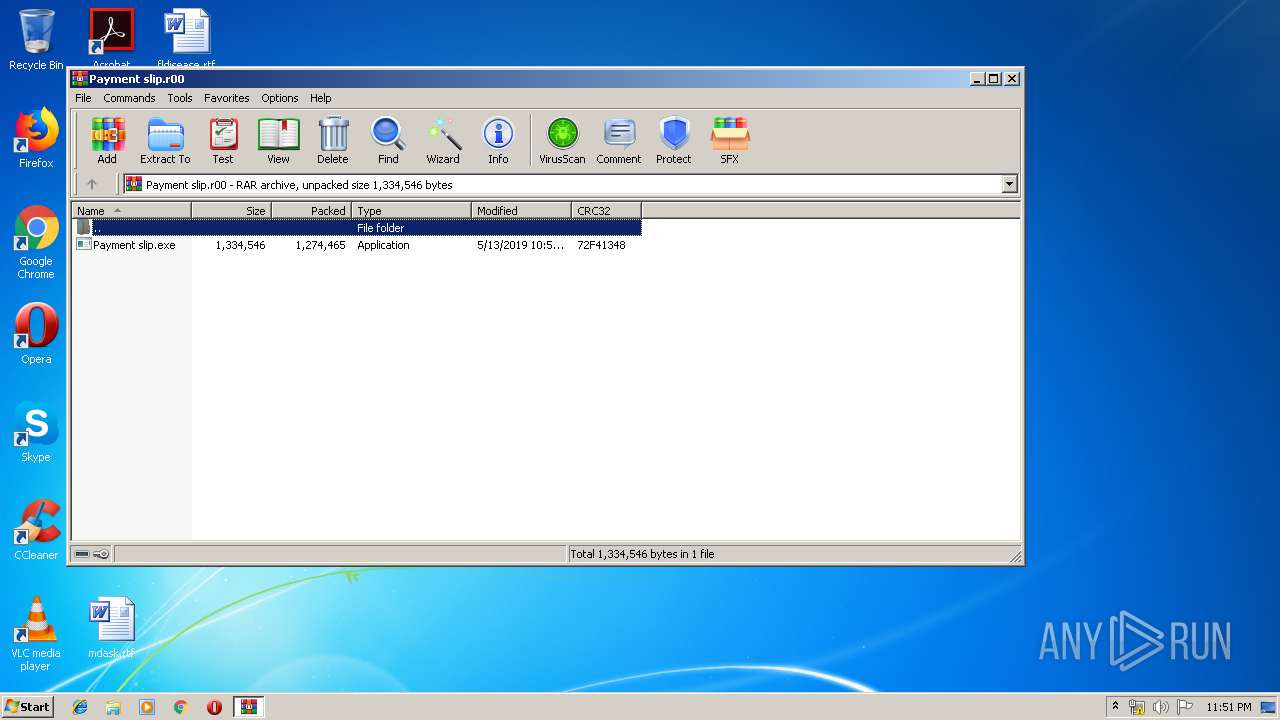
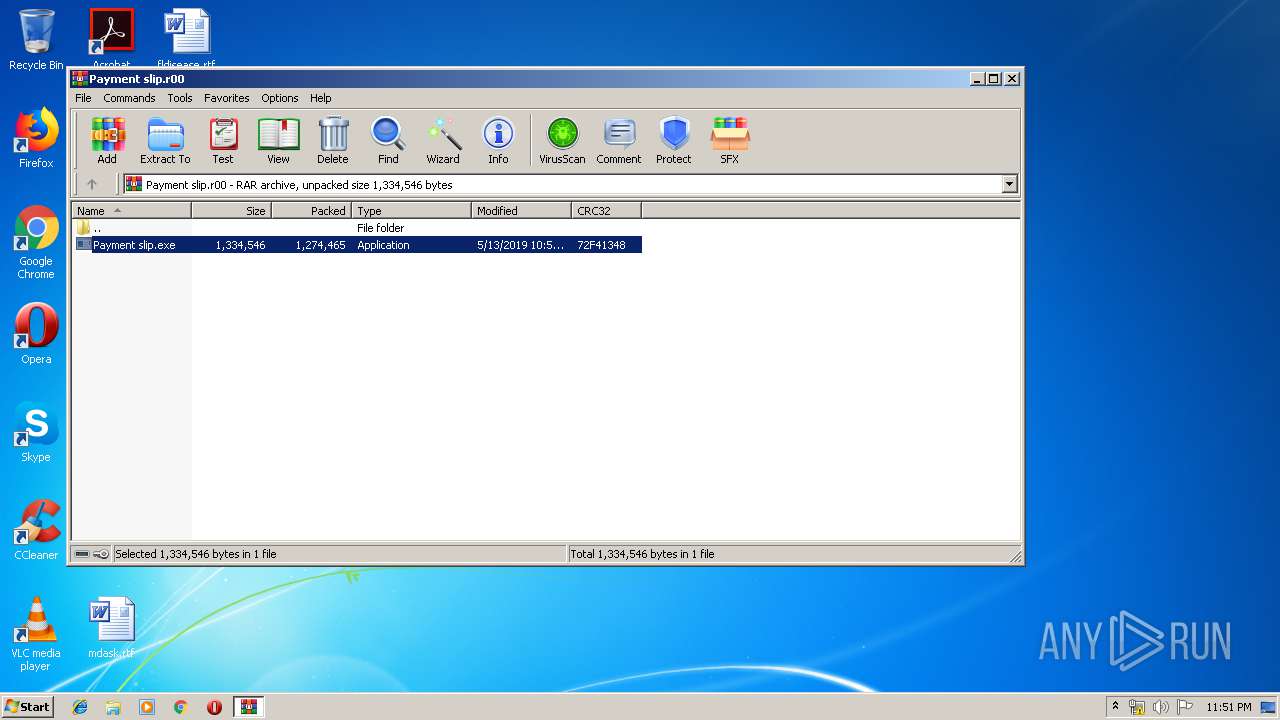
| File name: | Payment slip.r00 |
| Full analysis: | https://app.any.run/tasks/84460516-d512-4c0a-b7b2-d8925273a129 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | May 14, 2019, 22:51:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5BE6F6F30D87CA5DAF0753C40D17E10B |
| SHA1: | 400D51E9B74D17C82EF4D115EF0FF1B76EB15EDE |
| SHA256: | 6FFD492EB82A4FF227CDACB0A2FC0AC6368E649F8E4F931D55327C80BED6B9B7 |
| SSDEEP: | 24576:i5/q4JX1Jx+0Z1lGq+vH5DLHCc/u6NDLRFbqBD5slNT9:idXbXvwDLFu6NHbT9 |
MALICIOUS
Changes the autorun value in the registry
- iwa.exe (PID: 2528)
Detected Hawkeye Keylogger
- RegSvcs.exe (PID: 3076)
Application was dropped or rewritten from another process
- Payment slip.exe (PID: 1432)
- iwa.exe (PID: 3664)
- iwa.exe (PID: 2528)
Actions looks like stealing of personal data
- vbc.exe (PID: 1028)
- vbc.exe (PID: 1916)
Stealing of credential data
- vbc.exe (PID: 1916)
SUSPICIOUS
Executable content was dropped or overwritten
- Payment slip.exe (PID: 1432)
- WinRAR.exe (PID: 1440)
Drop AutoIt3 executable file
- Payment slip.exe (PID: 1432)
Application launched itself
- iwa.exe (PID: 3664)
Executes scripts
- RegSvcs.exe (PID: 3076)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 1028)
INFO
Dropped object may contain Bitcoin addresses
- iwa.exe (PID: 3664)
- Payment slip.exe (PID: 1432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
38
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1028 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp5E83.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegSvcs.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 1432 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1440.29818\Payment slip.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1440.29818\Payment slip.exe | WinRAR.exe | ||||||||||||
User: admin Company: I79ES90RF71X Integrity Level: MEDIUM Description: T74KK73VJ83C Exit code: 0 Version: J68ZG74FT75M Modules
| |||||||||||||||
| 1440 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Payment slip.r00" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1916 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp7623.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegSvcs.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 2528 | C:\Users\admin\AppData\Local\Temp\76398576\iwa.exe C:\Users\admin\AppData\Local\Temp\76398576\JATGG | C:\Users\admin\AppData\Local\Temp\76398576\iwa.exe | iwa.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 3076 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | iwa.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 3664 | "C:\Users\admin\AppData\Local\Temp\76398576\iwa.exe" ldw=kvp | C:\Users\admin\AppData\Local\Temp\76398576\iwa.exe | — | Payment slip.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
Total events
878
Read events
827
Write events
51
Delete events
0
Modification events
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Payment slip.r00 | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
0
Text files
53
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1440.29818\Payment slip.exe | executable | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\ColorConstants.xl | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\kef.mp3 | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\FileConstants.bmp | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\ben.ppt | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\bjw.xl | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\qbr.ico | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\dhv.xl | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\pbh.pdf | text | |
MD5:— | SHA256:— | |||
| 1432 | Payment slip.exe | C:\Users\admin\AppData\Local\Temp\76398576\prs.ico | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3076 | RegSvcs.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 15 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3076 | RegSvcs.exe | 77.88.21.38:587 | smtp.yandex.com | YANDEX LLC | RU | whitelisted |
3076 | RegSvcs.exe | 66.171.248.178:80 | bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bot.whatismyipaddress.com |
| shared |
smtp.yandex.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3076 | RegSvcs.exe | A Network Trojan was detected | MALWARE [PTsecurity] Spy.HawkEye IP Check |
2 ETPRO signatures available at the full report