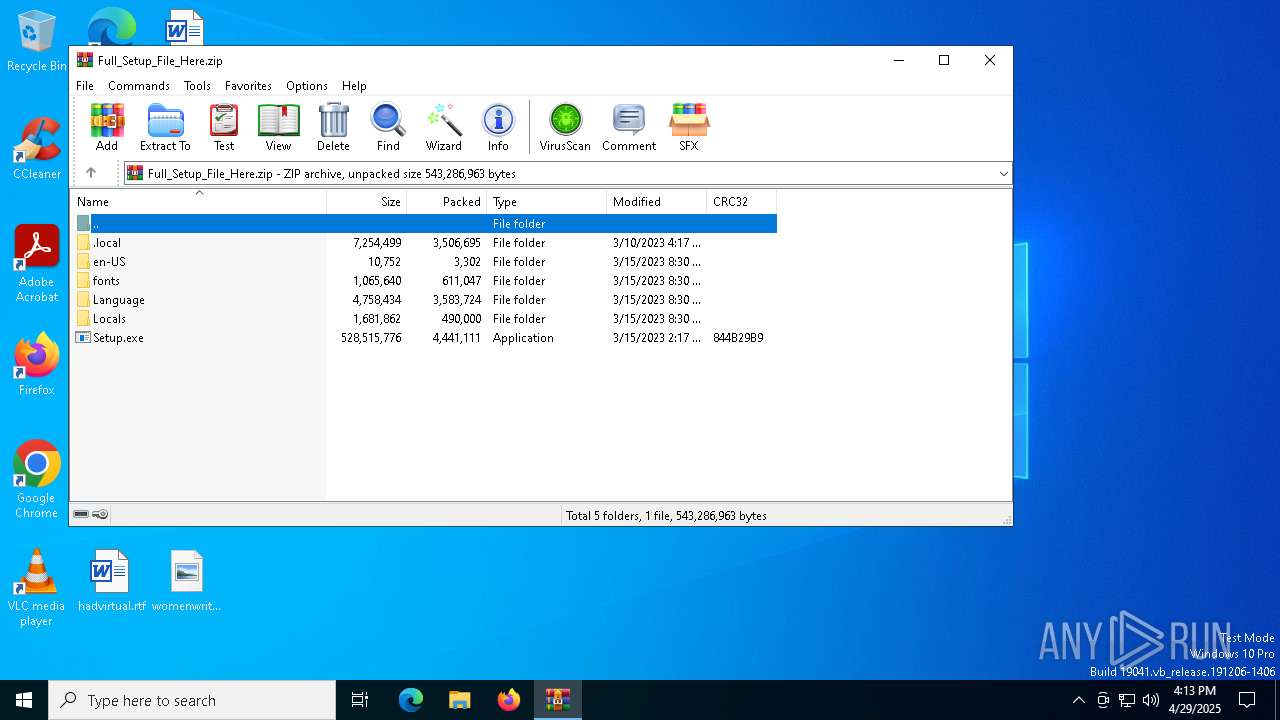
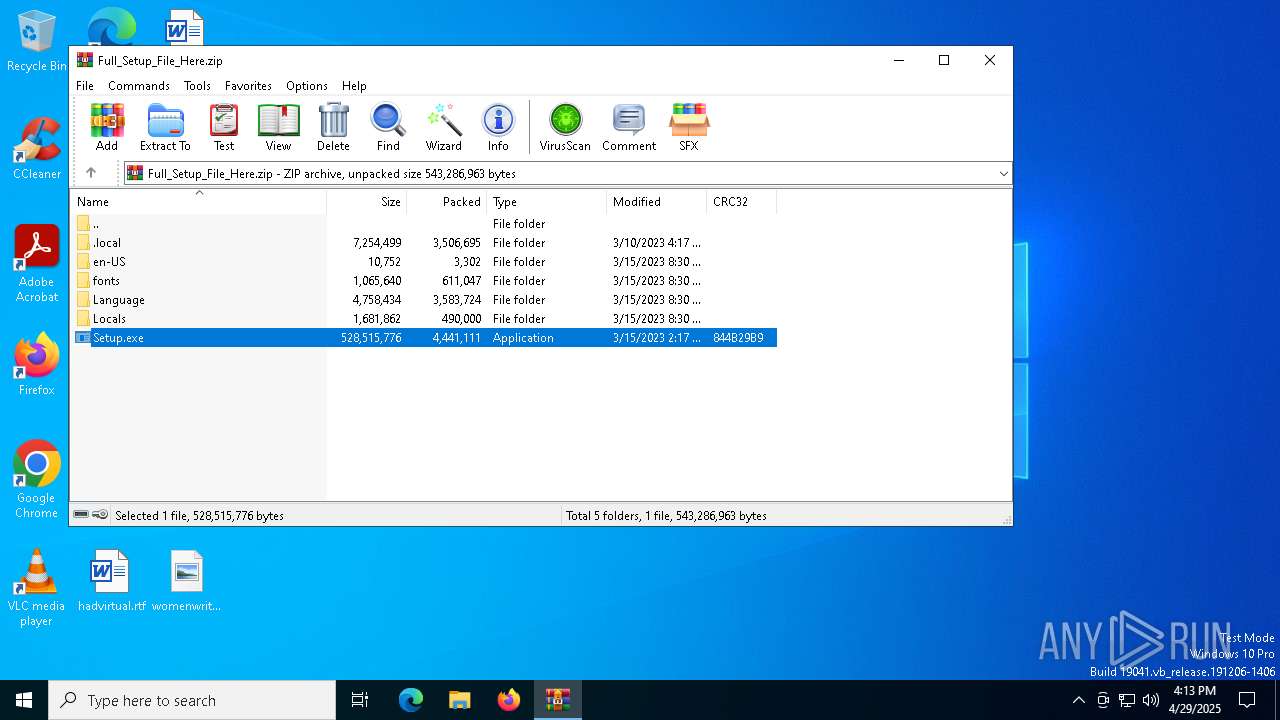
| File name: | Full_Setup_File_Here.zip |
| Full analysis: | https://app.any.run/tasks/dfdb6aa5-10cc-47e6-bae9-e4fb5400fc4b |
| Verdict: | Malicious activity |
| Threats: | Raccoon is an info stealer type malware available as a Malware as a Service. It can be obtained for a subscription and costs $200 per month. Raccoon malware has already infected over 100,000 devices and became one of the most mentioned viruses on the underground forums in 2019. |
| Analysis date: | April 29, 2025, 16:12:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | AA2F8BB06E8DF9513FDD6239575E1144 |
| SHA1: | A804EC4B69DC1E70069BEA8E7F31E017F682609C |
| SHA256: | 7188F0E5B7EA30CA871BD0FB9C0E1E55B6D1D55EECE9F716DA591D65A848CA21 |
| SSDEEP: | 98304:BmKndhku8q16aOD0LugfHNSt+oS99i98EH/kD468RL3IroSiMkmbduo62S9F9t68:1E7SMEesZltBIsiNMtTI1Jl |
MALICIOUS
Connects to the CnC server
- jsc.exe (PID: 7664)
RACCOON has been detected (SURICATA)
- jsc.exe (PID: 7664)
SUSPICIOUS
Reads the BIOS version
- Setup.exe (PID: 7468)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4812)
- jsc.exe (PID: 7664)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4812)
Connects to the server without a host name
- jsc.exe (PID: 7664)
INFO
Reads the machine GUID from the registry
- Setup.exe (PID: 7468)
- jsc.exe (PID: 7664)
Checks supported languages
- jsc.exe (PID: 7664)
- Setup.exe (PID: 7468)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4812)
The sample compiled with english language support
- WinRAR.exe (PID: 4812)
Reads the computer name
- jsc.exe (PID: 7664)
- Setup.exe (PID: 7468)
The sample compiled with russian language support
- WinRAR.exe (PID: 4812)
Checks proxy server information
- jsc.exe (PID: 7664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (42.1) |
|---|---|---|
| .zip | | | ZIP compressed archive (21) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:03:16 02:00:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | en-US/ |
Total processes
138
Monitored processes
15
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4812 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Full_Setup_File_Here.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7468 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Schneider Electric Software, LLC. Integrity Level: MEDIUM Description: InTouch WindowMaker Exit code: 0 Version: 2400.0852.0527.0052 Modules
| |||||||||||||||
| 7532 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\RegSvcs.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7544 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7556 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\vbc.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 4294967295 Version: 14.8.9037.0 Modules
| |||||||||||||||
| 7568 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7580 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_wp.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_wp.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_wp.exe Exit code: 4294967295 Version: 4.8.9220.0 built by: NET481REL1LAST_C Modules
| |||||||||||||||
| 7592 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_regbrowsers.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_regbrowsers.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regbrowsers.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7604 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_compiler.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7616 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngentask.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngentask.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework optimization service Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
2 517
Read events
2 506
Write events
11
Delete events
0
Modification events
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Full_Setup_File_Here.zip | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7664) jsc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7664) jsc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
3
Suspicious files
152
Text files
234
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\fonts\dosapp.fon | binary | |
MD5:8A5853EBFC046F428DD31C5F3AE217EF | SHA256:0DA0D4ED89FD1E8810C7F2CDB5372ABFB02CB3D031ACACC1A5BBC853F879C2BD | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\fonts\8514sys.fon | binary | |
MD5:BB8F1F693BEBF6C738E47B68C4DB7D06 | SHA256:DC7E1C9BB168E22B7A8B1A10C5D9555D71EA8486DC0D628FA17D117698BAE61B | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\Language\az.txt | text | |
MD5:81B732A8B4206FB747BFBFE524DDE192 | SHA256:CAEC460E73BD0403C2BCDE7E773459BEA9112D1BFACBE413D4F21E51A5762BA6 | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\fonts\trebucbi.ttf | binary | |
MD5:7B0201D14BB2A17514480EAFD86DA51F | SHA256:87942234AB0CC4400088648BEF8D1F7AFC4C44E676C7ED6B32CA31462C18307D | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\fonts\verdanab.ttf | binary | |
MD5:215ACCAAD3DD60E8A5AB1B110F79D507 | SHA256:F3245F5F38F61BD1CEEFB0F1338A5B88A21E6220832C2F43A38BBC7E1547C36F | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\Language\be.txt | text | |
MD5:3C21135144AC7452E7DB66F0214F9D68 | SHA256:D095879B8BBC67A1C9875C5E9896942BACF730BD76155C06105544408068C59E | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\Language\an.txt | text | |
MD5:BF8564B2DAD5D2506887F87AEE169A0A | SHA256:0E8DD119DFA6C6C1B3ACA993715092CDF1560947871092876D309DBC1940A14A | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\fonts\smalle.fon | binary | |
MD5:ABC2DDA06AC9D95B210A3A805D724391 | SHA256:DE416395301DA32C96BF34625483EA6ECDCDAAEB9FF72CDCA00B5AF4D7092DA9 | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\fonts\symbol.ttf | binary | |
MD5:3E443984997631A694DABF0FBA9C8693 | SHA256:BBF1192965E5266FBF23370416337D2861FC1E8BD349DEF93F2994BA67382FC3 | |||
| 4812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4812.426\fonts\verdana.ttf | binary | |
MD5:5587517D47893E1470AB2296EB609C93 | SHA256:6A8481FE107EE547893C018B13DBA291C2020BEC3DE5DA6525D9AC09F6BC2105 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
44
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7664 | jsc.exe | POST | 404 | 45.9.74.36:80 | http://45.9.74.36/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7664 | jsc.exe | 45.9.74.36:80 | — | Delta Ltd | SC | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
198.187.3.20.in-addr.arpa |
| unknown |
6.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7664 | jsc.exe | A Network Trojan was detected | ET MALWARE Win32/RecordBreaker CnC Checkin M1 |