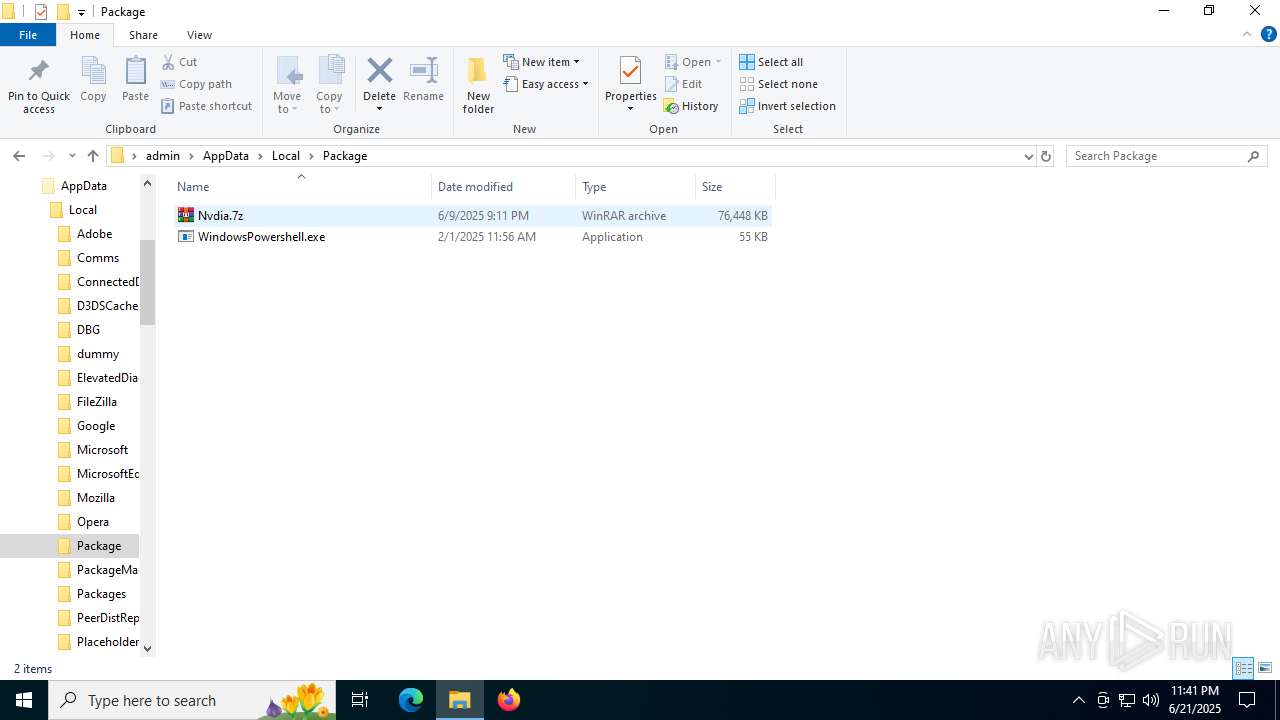
| URL: | https://filebin.net/cyrg4eokmhxqfh8w |
| Full analysis: | https://app.any.run/tasks/9e762f86-c190-4913-8743-7904aa36ad17 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | June 21, 2025, 23:38:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BADDF9C49960A5F747FD31D8F61A374C |
| SHA1: | 9030549D0EEC51042F07C348646A20F39A4794E6 |
| SHA256: | 7195360C5AC12E45F8570E971205024C62BC767811383AE48CB2C00335292FF9 |
| SSDEEP: | 3:N8wLnSpNEPS:2WS |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 188)
- powershell.exe (PID: 2168)
- powershell.exe (PID: 8072)
- powershell.exe (PID: 5824)
- powershell.exe (PID: 7616)
- powershell.exe (PID: 4032)
- powershell.exe (PID: 1440)
- powershell.exe (PID: 8132)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 8080)
- powershell.exe (PID: 3540)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 4084)
- cmd.exe (PID: 6960)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 7976)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 4032)
- cmd.exe (PID: 6896)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 7452)
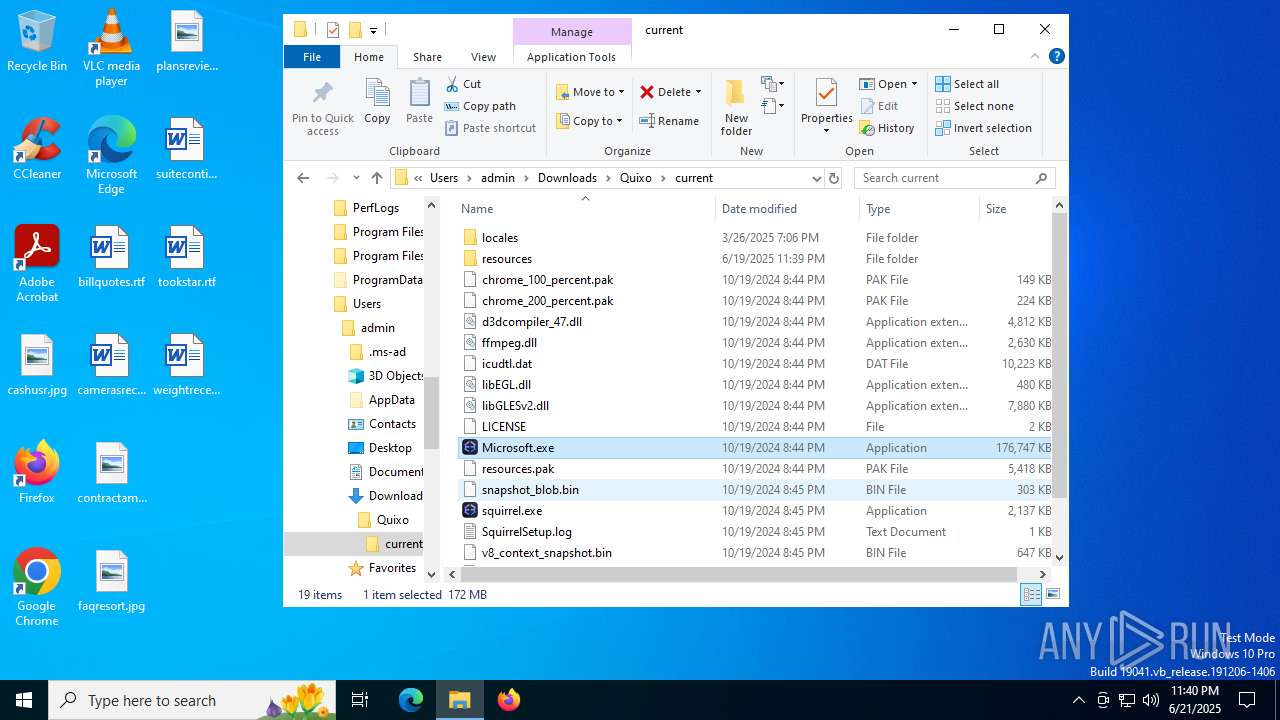
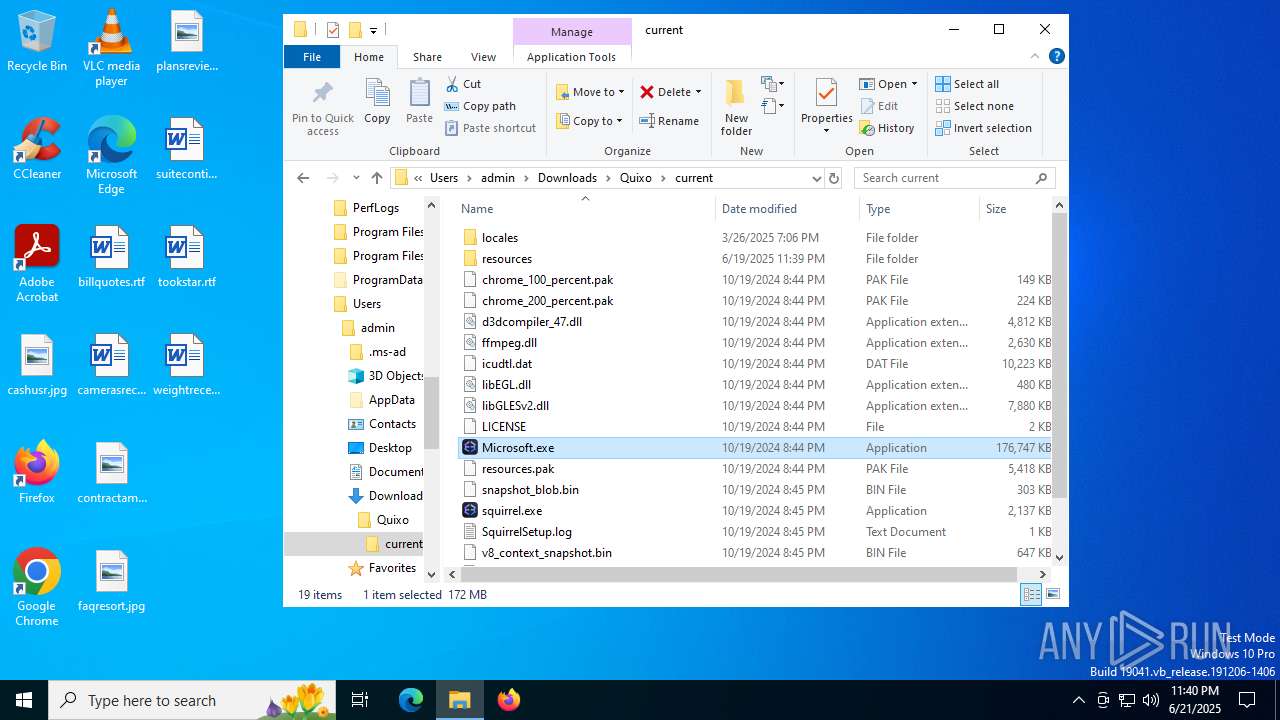
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
UAC/LUA settings modification
- reg.exe (PID: 2276)
Disables Windows Defender
- reg.exe (PID: 6004)
- reg.exe (PID: 3980)
- reg.exe (PID: 5876)
- reg.exe (PID: 7156)
- reg.exe (PID: 2612)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 7608)
Actions looks like stealing of personal data
- SearchFilterHost.exe (PID: 7664)
Steals credentials from Web Browsers
- SearchFilterHost.exe (PID: 7664)
Run PowerShell with an invisible window
- powershell.exe (PID: 3540)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 3540)
REMCOS has been detected
- WindowsPowershell.exe (PID: 7612)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3540)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 3540)
REMCOS has been detected (SURICATA)
- WindowsPowershell.exe (PID: 7612)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3704)
- 7zr1.exe (PID: 3860)
- Microsoft.exe (PID: 3572)
- 77zip.exe (PID: 4048)
- 7zr1.exe (PID: 8108)
- cmd.exe (PID: 360)
Starts CMD.EXE for commands execution
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- SearchFilterHost.exe (PID: 7664)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4084)
- cmd.exe (PID: 6960)
- cmd.exe (PID: 7976)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 4032)
- cmd.exe (PID: 6896)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 7452)
- Microsoft.exe (PID: 1816)
- Microsoft.exe (PID: 3572)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 6492)
- cmd.exe (PID: 6152)
Application launched itself
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- SearchFilterHost.exe (PID: 7664)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 1164)
- WMIC.exe (PID: 6748)
Uses WMIC.EXE to obtain local storage devices information
- cmd.exe (PID: 4560)
- cmd.exe (PID: 7188)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 3876)
- cmd.exe (PID: 7812)
Executable content was dropped or overwritten
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- 7zr1.exe (PID: 3860)
- 77zip.exe (PID: 4048)
- SearchFilterHost.exe (PID: 7664)
- csc.exe (PID: 3876)
- 77zip.exe (PID: 7444)
- 7zr1.exe (PID: 8108)
- cmd.exe (PID: 360)
- cmd.exe (PID: 5232)
Drops 7-zip archiver for unpacking
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- 7zr1.exe (PID: 3860)
- SearchFilterHost.exe (PID: 7664)
- 7zr1.exe (PID: 8108)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Microsoft.exe (PID: 1816)
- Microsoft.exe (PID: 3572)
- SearchFilterHost.exe (PID: 7664)
Checks for external IP
- svchost.exe (PID: 2200)
- Microsoft.exe (PID: 1816)
- curl.exe (PID: 7840)
- Microsoft.exe (PID: 3572)
- SearchFilterHost.exe (PID: 7664)
Starts NET.EXE to display or manage information about active sessions
- net.exe (PID: 5560)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 7260)
- net.exe (PID: 8148)
- net.exe (PID: 8108)
- cmd.exe (PID: 4528)
- net.exe (PID: 5464)
- cmd.exe (PID: 3628)
- cmd.exe (PID: 4576)
- net.exe (PID: 7164)
Hides command output
- cmd.exe (PID: 2072)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2064)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 4528)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 6356)
- cmd.exe (PID: 5692)
- cmd.exe (PID: 3820)
- cmd.exe (PID: 7128)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 2044)
- cmd.exe (PID: 2580)
- cmd.exe (PID: 1652)
- cmd.exe (PID: 7152)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 6224)
- cmd.exe (PID: 6104)
- cmd.exe (PID: 6828)
- cmd.exe (PID: 1688)
- cmd.exe (PID: 3488)
- cmd.exe (PID: 5140)
- cmd.exe (PID: 4648)
- cmd.exe (PID: 432)
- cmd.exe (PID: 6404)
- cmd.exe (PID: 6004)
- cmd.exe (PID: 4700)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 5692)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 1192)
- cmd.exe (PID: 4380)
- cmd.exe (PID: 5140)
Found strings related to reading or modifying Windows Defender settings
- Microsoft.exe (PID: 1816)
Possible usage of Discord/Telegram API has been detected (YARA)
- Microsoft.exe (PID: 3572)
There is functionality for taking screenshot (YARA)
- Microsoft.exe (PID: 5424)
The process creates files with name similar to system file names
- 7zr1.exe (PID: 3860)
- 77zip.exe (PID: 4048)
- 7zr1.exe (PID: 8108)
Runs shell command (SCRIPT)
- cscript.exe (PID: 7608)
The process executes VB scripts
- cmd.exe (PID: 7556)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7608)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 7608)
The process executes Powershell scripts
- cmd.exe (PID: 7776)
Get information on the list of running processes
- SearchFilterHost.exe (PID: 7664)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 7596)
- cmd.exe (PID: 7028)
- cmd.exe (PID: 6420)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 5824)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2656)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 7536)
Possibly malicious use of IEX has been detected
- Microsoft.exe (PID: 3572)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3540)
- cmd.exe (PID: 8076)
- 77zip.exe (PID: 7444)
- cmd.exe (PID: 5232)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3876)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 1636)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3540)
Connects to unusual port
- WindowsPowershell.exe (PID: 7612)
The executable file from the user directory is run by the CMD process
- 77zip.exe (PID: 7444)
Detected use of alternative data streams (AltDS)
- 77zip.exe (PID: 7444)
Reads security settings of Internet Explorer
- WindowsPowershell.exe (PID: 7612)
Contacting a server suspected of hosting an CnC
- WindowsPowershell.exe (PID: 7612)
Created directory related to system
- cmd.exe (PID: 7444)
- cmd.exe (PID: 7452)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5824)
The process deletes folder contents (may hide traces)
- Microsoft.exe (PID: 3572)
Query Microsoft Defender preferences
- Microsoft.exe (PID: 1816)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 1652)
INFO
Manual execution by a user
- WinRAR.exe (PID: 420)
- Microsoft.exe (PID: 3572)
- WinRAR.exe (PID: 3704)
- notepad++.exe (PID: 2680)
- Microsoft.exe (PID: 1816)
- WinRAR.exe (PID: 5824)
- firefox.exe (PID: 6212)
- firefox.exe (PID: 8160)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3704)
The sample compiled with english language support
- WinRAR.exe (PID: 3704)
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- 7zr1.exe (PID: 3860)
- 77zip.exe (PID: 4048)
- SearchFilterHost.exe (PID: 7664)
- 7zr1.exe (PID: 8108)
- cmd.exe (PID: 360)
Checks proxy server information
- slui.exe (PID: 472)
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- SearchFilterHost.exe (PID: 7664)
- WindowsPowershell.exe (PID: 7612)
Reads product name
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 4080)
- WMIC.exe (PID: 1164)
- WMIC.exe (PID: 3908)
- cscript.exe (PID: 7608)
- WMIC.exe (PID: 6748)
- WMIC.exe (PID: 1652)
- powershell.exe (PID: 8080)
- WMIC.exe (PID: 8108)
Reads Environment values
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4080)
- firefox.exe (PID: 1164)
- firefox.exe (PID: 516)
Checks supported languages
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 5424)
- Microsoft.exe (PID: 4860)
- Microsoft.exe (PID: 1816)
- Microsoft.exe (PID: 1212)
- Microsoft.exe (PID: 6228)
- 7zr1.exe (PID: 3860)
- 77zip.exe (PID: 4048)
- curl.exe (PID: 7840)
- SearchFilterHost.exe (PID: 7856)
- SearchFilterHost.exe (PID: 7944)
- SearchFilterHost.exe (PID: 7664)
- WindowsPowershell.exe (PID: 7612)
- csc.exe (PID: 3876)
- cvtres.exe (PID: 1844)
- 77zip.exe (PID: 7444)
- 7zr1.exe (PID: 8108)
- 7z.exe (PID: 7560)
- Microsoft.exe (PID: 7388)
- ComputerDefaults.exe (PID: 4888)
- Microsoft.exe (PID: 3540)
Reads the computer name
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 5424)
- Microsoft.exe (PID: 4860)
- Microsoft.exe (PID: 1816)
- Microsoft.exe (PID: 1212)
- Microsoft.exe (PID: 6228)
- 7zr1.exe (PID: 3860)
- 77zip.exe (PID: 4048)
- curl.exe (PID: 7840)
- SearchFilterHost.exe (PID: 7856)
- SearchFilterHost.exe (PID: 7664)
- SearchFilterHost.exe (PID: 7944)
- WindowsPowershell.exe (PID: 7612)
- 77zip.exe (PID: 7444)
- 7zr1.exe (PID: 8108)
- 7z.exe (PID: 7560)
- Microsoft.exe (PID: 7388)
- Microsoft.exe (PID: 3540)
Process checks computer location settings
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- SearchFilterHost.exe (PID: 7664)
Application launched itself
- chrome.exe (PID: 6620)
- firefox.exe (PID: 6212)
- firefox.exe (PID: 1164)
- firefox.exe (PID: 8160)
- firefox.exe (PID: 516)
Reads the software policy settings
- slui.exe (PID: 472)
- powershell.exe (PID: 8080)
Reads the machine GUID from the registry
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- SearchFilterHost.exe (PID: 7664)
- csc.exe (PID: 3876)
- WindowsPowershell.exe (PID: 7612)
- Microsoft.exe (PID: 7388)
- Microsoft.exe (PID: 3540)
Create files in a temporary directory
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 1816)
- 7zr1.exe (PID: 3860)
- SearchFilterHost.exe (PID: 7664)
- powershell.exe (PID: 8080)
- csc.exe (PID: 3876)
- cvtres.exe (PID: 1844)
- 7zr1.exe (PID: 8108)
Creates files or folders in the user directory
- Microsoft.exe (PID: 3572)
- 77zip.exe (PID: 4048)
- SearchFilterHost.exe (PID: 7664)
- WindowsPowershell.exe (PID: 7612)
- Microsoft.exe (PID: 7388)
- 7z.exe (PID: 7560)
Node.js compiler has been detected
- Microsoft.exe (PID: 3572)
- Microsoft.exe (PID: 5424)
- Microsoft.exe (PID: 4860)
Attempting to use instant messaging service
- Microsoft.exe (PID: 1816)
Reads CPU info
- SearchFilterHost.exe (PID: 7664)
- Microsoft.exe (PID: 1816)
Execution of CURL command
- cmd.exe (PID: 7748)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 4032)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4032)
Creates files in the program directory
- SearchFilterHost.exe (PID: 7664)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8080)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3540)
Creates a new folder
- cmd.exe (PID: 7444)
- cmd.exe (PID: 7452)
- cmd.exe (PID: 7452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(3572) Microsoft.exe
Telegram-Tokens (3)7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c
7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E
8161090604:AAGrWJUef2U3VenSqky6kBx9iLxXYn8M2yE
Telegram-Info-Links
7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c
Get info about bothttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/getMe
Get incoming updateshttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/getUpdates
Get webhookhttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/deleteWebhook?drop_pending_updates=true
7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E
Get info about bothttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/getMe
Get incoming updateshttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/getUpdates
Get webhookhttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/deleteWebhook?drop_pending_updates=true
8161090604:AAGrWJUef2U3VenSqky6kBx9iLxXYn8M2yE
Get info about bothttps://api.telegram.org/bot8161090604:AAGrWJUef2U3VenSqky6kBx9iLxXYn8M2yE/getMe
Get incoming updateshttps://api.telegram.org/bot8161090604:AAGrWJUef2U3VenSqky6kBx9iLxXYn8M2yE/getUpdates
Get webhookhttps://api.telegram.org/bot8161090604:AAGrWJUef2U3VenSqky6kBx9iLxXYn8M2yE/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8161090604:AAGrWJUef2U3VenSqky6kBx9iLxXYn8M2yE/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8161090604:AAGrWJUef2U3VenSqky6kBx9iLxXYn8M2yE/deleteWebhook?drop_pending_updates=true
Telegram-Tokens (2)7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c
7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E
Telegram-Info-Links
7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c
Get info about bothttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/getMe
Get incoming updateshttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/getUpdates
Get webhookhttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7176866895:AAEblaNHKcMpGp3Vo3ZhiSGwpJ4SnjhSx5c/deleteWebhook?drop_pending_updates=true
7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E
Get info about bothttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/getMe
Get incoming updateshttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/getUpdates
Get webhookhttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7921253212:AAFt8Y6IvR75sRCTN4WtukL-xRg_n8Akc5E/deleteWebhook?drop_pending_updates=true
Total processes
461
Monitored processes
309
Malicious processes
12
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | powershell -ExecutionPolicy Bypass -Command "(Get-WmiObject Win32_OperatingSystem).OSArchitecture" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 360 | C:\WINDOWS\system32\cmd.exe /d /s /c "copy "C:\Windows\System32\ComputerDefaults.exe" "C:\Windows \System32\"" | C:\Windows\System32\cmd.exe | Microsoft.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
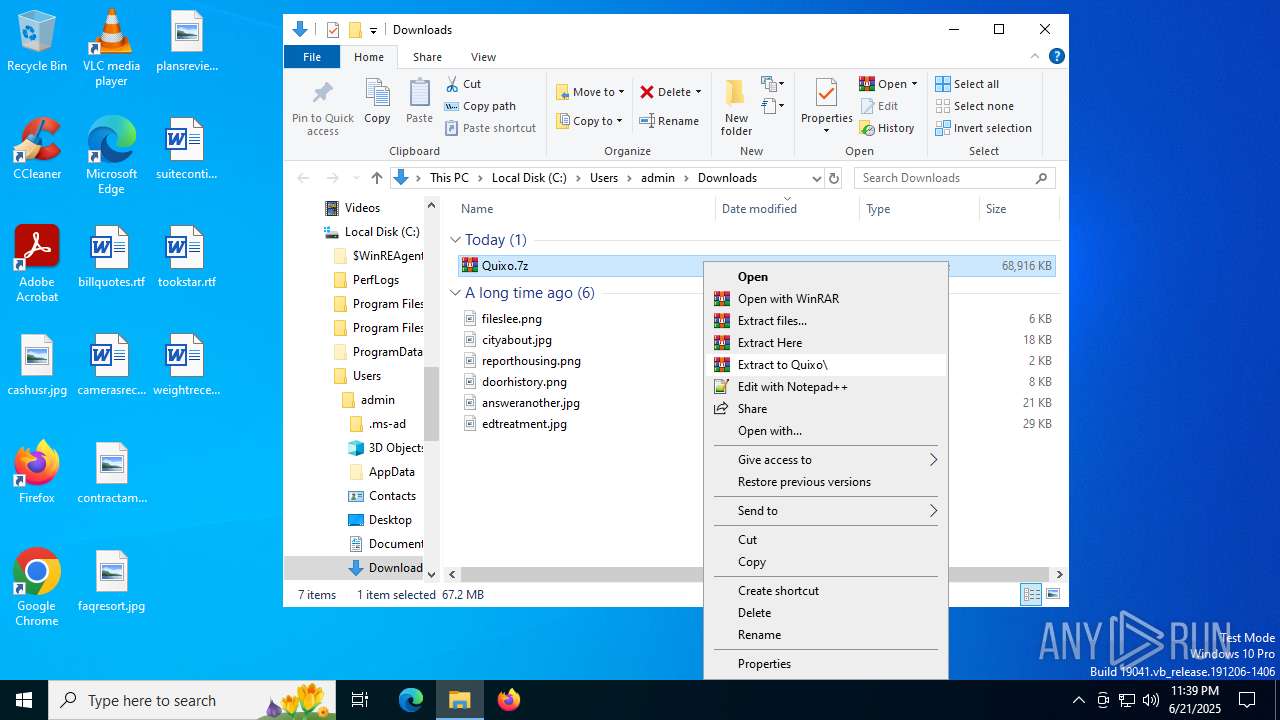
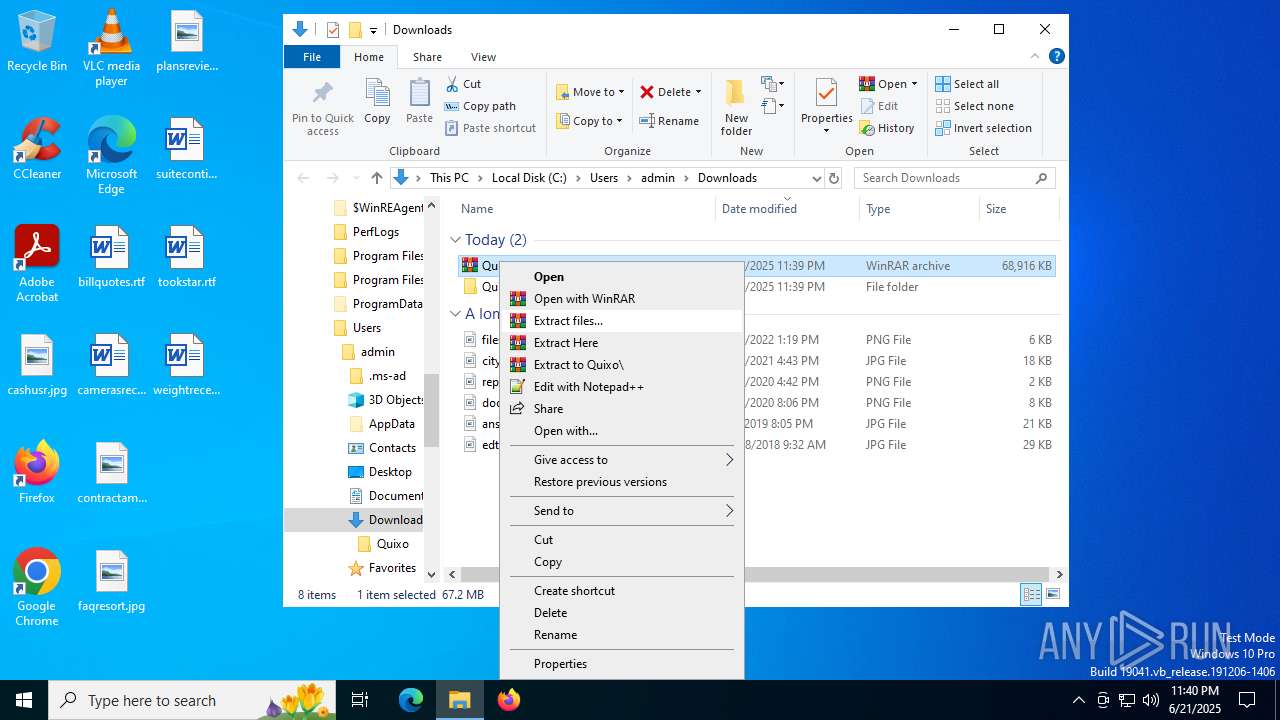
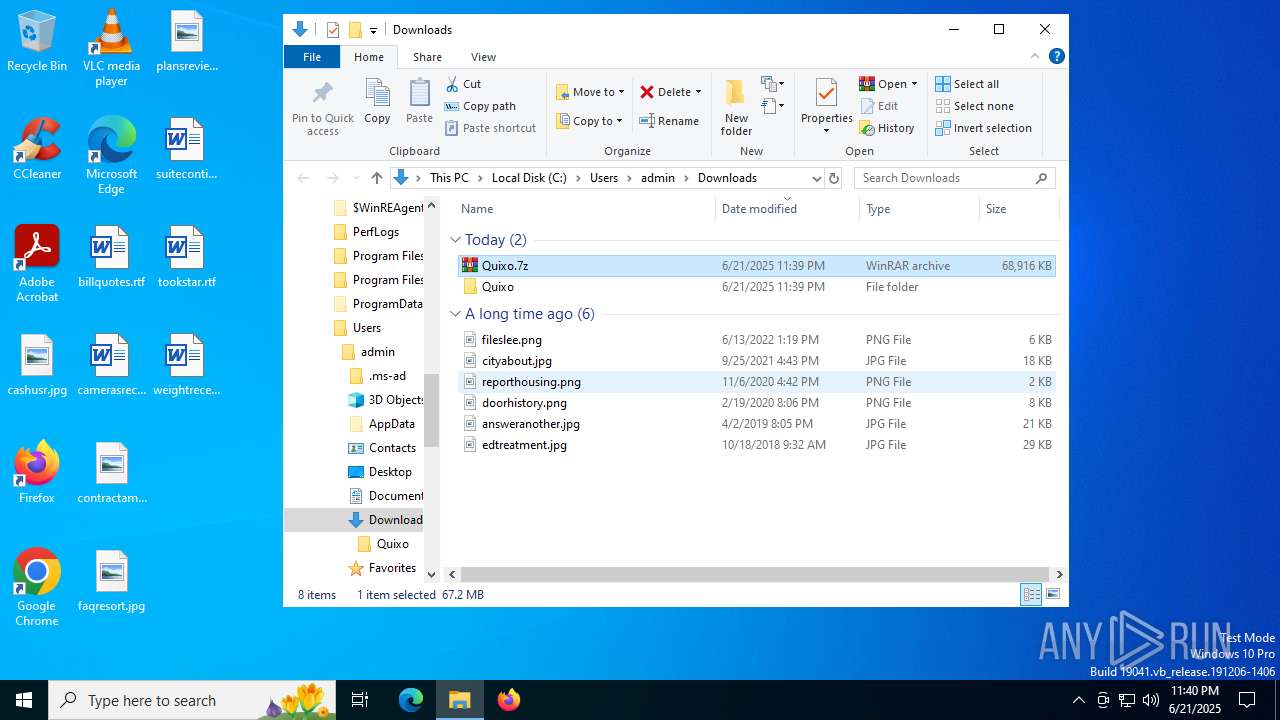
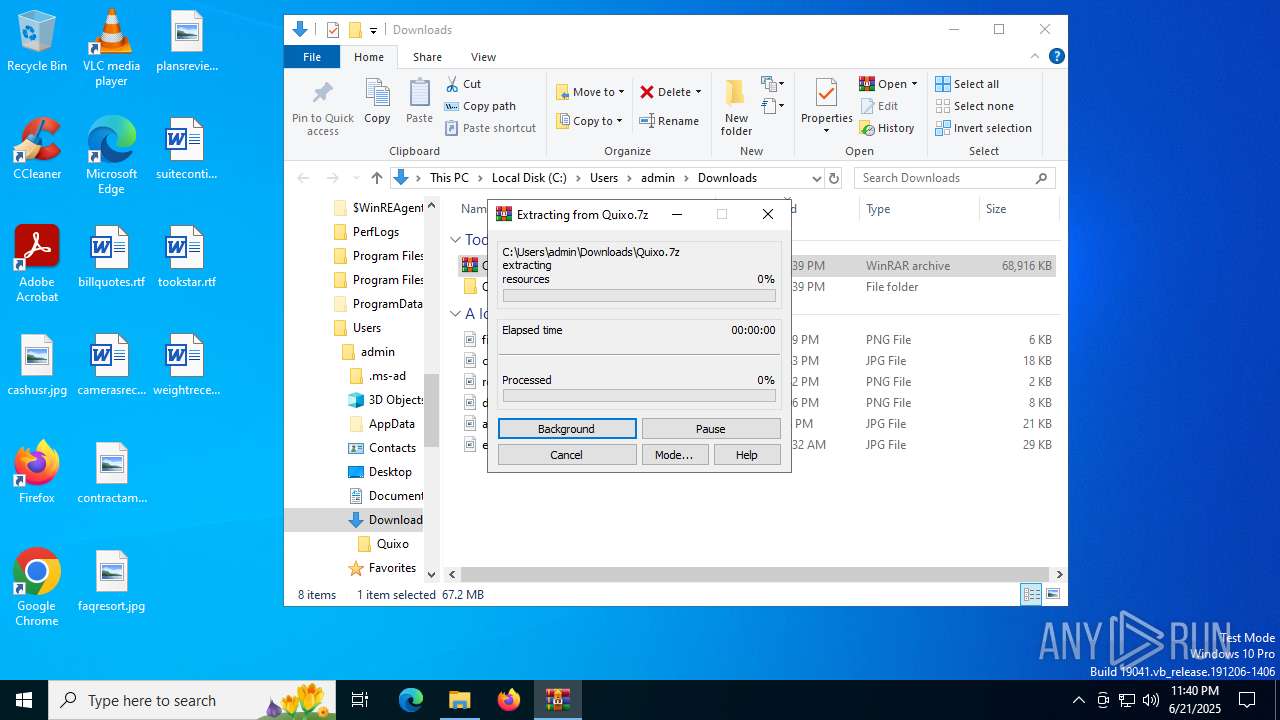
| 420 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Quixo.7z" C:\Users\admin\Downloads\Quixo\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3 Version: 5.91.0 Modules
| |||||||||||||||
| 424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | C:\WINDOWS\system32\cmd.exe /d /s /c "reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableScanOnRealtimeEnable" /t REG_DWORD /d "1" /f" | C:\Windows\System32\cmd.exe | — | Microsoft.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | reg delete "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" /v "SecurityHealth" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
153 760
Read events
153 375
Write events
349
Delete events
36
Modification events
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (6620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | GoogleChromeAutoLaunch_A822CA3D40D4B8944864CFEA751D8D57 |
Value: | |||
| (PID) Process: | (420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
35
Suspicious files
664
Text files
153
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF176522.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF176542.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF176542.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF176542.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF176551.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF176551.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
76
TCP/UDP connections
236
DNS requests
223
Threats
117
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3100 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6948 | chrome.exe | GET | 200 | 142.250.186.110:80 | http://clients2.google.com/time/1/current?cup2key=8:KhF8A_hMpFAYKR_1Gm2g3EWF05Lk3yS3ovHMO7VfFc0&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 64.7.118.152:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2512 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2512 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1816 | Microsoft.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
1816 | Microsoft.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
1816 | Microsoft.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6672 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6948 | chrome.exe | 216.58.212.170:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
6948 | chrome.exe | 88.99.137.18:443 | filebin.net | Hetzner Online GmbH | DE | suspicious |
6948 | chrome.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6948 | chrome.exe | 142.250.186.110:80 | clients2.google.com | GOOGLE | US | whitelisted |
3100 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
filebin.net |
| unknown |
clients2.google.com |
| whitelisted |
accounts.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6948 | chrome.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Abused File Sharing Domain in DNS Lookup (filebin .net) |
6948 | chrome.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Abused File Sharing Domain in DNS Lookup (filebin .net) |
6948 | chrome.exe | Misc activity | ET INFO Observed Abused File Sharing Domain in TLS SNI (filebin .net) |
6948 | chrome.exe | Misc activity | ET INFO Observed Abused File Sharing Domain in TLS SNI (filebin .net) |
6948 | chrome.exe | Misc activity | ET INFO Observed Abused File Sharing Domain in TLS SNI (filebin .net) |
6948 | chrome.exe | Misc activity | ET INFO Observed Abused File Sharing Domain in TLS SNI (filebin .net) |
6948 | chrome.exe | Misc activity | ET INFO Observed Abused File Sharing Domain in TLS SNI (filebin .net) |
6948 | chrome.exe | Misc activity | ET INFO Observed Abused File Sharing Domain in TLS SNI (filebin .net) |
6948 | chrome.exe | Misc activity | ET INFO Observed Abused File Sharing Domain in TLS SNI (filebin .net) |
6948 | chrome.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Abused File Sharing Domain in DNS Lookup (filebin .net) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|