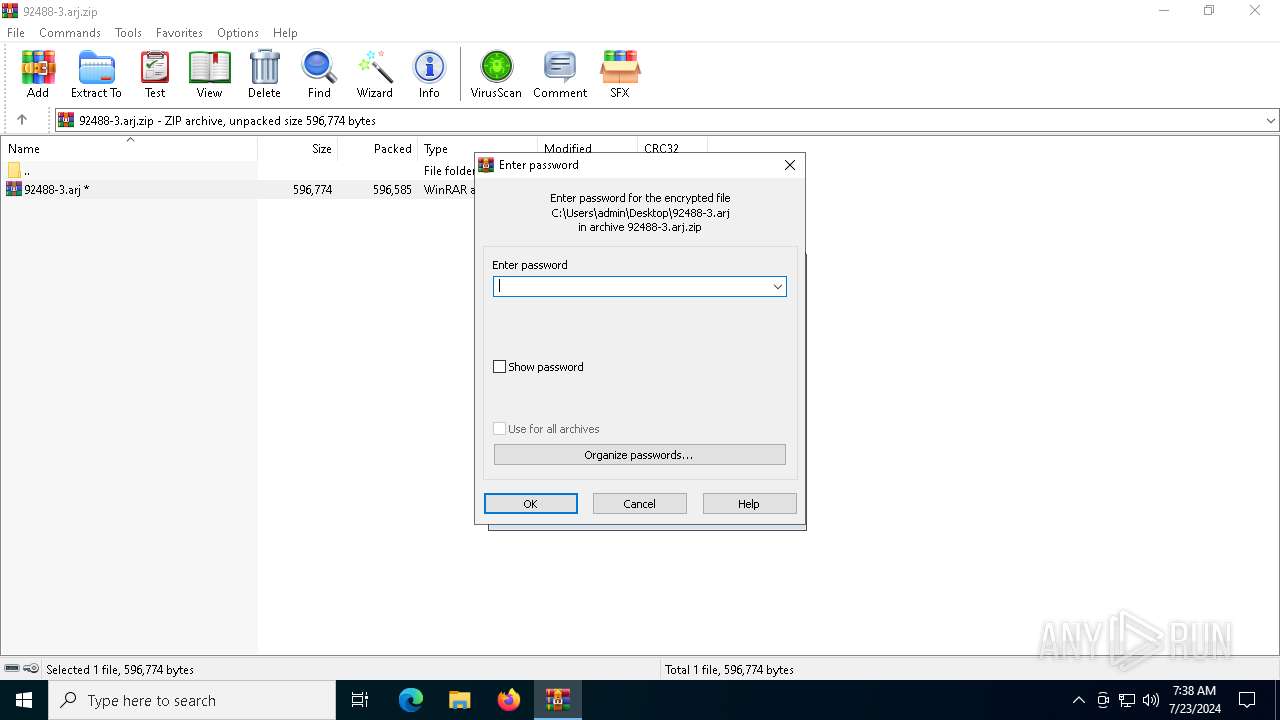
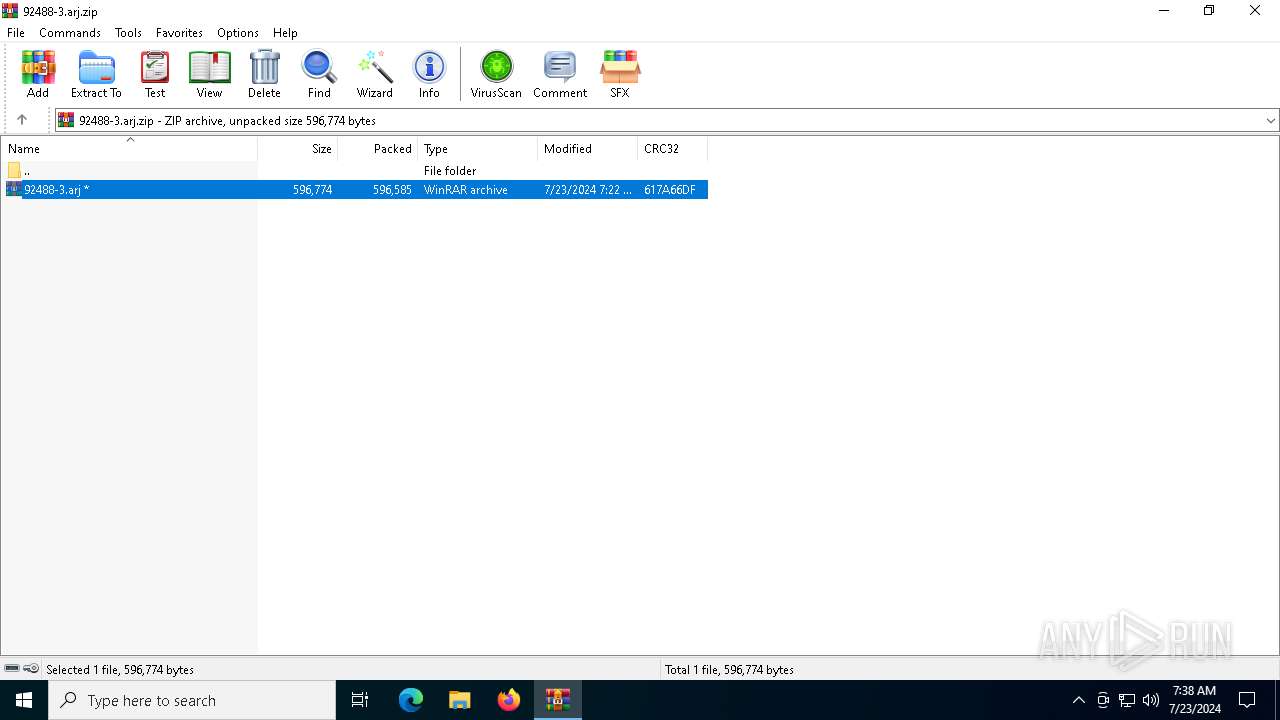
| File name: | 92488-3.arj.zip |
| Full analysis: | https://app.any.run/tasks/fffad4c3-3280-4f93-809d-086a5fbbc1a7 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 23, 2024, 07:38:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6511F26BE85C6B95B8978BEA99E05B1A |
| SHA1: | 5983B5A2BBD72B3350E254841D2C02167A9774F2 |
| SHA256: | 71B20880327E44F73FA96D11AB0932C45321A061731F9867901C80AEFFDA8715 |
| SSDEEP: | 24576:OFba0OSX+EWI1vAbE9b2780n+G2T6OZS74Tux4AOqcrSQ3GDmd4iUt4lYNb:OFba0OSX+EWI1vAbE9b2780n+G2T6OZG |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4192)
Steals credentials from Web Browsers
- Transfer Slip.exe (PID: 7148)
Actions looks like stealing of personal data
- Transfer Slip.exe (PID: 7148)
Scans artifacts that could help determine the target
- Transfer Slip.exe (PID: 7148)
AGENTTESLA has been detected (YARA)
- Transfer Slip.exe (PID: 7148)
SUSPICIOUS
Application launched itself
- Transfer Slip.exe (PID: 6312)
Connects to SMTP port
- Transfer Slip.exe (PID: 7148)
INFO
Manual execution by a user
- Transfer Slip.exe (PID: 6312)
- WinRAR.exe (PID: 1956)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1956)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1956)
Checks supported languages
- Transfer Slip.exe (PID: 6312)
- Transfer Slip.exe (PID: 7148)
Reads the computer name
- Transfer Slip.exe (PID: 6312)
- Transfer Slip.exe (PID: 7148)
Reads the machine GUID from the registry
- Transfer Slip.exe (PID: 6312)
- Transfer Slip.exe (PID: 7148)
Reads Environment values
- Transfer Slip.exe (PID: 7148)
Reads Microsoft Office registry keys
- Transfer Slip.exe (PID: 7148)
Attempt to transmit an email message via SMTP
- Transfer Slip.exe (PID: 7148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(7148) Transfer Slip.exe
Protocolsmtp
Hostsmtp.caritasbolivia.org
Port587
Usernamedireccion2@caritasbolivia.org
PasswordDireccion#22
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:23 07:22:08 |
| ZipCRC: | 0x617a66df |
| ZipCompressedSize: | 596585 |
| ZipUncompressedSize: | 596774 |
| ZipFileName: | 92488-3.arj |
Total processes
144
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1956 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\92488-3.arj" C:\Users\admin\Desktop\92488-3\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4192 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\92488-3.arj.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4688 | "C:\Users\admin\Desktop\92488-3\Transfer Slip.exe" | C:\Users\admin\Desktop\92488-3\Transfer Slip.exe | — | Transfer Slip.exe | |||||||||||
User: admin Company: Huffman and Boyle Integrity Level: MEDIUM Description: Basketball_Simulation Exit code: 4294967295 Version: 7.0.0.0 Modules
| |||||||||||||||
| 6312 | "C:\Users\admin\Desktop\92488-3\Transfer Slip.exe" | C:\Users\admin\Desktop\92488-3\Transfer Slip.exe | — | explorer.exe | |||||||||||
User: admin Company: Huffman and Boyle Integrity Level: MEDIUM Description: Basketball_Simulation Exit code: 0 Version: 7.0.0.0 Modules
| |||||||||||||||
| 6512 | "C:\Users\admin\Desktop\92488-3\Transfer Slip.exe" | C:\Users\admin\Desktop\92488-3\Transfer Slip.exe | — | Transfer Slip.exe | |||||||||||
User: admin Company: Huffman and Boyle Integrity Level: MEDIUM Description: Basketball_Simulation Exit code: 4294967295 Version: 7.0.0.0 Modules
| |||||||||||||||
| 7148 | "C:\Users\admin\Desktop\92488-3\Transfer Slip.exe" | C:\Users\admin\Desktop\92488-3\Transfer Slip.exe | Transfer Slip.exe | ||||||||||||
User: admin Company: Huffman and Boyle Integrity Level: MEDIUM Description: Basketball_Simulation Version: 7.0.0.0 Modules
AgentTesla(PID) Process(7148) Transfer Slip.exe Protocolsmtp Hostsmtp.caritasbolivia.org Port587 Usernamedireccion2@caritasbolivia.org PasswordDireccion#22 | |||||||||||||||
Total events
7 223
Read events
7 196
Write events
27
Delete events
0
Modification events
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\92488-3.arj.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
1
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4192 | WinRAR.exe | C:\Users\admin\Desktop\92488-3.arj | compressed | |
MD5:265F776AA4A6A36E68F037583D6A8B7B | SHA256:6123D640BE1E93E99411C083CB38AFE0ACEE766CCA88C913668EA045F1414530 | |||
| 1956 | WinRAR.exe | C:\Users\admin\Desktop\92488-3\Transfer Slip.exe | executable | |
MD5:C63E26C77A1952A86B7A42774573795A | SHA256:E9D7842178046601F88934E1E6F315C225323465BE6FE64E00B1768567C5AEBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
47
DNS requests
20
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2136 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2976 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4048 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4520 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5368 | SearchApp.exe | 184.86.251.7:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7148 | Transfer Slip.exe | Generic Protocol Command Decode | SURICATA SMTP invalid reply |
7148 | Transfer Slip.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |