (PID: 1880)
- wsuscr.exe (PID: 2360)
- wsuscr.exe (PID: 2328)
- wsus.exe (PID: 1432)
- wsus.exe (PID: 3024)
- VLTKBacdau.exe (PID: 2336)
- more.exe (PID: 1420)
- images.exe (PID: 1412)
- Cheat.tmp (PID: 2900)
- tuc6.tmp (PID: 1036)
- DNS1.exe (PID: 2148)
- Ulpktkx.exe (PID: 1436)
- BestSoftware.exe (PID: 1880)
- KarLocker_exe.exe (PID: 2256)
- bitrestore.exe (PID: 2864)
- tuc2.tmp (PID: 2552)
- kb%5Efr_ouverture.exe (PID: 2568)
- Controlbackup.exe (PID: 2236)
- liveupdate.exe (PID: 972)
- RegSvcs.exe (PID: 2420)
- IMEKLMG.EXE (PID: 1688)
- IMEKLMG.EXE (PID: 1676)
- x.exe (PID: 1720)
- wsus.exe (PID: 1696)
- IMEKLMG.EXE (PID: 1844)
- IMEKLMG.EXE (PID: 1824)
- Ulpktkx.exe (PID: 1864)
- UiKVWpFsayx.exe (PID: 1548)
- wsus.exe (PID: 1856)
- images.exe (PID: 1624)
- Vnloubk.exe (PID: 2140)
- wsus.exe (PID: 2004)
- 4363463463464363463463463.bin.exe (PID: 1940)
- Restoro.exe (PID: 2580)
- images.exe (PID: 2648)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 2708)
- ghoul.exe (PID: 2680)
- UiKVWpFsayx.exe (PID: 2444)
- 1230.exe (PID: 1948)
- Vpeswawqko.exe (PID: 2452)
- chungzx.exe (PID: 2180)
- 1701610814-Dvnzfr.exe (PID: 920)
- KarLocker_exe.exe (PID: 2428)
- hv.exe (PID: 2656)
- DNS2.exe (PID: 1884)
- npp.exe (PID: 2112)
- plugmanzx.exe (PID: 2372)
- somzx.exe (PID: 2692)
- RestoroSetup.exe (PID: 2568)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 1060)
- vbc.exe (PID: 1764)
- fcc.exe (PID: 1380)
- InstallUtil.exe (PID: 920)
- Installsetup2.exe (PID: 2828)
- vbc.exe (PID: 1192)
- RegAsm.exe (PID: 2920)
- sysplorsv.exe (PID: 3064)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- chungzx.exe (PID: 3080)
- s5.exe (PID: 3148)
- BroomSetup.exe (PID: 2628)
- nsnDE38.tmp.exe (PID: 3660)
- Windows Sessions Pause.exe (PID: 3464)
- RestoroUpdater.exe (PID: 3788)
- Vnloubk.exe (PID: 1692)
- UiKVWpFsayx.exe (PID: 1708)
- IMEKLMG.EXE (PID: 2260)
- IMEKLMG.EXE (PID: 2252)
- wsus.exe (PID: 2296)
- Windows Sessions Pause.exe (PID: 2308)
- images.exe (PID: 664)
- IMEKLMG.EXE (PID: 2512)
- IMEKLMG.EXE (PID: 2560)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- x.exe (PID: 2496)
- wsus.exe (PID: 2640)
- tYGPdjEu3zTeOYFPT8GpiPR9.exe (PID: 2596)
- wsus.exe (PID: 2780)
- Ulpktkx.exe (PID: 2816)
- Windows Sessions Pause.exe (PID: 3048)
- sysplorsv.exe (PID: 2992)
- 4363463463464363463463463.bin.exe (PID: 2404)
- timeSync.exe (PID: 2832)
- file.exe (PID: 1488)
- Temp3.exe (PID: 2624)
- plink.exe (PID: 2912)
- Windows Security Client.exe (PID: 2052)
- vbc.exe (PID: 2832)
- pdf.exe (PID: 1004)
- tuc6.tmp (PID: 2856)
- bitrestore.exe (PID: 2604)
- images.exe (PID: 3140)
- UiKVWpFsayx.exe (PID: 3164)
- sylsplvc.exe (PID: 3420)
Creates files or folders in the user directory
- 4363463463464363463463463.bin.exe (PID: 2992)
- svchost1.exe (PID: 2948)
- more.exe (PID: 1932)
- more.exe (PID: 1420)
- explorer.exe (PID: 2004)
- DNS1.exe (PID: 2148)
- KarLocker_exe.exe (PID: 2256)
- Controlbackup.exe (PID: 2236)
- UiKVWpFsayx.exe (PID: 1548)
- sqlite3.exe (PID: 2508)
- Restoro.exe (PID: 2580)
- npp.exe (PID: 2112)
- explorer.exe (PID: 1428)
- plugmanzx.exe (PID: 2372)
- fcc.exe (PID: 1380)
- InstallUtil.exe (PID: 920)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- s5.exe (PID: 3148)
- RestoroUpdater.exe (PID: 3788)
- RestoroSetup.exe (PID: 2568)
- x.exe (PID: 2496)
- Windows Sessions Pause.exe (PID: 2308)
- I9F1lRkM2WF363lNqFIBXwYZ.exe (PID: 2540)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- file.exe (PID: 1488)
- Windows Security Client.exe (PID: 2052)
- sysplorsv.exe (PID: 2992)
Create files in a temporary directory
- 4363463463464363463463463.bin.exe (PID: 2992)
- WPS_Setup.exe (PID: 1176)
- irsetup.exe (PID: 2420)
- iusb3mon.exe (PID: 1268)
- more.exe (PID: 1932)
- more.exe (PID: 1420)
- Cheat.exe (PID: 2680)
- tuc6.tmp (PID: 1036)
- tuc6.exe (PID: 2464)
- Cheat.tmp (PID: 2900)
- KarLocker_exe.exe (PID: 2256)
- tuc2.tmp (PID: 2552)
- tuc2.exe (PID: 2480)
- x.exe (PID: 1720)
- Restoro.exe (PID: 2580)
- images.exe (PID: 1624)
- UiKVWpFsayx.exe (PID: 1548)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 2708)
- adm_atu.exe (PID: 992)
- KarLocker_exe.exe (PID: 2428)
- npp.exe (PID: 2112)
- RestoroSetup.exe (PID: 2568)
- hv.exe (PID: 2656)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- chungzx.exe (PID: 3080)
- RegAsm.exe (PID: 2920)
- RestoroUpdater.exe (PID: 3788)
- SOy7KgXVlpw0UVbmg24njYLI.exe (PID: 3928)
- I9F1lRkM2WF363lNqFIBXwYZ.exe (PID: 2540)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- x.exe (PID: 2496)
- tuc6.exe (PID: 1656)
- tuc6.tmp (PID: 2856)
- UiKVWpFsayx.exe (PID: 1708)
- images.exe (PID: 664)
- sysplorsv.exe (PID: 2992)
Creates files in the program directory
- irsetup.exe (PID: 2420)
- un.exe (PID: 2664)
- lve5.exe (PID: 284)
- wsuscr.exe (PID: 2328)
- tuc6.tmp (PID: 1036)
- DNS1.exe (PID: 2148)
- bitrestore.exe (PID: 2864)
- tuc2.tmp (PID: 2552)
- ghoul.exe (PID: 2680)
- Restoro.exe (PID: 2580)
- RestoroSetup.exe (PID: 2568)
- LZMA.EXE (PID: 2500)
- LZMA.EXE (PID: 3332)
- RestoroUpdater.exe (PID: 3788)
- h3EtHLBXagaPAmj4nXQlFXK3.exe (PID: 2520)
- tuc6.tmp (PID: 2856)
Checks proxy server information
- svchost1.exe (PID: 2948)
- DNS1.exe (PID: 2148)
- Restoro.exe (PID: 2580)
- 1230.exe (PID: 1948)
- npp.exe (PID: 2112)
- sysplorsv.exe (PID: 3064)
- s5.exe (PID: 3148)
- fhEcMHZlHaUjWFtfb3cfCShv.exe (PID: 2588)
- nsnDE38.tmp.exe (PID: 3660)
- RestoroUpdater.exe (PID: 3788)
- RestoroSetup.exe (PID: 2568)
- sysplorsv.exe (PID: 2992)
- timeSync.exe (PID: 2832)
- file.exe (PID: 1488)
- plink.exe (PID: 2912)
- sylsplvc.exe (PID: 3420)
Executes as Windows Service
- Vnloubk.exe (PID: 2312)
Application launched itself
- Vnloubk.exe (PID: 2312)
- wsuscr.exe (PID: 2360)
- wsus.exe (PID: 1432)
- more.exe (PID: 1932)
- wsus.exe (PID: 1856)
- wsus.exe (PID: 1696)
- images.exe (PID: 1624)
- UiKVWpFsayx.exe (PID: 1548)
- toolspub2.exe (PID: 1952)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 2260)
- toolspub4.exe (PID: 1364)
- chungzx.exe (PID: 2180)
- s5.exe (PID: 884)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 1960)
- somzx.exe (PID: 2692)
- plugmanzx.exe (PID: 2372)
- evhtujv (PID: 1700)
- wsus.exe (PID: 2296)
- wsus.exe (PID: 2640)
- Windows Sessions Pause.exe (PID: 2308)
- Windows Sessions Pause.exe (PID: 3048)
- UiKVWpFsayx.exe (PID: 1708)
- images.exe (PID: 664)
Reads CPU info
- lve5.exe (PID: 284)
- Ulpktkx.exe (PID: 1436)
- Ulpktkx.exe (PID: 1864)
- Vnloubk.exe (PID: 2140)
- Vnloubk.exe (PID: 1692)
- Ulpktkx.exe (PID: 2816)
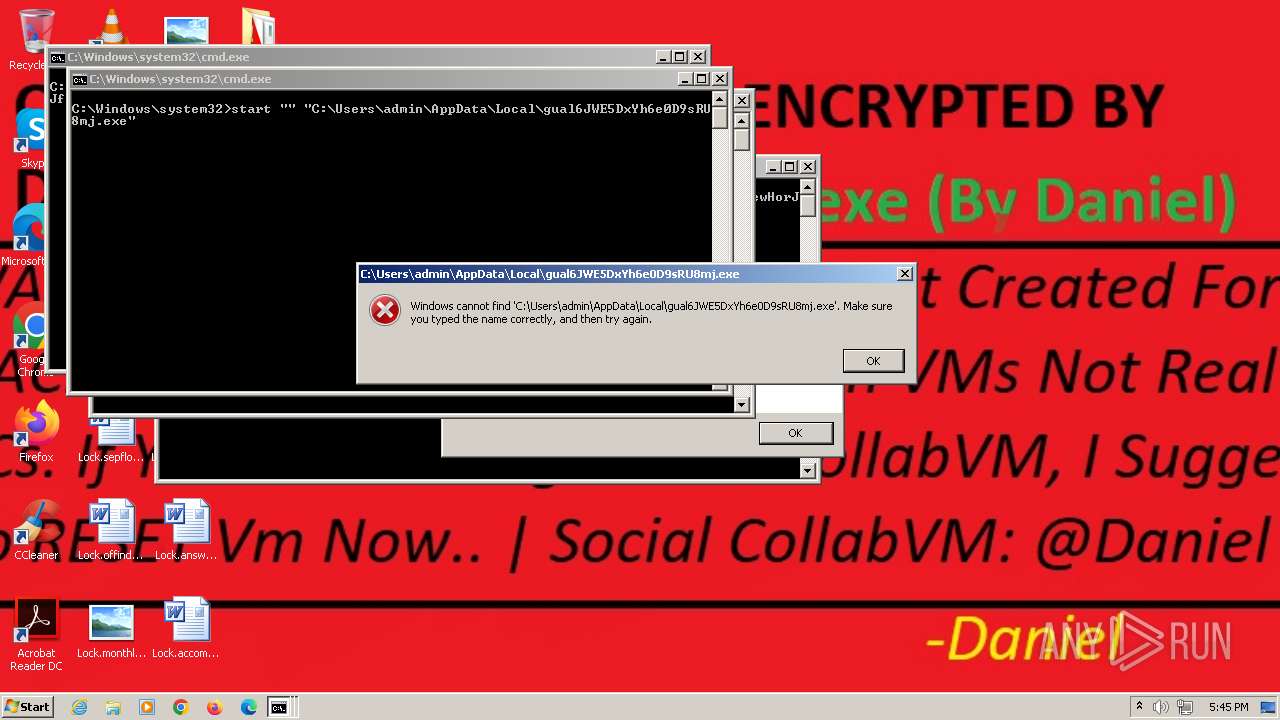
Starts itself from another location
- wsuscr.exe (PID: 2328)
- DNS1.exe (PID: 2148)
- newtpp.exe (PID: 2792)
- Temp3.exe (PID: 2624)
- 1226721741.exe (PID: 3400)
Application was injected by another process
- explorer.exe (PID: 2004)
- explorer.exe (PID: 1428)
- explorer.exe (PID: 2120)
The executable file from the user directory is run by the CMD process
- images.exe (PID: 1412)
- sqlite3.exe (PID: 2536)
- sqlite3.exe (PID: 2508)
- sqlite3.exe (PID: 2688)
- sqlite3.exe (PID: 3004)
Process drops legitimate windows executable
- tuc6.tmp (PID: 1036)
- tuc2.tmp (PID: 2552)
- 4363463463464363463463463.bin.exe (PID: 1940)
- RestoroSetup.exe (PID: 2568)
- tuc6.tmp (PID: 2856)
Process drops SQLite DLL files
- tuc6.tmp (PID: 1036)
- tuc2.tmp (PID: 2552)
- tuc6.tmp (PID: 2856)
Drops 7-zip archiver for unpacking
- tuc6.tmp (PID: 1036)
- tuc2.tmp (PID: 2552)
- RestoroSetup.exe (PID: 2568)
- tuc6.tmp (PID: 2856)
Reads mouse settings
- KarLocker_exe.exe (PID: 2256)
- x.exe (PID: 1720)
- KarLocker_exe.exe (PID: 2428)
- x.exe (PID: 2496)
The process executes via Task Scheduler
- adhtujv (PID: 1520)
- UiKVWpFsayx.exe (PID: 1548)
- images.exe (PID: 1624)
- dialer.exe (PID: 280)
- adhtujv (PID: 1488)
- evhtujv (PID: 1700)
- images.exe (PID: 664)
- UiKVWpFsayx.exe (PID: 1708)
- dllhost.exe (PID: 3164)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 1688)
- IMEKLMG.EXE (PID: 1676)
- Installsetup2.exe (PID: 2828)
- IMEKLMG.EXE (PID: 2252)
- IMEKLMG.EXE (PID: 2260)
Malware-specific behavior (creating "System.dll" in Temp)
- Restoro.exe (PID: 2580)
- RestoroSetup.exe (PID: 2568)
- RestoroUpdater.exe (PID: 3788)
The process drops C-runtime libraries
- RestoroSetup.exe (PID: 2568)
Executing commands from a ".bat" file
- explorer.exe (PID: 2120)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 2120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(2948) svchost1.exe
C2 (1)38.181.25.204
Ports (1)5858
BotnetDefault
Version东方控制-[RAT-HVNC]
Options
AutoRunfalse
Mutexifyviyeiimfgf
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAOKdH0p4VoRrNYF8+HLW2ZXVKcCnMA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMTAwMjA1NDAzNVoXDTMzMDcxMTA1NDAzNVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_Signaturej++9XGmFmNLtVnqAuLIiYK1NC3NzPemkqAm+aFfUFuxmkXWsV1r3n4yOtEgO40UUDb5of3cp9SN8ImXoICX357QH4sv8dcG8q+NPcWSk3kG1mV9Cc+42SnWd3mobMAdI1GXIUWA5DswC7B8oCqXjUeF8RGwNO6FbOv4E2HGG388=
Keys
AES0bdac385494da40655a40166423742f88d293d427de7a8595aa505df12fae611
SaltVenomRATByVenom
Remcos
(PID) Process(3024) wsus.exe
C2 (13)45.87.155.41:8080:0
45.87.155.41:465
45.87.155.41:54550
45.87.155.41:80
45.87.154.153:80
45.87.154.153:8080:0
101.99.75.16:8080:0
101.99.75.16:80
101.99.75.16:465
101.99.75.145:465
101.99.75.145:80
94.131.102.115:80
94.131.102.117:80
94.131.102.119:80
94.131.102.122:80
94.131.102.124:80
Botnetwsus
Options
Connect_interval1
Install_flagTrue
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%LOCALAPPDATA%
Copy_filewsus.exe
Startup_valueFalse
Hide_fileFalse
Mutex_namedvwsus-SFNWWW
Keylog_flag0
Keylog_path%LOCALAPPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%ProgramFiles%
Audio_dirMicRecords
Connect_delay0
Copy_dirwsus
Keylog_dirremcos
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2023:12:22 17:22:14 |
| ZipCRC: | 0x31d44928 |
| ZipCompressedSize: | 4787 |
| ZipUncompressedSize: | 10752 |
| ZipFileName: | 4363463463464363463463463.bin |
Total processes
476
Monitored processes
258
Malicious processes
77
Suspicious processes
20
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Windows\system32\dialer.exe" | C:\Windows\SysWOW64\dialer.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Phone Dialer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | "C:\Users\admin\Desktop\Files\lve5.exe" | C:\Users\admin\Desktop\Files\lve5.exe | 4363463463464363463463463.bin.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 340 | cmd /C tasklist /FI "IMAGENAME eq Wireshark.exe" > C:\Users\admin\AppData\Local\Temp\IsProcessActive.txt | C:\Windows\SysWOW64\cmd.exe | — | Restoro.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 364 | "C:\Users\admin\Desktop\4363463463464363463463463.bin\Files\plugmanzx.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin\Files\plugmanzx.exe | — | plugmanzx.exe | |||||||||||
User: admin Integrity Level: HIGH Description: WindowsFormsApp3 Exit code: 3221226091 Version: 1.0.0.0 Modules
| |||||||||||||||
| 576 | "C:\un.exe" x -o+ -ppoiuytrewq C:\ProgramData\Data\upx.rar iusb3mon.exe iusb3mon.dat Media.xml C:\Microsoft\ | C:\un.exe | — | irsetup.exe | |||||||||||
User: admin Company: WinRAR 压缩管理软件中文版 Integrity Level: HIGH Description: 命令行 RAR Exit code: 0 Version: 5.20.0 Modules
| |||||||||||||||
| 664 | C:\Users\admin\AppData\Roaming\images.exe | C:\Users\admin\AppData\Roaming\images.exe | — | taskeng.exe | |||||||||||
User: admin Company: BinanceTech Integrity Level: HIGH Description: Binance Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 684 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath "C:\Users\admin\AppData\Roaming\UiKVWpFsayx.exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | more.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 884 | "C:\Users\admin\Desktop\4363463463464363463463463.bin\Files\s5.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin\Files\s5.exe | — | 4363463463464363463463463.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop\4363463463464363463463463.bin\Files\1701610814-Dvnzfr.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin\Files\1701610814-Dvnzfr.exe | 4363463463464363463463463.bin.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 920 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | Installsetup2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Framework installation utility Exit code: 1073807364 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
141 548
Read events
139 765
Write events
1 686
Delete events
97
Modification events
| (PID) Process: | (2004) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000000425B8FBD140304D952DBE1156DB516600000000020000000000106600000001000020000000DB7CFDADD20035B54FE72E91B52C386E688080B10C096541937D15768230E9B4000000000E8000000002000020000000FC5BD8C24841EC802021354E72CCCB98F326B765B114F6B99237B0E53C70855230000000E5259FA42E3216E6ABD96FBA3A6491DBFE5EABB7874FD90C6180CAAA39FCB4DA5097AFD783F475C120AF35A7DAD783F44000000017650D25D4C3008FF427790B98E977F1147A37B555438BA5F03FADACC116CEA191D18AD610A15D4BB60F12EF1F1AF002B029515D03AC7340FF8EFA43530BF5CD | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2004) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7AndW2K8R2-KB3191566-x64.zip | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_3-win64-mingw.zip | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
476
Suspicious files
177
Text files
331
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2004 | explorer.exe | C:\Users\admin\Desktop\4363463463464363463463463.bin | executable | |
MD5:2A94F3960C58C6E70826495F76D00B85 | SHA256:2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE | |||
| 2004 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\4363463463464363463463463.bin.zip.lnk | binary | |
MD5:C72A89197EF806169AC32F894E63103E | SHA256:881789F9C3923F9A12C2A0019D4887DAB0B07555459779490EB1AB6ACA4141BA | |||
| 2992 | 4363463463464363463463463.bin.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F59A01A8B782D93EA6991BC172CEFFB1 | binary | |
MD5:C5DFB849CA051355EE2DBA1AC33EB028 | SHA256:CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B | |||
| 1176 | WPS_Setup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\lua5.1.dll | executable | |
MD5:B5FC476C1BF08D5161346CC7DD4CB0BA | SHA256:12CB9B8F59C00EF40EA8F28BFC59A29F12DC28332BF44B1A5D8D6A8823365650 | |||
| 2004 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | binary | |
MD5:1DDF1C4970A15627196F60897D7D5ECF | SHA256:790CD62ADE734E8C4E5E026B6914AE34F2EC6E1F1C4E45D2F1C567BAC1E63AB8 | |||
| 2420 | irsetup.exe | C:\ProgramData\data\UPX.rar | compressed | |
MD5:BCB4E84D2E5618A434924F9133EA2EB6 | SHA256:50FC373CC7D214B806BA21CE2BD21572D7C322F1C6E61C05416ECCBD6BE5C06C | |||
| 2992 | 4363463463464363463463463.bin.exe | C:\Users\admin\AppData\Local\Temp\TarBEEE.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 2420 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG1.JPG | image | |
MD5:3220A6AEFB4FC719CC8849F060859169 | SHA256:988CF422CBF400D41C48FBE491B425A827A1B70691F483679C1DF02FB9352765 | |||
| 2004 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\46f433176bc0b3d2.automaticDestinations-ms | binary | |
MD5:6AD5FB9C2DF01FC36B8F237C0A5C7125 | SHA256:637A1EF13A6E520E20BA723D78C3B9CE9D5FF737E817F6C0D997E880CF383151 | |||
| 2420 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.dat | binary | |
MD5:9FE51FE6DC9B0DF64AEBA16164A29883 | SHA256:C1E7A11C4E7F65494E1F7D8B8083A371759A08E244BE93CEC3500F7E6D36CE9E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
146
TCP/UDP connections
352
DNS requests
91
Threats
362
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2992 | 4363463463464363463463463.bin.exe | GET | 200 | 151.101.2.133:80 | http://secure.globalsign.com/cacert/root-r3.crt | unknown | binary | 867 b | unknown |
2992 | 4363463463464363463463463.bin.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?440aaa20924fcacc | unknown | compressed | 65.2 Kb | unknown |
2992 | 4363463463464363463463463.bin.exe | GET | 200 | 209.205.200.74:80 | http://oazahotel.com.mk/more.exe | unknown | executable | 299 Kb | unknown |
2272 | lumtru.exe | POST | 200 | 104.21.24.252:80 | http://soupinterestoe.fun/api | unknown | html | 4.62 Kb | unknown |
2992 | 4363463463464363463463463.bin.exe | GET | 200 | 5.252.176.77:80 | http://5.252.176.77/reverse.exe | unknown | executable | 7.00 Kb | unknown |
2992 | 4363463463464363463463463.bin.exe | GET | 200 | 185.172.128.113:80 | http://185.172.128.113/ma.exe | unknown | executable | 2.09 Mb | unknown |
2992 | 4363463463464363463463463.bin.exe | GET | 200 | 77.91.124.172:80 | http://77.91.124.172/files/lumtru.exe | unknown | executable | 448 Kb | unknown |
2272 | lumtru.exe | POST | 200 | 104.21.24.252:80 | http://soupinterestoe.fun/api | unknown | text | 16.9 Kb | unknown |
2272 | lumtru.exe | POST | 200 | 104.21.24.252:80 | http://soupinterestoe.fun/api | unknown | text | 21 b | unknown |
2992 | 4363463463464363463463463.bin.exe | GET | 200 | 45.197.46.193:80 | http://45.197.46.193/003/tbbhts.exe | unknown | executable | 323 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2992 | 4363463463464363463463463.bin.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2992 | 4363463463464363463463463.bin.exe | 151.101.2.133:80 | secure.globalsign.com | FASTLY | US | unknown |
2992 | 4363463463464363463463463.bin.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2992 | 4363463463464363463463463.bin.exe | 47.75.19.76:443 | windowswps.oss-cn-hongkong.aliyuncs.com | Alibaba US Technology Co., Ltd. | HK | unknown |
2992 | 4363463463464363463463463.bin.exe | 209.205.200.74:80 | oazahotel.com.mk | 24SHELLS | US | unknown |
2992 | 4363463463464363463463463.bin.exe | 5.252.176.77:80 | — | MivoCloud SRL | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
secure.globalsign.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
windowswps.oss-cn-hongkong.aliyuncs.com |
| malicious |
oazahotel.com.mk |
| malicious |
soupinterestoe.fun |
| malicious |
bitbucket.org |
| shared |
bbuseruploads.s3.amazonaws.com |
| shared |
www.996m2m2.top |
| unknown |
kimyen.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2992 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2992 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2992 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2992 | 4363463463464363463463463.bin.exe | Misc activity | ET HUNTING [TW] Likely Hex Executable String |
2992 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2992 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2992 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2992 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2992 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2992 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
49 ETPRO signatures available at the full report