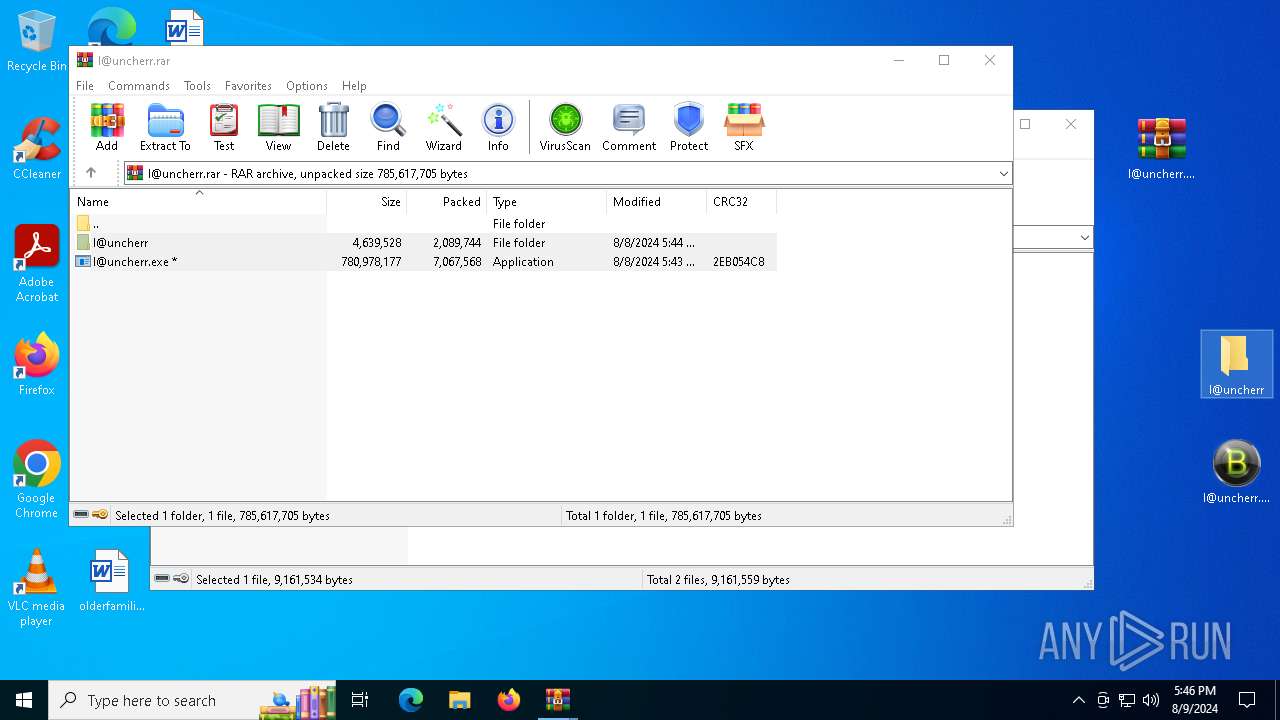
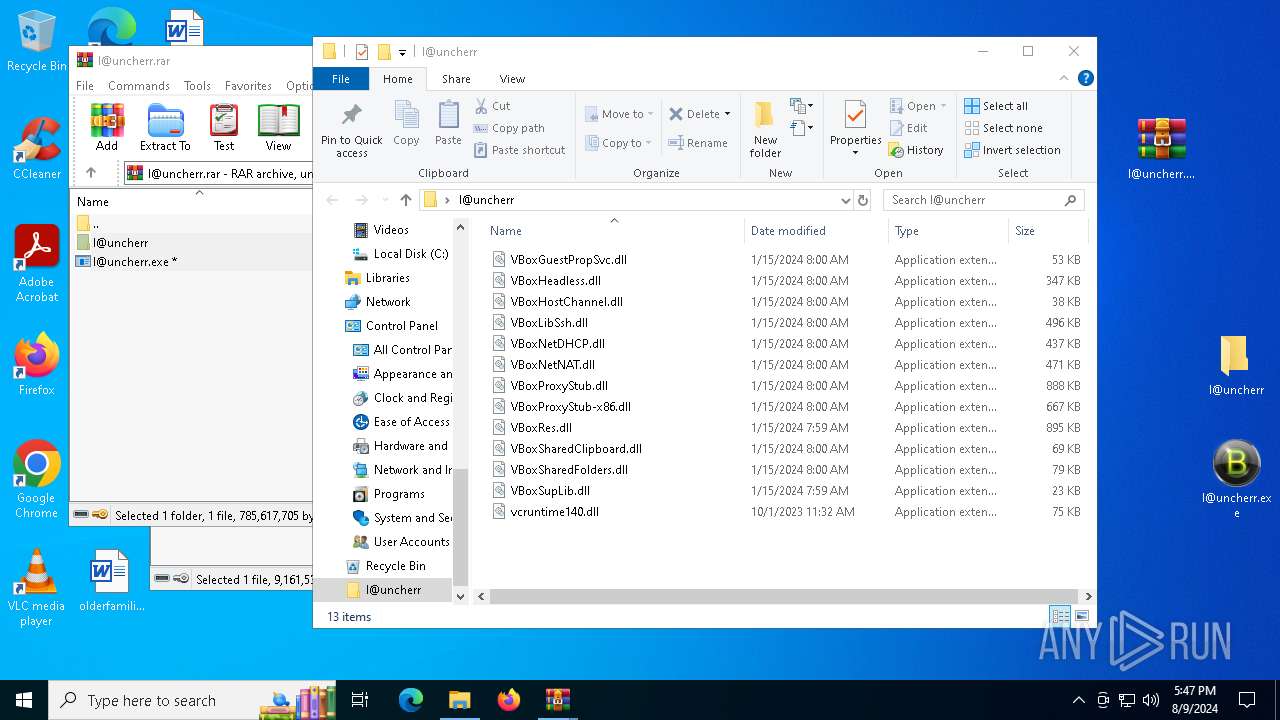
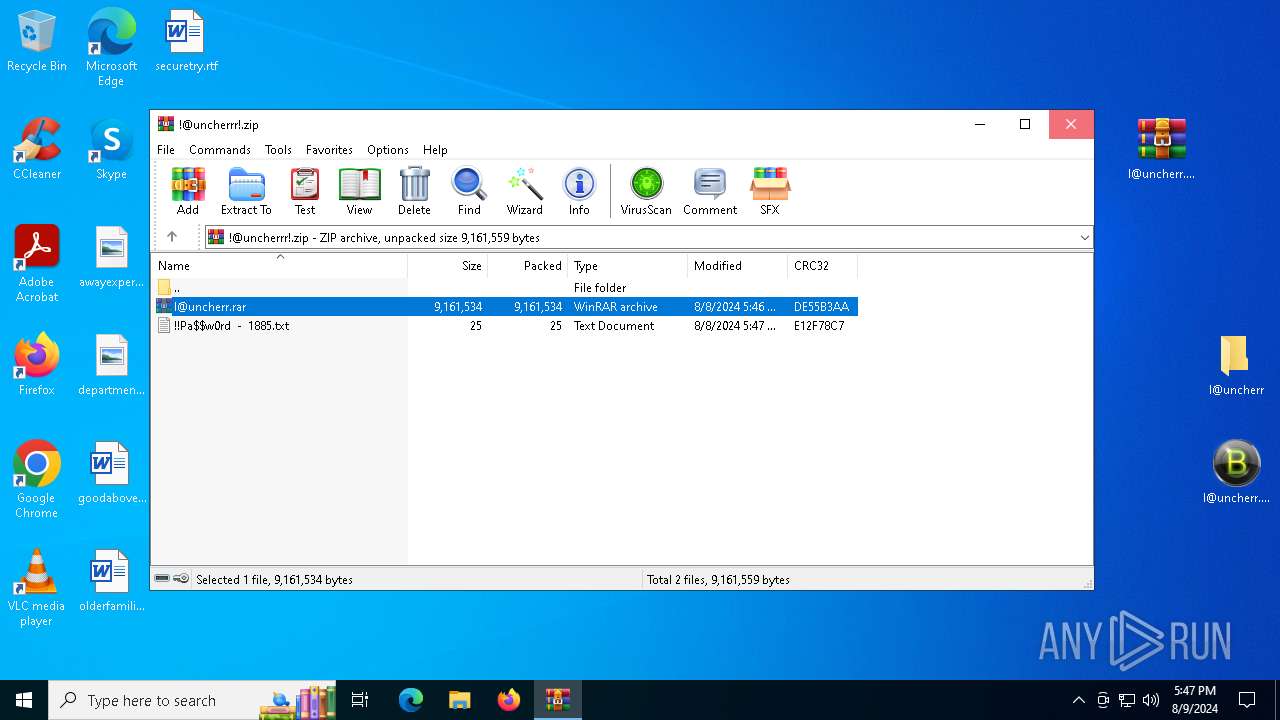
| File name: | !@uncherrr!.zip |
| Full analysis: | https://app.any.run/tasks/dd02cb4e-20cb-4d72-8471-8ad6f7145fb8 |
| Verdict: | Malicious activity |
| Threats: | Stealc is a stealer malware that targets victims’ sensitive data, which it exfiltrates from browsers, messaging apps, and other software. The malware is equipped with advanced features, including fingerprinting, control panel, evasion mechanisms, string obfuscation, etc. Stealc establishes persistence and communicates with its C2 server through HTTP POST requests. |
| Analysis date: | August 09, 2024, 17:45:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 9BB52E5C7ED736E4F9A5452C85E08BA9 |
| SHA1: | 39CC5DD3CE8597A9B774F85F3F23187341FE658A |
| SHA256: | 7078F23E3D24F2D72E83BDF10212B2C47BA7D5C5DBE057846AC65D4FF5777E61 |
| SSDEEP: | 98304:tsdEchxlSFKMZBVzCncxofX8SPGls3YE80Ge4rkFq69z3gzP5FOB/uNmQ2Es8kOF:PDRxTNQuUOGtg |
MALICIOUS
STEALC has been detected (SURICATA)
- BitLockerToGo.exe (PID: 6296)
Stealers network behavior
- BitLockerToGo.exe (PID: 6296)
Connects to the CnC server
- BitLockerToGo.exe (PID: 6296)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7036)
Connects to the server without a host name
- BitLockerToGo.exe (PID: 6296)
Windows Defender mutex has been found
- BitLockerToGo.exe (PID: 6296)
Reads security settings of Internet Explorer
- BitLockerToGo.exe (PID: 6296)
Contacting a server suspected of hosting an CnC
- BitLockerToGo.exe (PID: 6296)
INFO
Manual execution by a user
- WinRAR.exe (PID: 7036)
- I@uncherr.exe (PID: 1288)
- Taskmgr.exe (PID: 2080)
- Taskmgr.exe (PID: 208)
- firefox.exe (PID: 1140)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7036)
- firefox.exe (PID: 7072)
Checks supported languages
- I@uncherr.exe (PID: 1288)
- BitLockerToGo.exe (PID: 6296)
- TextInputHost.exe (PID: 4576)
Create files in a temporary directory
- I@uncherr.exe (PID: 1288)
Reads the computer name
- I@uncherr.exe (PID: 1288)
- BitLockerToGo.exe (PID: 6296)
- TextInputHost.exe (PID: 4576)
Checks proxy server information
- BitLockerToGo.exe (PID: 6296)
Creates files or folders in the user directory
- BitLockerToGo.exe (PID: 6296)
Application launched itself
- firefox.exe (PID: 1140)
- firefox.exe (PID: 7072)
Reads Microsoft Office registry keys
- firefox.exe (PID: 7072)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:08 10:46:46 |
| ZipCRC: | 0xde55b3aa |
| ZipCompressedSize: | 9161534 |
| ZipUncompressedSize: | 9161534 |
| ZipFileName: | I@uncherr.rar |
Total processes
151
Monitored processes
19
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1288 | "C:\Users\admin\Desktop\I@uncherr.exe" | C:\Users\admin\Desktop\I@uncherr.exe | — | explorer.exe | |||||||||||
User: admin Company: High Motion Software Integrity Level: MEDIUM Description: ImBatch (64-bit) Setup Exit code: 666 Version: 7, 6, 1, 0 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4620 -childID 2 -isForBrowser -prefsHandle 4616 -prefMapHandle 4612 -prefsLen 36263 -prefMapSize 244343 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {3aee649a-7647-4595-9c06-1d78cf4efb41} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 194e2579a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2080 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5444 -childID 3 -isForBrowser -prefsHandle 5436 -prefMapHandle 5432 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9b5c3ea9-de9f-42dc-a6c2-c05bc23430a0} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 194e39f6690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4888 -childID 6 -isForBrowser -prefsHandle 4940 -prefMapHandle 4936 -prefsLen 31242 -prefMapSize 244343 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {26382a72-59e0-40ef-85cb-7e4385e6dfb7} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 194e2e97a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3356 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1916 -parentBuildID 20240213221259 -prefsHandle 1844 -prefMapHandle 1824 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {9f332cc4-0ebb-4200-8bda-2db1fe24fbe1} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 194dbcd6710 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3812 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2968 -childID 1 -isForBrowser -prefsHandle 2920 -prefMapHandle 2976 -prefsLen 30953 -prefMapSize 244343 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {6326f7d2-8980-4be5-9bfa-ae2c8c2e02bc} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 194e174e150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3916 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=3004 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 5332 -prefMapHandle 4804 -prefsLen 34713 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c95dd33a-9134-401e-ae49-320ea51afb25} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 194e4613d10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
28 132
Read events
27 801
Write events
329
Delete events
2
Modification events
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\!@uncherrr!.zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
15
Suspicious files
152
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.37409\I@uncherr.rar | — | |
MD5:— | SHA256:— | |||
| 7036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7036.38288\I@uncherr.exe | — | |
MD5:— | SHA256:— | |||
| 1288 | I@uncherr.exe | C:\Users\Public\Libraries\aikco.scif | — | |
MD5:— | SHA256:— | |||
| 1288 | I@uncherr.exe | C:\Users\Public\Libraries\ppbab.scif | — | |
MD5:— | SHA256:— | |||
| 7036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7036.38288\I@uncherr\VBoxGuestPropSvc.dll | executable | |
MD5:2D2FACDCFC48DF336F2CB462ADDD7583 | SHA256:18DD854FD4BDC403384C16E586581A9FD714141953AE6FADEF65F41F895B9614 | |||
| 7036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7036.38288\I@uncherr\VBoxProxyStub-x86.dll | executable | |
MD5:6D3C7D2E108CBB7B5389F51FF68BCB9A | SHA256:53ED3512437FBEB4277C24790CE67DB048F81B60C3669765541495EF88056B88 | |||
| 7036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7036.38288\I@uncherr\VBoxSharedClipboard.dll | executable | |
MD5:A802413B13E45C7D526705CBD3974AE5 | SHA256:9FDC76DA45016187D325B992B83980227112BA14ED1CB3A2DEA8929046163A13 | |||
| 7036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7036.38288\I@uncherr\VBoxSharedFolders.dll | executable | |
MD5:93F9F9335E95AEBD2C914971C9F6BC58 | SHA256:45B9BD24A786F5F9EAF3782F1C1D659FCCEE5E9B6AC941C756C43F09F0D10819 | |||
| 7036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7036.38288\I@uncherr\VBoxNetDHCP.dll | executable | |
MD5:92E2E417F177BDC25275F75A1CFC5224 | SHA256:067D5D904F68633301CF36DCFEA43E9F564EECEC375B78F4FF61957746E296A2 | |||
| 7072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
87
DNS requests
116
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
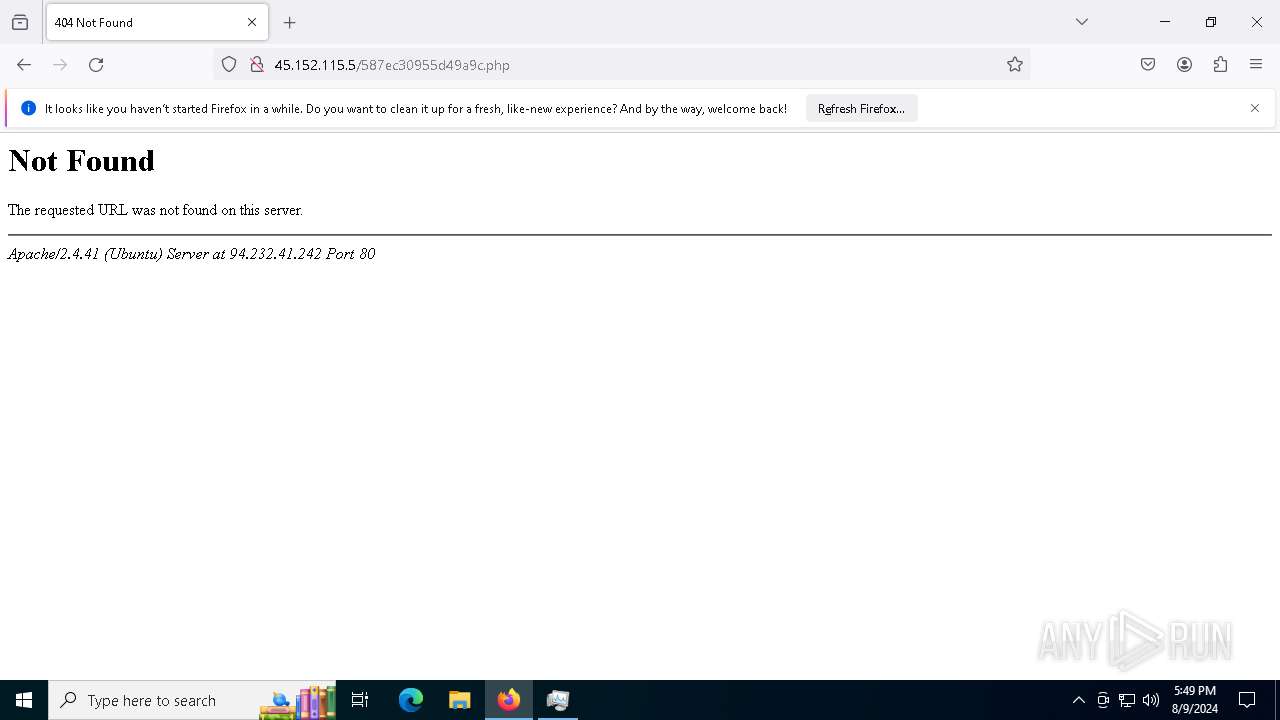
6296 | BitLockerToGo.exe | POST | 200 | 45.152.115.5:80 | http://45.152.115.5/587ec30955d49a9c.php | unknown | — | — | unknown |
6296 | BitLockerToGo.exe | GET | 200 | 45.152.115.5:80 | http://45.152.115.5/ | unknown | — | — | unknown |
7144 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6260 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7072 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
7072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7072 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1108 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1420 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5924 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6296 | BitLockerToGo.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Stealc HTTP POST Request |
6296 | BitLockerToGo.exe | Malware Command and Control Activity Detected | ET MALWARE [SEKOIA.IO] Win32/Stealc C2 Check-in |
1 ETPRO signatures available at the full report