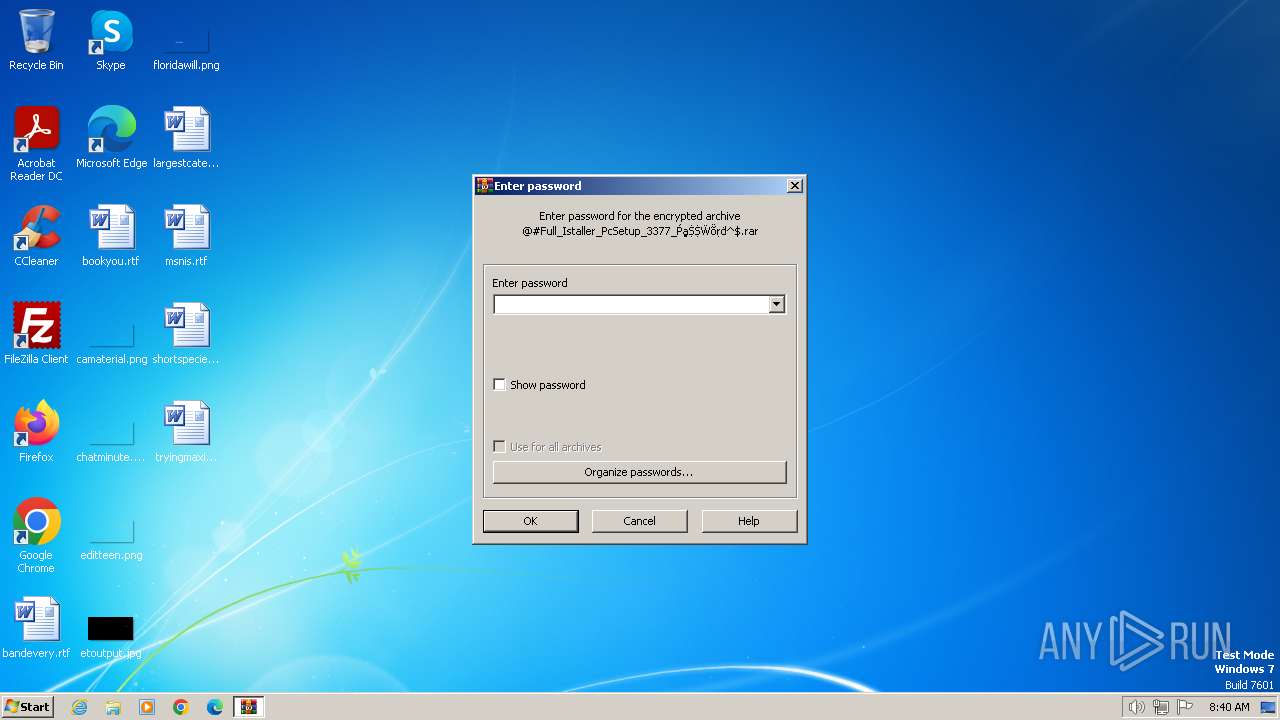
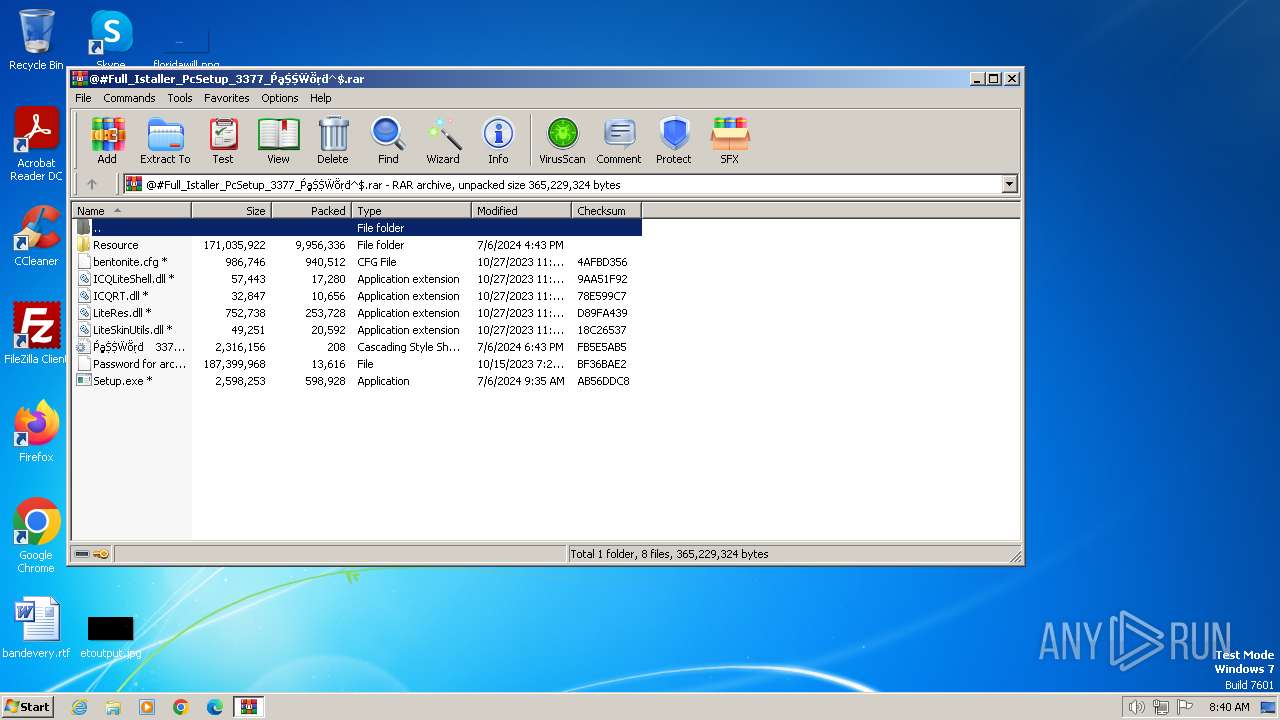
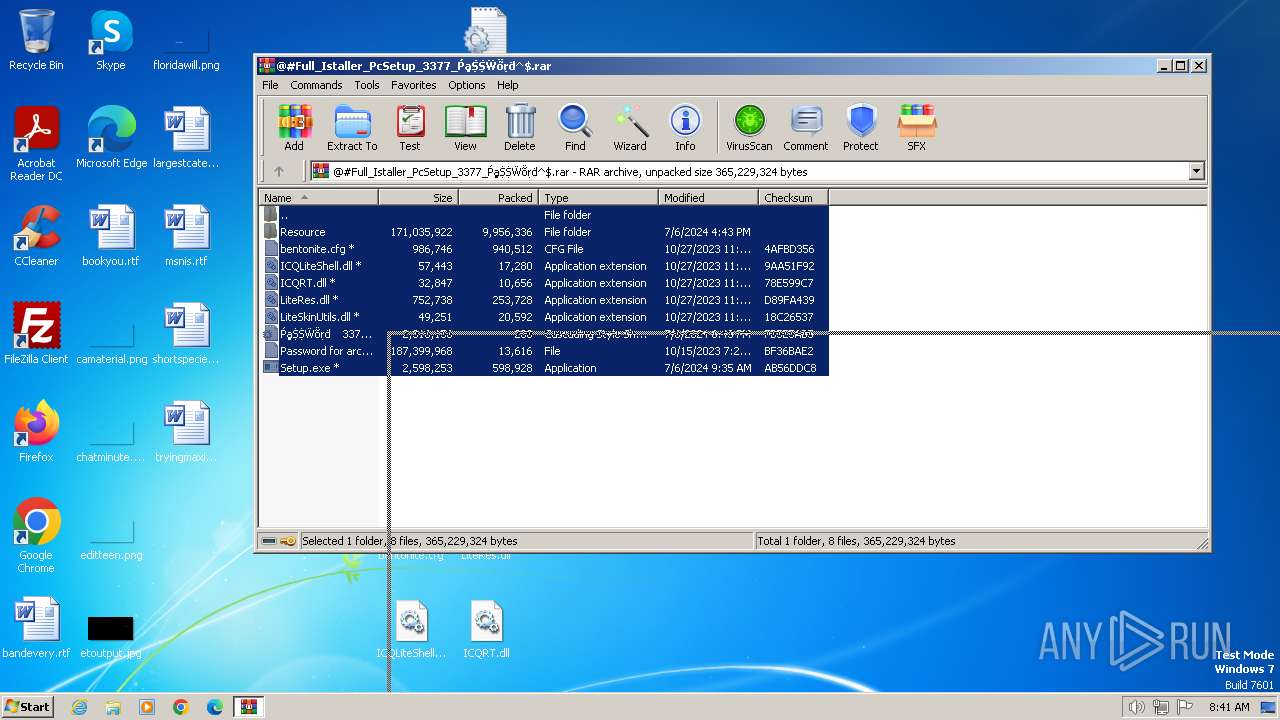
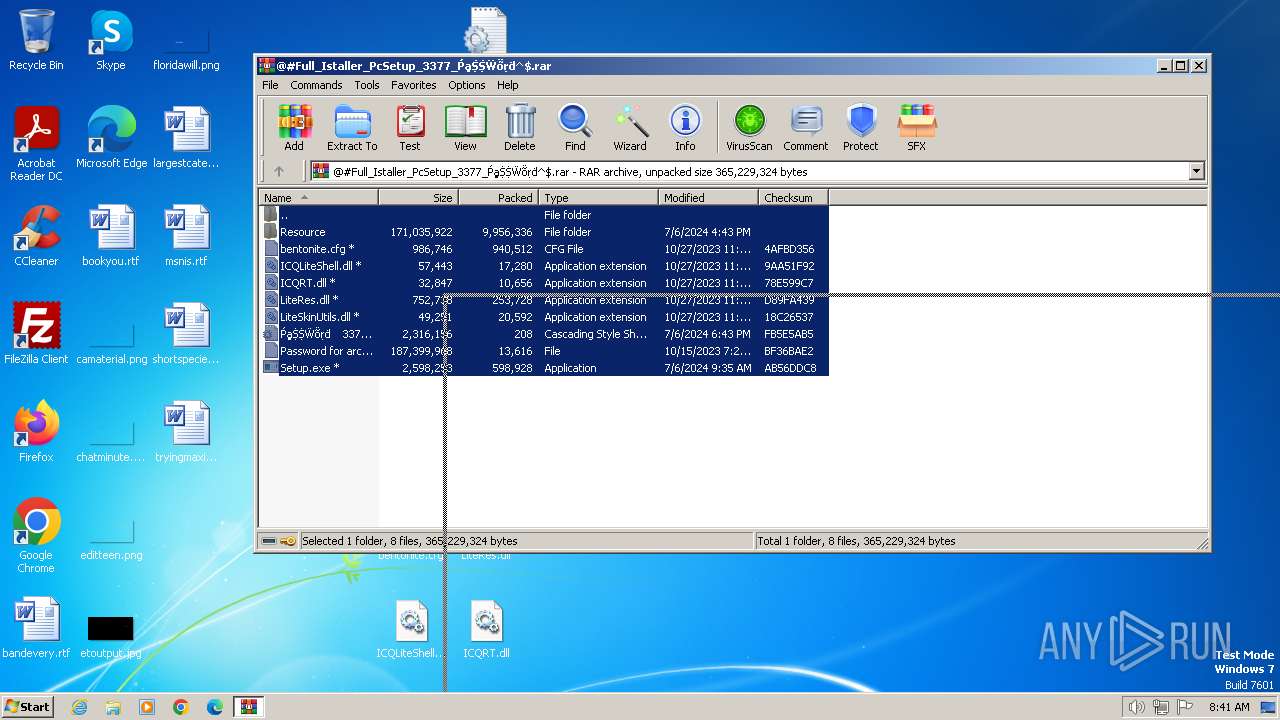
| File name: | @#Full_Istaller_PcSetup_3377_ṔḁṨṨẄṏṛḋ^$.rar |
| Full analysis: | https://app.any.run/tasks/268fb3de-4d61-45b1-ab62-f58b78fbea46 |
| Verdict: | Malicious activity |
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | July 07, 2024, 07:40:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4AFA6DF856AEEF43F946A8FB88FA0EB5 |
| SHA1: | 7356748DDA0A3CC4A3A50D20C89799F25F686F60 |
| SHA256: | 6F848DD7B20B76EE893512963FC7B5BEF1E638C99A43EE40AABFB16341290DCC |
| SSDEEP: | 98304:Y8B+AuYUvEbORdjt++GsSme56DZfBMN8tfo3fUzjBXFmkVEH8b2ug3F6sScsO2+X:St5ESDuv9XWVwXPFVB |
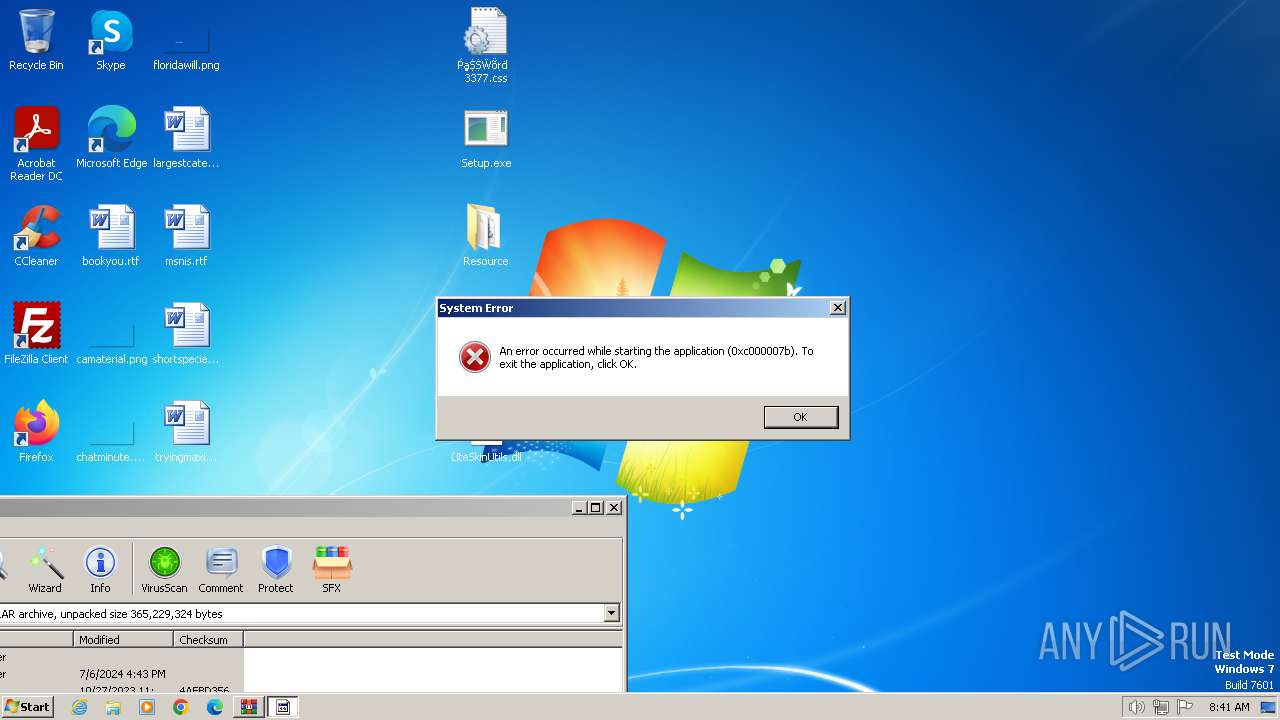
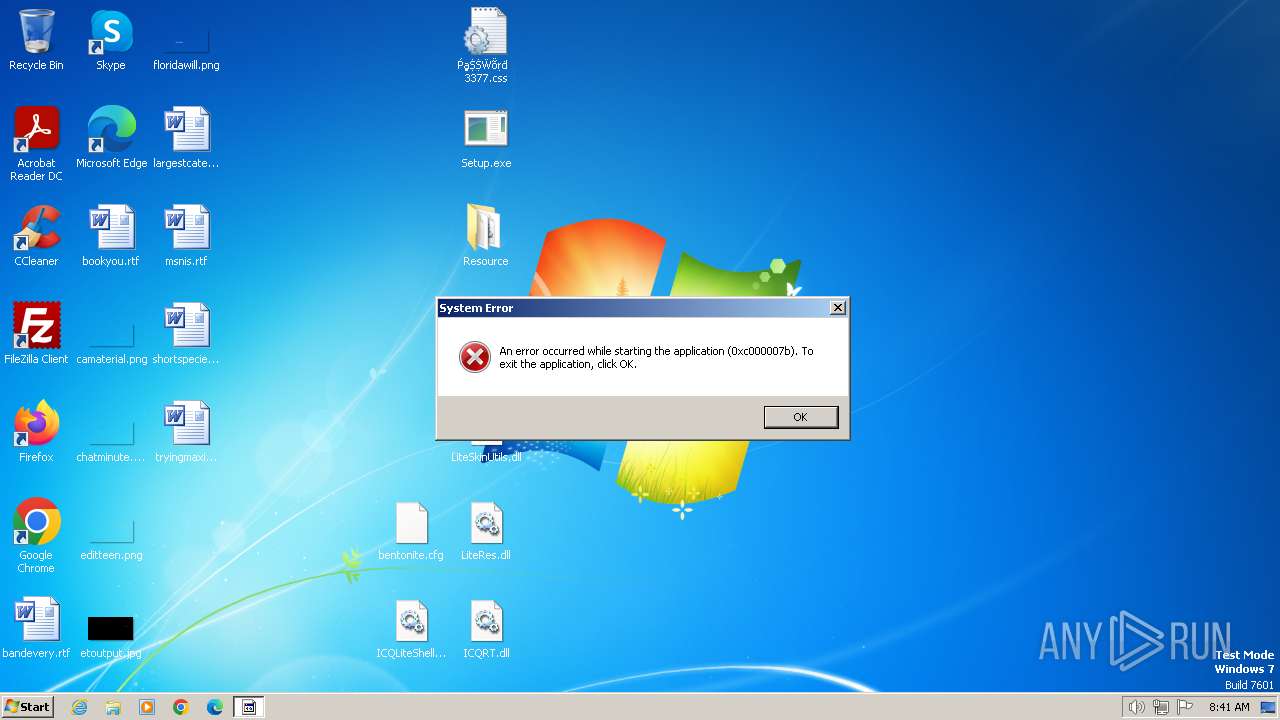
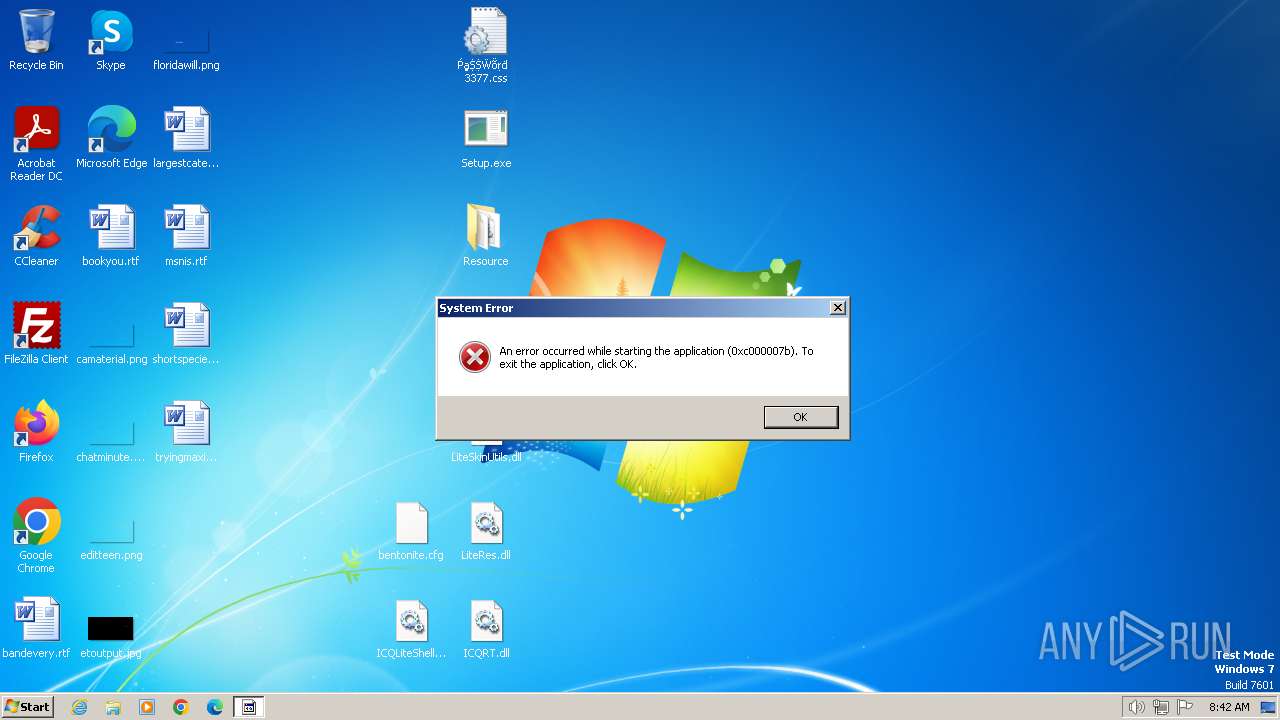
MALICIOUS
Connects to the CnC server
- Sеtup.exe (PID: 3272)
Actions looks like stealing of personal data
- Sеtup.exe (PID: 3272)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3384)
Searches for installed software
- Sеtup.exe (PID: 3272)
Reads browser cookies
- Sеtup.exe (PID: 3272)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3384)
INFO
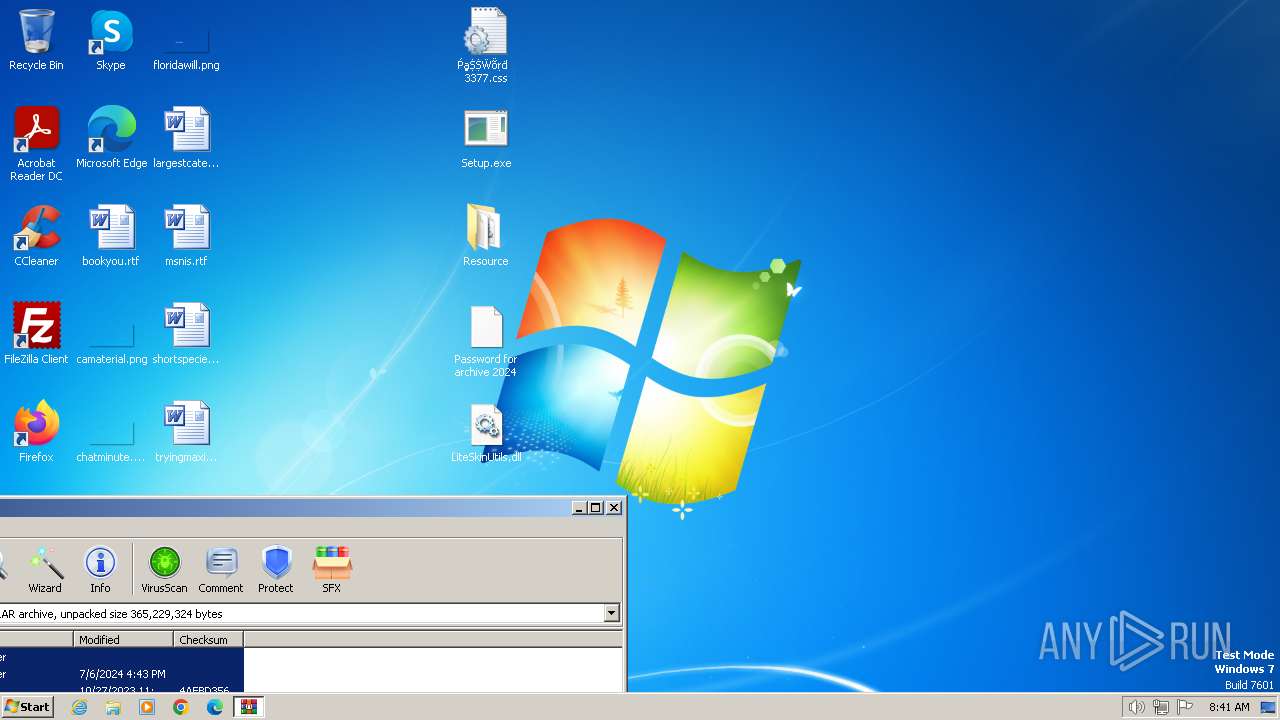
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3384)
Checks supported languages
- Sеtup.exe (PID: 3272)
- Sеtup.exe (PID: 3164)
- Sеtup.exe (PID: 2192)
- Sеtup.exe (PID: 764)
- Sеtup.exe (PID: 2492)
Reads the computer name
- Sеtup.exe (PID: 3272)
Reads CPU info
- Sеtup.exe (PID: 3272)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3384)
Manual execution by a user
- Sеtup.exe (PID: 2192)
- taskmgr.exe (PID: 3612)
- Sеtup.exe (PID: 3164)
- Sеtup.exe (PID: 2492)
- taskmgr.exe (PID: 2428)
- Sеtup.exe (PID: 764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
48
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Users\admin\Desktop\Sеtup.exe" | C:\Users\admin\Desktop\Sеtup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\Desktop\Sеtup.exe" | C:\Users\admin\Desktop\Sеtup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2428 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2492 | "C:\Users\admin\Desktop\Sеtup.exe" | C:\Users\admin\Desktop\Sеtup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3164 | "C:\Users\admin\Desktop\Sеtup.exe" | C:\Users\admin\Desktop\Sеtup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3272 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Sеtup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Sеtup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3384 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\@#Full_Istaller_PcSetup_3377_ṔḁṨṨẄṏṛḋ^$.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3612 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 908
Read events
4 871
Write events
37
Delete events
0
Modification events
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\@#Full_Istaller_PcSetup_3377_ṔḁṨṨẄṏṛḋ^$.rar | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
20
Suspicious files
46
Text files
50
Unknown types
32
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\CourierStd-Bold.otf | otf | |
MD5:404952EC4D0AE00DD2F58FB980A99326 | SHA256:A3C25F2EC60F8D44F150CD4E478067B06CC7267FBAAF844DA600CE1C31C6E5C1 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\CMap\UniKS-UTF16-H | binary | |
MD5:F65C06189A55139E13885D9716BFE35C | SHA256:AB87D320C81E4C761B7A4CBD342E212DB4EBE169B5D10848F2F57D828874E342 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\CMap\Identity-V | binary | |
MD5:B5084CBF0AB0C3DEAC97E06CD3CB2ECC | SHA256:7483DB44E4449A7AE232B30D6CBA0D8746592757D0E91BE82EC45B646C608807 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\Pfm\zx______.pfm | pfm | |
MD5:705CD85804C3DC1EEF81B624EA813BFB | SHA256:B3E66A48A576F1D90277AEFB89AF9CFD370E7C216978234BFE66B6AB6FA2C0FD | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\MinionPro-Bold.otf | otf | |
MD5:B3870BE83F40B14CB382BD498920A137 | SHA256:6AF523A01B268DDAAB5177E6C0DF5024F7192D72B0B1CA9523721FBAA2AA9257 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\MinionPro-It.otf | otf | |
MD5:45E2315E99F24AB596F9D3AED29A0FC3 | SHA256:90DEF22F2B7B3E4AA78A160084A7A2C8F28883B700ABAEDC004DC74CBC2D9B4C | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\AdobePIStd.otf | otf | |
MD5:8653BFE4C32A8528E981748E28C59570 | SHA256:5DBC496C0B5A12D9F9FFDB83A46B9FCDA8D1FC1FCD50832C783BE5E9277A698E | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\MyriadPro-Bold.otf | otf | |
MD5:E6D1585E6C81E3206948D8548D914FEC | SHA256:2D09971801F2C18FC5A825379404113DB237866073AB463A9BF0F3DA8C62459A | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\Pfm\SY______.PFM | pfm | |
MD5:692B5B1BE7394E93FD6E0750CAE81474 | SHA256:035AF7591938139C78F8AD715047C16CD439C6A7791035DEEC013439921E6925 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3384.33504\Resource\Font\MyriadPro-BoldIt.otf | otf | |
MD5:01E3D8472C3CBC43799FED290B0DC219 | SHA256:7BCFA54CB8FB5B64DFE36F411D5265F7F71DC6F3B685C7ED0EB3753EE194BB45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
13
DNS requests
5
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
3272 | Sеtup.exe | POST | 200 | 5.188.88.16:80 | http://tzten10sb.top/v1/upload.php | unknown | — | — | unknown |
3272 | Sеtup.exe | POST | 200 | 5.188.88.16:80 | http://tzten10sb.top/v1/upload.php | unknown | — | — | unknown |
3272 | Sеtup.exe | POST | 200 | 5.188.88.16:80 | http://tzten10sb.top/v1/upload.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
3272 | Sеtup.exe | 5.188.88.16:80 | tzten10sb.top | PINVDS OU | RU | unknown |
1060 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
tzten10sb.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3272 | Sеtup.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3272 | Sеtup.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4 |
3272 | Sеtup.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4 |
3272 | Sеtup.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4 |