| File name: | 701435e822a78b82d53281af3ffb20b3732462ec99c6f36afdfc6f8eed4123f9.jar |
| Full analysis: | https://app.any.run/tasks/552cd48d-484e-4eba-b36c-97bfca897fda |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | January 20, 2025, 03:59:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (65536), with no line terminators |
| MD5: | E865DE0263ADA94EA596FCE4EFD89AD0 |
| SHA1: | 96447CBCAE6C1AF91DD19587F729EC6CDDDABC54 |
| SHA256: | 701435E822A78B82D53281AF3FFB20B3732462EC99C6F36AFDFC6F8EED4123F9 |
| SSDEEP: | 3072:mOAfrLpHJttJamF2HVF1SPtDNu8JPJRl0JSc:hAzdtEBF05NdJ7l0JSc |
MALICIOUS
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 2424)
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 2424)
Create files in the Startup directory
- javaw.exe (PID: 6560)
ADWIND has been detected
- javaw.exe (PID: 6560)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 5300)
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 5300)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 5300)
Actions looks like stealing of personal data
- java.exe (PID: 3220)
- java.exe (PID: 2200)
Deletes a file (SCRIPT)
- wscript.exe (PID: 5300)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2424)
- wscript.exe (PID: 5300)
Checks for Java to be installed
- java.exe (PID: 6360)
- java.exe (PID: 2200)
- java.exe (PID: 3220)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 2424)
Creates XML DOM element (SCRIPT)
- wscript.exe (PID: 2424)
Script creates XML DOM node (SCRIPT)
- wscript.exe (PID: 2424)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 2424)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2424)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 2424)
Reads security settings of Internet Explorer
- javaw.exe (PID: 6560)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 6560)
Reads the date of Windows installation
- javaw.exe (PID: 6560)
Starts itself from another location
- javaw.exe (PID: 6560)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 5300)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 5300)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 5300)
The process executes JS scripts
- cmd.exe (PID: 6644)
Executable content was dropped or overwritten
- java.exe (PID: 3220)
- java.exe (PID: 2200)
Accesses domain name via WMI (SCRIPT)
- WMIC.exe (PID: 7460)
Uses WMIC.EXE to obtain computer system information
- java.exe (PID: 2380)
Process drops python dynamic module
- java.exe (PID: 3220)
Process drops legitimate windows executable
- java.exe (PID: 3220)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 2424)
Get information on the list of running processes
- javaw.exe (PID: 6560)
INFO
Checks supported languages
- java.exe (PID: 6360)
- javaw.exe (PID: 6704)
- java.exe (PID: 2200)
- java.exe (PID: 3220)
- javaw.exe (PID: 6560)
Create files in a temporary directory
- javaw.exe (PID: 6560)
- java.exe (PID: 6360)
- java.exe (PID: 2380)
- java.exe (PID: 3220)
- java.exe (PID: 2200)
The process uses the downloaded file
- wscript.exe (PID: 2424)
- javaw.exe (PID: 6560)
Reads the computer name
- javaw.exe (PID: 6560)
- java.exe (PID: 2380)
Creates files or folders in the user directory
- javaw.exe (PID: 6560)
- java.exe (PID: 2200)
- java.exe (PID: 3220)
Process checks computer location settings
- javaw.exe (PID: 6560)
Application launched itself
- AcroCEF.exe (PID: 5640)
- Acrobat.exe (PID: 7072)
Sends debugging messages
- Acrobat.exe (PID: 6448)
Application based on Java
- javaw.exe (PID: 6704)
- javaw.exe (PID: 6560)
Reads Microsoft Office registry keys
- javaw.exe (PID: 6560)
Reads the machine GUID from the registry
- java.exe (PID: 3220)
- java.exe (PID: 2200)
- javaw.exe (PID: 6560)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7460)
The sample compiled with english language support
- java.exe (PID: 3220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
166
Monitored processes
33
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2104 --field-trial-handle=1604,i,9873192267942562165,634259985008855080,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1668 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2924 --field-trial-handle=1604,i,9873192267942562165,634259985008855080,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2200 | java -jar C:\Users\admin\AppData\Roaming\Microsoft\Vault\cred\history.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3568 --field-trial-handle=1604,i,9873192267942562165,634259985008855080,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2380 | java -jar C:\Users\admin\AppData\Roaming\Microsoft\Vault\cred\checker.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2424 | "C:\Windows\System32\WScript.exe" C:\Users\admin\AppData\Local\Temp\701435e822a78b82d53281af3ffb20b3732462ec99c6f36afdfc6f8eed4123f9.jar.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2744 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2356 --field-trial-handle=1604,i,9873192267942562165,634259985008855080,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2972 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3220 | java -jar C:\Users\admin\AppData\Roaming\Microsoft\Vault\cred\recovery.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
25 274
Read events
24 808
Write events
425
Delete events
41
Modification events
| (PID) Process: | (6560) javaw.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\OpenWithProgids |
| Operation: | write | Name: | Acrobat.Document.DC |
Value: | |||
| (PID) Process: | (7072) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 7 | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ToolsSearch |
| Operation: | write | Name: | iSearchHintIndex |
Value: 3 | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\DLLInjection |
| Operation: | write | Name: | bBlockDLLInjection |
Value: 0 | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | delete value | Name: | ProductInfoCache |
Value: | |||
| (PID) Process: | (6448) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | write | Name: | EULAAcceptedForBrowser |
Value: 1 | |||
Executable files
41
Suspicious files
210
Text files
642
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2424 | wscript.exe | C:\Users\admin\AppData\Local\Temp\Swift Confirmation Copy.jar | java | |
MD5:8E96E66F83E748D267DF96390C880297 | SHA256:AE345B40D165255284BF4C6AB00A871FCB035B552AC0B20B3CFB19E4644E49B7 | |||
| 6560 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\83aa4cc77f591dfc2374580bbd95f6ba_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
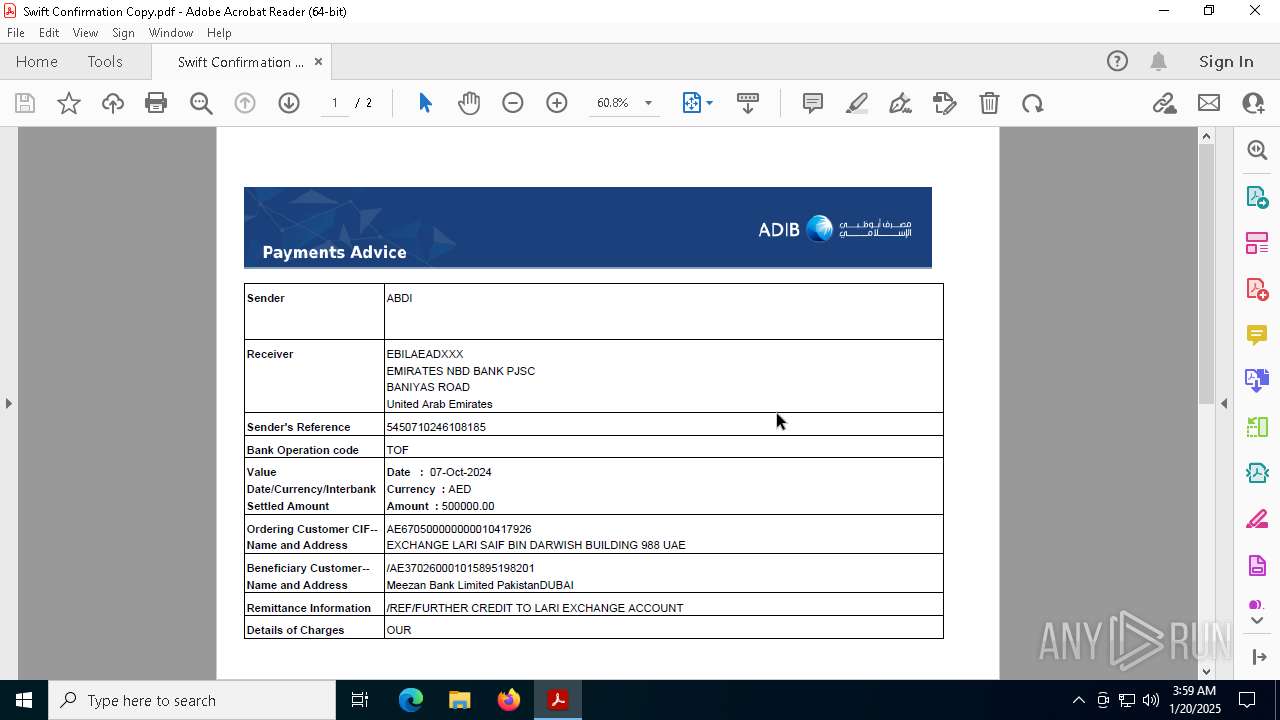
| 6560 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Vault\cred\temp_swiftcopy.pdf | ||
MD5:B33A3A023783CFB6F9B63AF90B0C03D5 | SHA256:8BCBA87DF6D459A573441FB848B90451D65BCE3A0F2AC08844C098922672B734 | |||
| 6448 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt23.lst.6448 | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 6448 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 6560 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\windowsdefi1.jar | compressed | |
MD5:04C1C03B037268D45E2E6197116A8574 | SHA256:CA6DBEAA3767A924FE88C2E4FEB5CBBD10697A7EFD9FC09C03D2202EDA311191 | |||
| 6448 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\NGLClient_AcrobatReader123.1.20093.6 2025-01-20 03-59-16-055.log | text | |
MD5:460C6041966002D8384A18C895A65EB0 | SHA256:C83EC6E8FB3EC62481289C033238C1D9B08DB8076EAAD304099FD7A7F594F1B9 | |||
| 7072 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 6448 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 6448 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents | binary | |
MD5:2DFB247745871D4545D624DF148A0D7B | SHA256:025449CD00072F5C2EC96C7E7744A39EB6762E8B46DBECCB5F392C68936E626F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
45
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4944 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4944 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7072 | Acrobat.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
1224 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6560 | javaw.exe | 52.217.117.10:443 | seasonmonster.s3.us-east-1.amazonaws.com | — | US | shared |
5064 | SearchApp.exe | 2.21.65.132:443 | th.bing.com | Akamai International B.V. | NL | whitelisted |
5156 | AcroCEF.exe | 184.28.88.176:443 | geo2.adobe.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
seasonmonster.s3.us-east-1.amazonaws.com |
| shared |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
arc.msn.com |
| whitelisted |