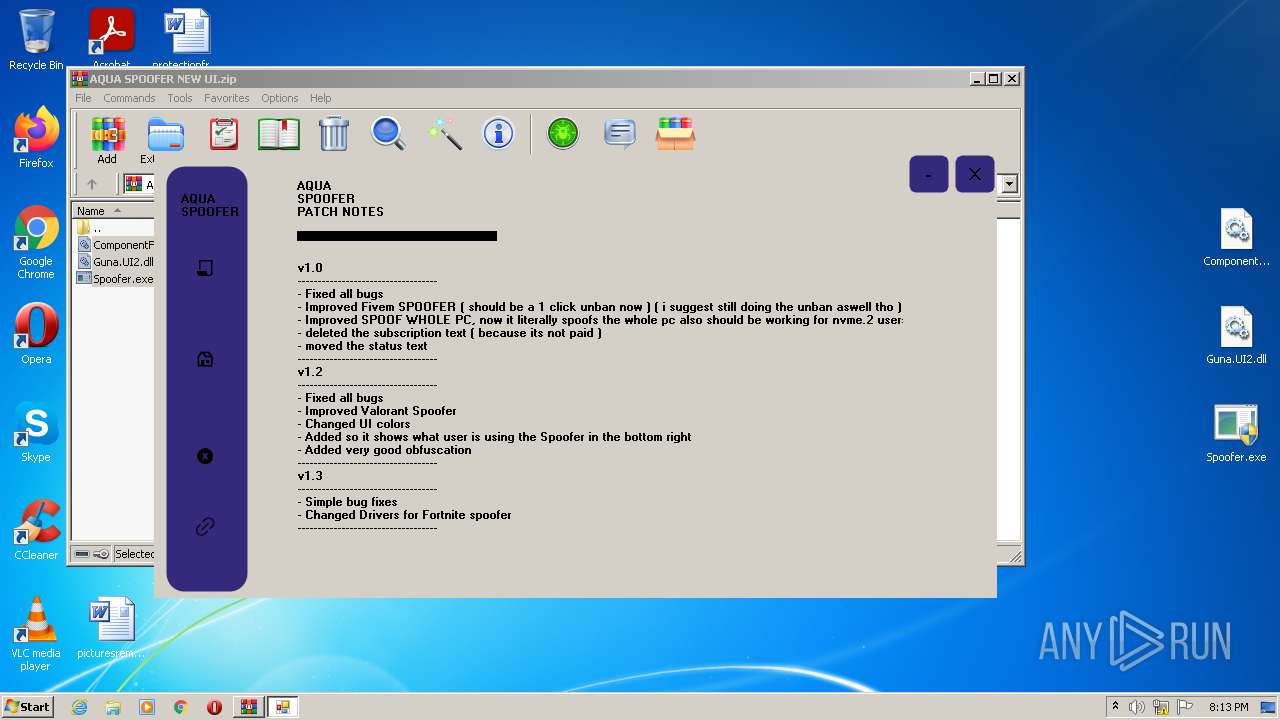
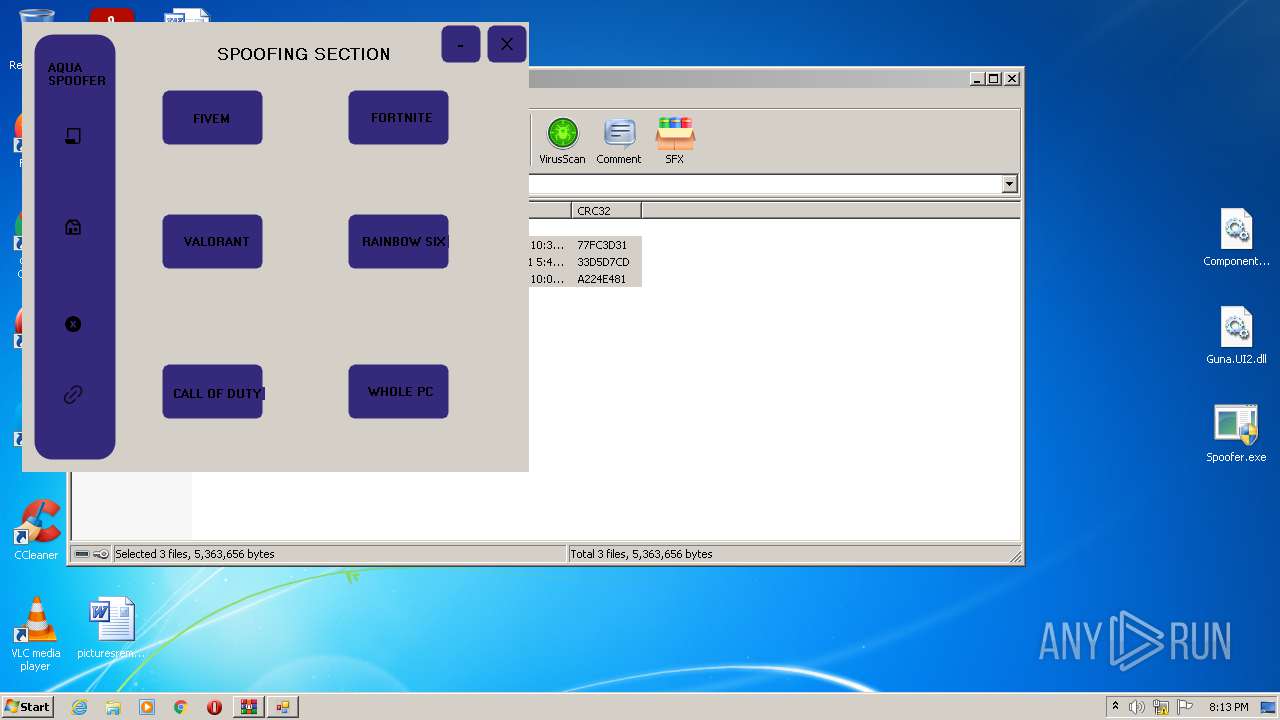
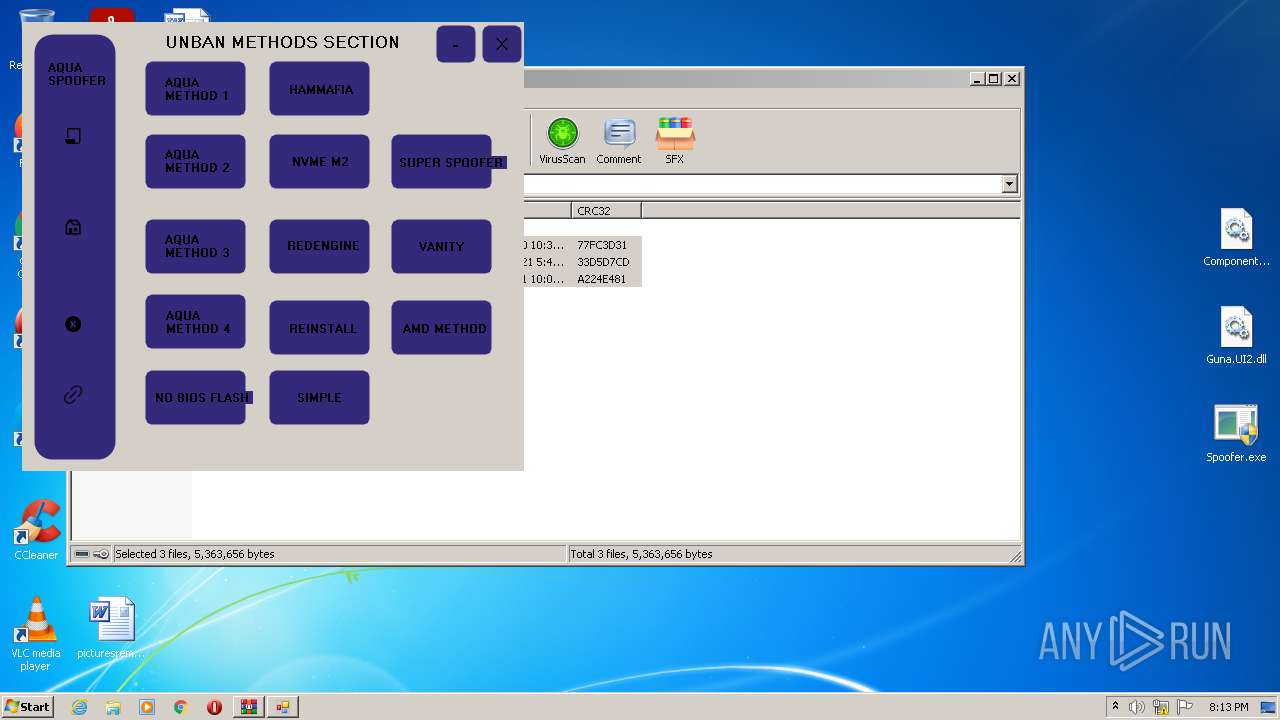
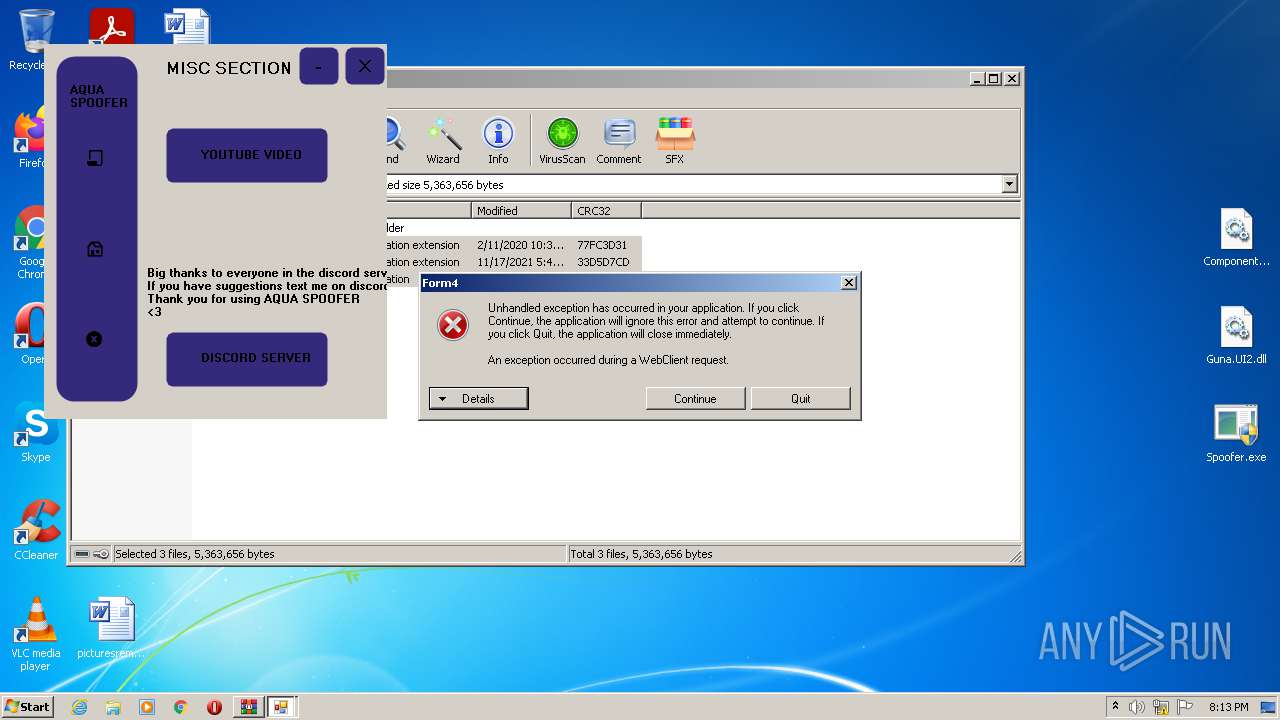
| File name: | AQUA SPOOFER NEW UI.zip |
| Full analysis: | https://app.any.run/tasks/dc56f17f-aa89-4b87-ac54-87fb3c6edcb1 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 05, 2021, 20:13:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | AE8DD5405FB4E2F24001CB834E58605A |
| SHA1: | 0EC0B3882C205C2757E93D8A5787AB2E07B7D3A6 |
| SHA256: | 7008347D481FB760104486B02DA7CEC2F7DC9A79E89166EC96261CF95C73CE35 |
| SSDEEP: | 49152:T6j4UlD6qsW67AVt2XnyY4hQctNbnWhNJqgWTf5uH:TrpBTXyJiwbnWvUZf5W |
MALICIOUS
Application was dropped or rewritten from another process
- Spoofer.exe (PID: 3292)
- Spoofer.exe (PID: 2128)
- System lnterrupts.exe (PID: 2752)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3692)
- Spoofer.exe (PID: 2128)
Drops executable file immediately after starts
- Spoofer.exe (PID: 2128)
Changes the autorun value in the registry
- Spoofer.exe (PID: 2128)
ASYNCRAT was detected
- System lnterrupts.exe (PID: 2752)
Writes to a start menu file
- Spoofer.exe (PID: 2128)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3660)
- Spoofer.exe (PID: 2128)
Checks supported languages
- WinRAR.exe (PID: 3660)
- Spoofer.exe (PID: 2128)
- System lnterrupts.exe (PID: 2752)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3660)
- Spoofer.exe (PID: 2128)
Reads the computer name
- WinRAR.exe (PID: 3660)
- Spoofer.exe (PID: 2128)
- System lnterrupts.exe (PID: 2752)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3660)
Creates files in the user directory
- Spoofer.exe (PID: 2128)
Reads Environment values
- Spoofer.exe (PID: 2128)
- System lnterrupts.exe (PID: 2752)
Creates files in the program directory
- Spoofer.exe (PID: 2128)
INFO
Manual execution by user
- Spoofer.exe (PID: 3292)
- Spoofer.exe (PID: 2128)
Reads settings of System Certificates
- Spoofer.exe (PID: 2128)
- System lnterrupts.exe (PID: 2752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | ComponentFactory.Krypton.Toolkit.dll |
|---|---|
| ZipUncompressedSize: | 2965504 |
| ZipCompressedSize: | 885736 |
| ZipCRC: | 0x77fc3d31 |
| ZipModifyDate: | 2020:02:11 10:39:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
41
Monitored processes
5
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2128 | "C:\Users\admin\Desktop\Spoofer.exe" | C:\Users\admin\Desktop\Spoofer.exe | Explorer.EXE | ||||||||||||
User: admin Company: 20188-2222 Integrity Level: HIGH Description: WindowsFormsApp18 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2752 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\System lnterrupts.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\System lnterrupts.exe | Spoofer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: System Interrupts Exit code: 0 Version: 6.2.19041.746 Modules
| |||||||||||||||
| 3292 | "C:\Users\admin\Desktop\Spoofer.exe" | C:\Users\admin\Desktop\Spoofer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: 20188-2222 Integrity Level: MEDIUM Description: WindowsFormsApp18 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3660 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\AQUA SPOOFER NEW UI.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3692 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
8 579
Read events
8 518
Write events
61
Delete events
0
Modification events
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AQUA SPOOFER NEW UI.zip | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
6
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3660.35484\Spoofer.exe | executable | |
MD5:— | SHA256:— | |||
| 2128 | Spoofer.exe | C:\Program Files\System lnterrupts.exe | executable | |
MD5:— | SHA256:— | |||
| 2128 | Spoofer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\System lnterrupts.exe | executable | |
MD5:— | SHA256:— | |||
| 2128 | Spoofer.exe | C:\Users\admin\AppData\Local\Temp\45cf148a-5b20-4de7-ac3f-490a30261b0a\rabu.dll | executable | |
MD5:14FF402962AD21B78AE0B4C43CD1F194 | SHA256:FB9646CB956945BDC503E69645F6B5316D3826B780D3C36738D6B944E884D15B | |||
| 3660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3660.35484\Guna.UI2.dll | executable | |
MD5:38AB8E6E56CEE9F49E2167FB43275F05 | SHA256:1CAA3FD09153C8EA3D623D5723133F98751F2AFC1C135992F19F1F1A7044490C | |||
| 3660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3660.35484\ComponentFactory.Krypton.Toolkit.dll | executable | |
MD5:129884DE0E136521FD650C59B2633E82 | SHA256:8C69F5DF110BC1A61BDC3D8754EBFD3F49D9D995B9DD129ACCAF88371CE71E30 | |||
| 2128 | Spoofer.exe | C:\Users\admin\.guna\Guna.UI2\Licensing\.licenseengineversion | text | |
MD5:4DF604C34AC416CD49E8C15DB087A2DA | SHA256:64C6EBA21CA5A6D3D07D2E216C48934A2105B4EB2AAF04DB0CE74FB73BE813BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
3
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2128 | Spoofer.exe | 162.159.130.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2752 | System lnterrupts.exe | 3.138.45.170:80 | 2.tcp.ngrok.io | — | US | malicious |
2752 | System lnterrupts.exe | 3.138.45.170:19547 | 2.tcp.ngrok.io | — | US | malicious |
— | — | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
2.tcp.ngrok.io |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query to a *.ngrok domain (ngrok.io) |
2752 | System lnterrupts.exe | A Network Trojan was detected | ET TROJAN Observed Malicious SSL Cert (AsyncRAT Server) |
1 ETPRO signatures available at the full report