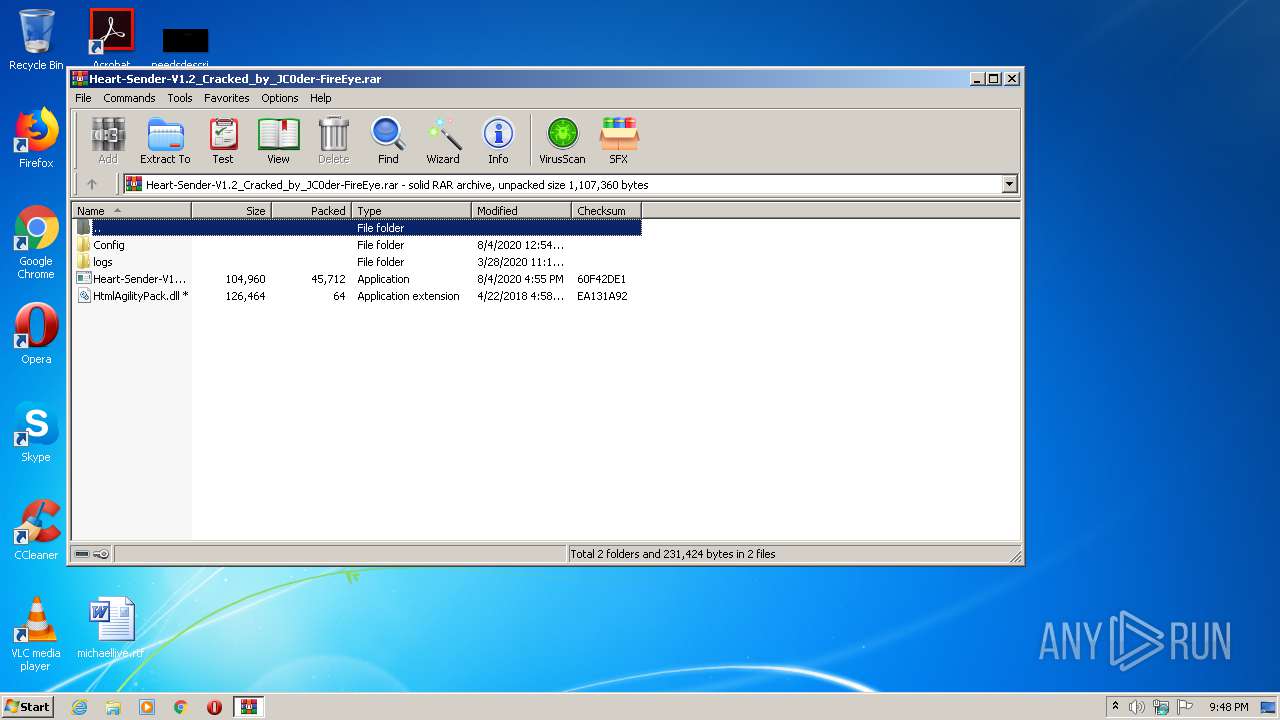
| File name: | Heart-Sender-V1.2_Cracked_by_JC0der-FireEye.rar |
| Full analysis: | https://app.any.run/tasks/31880028-2d60-4347-944a-a0ec8ac527f4 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | August 05, 2020, 20:47:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0737CCF9E78859896254F0D119AA1AF9 |
| SHA1: | F4DE3D02DF395F9C1AEC3ED0F39496EF0A75707B |
| SHA256: | 705C30ECABF1F694C24F521D35CBF3027798DD6F6965134C98F9CAD0CF8833CE |
| SSDEEP: | 12288:15AFdXQ59vpVC1lorbwS/hPW8veGzKopC:IA51zC1iwwPW8HKj |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3480)
Application was dropped or rewritten from another process
- Heart.exe (PID: 3776)
- Loader1.exe (PID: 2344)
- config.exe (PID: 2432)
- Heart-Sender-V1.2 Cracked by JC0der-FireEye.exe (PID: 3992)
- Loader4.exe (PID: 2220)
- Loader3.exe (PID: 3216)
- Loader2.exe (PID: 2956)
- config.exe (PID: 2552)
- svchost.exe (PID: 676)
- svchost.exe (PID: 3012)
Executes PowerShell scripts
- cmd.exe (PID: 1728)
- cmd.exe (PID: 2700)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 952)
- schtasks.exe (PID: 2264)
Drops/Copies Quasar RAT executable
- Loader3.exe (PID: 3216)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1728)
QUASAR was detected
- svchost.exe (PID: 3012)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2684)
- Loader1.exe (PID: 2344)
- Loader3.exe (PID: 3216)
- Loader4.exe (PID: 2220)
- Loader2.exe (PID: 2956)
Starts CMD.EXE for commands execution
- Heart-Sender-V1.2 Cracked by JC0der-FireEye.exe (PID: 3992)
- config.exe (PID: 2432)
- config.exe (PID: 2552)
Creates files in the user directory
- powershell.exe (PID: 2120)
- powershell.exe (PID: 2396)
- powershell.exe (PID: 1396)
- powershell.exe (PID: 1216)
- powershell.exe (PID: 2360)
- powershell.exe (PID: 1924)
- powershell.exe (PID: 1956)
- Loader3.exe (PID: 3216)
- powershell.exe (PID: 2388)
- Loader4.exe (PID: 2220)
- powershell.exe (PID: 1556)
- svchost.exe (PID: 3012)
- powershell.exe (PID: 2096)
Creates executable files which already exist in Windows
- Loader3.exe (PID: 3216)
- Loader4.exe (PID: 2220)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1728)
Executed via Task Scheduler
- svchost.exe (PID: 676)
- svchost.exe (PID: 3012)
Checks for external IP
- svchost.exe (PID: 3012)
INFO
Manual execution by user
- Heart-Sender-V1.2 Cracked by JC0der-FireEye.exe (PID: 3992)
Dropped object may contain Bitcoin addresses
- Loader1.exe (PID: 2344)
- Loader4.exe (PID: 2220)
- Loader2.exe (PID: 2956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
71
Monitored processes
29
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 676 | C:\Users\admin\AppData\Roaming\Microsoft\svchost10\svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\svchost10\svchost.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Services Exit code: 0 Version: 7.2.5.0 (WinBuild. 7.2.5.0) Modules
| |||||||||||||||
| 952 | schtasks /create /sc minute /mo 1 /tn "Microsoft\svchost\svchost9" /tr "C:\Users\admin\AppData\Roaming\Microsoft\svchost9\svchost.exe" /RL HIGHEST /f | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1216 | powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath "C:\users" -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1396 | powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath "$env:APPDATA\Microsoft\svchost10" -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | powershell Remove-MpPreference -ExclusionPath "C:\users" -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1728 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\270C.tmp\270D.tmp\270E.bat C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\config.exe" | C:\Windows\system32\cmd.exe | — | config.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1924 | powershell Add-MpPreference -ExclusionPath "$env:TEMP" -force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1956 | powershell Add-MpPreference -ExclusionPath "$env:APPDATA\Microsoft\svchost10" -force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2096 | powershell -inputformat none -outputformat none -NonInteractive -Command Remove-MpPreference -ExclusionPath "C:\users" -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | powershell Add-MpPreference -ExclusionPath "$env:APPDATA\Microsoft\svchost9" -force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 280
Read events
3 674
Write events
606
Delete events
0
Modification events
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Heart-Sender-V1.2_Cracked_by_JC0der-FireEye.rar | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
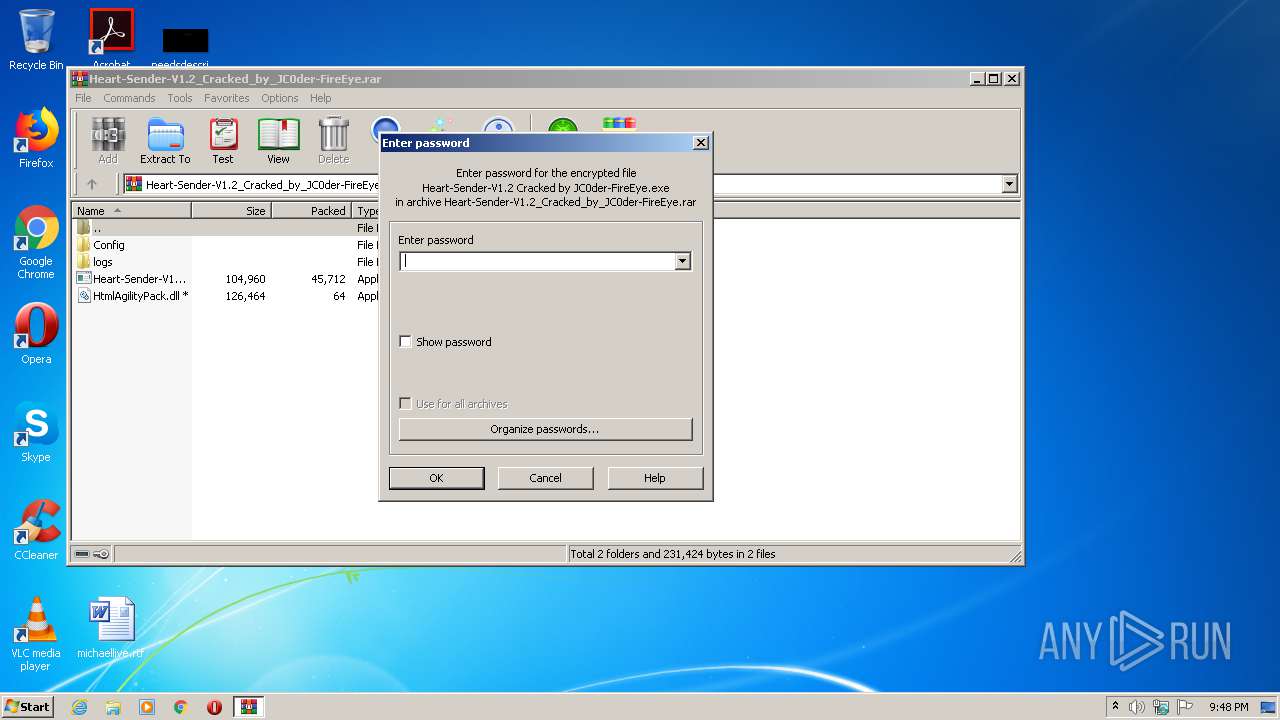
| (PID) Process: | (2684) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
12
Suspicious files
21
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1216 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JH8DHWAY2U7XCL1TAVSR.temp | — | |
MD5:— | SHA256:— | |||
| 2360 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\X1PIORTNJZZDHRVQGJM4.temp | — | |
MD5:— | SHA256:— | |||
| 2396 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\T9FAZZTOZ069WF2THOTT.temp | — | |
MD5:— | SHA256:— | |||
| 2684 | WinRAR.exe | C:\Users\admin\Desktop\Config\Loader1.exe | executable | |
MD5:— | SHA256:— | |||
| 2120 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OW2WB1HD8HF78Z4DYEE2.temp | — | |
MD5:— | SHA256:— | |||
| 2684 | WinRAR.exe | C:\Users\admin\Desktop\Config\Loader3.exe | executable | |
MD5:— | SHA256:— | |||
| 2684 | WinRAR.exe | C:\Users\admin\Desktop\Config\Loader4.exe | executable | |
MD5:— | SHA256:— | |||
| 1396 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\EOC7IG8Q205R7FF1SVJA.temp | — | |
MD5:— | SHA256:— | |||
| 2344 | Loader1.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Config.bat | text | |
MD5:— | SHA256:— | |||
| 3776 | Heart.exe | C:\Users\admin\Desktop\Settings.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
24
DNS requests
1
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3012 | svchost.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 319 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3012 | svchost.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
— | — | 185.81.157.212:60010 | — | Inulogic Sarl | FR | suspicious |
3012 | svchost.exe | 185.81.157.212:60010 | — | Inulogic Sarl | FR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3012 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3012 | svchost.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3012 | svchost.exe | A Network Trojan was detected | REMOTE [PTsecurity] Quasar.RAT IP Lookup |
1 ETPRO signatures available at the full report