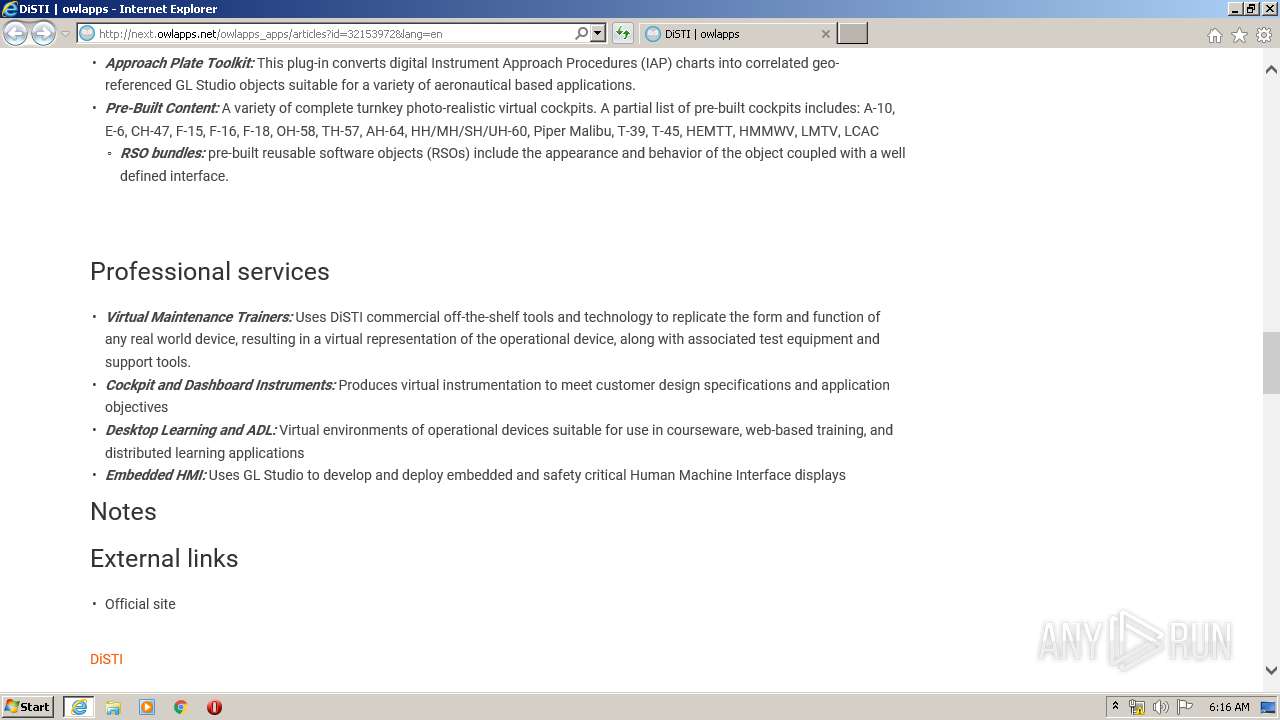
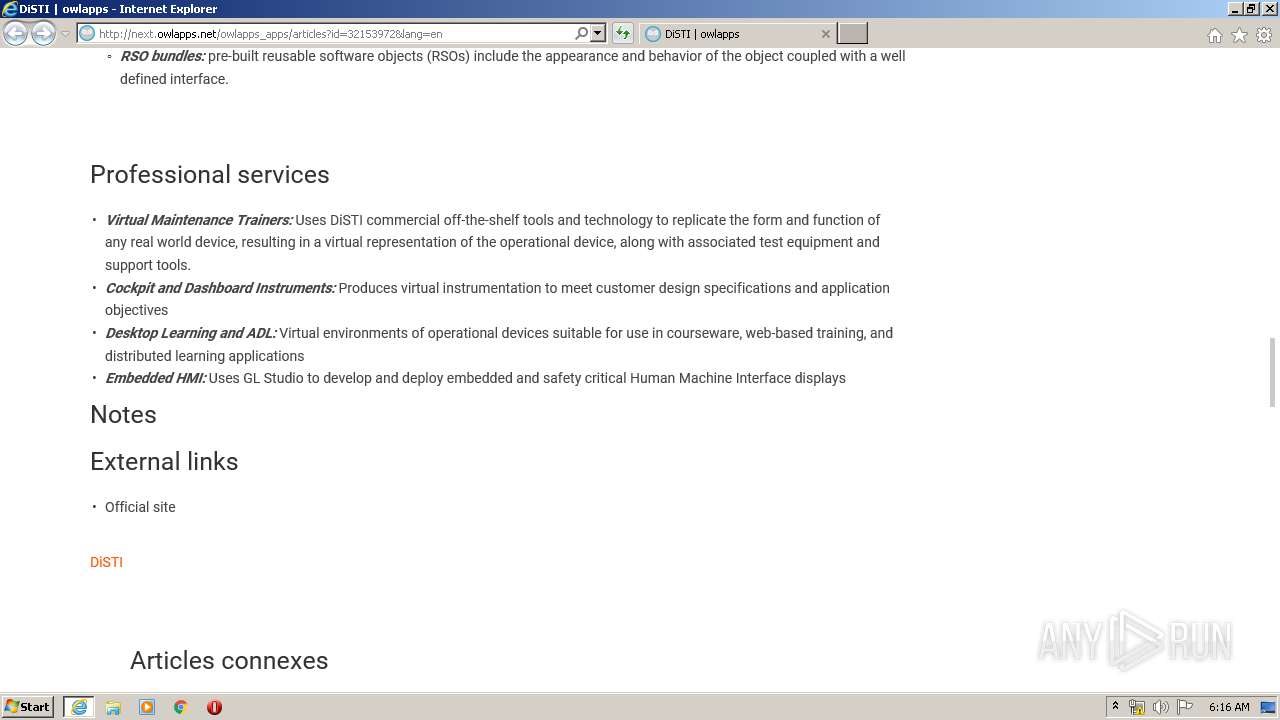
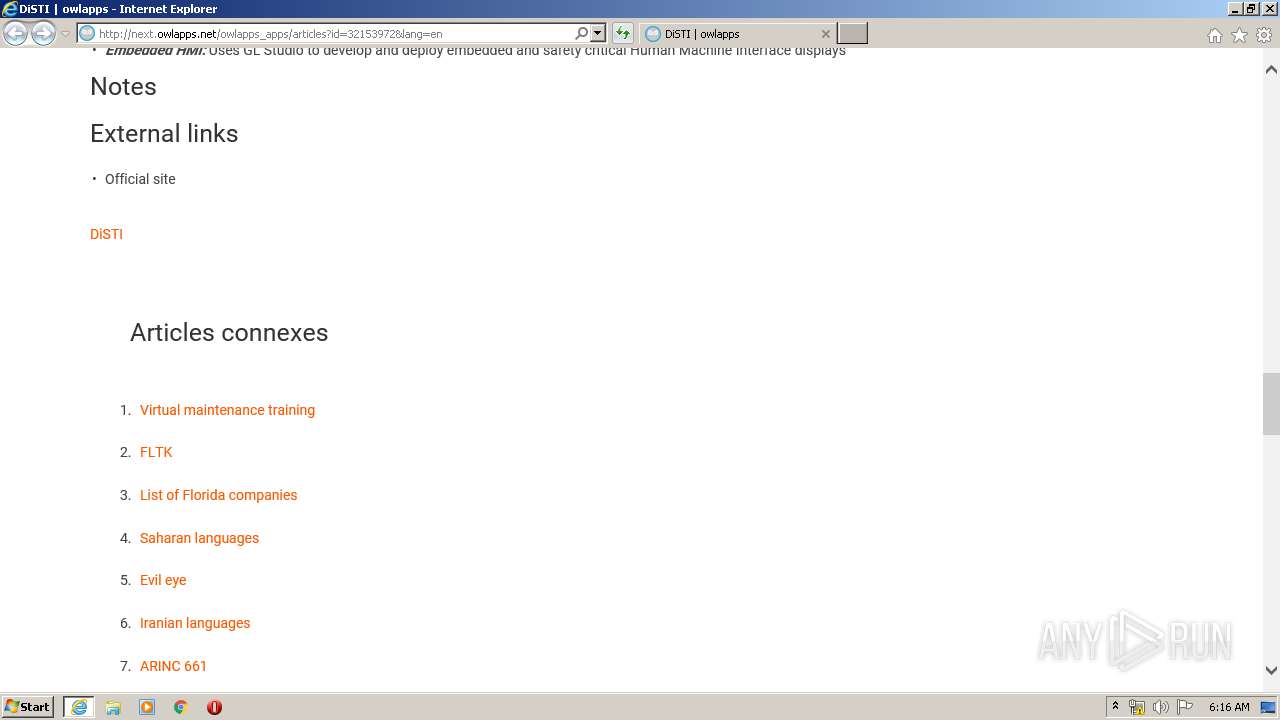
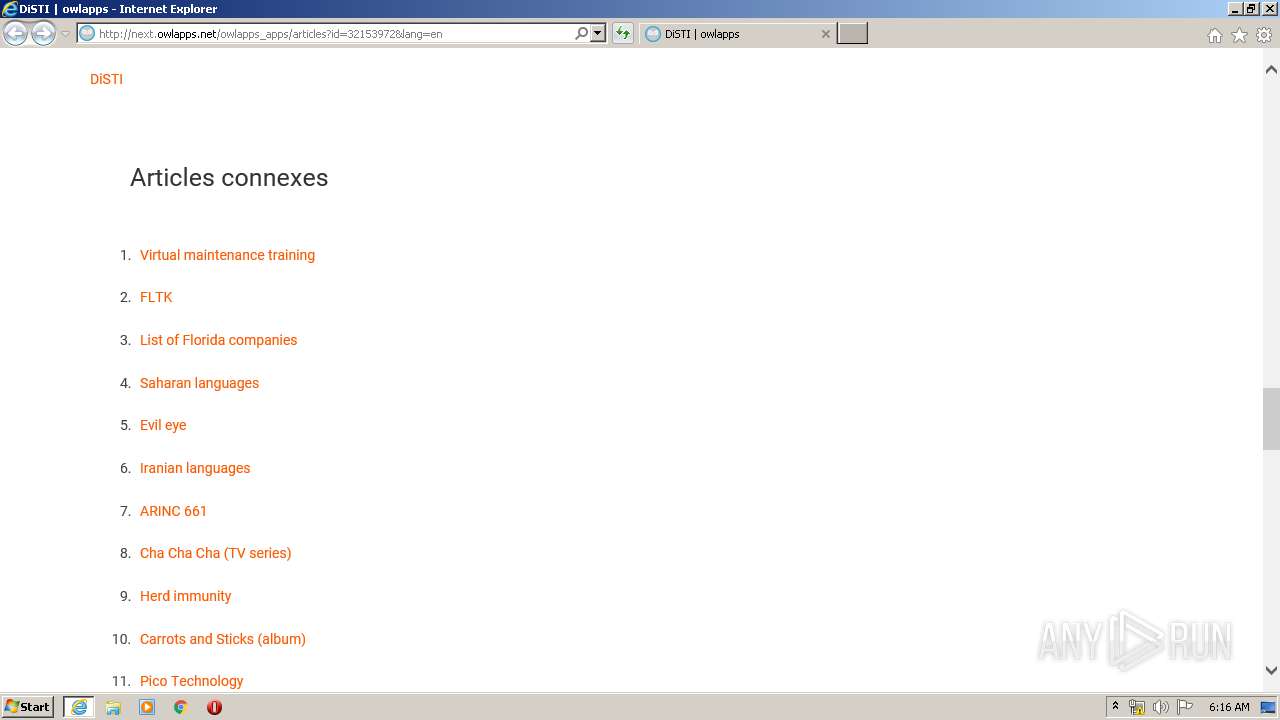
| URL: | http://next.owlapps.net/owlapps_apps/articles?id=32153972&lang=en |
| Full analysis: | https://app.any.run/tasks/e666b78a-138b-4176-8c4b-4d8b10e63a02 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | March 24, 2020, 06:15:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B9ACCAD3D12FACAF03A1D9D5C518A630 |
| SHA1: | 055EC9F4387ED4152A0ED6E077E7A56D637FFC3B |
| SHA256: | 70249395AB213F4DF077C6B769D4CDFD45A71A80E024AF6974C804C0D658290C |
| SSDEEP: | 3:N1KQ4R+N8LZJ/NHWaM6nMun:CQc+2L3/kabnMun |
MALICIOUS
COINMINER was detected
- iexplore.exe (PID: 3888)
SUSPICIOUS
No suspicious indicators.INFO
Reads internet explorer settings
- iexplore.exe (PID: 3888)
Reads Internet Cache Settings
- iexplore.exe (PID: 3888)
- iexplore.exe (PID: 780)
Changes internet zones settings
- iexplore.exe (PID: 780)
Creates files in the user directory
- iexplore.exe (PID: 780)
- iexplore.exe (PID: 3888)
Reads settings of System Certificates
- iexplore.exe (PID: 780)
- iexplore.exe (PID: 3888)
Adds / modifies Windows certificates
- iexplore.exe (PID: 780)
Changes settings of System certificates
- iexplore.exe (PID: 780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://next.owlapps.net/owlapps_apps/articles?id=32153972&lang=en" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3888 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:780 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
9 688
Read events
2 838
Write events
4 606
Delete events
2 244
Modification events
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2843543406 | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30802339 | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (780) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
65
Text files
67
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 780 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab868D.tmp | — | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar868E.tmp | — | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\css_UqzB48sGGwYUuT-h7QX_YpfiXvHvf6JTECzXllEXDKE[1].css | text | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\articles[1].htm | html | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:0392ADA071EB68355BED625D8F9695F3 | SHA256:B1313DD95EAF63F33F86F72F09E2ECD700D11159A8693210C37470FCB84038F7 | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\nopic[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\css_tJBWkM5TkLZjAF0xyWc7teCIsxxZuUMn2y8ffK_dN9o[1].css | text | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | binary | |
MD5:— | SHA256:— | |||
| 3888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ghbasslogo[1].png | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
96
DNS requests
38
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/owlapps_apps/articles?id=32153972&lang=en | FR | html | 29.0 Kb | malicious |
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/sites/default/files/css/css_UqzB48sGGwYUuT-h7QX_YpfiXvHvf6JTECzXllEXDKE.css?q7ntmf | FR | text | 2.21 Kb | malicious |
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/modules/owlapps_apps/img/ghbasslogo.png | FR | image | 38.4 Kb | malicious |
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/sites/default/files/js/js_KCPJZWaouR2asJMgAQZRUoi60GD790g8QBy-qm_U5CU.js | FR | text | 62.2 Kb | malicious |
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/modules/owlapps_apps/img/nopic.jpg | FR | image | 9.61 Kb | malicious |
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/sites/default/files/inline-images/ghbassD.gif | FR | image | 524 Kb | malicious |
3888 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3888 | iexplore.exe | GET | 200 | 52.222.172.135:80 | http://z-na.amazon-adsystem.com/widgets/q?ServiceVersion=20070822&Operation=GetScript&ID=OneJS&WS=1 | US | text | 7.73 Kb | whitelisted |
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/sites/default/files/css/css_tJBWkM5TkLZjAF0xyWc7teCIsxxZuUMn2y8ffK_dN9o.css?q7ntmf | FR | text | 32.0 Kb | malicious |
3888 | iexplore.exe | GET | 200 | 195.154.180.68:80 | http://next.owlapps.net/modules/owlapps_apps/img/ghbassB.gif | FR | image | 371 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | iexplore.exe | 172.217.22.66:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
3888 | iexplore.exe | 52.222.172.135:80 | z-na.amazon-adsystem.com | Amazon.com, Inc. | US | unknown |
3888 | iexplore.exe | 195.154.180.68:80 | next.owlapps.net | Online S.a.s. | FR | malicious |
3888 | iexplore.exe | 172.217.22.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
3888 | iexplore.exe | 151.101.0.241:443 | rlv.zcache.fr | Fastly | US | suspicious |
3888 | iexplore.exe | 81.171.8.143:443 | www.hostingcloud.racing | LeaseWeb Netherlands B.V. | NL | malicious |
3888 | iexplore.exe | 104.17.64.4:80 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
780 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3888 | iexplore.exe | 172.217.22.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3888 | iexplore.exe | 172.217.16.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
next.owlapps.net |
| malicious |
pagead2.googlesyndication.com |
| whitelisted |
z-na.amazon-adsystem.com |
| whitelisted |
rlv.zcache.fr |
| suspicious |
www.googletagmanager.com |
| whitelisted |
www.hostingcloud.racing |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3888 | iexplore.exe | A Network Trojan was detected | MALWARE [PTsecurity] Coinhive/DeepMiner JavaScript Miner |
2 ETPRO signatures available at the full report