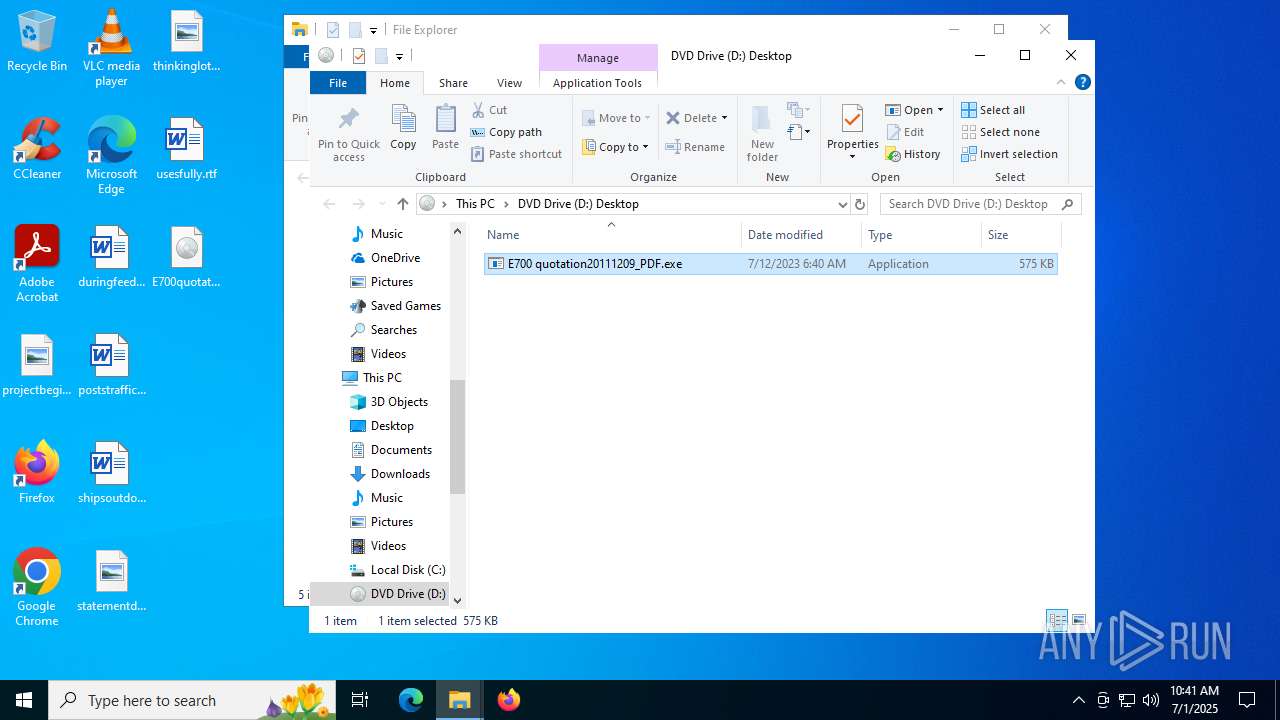
| File name: | E700quotation20111209_PDF.img |
| Full analysis: | https://app.any.run/tasks/0278192d-754b-4aa8-9de3-240d2f8e4e25 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 01, 2025, 10:39:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | UDF filesystem data (version 1.5) 'DESKTOP' |
| MD5: | 112654E4E0E264B2D63574BD6E772F52 |
| SHA1: | 2A119AD7C7FEACBE3026858C8BB2F7A728C99AFE |
| SHA256: | 70116650AEF13CEBF56D48CFDA5027D8DCB8B3EDA2FB97FBD05D92804BD382B6 |
| SSDEEP: | 49152:liwuLwecrC4+Kgoc5uRRoF5uXzGGcn/bYawdRinmeF0:cwusNCnK1c5uR4uDmn7C0nme6 |
MALICIOUS
Actions looks like stealing of personal data
- E700 quotation20111209_PDF.exe (PID: 4456)
Steals credentials from Web Browsers
- E700 quotation20111209_PDF.exe (PID: 4456)
AGENTTESLA has been detected (YARA)
- E700 quotation20111209_PDF.exe (PID: 4456)
SUSPICIOUS
Application launched itself
- explorer.exe (PID: 4772)
- E700 quotation20111209_PDF.exe (PID: 4932)
Image mount has been detect
- explorer.exe (PID: 4772)
Connects to SMTP port
- E700 quotation20111209_PDF.exe (PID: 4456)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
Creates files or folders in the user directory
- explorer.exe (PID: 4772)
- E700 quotation20111209_PDF.exe (PID: 4456)
Manual execution by a user
- E700 quotation20111209_PDF.exe (PID: 4932)
- E700 quotation20111209_PDF.exe (PID: 5444)
Checks supported languages
- E700 quotation20111209_PDF.exe (PID: 4932)
- E700 quotation20111209_PDF.exe (PID: 5444)
- E700 quotation20111209_PDF.exe (PID: 4456)
Reads the computer name
- E700 quotation20111209_PDF.exe (PID: 4932)
- E700 quotation20111209_PDF.exe (PID: 5444)
- E700 quotation20111209_PDF.exe (PID: 4456)
Reads the machine GUID from the registry
- E700 quotation20111209_PDF.exe (PID: 4932)
- E700 quotation20111209_PDF.exe (PID: 5444)
- E700 quotation20111209_PDF.exe (PID: 4456)
Reads the software policy settings
- E700 quotation20111209_PDF.exe (PID: 4456)
- slui.exe (PID: 6348)
ULTRAVNC has been detected
- E700 quotation20111209_PDF.exe (PID: 4456)
Checks proxy server information
- slui.exe (PID: 6348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(4456) E700 quotation20111209_PDF.exe
Protocolsmtp
Hostmail.flumetec.com
Port587
Usernameshahd.ibraheem@flumetec.com
PasswordS2022ahd@
TRiD
| .atn | | | Photoshop Action (37.5) |
|---|---|---|
| .gmc | | | Game Music Creator Music (8.4) |
| .abr | | | Adobe PhotoShop Brush (7.5) |
EXIF
ISO
| VolumeName: | DESKTOP |
|---|---|
| VolumeBlockCount: | 599 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2023:07:12 07:42:26+12:00 |
| VolumeSetName: | UNDEFINED |
| Software: | IMGBURN V2.5.8.0 - THE ULTIMATE IMAGE BURNER! |
| VolumeCreateDate: | 2023:07:12 07:42:26.00+12:00 |
| VolumeModifyDate: | 2023:07:12 07:42:26.00+12:00 |
Composite
| VolumeSize: | 1227 kB |
|---|
Total processes
147
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4456 | "D:\E700 quotation20111209_PDF.exe" | D:\E700 quotation20111209_PDF.exe | E700 quotation20111209_PDF.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: QuanLySanPham Version: 1.0.0.0 Modules
AgentTesla(PID) Process(4456) E700 quotation20111209_PDF.exe Protocolsmtp Hostmail.flumetec.com Port587 Usernameshahd.ibraheem@flumetec.com PasswordS2022ahd@ | |||||||||||||||
| 4772 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | "D:\E700 quotation20111209_PDF.exe" | D:\E700 quotation20111209_PDF.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: QuanLySanPham Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5444 | "D:\E700 quotation20111209_PDF.exe" | D:\E700 quotation20111209_PDF.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: QuanLySanPham Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6284 | "D:\E700 quotation20111209_PDF.exe" | D:\E700 quotation20111209_PDF.exe | — | E700 quotation20111209_PDF.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: QuanLySanPham Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6348 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7032 | "C:\WINDOWS\Explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 944
Read events
19 884
Write events
60
Delete events
0
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 030000000000000004000000110000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: FEBA636800000000 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000901FE |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 0000000000000000000000000000000003000100010001000F000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000001400000000000000700072006F006A0065006300740062006500670069006E002E006A00700067003E002000200000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C000000120000000000000064007500720069006E00670066006500650064002E007200740066003E00200020000000140000000000000070006F0073007400730074007200610066006600690063002E007200740066003E002000200000001400000000000000730068006900700073006F007500740064006F006F0072002E007200740066003E002000200000001400000000000000730074006100740065006D0065006E0074006400690065002E0070006E0067003E0020002000000014000000000000007400680069006E006B0069006E0067006C006F00740073002E006A00700067003E0020002000000011000000000000007500730065007300660075006C006C0079002E007200740066003E0020002000000021000000000000004500370030003000710075006F0074006100740069006F006E00320030003100310031003200300039005F005000440046002E0069006D0067003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000000F00000000000000000000000000000000000000803F0000004008000000803F000040400900000000000000404003000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D00000000000000803F01000000000000000040020000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000000400E00 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4456 | E700 quotation20111209_PDF.exe | C:\Users\admin\AppData\Roaming\cazhhno4.to3\Chrome\Default\Network\Cookies | sqlite | |
MD5:3EB66F8F3F058E157563F42DBF644355 | SHA256:AD0A6073D226341F699F465BDD35F01E88F0E9D4BCCEC816D6DF06D34F848350 | |||
| 4456 | E700 quotation20111209_PDF.exe | C:\Users\admin\AppData\Roaming\cazhhno4.to3\Edge Chromium\Default\Network\Cookies | sqlite | |
MD5:95880FF3BCDAFC337483887A27A907B9 | SHA256:3873D85E74D163F4D149BDDD6722276E446BB72FAAF42A7E328FCBAAEBE30A6D | |||
| 4456 | E700 quotation20111209_PDF.exe | C:\Users\admin\AppData\Roaming\cazhhno4.to3\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite | sqlite | |
MD5:34B2848FBEDBF3D43462938703592DBC | SHA256:6CF535DAEEC70899C28C0C6127F210900C2999A97189DEDDA415987D0F353A72 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
49
DNS requests
27
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2876 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6980 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2876 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2876 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |