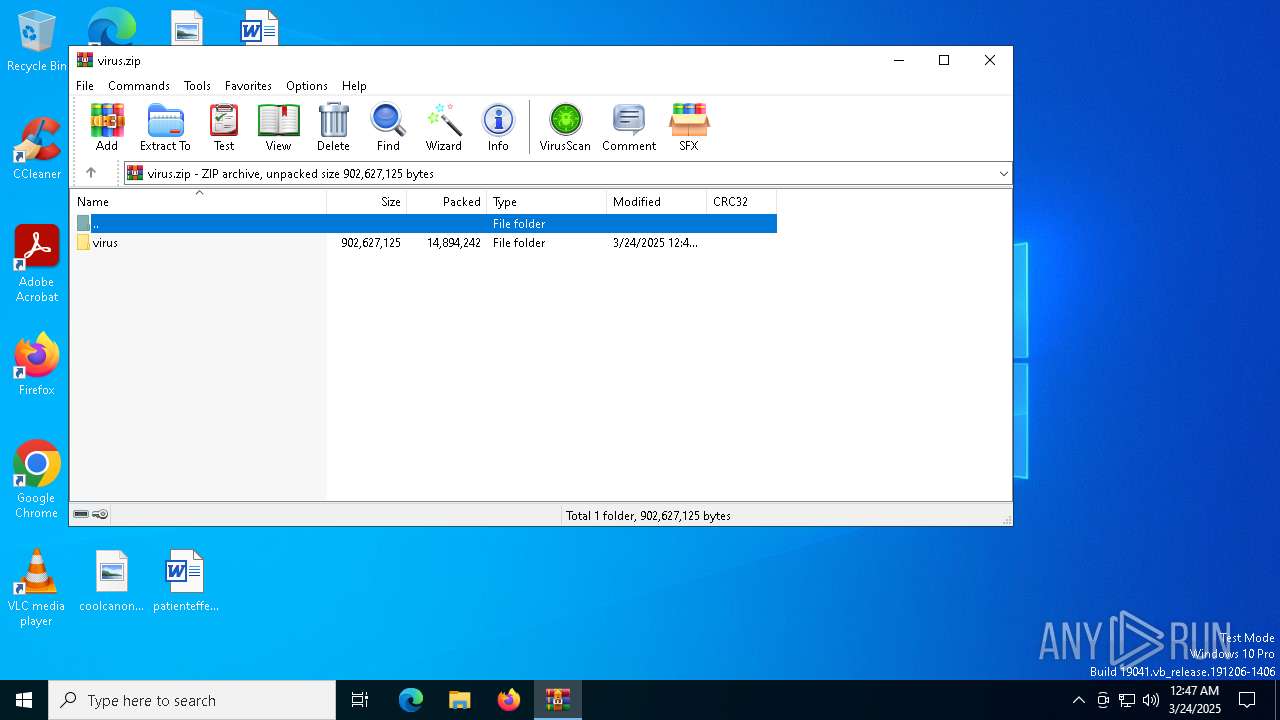
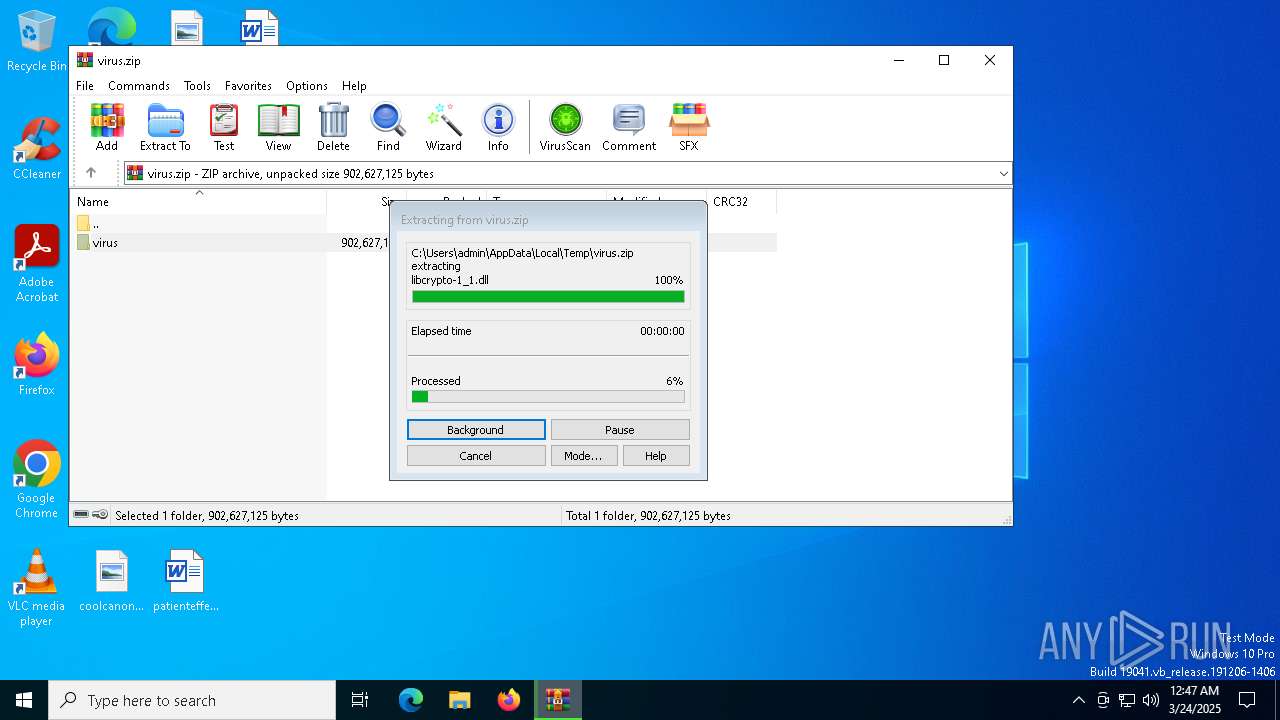
| File name: | virus.zip |
| Full analysis: | https://app.any.run/tasks/111be40b-626a-463f-bb7f-827e79096f58 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | March 24, 2025, 00:47:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 200E60440114A7D93916B0D862E44C24 |
| SHA1: | 428E8CC692E70299996EF5BCF506F7212417CDA6 |
| SHA256: | 712A0749FD010E635EB1EA6D8D9EB685CC52FB353043A140B33F1C4902DD94D9 |
| SSDEEP: | 196608:piLtGpDWFMcnkqhzRRNT8HWTK1jm8bRVCqdz:vpenHRPTrTCjm8FVdz |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7412)
Known privilege escalation attack
- dllhost.exe (PID: 8188)
LUMMA mutex has been found
- svchost.exe (PID: 660)
- svchost.exe (PID: 6480)
Steals credentials from Web Browsers
- svchost.exe (PID: 660)
- svchost.exe (PID: 6480)
Executing a file with an untrusted certificate
- kcpytkt.exe (PID: 7800)
SUSPICIOUS
Executable content was dropped or overwritten
- Set-up.exe (PID: 7300)
- Set-up.exe (PID: 5404)
Process drops legitimate windows executable
- Set-up.exe (PID: 7300)
- WinRAR.exe (PID: 7412)
The process drops C-runtime libraries
- Set-up.exe (PID: 7300)
Starts application with an unusual extension
- Set-up.exe (PID: 7300)
- Set-up.exe (PID: 1512)
- Set-up.exe (PID: 5404)
- Set-up.exe (PID: 680)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5728)
Potential Corporate Privacy Violation
- svchost.exe (PID: 660)
Searches for installed software
- svchost.exe (PID: 660)
- svchost.exe (PID: 6480)
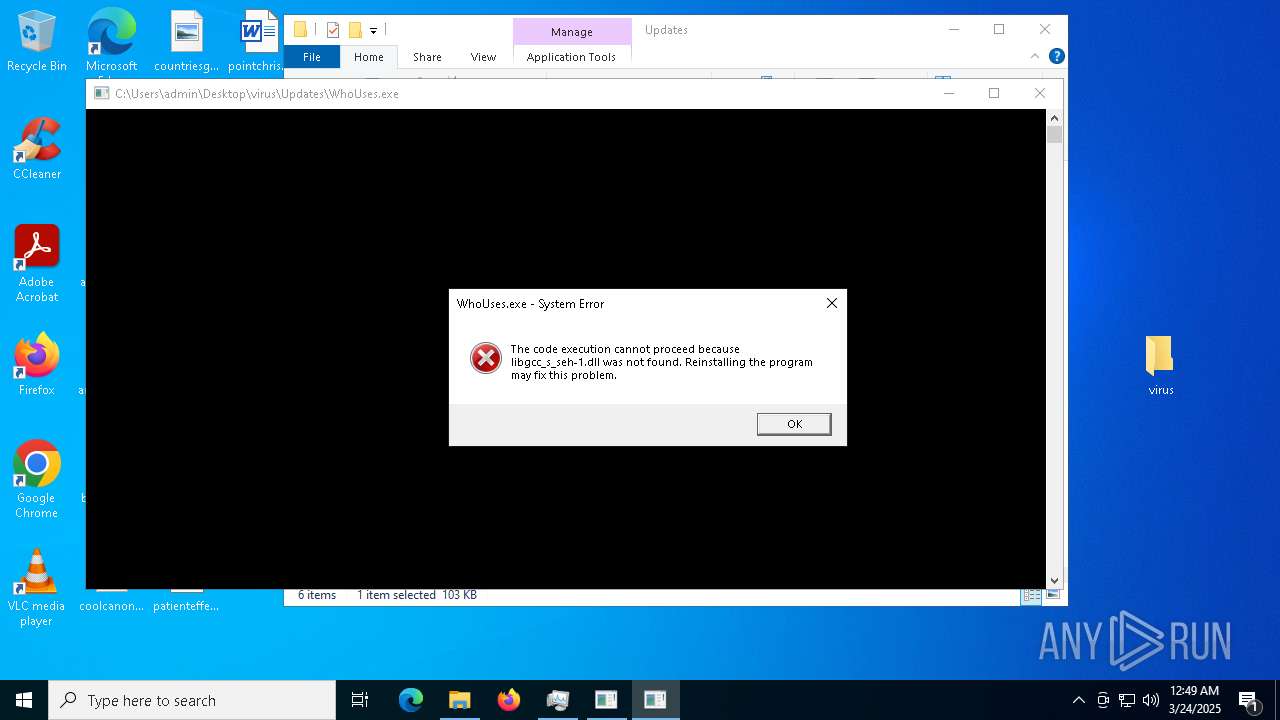
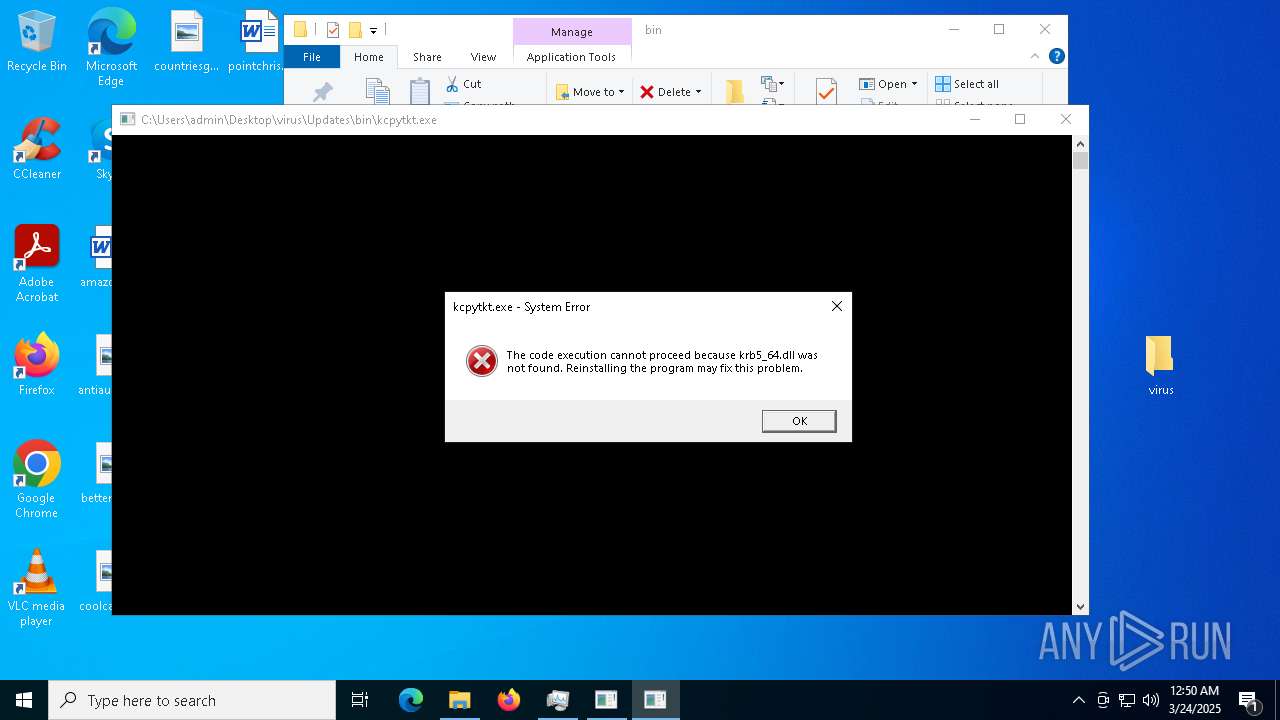
Executes application which crashes
- git-credential-manager-ui.exe (PID: 7000)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4000)
- BackgroundTransferHost.exe (PID: 5556)
- BackgroundTransferHost.exe (PID: 7236)
- BackgroundTransferHost.exe (PID: 5728)
- BackgroundTransferHost.exe (PID: 4988)
- dllhost.exe (PID: 8188)
- Taskmgr.exe (PID: 8088)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 5556)
- slui.exe (PID: 6436)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 5556)
- slui.exe (PID: 7584)
- slui.exe (PID: 6436)
Creates files in the program directory
- Set-up.exe (PID: 7300)
Checks supported languages
- Set-up.exe (PID: 7300)
- Set-up.exe (PID: 1512)
- more.com (PID: 5680)
- more.com (PID: 1188)
- MSBuild.exe (PID: 5988)
- Set-up.exe (PID: 5404)
- more.com (PID: 8144)
- MSBuild.exe (PID: 2420)
- ShellExperienceHost.exe (PID: 5728)
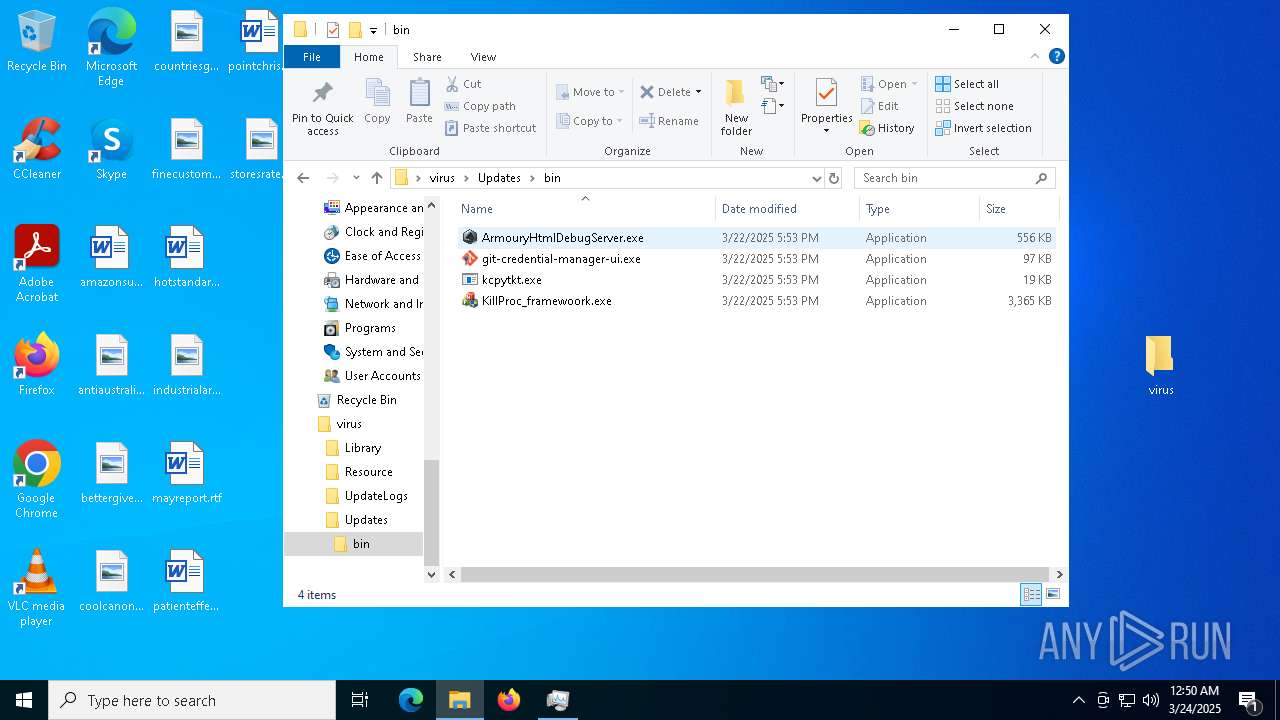
- KillProc_framewoork.exe (PID: 4200)
- git-credential-manager-ui.exe (PID: 7000)
- ArmouryHtmlDebugServer.exe (PID: 7948)
- Set-up.exe (PID: 680)
- more.com (PID: 2840)
- Set-up.exe (PID: 2852)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7412)
The sample compiled with russian language support
- WinRAR.exe (PID: 7412)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 5556)
- WerFault.exe (PID: 2552)
The sample compiled with english language support
- Set-up.exe (PID: 7300)
- WinRAR.exe (PID: 7412)
- Set-up.exe (PID: 5404)
Manual execution by a user
- Set-up.exe (PID: 7300)
- Taskmgr.exe (PID: 7768)
- Taskmgr.exe (PID: 8088)
- Set-up.exe (PID: 5404)
- Acrobat.exe (PID: 3032)
- KillProc_framewoork.exe (PID: 7496)
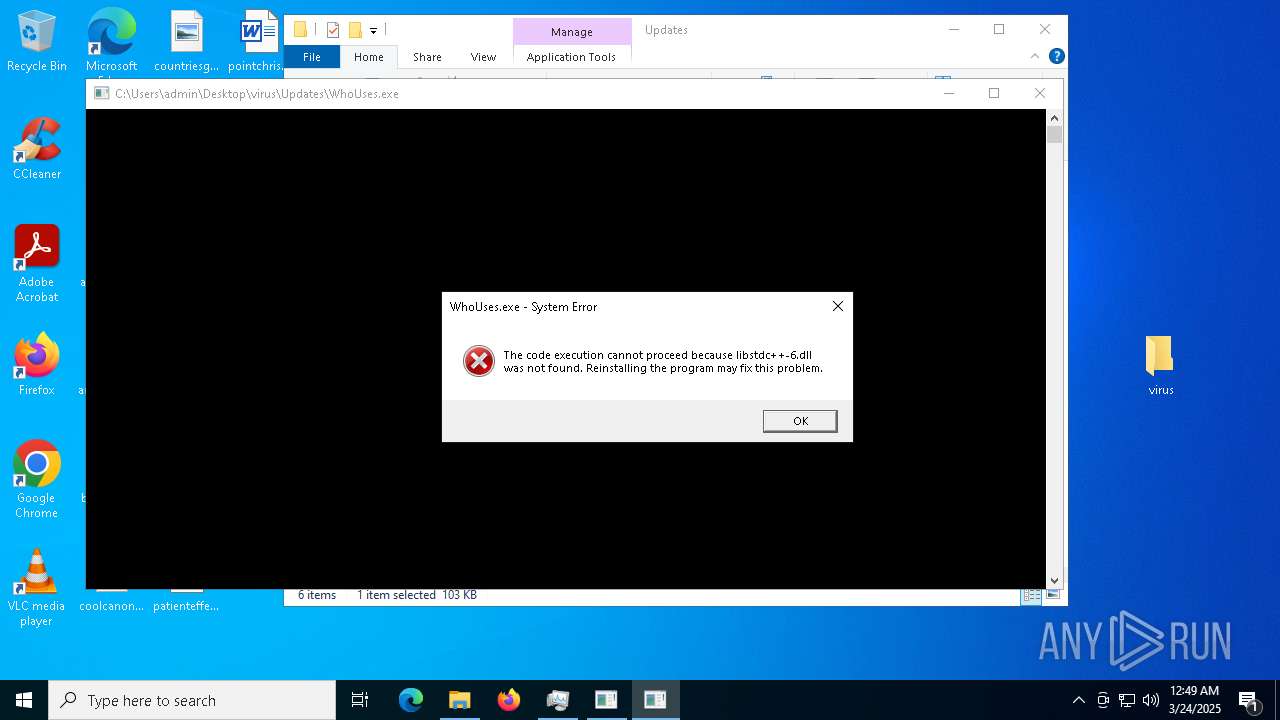
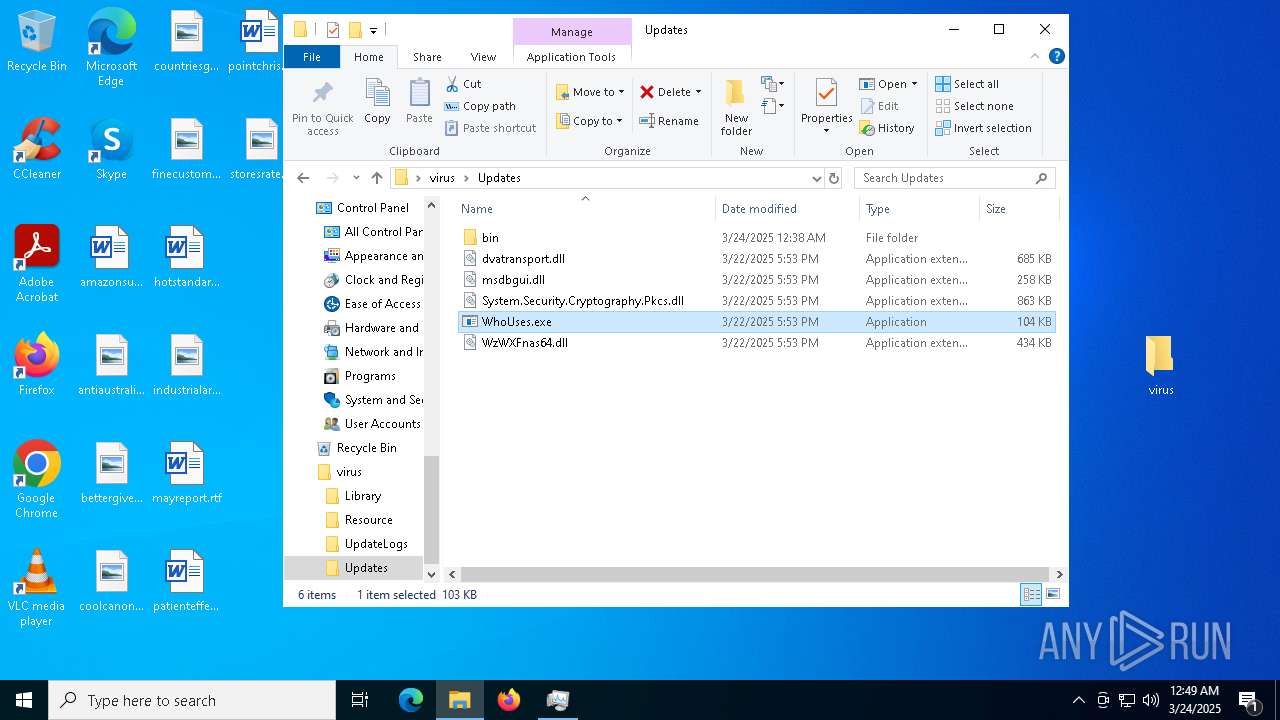
- WhoUses.exe (PID: 4016)
- kcpytkt.exe (PID: 7800)
- KillProc_framewoork.exe (PID: 4200)
- git-credential-manager-ui.exe (PID: 7000)
- Set-up.exe (PID: 680)
- ArmouryHtmlDebugServer.exe (PID: 7948)
Reads the computer name
- Set-up.exe (PID: 7300)
- more.com (PID: 5680)
- Set-up.exe (PID: 1512)
- MSBuild.exe (PID: 5988)
- more.com (PID: 1188)
- ShellExperienceHost.exe (PID: 5728)
- Set-up.exe (PID: 5404)
- MSBuild.exe (PID: 2420)
- more.com (PID: 8144)
- git-credential-manager-ui.exe (PID: 7000)
- Set-up.exe (PID: 680)
- Set-up.exe (PID: 2852)
- more.com (PID: 2840)
Create files in a temporary directory
- Set-up.exe (PID: 7300)
- Set-up.exe (PID: 1512)
- Set-up.exe (PID: 5404)
- Set-up.exe (PID: 2852)
- Set-up.exe (PID: 680)
Reads the machine GUID from the registry
- more.com (PID: 5680)
- MSBuild.exe (PID: 5988)
- MSBuild.exe (PID: 2420)
- git-credential-manager-ui.exe (PID: 7000)
- more.com (PID: 2840)
Application launched itself
- Acrobat.exe (PID: 3032)
- AcroCEF.exe (PID: 7912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (21) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:24 00:46:26 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | virus/ |
Total processes
195
Monitored processes
51
Malicious processes
4
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | git-credential-manager-ui.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\WINDOWS\system32\svchost.exe" | C:\Windows\SysWOW64\svchost.exe | MSBuild.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\virus\Set-up.exe" | C:\Users\admin\Desktop\virus\Set-up.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 736 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | Set-up.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1760 --field-trial-handle=1604,i,4417630830600772824,6645803987201412889,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\Desktop\virus\Set-up.exe" | C:\Users\admin\Desktop\virus\Set-up.exe | — | dllhost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1676 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | Set-up.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
21 940
Read events
21 745
Write events
184
Delete events
11
Modification events
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\virus.zip | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7236) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7236) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
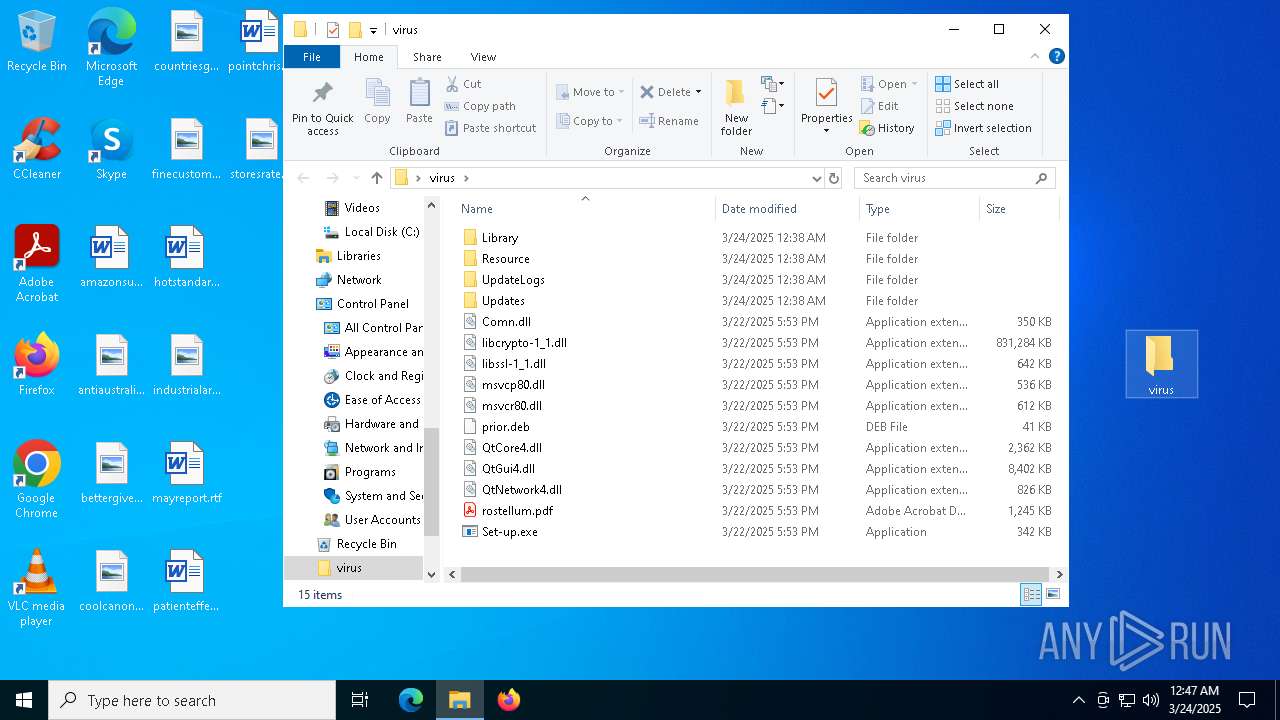
Executable files
61
Suspicious files
125
Text files
60
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\libcrypto-1_1.dll | — | |
MD5:— | SHA256:— | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\clang_rt.asan_dynamic-i386.dll | executable | |
MD5:031560A519FFA0584649AFD7E10B3B1F | SHA256:6EF8C965BBC5D82CD01CD8F66E94899F5D357C0E290C813F9CCAC42AAB5D7E8C | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\clui.dll | executable | |
MD5:89F3712DE56BE440A0B1D691577204F9 | SHA256:723C6763A9EFD776CD435858BC74659205A9F2EB5AB4F381E11C7B5D9C3AD32F | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\Microsoft.DotNet.Interactive.VisualStudio.dll | executable | |
MD5:25CE12A0BE426368FD1B7D8F77308140 | SHA256:993EA8DF3D1274C3B765C9F20A1D85E1219516CFCBB9412AC0B9BC81CF9827D2 | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Comn.dll | executable | |
MD5:F76F5A566CBB5F561D26E7ACA841C723 | SHA256:9DAAED978746AA51B30F27104D89CC16230042E41427E610A8E609CDBCFDC964 | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\EnumIndex.dll | executable | |
MD5:BA885CBC2E0CE2D0AEC9DA6E09F25A7B | SHA256:DF6EDCFD9DF09A338B08F127EE1E8063FE4B048C0215343E2DC8DB983AF5E34C | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\cpfecl.iOS.x86.dll | executable | |
MD5:ADACDD3A75919DA648B899C7B91874EB | SHA256:33F3FB246F7C6B367114C0276FB390C09B70E24F14B6D106C040FBBCF89A0BA2 | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\HResultCheck.dll | executable | |
MD5:E0428C7C3A82B9A519556410BF6281FF | SHA256:1AFD8E9B394010BA7E216D8233BE4CA829AB0D6B45ACEA099CABF41F4A4B7A3B | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\libbluray.dll | executable | |
MD5:A87AA7013CBED231DB08D6141C63BDF0 | SHA256:C47A372B84409DB9DB0D63A2F17AF519EE82F74075CAEC61C6A626A137094CCE | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.4609\virus\Library\msdarem.dll | executable | |
MD5:6C59E0BA258A59896C195A67138B4052 | SHA256:4084E94BB7396E634F0E6CD4F735E9AA5A3AB5422966B76B5ED072C770809057 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
46
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5556 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7652 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6512 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6512 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7652 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
660 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Dropbox.com Offsite File Backup in Use |